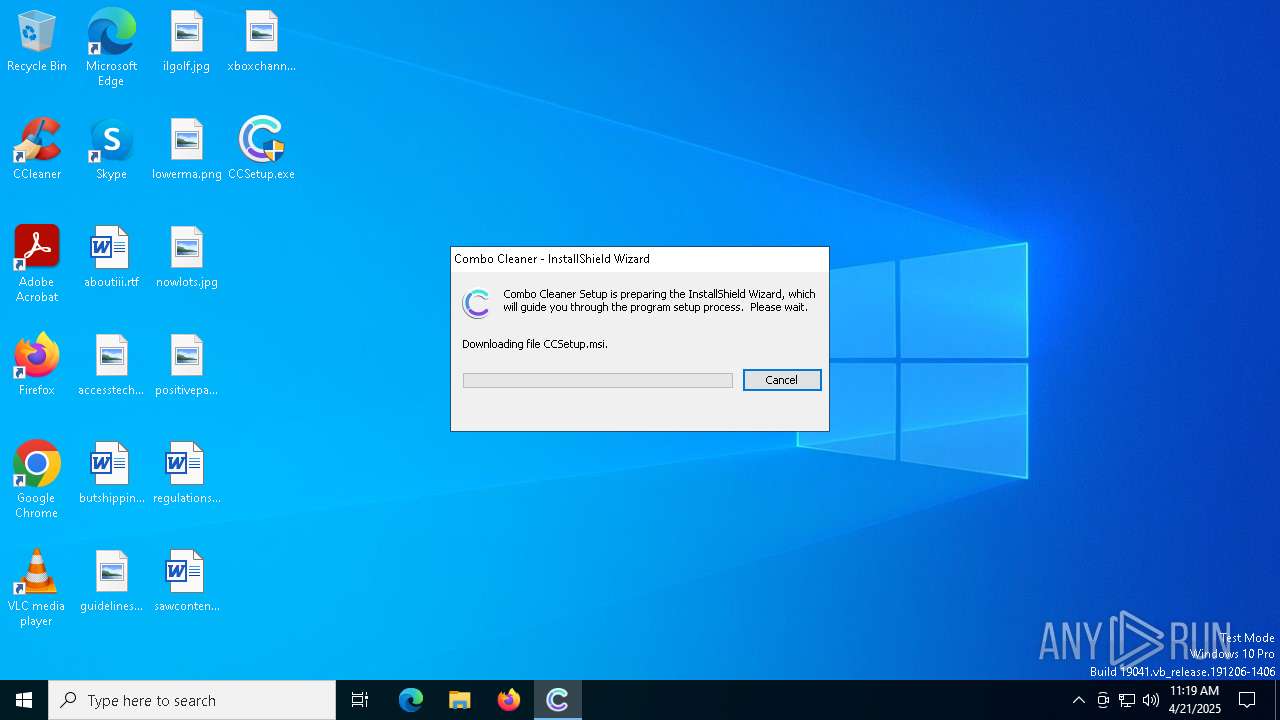
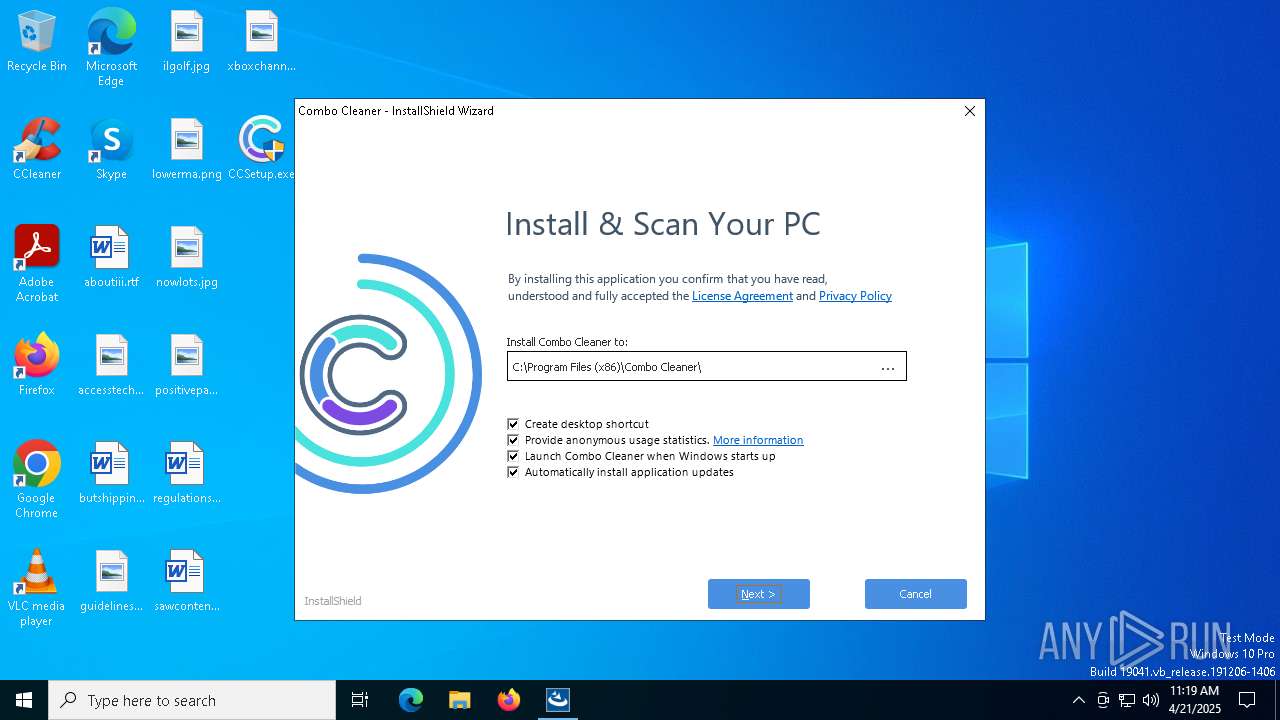
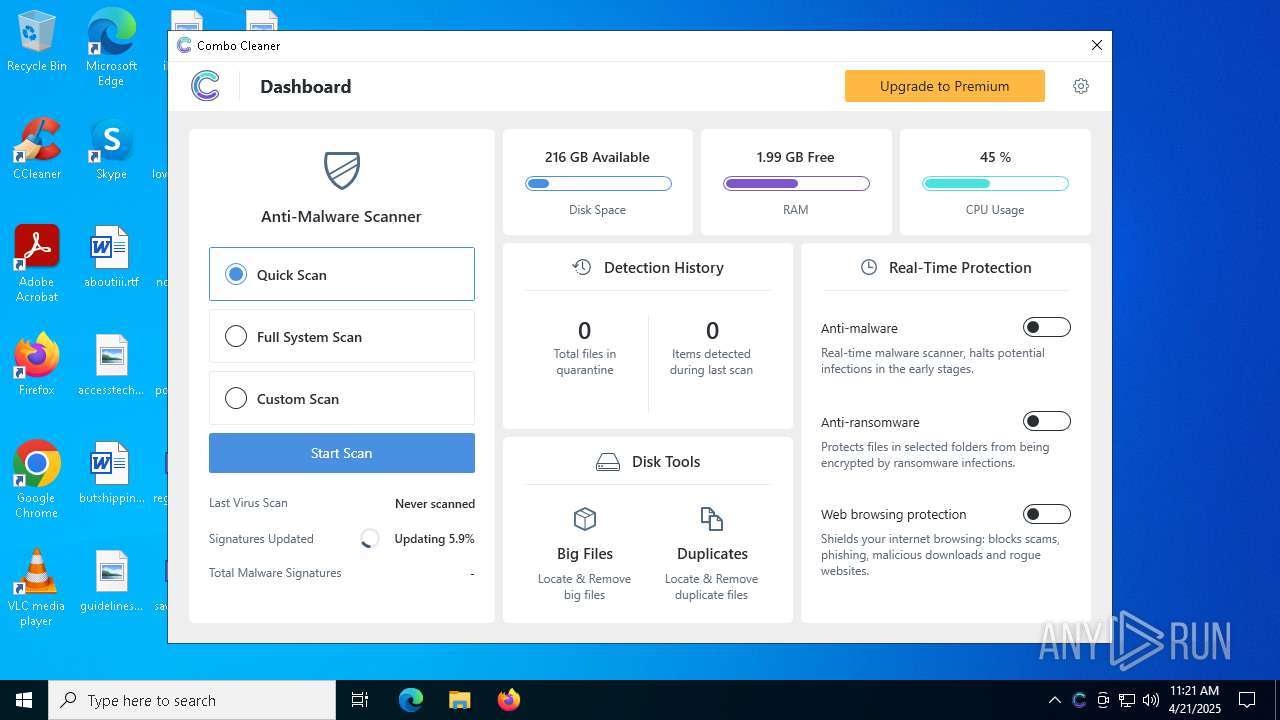
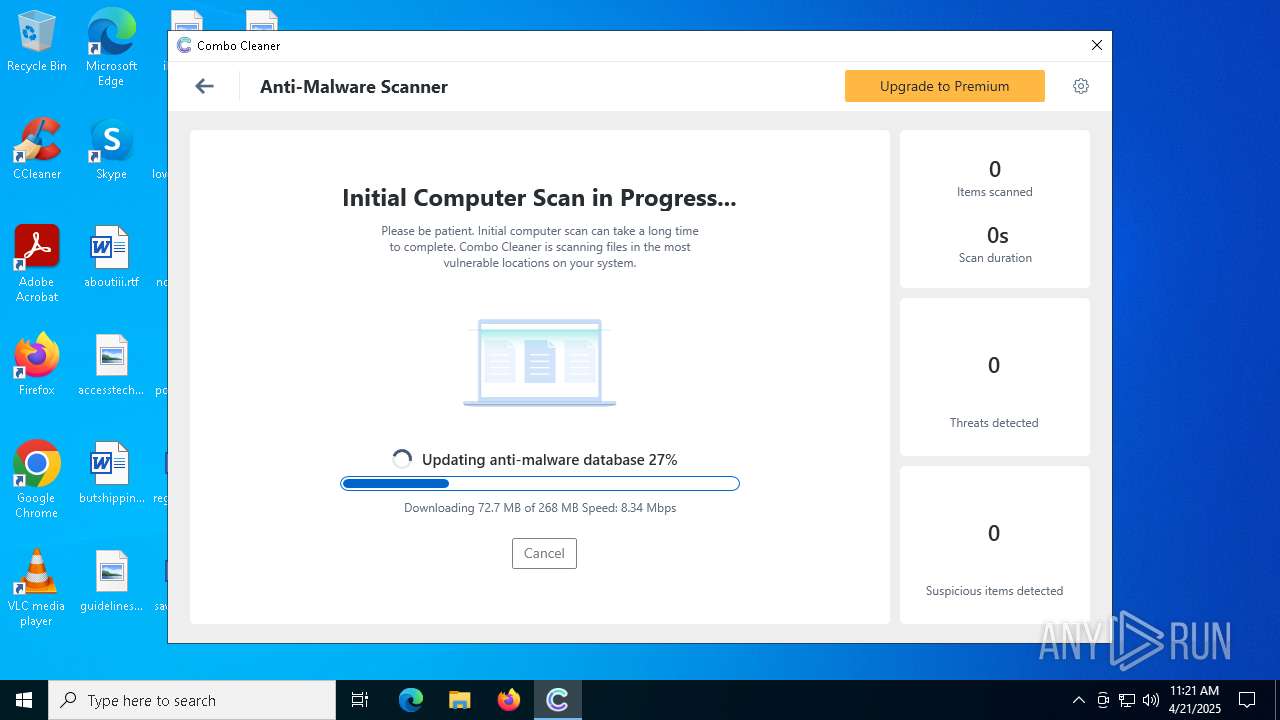
| File name: | CCSetup.exe |
| Full analysis: | https://app.any.run/tasks/df28d858-2d03-49fb-ad5b-98352f72bbe4 |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2025, 11:19:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 0EC9375CDC93C611D2AF8D2B822C142D |
| SHA1: | 6ABD93248D8278B0B17365103DF373E1DC6E1268 |
| SHA256: | B088C2D984211F0468BD6F56E14555CF6AC0E682CFBAD434AFDB85498A148BD5 |
| SSDEEP: | 98304:LlTe0IagfW5Tf+S+PWDCx5KP9MyD4ND2Ysncs0RLrfuPezikohzWlolcIjEMHGN4:0Vl2 |
MALICIOUS
Executing a file with an untrusted certificate
- ISBEW64.exe (PID: 6112)
- ISBEW64.exe (PID: 4620)
- ISBEW64.exe (PID: 5720)
- ISBEW64.exe (PID: 1388)
- ISBEW64.exe (PID: 1116)
- ISBEW64.exe (PID: 5072)
- ISBEW64.exe (PID: 2096)
- ISBEW64.exe (PID: 3332)
- ISBEW64.exe (PID: 6272)
- ISBEW64.exe (PID: 6564)
Changes the autorun value in the registry
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 2096)
- rundll32.exe (PID: 5592)
- CCSetup.exe (PID: 5408)
- ComboCleaner.WinService.exe (PID: 5780)
Starts NET.EXE for service management
- cmd.exe (PID: 6416)
- cmd.exe (PID: 5392)
- net.exe (PID: 3768)
- net.exe (PID: 5392)
- cmd.exe (PID: 2316)
- net.exe (PID: 6392)
SUSPICIOUS
Executable content was dropped or overwritten
- CCSetup.exe (PID: 5408)
- CCSetup.exe (PID: 2392)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 2096)
- rundll32.exe (PID: 5592)
Reads security settings of Internet Explorer
- CCSetup.exe (PID: 5408)
- msiexec.exe (PID: 2420)
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
- ComboCleaner.exe (PID: 3768)
Starts itself from another location
- CCSetup.exe (PID: 2392)
Reads the Windows owner or organization settings
- CCSetup.exe (PID: 5408)
- msiexec.exe (PID: 2420)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- cmd.exe (PID: 1628)
There is functionality for taking screenshot (YARA)
- CCSetup.exe (PID: 2392)
- CCSetup.exe (PID: 5408)
Executes as Windows Service
- VSSVC.exe (PID: 3176)
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
- WmiApSrv.exe (PID: 7372)
- WmiApSrv.exe (PID: 7592)
Searches for installed software
- dllhost.exe (PID: 5392)
- CCSetup.exe (PID: 5408)
- ComboCleaner.WinService.exe (PID: 5780)
Starts CMD.EXE for commands execution
- CCSetup.exe (PID: 5408)
- ComboCleaner.WinService.exe (PID: 5780)
Reads Microsoft Outlook installation path
- CCSetup.exe (PID: 5408)
Reads Internet Explorer settings
- CCSetup.exe (PID: 5408)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 2420)
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 5592)
- rundll32.exe (PID: 2096)
Process drops legitimate windows executable
- msiexec.exe (PID: 2420)
Creates a software uninstall entry
- CCSetup.exe (PID: 5408)
- ComboCleaner.WinService.exe (PID: 5780)
Uses RUNDLL32.EXE to load library
- CCSetup.exe (PID: 5408)
Creates or modifies Windows services
- rundll32.exe (PID: 2552)
- rundll32.exe (PID: 5592)
- ComboCleaner.WinService.exe (PID: 5780)
Sets the service to start on system boot
- sc.exe (PID: 6248)
- sc.exe (PID: 6800)
Reads the date of Windows installation
- ComboCleaner.WinService.exe (PID: 5780)
The process checks if it is being run in the virtual environment
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.exe (PID: 3768)
The process deletes folder without confirmation
- CCSetup.exe (PID: 5408)
INFO
Reads the software policy settings
- CCSetup.exe (PID: 5408)
- msiexec.exe (PID: 2420)
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
- ComboCleaner.exe (PID: 3768)
- slui.exe (PID: 6456)
- slui.exe (PID: 7492)
Checks proxy server information
- CCSetup.exe (PID: 5408)
- ComboCleaner.exe (PID: 3768)
- slui.exe (PID: 7492)
Reads the computer name
- CCSetup.exe (PID: 5408)
- CCSetup.exe (PID: 2392)
- msiexec.exe (PID: 2420)
- msiexec.exe (PID: 960)
- ISBEW64.exe (PID: 2096)
- ISBEW64.exe (PID: 6112)
- ISBEW64.exe (PID: 4620)
- ISBEW64.exe (PID: 5720)
- ISBEW64.exe (PID: 1388)
- ISBEW64.exe (PID: 5072)
- ISBEW64.exe (PID: 3332)
- ISBEW64.exe (PID: 6564)
- ISBEW64.exe (PID: 6272)
- ISBEW64.exe (PID: 1116)
- msiexec.exe (PID: 6004)
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
- ComboCleaner.exe (PID: 3768)
Reads the machine GUID from the registry
- CCSetup.exe (PID: 5408)
- msiexec.exe (PID: 2420)
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
- ComboCleaner.exe (PID: 3768)
Create files in a temporary directory
- CCSetup.exe (PID: 2392)
- CCSetup.exe (PID: 5408)
Checks supported languages
- CCSetup.exe (PID: 5408)
- CCSetup.exe (PID: 2392)
- msiexec.exe (PID: 2420)
- msiexec.exe (PID: 960)
- ISBEW64.exe (PID: 6112)
- ISBEW64.exe (PID: 2096)
- ISBEW64.exe (PID: 4620)
- ISBEW64.exe (PID: 5720)
- ISBEW64.exe (PID: 1388)
- ISBEW64.exe (PID: 5072)
- ISBEW64.exe (PID: 1116)
- ISBEW64.exe (PID: 3332)
- ISBEW64.exe (PID: 6272)
- ISBEW64.exe (PID: 6564)
- msiexec.exe (PID: 6004)
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
- ComboCleaner.exe (PID: 3768)
The sample compiled with english language support
- CCSetup.exe (PID: 2392)
- CCSetup.exe (PID: 5408)
- msiexec.exe (PID: 2420)
- rundll32.exe (PID: 5592)
- rundll32.exe (PID: 2096)
Creates files or folders in the user directory
- CCSetup.exe (PID: 5408)
- ComboCleaner.exe (PID: 3768)
Manages system restore points
- SrTasks.exe (PID: 2284)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2420)
Creates a software uninstall entry
- msiexec.exe (PID: 2420)
Creates files in the program directory
- CCSetup.exe (PID: 5408)
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
Process checks computer location settings
- CCSetup.exe (PID: 5408)
Creates files in the driver directory
- rundll32.exe (PID: 5592)
- rundll32.exe (PID: 2096)
- rundll32.exe (PID: 2552)
Reads security settings of Internet Explorer
- runonce.exe (PID: 744)
- runonce.exe (PID: 920)
- runonce.exe (PID: 2192)
Reads the time zone
- runonce.exe (PID: 744)
- runonce.exe (PID: 920)
- runonce.exe (PID: 2192)
- ComboCleaner.exe (PID: 3768)
- ComboCleaner.WinService.exe (PID: 5780)
Reads Environment values
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
- ComboCleaner.exe (PID: 3768)
Disables trace logs
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.Guard.exe (PID: 2192)
- ComboCleaner.exe (PID: 3768)
Reads CPU info
- ComboCleaner.WinService.exe (PID: 5780)
- ComboCleaner.exe (PID: 3768)
Reads Windows Product ID
- ComboCleaner.Guard.exe (PID: 2192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:23 00:55:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 614400 |
| InitializedDataSize: | 776704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5851a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.51.0 |
| ProductVersionNumber: | 1.0.51.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | RCS LT |
| FileDescription: | Combo Cleaner |
| FileVersion: | 1.0.51.0 |
| InternalName: | Setup |
| LegalCopyright: | Copyright (c) 2021 RCS LT, UAB. All Rights Reserved. |
| OriginalFileName: | CCSetup.exe |
| ProductName: | Combo Cleaner |
| ProductVersion: | 1.0.51.0 |
| InternalBuildNumber: | 200860 |
| ISInternalVersion: | 26.0.717 |
| ISInternalDescription: | Setup Launcher Unicode |
Total processes
195
Monitored processes
59
Malicious processes
7
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | C:\WINDOWS\system32\net1 start trufos | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\System32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | C:\Windows\syswow64\MsiExec.exe -Embedding 1F696033D65E568AE6B792D461E5FCB8 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | C:\Users\admin\AppData\Local\Temp\{6428AE8F-E773-4C20-9BE9-92D7BE2C9EA2}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{E062BB9C-F2E3-4E46-8779-3BF70690B607} | C:\Users\admin\AppData\Local\Temp\{6428AE8F-E773-4C20-9BE9-92D7BE2C9EA2}\ISBEW64.exe | — | CCSetup.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 26.0.717 Modules
| |||||||||||||||
| 1388 | C:\Users\admin\AppData\Local\Temp\{6428AE8F-E773-4C20-9BE9-92D7BE2C9EA2}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{F6495546-5681-4002-80A9-1070EA48D437} | C:\Users\admin\AppData\Local\Temp\{6428AE8F-E773-4C20-9BE9-92D7BE2C9EA2}\ISBEW64.exe | — | CCSetup.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 26.0.717 Modules
| |||||||||||||||
| 1628 | CMD.EXE /C driverquery /v >C:\Users\admin\AppData\Local\Temp\drivers.txt | C:\Windows\SysWOW64\cmd.exe | — | CCSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 749
Read events
46 150
Write events
565
Delete events
34
Modification events
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | delete value | Name: | %IS_PREREQ%-Combo Cleaner |
Value: | |||
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | delete value | Name: | %IS_PREREQF%-Combo Cleaner |
Value: | |||
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | ISSetupPrerequisistes |
Value: | |||
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
| (PID) Process: | (5408) CCSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009D645C53AFB2DB012015000044190000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5392) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000074D85E53AFB2DB0110150000FC050000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
89
Suspicious files
1 446
Text files
38
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5408 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\{2CB9AC60-D914-45A7-895C-687FB55EEDD6}\Setup.INI | text | |
MD5:153880A11587FCAC6200AC33F96EC901 | SHA256:14E055AD797E92BC9A257428A784418DEF63A7303FA4E6F4B9F6C8BAFA5D26E4 | |||
| 2392 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\~ECA7.tmp | text | |
MD5:153880A11587FCAC6200AC33F96EC901 | SHA256:14E055AD797E92BC9A257428A784418DEF63A7303FA4E6F4B9F6C8BAFA5D26E4 | |||
| 2392 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\~EC75.tmp | text | |
MD5:153880A11587FCAC6200AC33F96EC901 | SHA256:14E055AD797E92BC9A257428A784418DEF63A7303FA4E6F4B9F6C8BAFA5D26E4 | |||
| 2392 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\{2CB9AC60-D914-45A7-895C-687FB55EEDD6}\_ISMSIDEL.INI | binary | |
MD5:F73B54796E5584CFFF36ED31E33530A6 | SHA256:37A016E73837FDD46B5ABAA4D1238552C38BCFEE9FE2C496A609B3AEDA5481A8 | |||
| 2392 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\~EC96.tmp | text | |
MD5:153880A11587FCAC6200AC33F96EC901 | SHA256:14E055AD797E92BC9A257428A784418DEF63A7303FA4E6F4B9F6C8BAFA5D26E4 | |||
| 2392 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\{2CB9AC60-D914-45A7-895C-687FB55EEDD6}\CCSetup.exe | executable | |
MD5:0EC9375CDC93C611D2AF8D2B822C142D | SHA256:B088C2D984211F0468BD6F56E14555CF6AC0E682CFBAD434AFDB85498A148BD5 | |||
| 5408 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\{2CB9AC60-D914-45A7-895C-687FB55EEDD6}\setup.isn | binary | |
MD5:A9BAD727B8E7A1AD4C73EBCAB5B410F6 | SHA256:CCFA9FA871EB031B63AEC18EECA0CB7484A40F3AB52DBD8CF3ABB79E9DA03B2C | |||
| 5408 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\~ED70.tmp | text | |
MD5:153880A11587FCAC6200AC33F96EC901 | SHA256:14E055AD797E92BC9A257428A784418DEF63A7303FA4E6F4B9F6C8BAFA5D26E4 | |||
| 5408 | CCSetup.exe | C:\Users\admin\AppData\Local\Temp\{2CB9AC60-D914-45A7-895C-687FB55EEDD6}\CCSetup.isc | binary | |
MD5:79A8A52C2E0B4CF3A8ADFCAE1B245AF2 | SHA256:BCA1CAEEE69A58AEE5551272FC81C292E2574544A923E355EBE63E1FE807EEA6 | |||
| 5408 | CCSetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8890A77645B73478F5B1DED18ACBF795_C090A8C88B266C6FF99A97210E92B44D | binary | |
MD5:50FE3B308DF64009DC7B1A61DE57C1E1 | SHA256:B52D4A2ED816C2DD69556BEAA584A88E2A5CD4CC8D31517F586B102C4F90A1F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
47
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5680 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5408 | CCSetup.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5408 | CCSetup.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | unknown | — | — | whitelisted |
5408 | CCSetup.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEAd8LSBEPUs0z7O3OaCLOzM%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6132 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6132 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5780 | ComboCleaner.WinService.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5680 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5408 | CCSetup.exe | 104.25.186.50:443 | services.combocleaner.com | CLOUDFLARENET | US | unknown |
5408 | CCSetup.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | whitelisted |
5408 | CCSetup.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
services.combocleaner.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |