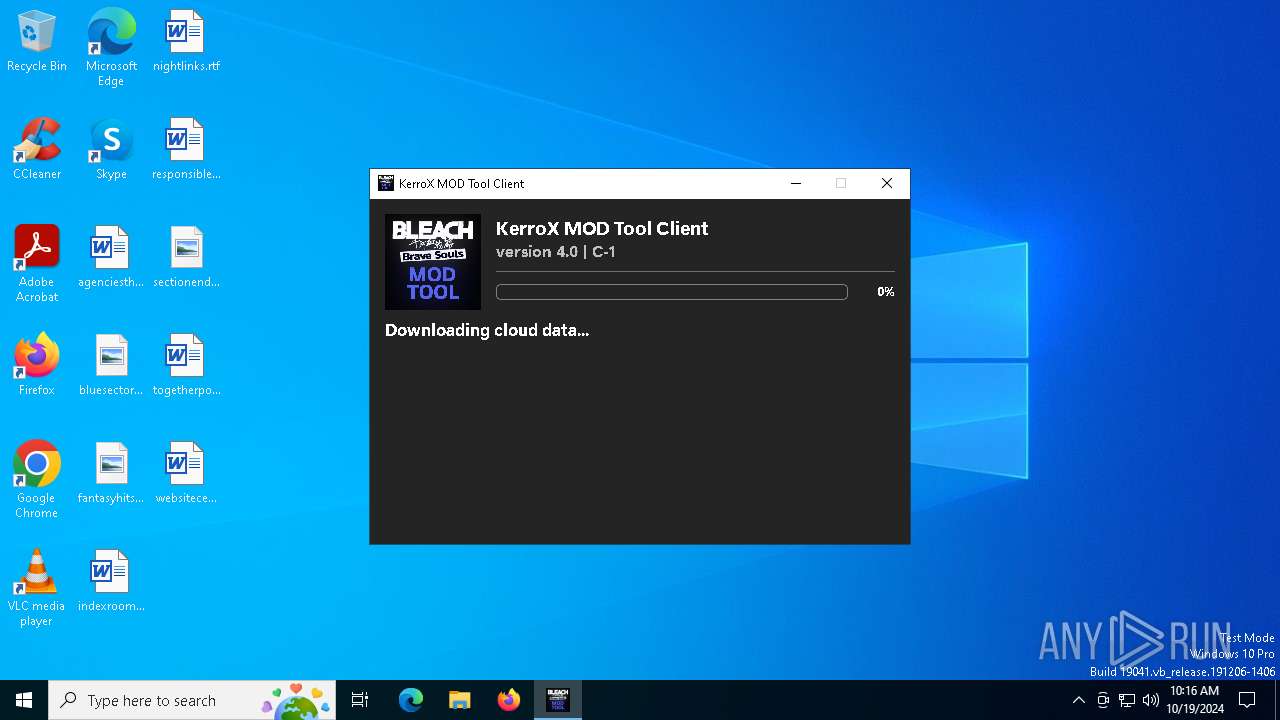
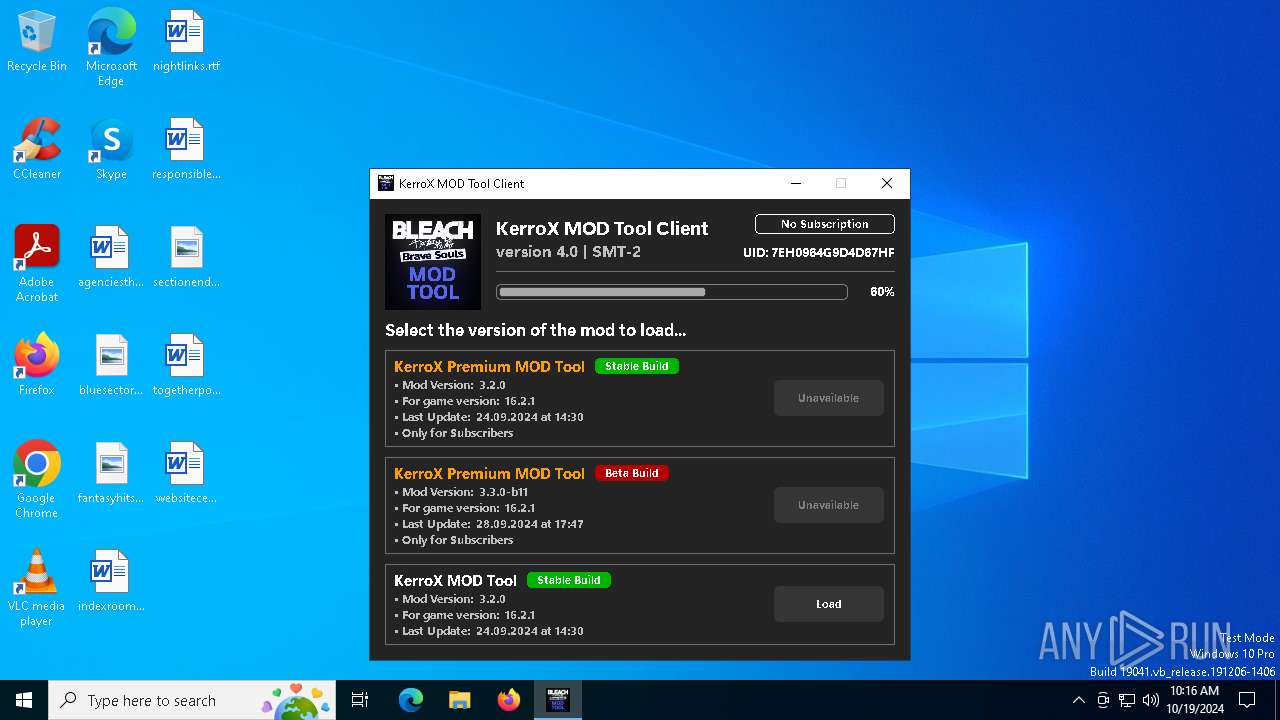
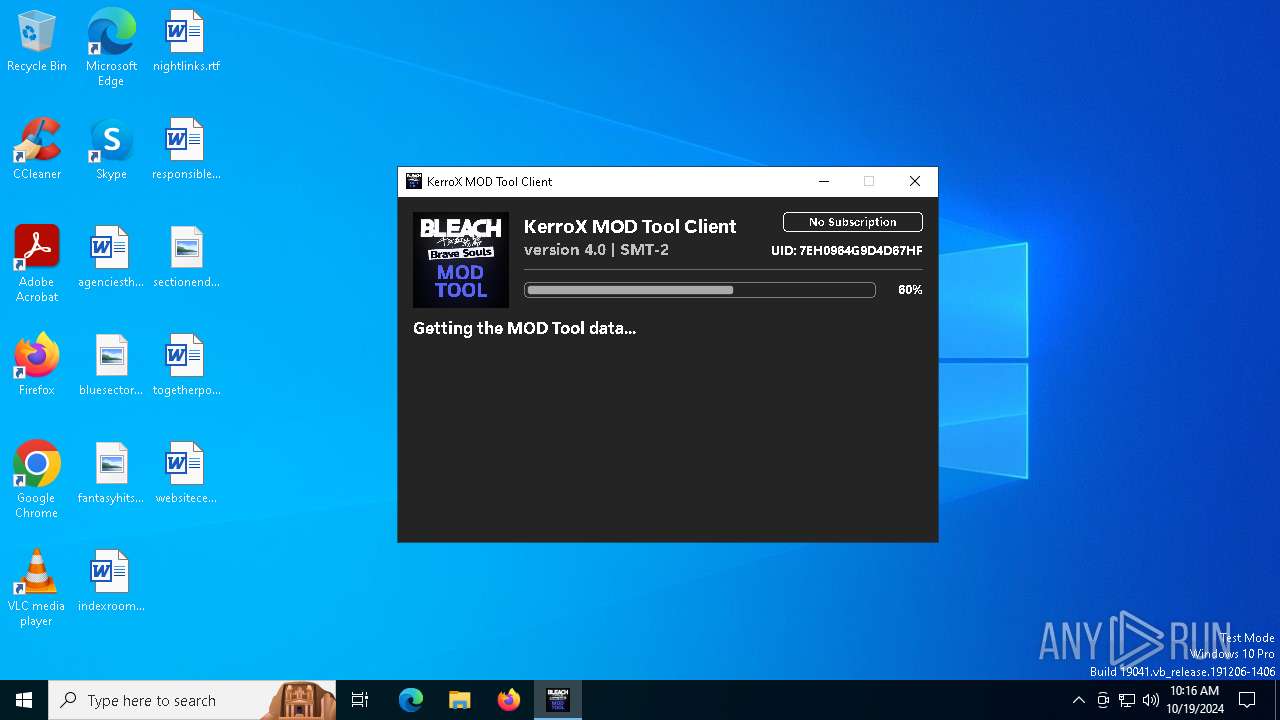
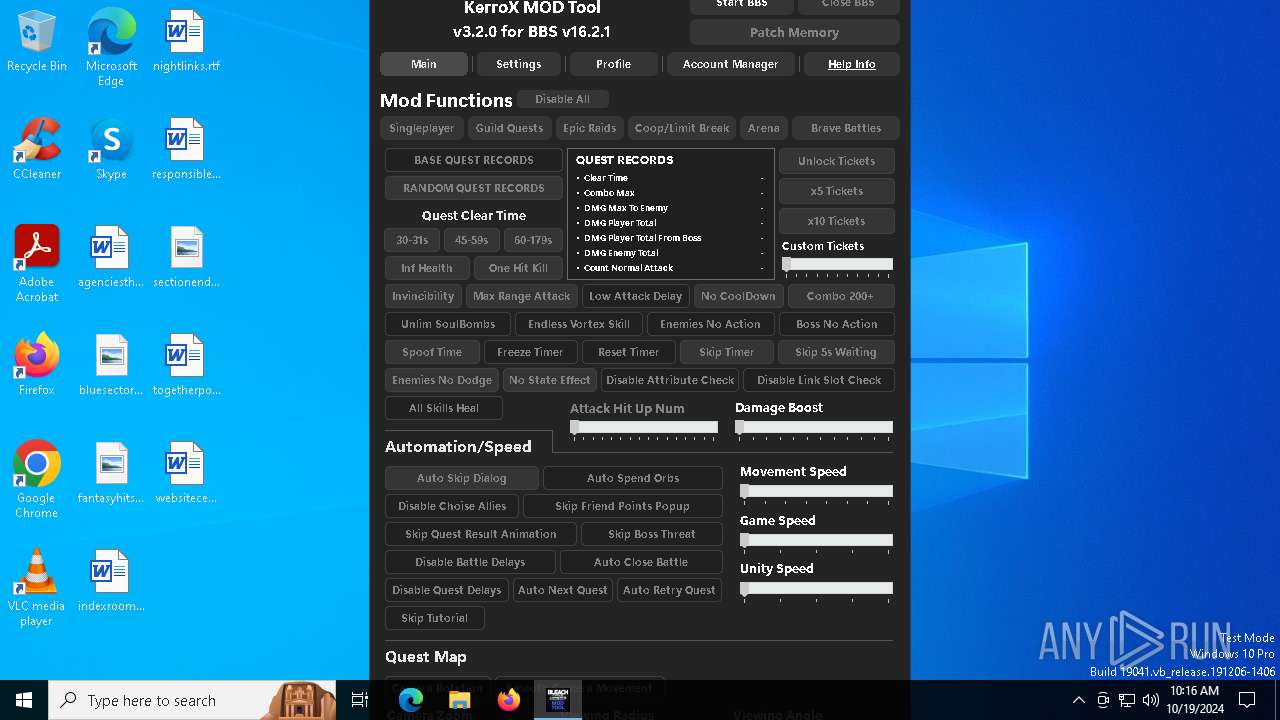
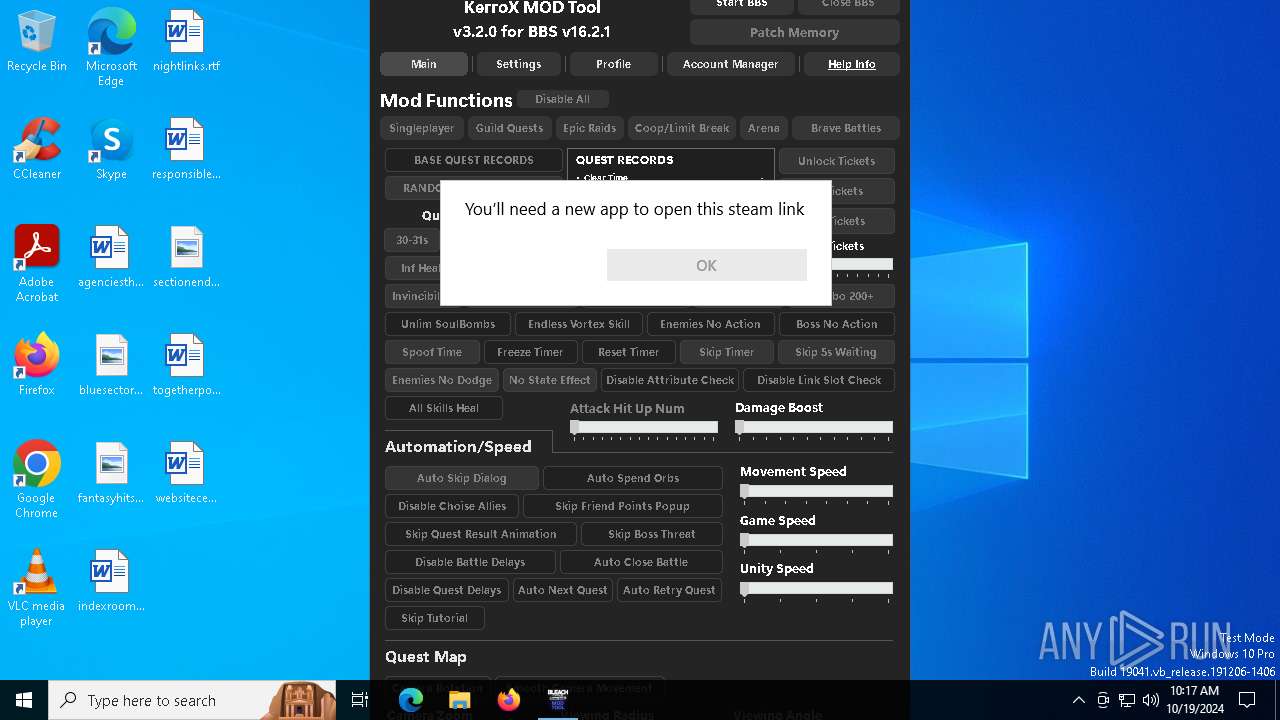
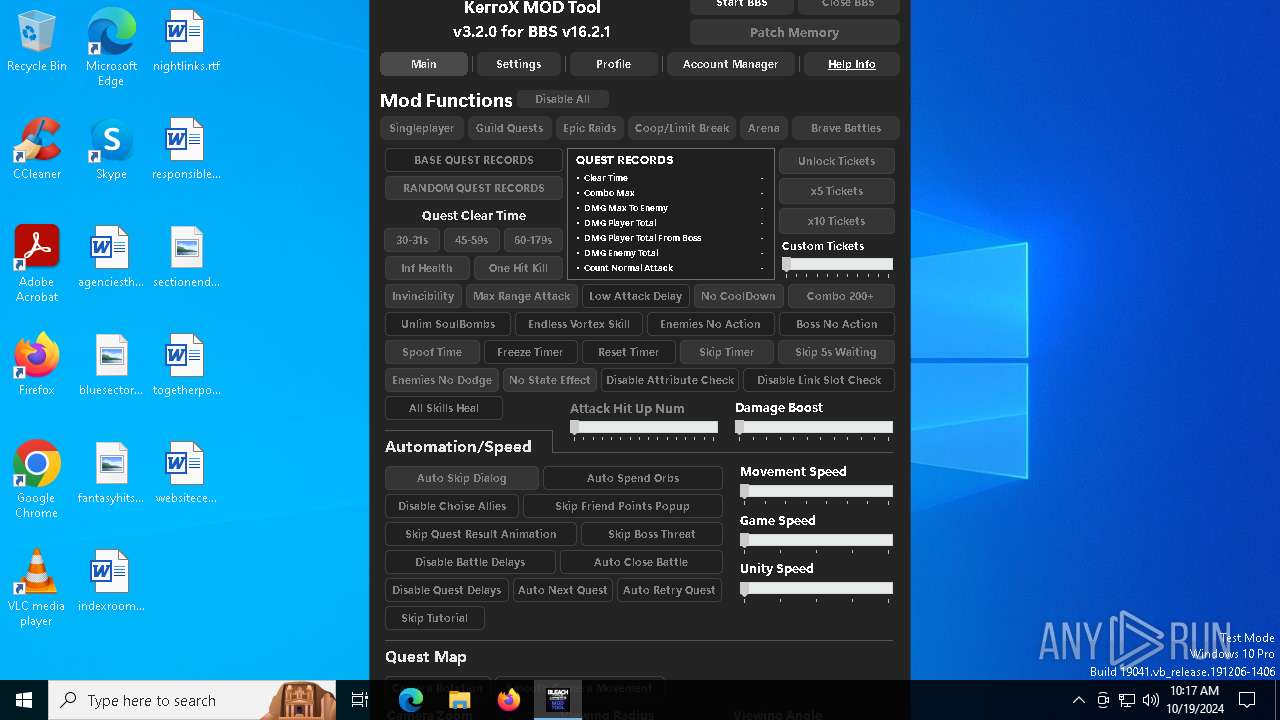
| File name: | KMT Client v4.0.EXE |
| Full analysis: | https://app.any.run/tasks/adfe9262-942d-4099-a17d-6706eae2ee13 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2024, 10:16:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0FB34582812451214830EA41086C9278 |
| SHA1: | 3DA2109D4B19A6C98E8A7B67183260AC6CA13FD5 |
| SHA256: | B058C246F7EF1C919D8A134F5F28FA8FEF4D37F2BCB8991A98E5800190685229 |
| SSDEEP: | 98304:KiSooXgMj6cT5a8VpaMuki5ClG/mbpCLOhK/YaFLeZArWie4JUbYX2Fe8L5gXd5u:zkuSS+H0EaoY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- KMT Client v4.0.EXE.exe (PID: 1156)
- KMT Client v4.0.EXE.exe (PID: 3568)
Reads security settings of Internet Explorer
- KMT Client v4.0.EXE.exe (PID: 6464)
Checks Windows Trust Settings
- KMT Client v4.0.EXE.exe (PID: 6464)
The process checks if it is being run in the virtual environment
- KMT Client v4.0.EXE.exe (PID: 6464)
Read disk information to detect sandboxing environments
- KMT Client v4.0.EXE.exe (PID: 6464)
There is functionality for communication over UDP network (YARA)
- KMT Client v4.0.EXE.exe (PID: 6464)
Creates file in the systems drive root
- KMT Client v4.0.EXE.exe (PID: 6464)
Detected use of alternative data streams (AltDS)
- KMT Client v4.0.EXE.exe (PID: 6464)
INFO
Create files in a temporary directory
- KMT Client v4.0.EXE.exe (PID: 1156)
- KMT Client v4.0.EXE.exe (PID: 3568)
Checks supported languages
- KMT Client v4.0.EXE.exe (PID: 1156)
- KMT Client v4.0.EXE.exe (PID: 3568)
- KMT Client v4.0.EXE.exe (PID: 6464)
Reads the computer name
- KMT Client v4.0.EXE.exe (PID: 6464)
- KMT Client v4.0.EXE.exe (PID: 1156)
Sends debugging messages
- KMT Client v4.0.EXE.exe (PID: 6464)
Checks proxy server information
- KMT Client v4.0.EXE.exe (PID: 6464)
- slui.exe (PID: 1500)
Reads the software policy settings
- KMT Client v4.0.EXE.exe (PID: 6464)
- slui.exe (PID: 6604)
- slui.exe (PID: 1500)
Creates files or folders in the user directory
- KMT Client v4.0.EXE.exe (PID: 6464)
Reads the machine GUID from the registry
- KMT Client v4.0.EXE.exe (PID: 6464)
Reads product name
- KMT Client v4.0.EXE.exe (PID: 6464)
Process checks computer location settings
- KMT Client v4.0.EXE.exe (PID: 6464)
Reads CPU info
- KMT Client v4.0.EXE.exe (PID: 6464)
Reads the time zone
- KMT Client v4.0.EXE.exe (PID: 6464)
Reads Environment values
- KMT Client v4.0.EXE.exe (PID: 6464)
The process uses Lua
- KMT Client v4.0.EXE.exe (PID: 6464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:06:28 14:45:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 36352 |
| InitializedDataSize: | 8494592 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x15eb |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
144
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1156 | "C:\Users\admin\AppData\Local\Temp\KMT Client v4.0.EXE.exe" | C:\Users\admin\AppData\Local\Temp\KMT Client v4.0.EXE.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1500 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3568 | "C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\KMT Client v4.0.EXE.exe" -ORIGIN:"C:\Users\admin\AppData\Local\Temp\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\KMT Client v4.0.EXE.exe | KMT Client v4.0.EXE.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3864 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4548 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6112 | "C:\Users\admin\AppData\Local\Temp\KMT Client v4.0.EXE.exe" | C:\Users\admin\AppData\Local\Temp\KMT Client v4.0.EXE.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6464 | "C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\KMT Client v4.0.EXE.exe" "C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\CET_TRAINER.CETRAINER" "-ORIGIN:C:\Users\admin\AppData\Local\Temp\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\KMT Client v4.0.EXE.exe | KMT Client v4.0.EXE.exe | ||||||||||||
User: admin Company: KerroX Engine Integrity Level: HIGH Description: KerroX Engine Version: 7.3.1.7297 Modules
| |||||||||||||||
| 6604 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 517
Read events
2 507
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\KerroX Engine |
| Operation: | write | Name: | DPI Aware |
Value: 1 | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\KerroX Engine\Window Positions 96 |
| Operation: | write | Name: | AdvancedOptions Position |
Value: C3000000030100003B0200002F010000 | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\KerroX Engine |
| Operation: | write | Name: | Disable DarkMode Support |
Value: 1 | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MtClnExtraData |
| Operation: | write | Name: | dat1 |
Value: AB78C4A298E6C2579B9AAF858E99A0A6E1C2E284BFB59160 | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MtClnExtraData |
| Operation: | write | Name: | dat3 |
Value: 643765316166653138646635366261302D31373239333332393739 | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MtClnExtraData |
| Operation: | write | Name: | dat2 |
Value: 64646365653833343132373666373762336538303638666333373136623030303665303730623334653861353662656565663362386536666164613365656538 | |||
| (PID) Process: | (6464) KMT Client v4.0.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
8
Suspicious files
13
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1156 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\CET_Archive.dat | — | |
MD5:— | SHA256:— | |||
| 3568 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\CET_TRAINER.CETRAINER | binary | |
MD5:9595C0CF528CCFBDC59CC6997A517ACA | SHA256:B2F45A14EEB29D18349304608BCB717F03E46EE64864497F16DA1EF6D3E97443 | |||
| 3568 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\KMT Client v4.0.EXE.exe | executable | |
MD5:9482A60BBA5F988F0AF50ED48042B390 | SHA256:D82637877302B539E2E6B38F1D69CDD99DD51C306490CC47461107EC7E023658 | |||
| 3568 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\lua53-64.dll | executable | |
MD5:B7C9F1E7E640F1A034BE84AF86970D45 | SHA256:6D0A06B90213F082CB98950890518C0F08B9FC16DBFAB34D400267CB6CDADEFF | |||
| 3568 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\defines.lua | text | |
MD5:50DDB39ECE0AABD0E709ADFC15F93CE2 | SHA256:30B816A90ABBE520BCB6606D022F3C870A72AD05A94522FF64B8395BFC088E67 | |||
| 3568 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\autorun\luasymbols.lua | text | |
MD5:DF4D243AB0407A1F03CCF448232FCF62 | SHA256:C5A35380AF8BEBE96B85377F5F41F8C068CB857C74B9CB85B7467B35C1DE10C4 | |||
| 3568 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\autorun\dlls\MonoDataCollector64.dll | executable | |
MD5:4161FD506386D51D62CF0D71C57ADF40 | SHA256:8D2B4E7251FA504AC6B4F21336AF8988009A828467DB6FE896FBB99A3F43F8A8 | |||
| 3568 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\autorun\forms\MonoDataCollector.frm | xml | |
MD5:03D4DD46084BCBE16A39D72BA22E5446 | SHA256:4F254BBC897AD0E165986D18577E0A04FD31C93CCA542A0999FA0093EDC5BC61 | |||
| 3568 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETB791.tmp\extracted\autorun\dlls\MonoDataCollector32.dll | executable | |
MD5:FD176C8F13EB31E348771E5CEC3A83C4 | SHA256:2A33EB24B091E19FA8D16D11205F8300303831ACE6DE19E5B8F8980589FF075D | |||
| 6464 | KMT Client v4.0.EXE.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:48DFE1CC3EF32BDFF8C68F3EA94516D4 | SHA256:37D46D90C12E9A4D3C47A6DAA447CD7A88610239B13C391BF5DB637FC703CC44 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
69
DNS requests
28
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6464 | KMT Client v4.0.EXE.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
6464 | KMT Client v4.0.EXE.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEA7zMlmFlmqbb5WJwfB6vlk%3D | unknown | — | — | whitelisted |
6464 | KMT Client v4.0.EXE.exe | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6464 | KMT Client v4.0.EXE.exe | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6464 | KMT Client v4.0.EXE.exe | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6464 | KMT Client v4.0.EXE.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEBPySE6YTqxrCQy07ABQAIU%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1584 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6464 | KMT Client v4.0.EXE.exe | 162.125.72.15:443 | dl.dropboxusercontent.com | DROPBOX | US | shared |
6464 | KMT Client v4.0.EXE.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6464 | KMT Client v4.0.EXE.exe | 188.114.97.3:443 | unixtime.org | CLOUDFLARENET | NL | unknown |
6464 | KMT Client v4.0.EXE.exe | 142.250.185.163:80 | c.pki.goog | GOOGLE | US | whitelisted |
6464 | KMT Client v4.0.EXE.exe | 216.239.36.54:443 | us-central1-kerrox-mod-tool-422807.cloudfunctions.net | GOOGLE | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
dl.dropboxusercontent.com |
| shared |
ocsp.digicert.com |
| whitelisted |
unixtime.org |
| unknown |
c.pki.goog |
| whitelisted |
us-central1-kerrox-mod-tool-422807.cloudfunctions.net |
| unknown |
o.pki.goog |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6464 | KMT Client v4.0.EXE.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
6464 | KMT Client v4.0.EXE.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
Process | Message |
|---|---|
KMT Client v4.0.EXE.exe | setDPIAware |
KMT Client v4.0.EXE.exe | DisassemblerThumb init |
KMT Client v4.0.EXE.exe | arm disassembler |
KMT Client v4.0.EXE.exe | Offset of LBR_Count=768 |
KMT Client v4.0.EXE.exe | sizeof fxstate = 512 |
KMT Client v4.0.EXE.exe | MainUnit2 |
KMT Client v4.0.EXE.exe | start |
KMT Client v4.0.EXE.exe | TSymbolListHandler.create 1 |
KMT Client v4.0.EXE.exe | TSymbolListHandler.create 2 |
KMT Client v4.0.EXE.exe | TSymbolListHandler.create exit |