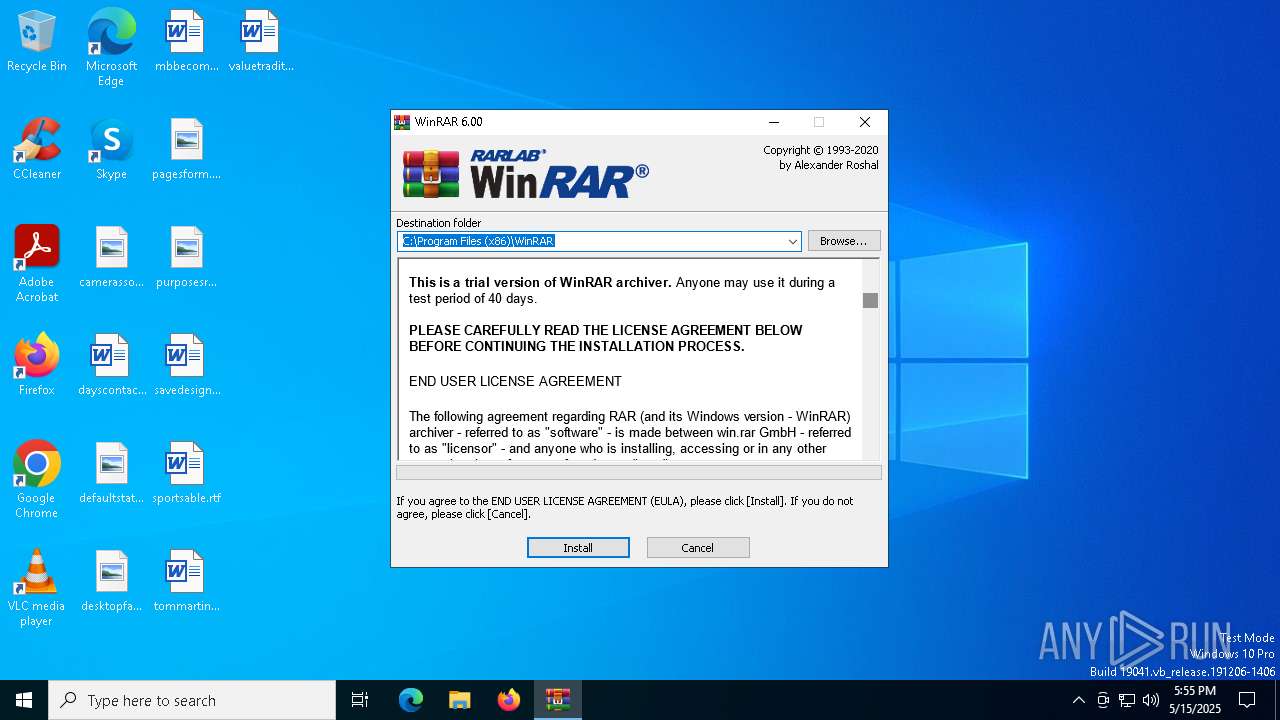
| File name: | winrar600.exe |
| Full analysis: | https://app.any.run/tasks/9af67c1c-43db-423f-ad89-d68638ce20d5 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 17:55:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | C74862E16BCC2B0E02CADB7AB14E3CD6 |
| SHA1: | 6569AA87D28DB836D7D3380B32A83654F3E909CF |
| SHA256: | AFF4BB9B15BCCFF67A112A7857D28D3F2F436E2E42F11BE14930FE496269D573 |
| SSDEEP: | 49152:5NUOBfJXA+Nwb7rbmRgHWoHB9F4QNdmXYKqFuevCenXBEjWjtiSvcC19BNFZ9JXj:PUOBfKzLHHBbXiIKqQeaeXFt9vTjB3bN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- winrar600.exe (PID: 1132)
Reads Microsoft Outlook installation path
- winrar600.exe (PID: 1132)
There is functionality for taking screenshot (YARA)
- winrar600.exe (PID: 1132)
Reads Internet Explorer settings
- winrar600.exe (PID: 1132)
Executable content was dropped or overwritten
- winrar600.exe (PID: 1132)
Drops 7-zip archiver for unpacking
- winrar600.exe (PID: 1132)
INFO
The sample compiled with english language support
- winrar600.exe (PID: 1132)
Checks supported languages
- winrar600.exe (PID: 1132)
- Uninstall.exe (PID: 6724)
Reads the computer name
- winrar600.exe (PID: 1132)
- Uninstall.exe (PID: 6724)
Creates files in the program directory
- winrar600.exe (PID: 1132)
Checks proxy server information
- winrar600.exe (PID: 1132)
The sample compiled with russian language support
- winrar600.exe (PID: 1132)
Process checks computer location settings
- winrar600.exe (PID: 1132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:12:01 18:01:08+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 199168 |
| InitializedDataSize: | 352256 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e4d0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.0.0 |
| ProductVersionNumber: | 6.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| ProductName: | WinRAR |
| CompanyName: | Alexander Roshal |
| FileDescription: | WinRAR archiver |
| FileVersion: | 6.0.0 |
| ProductVersion: | 6.0.0 |
| InternalName: | WinRAR |
| LegalCopyright: | Copyright © Alexander Roshal 1993-2020 |
| OriginalFileName: | WinRAR.exe |
Total processes
133
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1132 | "C:\Users\admin\AppData\Local\Temp\winrar600.exe" | C:\Users\admin\AppData\Local\Temp\winrar600.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: WinRAR archiver Exit code: 0 Version: 6.0.0 Modules
| |||||||||||||||
| 4688 | "C:\Users\admin\AppData\Local\Temp\winrar600.exe" | C:\Users\admin\AppData\Local\Temp\winrar600.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 3221226540 Version: 6.0.0 Modules
| |||||||||||||||
| 5776 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6040 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6724 | "C:\Program Files (x86)\WinRAR\uninstall.exe" /setup | C:\Program Files (x86)\WinRAR\Uninstall.exe | — | winrar600.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: Uninstall WinRAR Version: 6.0.0 Modules
