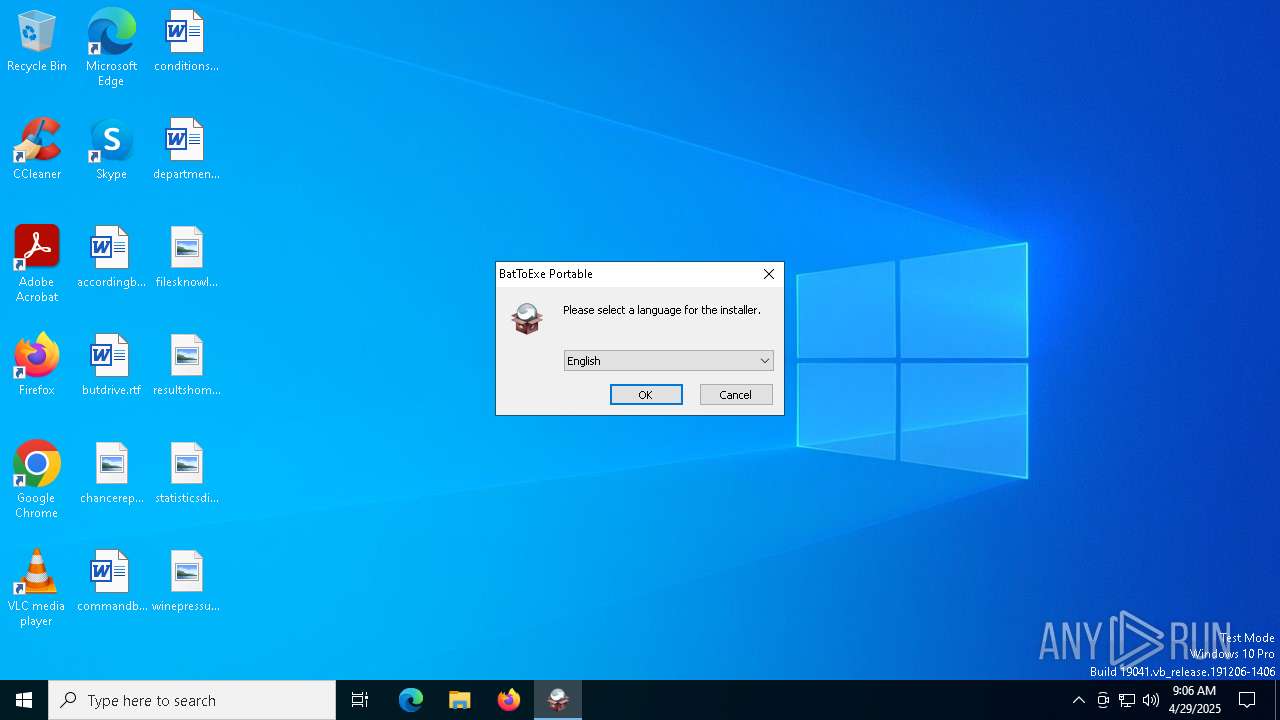
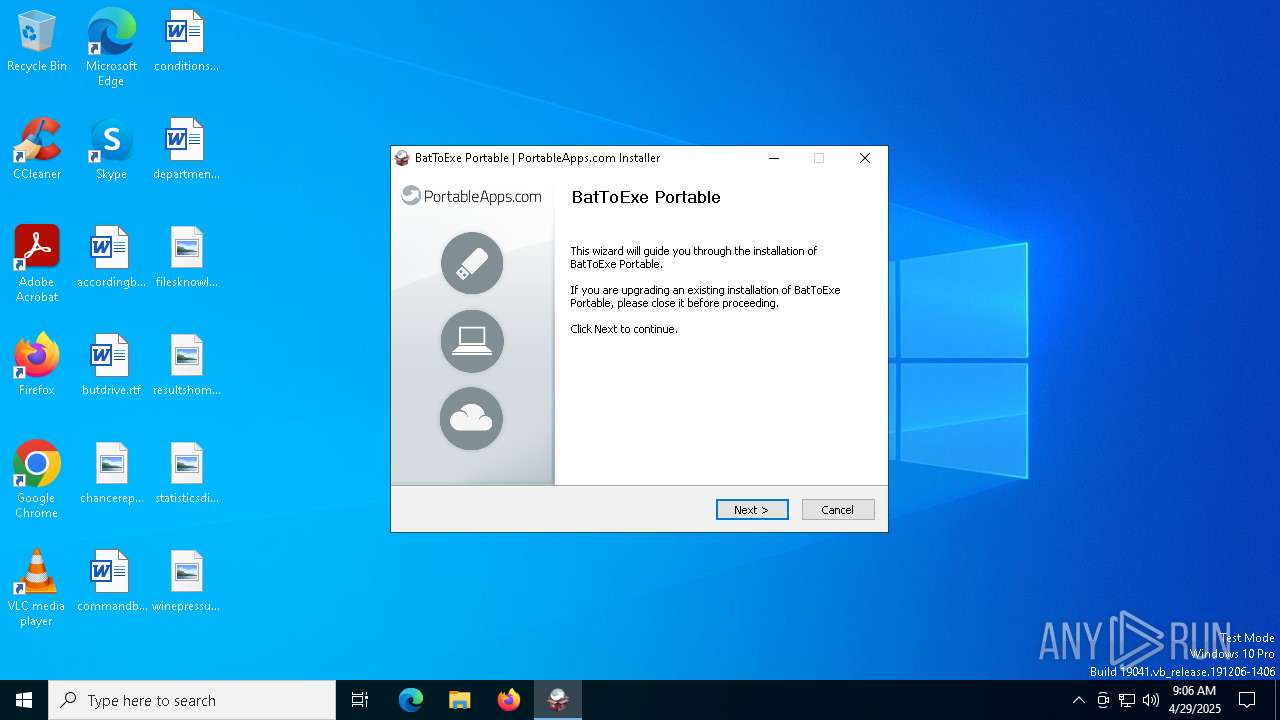
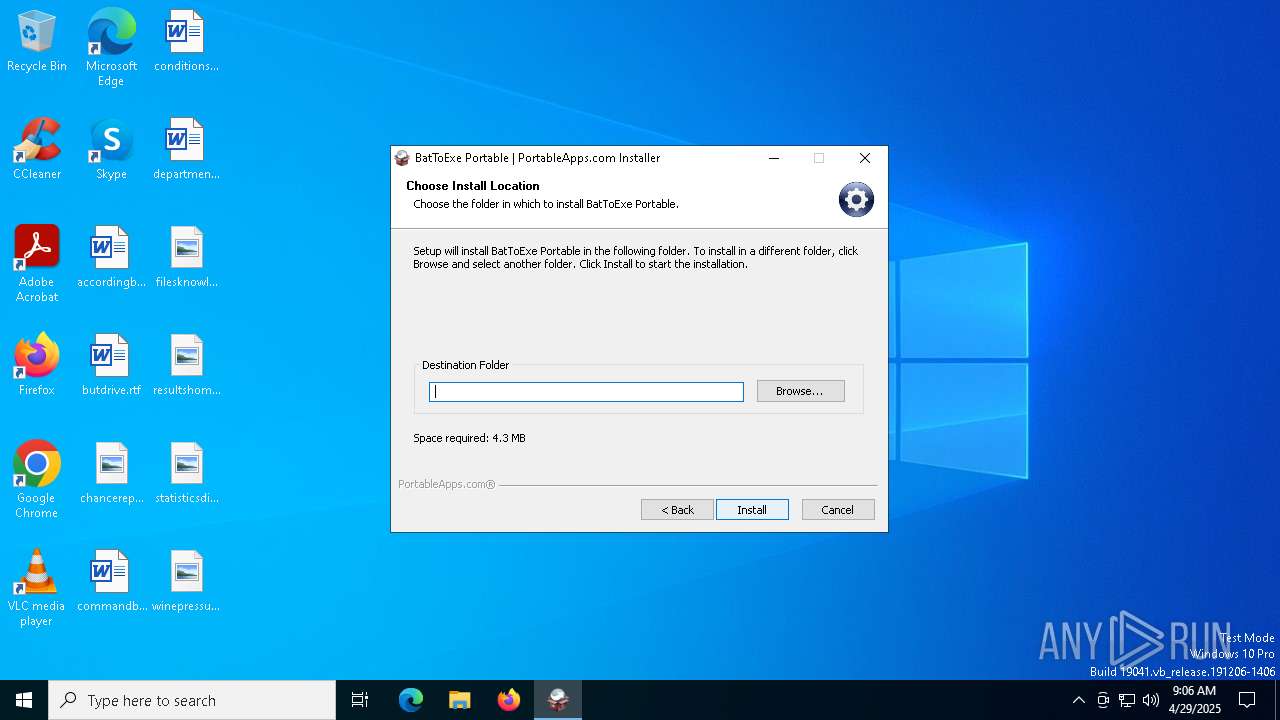
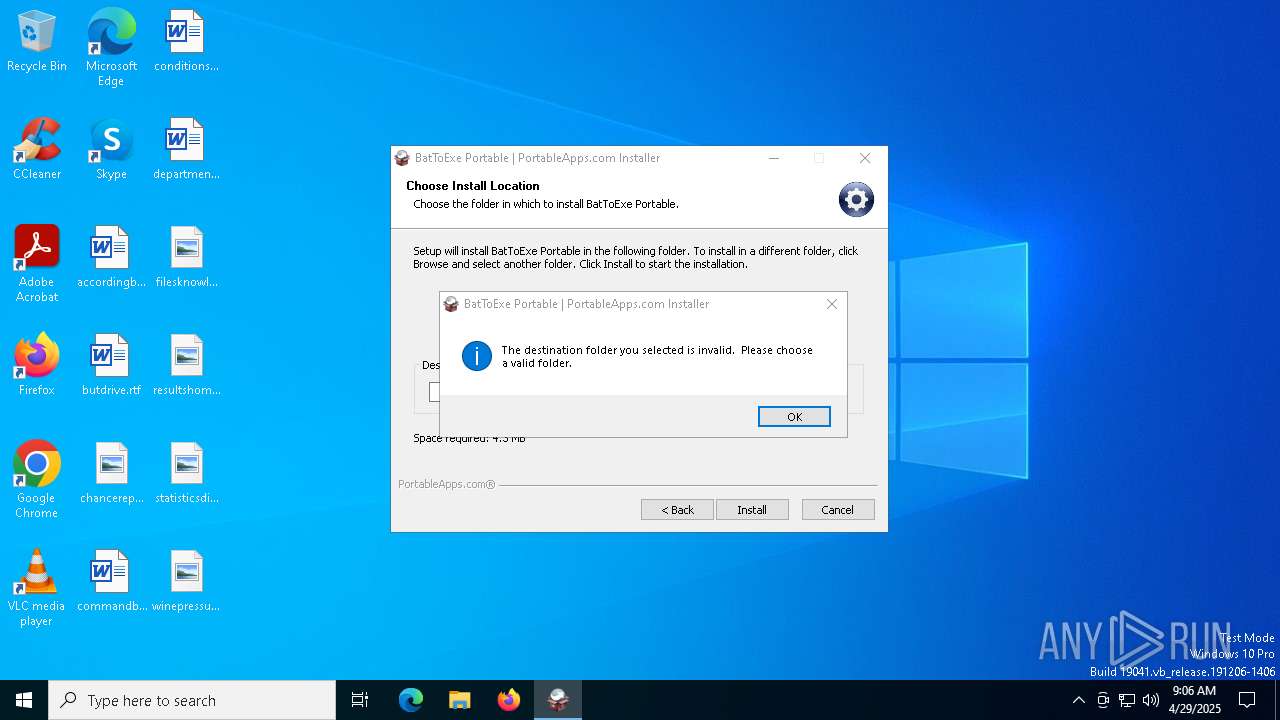
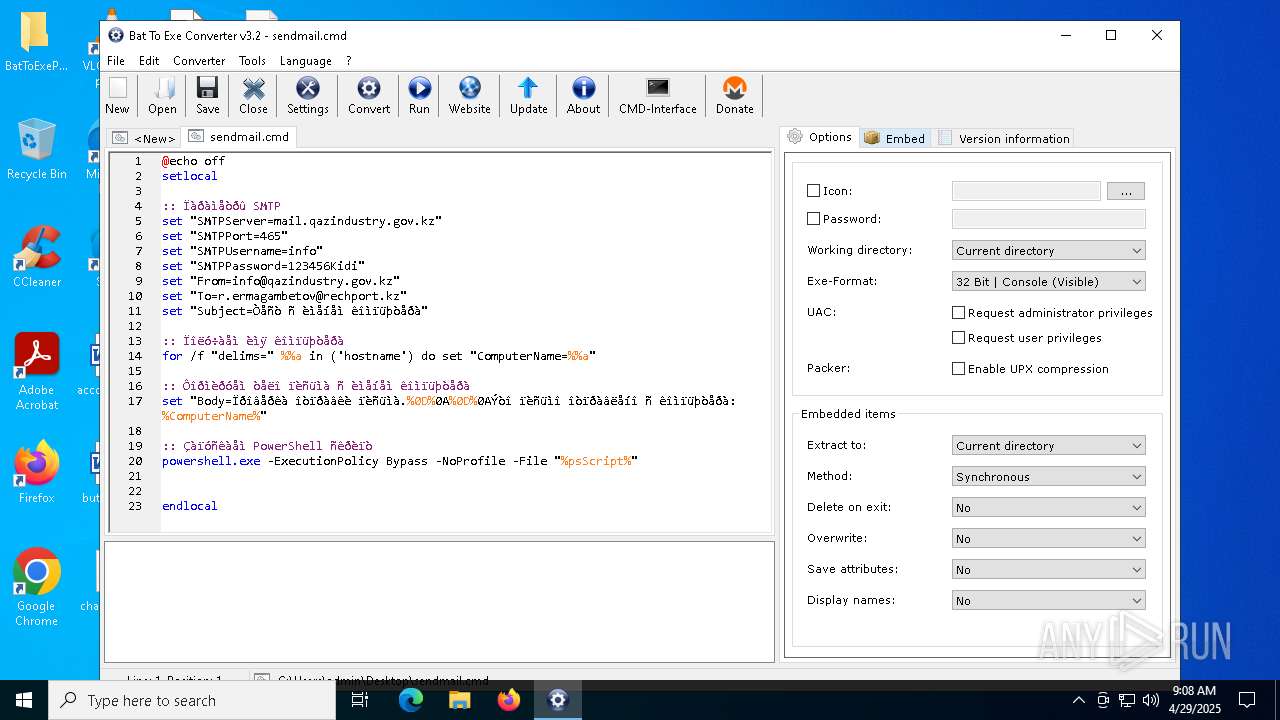
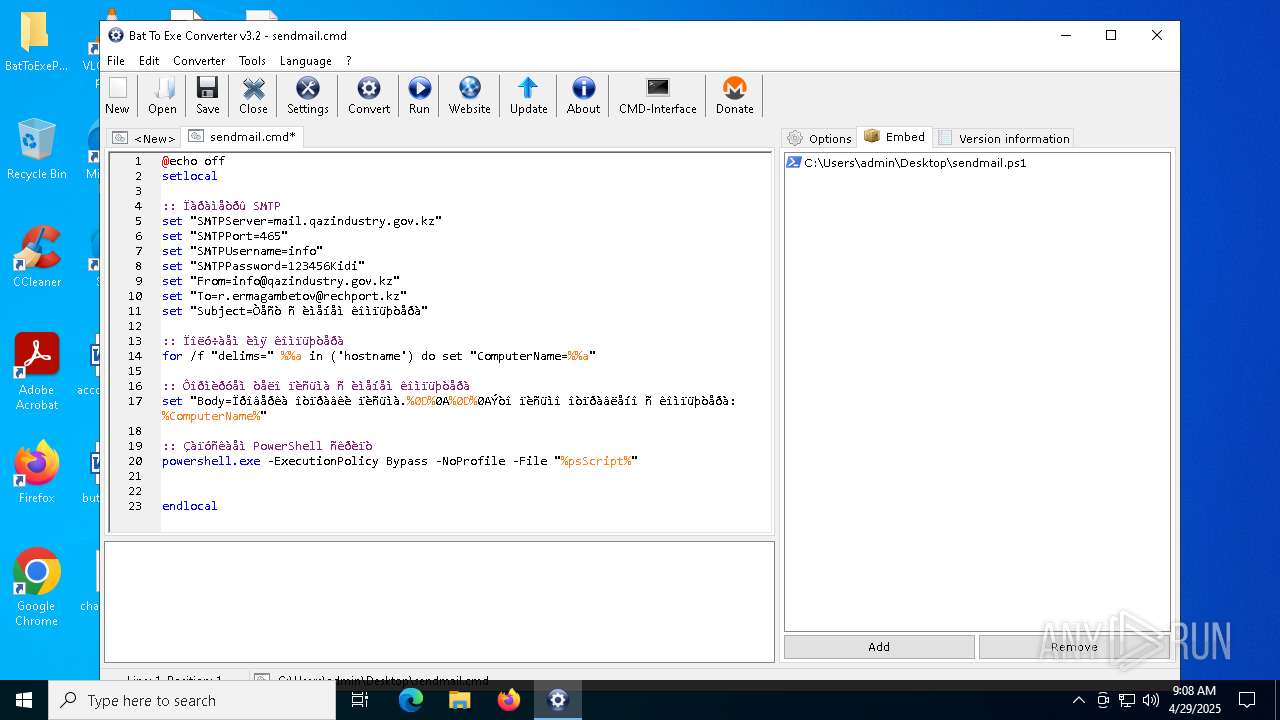
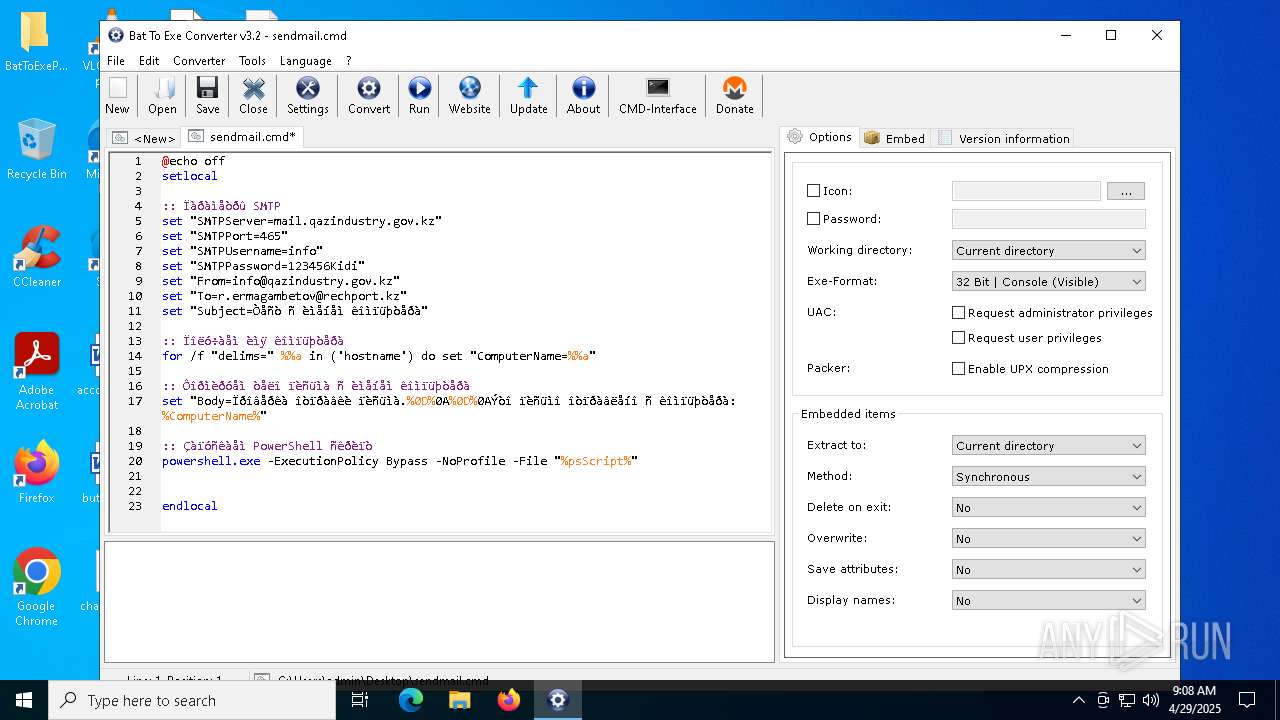
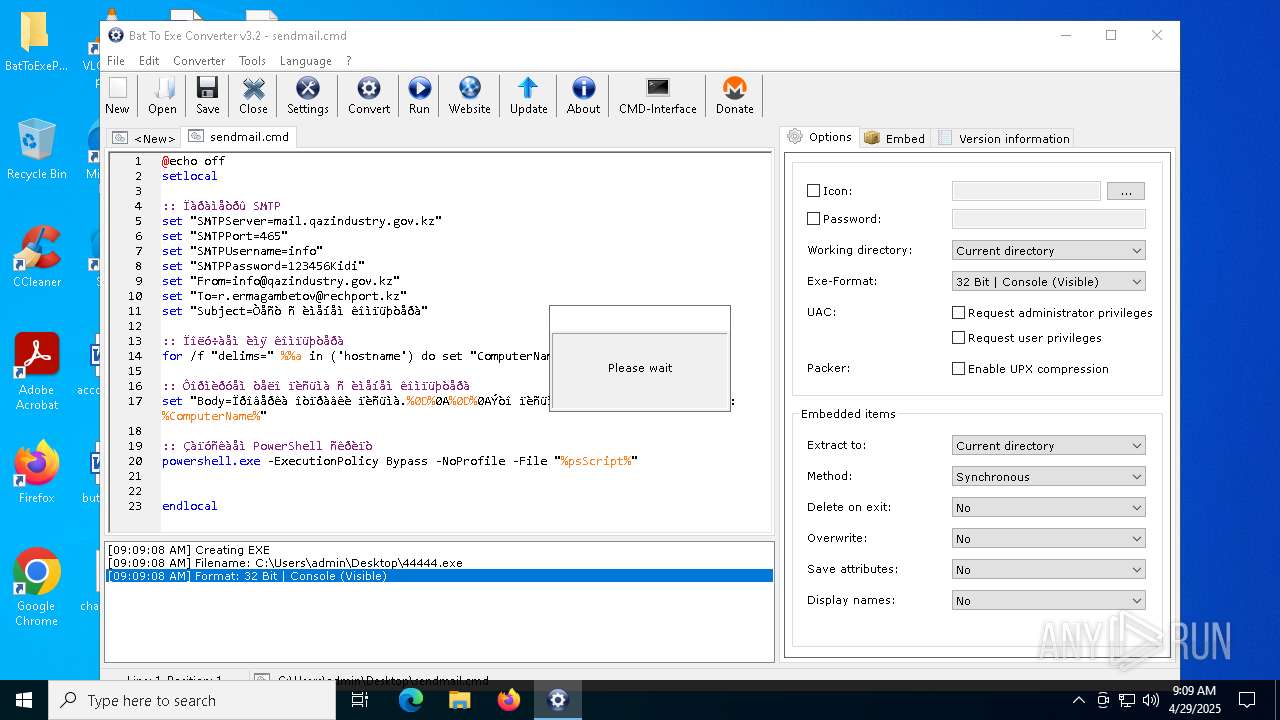
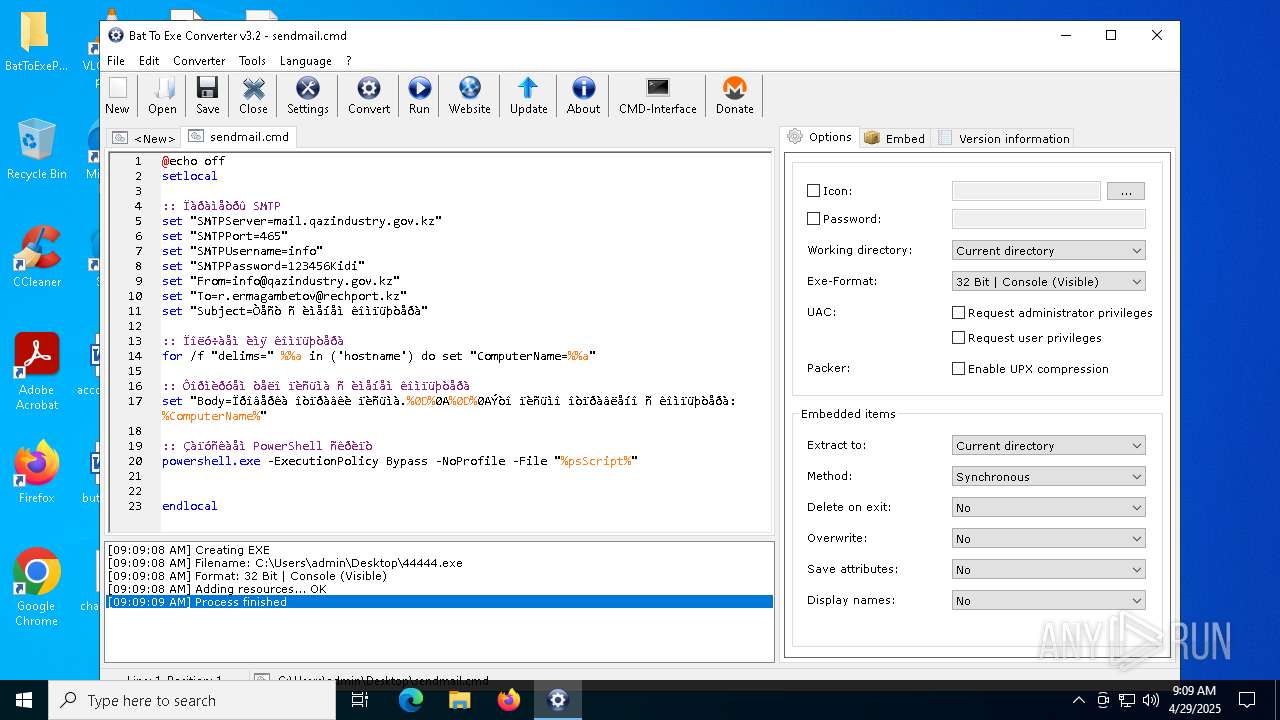
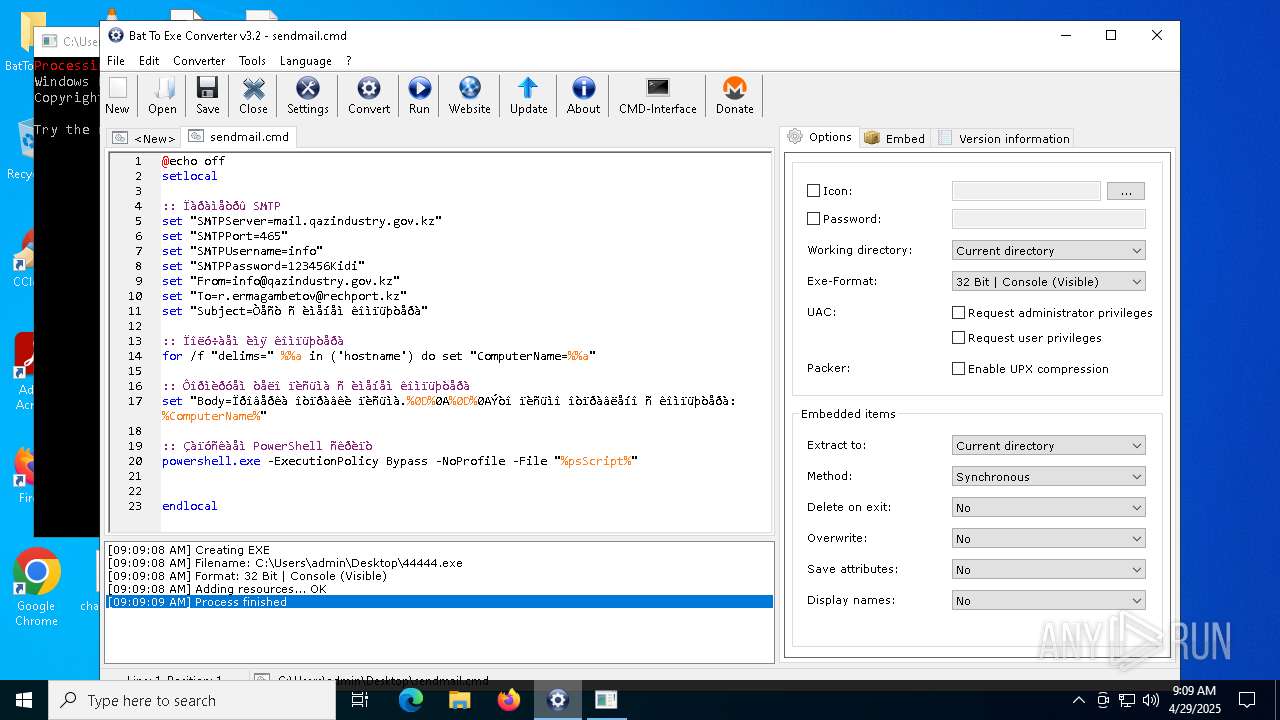
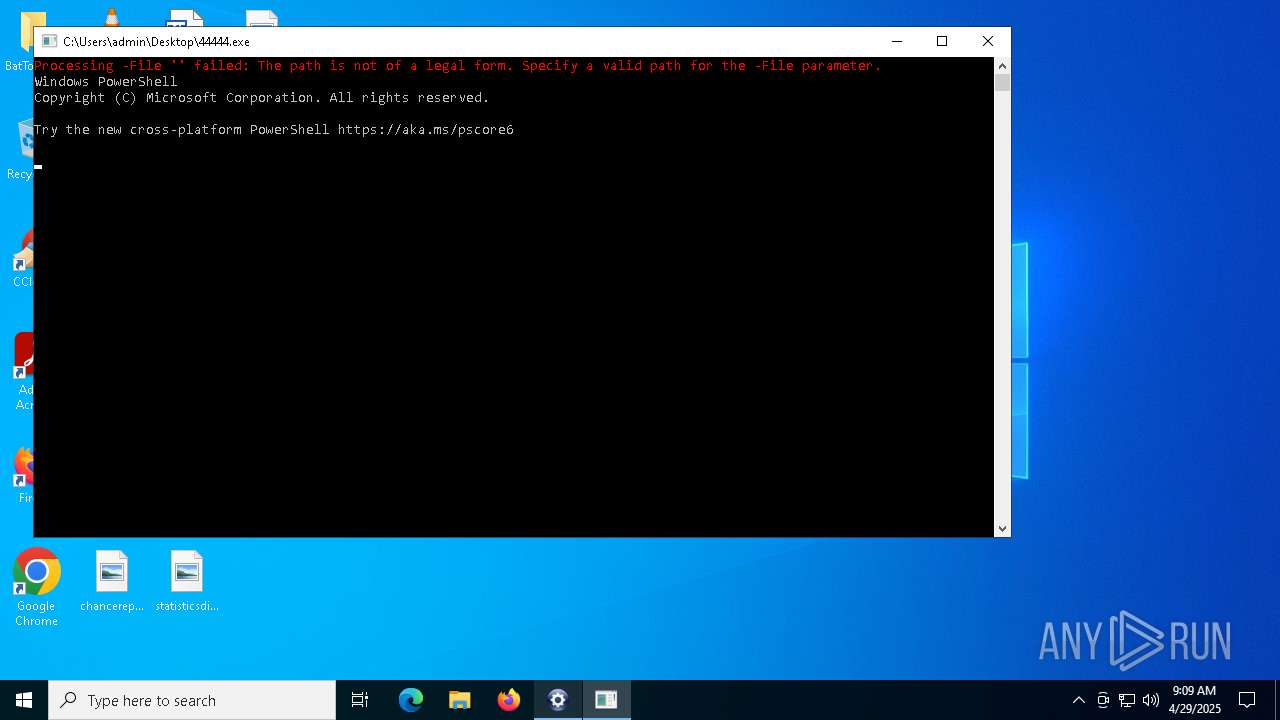
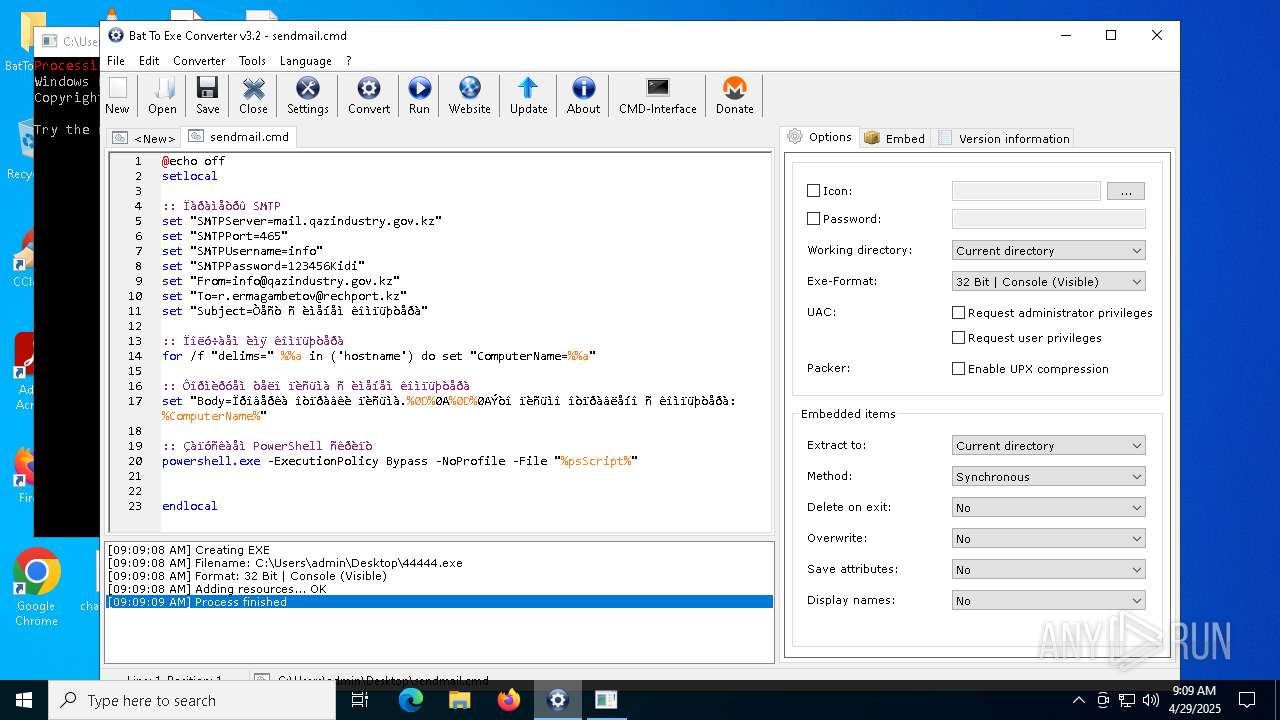
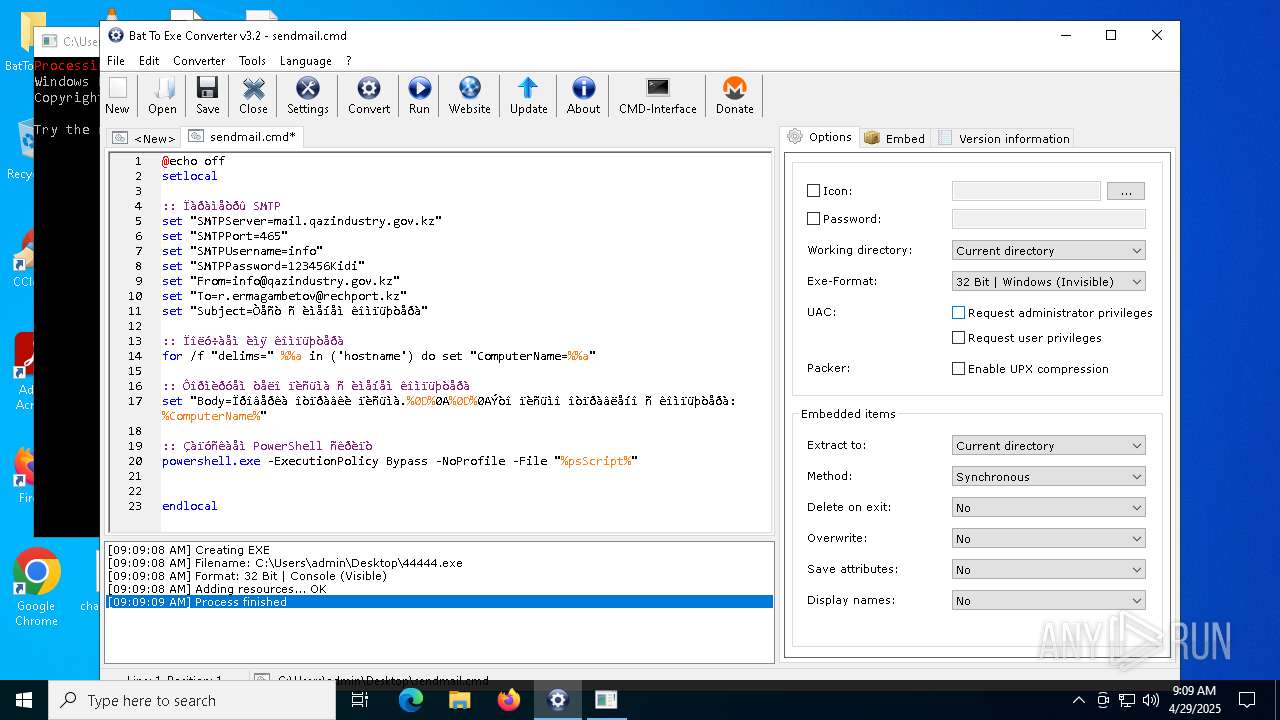
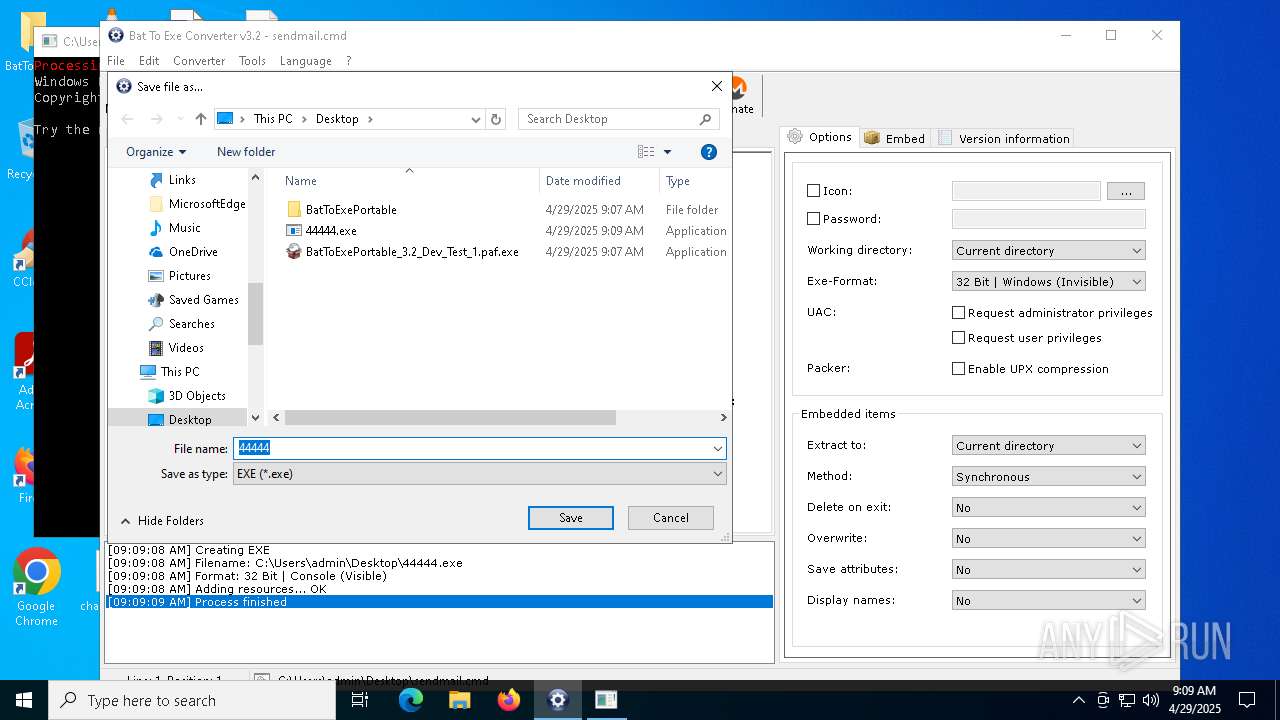
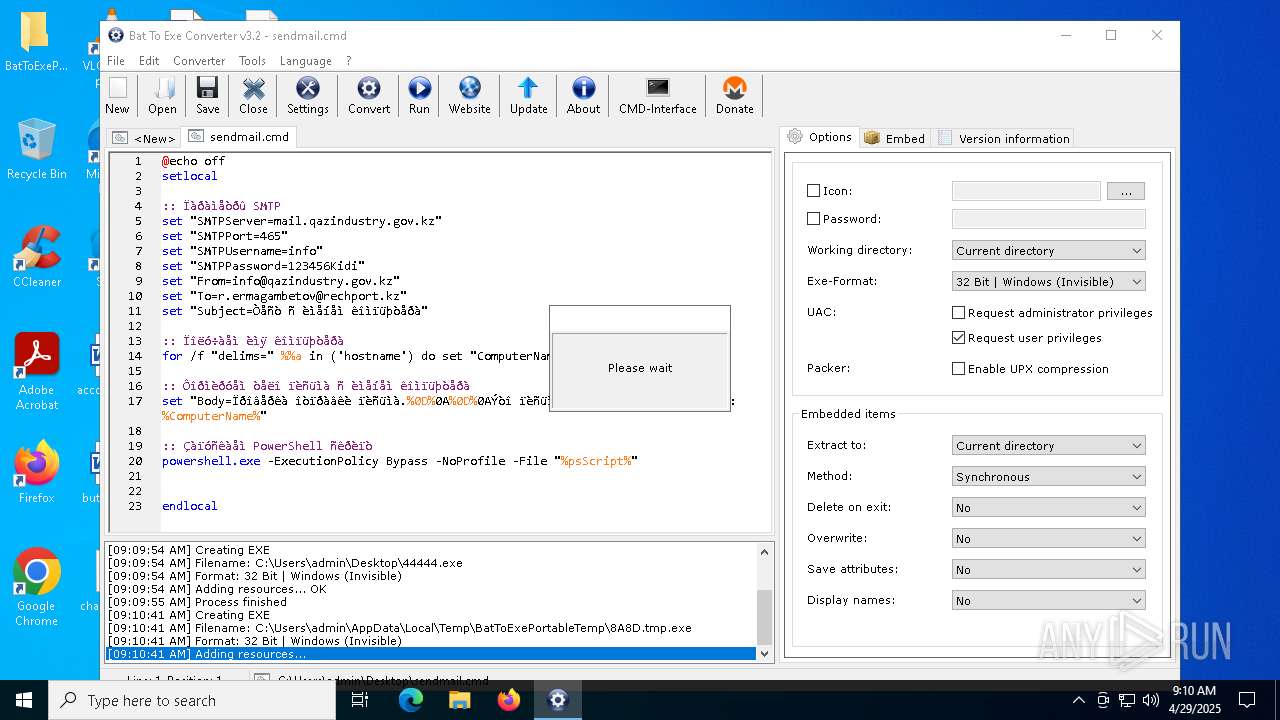
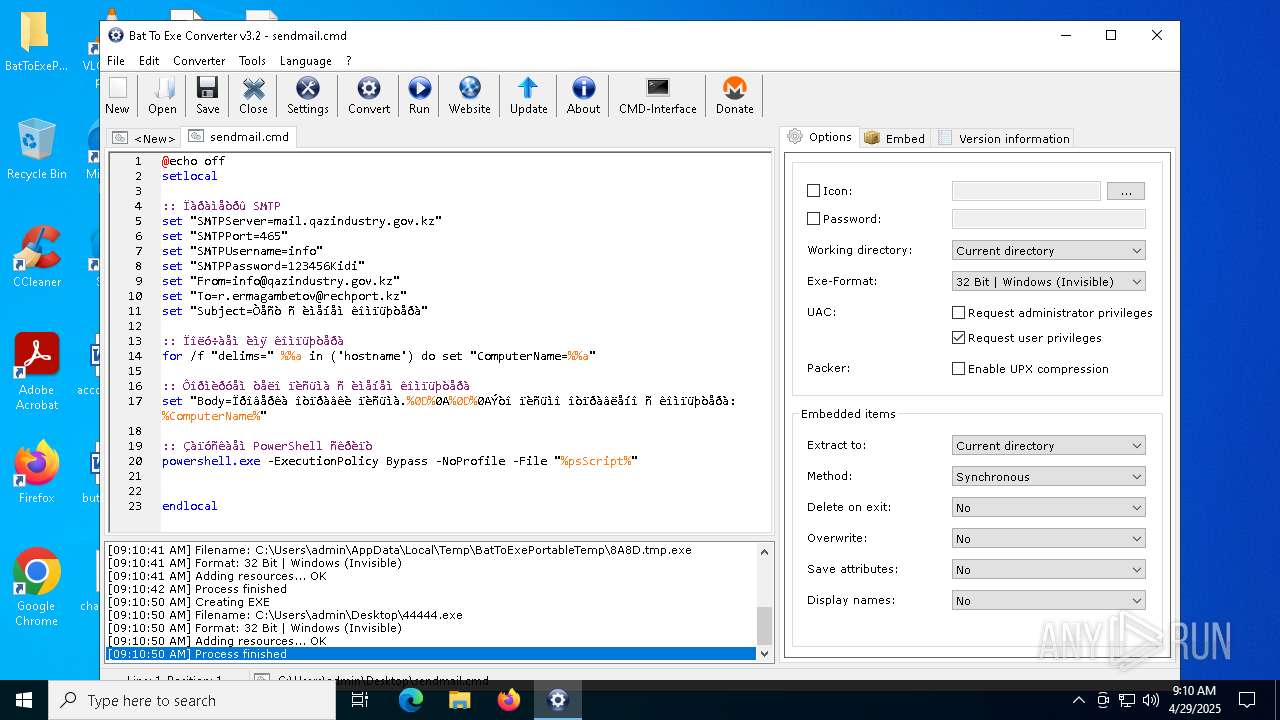
| File name: | BatToExePortable_3.2_Dev_Test_1.paf.exe |
| Full analysis: | https://app.any.run/tasks/9fe53a5c-38ae-4b44-99a1-85a2b2a89165 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 09:06:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 9A35E910967475490CA24631C07DDD48 |
| SHA1: | 227F582DD642F79B6E34F629155EBD057F55A4A3 |
| SHA256: | AFF48C00FD4C805239E920934640B5DB8A532E2EADC92A4409862B8D024D9686 |
| SSDEEP: | 98304:1aX8S9BQfj5XtqrAc+2FbVsI1bEFtygX6lZ3ADO/mfziDCGQIC95bMkpQ/sFMlIq:GhxT7Y7ub |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 5596)
- powershell.exe (PID: 5244)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 4112)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 976)
- cmd.exe (PID: 6416)
SUSPICIOUS
Executable content was dropped or overwritten
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 4892)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 5384)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
- BatToExePortable.exe (PID: 4268)
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
The process creates files with name similar to system file names
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 4892)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 5384)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
- BatToExePortable.exe (PID: 4268)
There is functionality for taking screenshot (YARA)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 4892)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
- BatToExePortable.exe (PID: 4268)
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
Malware-specific behavior (creating "System.dll" in Temp)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 4892)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 5384)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
- BatToExePortable.exe (PID: 4268)
Creates file in the systems drive root
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
Reads security settings of Internet Explorer
- BatToExePortable.exe (PID: 4268)
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
- 8A8D.tmp.exe (PID: 3828)
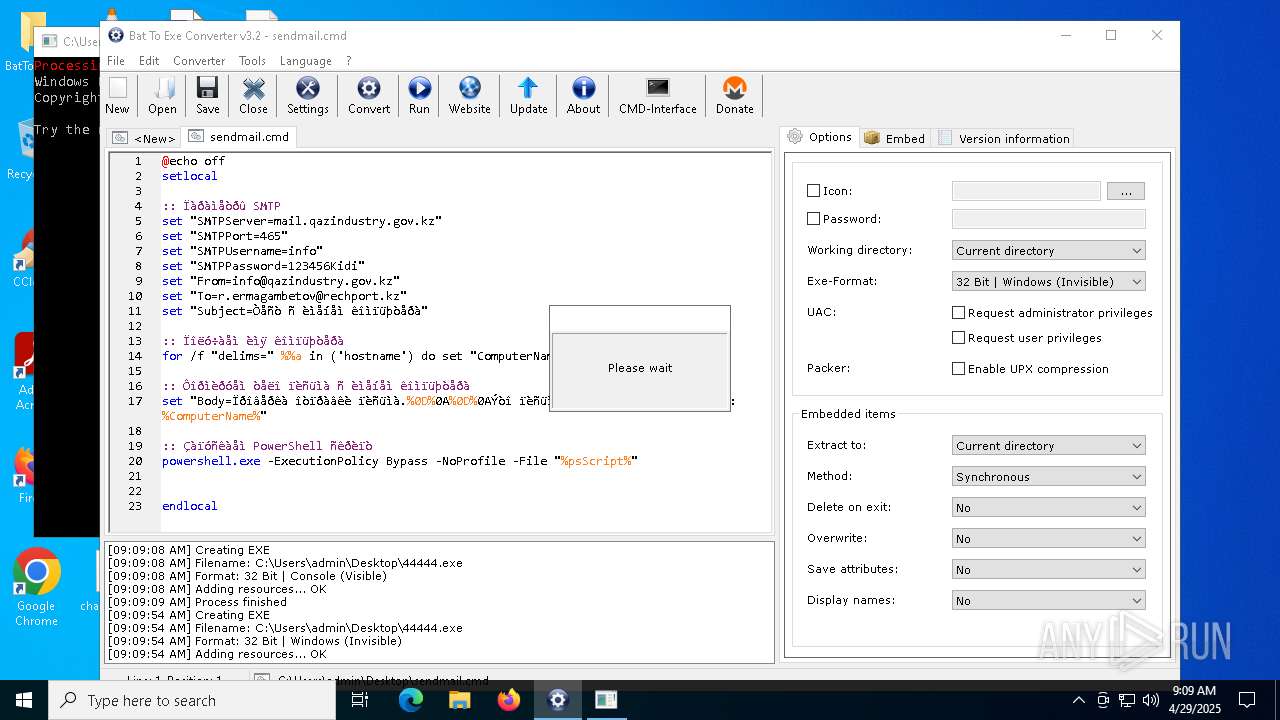
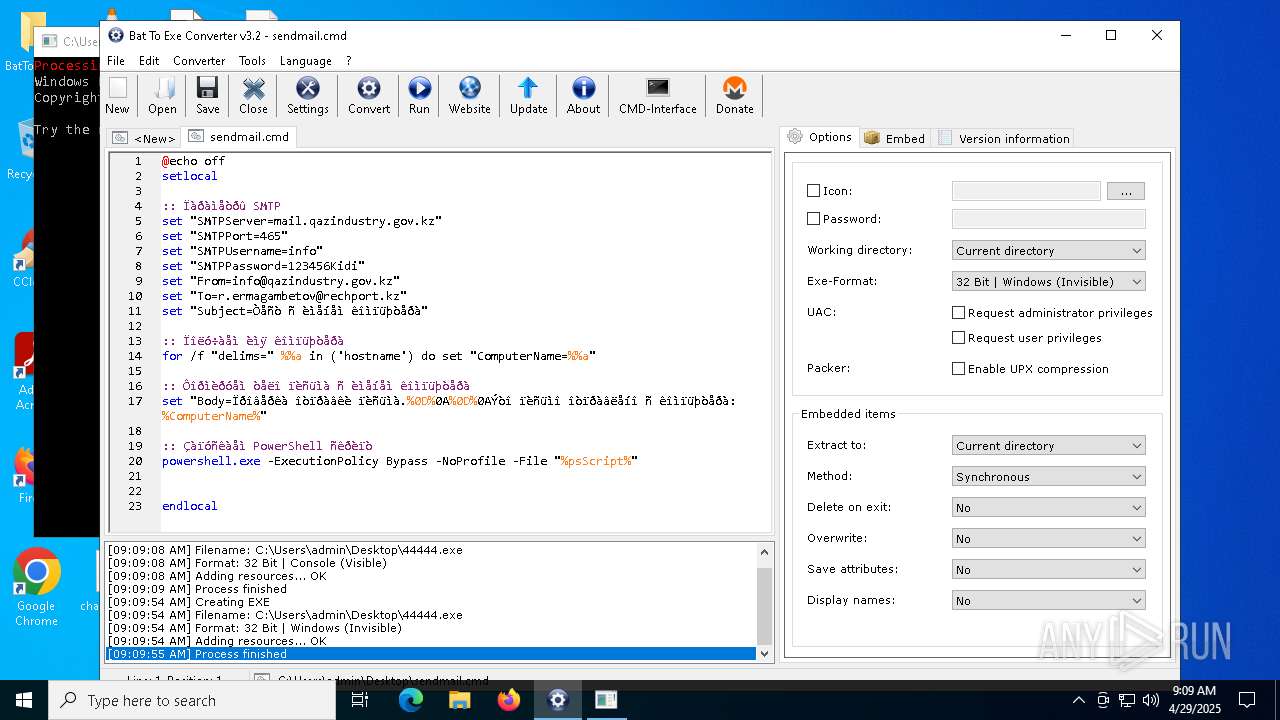
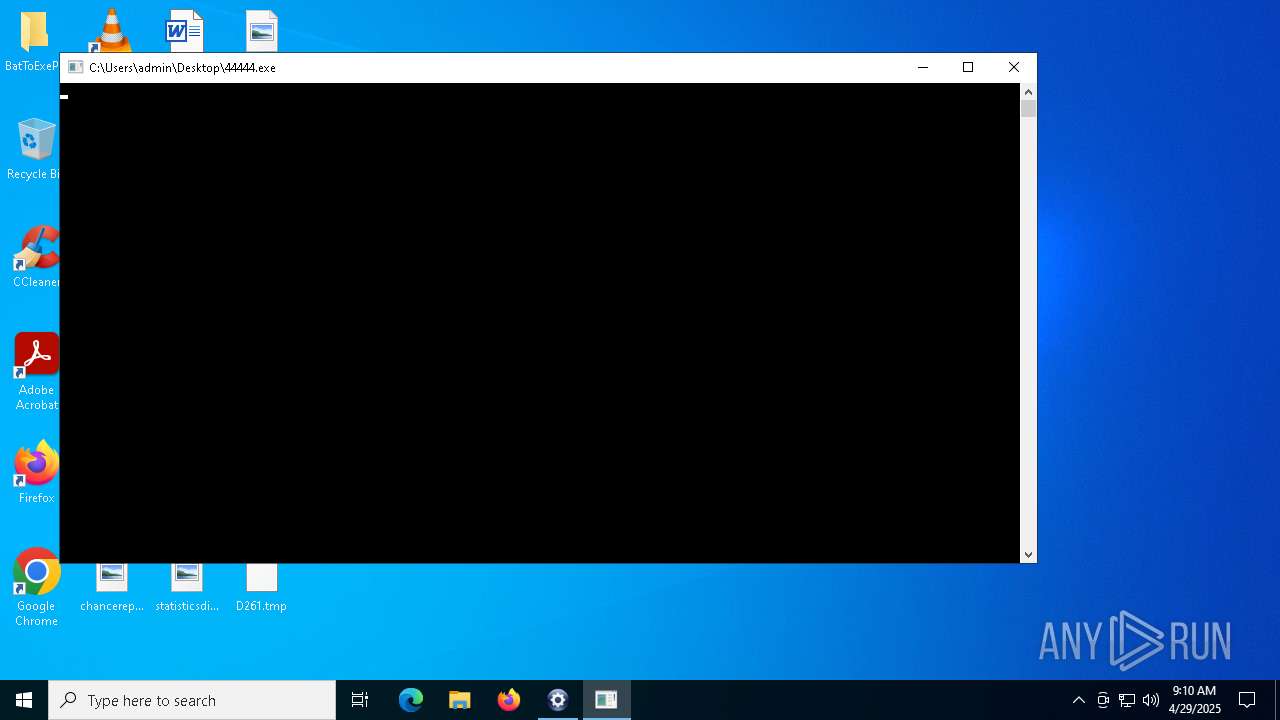
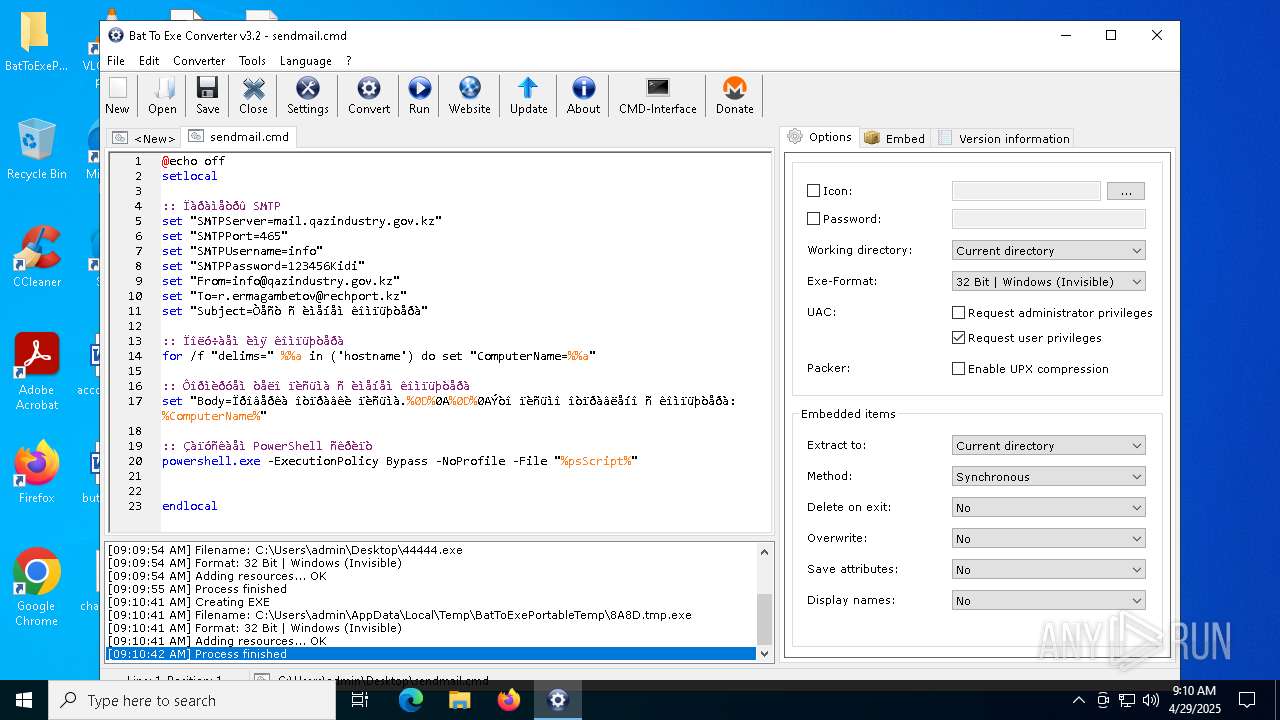
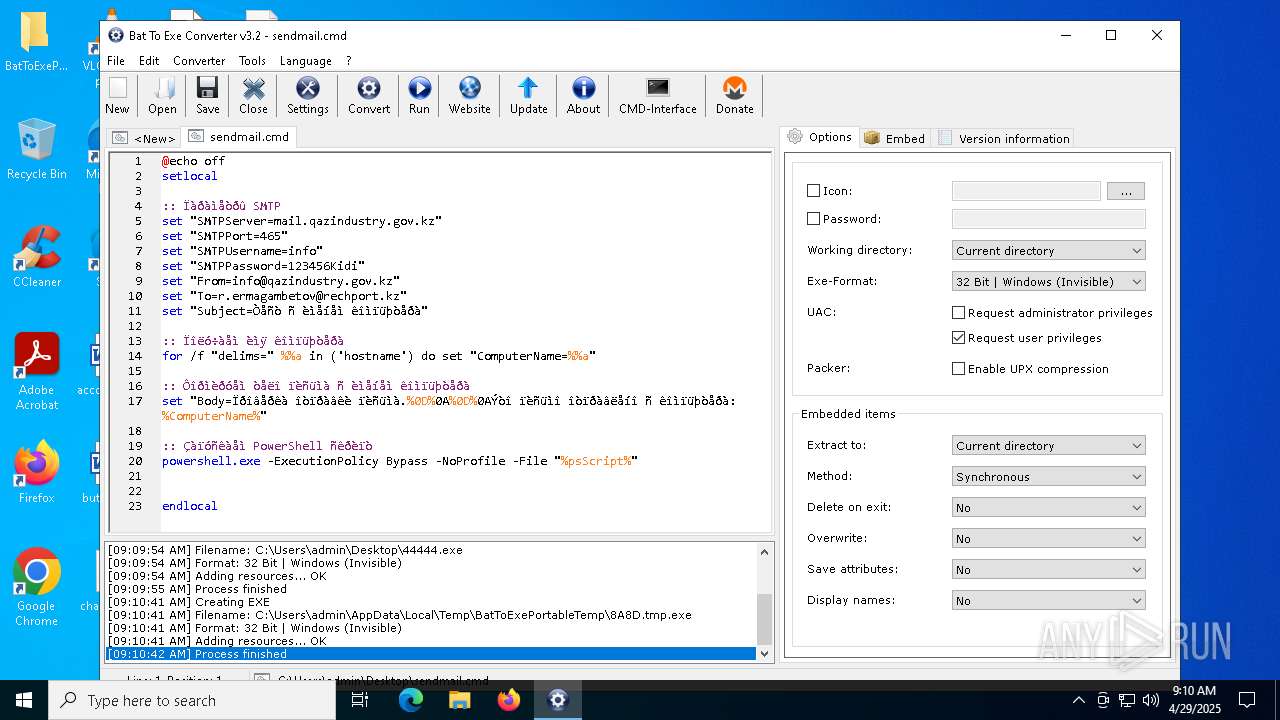
Executing commands from a ".bat" file
- 44444.exe (PID: 3968)
- 44444.exe (PID: 3804)
- 8A8D.tmp.exe (PID: 3828)
- 44444.exe (PID: 6592)
Starts CMD.EXE for commands execution
- 44444.exe (PID: 3968)
- cmd.exe (PID: 6416)
- 44444.exe (PID: 3804)
- cmd.exe (PID: 4188)
- 8A8D.tmp.exe (PID: 3828)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 976)
- 44444.exe (PID: 6592)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6416)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 976)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6416)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 976)
Application launched itself
- cmd.exe (PID: 4188)
- cmd.exe (PID: 6416)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 976)
INFO
The sample compiled with english language support
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 4892)
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
Checks supported languages
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 4892)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 5384)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
- BatToExePortable.exe (PID: 4268)
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
- 44444.exe (PID: 3968)
- 44444.exe (PID: 3804)
- 8A8D.tmp.exe (PID: 3828)
Reads the computer name
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 4892)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 5384)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
- BatToExePortable.exe (PID: 4268)
- 8A8D.tmp.exe (PID: 3828)
Create files in a temporary directory
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 4892)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 5384)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
- BatToExePortable.exe (PID: 4268)
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
- 44444.exe (PID: 3968)
- 44444.exe (PID: 3804)
- 8A8D.tmp.exe (PID: 3828)
Reads the software policy settings
- slui.exe (PID: 664)
- slui.exe (PID: 2088)
Manual execution by a user
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 5384)
- BatToExePortable_3.2_Dev_Test_1.paf.exe (PID: 6192)
- 44444.exe (PID: 3968)
- 44444.exe (PID: 3804)
- 44444.exe (PID: 6592)
The sample compiled with german language support
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
Checks proxy server information
- slui.exe (PID: 2088)
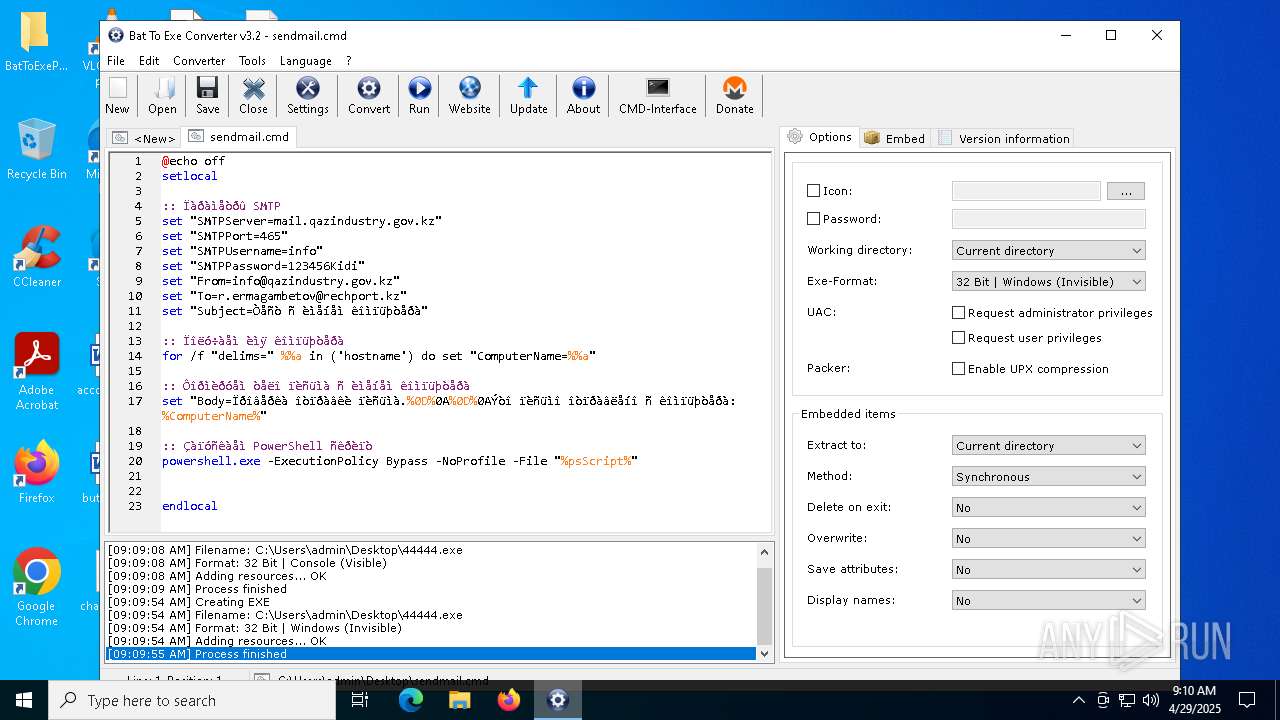
UPX packer has been detected
- Bat_To_Exe_Converter_(x64).exe (PID: 2616)
Process checks computer location settings
- 8A8D.tmp.exe (PID: 3828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:01+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 428544 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x34a5 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.1.99.1 |
| ProductVersionNumber: | 3.1.99.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | For additional details, visit PortableApps.com |
| CompanyName: | PortableApps.com |
| FileDescription: | BatToExe Portable |
| FileVersion: | 3.1.99.1 |
| InternalName: | BatToExe Portable |
| LegalCopyright: | 2007-2019 PortableApps.com, PortableApps.com Installer 3.5.14.0 |
| LegalTrademarks: | PortableApps.com is a registered trademark of Rare Ideas, LLC. |
| OriginalFileName: | BatToExePortable_3.2_Dev_Test_1.paf.exe |
| PortableAppscomAppID: | BatToExePortable |
| PortableAppscomFormatVersion: | 3.5.14 |
| PortableAppscomInstallerVersion: | 3.5.14.0 |
| ProductName: | BatToExe Portable |
| ProductVersion: | 3.1.99.1 |
Total processes
165
Monitored processes
32
Malicious processes
1
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | "C:\WINDOWS\sysnative\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\C37D.tmp\C37E.tmp\C37F.bat C:\Users\admin\Desktop\44444.exe" | C:\Windows\System32\cmd.exe | — | 44444.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
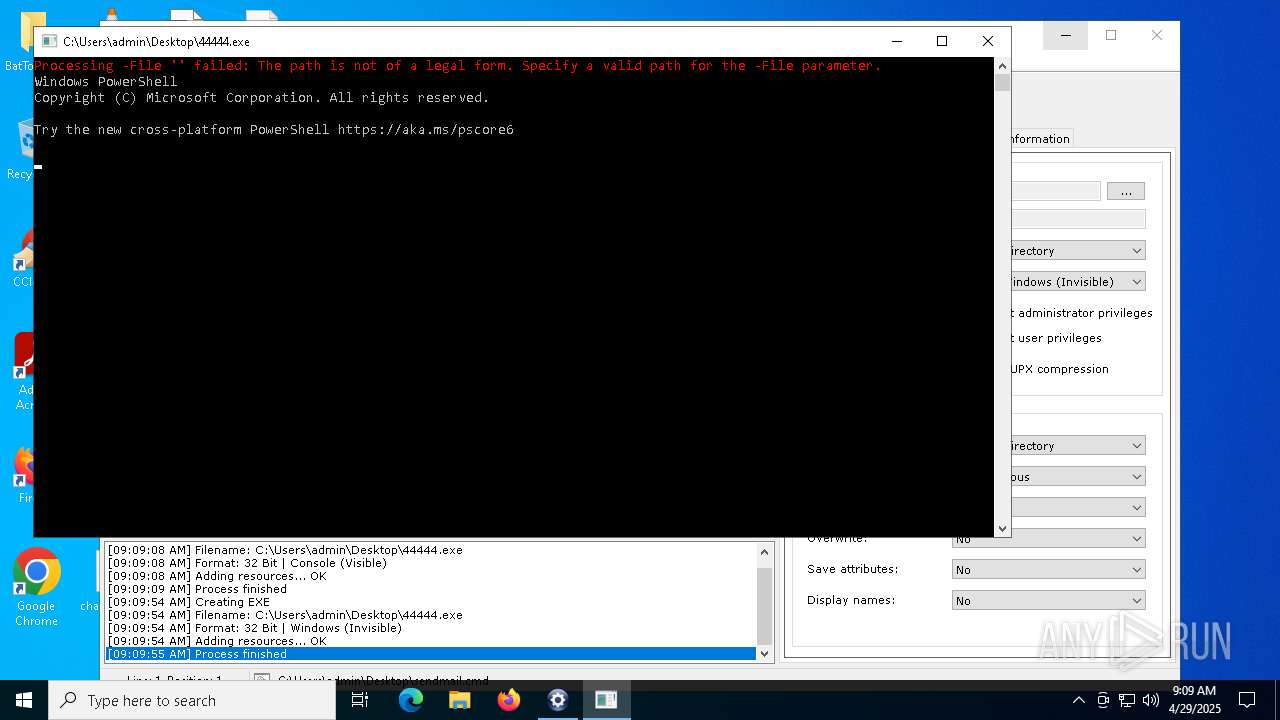
| 2084 | powershell.exe -ExecutionPolicy Bypass -NoProfile -File "" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294770688 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | "C:\BatToExePortable\App\BatToExe\Bat_To_Exe_Converter_(x64).exe" | C:\BatToExePortable\App\BatToExe\Bat_To_Exe_Converter_(x64).exe | BatToExePortable.exe | ||||||||||||
User: admin Company: Fatih Kodak Integrity Level: MEDIUM Description: Bat To Exe Converter Version: 3.2 Modules
| |||||||||||||||
| 3016 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 44444.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3804 | "C:\Users\admin\Desktop\44444.exe" | C:\Users\admin\Desktop\44444.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3828 | "C:\Users\admin\AppData\Local\Temp\BatToExePortableTemp\8A8D.tmp.exe" | C:\Users\admin\AppData\Local\Temp\BatToExePortableTemp\8A8D.tmp.exe | — | Bat_To_Exe_Converter_(x64).exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3888 | "C:\WINDOWS\sysnative\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\BatToExePortableTemp\8CBE.tmp\8CBF.tmp\8CC0.bat C:\Users\admin\AppData\Local\Temp\BatToExePortableTemp\8A8D.tmp.exe" | C:\Windows\System32\cmd.exe | — | 8A8D.tmp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 370
Read events
27 208
Write events
153
Delete events
9
Modification events
| (PID) Process: | (4892) BatToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (4892) BatToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: A696106800000000 | |||
| (PID) Process: | (4892) BatToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (4892) BatToExePortable_3.2_Dev_Test_1.paf.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (2616) Bat_To_Exe_Converter_(x64).exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 115 | |||
| (PID) Process: | (2616) Bat_To_Exe_Converter_(x64).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2616) Bat_To_Exe_Converter_(x64).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (2616) Bat_To_Exe_Converter_(x64).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (2616) Bat_To_Exe_Converter_(x64).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (2616) Bat_To_Exe_Converter_(x64).exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000400000000000000050000000200000003000000FFFFFFFF | |||
Executable files
96
Suspicious files
12
Text files
98
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszCDE3.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszCDE3.tmp\LangDLL.dll | executable | |
MD5:AB1DB56369412FE8476FEFFFD11E4CC0 | SHA256:6F14C8F01F50A30743DAC68C5AC813451463DFB427EB4E35FCDFE2410E1A913B | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszCDE3.tmp\w7tbp.dll | executable | |
MD5:9A3031CC4CEF0DBA236A28EECDF0AFB5 | SHA256:53BB519E3293164947AC7CBD7E612F637D77A7B863E3534BA1A7E39B350D3C00 | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\BatToExePortable\BatToExePortable.exe | executable | |
MD5:A7AF46DED9A327FAA37A8C94FC05DB1C | SHA256:61A170DF15C43CA758BE15B0C17D638C39D32ADF84C8E8C3ABAF409C126DA979 | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\BatToExePortable\App\Readme.txt | text | |
MD5:39809395CA95E97C59CB866F342435E3 | SHA256:6DDD6B23FDDDEFD100900089CC6873D6506D4EB496B7D570AB388823E44675C4 | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszCDE3.tmp\modern-wizard.bmp | image | |
MD5:4DF53EFCAA2C52F39618B2AAD77BB552 | SHA256:EE13539F3D66CC0592942EA1A4C35D8FD9AF67B1A7F272D0D791931E6E9CE4EB | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\BatToExePortable\App\AppInfo\appicon_32.png | image | |
MD5:E3816E99C6D23BF36E3BBBC4FEB18619 | SHA256:62473CFBE986876B23D92A179B3A93FEEDAE6558FC1476F1C44FFD7C87FDF05B | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\AppData\Local\Temp\nszCDE3.tmp\nsDialogs.dll | executable | |
MD5:466179E1C8EE8A1FF5E4427DBB6C4A01 | SHA256:1E40211AF65923C2F4FD02CE021458A7745D28E2F383835E3015E96575632172 | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\BatToExePortable\App\AppInfo\appicon.ico | image | |
MD5:62FF8D6E66BE21AB6B7386416210EFB4 | SHA256:66A766E7A3A8975EFC956387E1B419AD2DFA0E4AD8F2E860A8F8C7EAE1EE0FEE | |||
| 4892 | BatToExePortable_3.2_Dev_Test_1.paf.exe | C:\Users\admin\Desktop\BatToExePortable\App\AppInfo\appicon_75.png | image | |
MD5:5643F215D73253F8A83E4950BDE8C097 | SHA256:89E9AFC1F829AF6284C4EB94F4168091D2F48DA5FCCF31225BFDCF7286B2230E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
35
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6576 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6576 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1568 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |