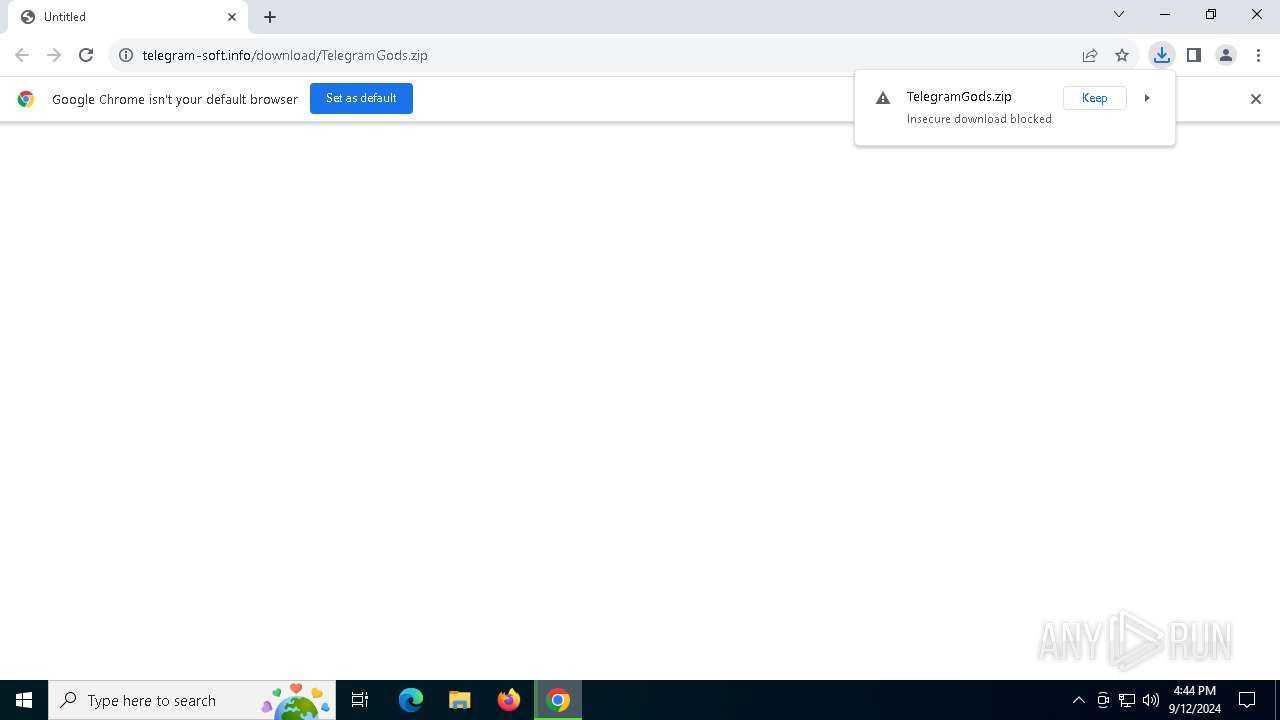
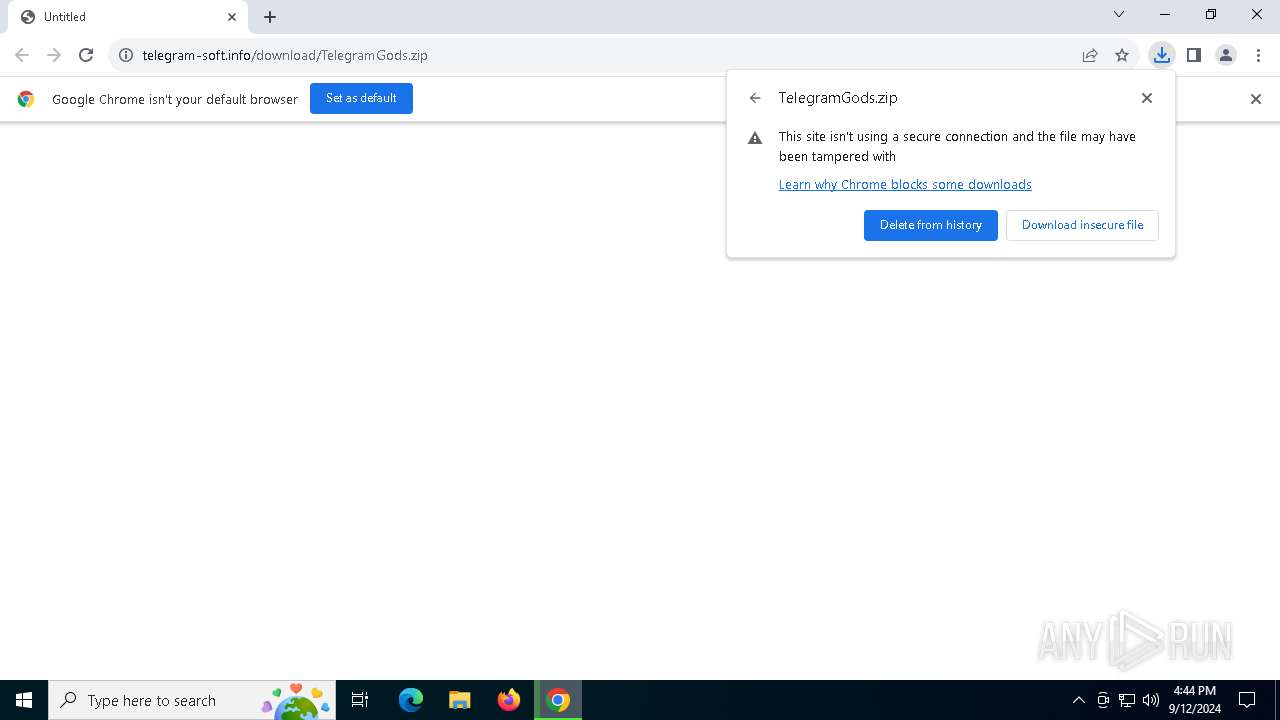
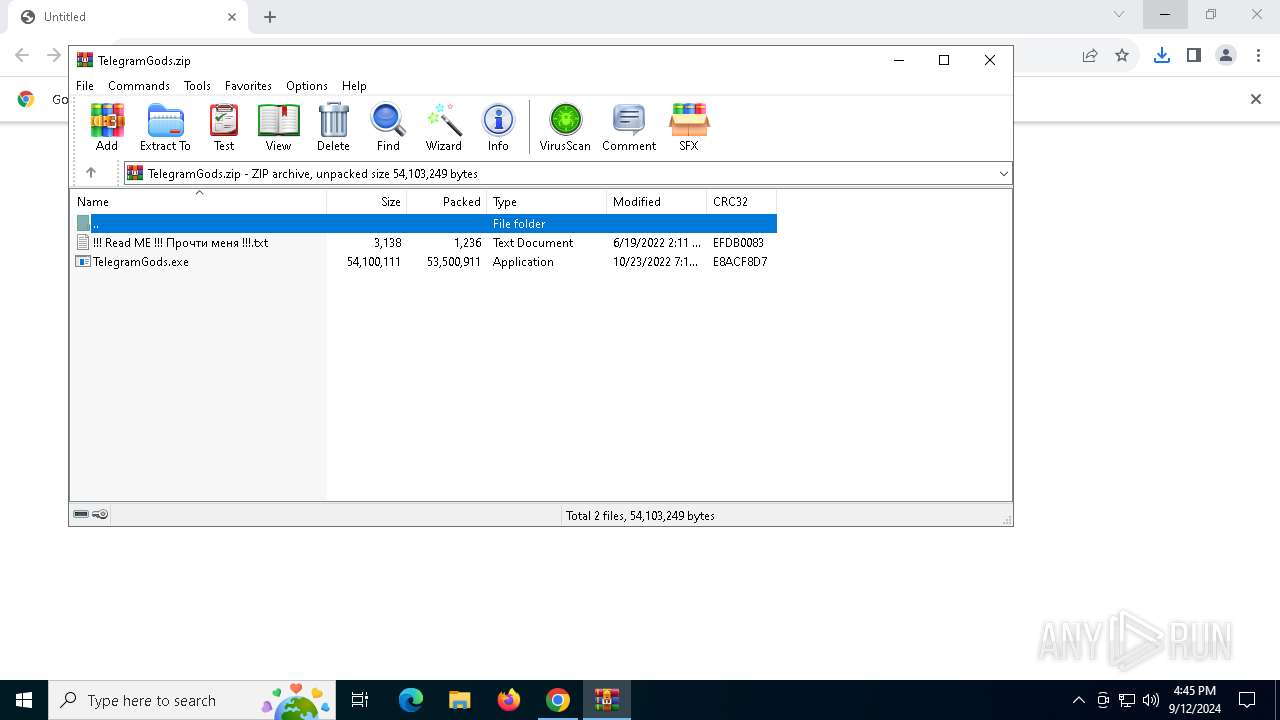
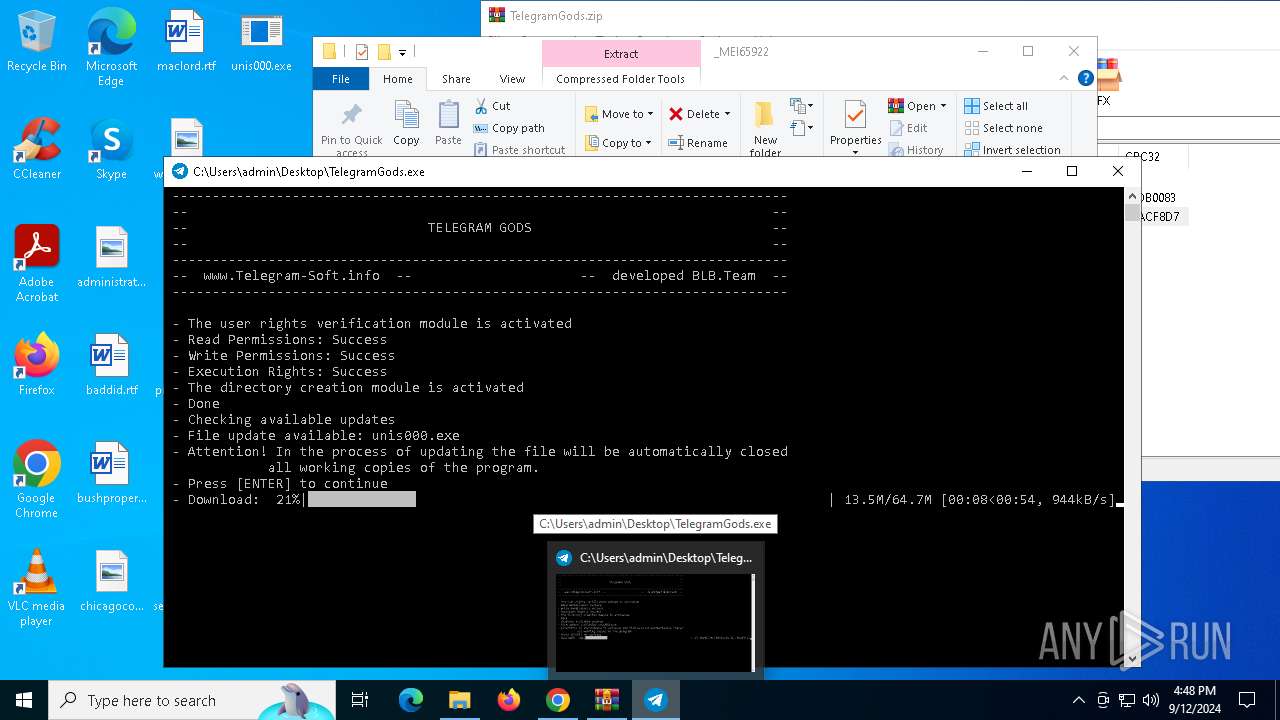
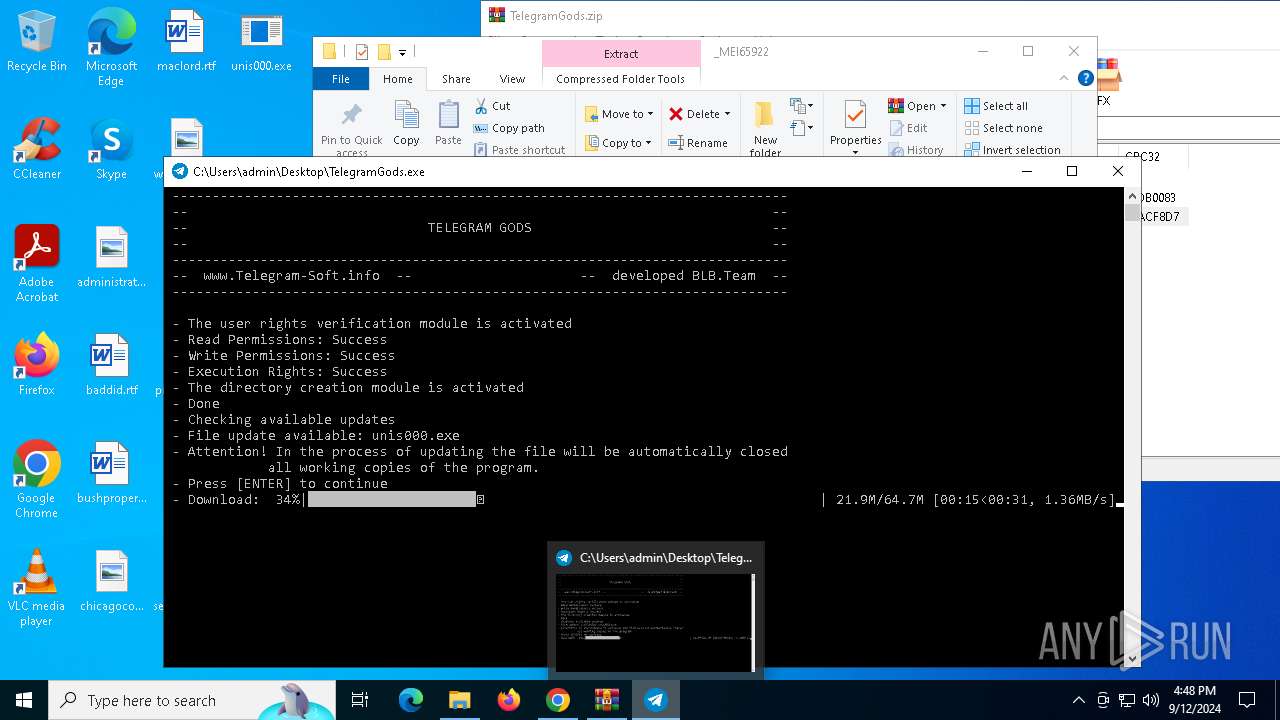
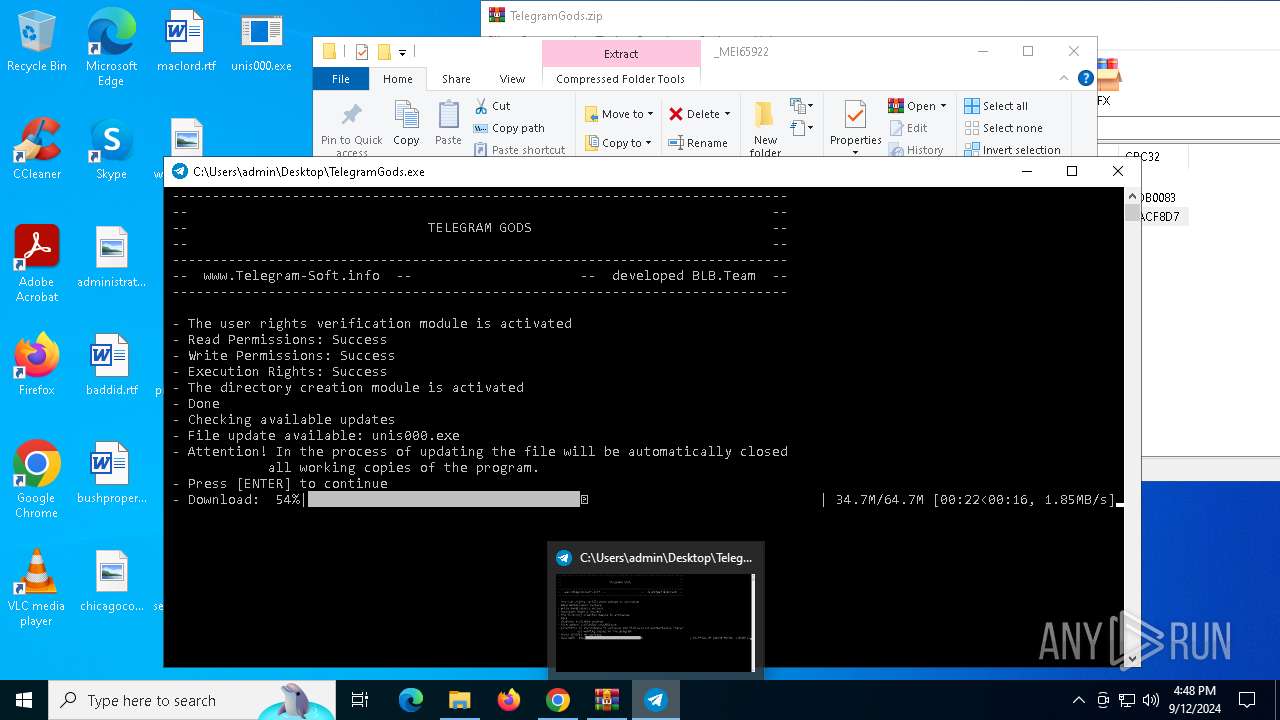
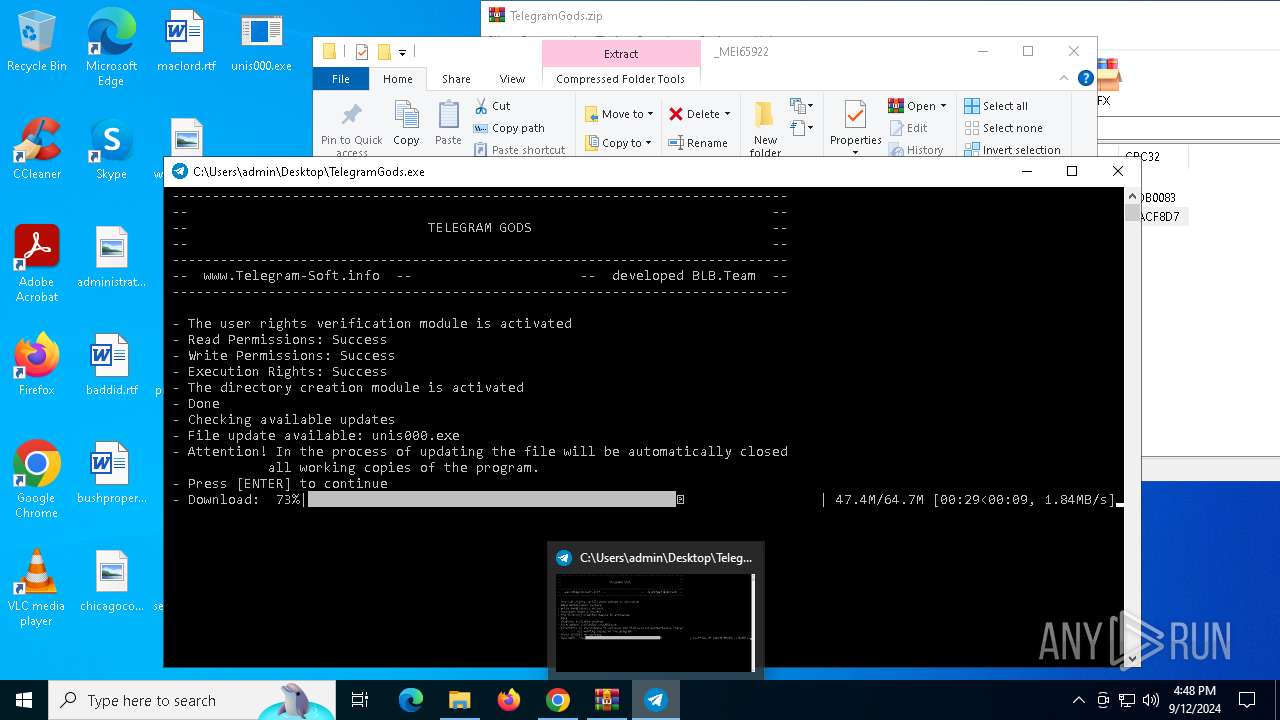
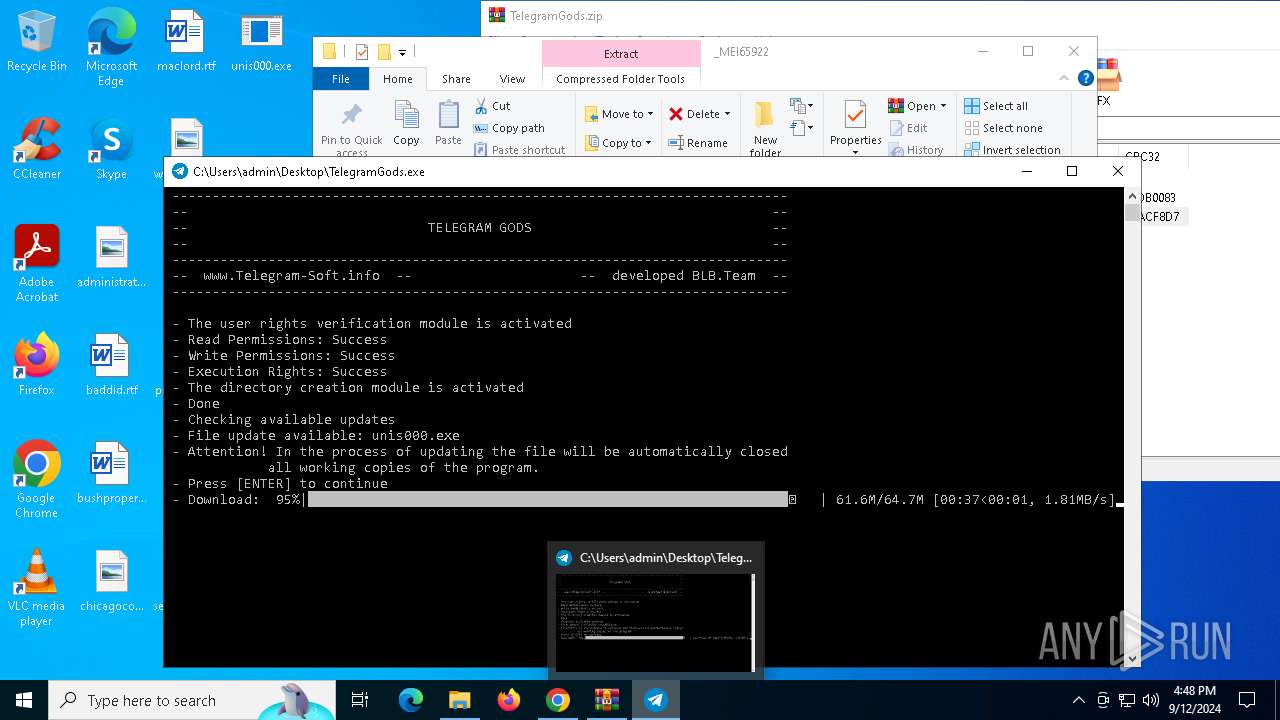
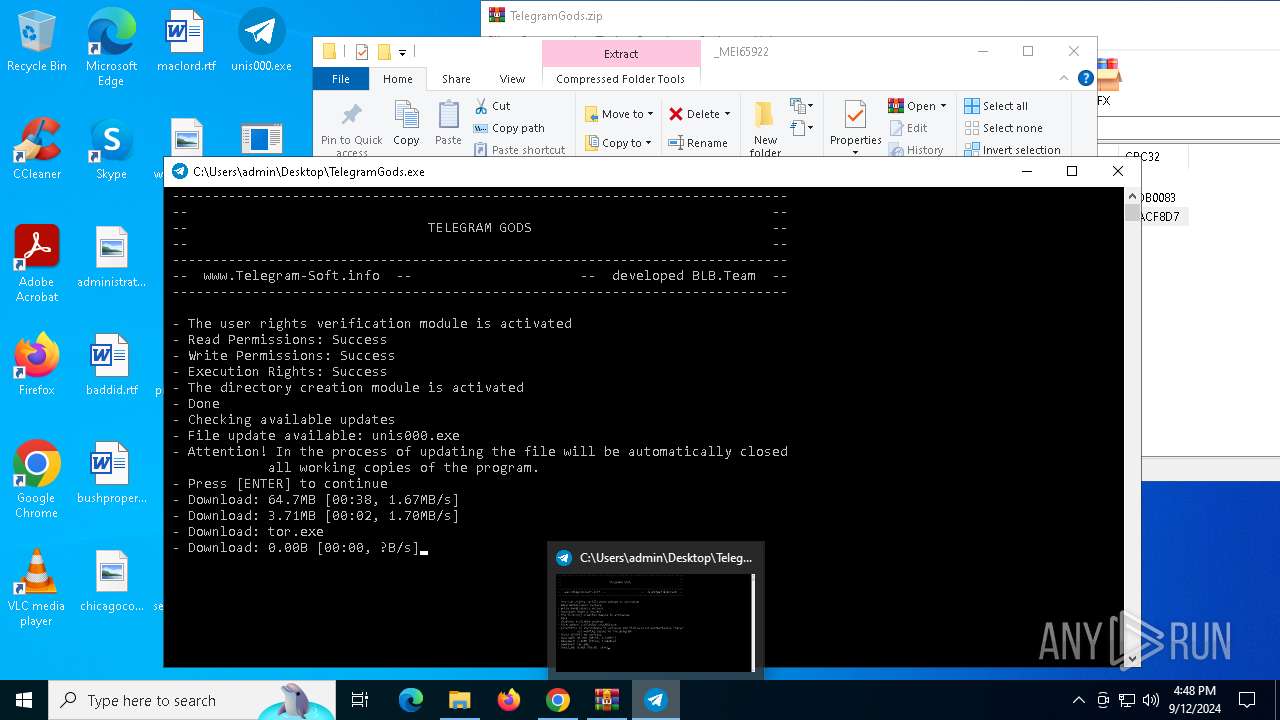
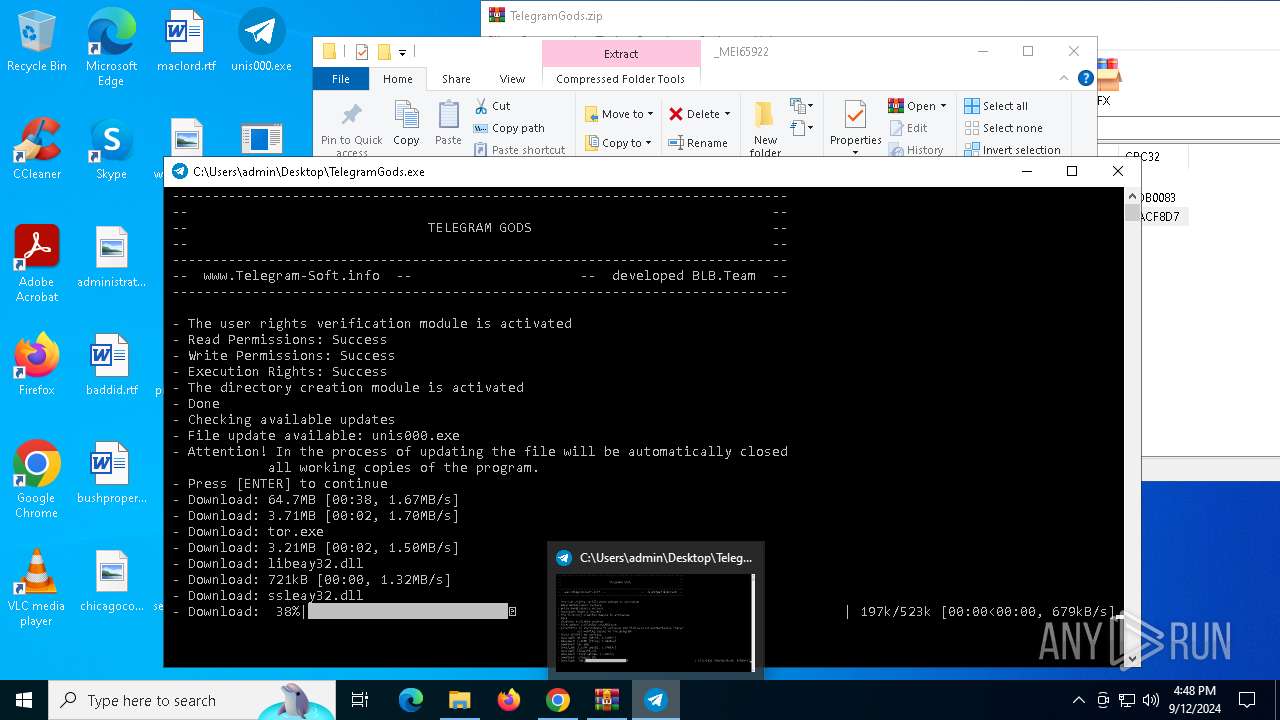
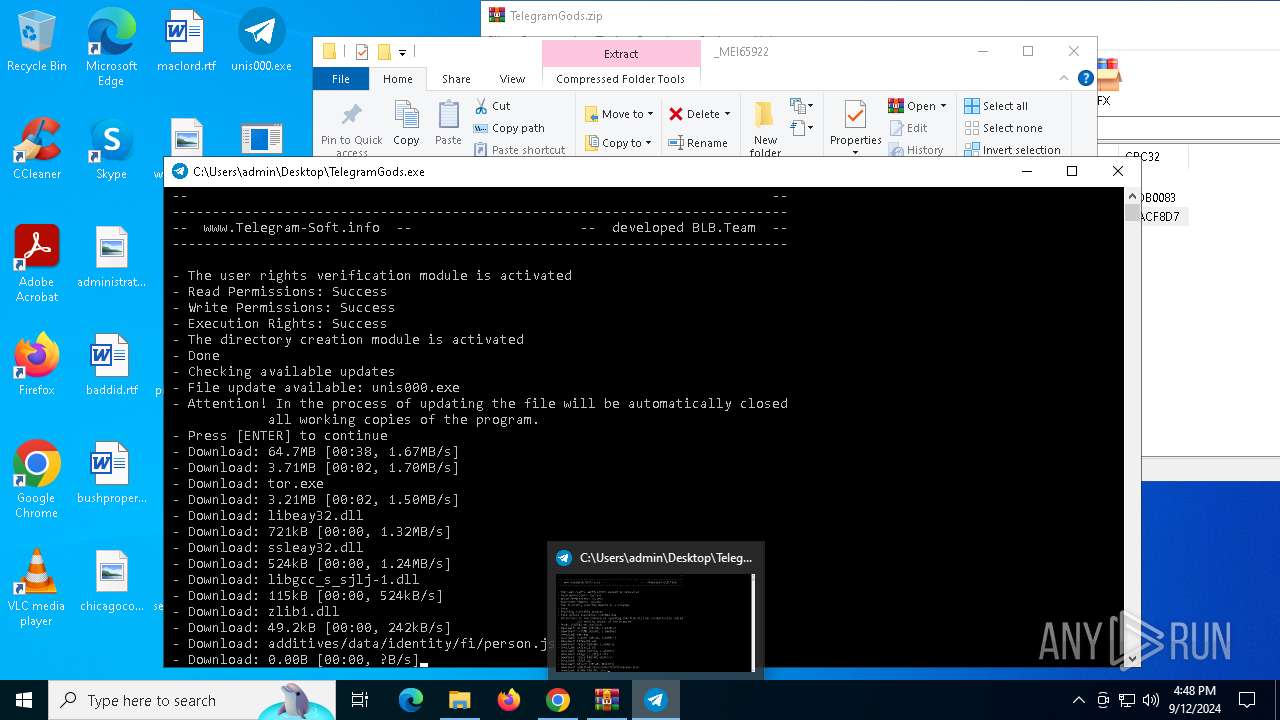
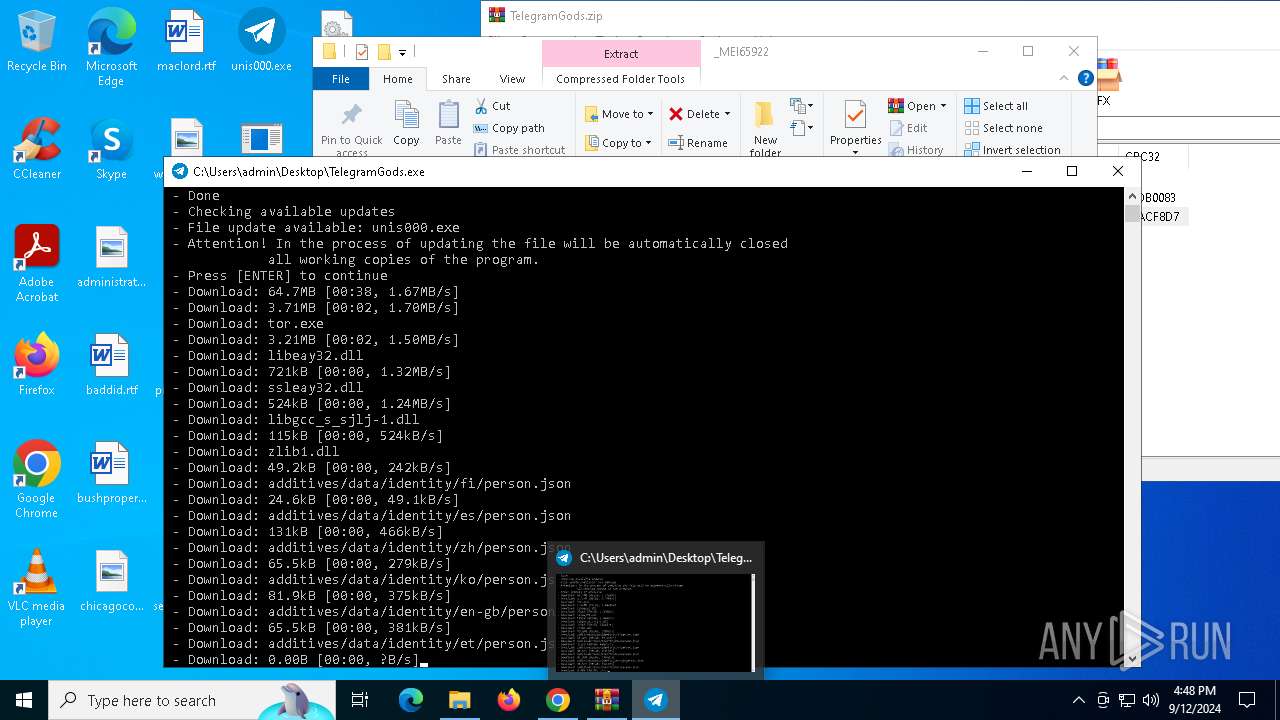
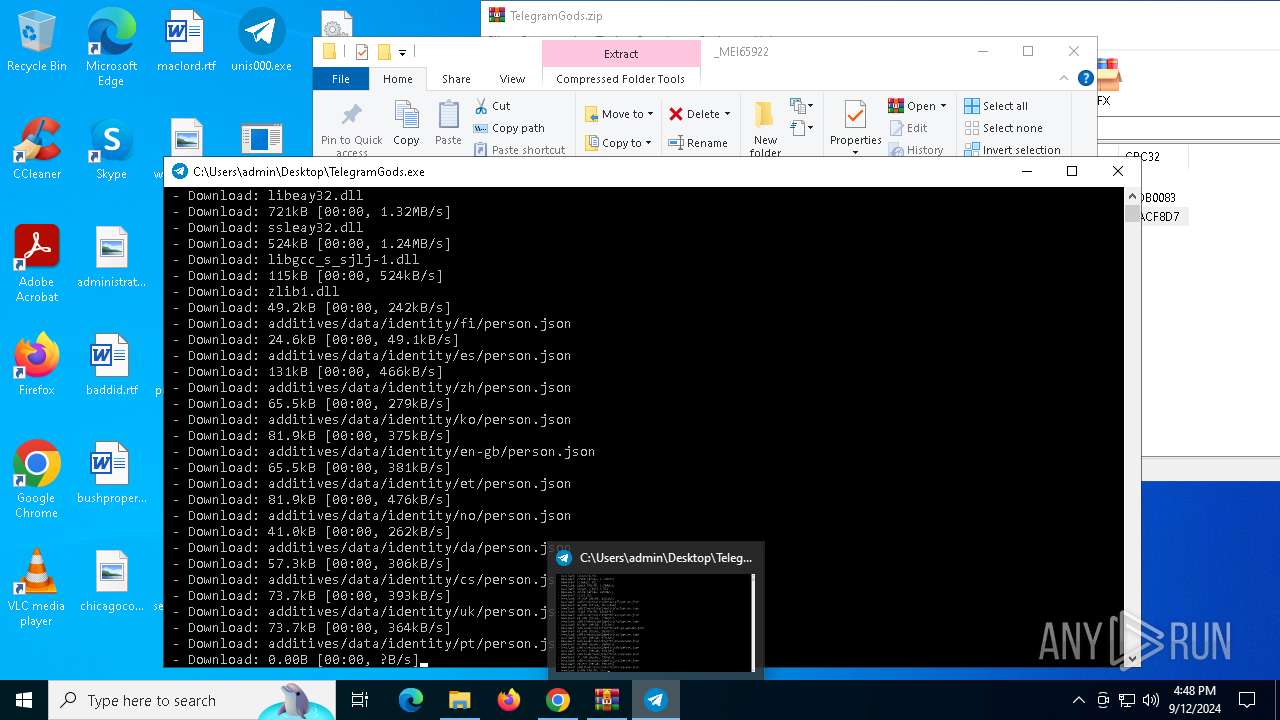
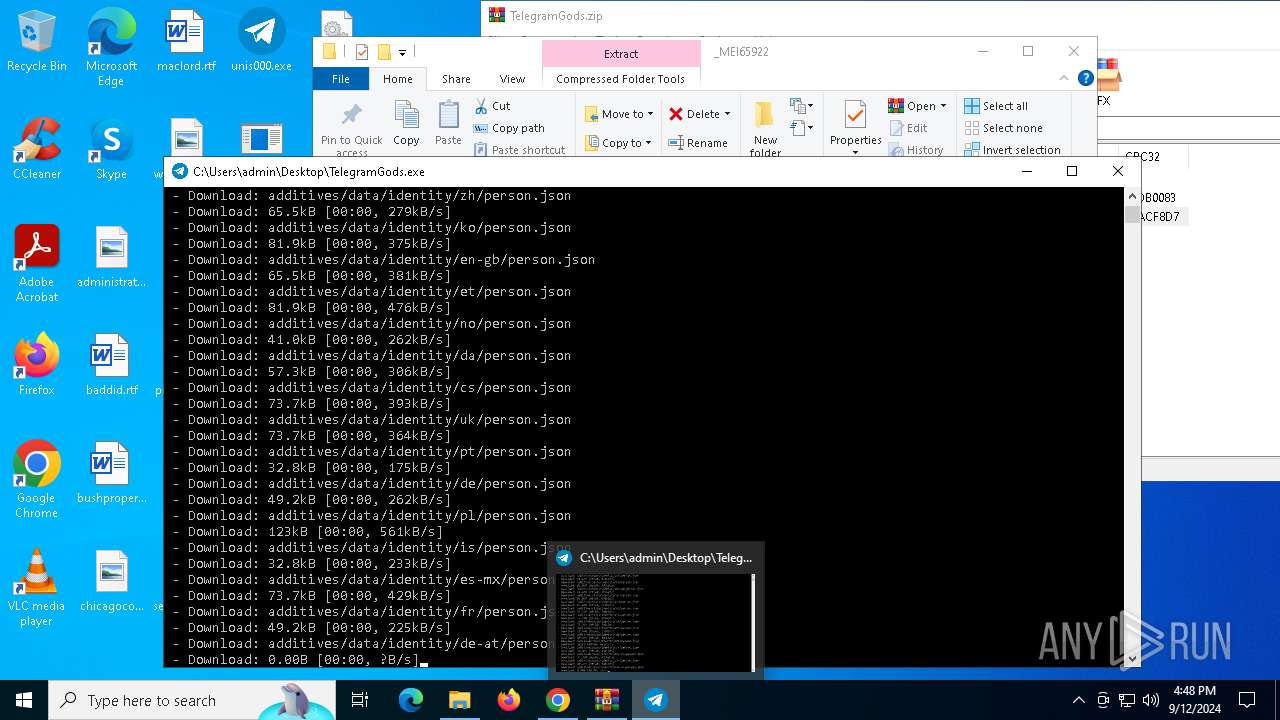
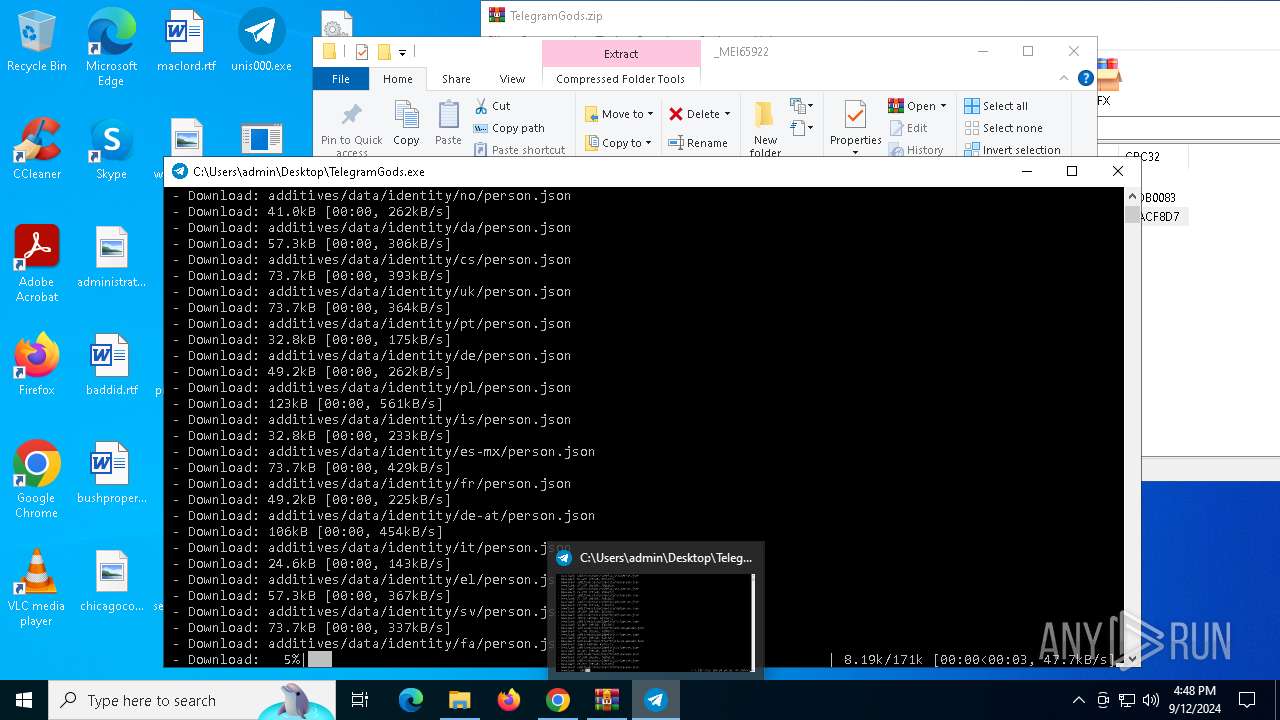
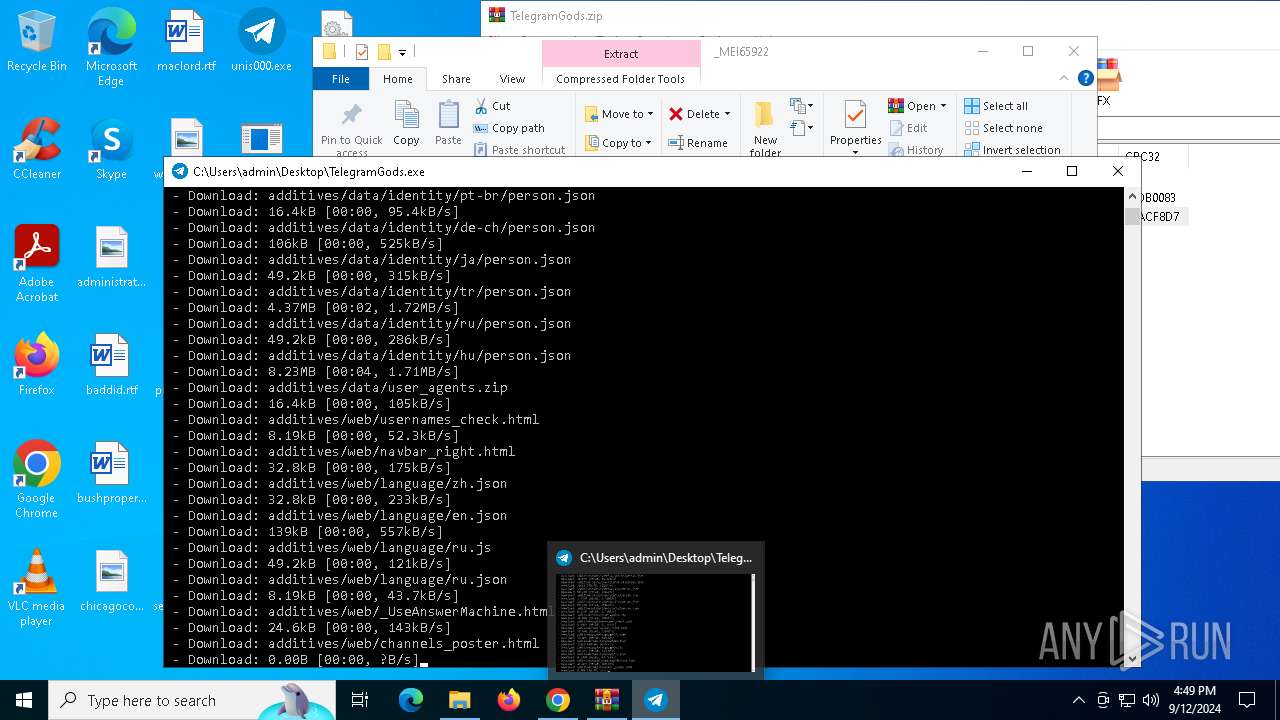
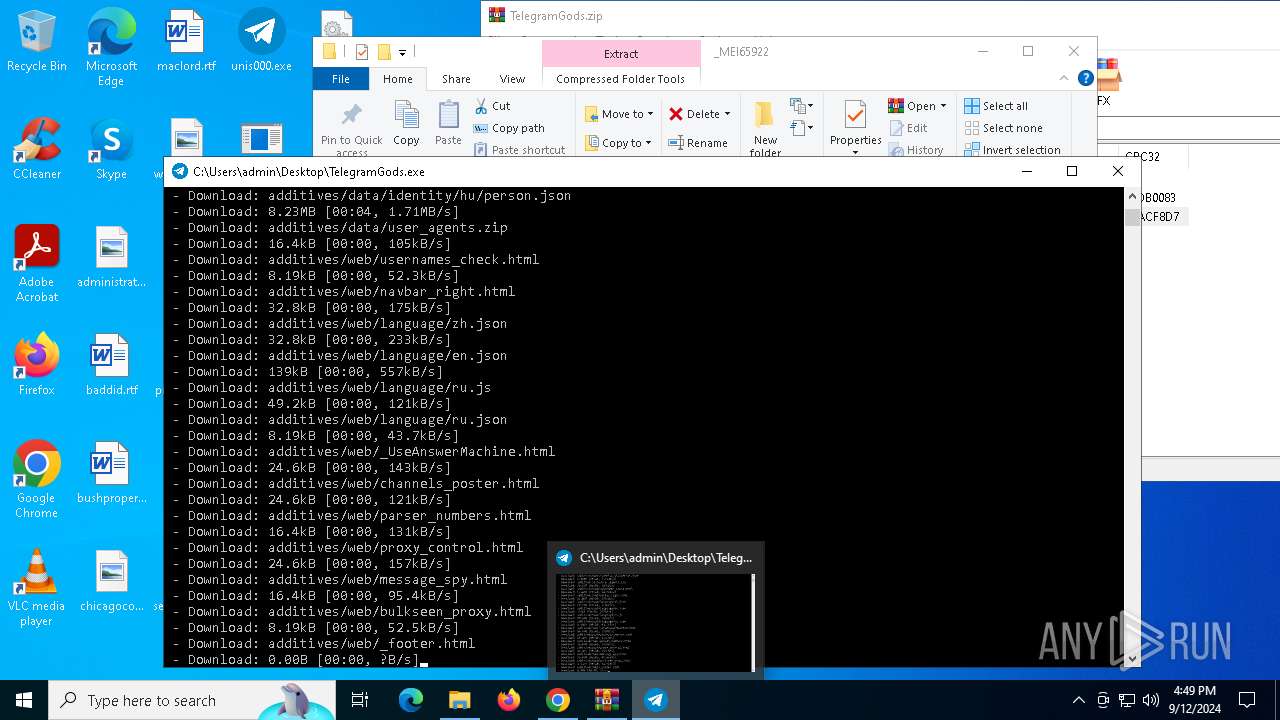
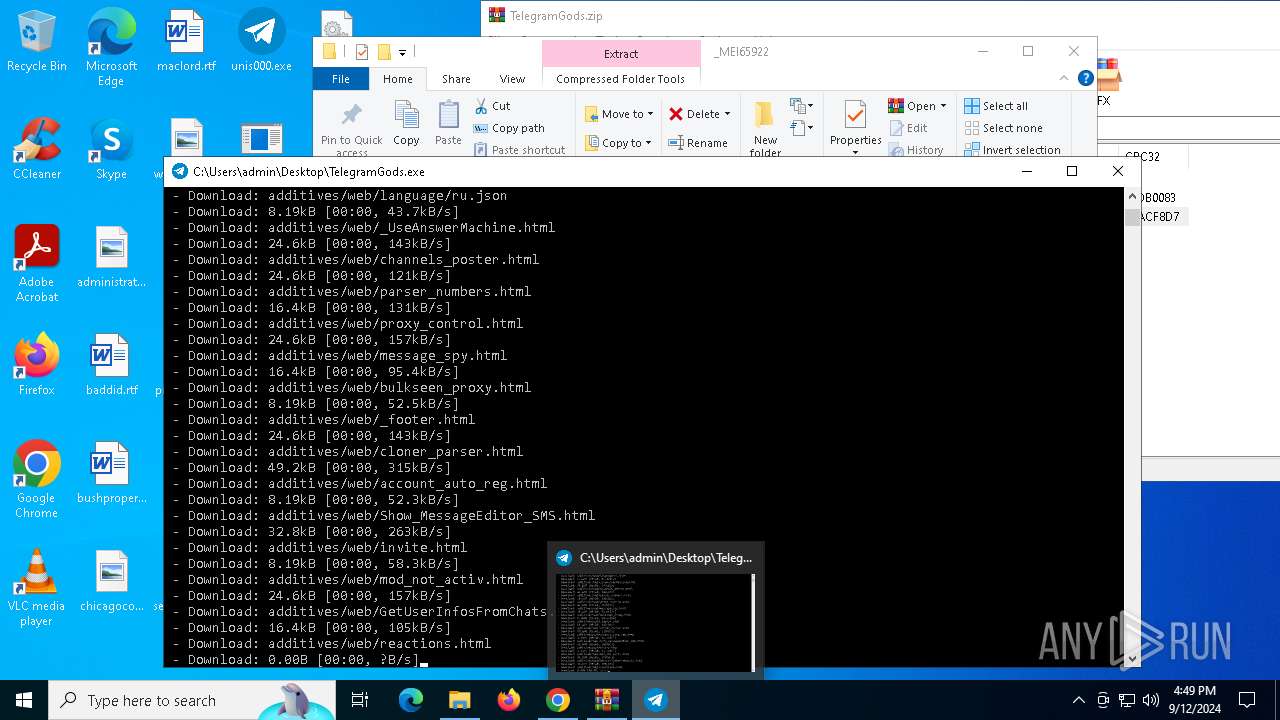
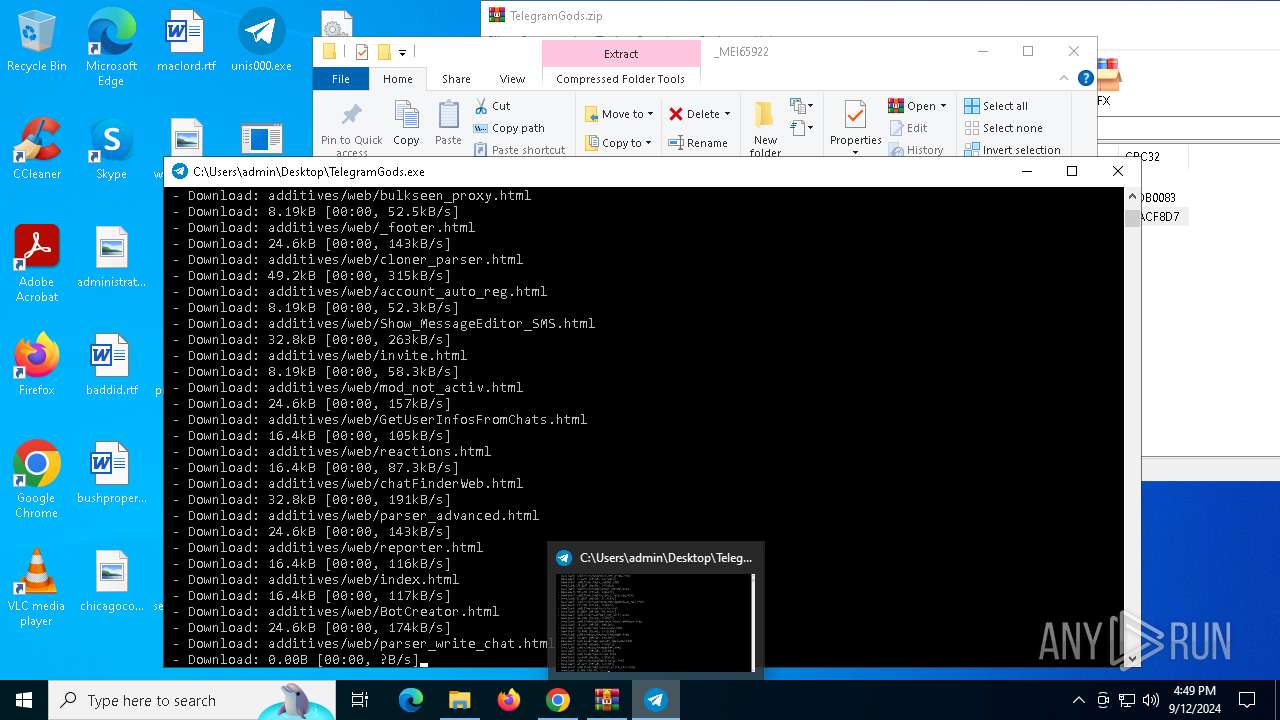
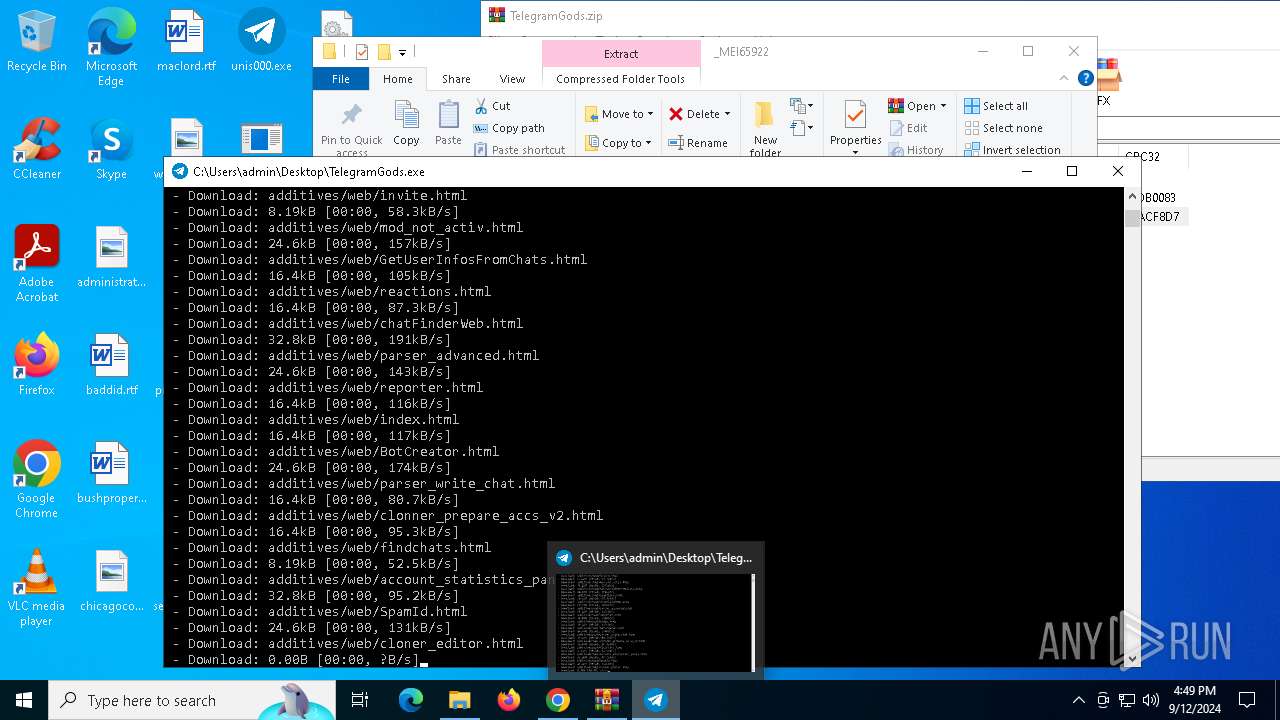
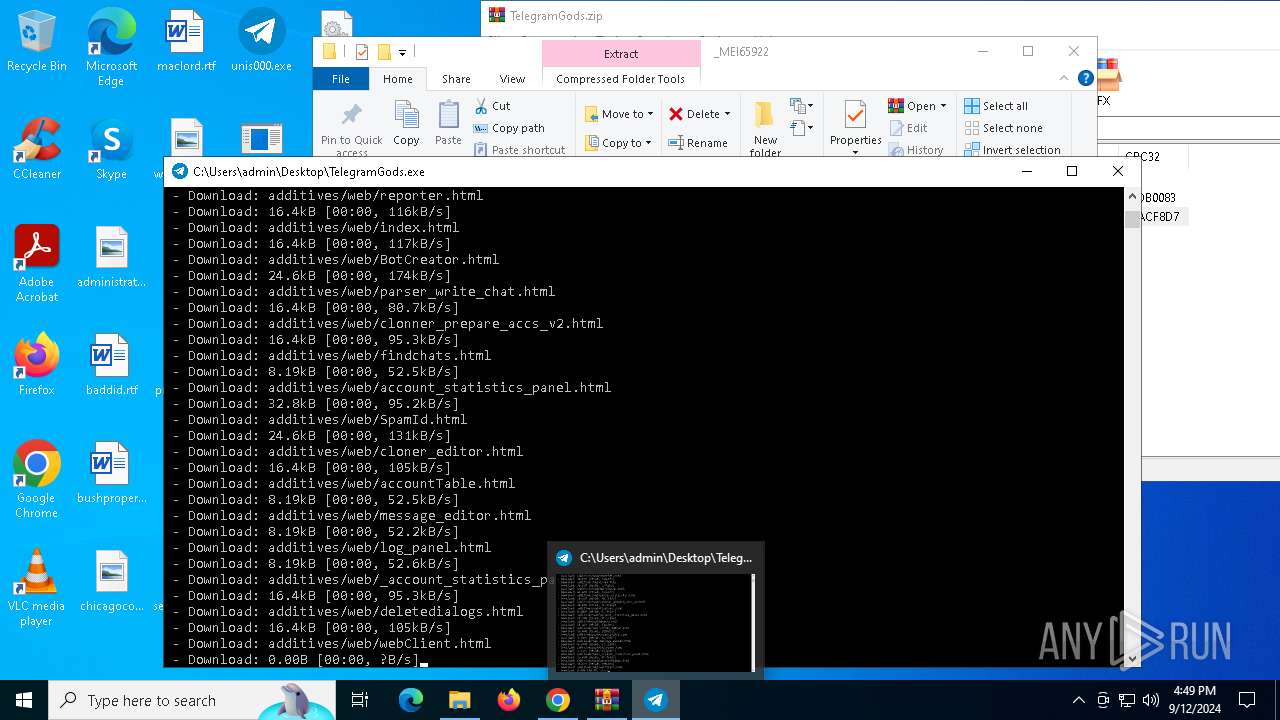
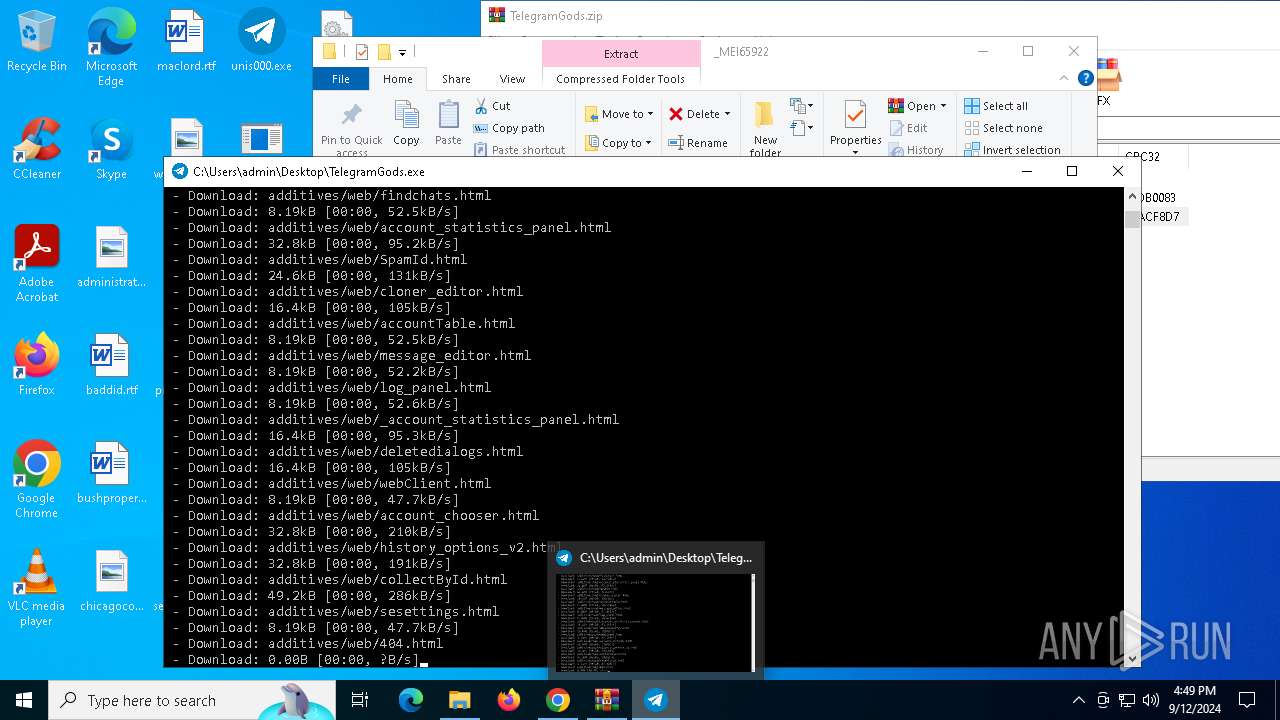
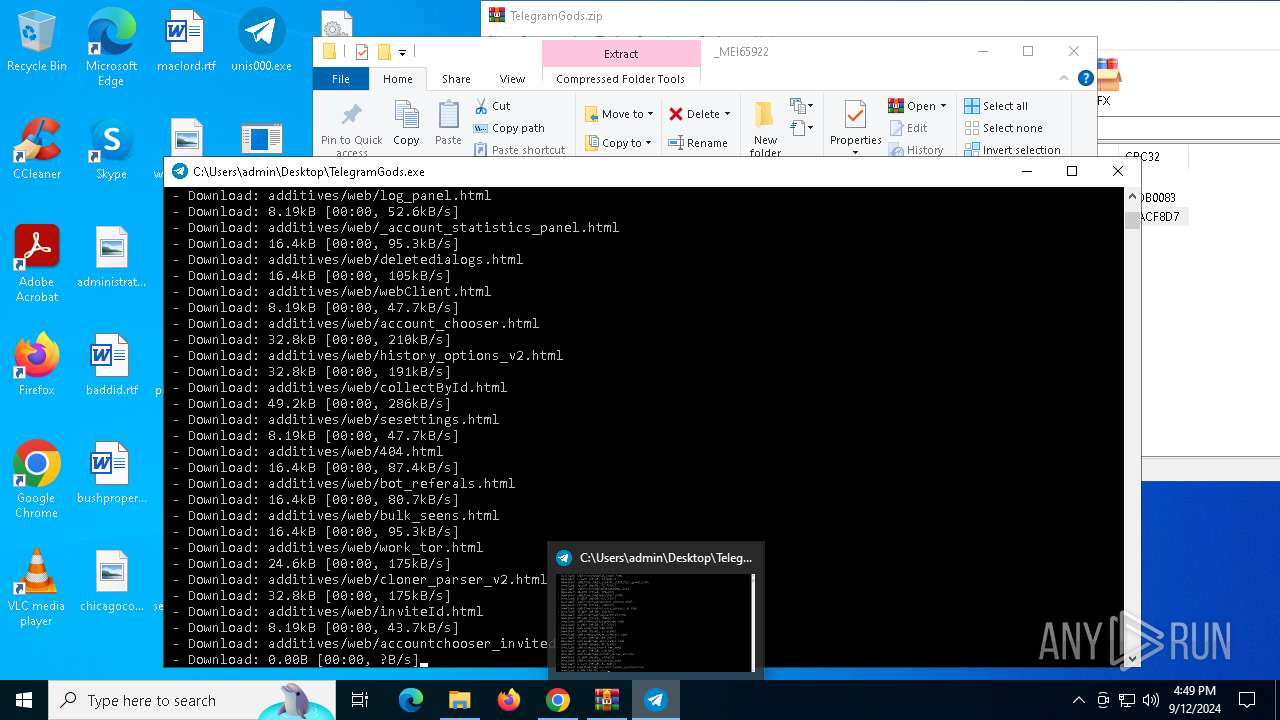
| URL: | http://telegram-soft.info/download/TelegramGods.zip |
| Full analysis: | https://app.any.run/tasks/3c26734d-8b7f-4bc2-ad07-fe45f9c60aea |
| Verdict: | Malicious activity |
| Analysis date: | September 12, 2024, 16:44:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D5ED7603FC080FEF14C4A70263D0C94B |
| SHA1: | AA056F84233E2AB0084F633461E43A04C88FD55B |
| SHA256: | B010D1CB557FF39868A0CBD25E6A4E909D13559D42A160C081DD07415F65606D |
| SSDEEP: | 3:N1KKA7YR4LxmGJX0KwU:CKzqX0RU |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- TelegramGods.exe (PID: 6592)
- TelegramGods.exe (PID: 4120)
Process drops legitimate windows executable
- TelegramGods.exe (PID: 6592)
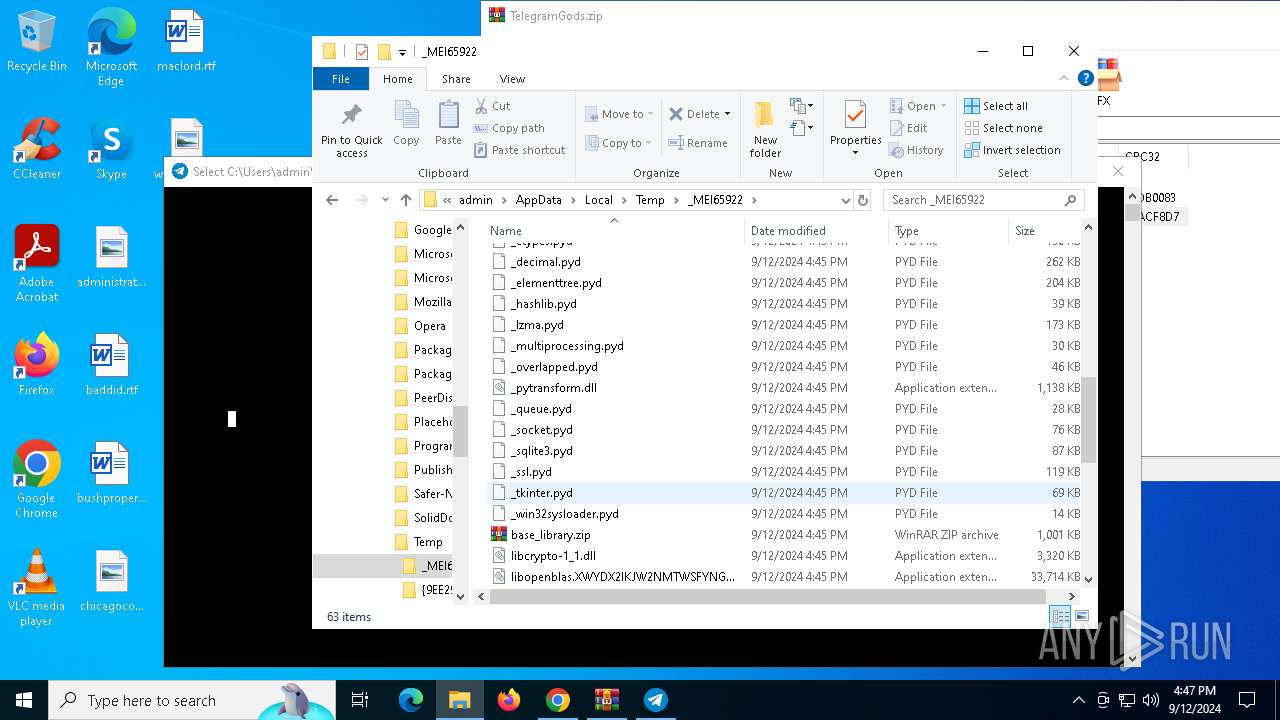
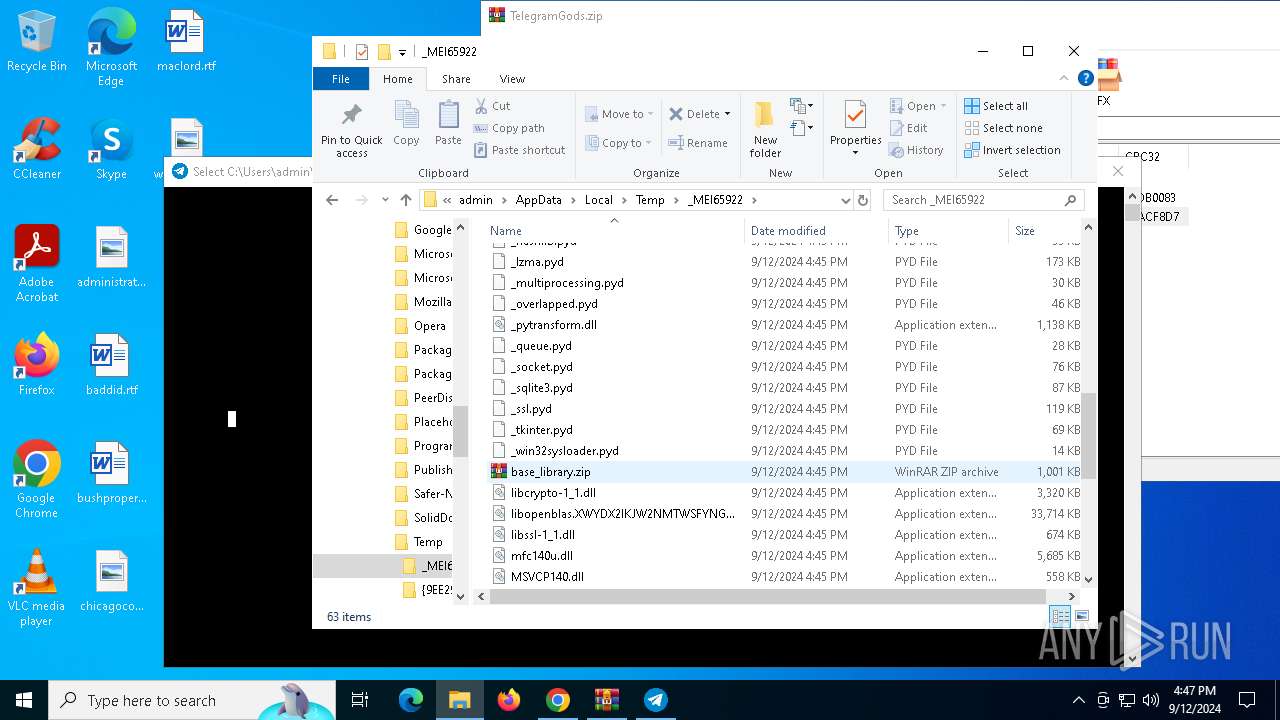
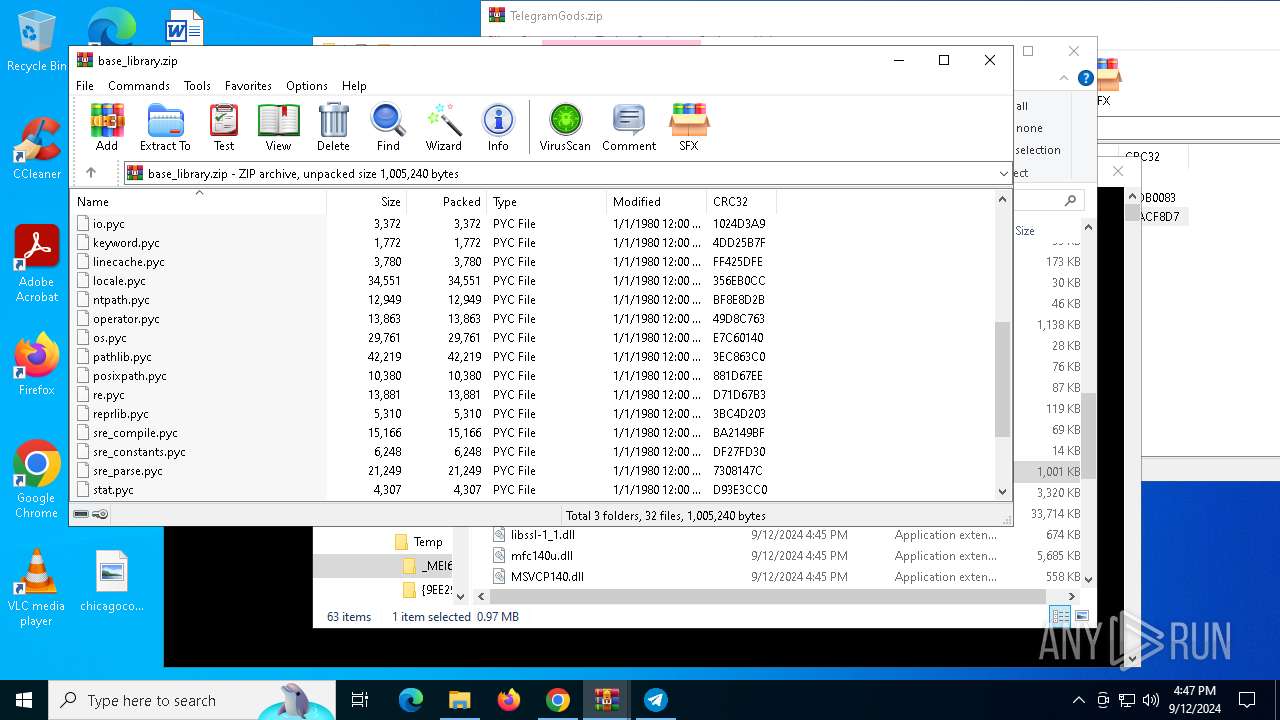
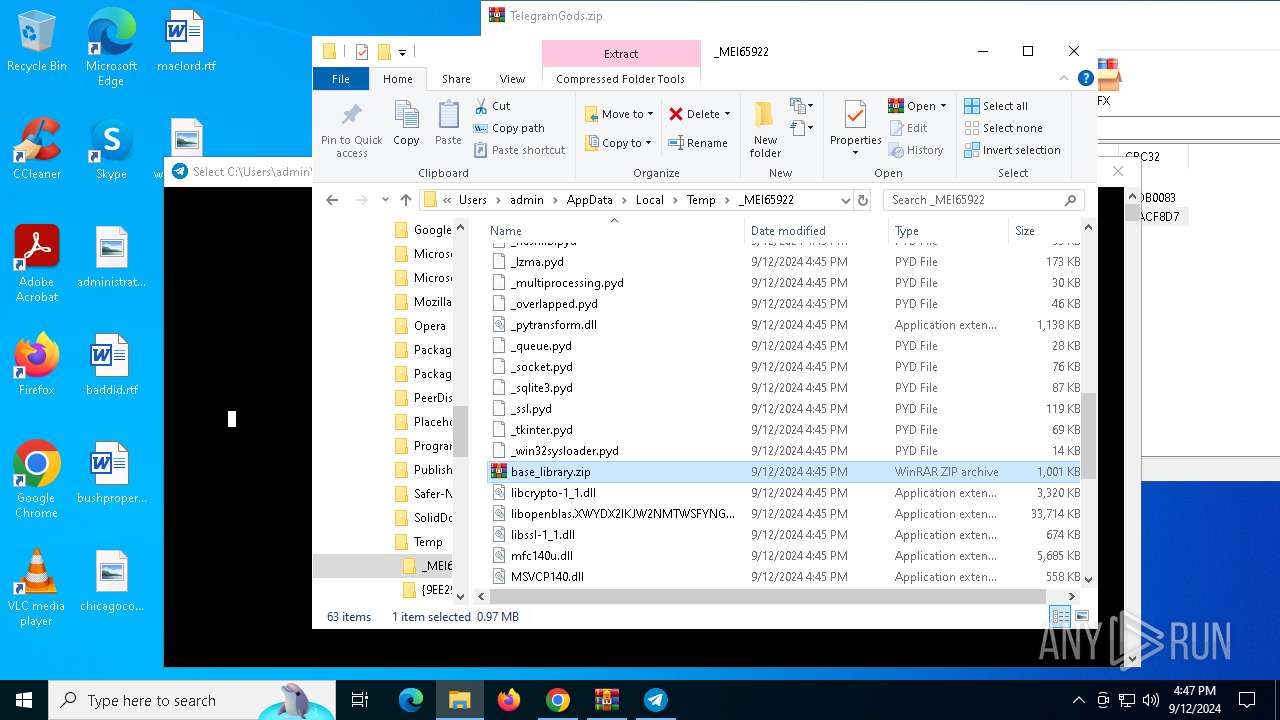
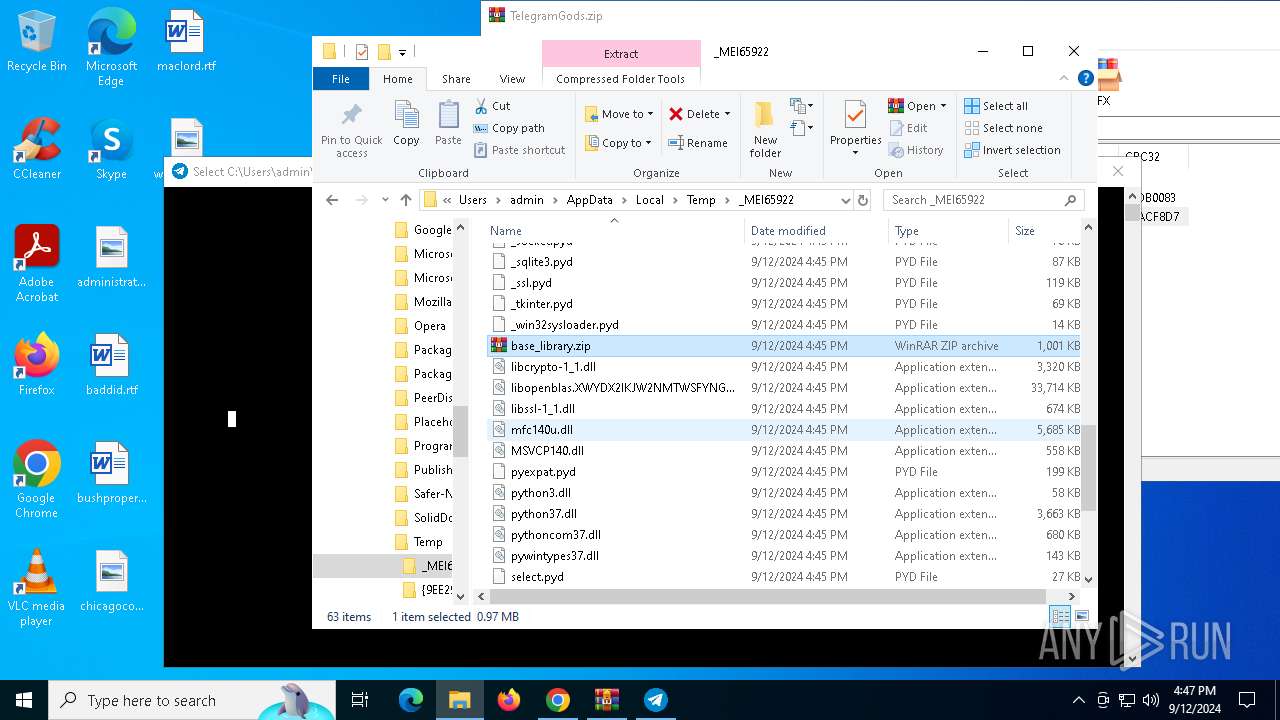
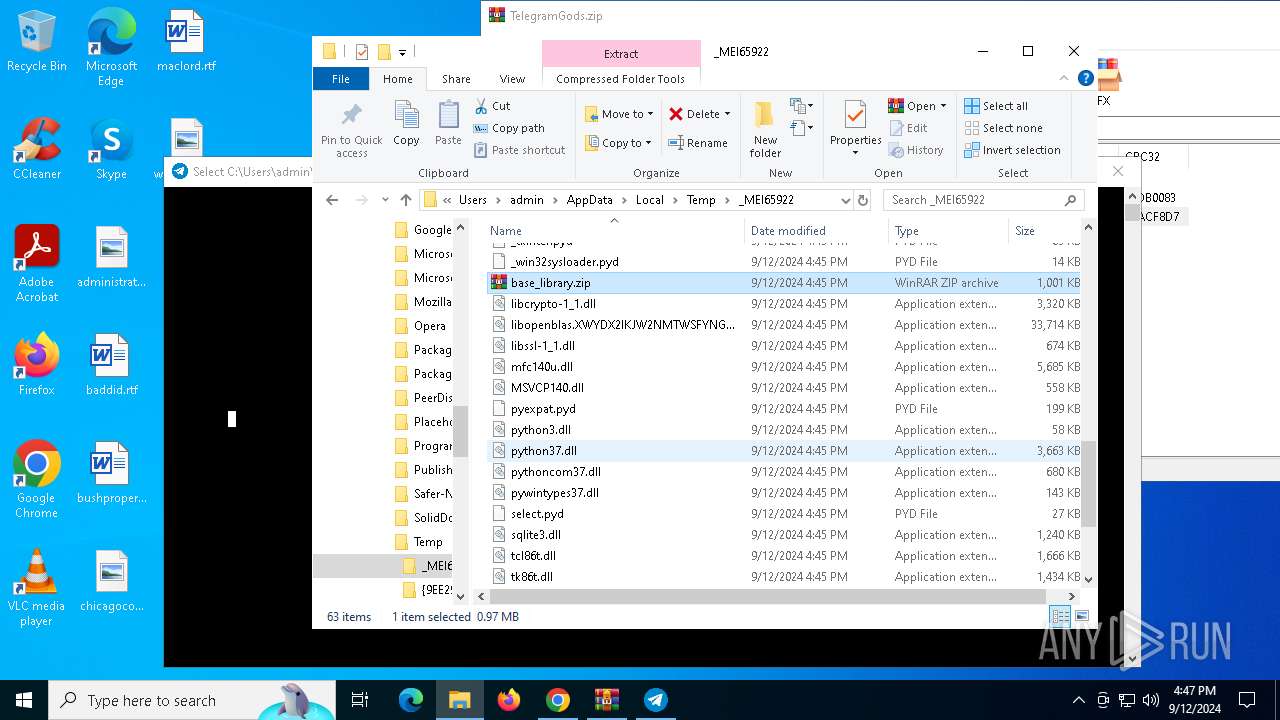
Process drops python dynamic module
- TelegramGods.exe (PID: 6592)
The process drops C-runtime libraries
- TelegramGods.exe (PID: 6592)
Loads Python modules
- TelegramGods.exe (PID: 4120)
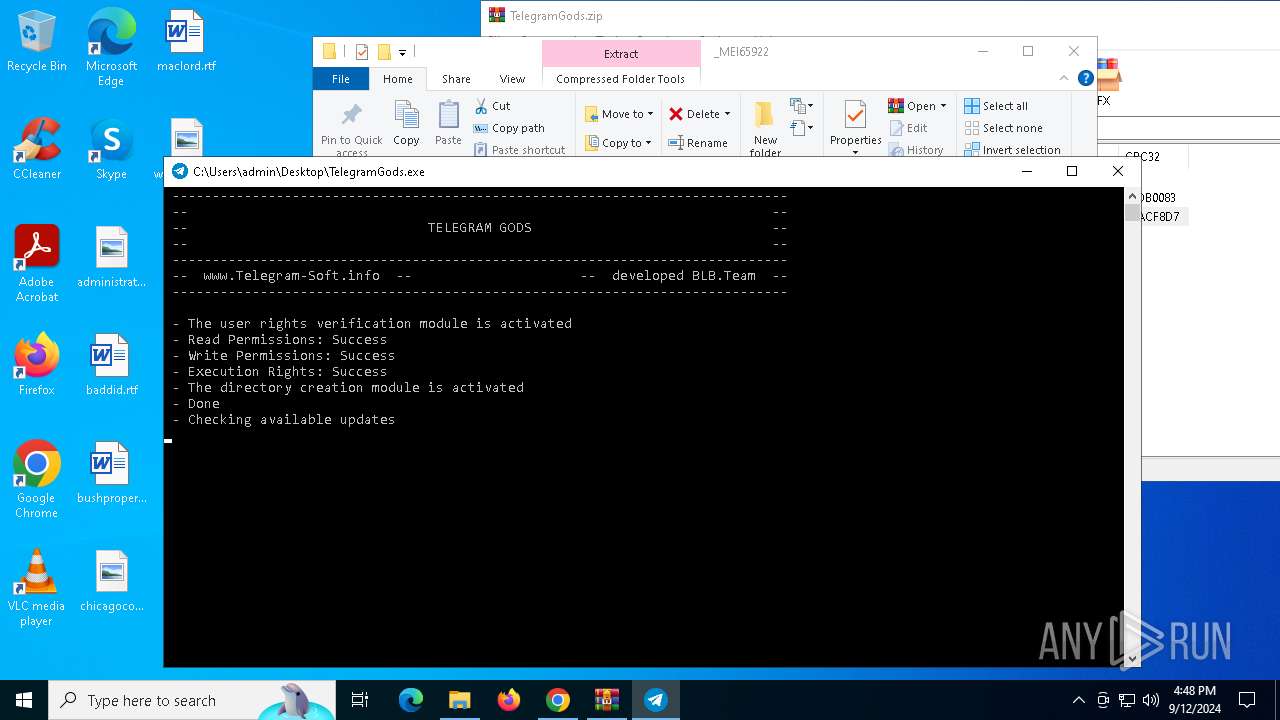
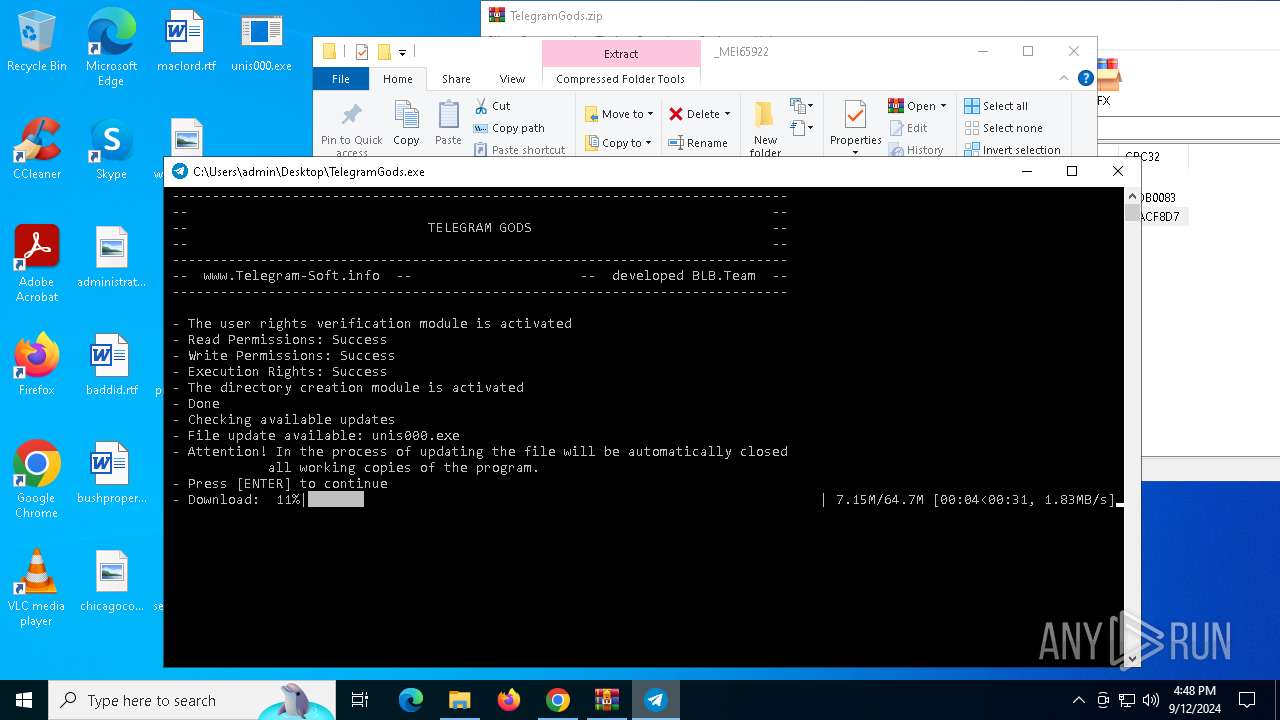
Application launched itself
- TelegramGods.exe (PID: 6592)
INFO
The process uses the downloaded file
- chrome.exe (PID: 6148)
- WinRAR.exe (PID: 7152)
- chrome.exe (PID: 6556)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6556)
Manual execution by a user
- TelegramGods.exe (PID: 6592)
- WinRAR.exe (PID: 3540)
- Taskmgr.exe (PID: 5112)
- Taskmgr.exe (PID: 3004)
Checks supported languages
- TelegramGods.exe (PID: 6592)
- TelegramGods.exe (PID: 4120)
Reads the computer name
- TelegramGods.exe (PID: 6592)
- TelegramGods.exe (PID: 4120)
Create files in a temporary directory
- TelegramGods.exe (PID: 6592)
- TelegramGods.exe (PID: 4120)
PyInstaller has been detected (YARA)
- TelegramGods.exe (PID: 6592)
- TelegramGods.exe (PID: 4120)
Reads the software policy settings
- slui.exe (PID: 2040)
- slui.exe (PID: 6540)
Checks proxy server information
- slui.exe (PID: 6540)
- TelegramGods.exe (PID: 4120)
Reads the machine GUID from the registry
- TelegramGods.exe (PID: 4120)
Application launched itself
- chrome.exe (PID: 6556)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 3004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
170
Monitored processes
30
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5184 --field-trial-handle=1916,i,14904335507025283118,4396473329247743445,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2116 --field-trial-handle=1916,i,14904335507025283118,4396473329247743445,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1636 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4168 --field-trial-handle=1916,i,14904335507025283118,4396473329247743445,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5216 --field-trial-handle=1916,i,14904335507025283118,4396473329247743445,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5184 --field-trial-handle=1916,i,14904335507025283118,4396473329247743445,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2016 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=4208 --field-trial-handle=1916,i,14904335507025283118,4396473329247743445,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2040 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3956 --field-trial-handle=1916,i,14904335507025283118,4396473329247743445,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=836 --field-trial-handle=1916,i,14904335507025283118,4396473329247743445,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
328 544
Read events
328 494
Write events
43
Delete events
7
Modification events
| (PID) Process: | (6556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6556) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6148) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000001C692E1B3305DB01 | |||
| (PID) Process: | (6556) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\TelegramGods.zip | |||
| (PID) Process: | (7152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
172
Suspicious files
733
Text files
1 259
Unknown types
134
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12aade.TMP | — | |
MD5:— | SHA256:— | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12aade.TMP | — | |
MD5:— | SHA256:— | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF12aacf.TMP | text | |
MD5:139F545948FC1F10256A27E3C2CEF062 | SHA256:9399CC6F9C335015E086DB37208B1816A7831221A005B04AC83C4F86CC04230D | |||
| 6556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:A95974F48FC4A0E16E9D7729D7874157 | SHA256:926422473F59B7759EA8EB2064FD6DF9D00A88B548DEF1D5C3E08860357C03A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
174
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1064 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1140 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3568 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
6880 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1140 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3568 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
3568 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
3568 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
3568 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
3568 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6224 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6880 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1480 | chrome.exe | 142.250.153.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6556 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1480 | chrome.exe | 172.67.160.197:443 | telegram-soft.info | CLOUDFLARENET | US | unknown |
6556 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
6880 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6880 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
telegram-soft.info |
| unknown |
accounts.google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |