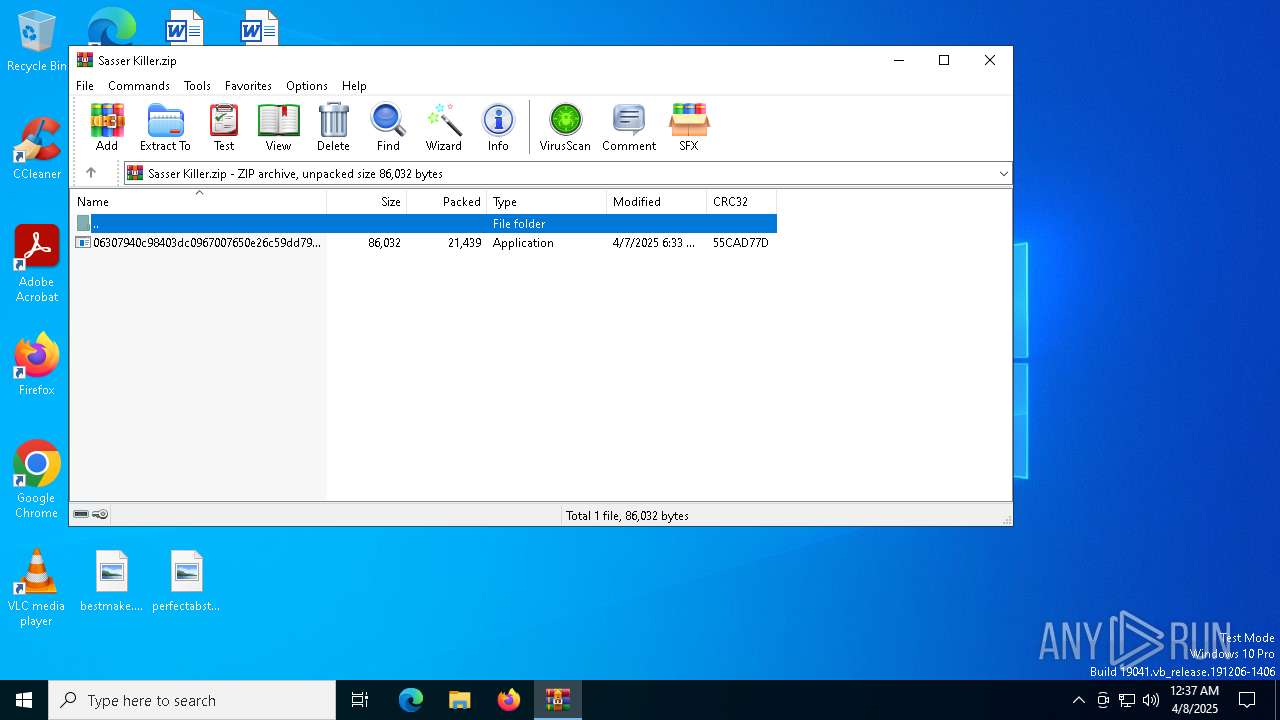
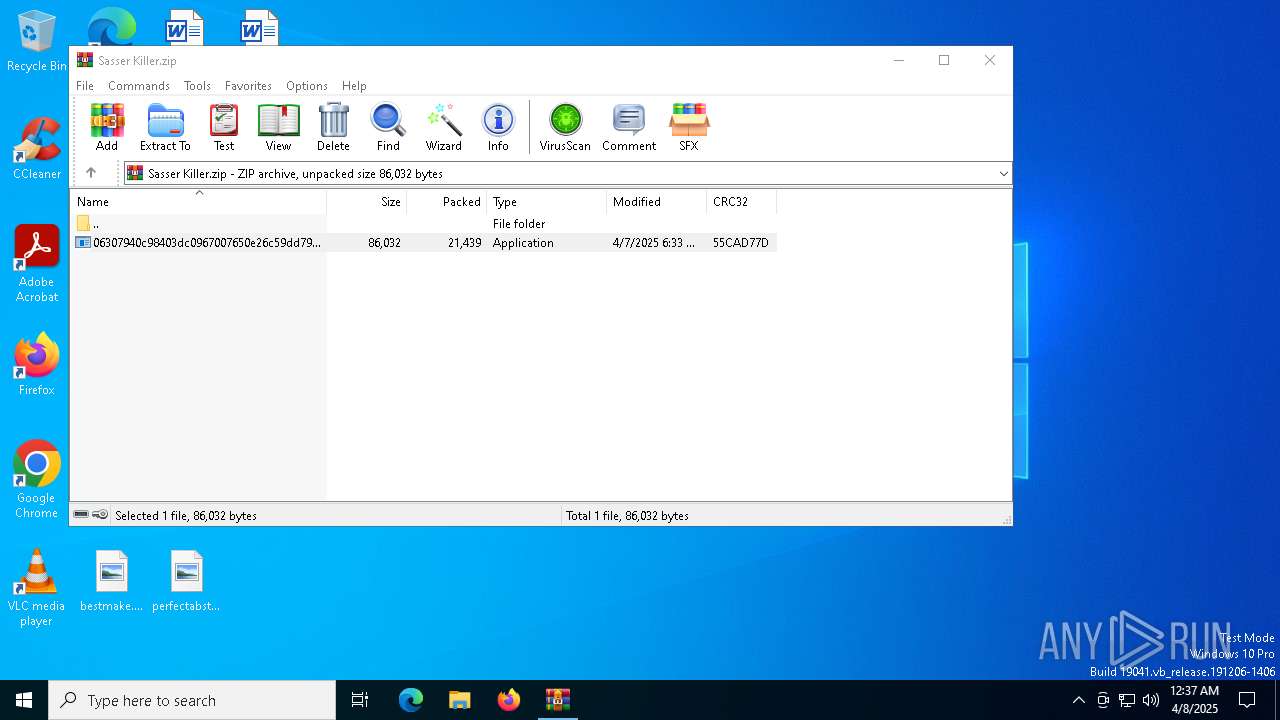
| File name: | Sasser Killer.zip |
| Full analysis: | https://app.any.run/tasks/4b4c07b1-00fe-426b-beb2-b733d1bd3a42 |
| Verdict: | Malicious activity |
| Analysis date: | April 08, 2025, 00:37:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F0CF706C986DC3639672D37A4C10034F |
| SHA1: | 0CF87E6A302BC173947C534476CDC3EA23D6AEC5 |
| SHA256: | B01DBB7A59213089B1E74EDCE09370B94EC06BA8284F58C07F828703C6CC06AA |
| SSDEEP: | 768:1llmTF07Kz4O7fNonpbJ7248+N7eSx1s33c3N:1ll80Wzb71I97F7eSxMs9 |
MALICIOUS
Changes the autorun value in the registry
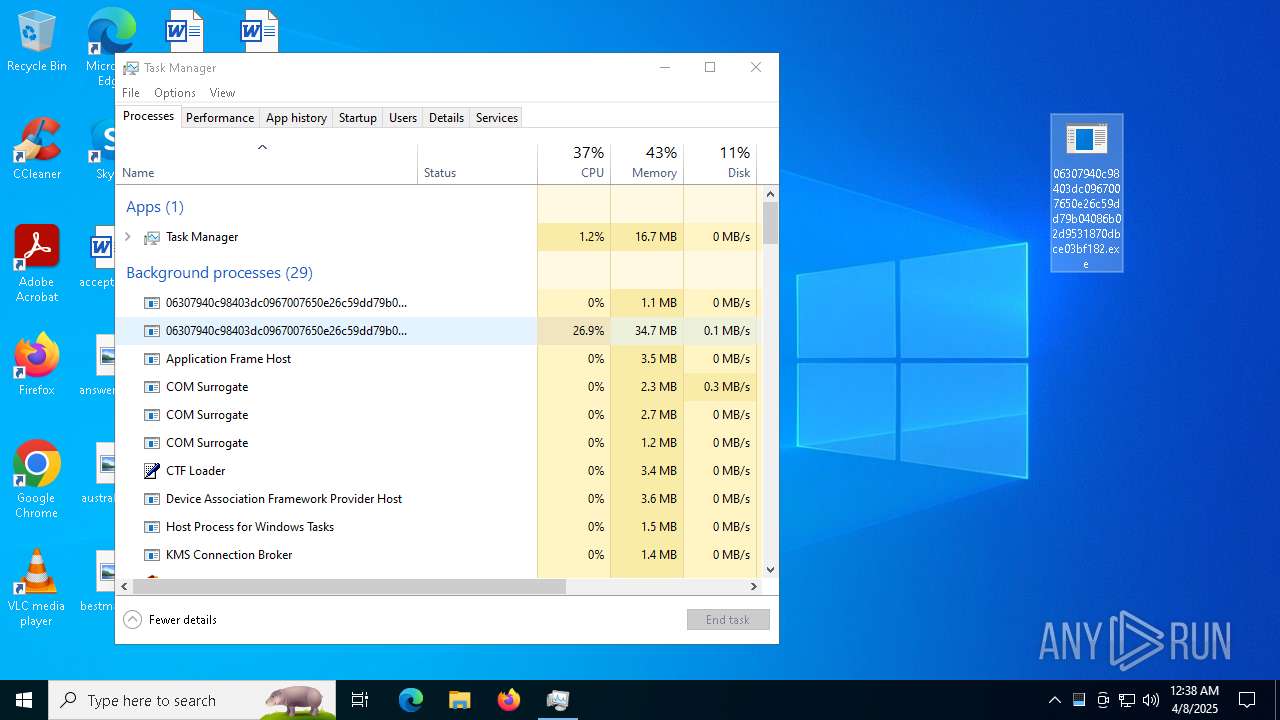
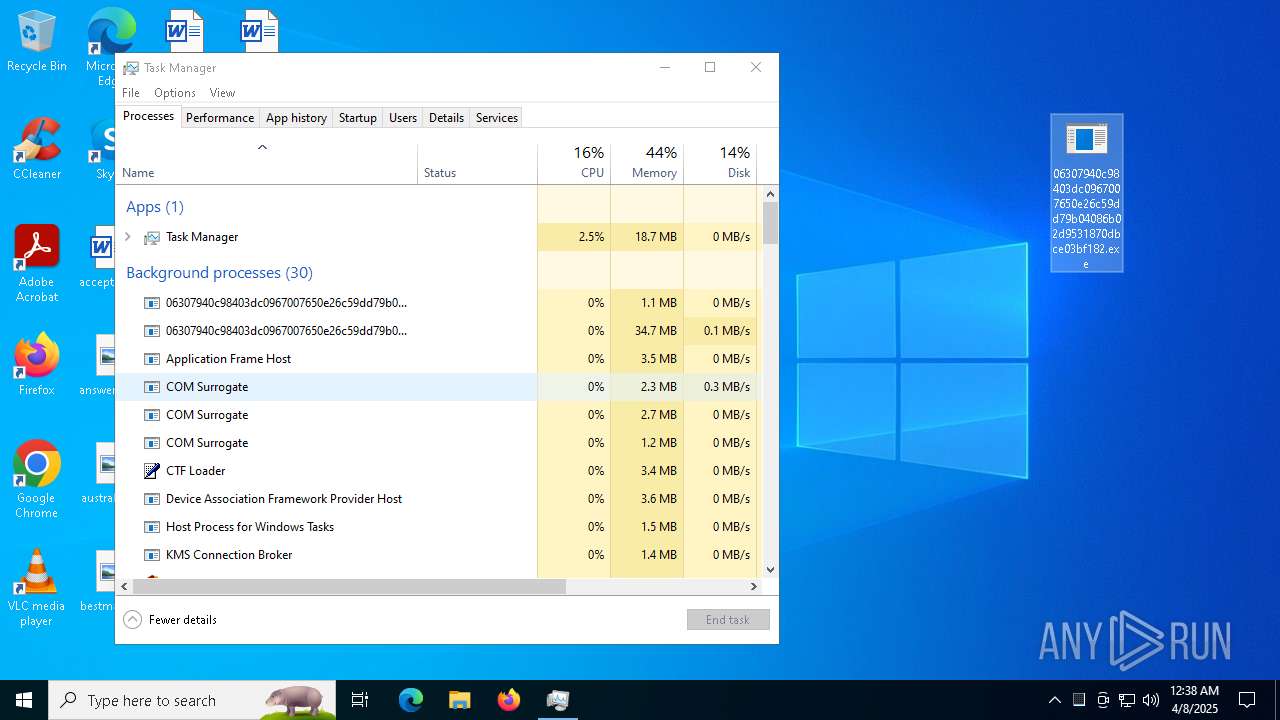
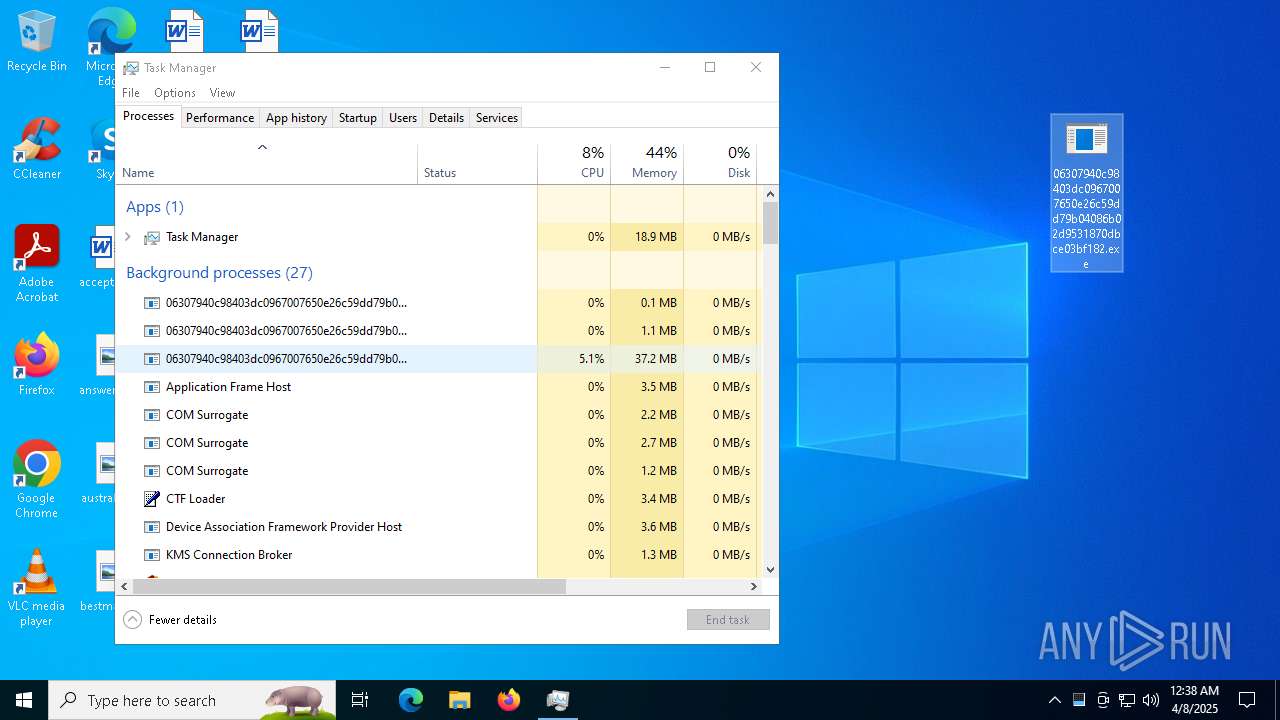
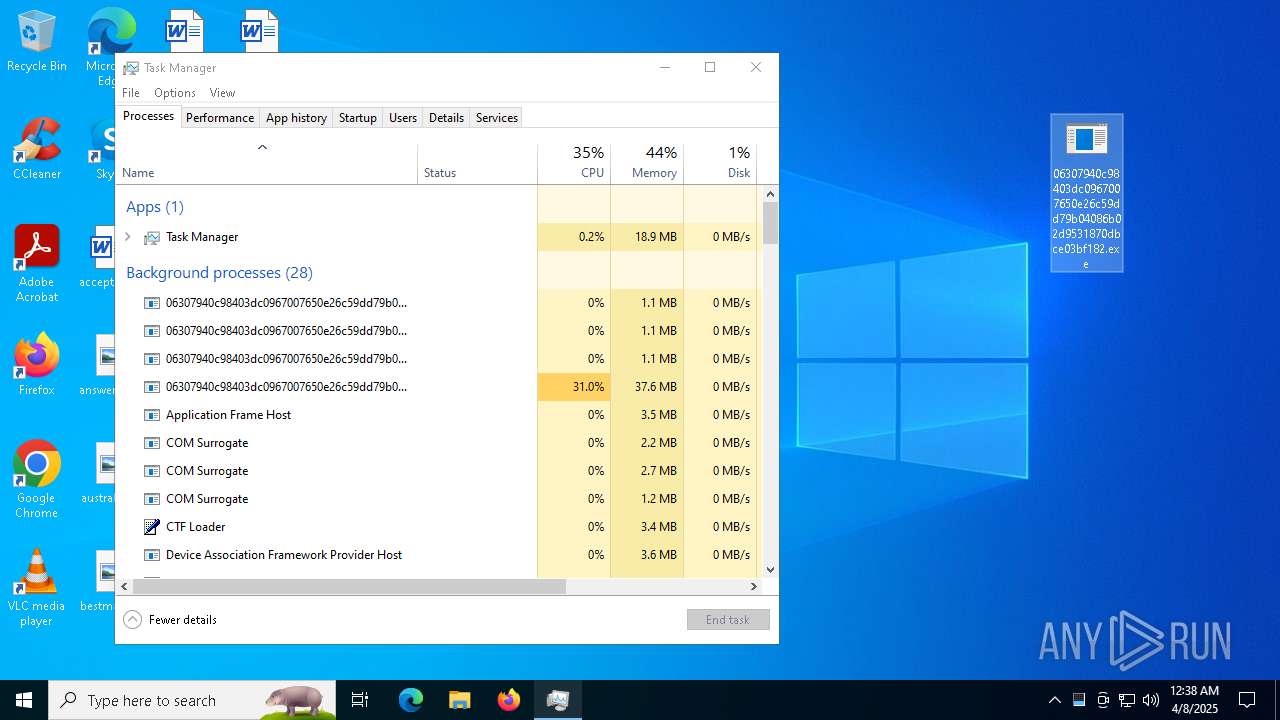
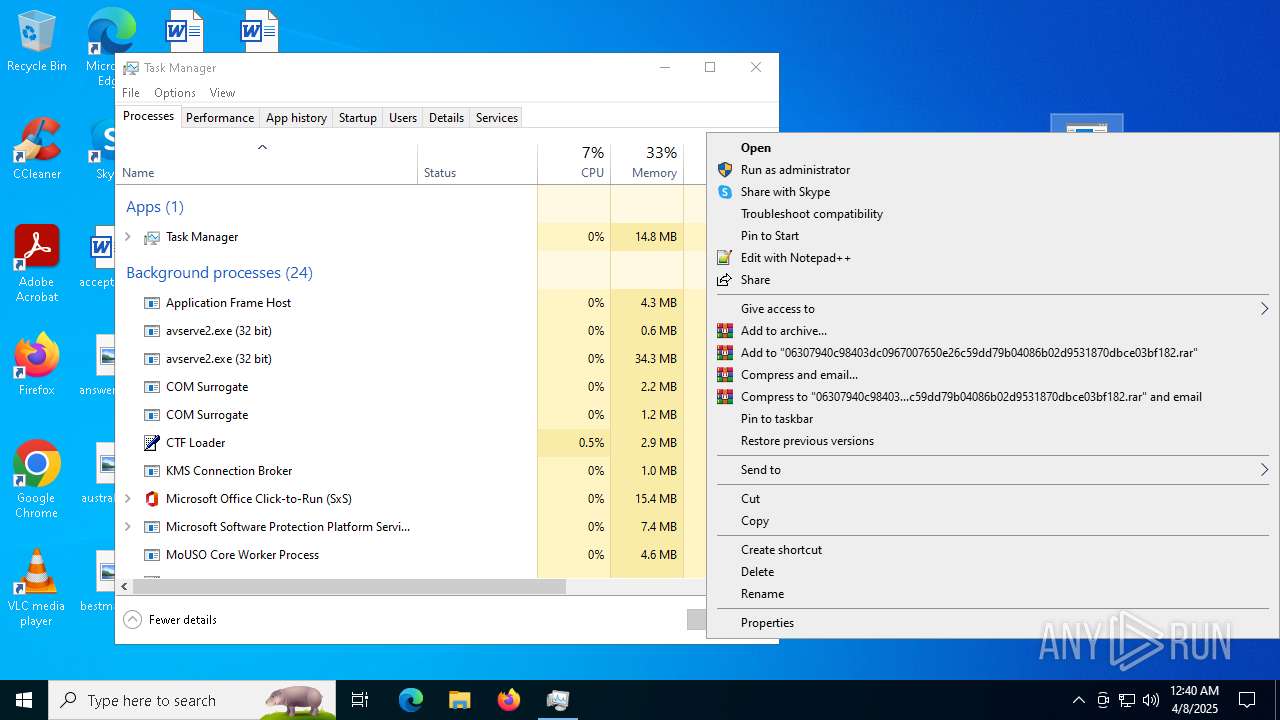
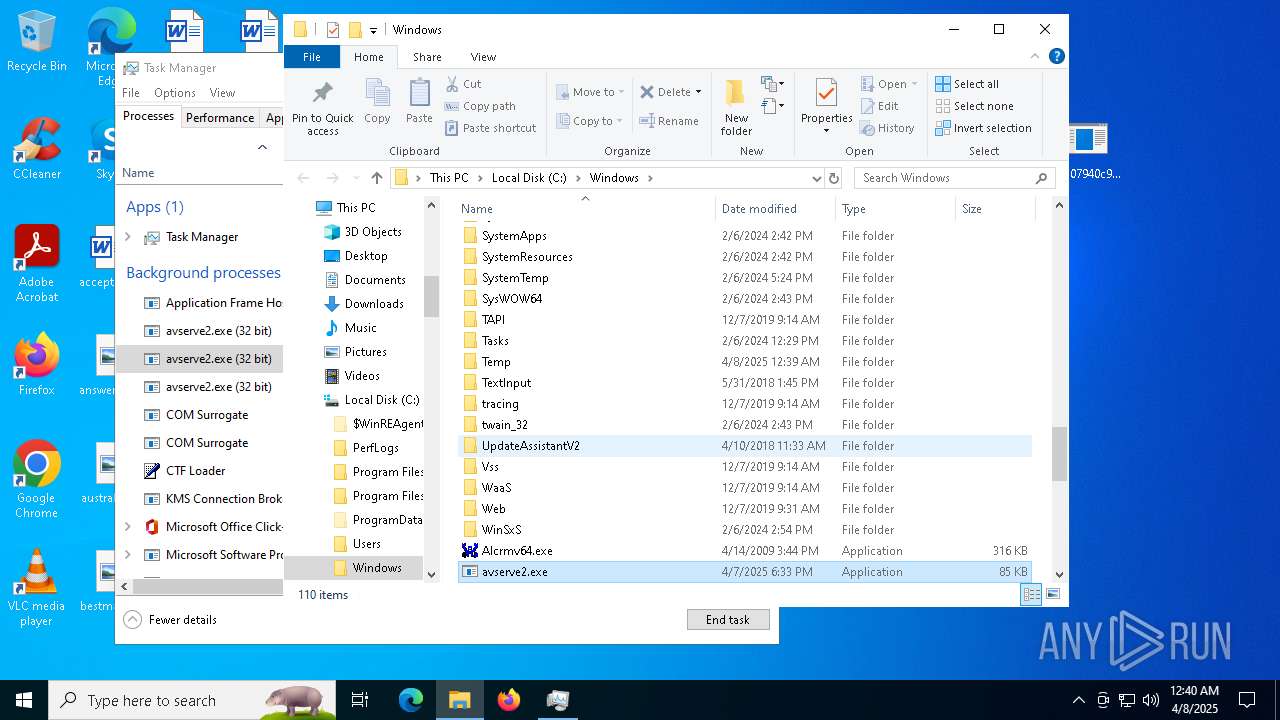
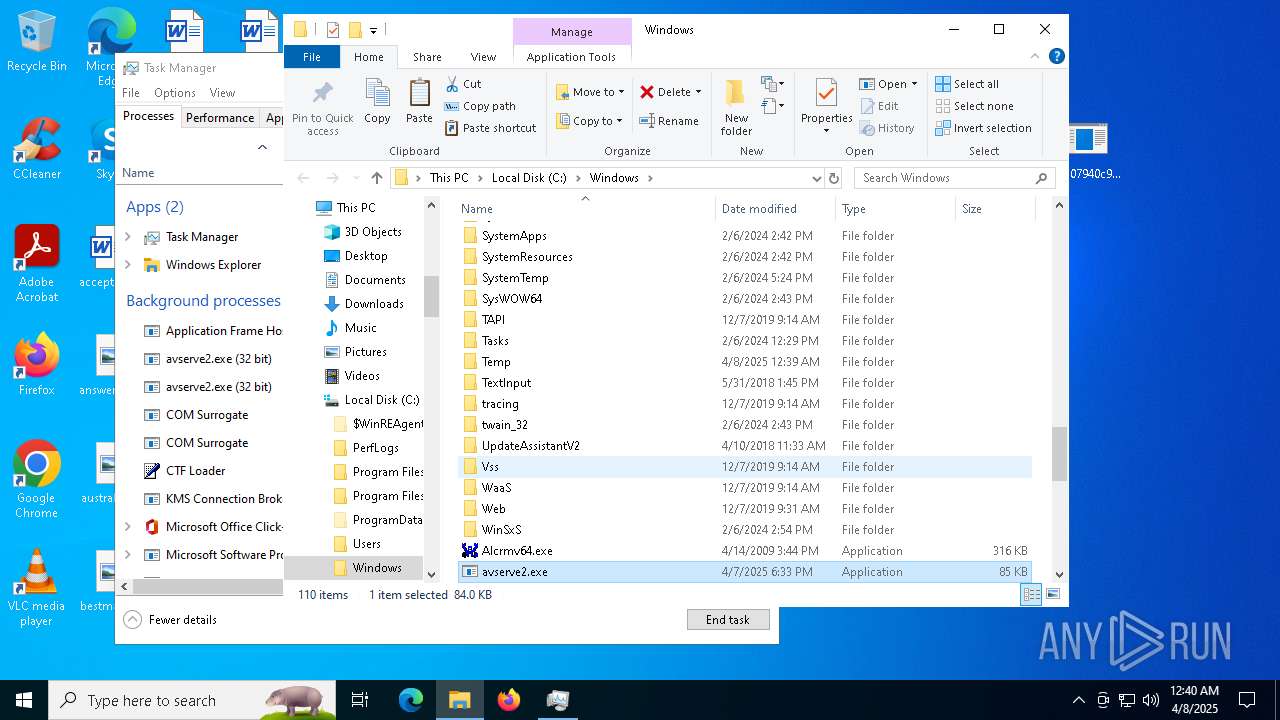
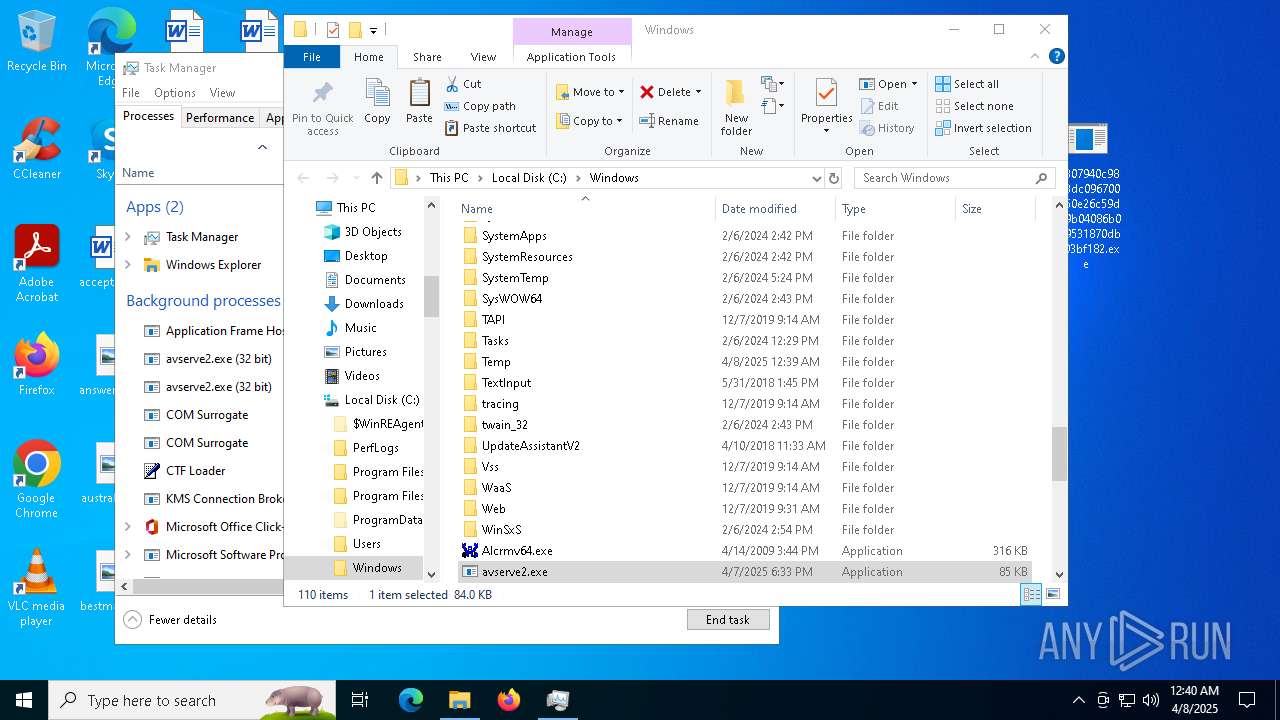
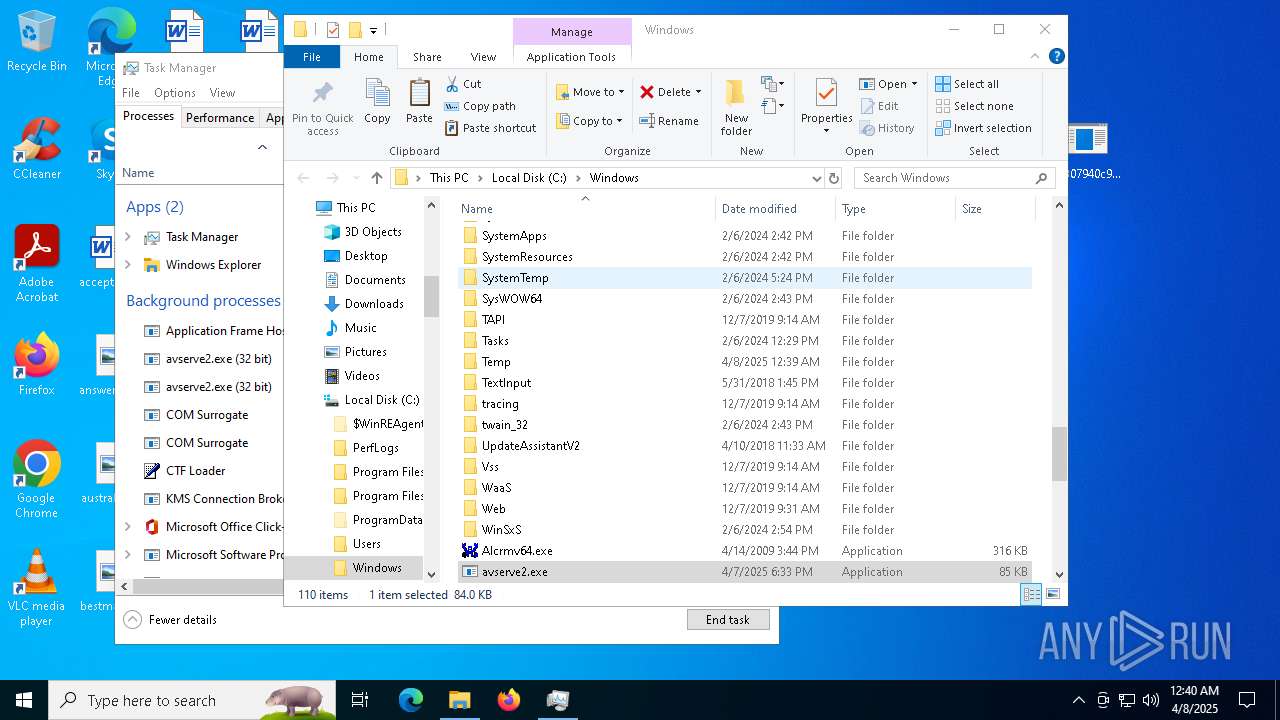
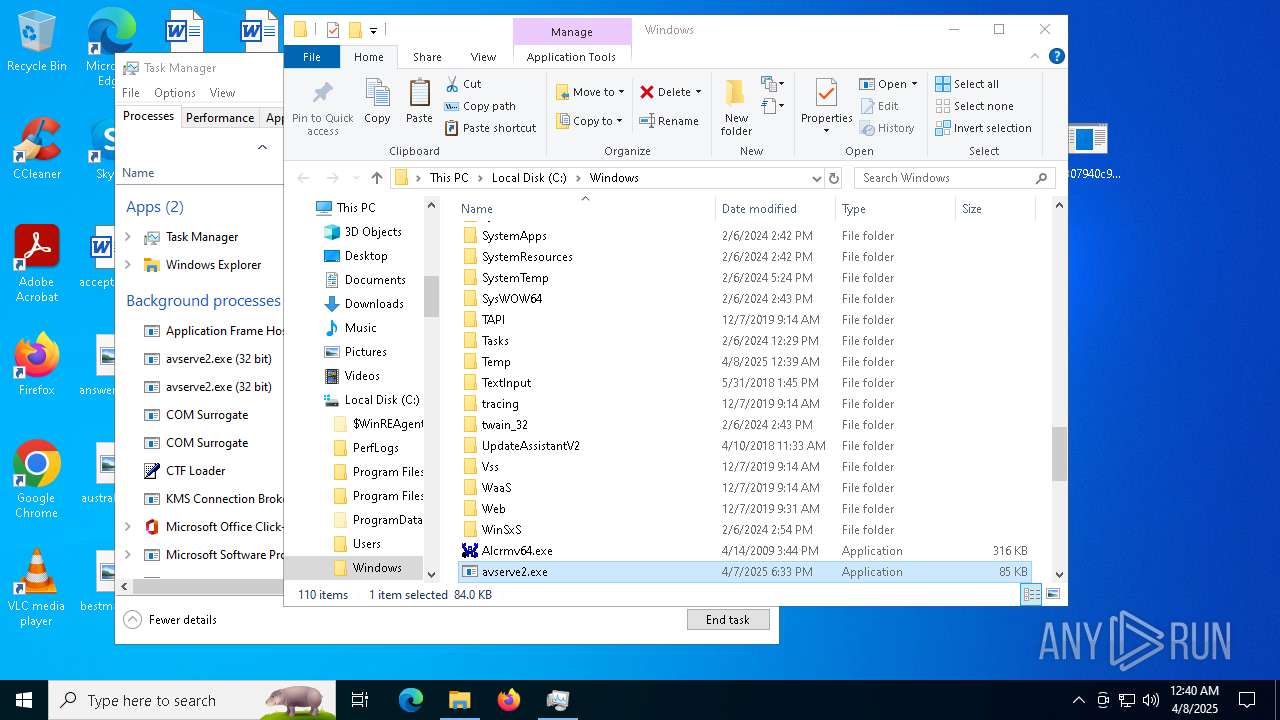
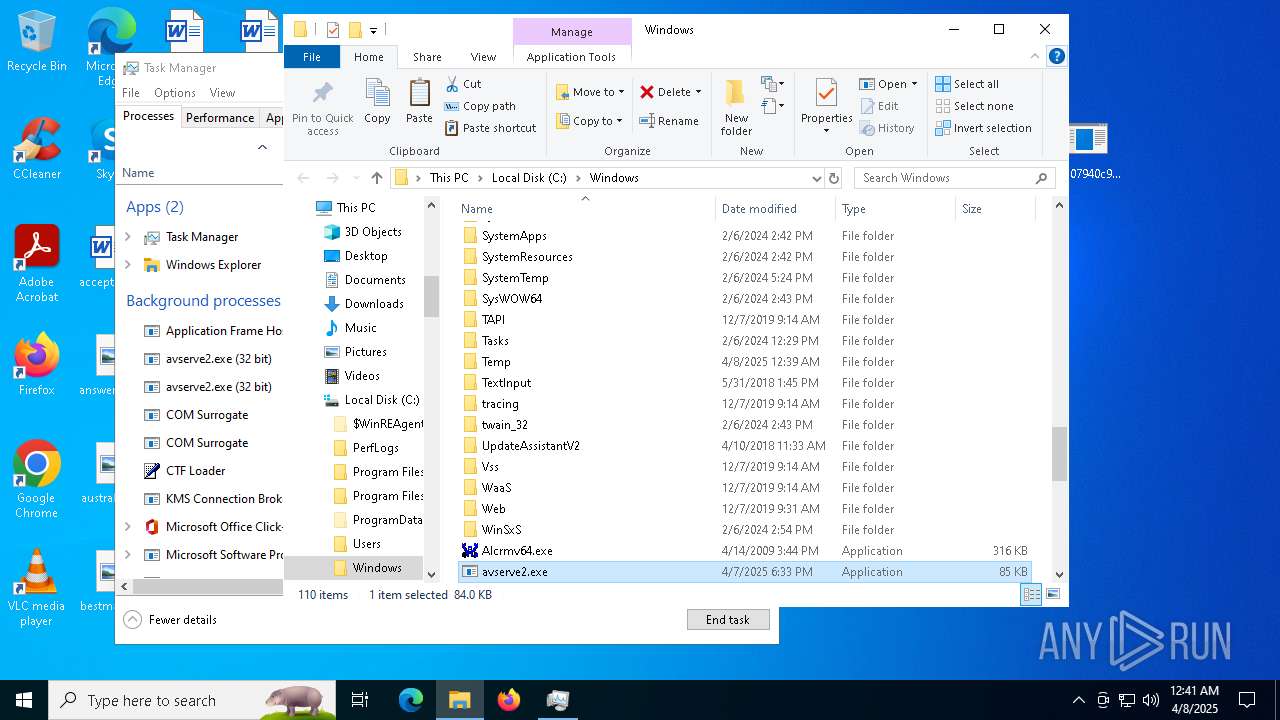
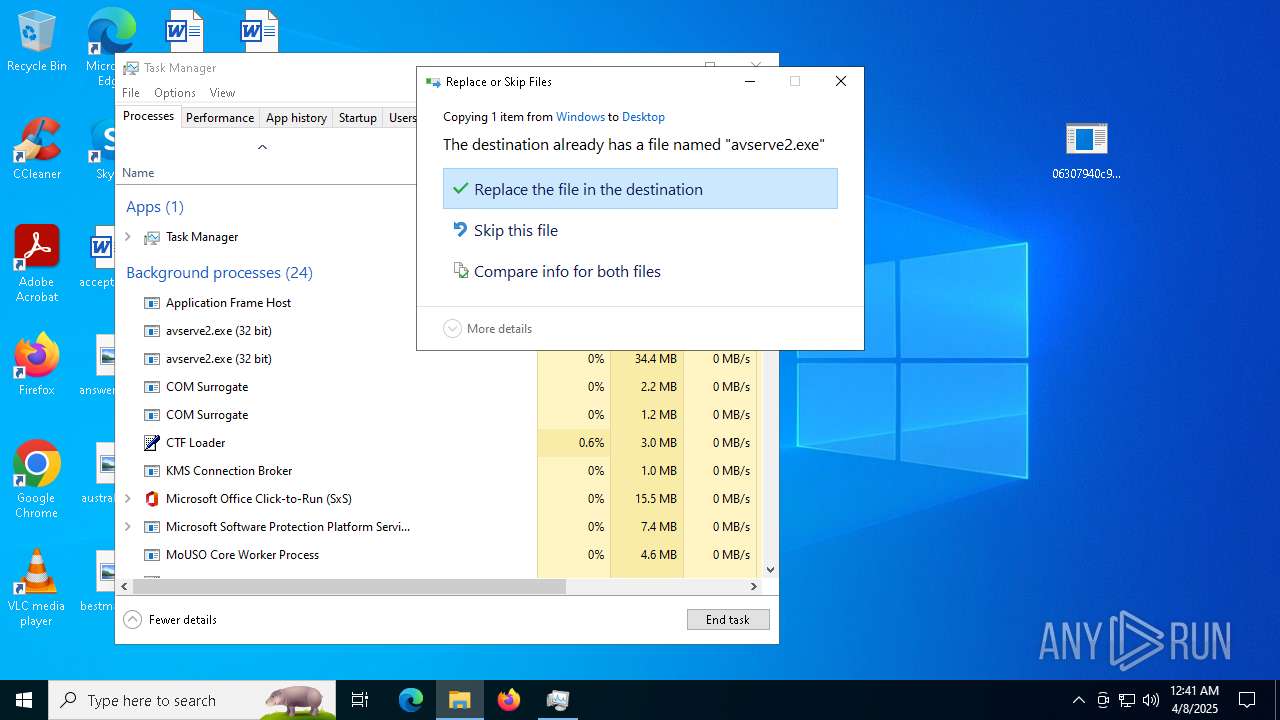
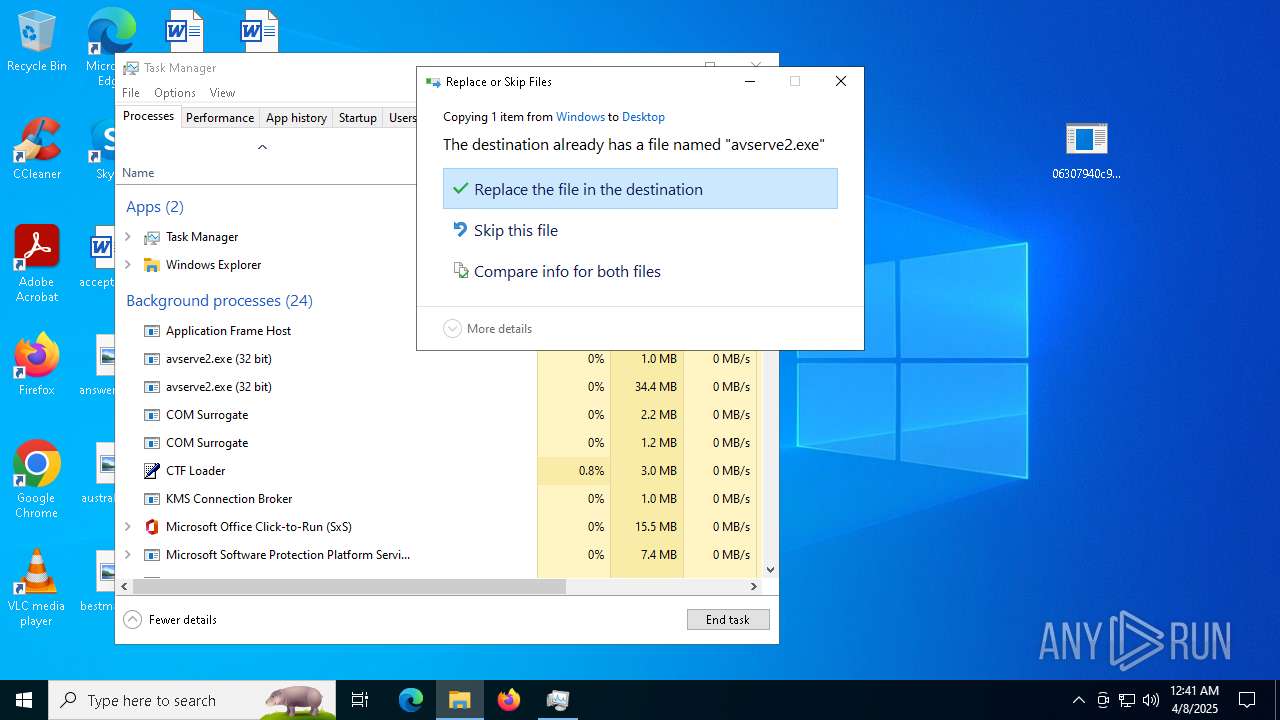
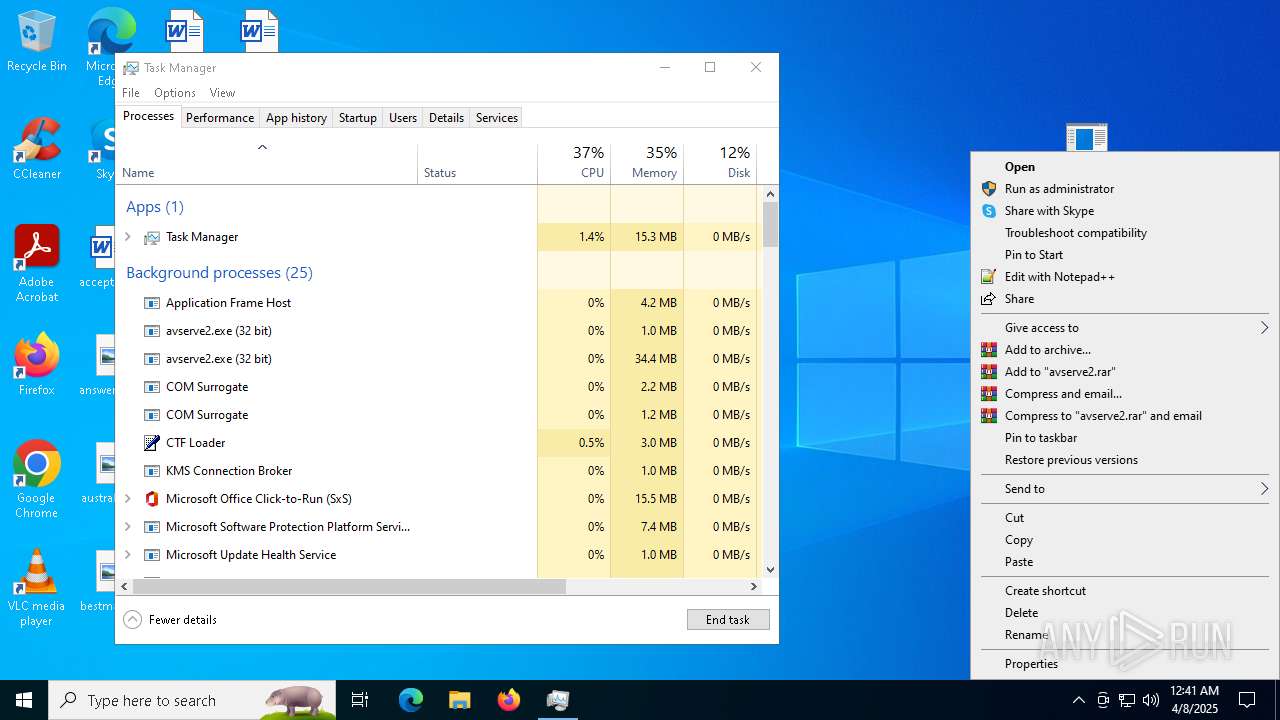
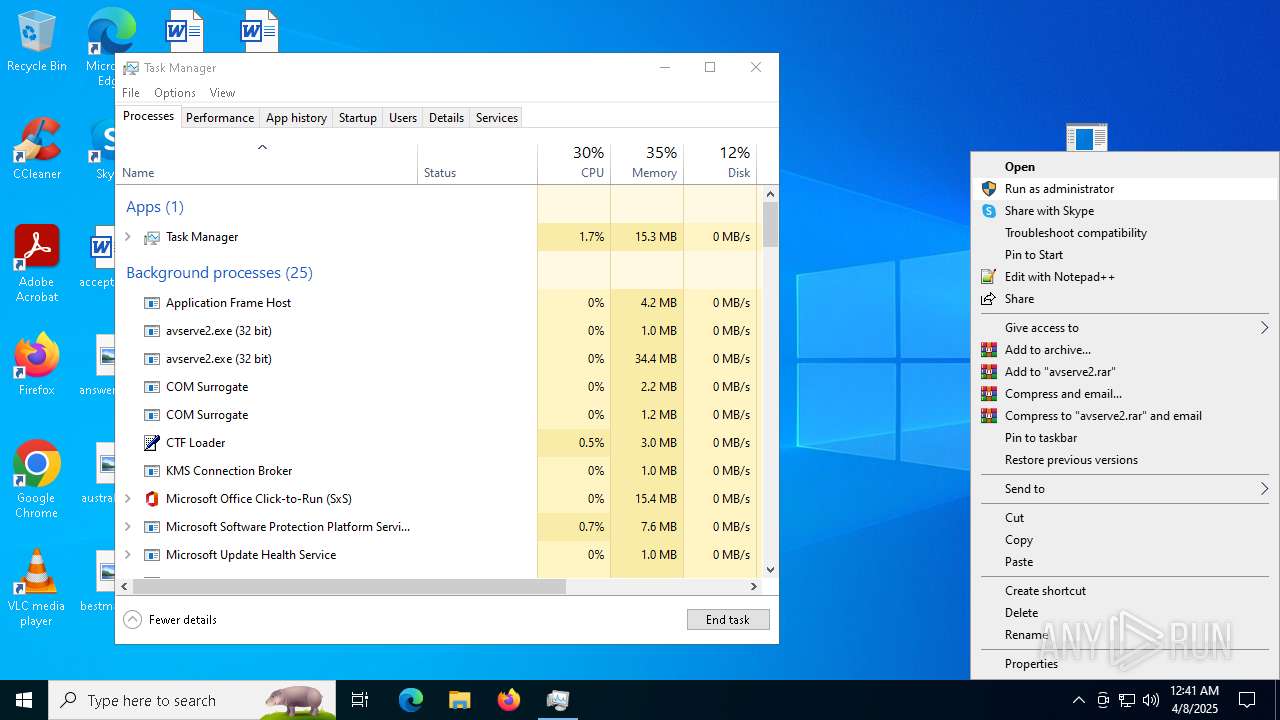
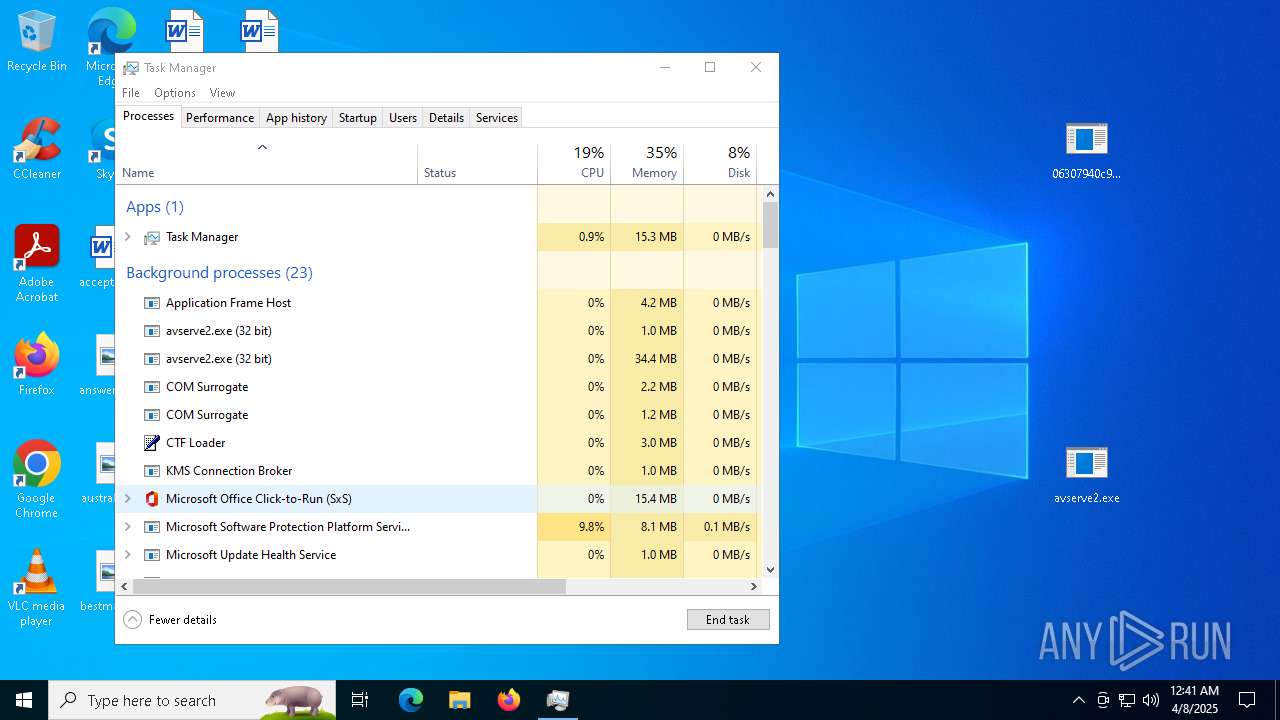
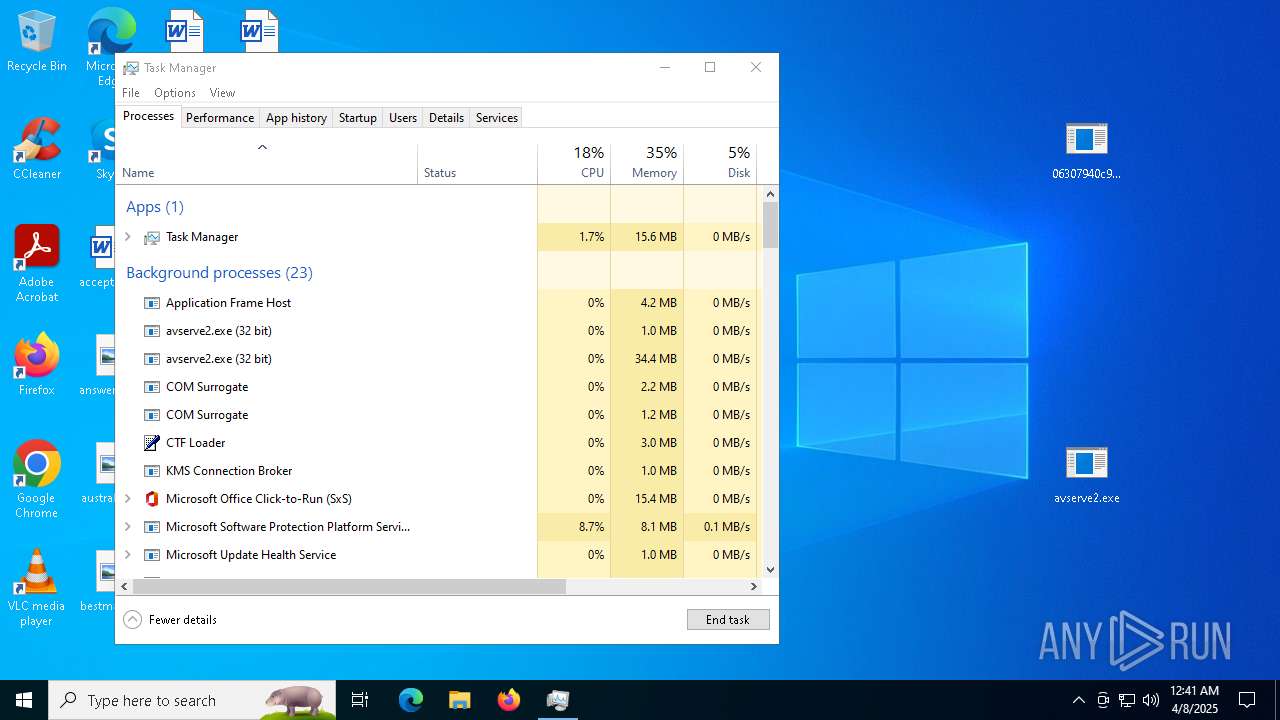
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
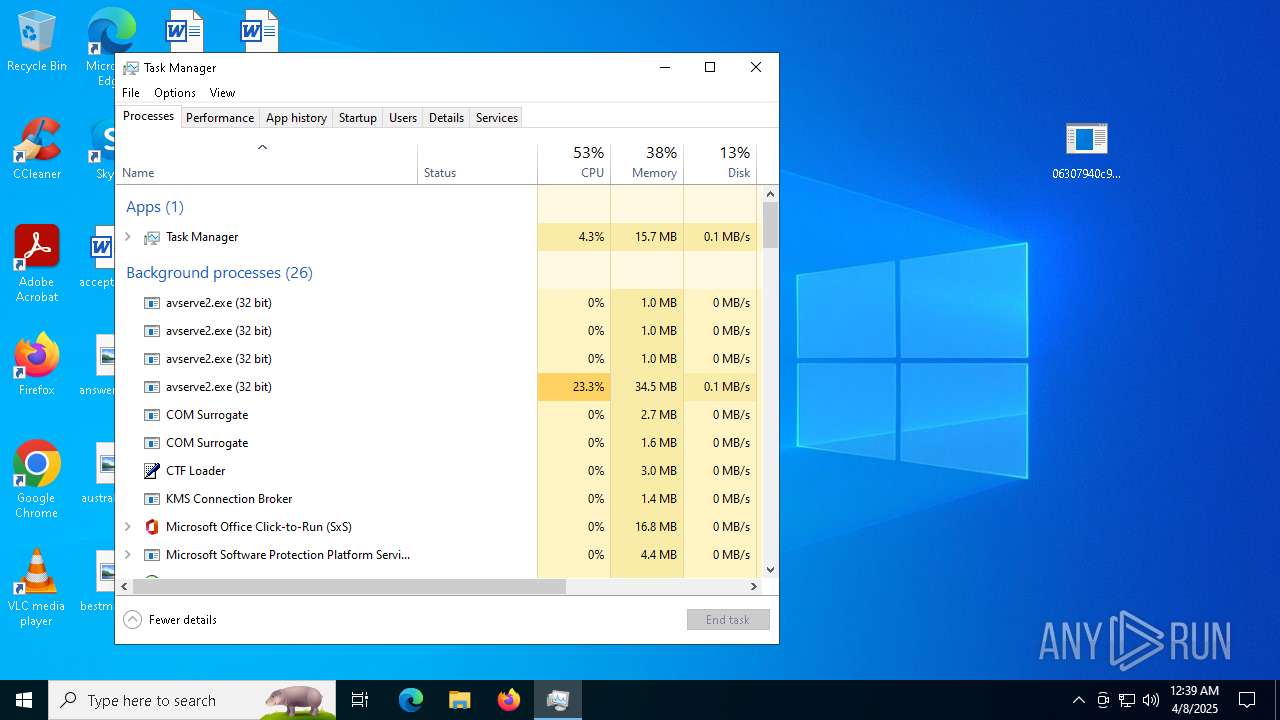
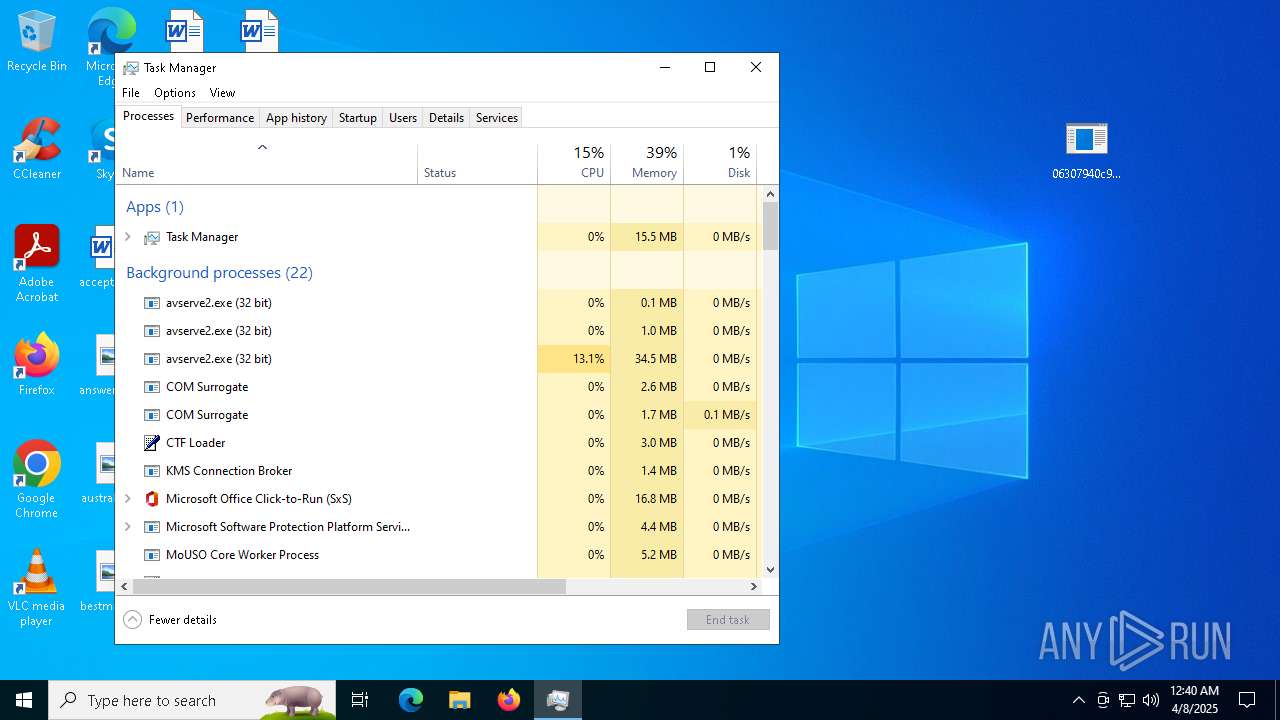
- avserve2.exe (PID: 7064)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10492)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 7056)
- avserve2.exe (PID: 11140)
- avserve2.exe (PID: 6716)
Attempt to connect to SMB server
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
- avserve2.exe (PID: 7064)
- avserve2.exe (PID: 6716)
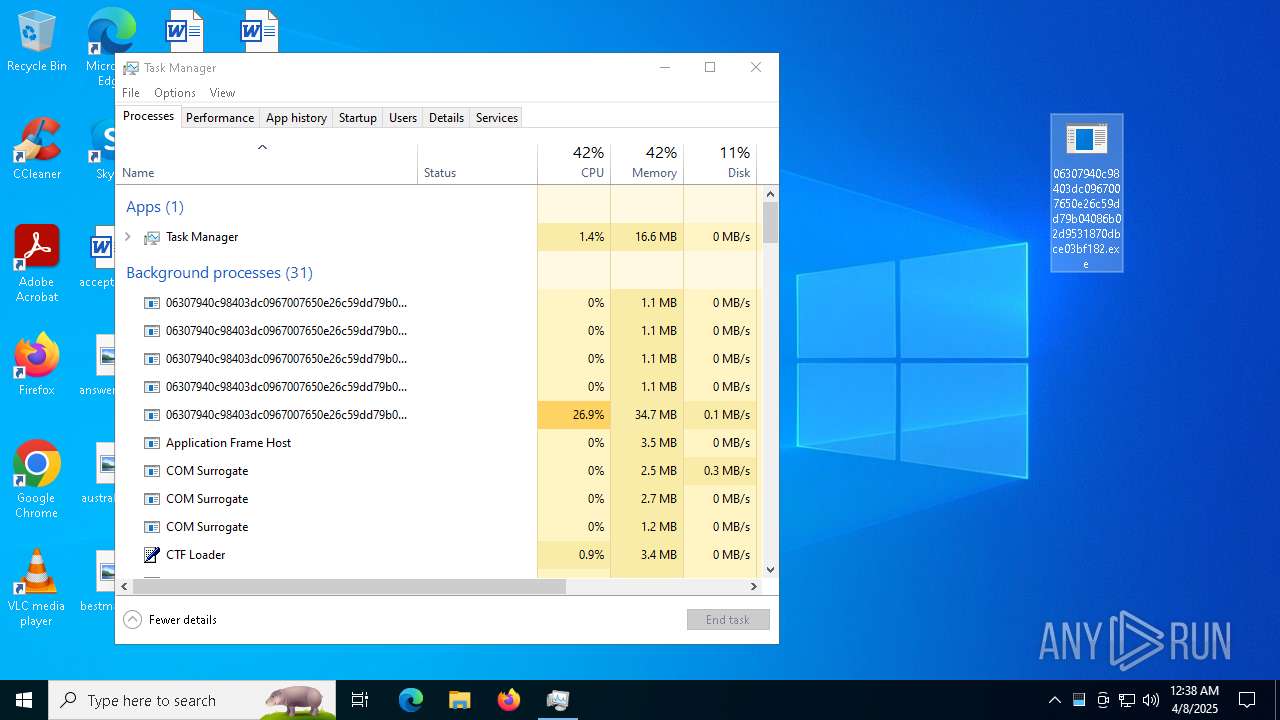
Attempting to scan the network
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
- avserve2.exe (PID: 7064)
- avserve2.exe (PID: 6716)
SMBSCAN has been detected (SURICATA)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
- avserve2.exe (PID: 7064)
- avserve2.exe (PID: 6716)
SUSPICIOUS
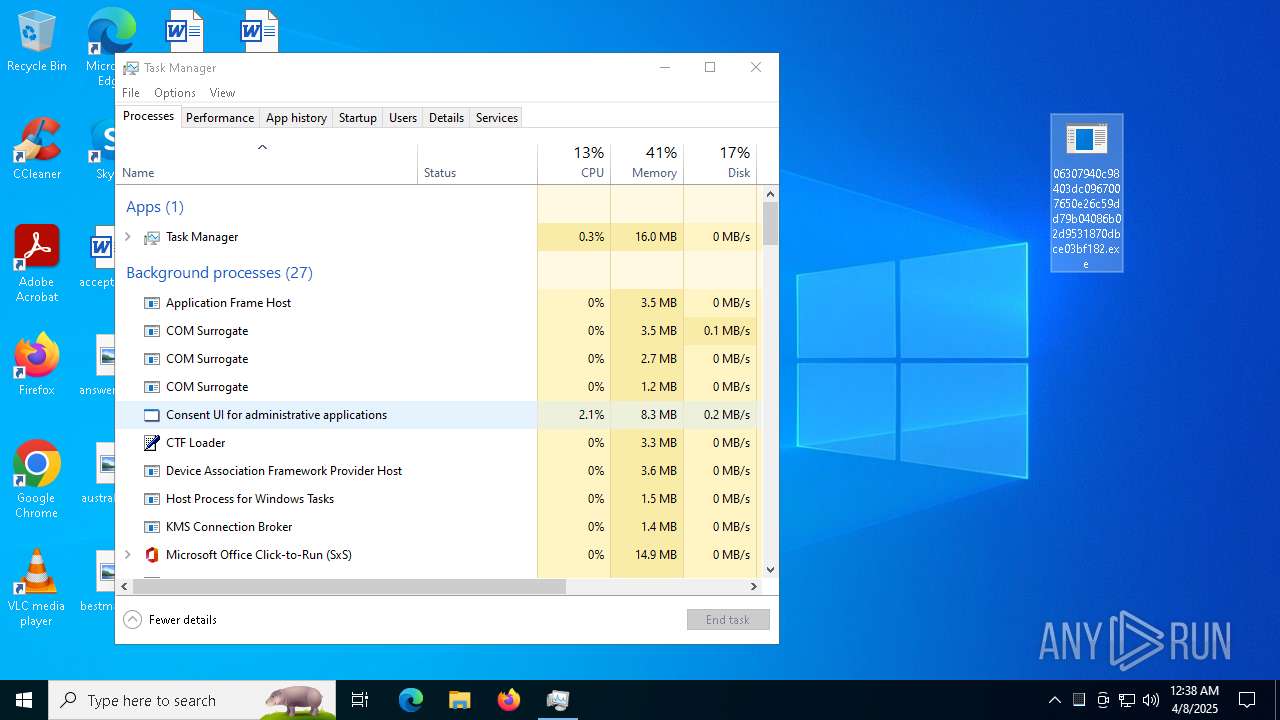
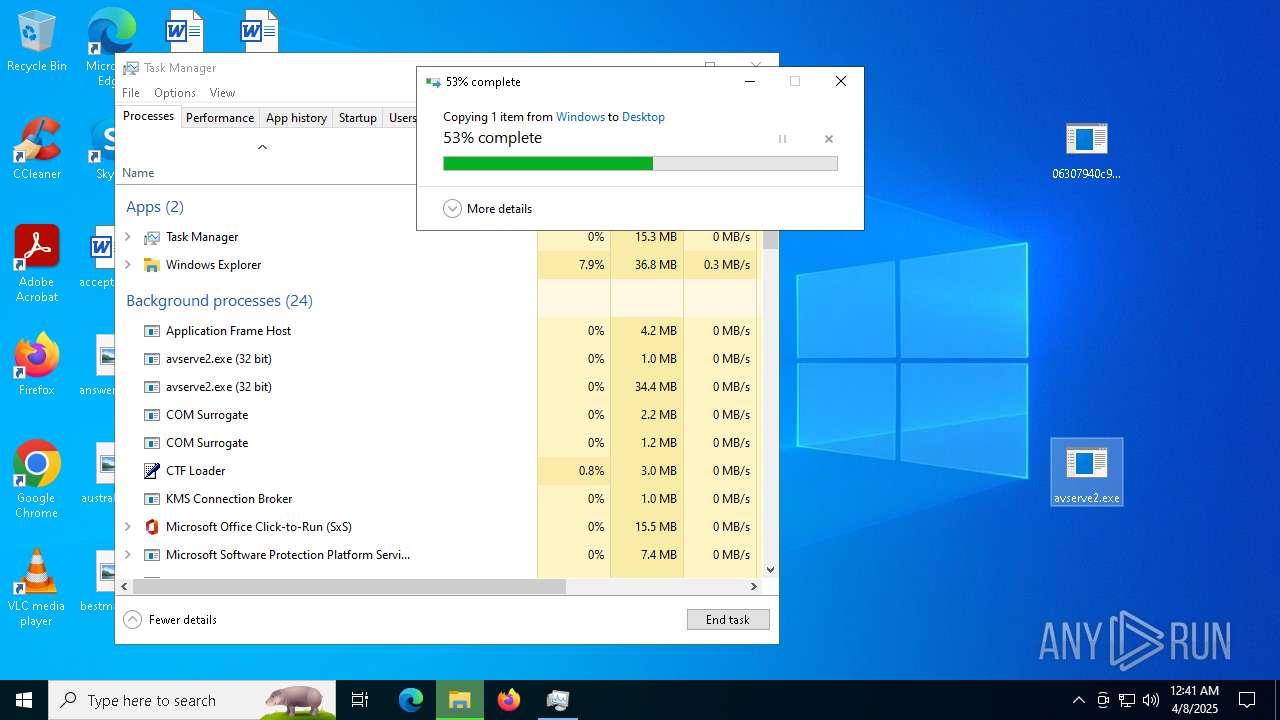
Executable content was dropped or overwritten
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
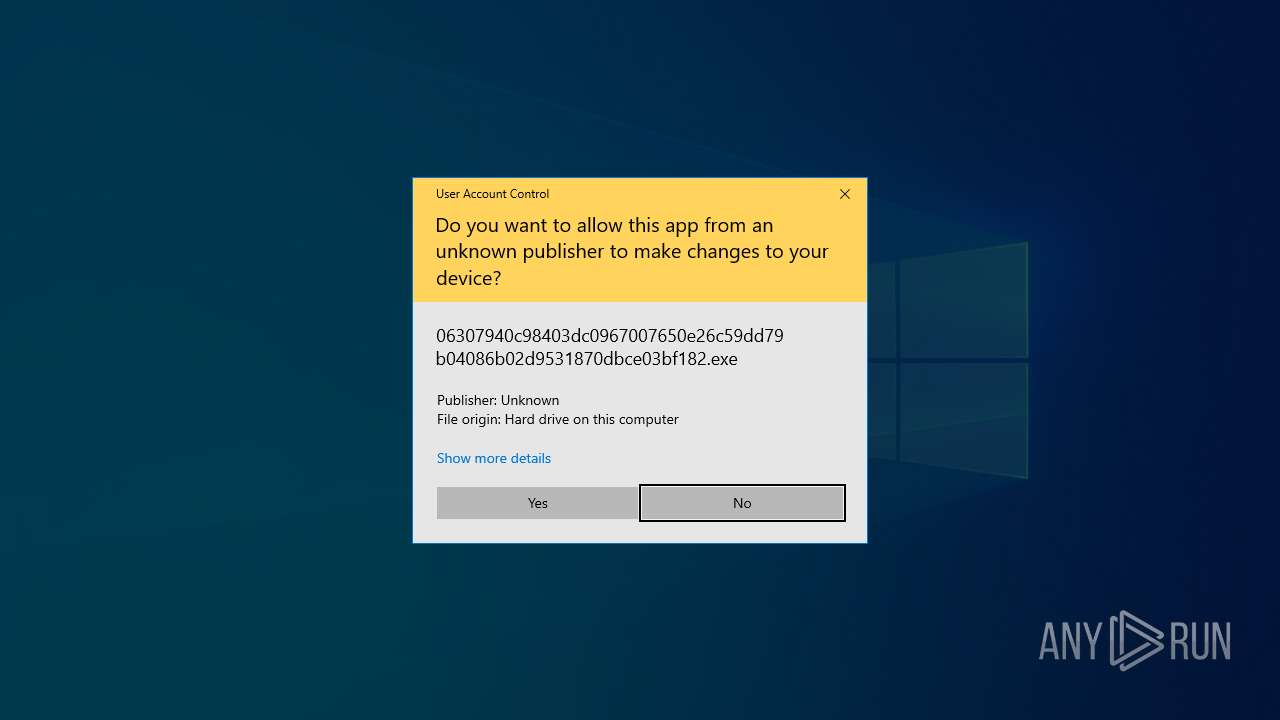
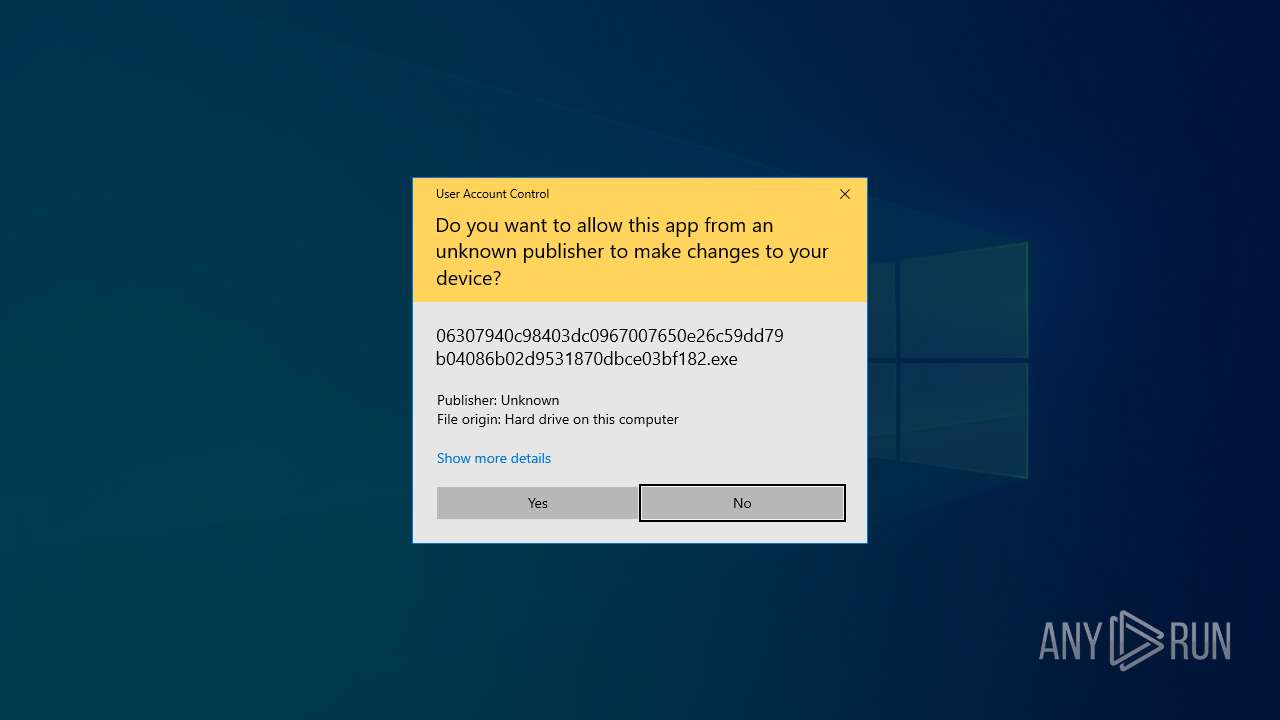
Application launched itself
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
- avserve2.exe (PID: 7064)
- avserve2.exe (PID: 6716)
Potential Corporate Privacy Violation
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
- avserve2.exe (PID: 7064)
- avserve2.exe (PID: 6716)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 684)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4172)
- PLUGScheduler.exe (PID: 2008)
INFO
Reads security settings of Internet Explorer
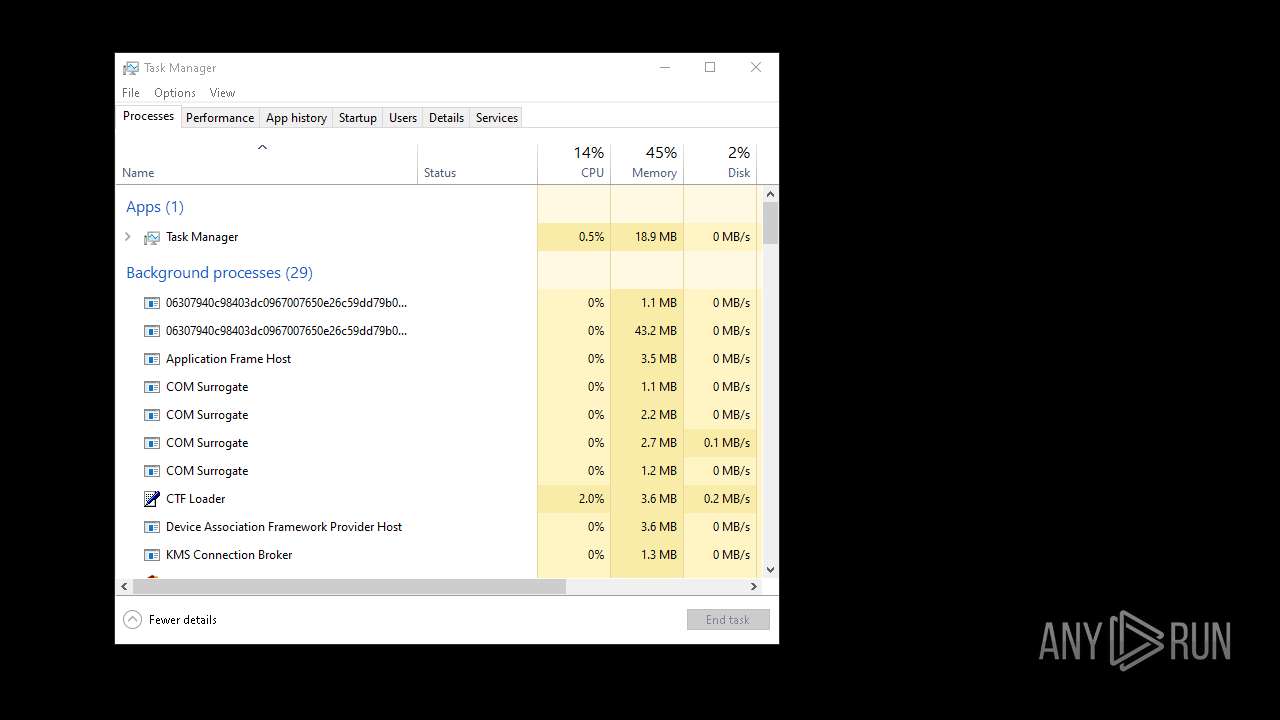
- Taskmgr.exe (PID: 1912)
- Taskmgr.exe (PID: 6932)
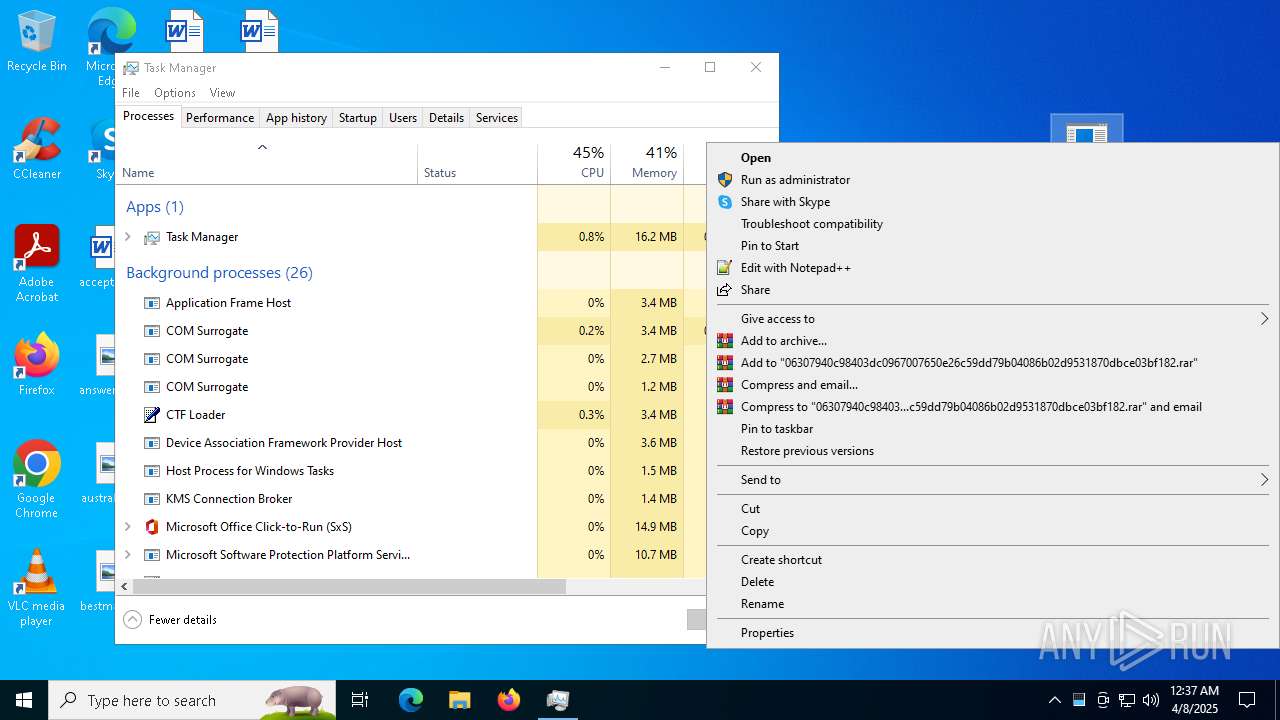
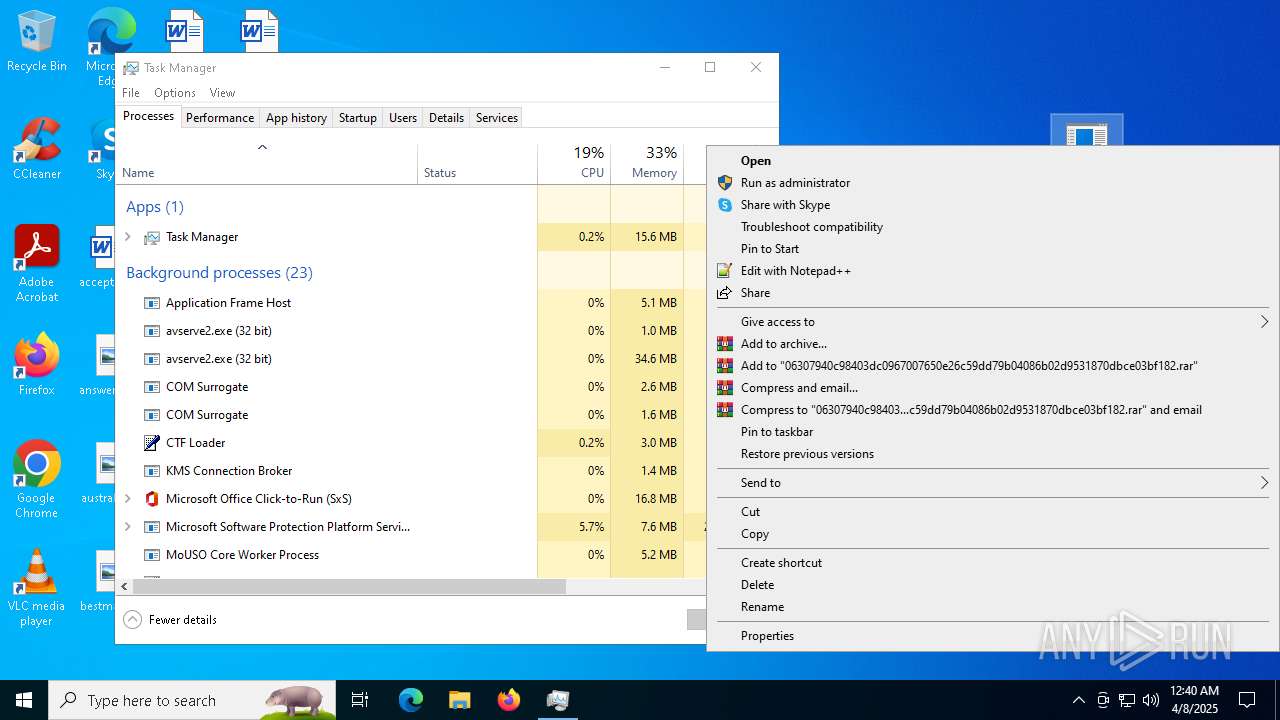
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7272)
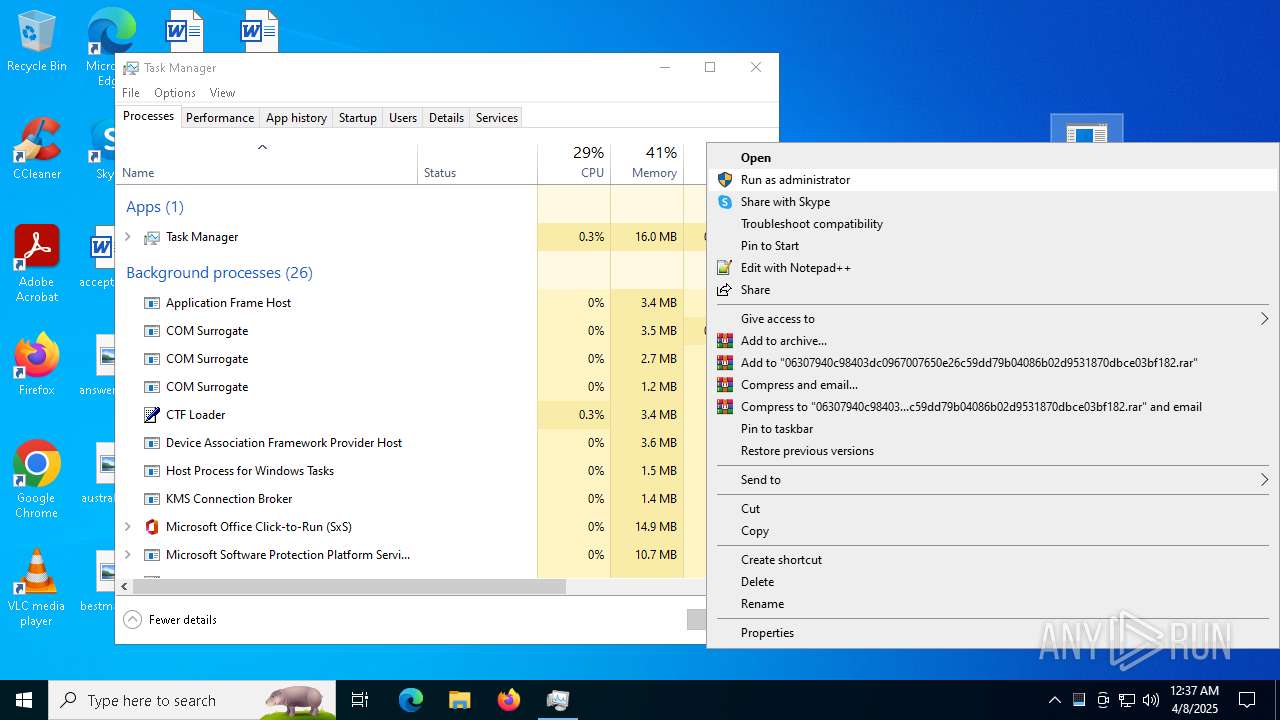
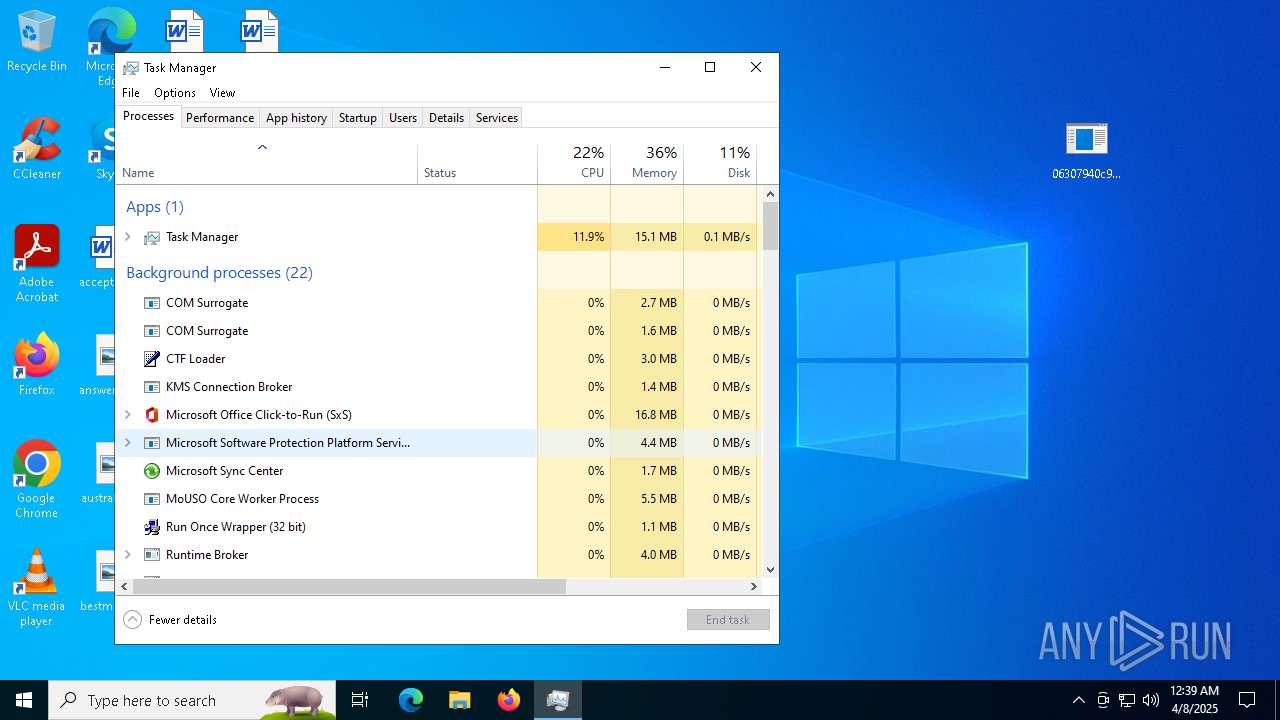
Manual execution by a user
- Taskmgr.exe (PID: 1912)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
- Taskmgr.exe (PID: 6840)
- Taskmgr.exe (PID: 6932)
- avserve2.exe (PID: 7064)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 7056)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10492)
- avserve2.exe (PID: 6716)
- avserve2.exe (PID: 11140)
Checks supported languages
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10936)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10944)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10928)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10952)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10952)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 11172)
- ShellExperienceHost.exe (PID: 684)
- avserve2.exe (PID: 7064)
- avserve2.exe (PID: 10448)
- avserve2.exe (PID: 10456)
- avserve2.exe (PID: 10464)
- avserve2.exe (PID: 10780)
- avserve2.exe (PID: 10804)
- avserve2.exe (PID: 10796)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10492)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 7056)
- avserve2.exe (PID: 7040)
- avserve2.exe (PID: 3020)
- avserve2.exe (PID: 2684)
- avserve2.exe (PID: 3056)
- avserve2.exe (PID: 2784)
- avserve2.exe (PID: 10760)
- avserve2.exe (PID: 11172)
- PLUGScheduler.exe (PID: 2008)
- avserve2.exe (PID: 6716)
- avserve2.exe (PID: 10616)
- avserve2.exe (PID: 11140)
Reads the computer name
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 4892)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10944)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10936)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10952)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10928)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 10952)
- PLUGScheduler.exe (PID: 4172)
- 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe (PID: 11172)
- ShellExperienceHost.exe (PID: 684)
- avserve2.exe (PID: 10456)
- avserve2.exe (PID: 10780)
- avserve2.exe (PID: 10448)
- avserve2.exe (PID: 10464)
- avserve2.exe (PID: 10796)
- avserve2.exe (PID: 10804)
- avserve2.exe (PID: 7064)
- avserve2.exe (PID: 10760)
- avserve2.exe (PID: 2684)
- avserve2.exe (PID: 7040)
- avserve2.exe (PID: 3020)
- avserve2.exe (PID: 3056)
- avserve2.exe (PID: 11172)
- PLUGScheduler.exe (PID: 2008)
- avserve2.exe (PID: 6716)
- avserve2.exe (PID: 10616)
- avserve2.exe (PID: 2784)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4172)
- PLUGScheduler.exe (PID: 2008)
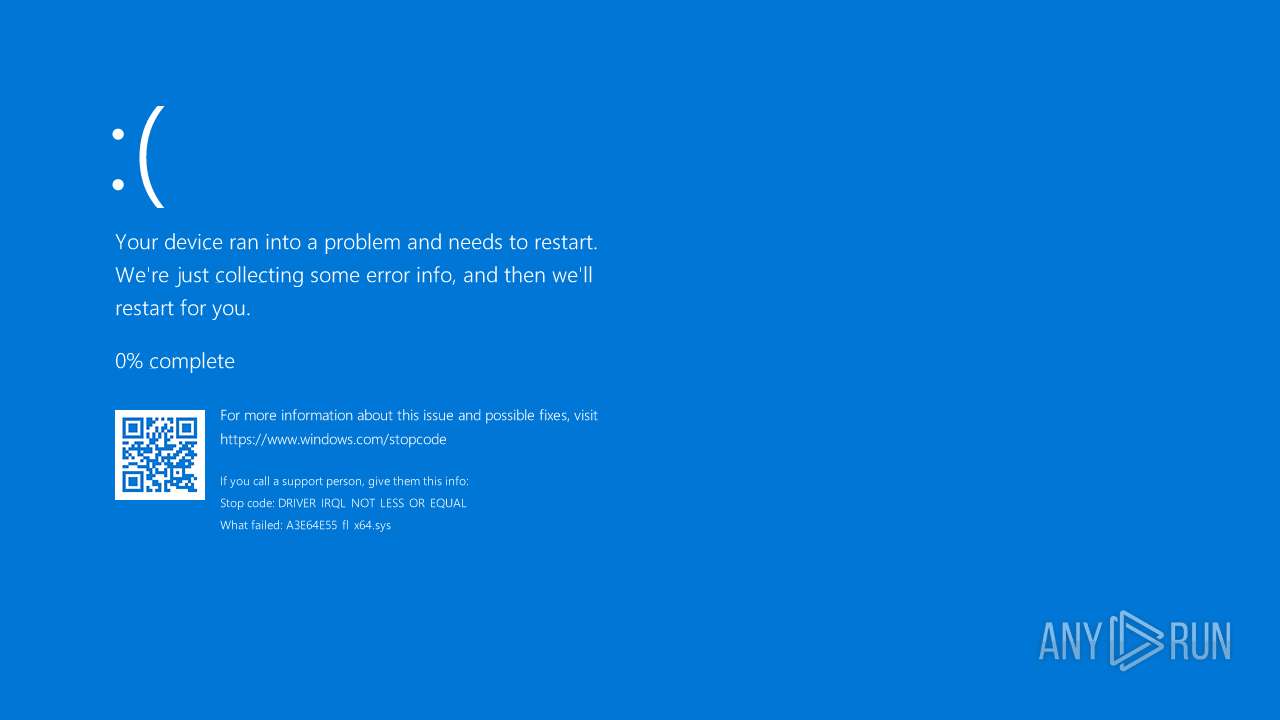
Failed to create an executable file in Windows directory
- avserve2.exe (PID: 7064)
- avserve2.exe (PID: 6716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:07 18:33:48 |
| ZipCRC: | 0x55cad77d |
| ZipCompressedSize: | 21439 |
| ZipUncompressedSize: | 86032 |
| ZipFileName: | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe |
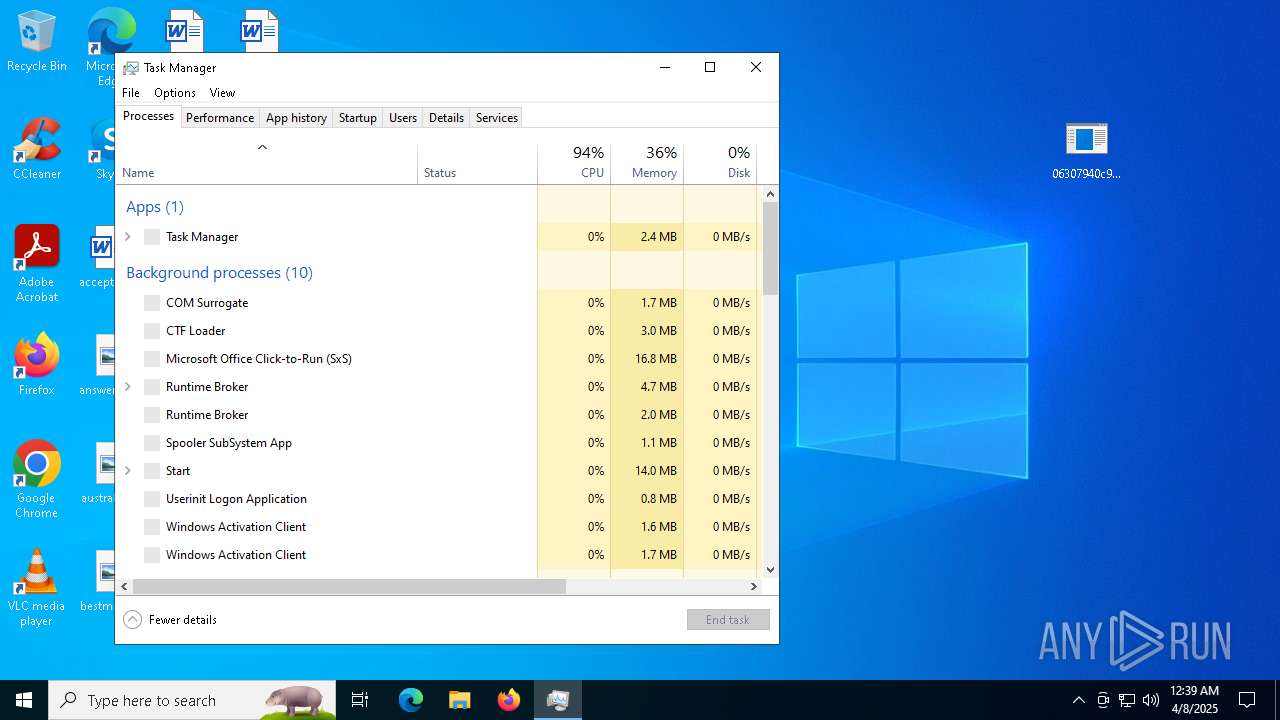
Total processes
430
Monitored processes
35
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | "C:\WINDOWS\system32\taskmgr.exe" /7 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2684 | C:\Windows\avserve2.exe 127.180.193.162 | C:\Windows\avserve2.exe | — | avserve2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2784 | C:\Windows\avserve2.exe 127.154.35.182 | C:\Windows\avserve2.exe | — | avserve2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3020 | C:\Windows\avserve2.exe 127.9.168.227 | C:\Windows\avserve2.exe | — | avserve2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3056 | C:\Windows\avserve2.exe 127.235.236.85 | C:\Windows\avserve2.exe | — | avserve2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 4172 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
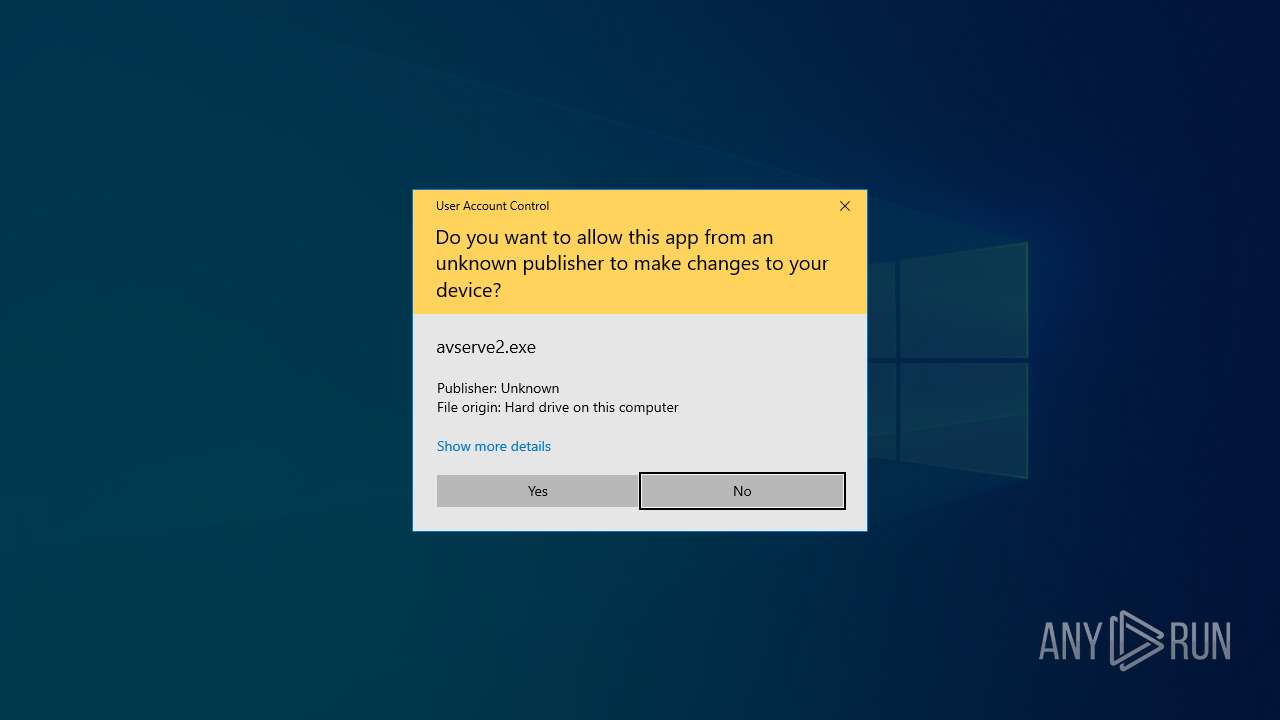
| 4892 | "C:\Users\admin\Desktop\06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe" | C:\Users\admin\Desktop\06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6716 | "C:\Windows\avserve2.exe" | C:\Windows\avserve2.exe | runonce.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
30 022
Read events
29 994
Write events
26
Delete events
2
Modification events
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Sasser Killer.zip | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
2
Suspicious files
87
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7272 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7272.47330\06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | executable | |
MD5:1F696B30880212766A804A20F6C52751 | SHA256:06307940C98403DC0967007650E26C59DD79B04086B02D9531870DBCE03BF182 | |||
| 4172 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.047.etl | binary | |
MD5:FED961067F664B5381B65A534B7AB728 | SHA256:652F31A8284AE812D1D9D24192BC800976BF74C240591C6AC443A28C4709FB7C | |||
| 4172 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 4172 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 4172 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.046.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 4172 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:89BD161BF7B46C9078937CF832786737 | SHA256:2B83DF5532E9F54ED301C8F82E2CDD489799C8D5222A2D44C97DCB151A96FAA9 | |||
| 1912 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 4172 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.033.etl | binary | |
MD5:AB9303129E2242D02DC2069E5A4F3896 | SHA256:9031A5BD681D52A903A2BCA625F6D9D8B1456B26D2335CA8170BB39A2FE8F2A0 | |||
| 4172 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.038.etl | binary | |
MD5:F9485F2BA891697F8B6CF8FB1E7F42C0 | SHA256:69146D4AAEFB8609745B6CA780B48ABC66054AA3CDB8061248CF7B32F3B32617 | |||
| 4172 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.041.etl | binary | |
MD5:09359EE89B0634478ADFF73CDA7BFB12 | SHA256:4D800AC7C55960B107C9D3E40F63130407835E69DF4F5C558C500FC0BD20D8ED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
8 985
DNS requests
35
Threats
41
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
11176 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
11176 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5600 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers inside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |
4892 | 06307940c98403dc0967007650e26c59dd79b04086b02d9531870dbce03bf182.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to scan SMB servers outside a home network |