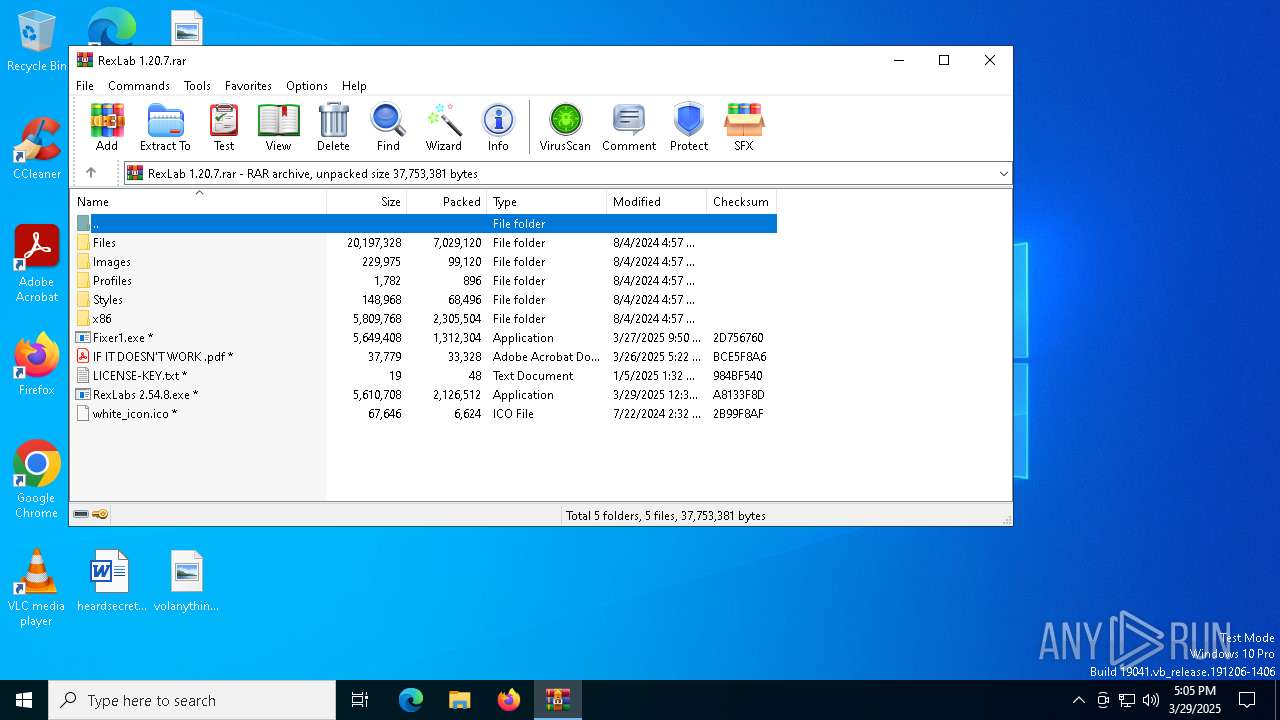
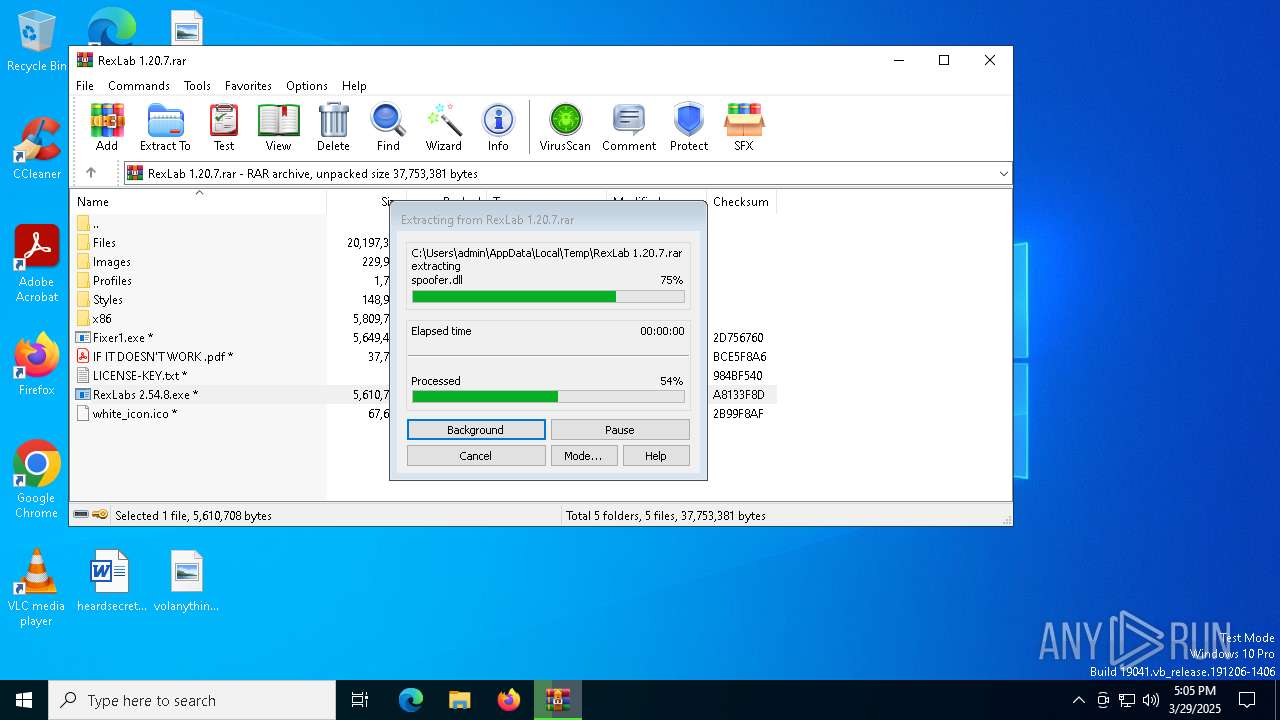
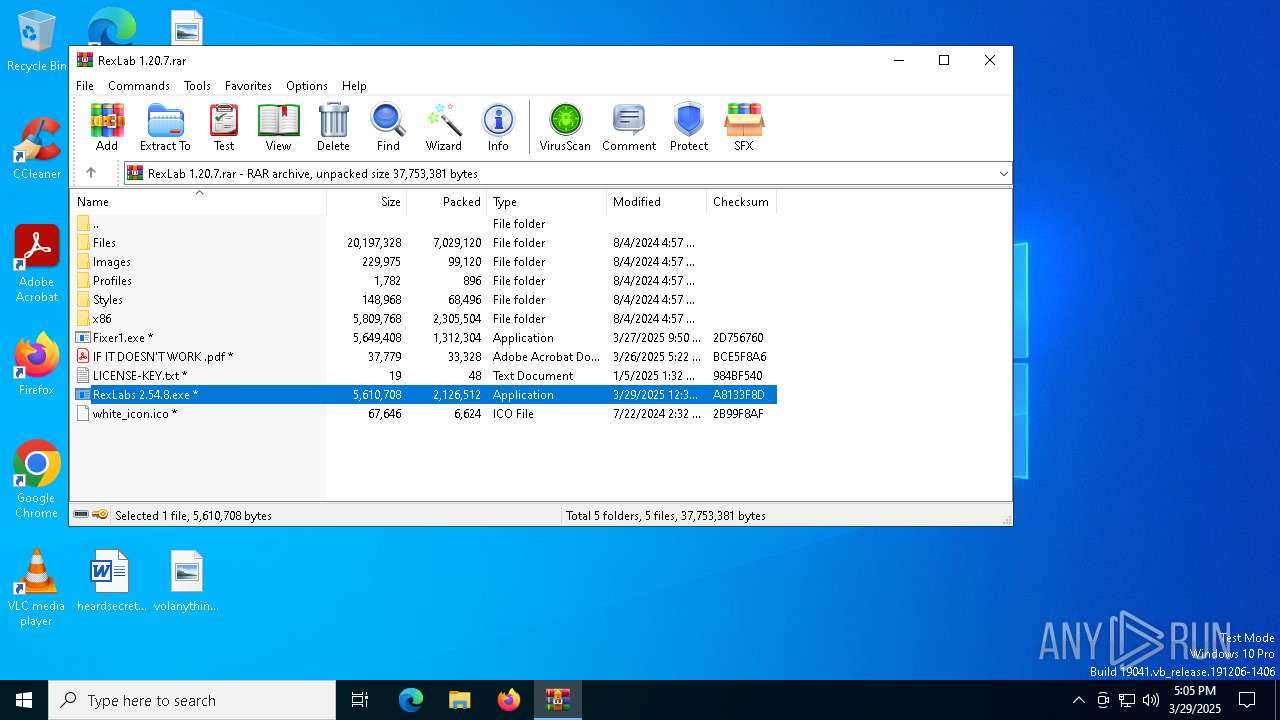
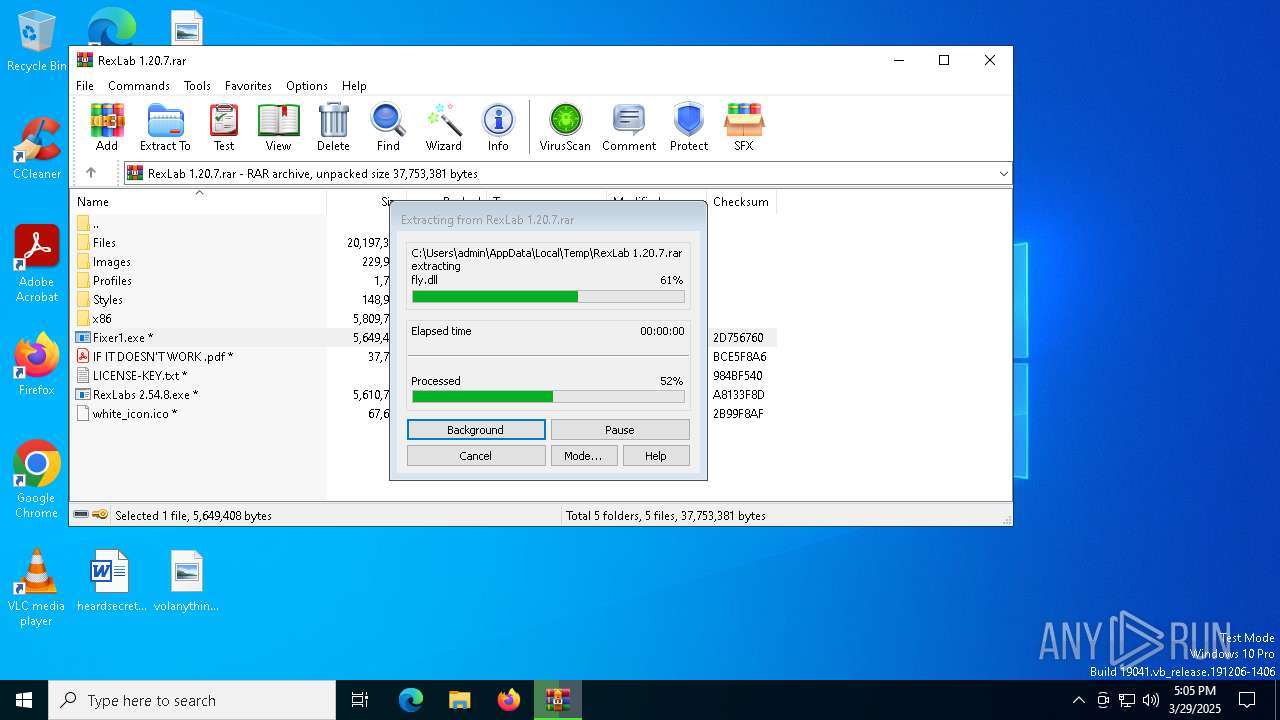
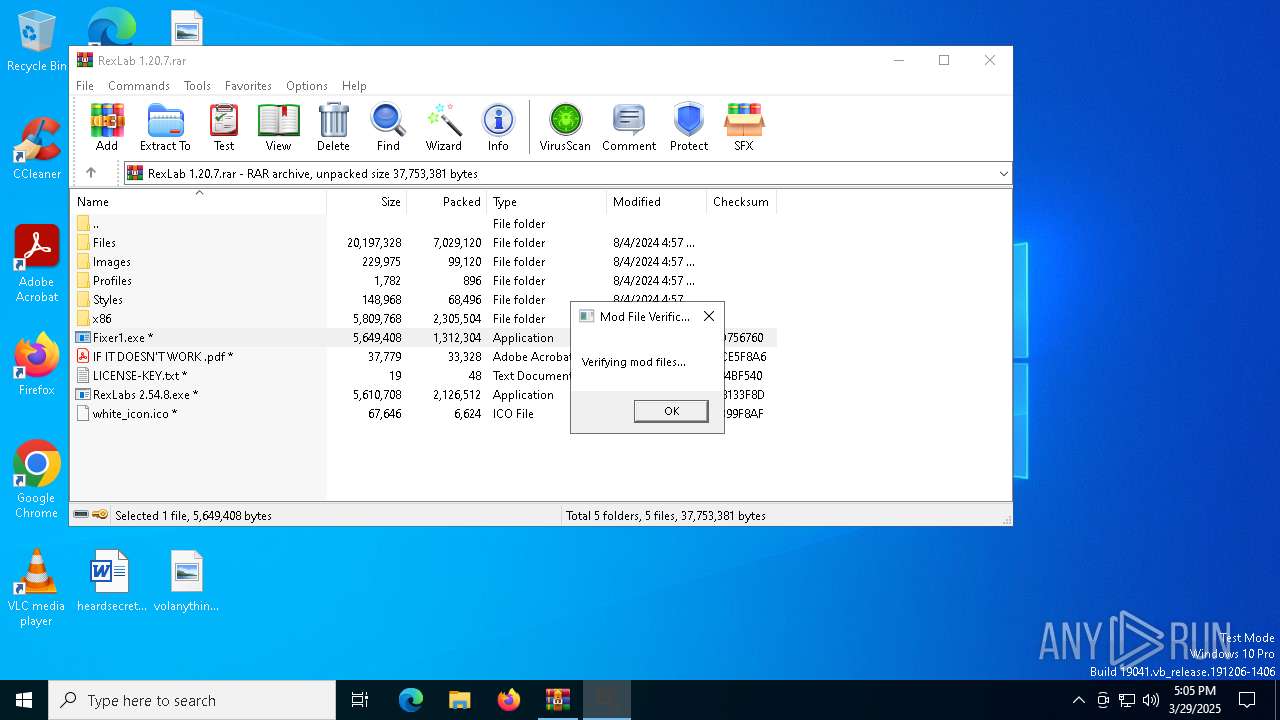
| File name: | RexLab 1.20.7.rar |
| Full analysis: | https://app.any.run/tasks/e50f83e9-f446-4563-938d-71d385bf8222 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | March 29, 2025, 17:04:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 00BE897A69ED95A6099857B3A0D19444 |
| SHA1: | FCFCF6E33D26C9453224982E703EC991F26C305D |
| SHA256: | B0535189AAF557EA6B9BBF14FB8E7D2B727FF27B49E914E10ECB5596E21A4A2B |
| SSDEEP: | 98304:C4xHMPpZm9eELeNRjqOQMhUFbNPggmsq95dZL3YjxBxu2Ki0+haXWIczL8HRan9Y:ODp3S/zoCHULXOz2vzFZE8/ |
MALICIOUS
Deletes a file (SCRIPT)
- wscript.exe (PID: 8092)
Steals credentials from Web Browsers
- RexLabs 2.54.8.exe (PID: 7668)
Run PowerShell with an invisible window
- powershell.exe (PID: 4008)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 7324)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 8144)
- cmd.exe (PID: 968)
- RuntimeBroker.exe (PID: 8164)
Changes Windows Defender settings
- cmd.exe (PID: 8144)
- cmd.exe (PID: 968)
- RuntimeBroker.exe (PID: 8164)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 8144)
- cmd.exe (PID: 968)
- RuntimeBroker.exe (PID: 8164)
Bypass execution policy to execute commands
- powershell.exe (PID: 8168)
- powershell.exe (PID: 7892)
- powershell.exe (PID: 3268)
- powershell.exe (PID: 7468)
- powershell.exe (PID: 8044)
- powershell.exe (PID: 684)
Suspicious browser debugging (Possible cookie theft)
- RexLabs 2.54.8.exe (PID: 7668)
Actions looks like stealing of personal data
- RexLabs 2.54.8.exe (PID: 7668)
Adds process to the Windows Defender exclusion list
- RuntimeBroker.exe (PID: 8164)
Uses Task Scheduler to run other applications
- RuntimeBroker.exe (PID: 8164)
XWORM has been detected (SURICATA)
- RuntimeBroker.exe (PID: 8164)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7420)
- RuntimeBroker.exe (PID: 8164)
Detected use of alternative data streams (AltDS)
- cmd.exe (PID: 7704)
Starts CMD.EXE for commands execution
- RexLabs 2.54.8.exe (PID: 7668)
- wscript.exe (PID: 8092)
- powershell.exe (PID: 4008)
The process checks if it is being run in the virtual environment
- RexLabs 2.54.8.exe (PID: 7668)
Executing commands from a ".bat" file
- wscript.exe (PID: 8092)
- powershell.exe (PID: 4008)
The process executes VB scripts
- Fixer1.exe (PID: 7932)
Loads DLL from Mozilla Firefox
- RexLabs 2.54.8.exe (PID: 7668)
Runs shell command (SCRIPT)
- wscript.exe (PID: 8092)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 8092)
Starts NET.EXE to display or manage information about active sessions
- net.exe (PID: 6640)
- cmd.exe (PID: 8144)
- net.exe (PID: 8060)
- cmd.exe (PID: 968)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8144)
- RexLabs 2.54.8.exe (PID: 7668)
- cmd.exe (PID: 968)
- RuntimeBroker.exe (PID: 8164)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 8092)
Starts process via Powershell
- powershell.exe (PID: 4008)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 7324)
Get information on the list of running processes
- RexLabs 2.54.8.exe (PID: 7668)
Probably obfuscated PowerShell command line is found
- RexLabs 2.54.8.exe (PID: 7668)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 8144)
- cmd.exe (PID: 968)
- RuntimeBroker.exe (PID: 8164)
There is functionality for taking screenshot (YARA)
- RexLabs 2.54.8.exe (PID: 7668)
There is functionality for VM detection VMWare (YARA)
- RexLabs 2.54.8.exe (PID: 7668)
There is functionality for VM detection VirtualBox (YARA)
- RexLabs 2.54.8.exe (PID: 7668)
Downloads file from URI via Powershell
- powershell.exe (PID: 4436)
- powershell.exe (PID: 6876)
Executable content was dropped or overwritten
- powershell.exe (PID: 4436)
- RuntimeBroker.exe (PID: 8164)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 5064)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 5064)
Reads the date of Windows installation
- RuntimeBroker.exe (PID: 8164)
Uses TASKKILL.EXE to kill Browsers
- RexLabs 2.54.8.exe (PID: 7668)
Uses TASKKILL.EXE to kill process
- RexLabs 2.54.8.exe (PID: 7668)
Script adds exclusion process to Windows Defender
- RuntimeBroker.exe (PID: 8164)
Connects to unusual port
- RuntimeBroker.exe (PID: 8164)
Contacting a server suspected of hosting an CnC
- RuntimeBroker.exe (PID: 8164)
INFO
Checks supported languages
- RexLabs 2.54.8.exe (PID: 7668)
- Fixer1.exe (PID: 7932)
- RuntimeBroker.exe (PID: 8164)
- RuntimeBroker.exe (PID: 4944)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7420)
Checks proxy server information
- RexLabs 2.54.8.exe (PID: 7668)
- Fixer1.exe (PID: 7932)
- powershell.exe (PID: 4436)
- powershell.exe (PID: 6876)
Reads the computer name
- Fixer1.exe (PID: 7932)
- RexLabs 2.54.8.exe (PID: 7668)
- RuntimeBroker.exe (PID: 8164)
- RuntimeBroker.exe (PID: 4944)
Reads the software policy settings
- Fixer1.exe (PID: 7932)
- RexLabs 2.54.8.exe (PID: 7668)
- powershell.exe (PID: 6564)
- powershell.exe (PID: 5064)
The sample compiled with english language support
- WinRAR.exe (PID: 7420)
Create files in a temporary directory
- Fixer1.exe (PID: 7932)
- RexLabs 2.54.8.exe (PID: 7668)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 6564)
Reads security settings of Internet Explorer
- powershell.exe (PID: 6564)
- powershell.exe (PID: 5064)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 8168)
- powershell.exe (PID: 8044)
- powershell.exe (PID: 1272)
- powershell.exe (PID: 7892)
- powershell.exe (PID: 684)
- powershell.exe (PID: 3268)
- powershell.exe (PID: 7468)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8044)
- powershell.exe (PID: 8168)
- powershell.exe (PID: 6876)
- powershell.exe (PID: 7892)
- powershell.exe (PID: 3268)
- powershell.exe (PID: 684)
- powershell.exe (PID: 7468)
Disables trace logs
- powershell.exe (PID: 6876)
- powershell.exe (PID: 4436)
Application launched itself
- chrome.exe (PID: 7756)
- msedge.exe (PID: 6744)
- msedge.exe (PID: 780)
- chrome.exe (PID: 7708)
The executable file from the user directory is run by the Powershell process
- RuntimeBroker.exe (PID: 4944)
- RuntimeBroker.exe (PID: 8164)
Reads the machine GUID from the registry
- RuntimeBroker.exe (PID: 8164)
- RuntimeBroker.exe (PID: 4944)
Process checks computer location settings
- RuntimeBroker.exe (PID: 8164)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 6456)
- conhost.exe (PID: 7644)
- conhost.exe (PID: 4756)
- conhost.exe (PID: 6740)
- conhost.exe (PID: 8020)
- conhost.exe (PID: 2084)
- conhost.exe (PID: 5136)
- conhost.exe (PID: 7292)
- conhost.exe (PID: 5228)
- conhost.exe (PID: 1764)
- conhost.exe (PID: 736)
- conhost.exe (PID: 3396)
Creates files or folders in the user directory
- RuntimeBroker.exe (PID: 8164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
251
Monitored processes
126
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "tasklist" | C:\Windows\System32\tasklist.exe | — | RexLabs 2.54.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 496 | "tasklist" | C:\Windows\System32\tasklist.exe | — | RexLabs 2.54.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-sandbox --headless --use-angle=swiftshader-webgl --headless --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1812 --field-trial-handle=1816,i,18098585887489387669,1747860411524569377,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 1 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 664 | "tasklist" | C:\Windows\System32\tasklist.exe | — | RexLabs 2.54.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass Add-MpPreference -ExclusionProcess 'RuntimeBroker.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | RuntimeBroker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tasklist.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tasklist.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --headless --disable-extensions --disable-gpu --no-sandbox --restore-last-session --remote-debugging-port=8761 --remote-allow-origins=* "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --profile-directory=Default --mute-audio | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | RexLabs 2.54.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tasklist.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | "cmdkey" /list:TERMSRV/69.48.201.74 | C:\Windows\System32\cmdkey.exe | — | RexLabs 2.54.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Credential Manager Command Line Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
82 944
Read events
82 921
Write events
23
Delete events
0
Modification events
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RexLab 1.20.7.rar | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4008) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
Executable files
28
Suspicious files
38
Text files
100
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\set-data\aimbot.dll | executable | |
MD5:EB4C38DFFE37658581A4F0FB7A028835 | SHA256:1FE544B454730DF33D926706DD6090E7FFD7DB5222F46D400565730C10BBDD7A | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\q5win1.dll | executable | |
MD5:84476375B8EF7E6B92F663CE3267414B | SHA256:BDB62134D450021D4FC318586AA9AC727C2873C7B425E506984CEA532AA19968 | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\fzs556.dll | executable | |
MD5:EB4C38DFFE37658581A4F0FB7A028835 | SHA256:1FE544B454730DF33D926706DD6090E7FFD7DB5222F46D400565730C10BBDD7A | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\set-data\eshp.dll | executable | |
MD5:B9C72AE386027DC6D784B9A9C85509E2 | SHA256:54FFF33860136D269B8D8E8CFA4AA3326F15425D259A00B2E5E237D4635FA59E | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\set-data\antibug.dll | executable | |
MD5:F0FBFCBB946E9096972E2AA245BA4BDD | SHA256:6FBC547BB8006F2E33234F3830FF1999C2D7FE6205AE2BF33854A02A024E354B | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\set-data\fly.dll | executable | |
MD5:CE7050DACA94E4917645835604F0BE76 | SHA256:0F4823CDECB332BD9534AD986ED8B7AAD93237DF1B78A3D95299D41DE14E41DB | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\qwset.dll | executable | |
MD5:897595076B353BD4D3560F6569BAD1D6 | SHA256:402BA1D0A30C732B7BAA6AF79FDB4EC945CD187968DE3A9A86355ECC13B7D491 | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\set-data\spoofer.dll | executable | |
MD5:9FD770F82F3384F7D65CD54E490F7B09 | SHA256:BB564680227413D0539DC2FC5D14E2F851BFF29D4B8B2791D79628BA86D33C2D | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\Files\set-data\client.dll | executable | |
MD5:85A03F5722B7E2C9A44BA54402573F03 | SHA256:ABAB9EA7BECBE81BEC52DF7D851586F7AC29846CD1E125FDEDF53109D3279A37 | |||
| 7420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7420.22351\x86\setx86.dll | executable | |
MD5:C1EEA8333DF35FD595059DA594734865 | SHA256:B63FDBE90BCD05413401CB534C60463C8BF03CCF62DB7E92A036D8907D32F25D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
26
DNS requests
16
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.172.255.216:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7932 | Fixer1.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
7668 | RexLabs 2.54.8.exe | 104.73.234.102:443 | steamcommunity.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
steamcommunity.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
8164 | RuntimeBroker.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 38 |
8164 | RuntimeBroker.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Xworm TCP Packet |