| |||||||||||||||
Total events
995
Read events
989
Write events
4
Delete events
2
Modification events
| (PID) Process: | (1132) winrar600.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1132) winrar600.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1132) winrar600.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1132) winrar600.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%Program Files (x86)%WinRAR |
Value: C:\Program Files (x86)\WinRAR | |||
| (PID) Process: | (1132) winrar600.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFavoritesInitialSelection |
Value: | |||
| (PID) Process: | (1132) winrar600.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\LowRegistry |
| Operation: | delete value | Name: | AddToFeedsInitialSelection |
Value: | |||
Executable files
10
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\Uninstall.lst | text | |
MD5:34BE8F16B04C175C40630A92D40F82E6 | SHA256:7CD94B59159B6C353E4F50F8AE26D4D8DF6AE7405CA0B68914E89FEA1C5183F5 | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\RarFiles.lst | text | |
MD5:08EA0309D72A874C182F08CBF9DA2CC3 | SHA256:12787F8204EEDB0B8BDABF5D68D557334FDDB2D70B46E1422510713DDA5E6A01 | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\UnRAR.exe | executable | |
MD5:032CEBEFCF143444894B57DE27567B29 | SHA256:E13A75A2936DB0E8BE3C5B72D19E0E9C6AB27BC37933490E2D847E189DBCA5EF | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\Rar.txt | text | |
MD5:A2CEBFD18B8B97FC0B18DB95D9364CA1 | SHA256:F3CCF2F7A7981A09B5AD75302D33CAD253394FCC344EDC8FDB59C2E66D405930 | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\Uninstall.exe | executable | |
MD5:54EBBA23AF8EA3562C143B6F9A2E0BC1 | SHA256:A434EF5347FA047E6EB21E0C00E689BDC88F3C715281C9C2AFB0EC1A46578586 | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\7zxa.dll | executable | |
MD5:786D4C74C05832A652BE5C0A559BE1E6 | SHA256:D0680AC62E94F953DF031533ACD0ACB718AD8494F938D84198C655507709E5DF | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\Rar.exe | executable | |
MD5:EB24024A8A46C71303E0B18D0E1859F6 | SHA256:770D7B5E40ED9B0AFF5D0E3FC2CCF9BA10D4925D3441F38B71A35BD26E6E8D98 | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\RarExt64.dll | executable | |
MD5:76A5F50D92F543E566B0152E0BE1CF9E | SHA256:DB28575F61B1ADC88A28AE51CE3B00226E4974CA60894896E414EA408C6FF9FE | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\RarExt.dll | executable | |
MD5:E3E09BA1CCA853535CAD6900133D819E | SHA256:35A21F1AEBF8EA0AB9BE1814131FEC1FA079D91B701E505054B69ECCBDFD0732 | |||
| 1132 | winrar600.exe | C:\Program Files (x86)\WinRAR\ReadMe.txt | text | |
MD5:FE2CEEB51614CD1832E929BC14914BF8 | SHA256:522337528299E460F5D742D54D17286D0D92DAF0D5B49204777BC32040455CB6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |