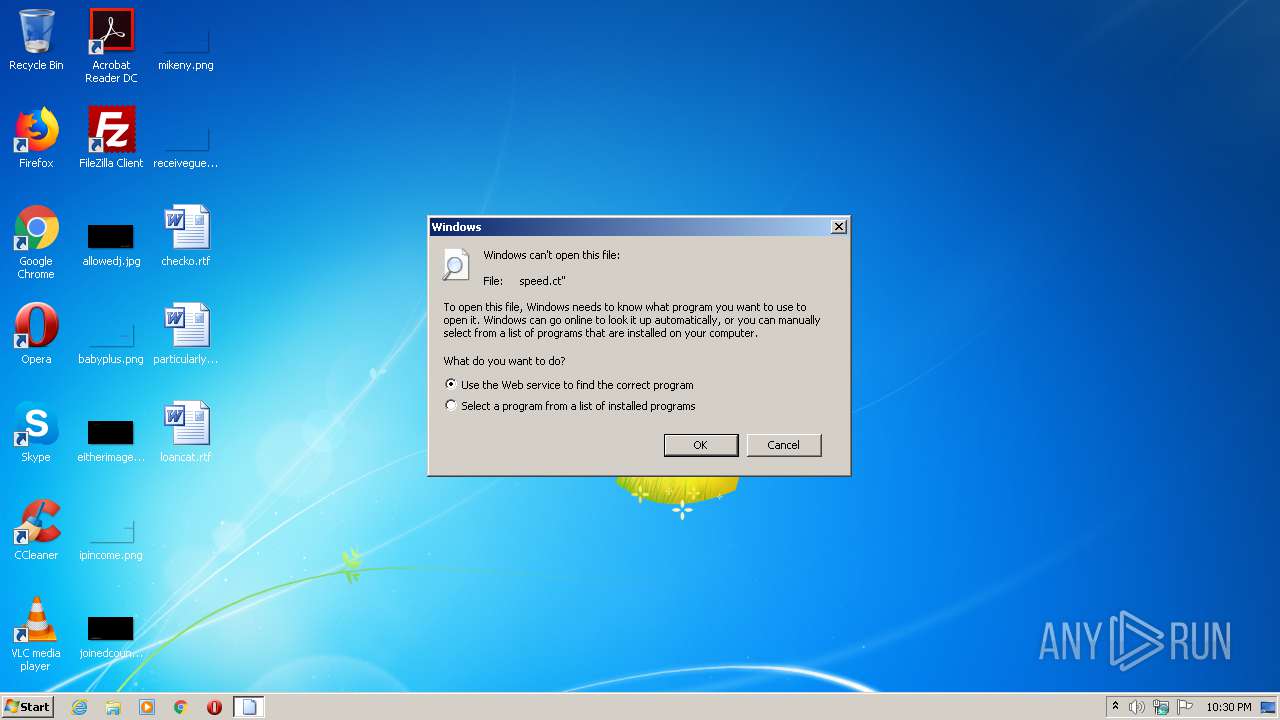
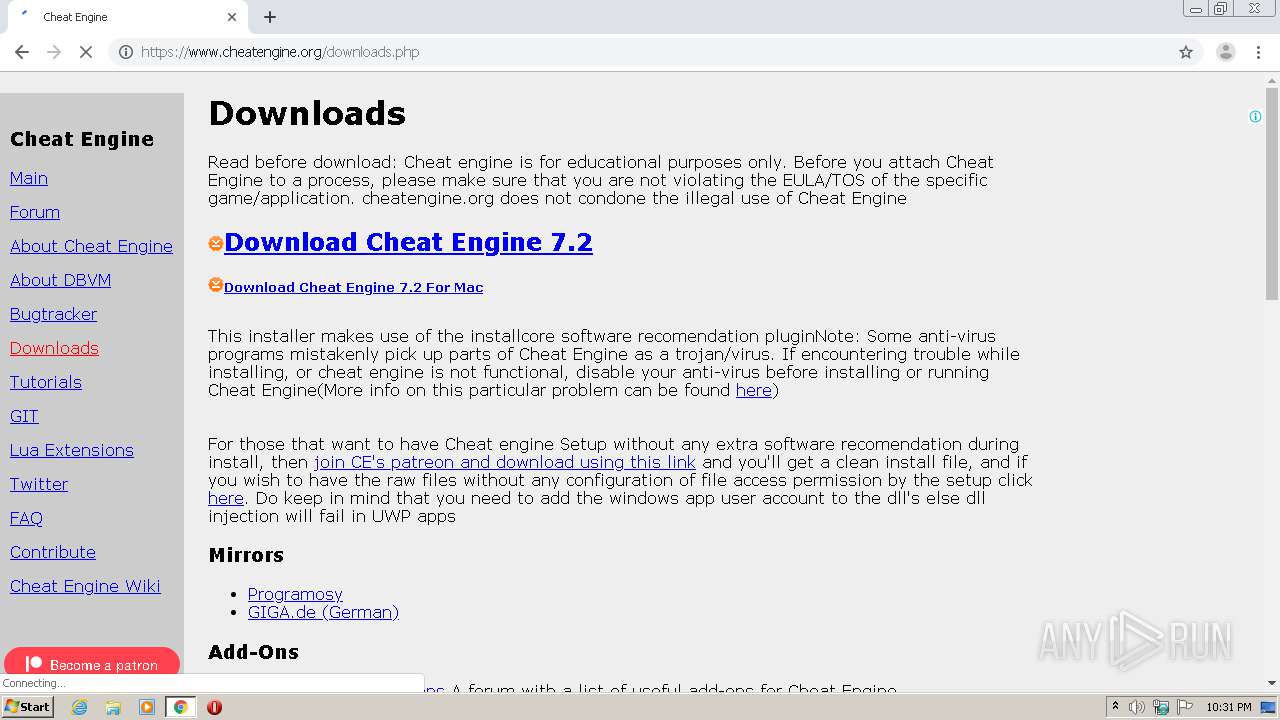
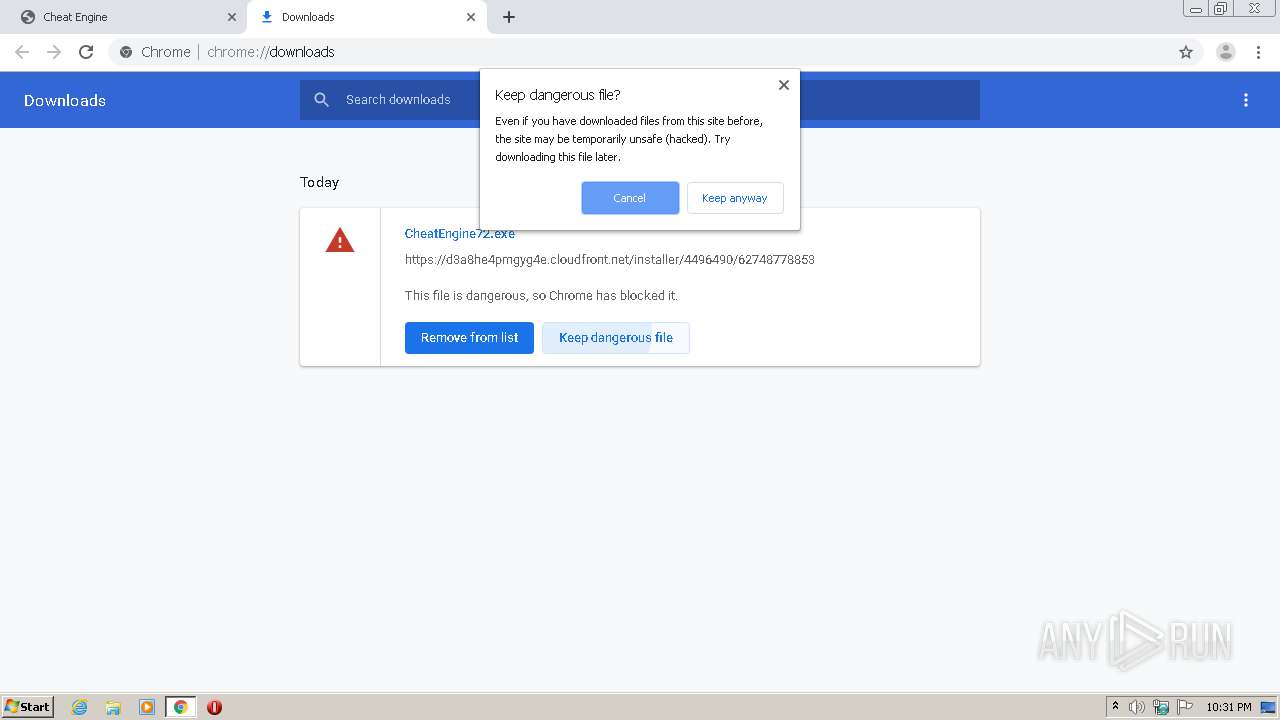
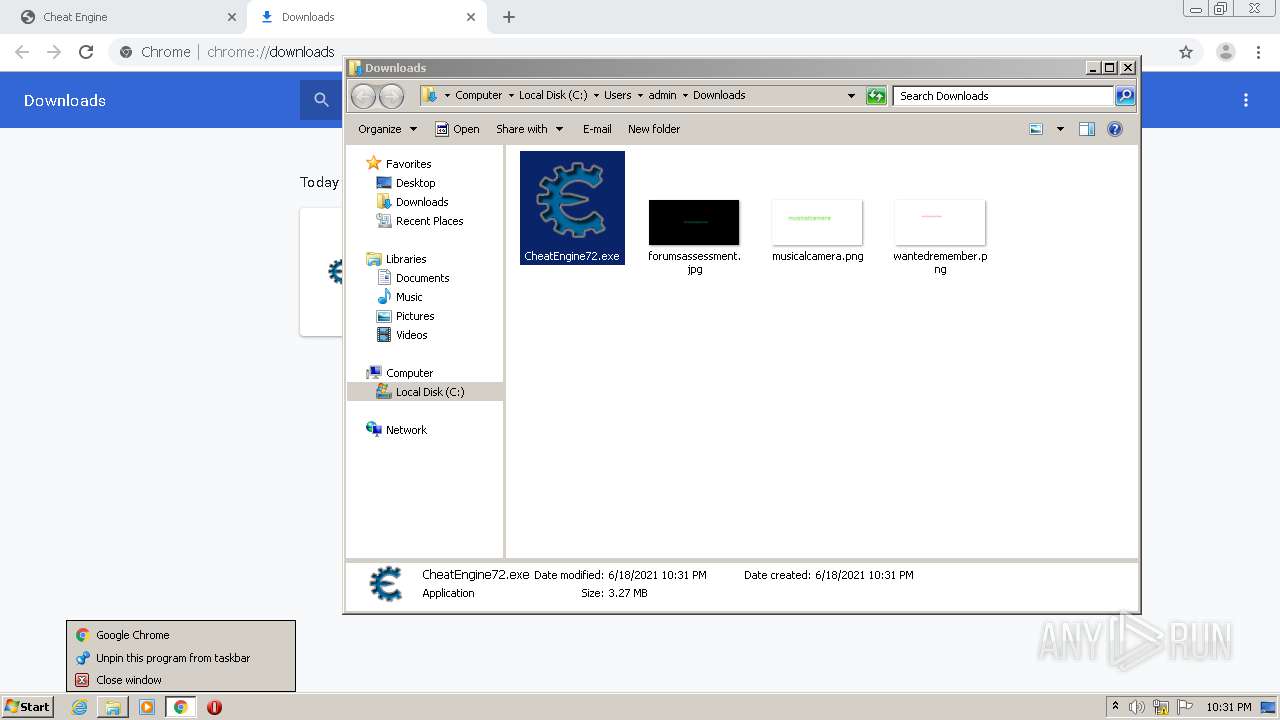
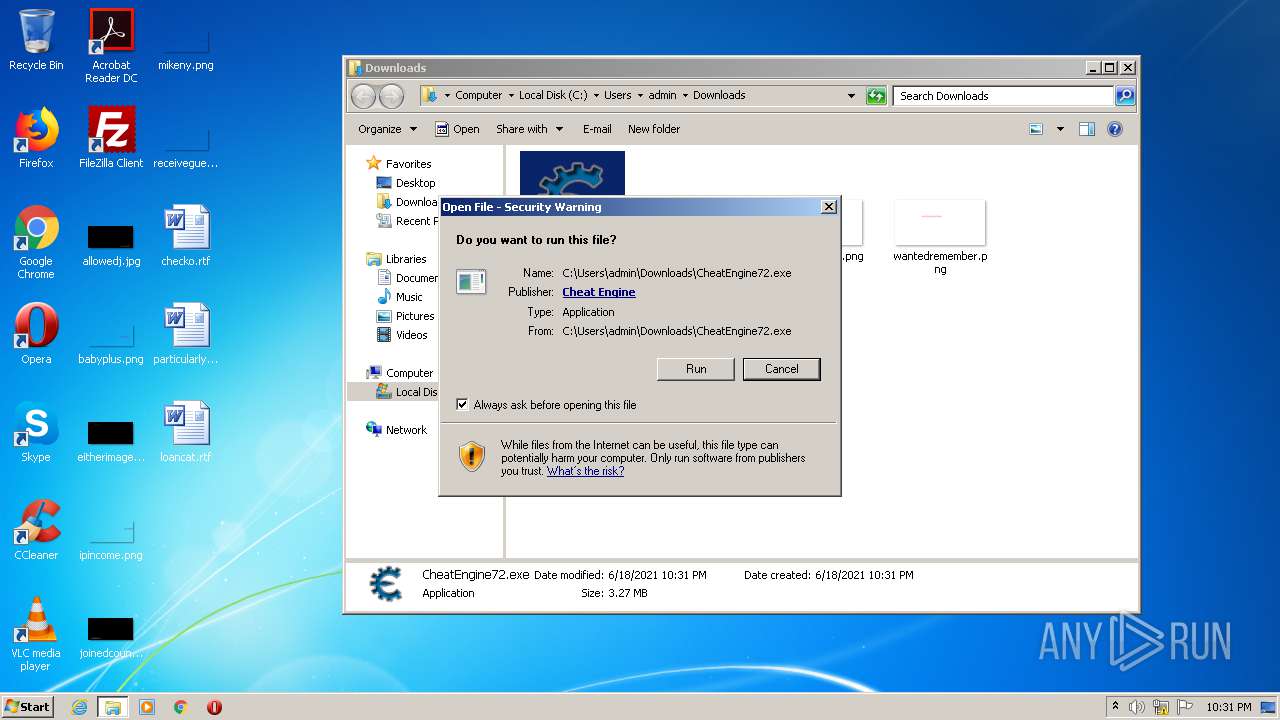
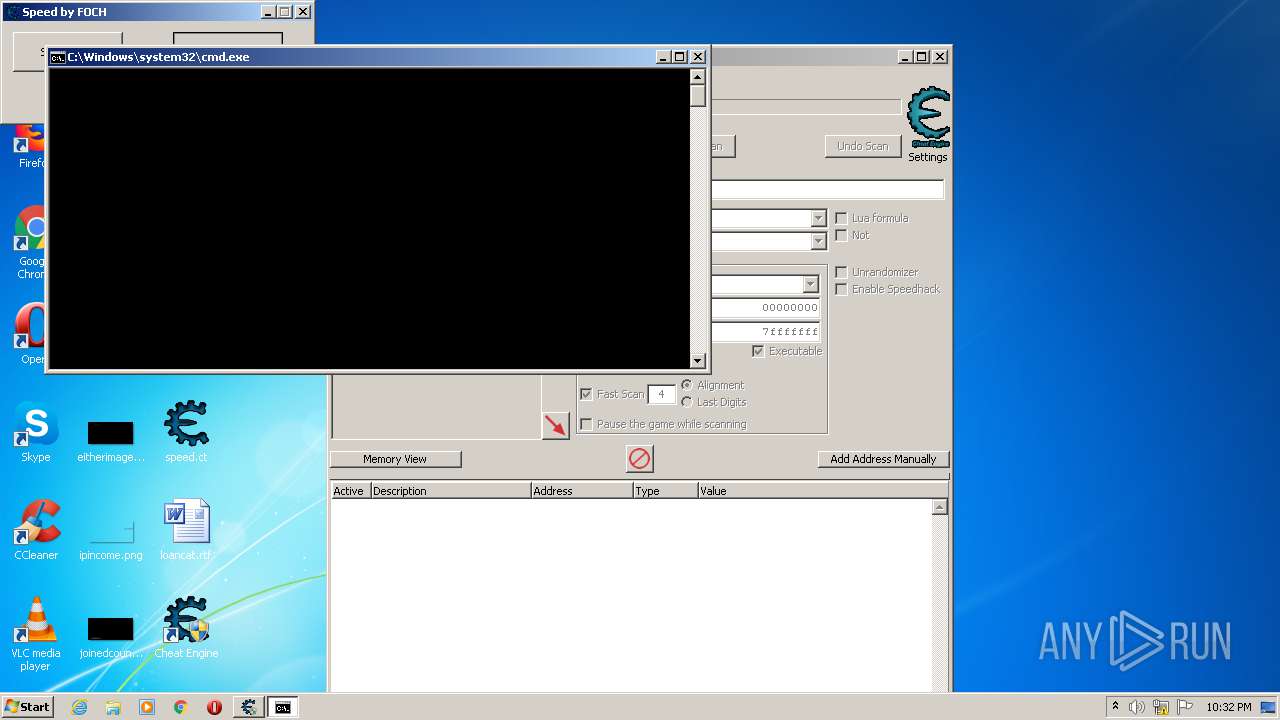
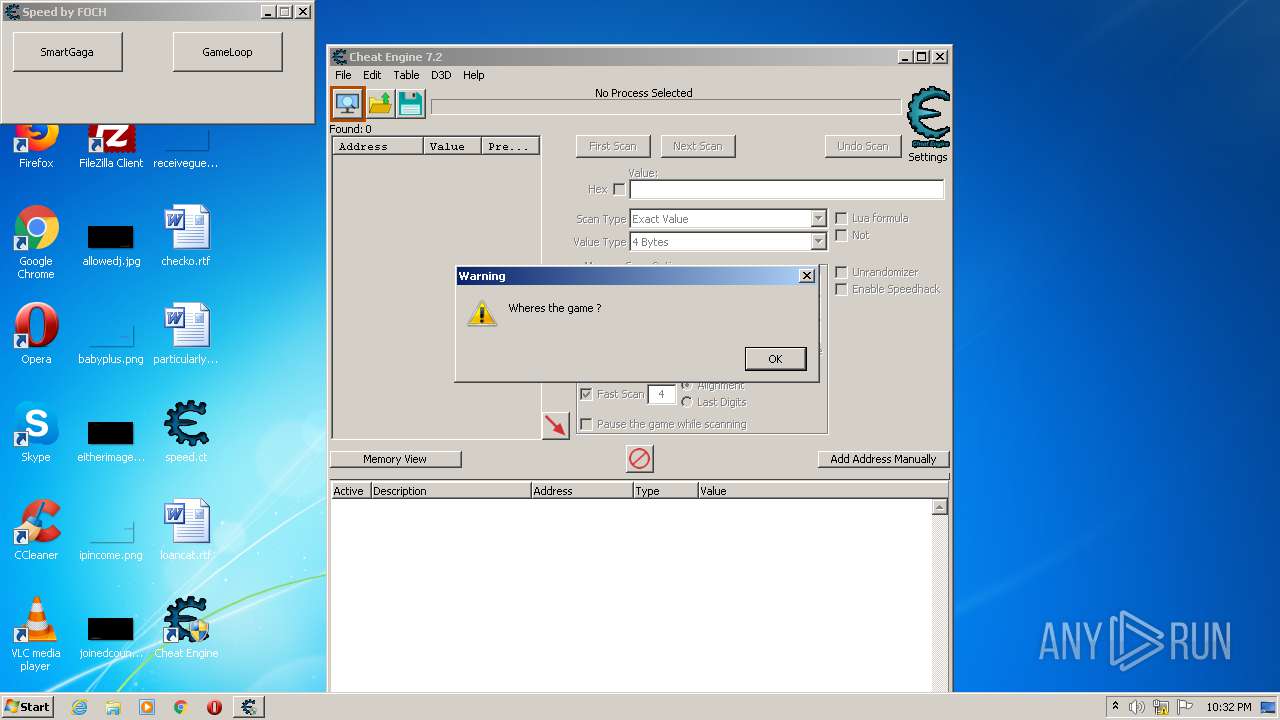
| File name: | speed.ct |
| Full analysis: | https://app.any.run/tasks/5bf945ff-b40f-4269-b80c-2f79f076aafd |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2021, 21:30:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/xml |
| File info: | XML 1.0 document, UTF-8 Unicode text, with CRLF line terminators |
| MD5: | D6E0D1FD228B4054D2C657BD7BC22FE3 |
| SHA1: | D75FB1152020C11B1CAFB545C9DEB4B419386EF0 |
| SHA256: | B04EDDA7E977D6629B3197E195B6149AE680227530C97423C5909647B21C0979 |
| SSDEEP: | 48:cS5Gya1ee4XYZIYSlFeVjgi0xHoK/3yDK31iV/3+GkWTgUIOV6eSFHF5sJ+QqzYv:RGnviVVJDGK3WHgYkFyJ+N8RQu |
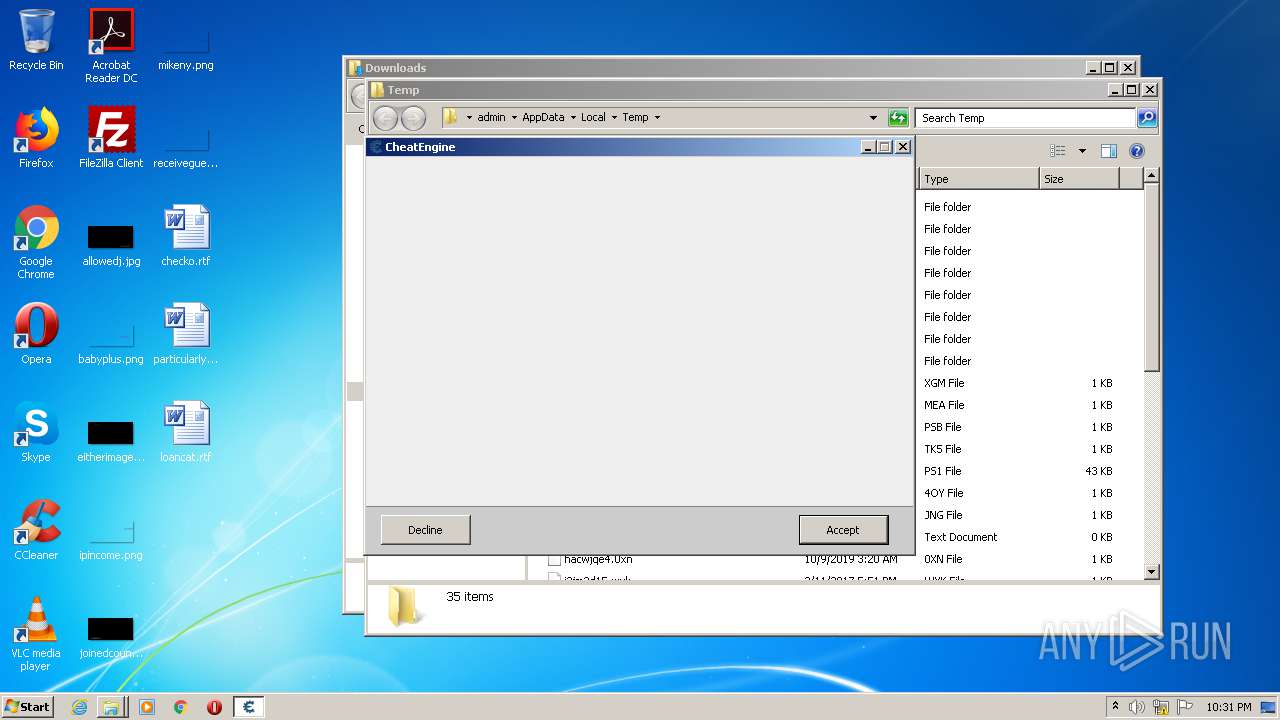
MALICIOUS
Application was dropped or rewritten from another process
- CheatEngine72.exe (PID: 1252)
- CheatEngine72.exe (PID: 2084)
- cheatengine-i386.exe (PID: 1476)
- windowsrepair.exe (PID: 3200)
- Kernelmoduleunloader.exe (PID: 2660)
- Cheat Engine.exe (PID: 2776)
- Cheat Engine.exe (PID: 2696)
Drops executable file immediately after starts
- CheatEngine72.exe (PID: 1252)
- CheatEngine72.exe (PID: 2084)
- CheatEngine72.exe (PID: 3616)
- CheatEngine72.tmp (PID: 2112)
Changes settings of System certificates
- CheatEngine72.tmp (PID: 3760)
- cheatengine-i386.exe (PID: 1476)
Starts NET.EXE for service management
- CheatEngine72.tmp (PID: 2112)
Loads dropped or rewritten executable
- cheatengine-i386.exe (PID: 1476)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 448)
- chrome.exe (PID: 2504)
- CheatEngine72.exe (PID: 1252)
- CheatEngine72.exe (PID: 2084)
- CheatEngine72.tmp (PID: 3760)
- CheatEngine72.exe (PID: 3616)
- CheatEngine72.tmp (PID: 2112)
Modifies files in Chrome extension folder
- chrome.exe (PID: 448)
Reads Windows owner or organization settings
- CheatEngine72.tmp (PID: 3760)
- CheatEngine72.tmp (PID: 2112)
Reads the Windows organization settings
- CheatEngine72.tmp (PID: 3760)
- CheatEngine72.tmp (PID: 2112)
Drops a file with too old compile date
- CheatEngine72.tmp (PID: 3760)
- CheatEngine72.tmp (PID: 2112)
Drops a file that was compiled in debug mode
- CheatEngine72.tmp (PID: 3760)
- CheatEngine72.tmp (PID: 2112)
Creates a directory in Program Files
- CheatEngine72.tmp (PID: 2112)
Uses ICACLS.EXE to modify access control list
- CheatEngine72.tmp (PID: 2112)
Starts SC.EXE for service management
- CheatEngine72.tmp (PID: 2112)
Adds / modifies Windows certificates
- CheatEngine72.tmp (PID: 3760)
- cheatengine-i386.exe (PID: 1476)
Changes default file association
- CheatEngine72.tmp (PID: 2112)
Creates files in the program directory
- cheatengine-i386.exe (PID: 1476)
Creates or modifies windows services
- cheatengine-i386.exe (PID: 1476)
Starts CMD.EXE for commands execution
- cheatengine-i386.exe (PID: 1476)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 1556)
INFO
Manual execution by user
- chrome.exe (PID: 448)
- CheatEngine72.exe (PID: 1252)
- verclsid.exe (PID: 2520)
- Cheat Engine.exe (PID: 2776)
- Cheat Engine.exe (PID: 2696)
Changes default file association
- chrome.exe (PID: 448)
Reads the hosts file
- chrome.exe (PID: 2504)
- chrome.exe (PID: 448)
Application launched itself
- chrome.exe (PID: 448)
Reads settings of System Certificates
- chrome.exe (PID: 448)
- cheatengine-i386.exe (PID: 1476)
Application was dropped or rewritten from another process
- CheatEngine72.tmp (PID: 3660)
- CheatEngine72.tmp (PID: 3760)
- CheatEngine72.tmp (PID: 2112)
- CheatEngine72.exe (PID: 3616)
Loads dropped or rewritten executable
- CheatEngine72.tmp (PID: 2112)
- CheatEngine72.tmp (PID: 3760)
Creates a software uninstall entry
- CheatEngine72.tmp (PID: 2112)
Creates files in the program directory
- CheatEngine72.tmp (PID: 2112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ct | | | Cheat Engine Cheat Table (XML) (91.8) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (8.1) |
EXIF
XMP
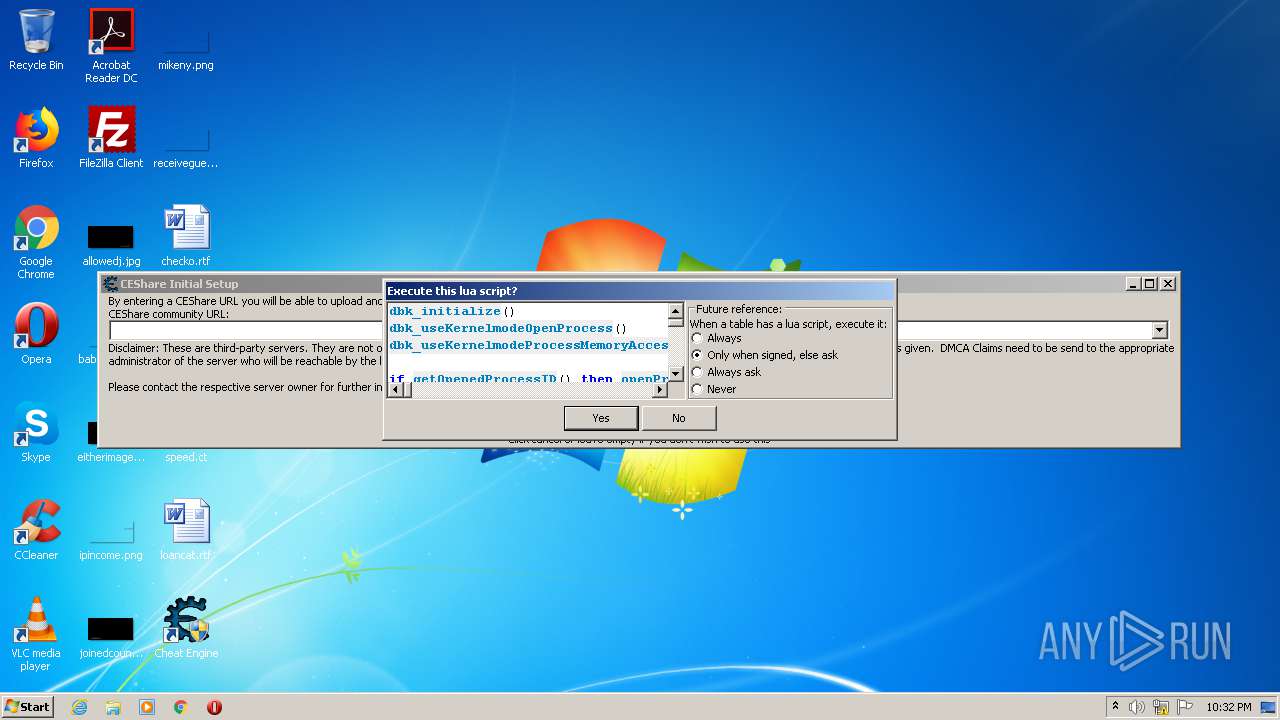
| CheatTableLuaScript: | dbk_initialize() dbk_useKernelmodeOpenProcess() dbk_useKernelmodeProcessMemoryAccess() if getOpenedProcessID() then openProcess(getOpenedProcessID()) end dbk_writesIgnoreWriteProtection(true) function AOBRep(search, change) local aob = AOBScan(search) if aob then for i=0,aob.Count-1 do autoAssemble(aob[i]..':\ndb '..change) end aob.Destroy() end end EmuForm = createForm(true) EmuForm.Caption = 'Speed by FOCH' EmuForm.Width = 310 EmuForm.Height = 100 function smartgaga() emu= "AndroidProcess" startmenu() EmuForm.hide() end EmuButton1 = createButton(EmuForm) EmuButton1.Left = 10 EmuButton1.Top = 10 EmuButton1.Width = 110 EmuButton1.Height = 40 EmuButton1.onClick = smartgaga EmuButton1.Caption = 'SmartGaga' function gameloop() emu= "aow_exe" startmenu() EmuForm.hide() end EmuButton2 = createButton(EmuForm) EmuButton2.Left = 170 EmuButton2.Top = 10 EmuButton2.Width = 110 EmuButton2.Height = 40 EmuButton2.onClick = gameloop EmuButton2.Caption = 'GameLoop' function startmenu() local p = io.popen('tasklist /fi "IMAGENAME eq '..emu..'.exe" /fi "MEMUSAGE gt 220000" /nh', 'r'); local procInfo = p:read('*a'); p:close(); local pid = procInfo:match('%d+'); pid = tonumber(pid); if(pid == nil)then messageDialog("Wheres the game ?", mtWarning, mbOK) closeCE() else openProcess(pid) ----------------HACK MENU START---------------- function cbfo() searchV = 'BD 37 86 35 71 0A 90 ED' --off replaceV = 'CD CC CC 3D 71 0A 90 ED' --lol AOBRep(searchV,replaceV) end MyForm = createForm(true) MyForm.Caption = 'Murp Hack v1.0' MyForm.Width = 180 MyForm.Height = 140 chl = createLabel(MyForm) chl.Caption= 'Bypass Menu**' chl.Left = 10 chl.Top = 410 cbbo = createButton(MyForm) cbbo.Left = 10 cbbo.Top = 40 cbbo.Width = 150 cbbo.Height = 40 cbbo.onClick = cbfo cbbo.Caption = 'Fast Runn' info2l = createLabel(MyForm) info2l.Caption= '** -> Lobide aktifleştirilmeli. - good.' info2l.Left = 10 info2l.Top = 535 info3l = createLabel(MyForm) info3l.Caption= 'JK GAMING WORLD' info3l.Left = 60 info3l.Top = 560 info3l.Font.Color= 0xff0000 info3l.Font.Size= 12 ----------------HACK MENU FINISH---------------- end end |
|---|---|
| CheatTableUserdefinedSymbols: | - |
| CheatTableCheatEntries: | - |
| CheatTableCheatEngineTableVersion: | 28 |
Total processes
120
Monitored processes
65
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,2157203826841519264,6327078059636017544,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17431423393108802784 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4488 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 308 | "net" stop BadlionAntic | C:\Windows\system32\net.exe | — | CheatEngine72.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,2157203826841519264,6327078059636017544,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12277889633246387095 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2520 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 752 | C:\Windows\system32\net1 stop BadlionAnticheat | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 816 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,2157203826841519264,6327078059636017544,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12561128760379077131 --mojo-platform-channel-handle=3508 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 952 | tasklist /fi "IMAGENAME eq aow_exe.exe" /fi "MEMUSAGE gt 220000" /nh | C:\Windows\system32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,2157203826841519264,6327078059636017544,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5711914890426522248 --mojo-platform-channel-handle=3260 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1004 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,2157203826841519264,6327078059636017544,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16016044589119154386 --mojo-platform-channel-handle=3616 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1252 | "C:\Users\admin\Downloads\CheatEngine72.exe" | C:\Users\admin\Downloads\CheatEngine72.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: cheatengine Installer Exit code: 0 Version: 7.2.0 Modules
| |||||||||||||||
Total events
1 561
Read events
1 328
Write events
209
Delete events
24
Modification events
| (PID) Process: | (448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2256) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 448-13268525440685875 |
Value: 259 | |||
| (PID) Process: | (448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (448) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
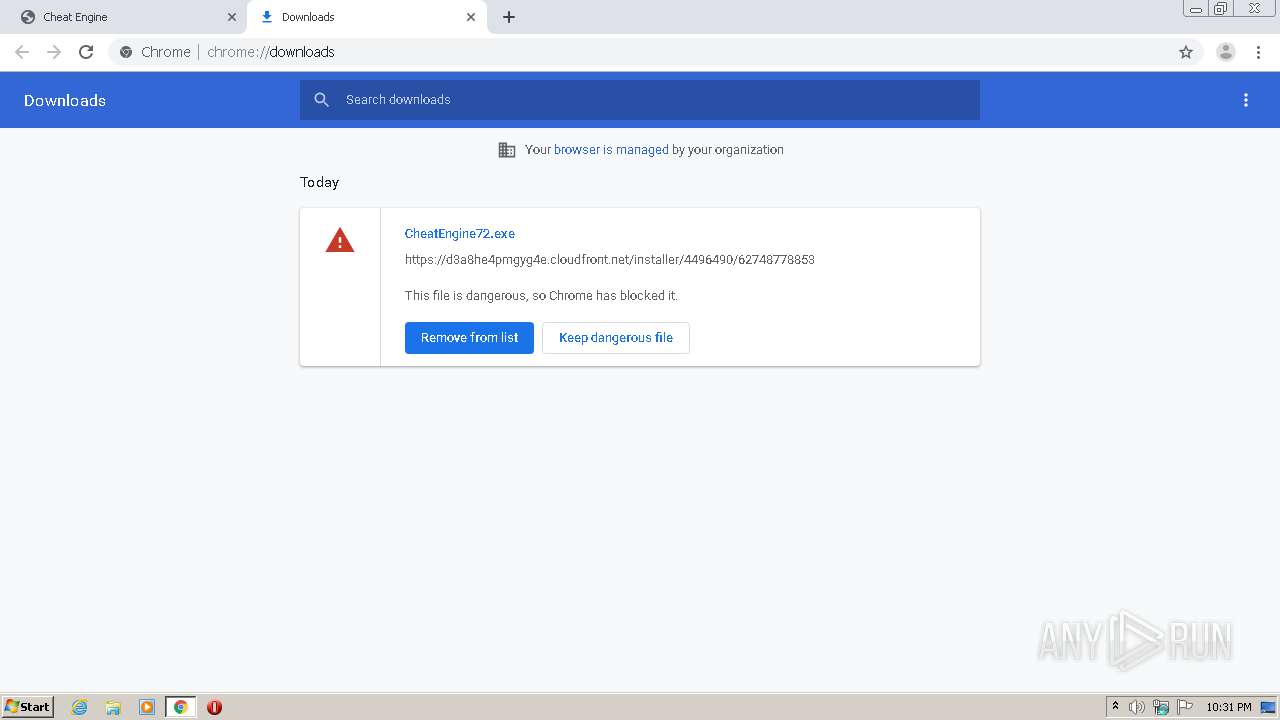
Executable files
69
Suspicious files
87
Text files
490
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60CD1081-1C0.pma | — | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\a89c05fd-04b1-4a2f-a0ce-24f0e2e268a5.tmp | — | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF164b94.TMP | text | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF164ba4.TMP | text | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF164e82.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
59
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2112 | CheatEngine72.tmp | GET | 200 | 65.9.84.128:80 | http://d6xkp4ffnq16f.cloudfront.net/ | US | — | — | whitelisted |
1476 | cheatengine-i386.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2504 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
2504 | chrome.exe | GET | 301 | 78.47.247.3:80 | http://www.freeware.de/assets/20/images/27/46/47/151.gif | DE | html | 178 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2504 | chrome.exe | 142.250.185.228:443 | www.google.com | Google Inc. | US | whitelisted |
2504 | chrome.exe | 172.217.16.110:443 | ogs.google.com.ua | Google Inc. | US | whitelisted |
2504 | chrome.exe | 104.20.175.30:443 | www.cheatengine.org | Cloudflare Inc | US | shared |
— | — | 104.20.175.30:443 | www.cheatengine.org | Cloudflare Inc | US | shared |
2504 | chrome.exe | 104.16.18.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
2504 | chrome.exe | 142.250.185.194:443 | pagead2.googlesyndication.com | Google Inc. | US | suspicious |
2504 | chrome.exe | 104.16.7.49:443 | c6.patreon.com | Cloudflare Inc | US | shared |
2504 | chrome.exe | 142.250.186.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2504 | chrome.exe | 172.217.18.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
2504 | chrome.exe | 142.250.180.225:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com.ua |
| whitelisted |
www.google.com |
| malicious |
fonts.gstatic.com |
| whitelisted |
www.cheatengine.org |
| unknown |