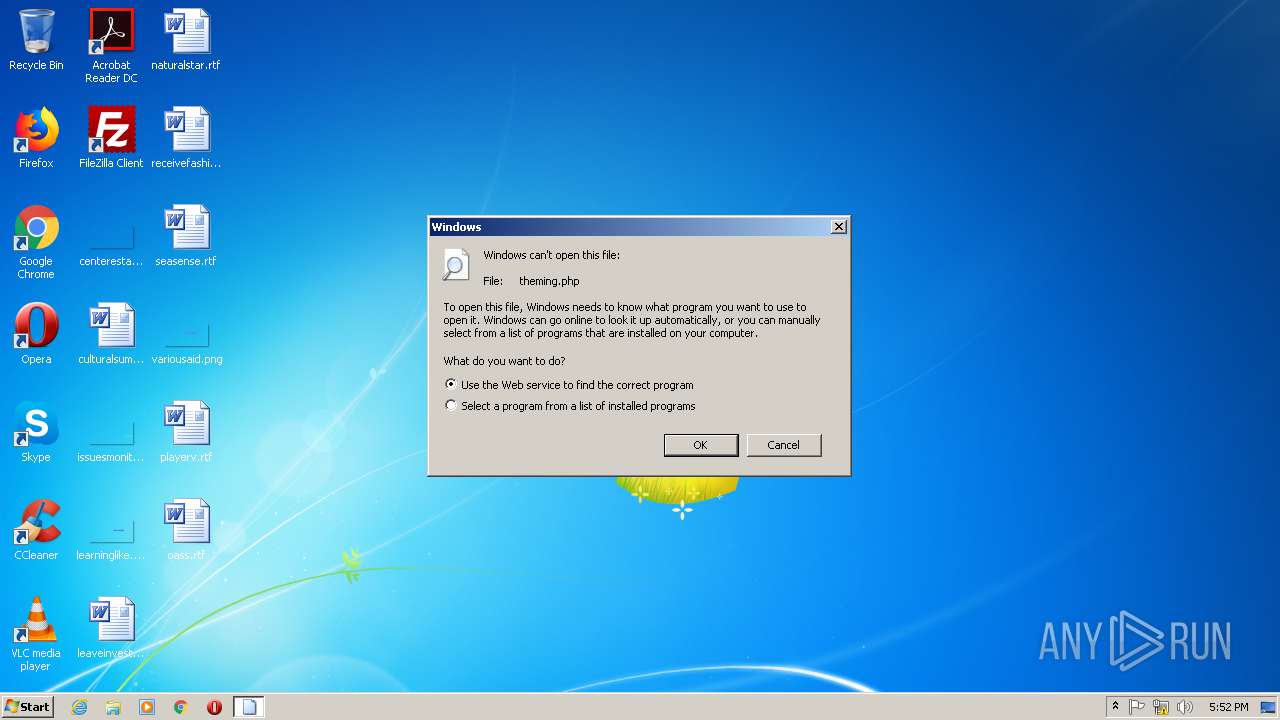
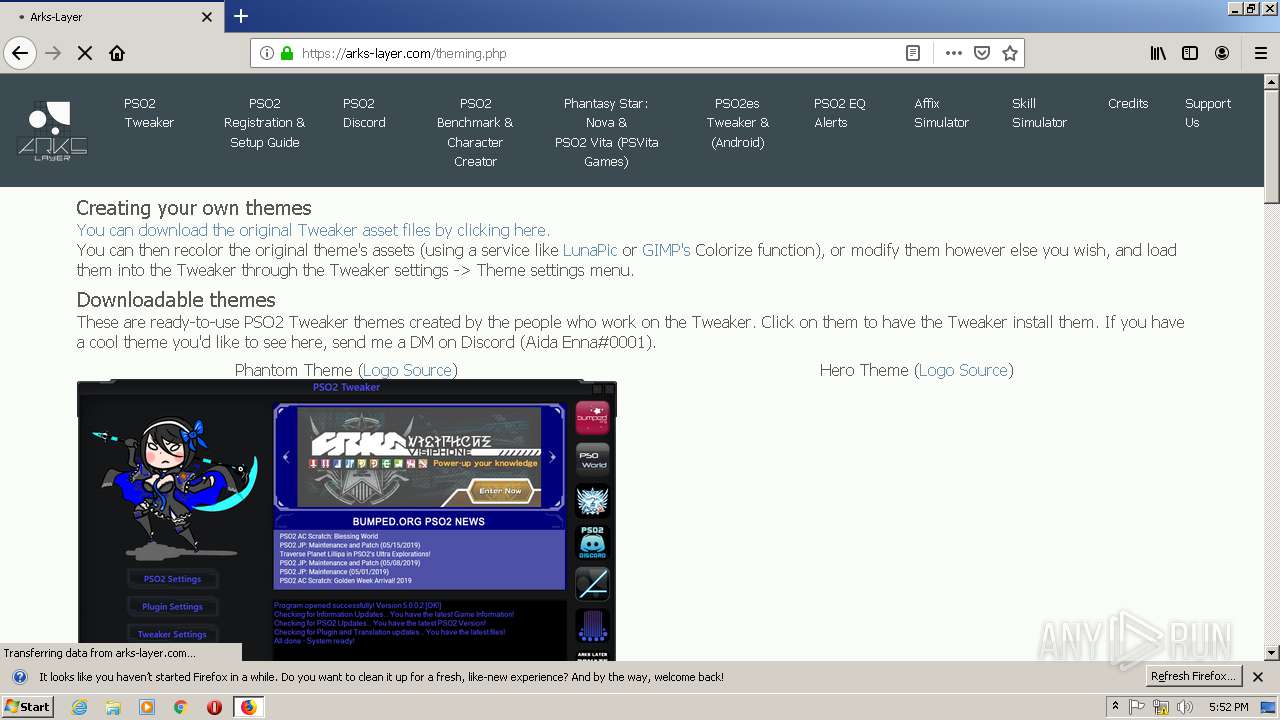
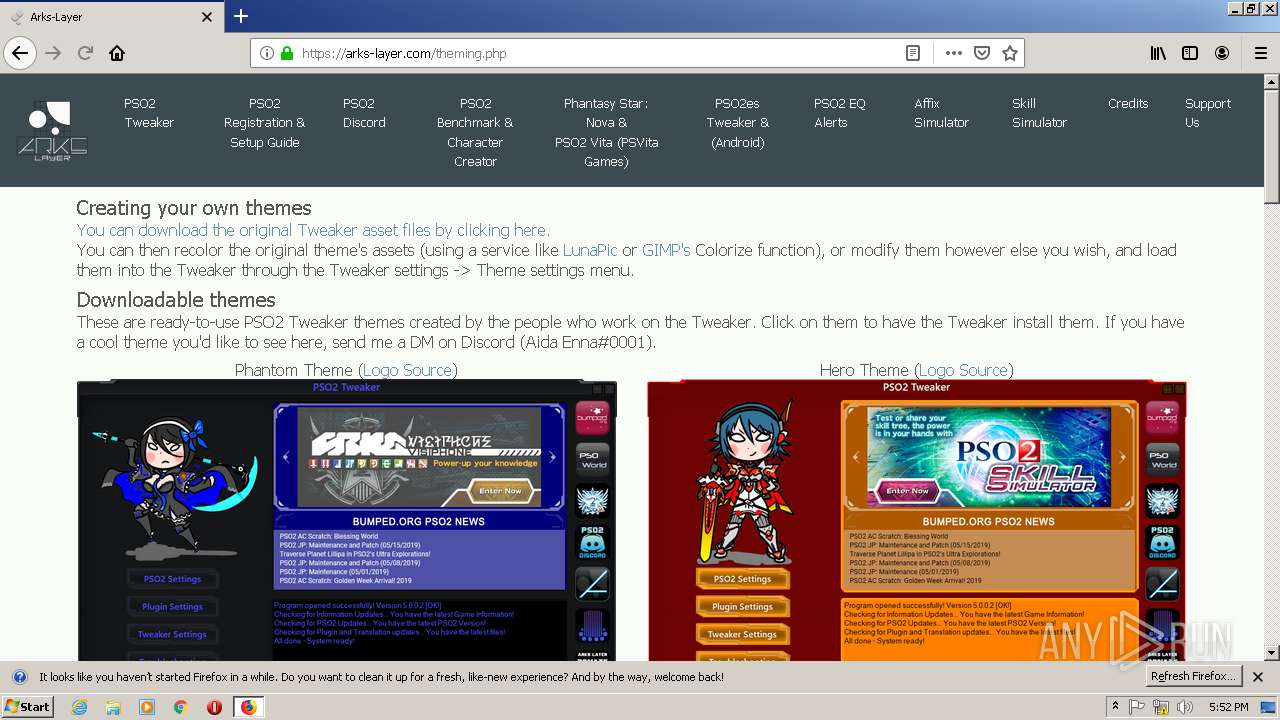
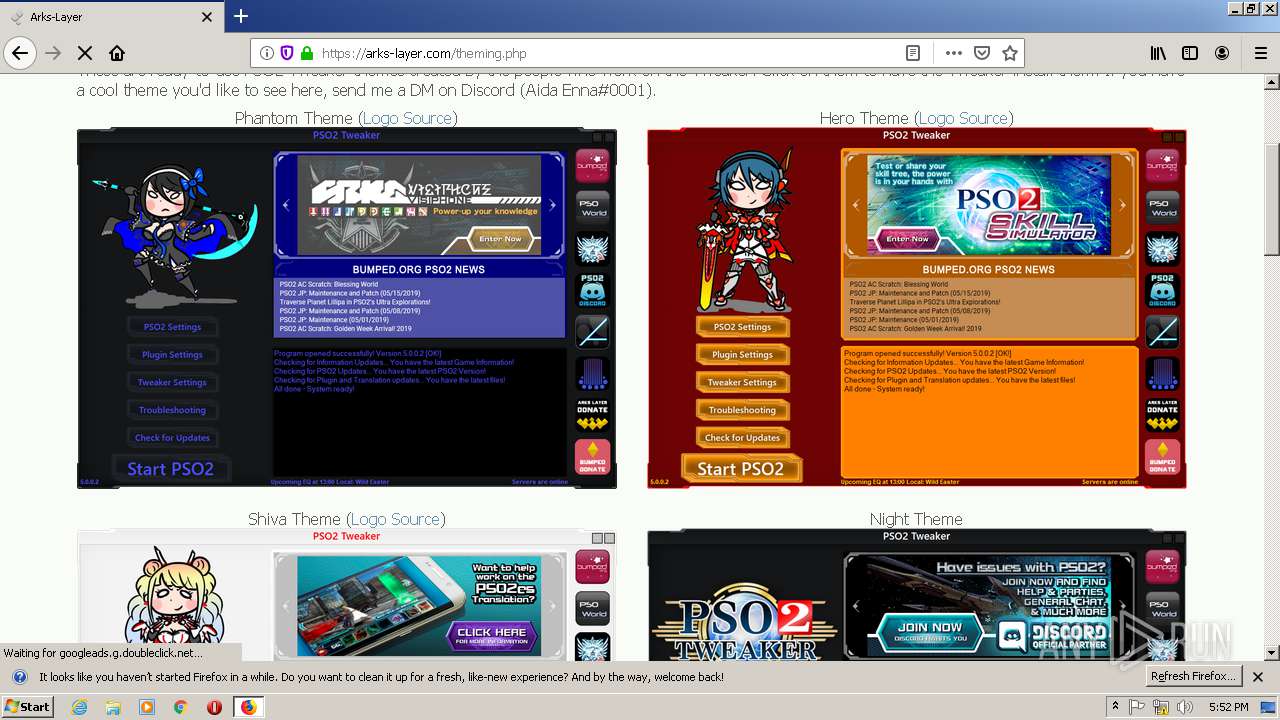
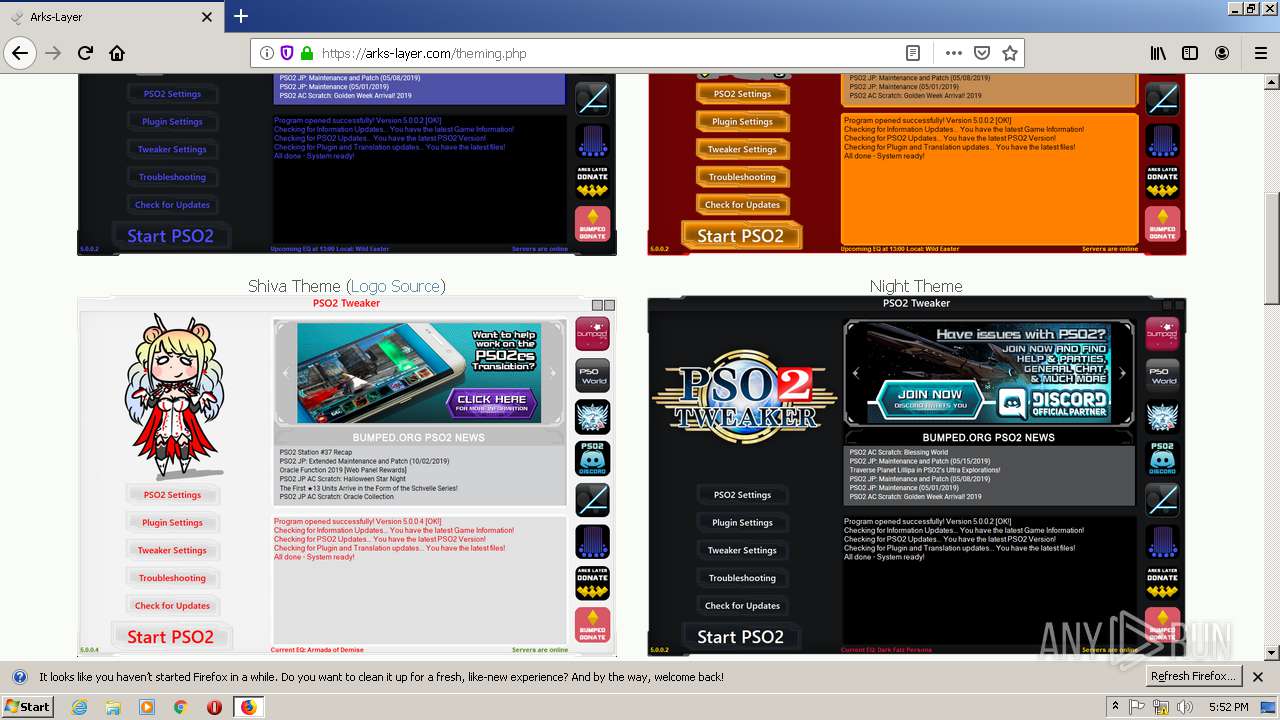
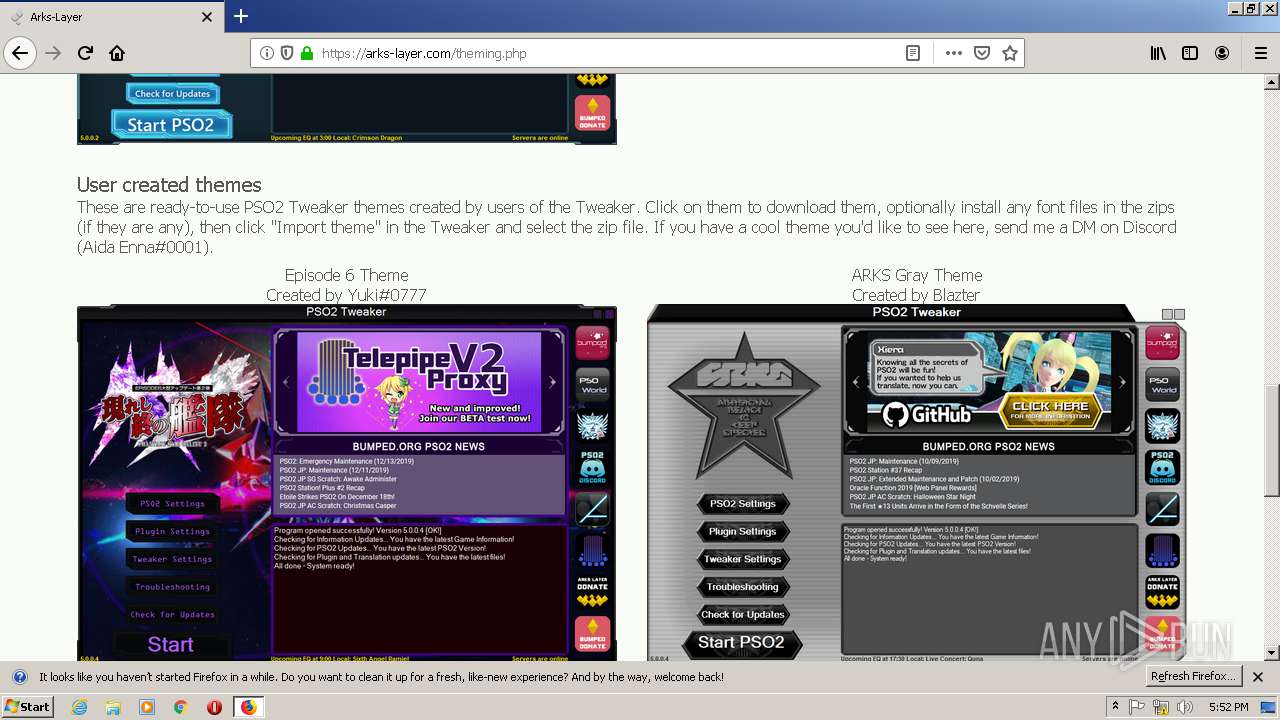
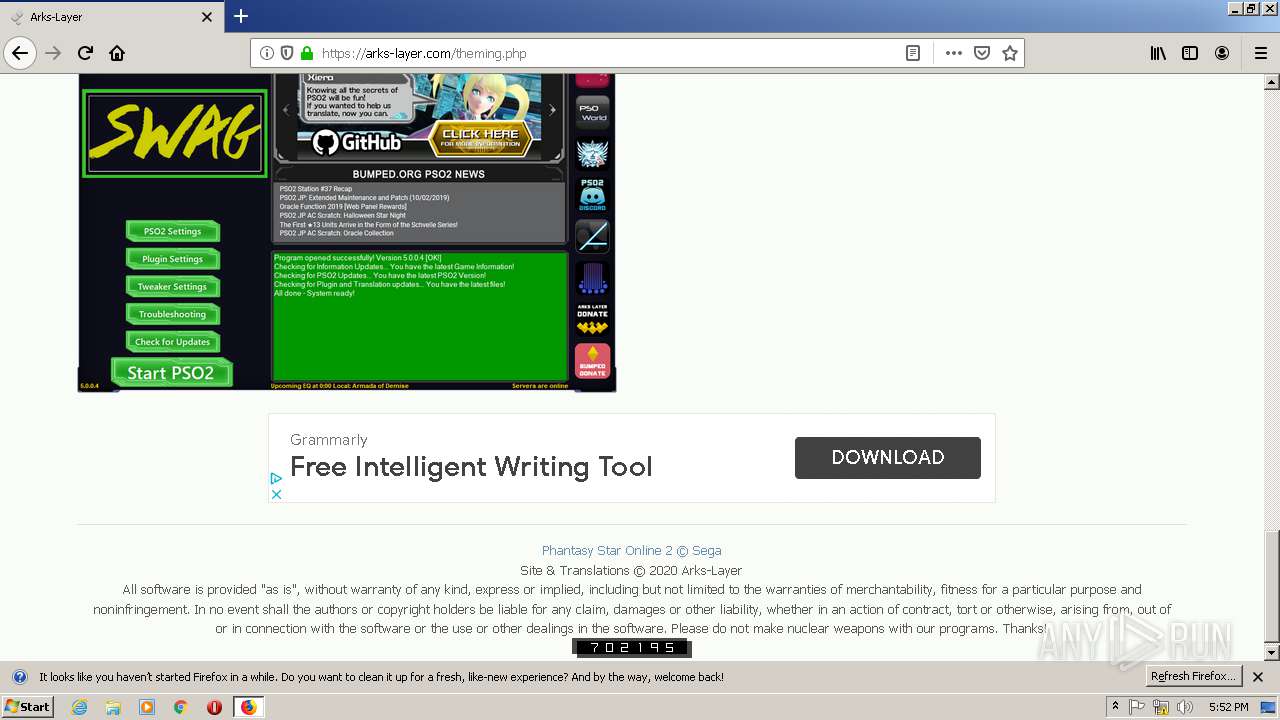
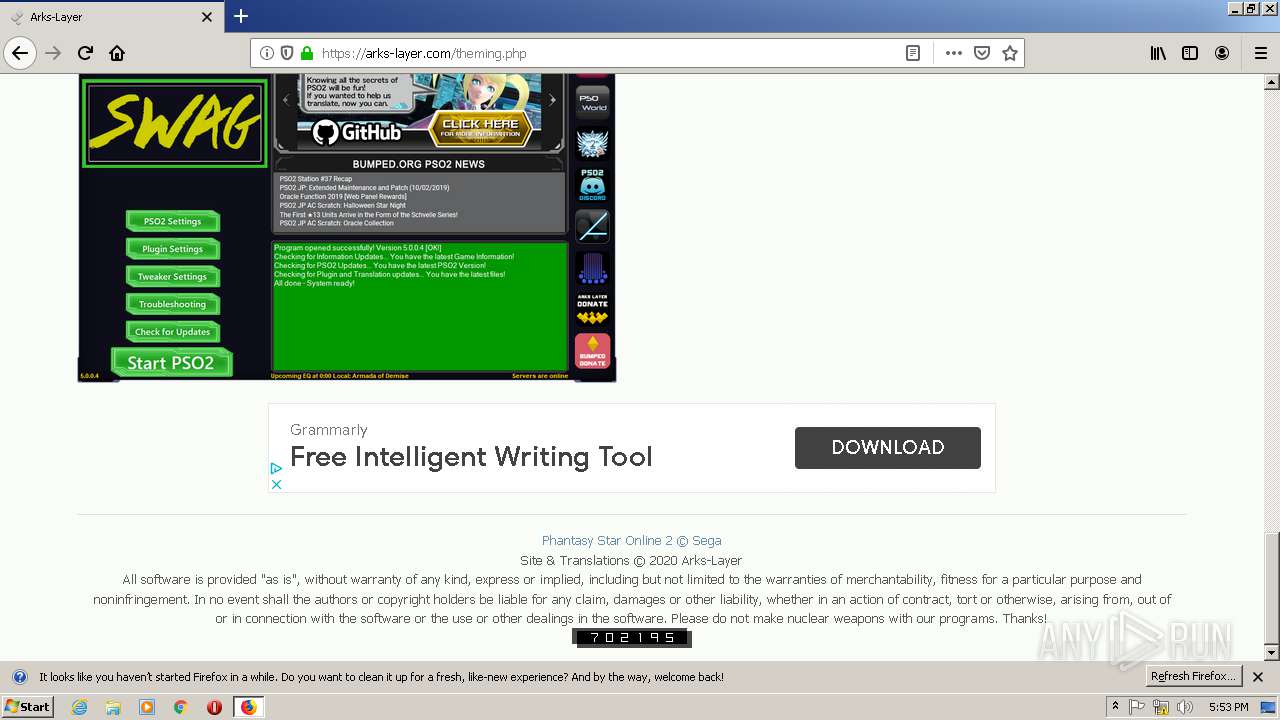
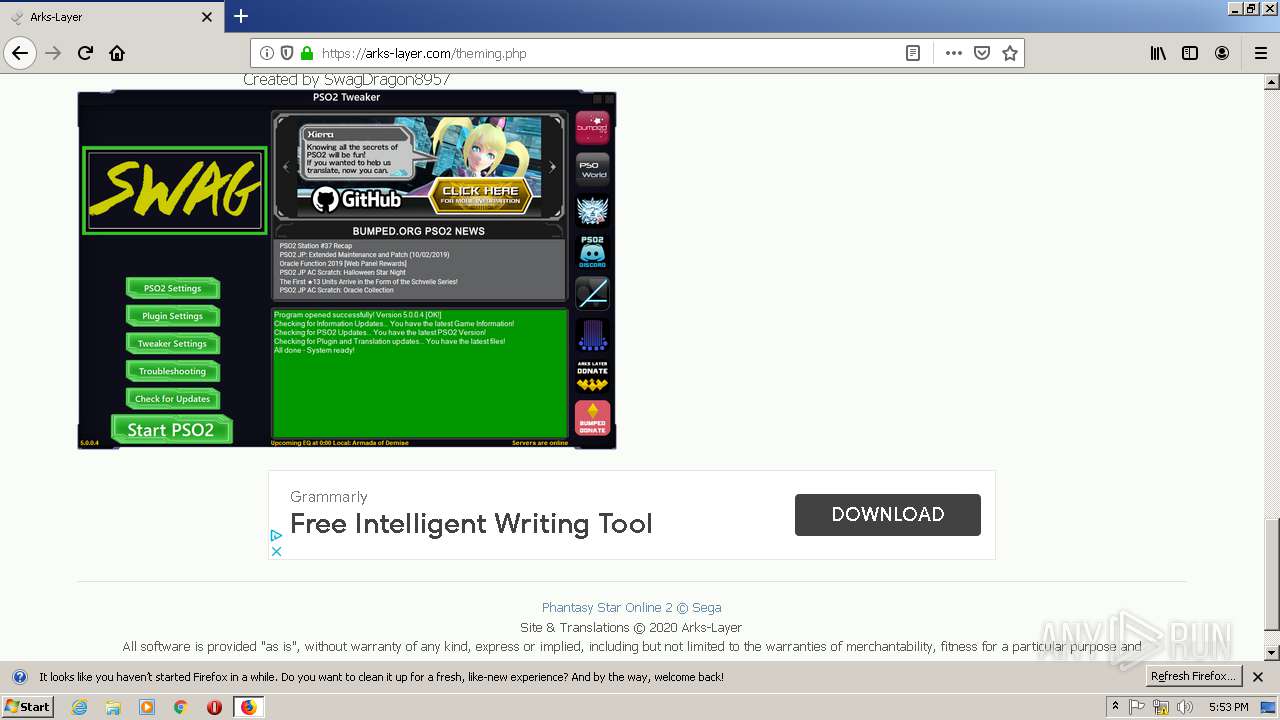
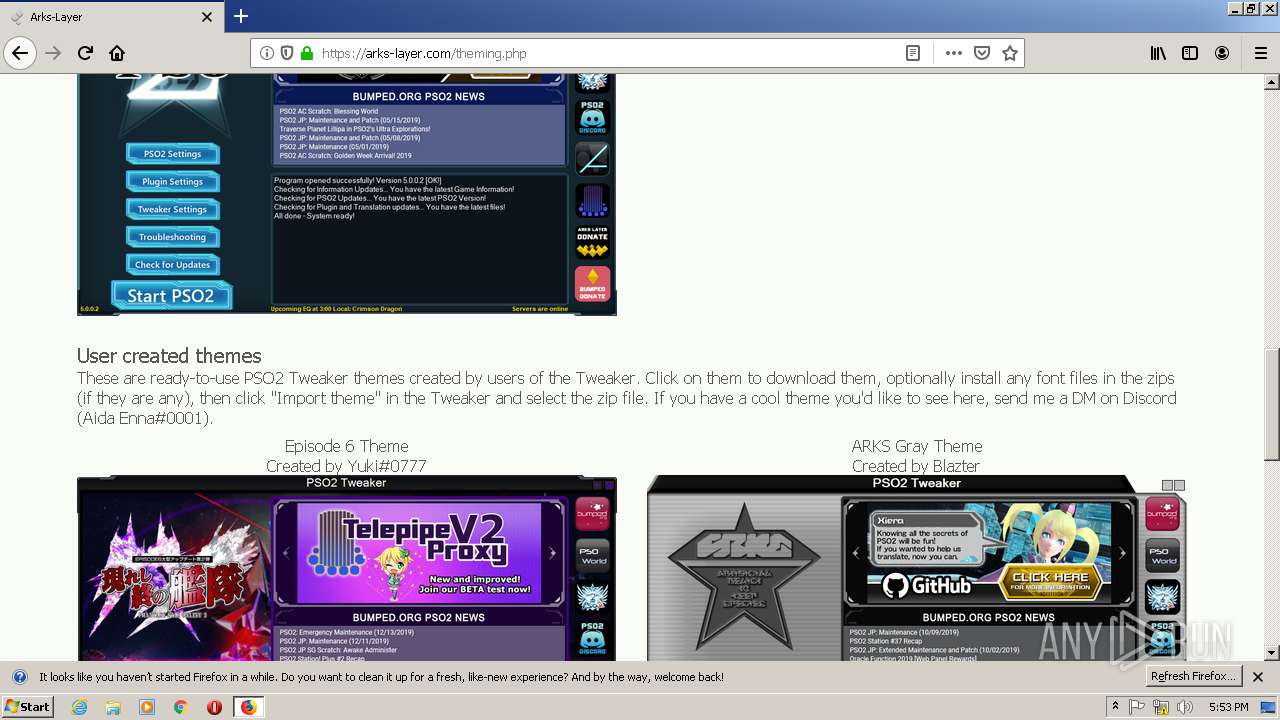
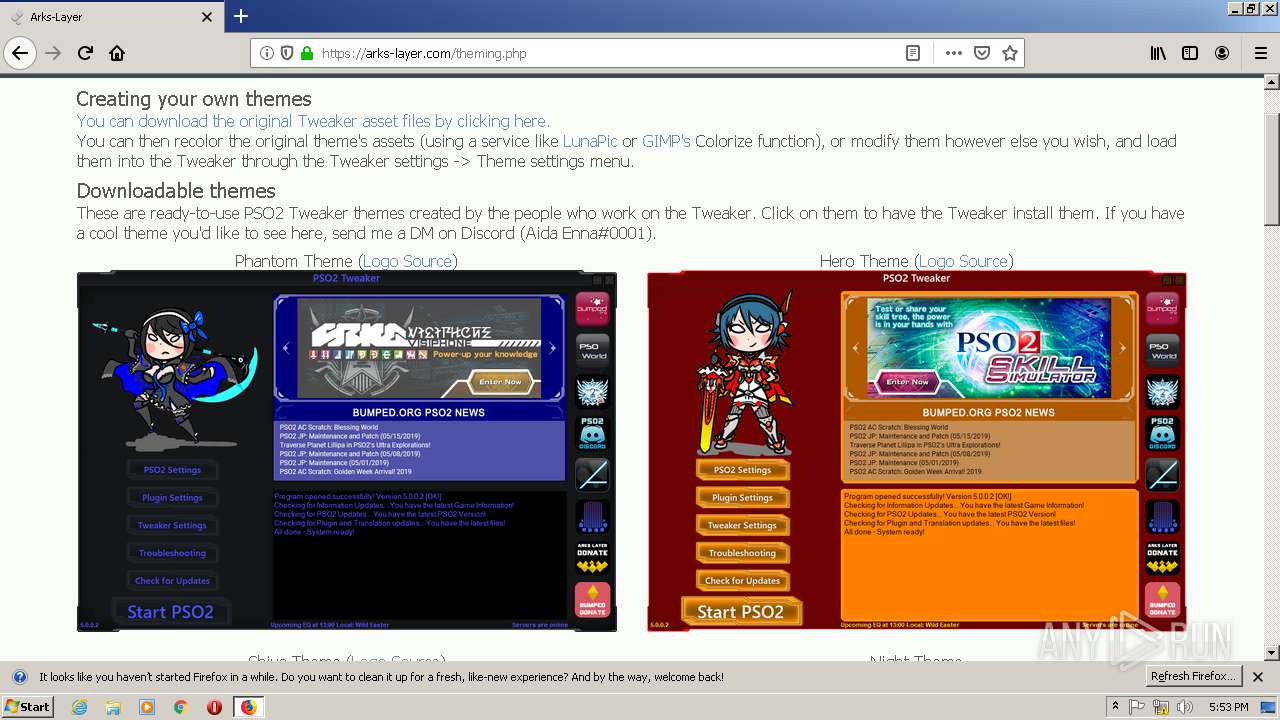
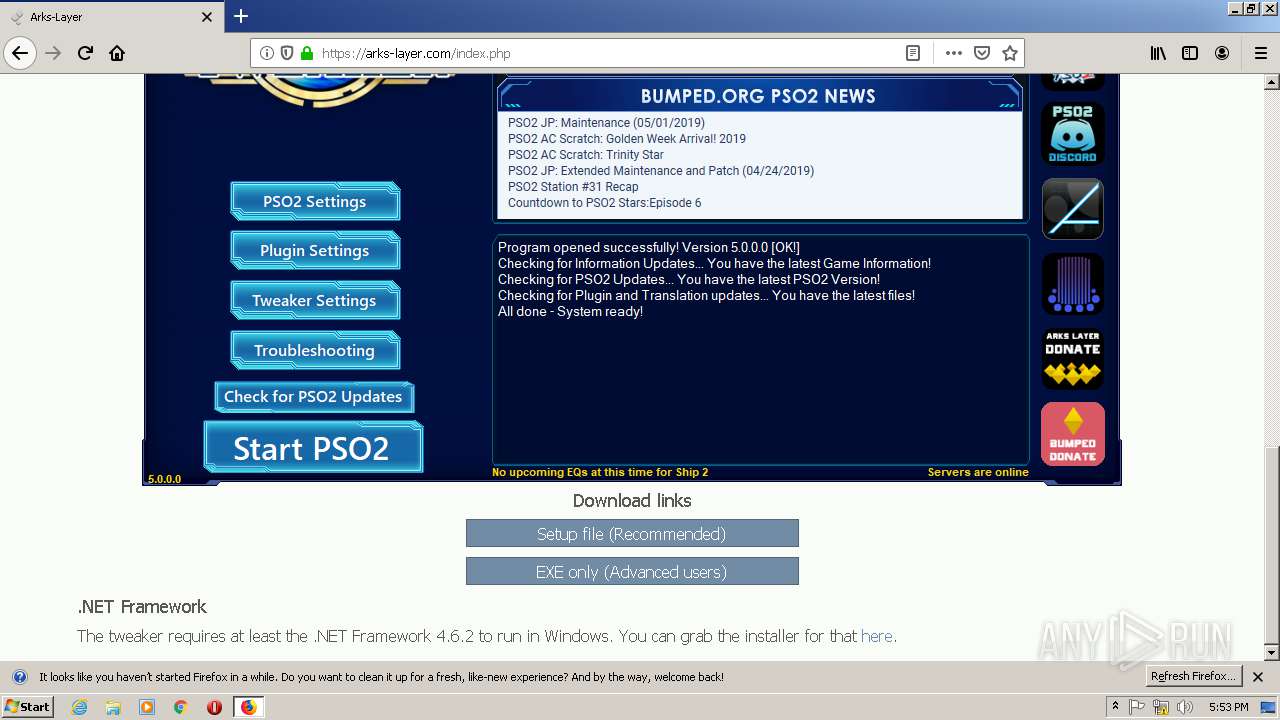
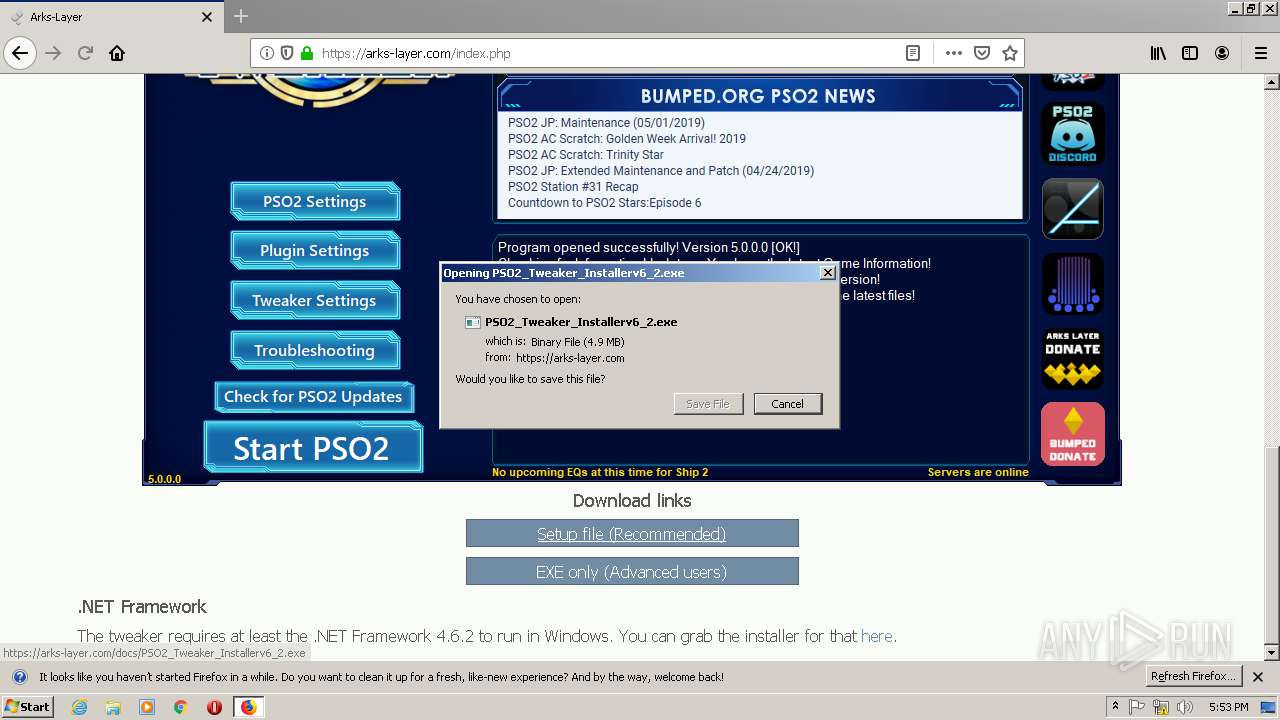
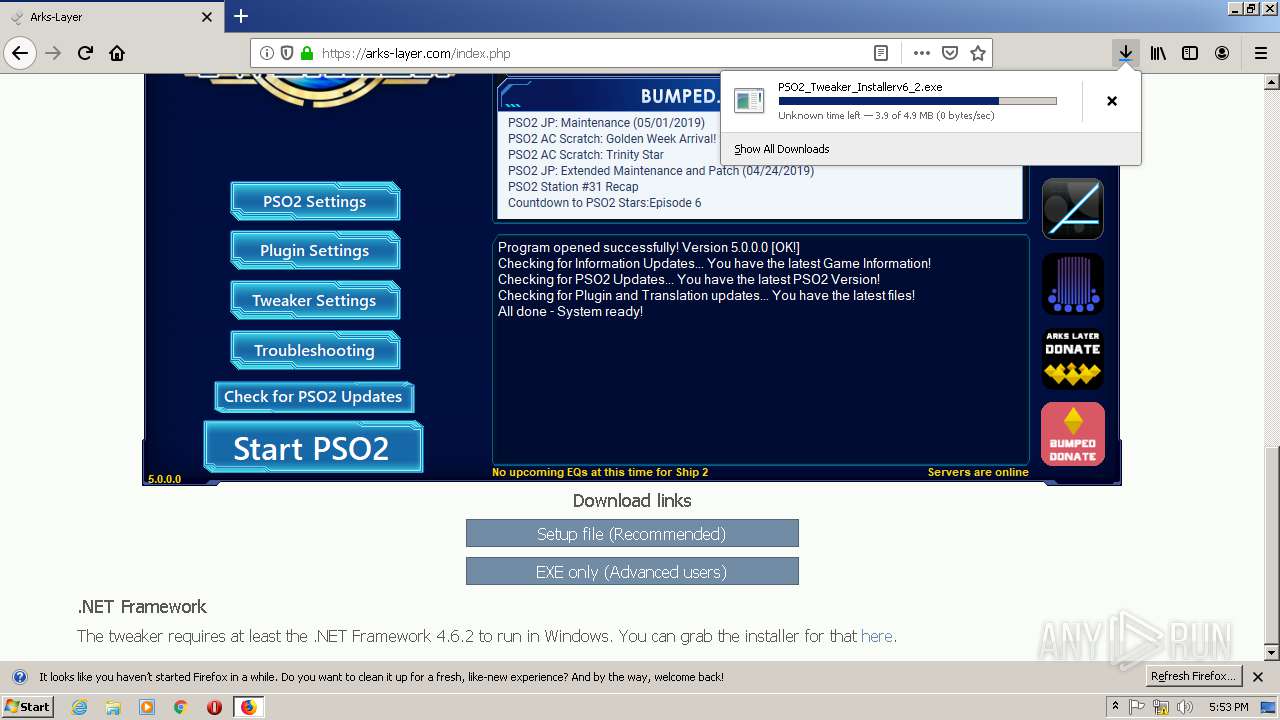
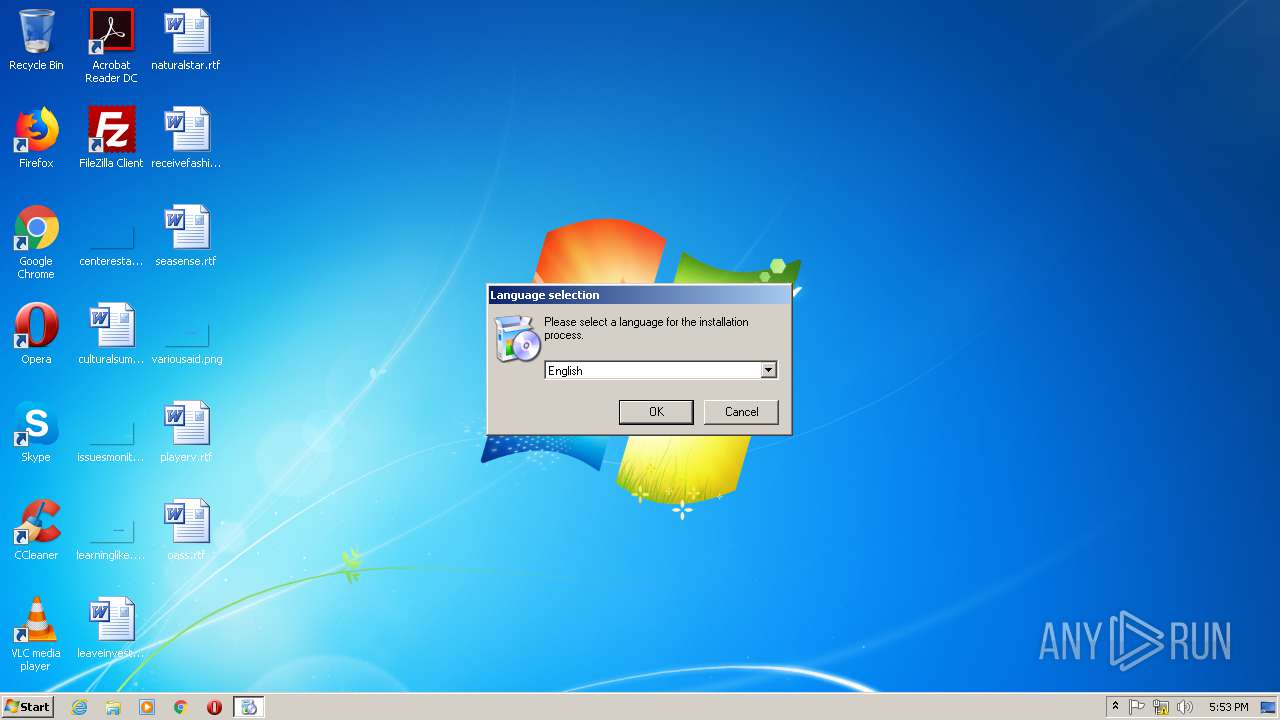
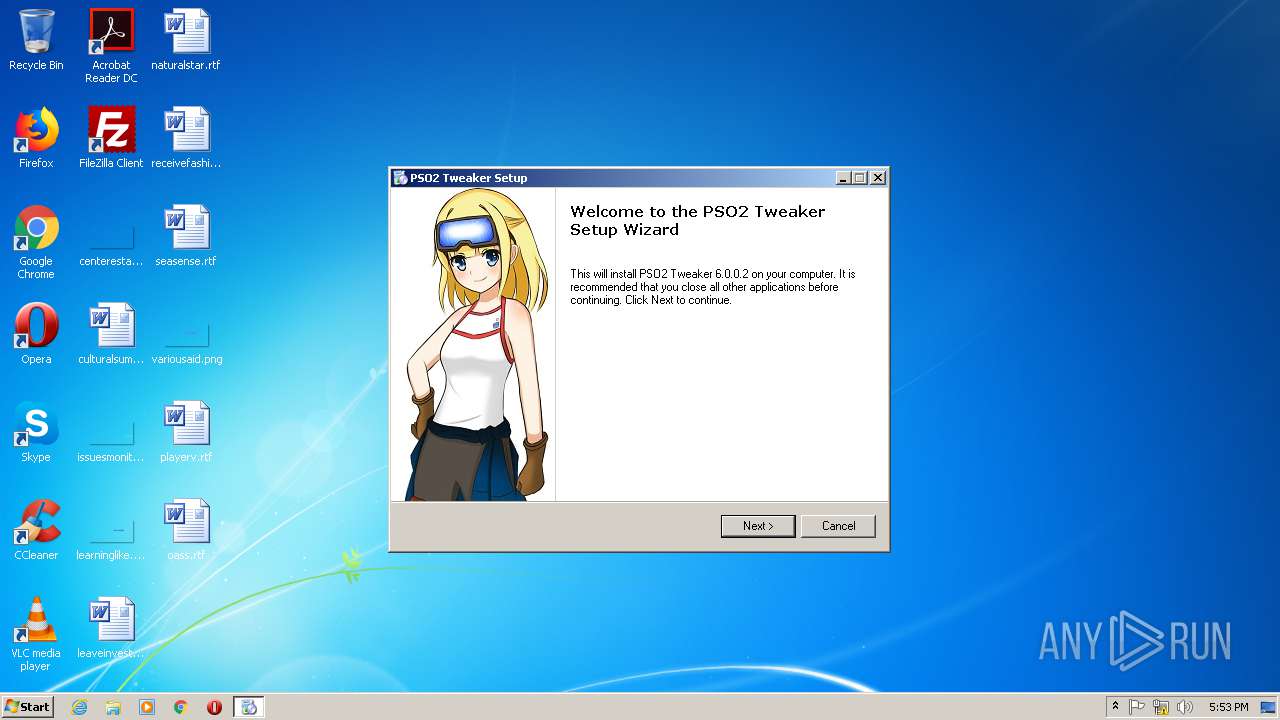
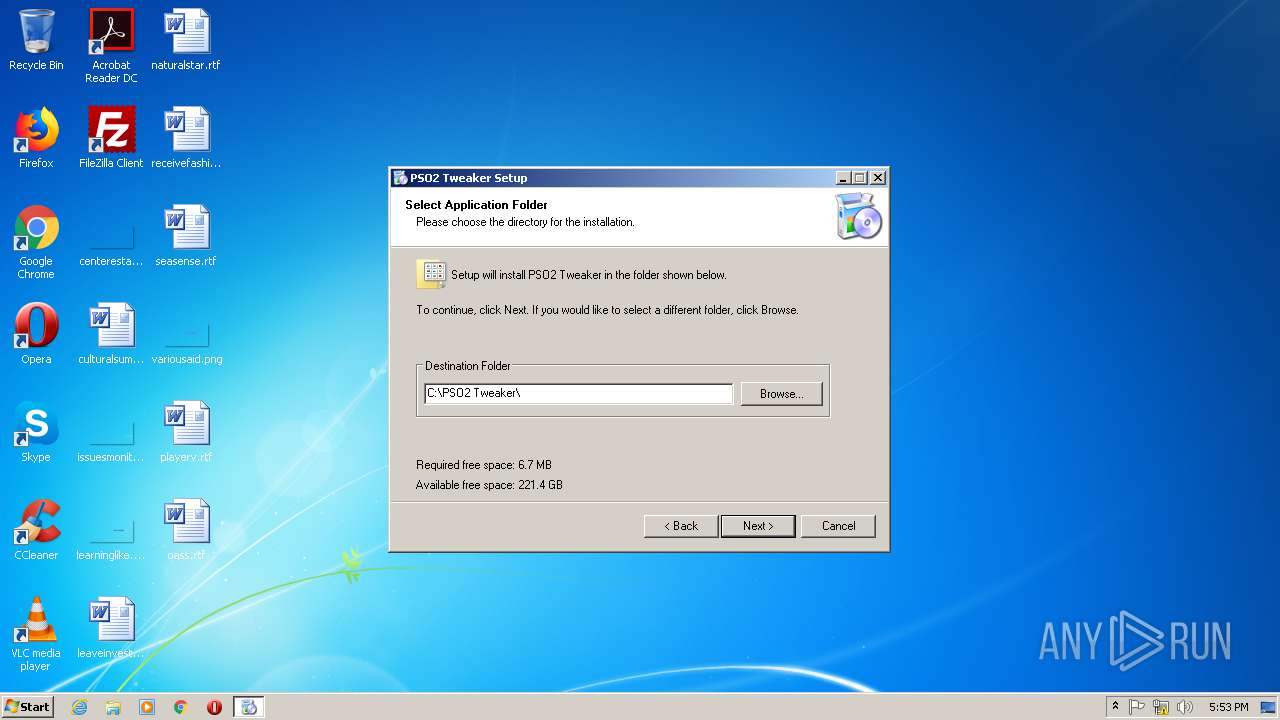
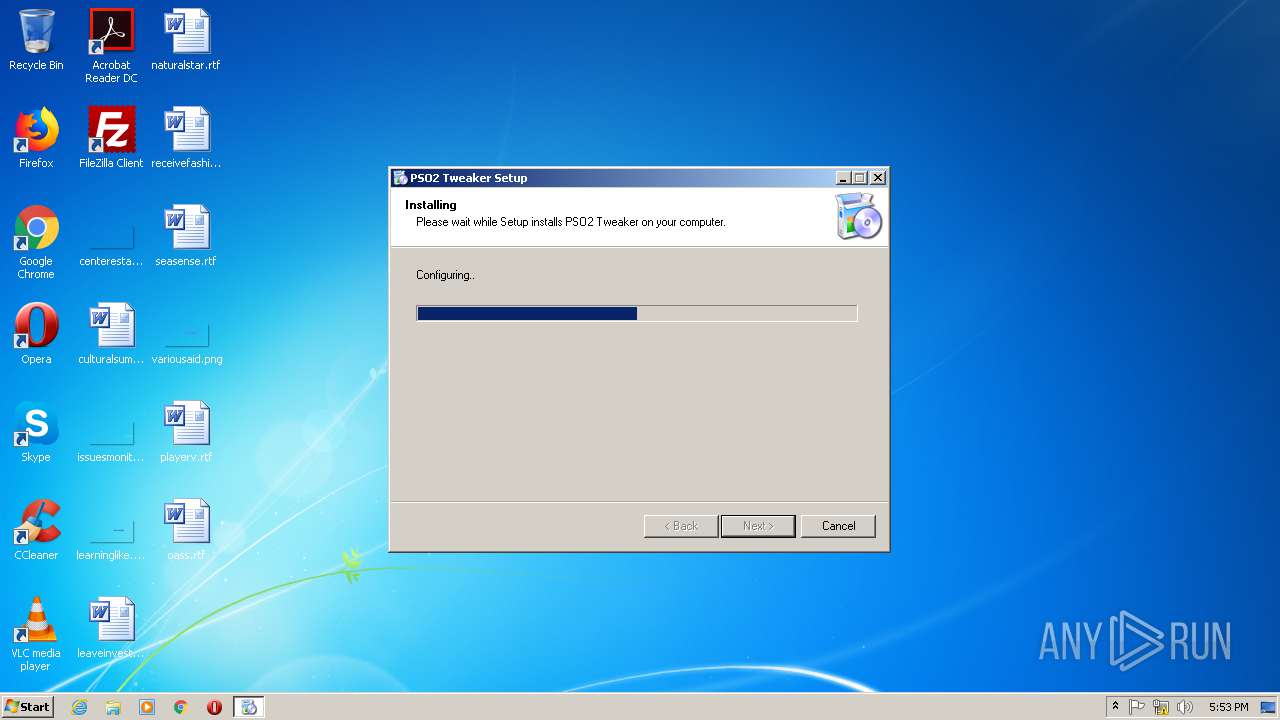
| download: | theming.php |
| Full analysis: | https://app.any.run/tasks/67619863-7554-4077-a141-21a98472d602 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 16:52:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with CRLF, LF line terminators |
| MD5: | C29BD9EF8825060D329BB9C5E3826F9E |
| SHA1: | 59FA7C9DEE6189C32E16BF47EE39DEEC3388AB56 |
| SHA256: | AFE3DF348FD58D0ED9BB240FDACA1C240B0C88D6CD31DA546EE54246F756E08E |
| SSDEEP: | 192:C2uWq9U6/d4EAmdlKd1dds6uidSGY1r+g4GXvPMvy480Vp:C9U6LqNani0tPMv1lVp |
MALICIOUS
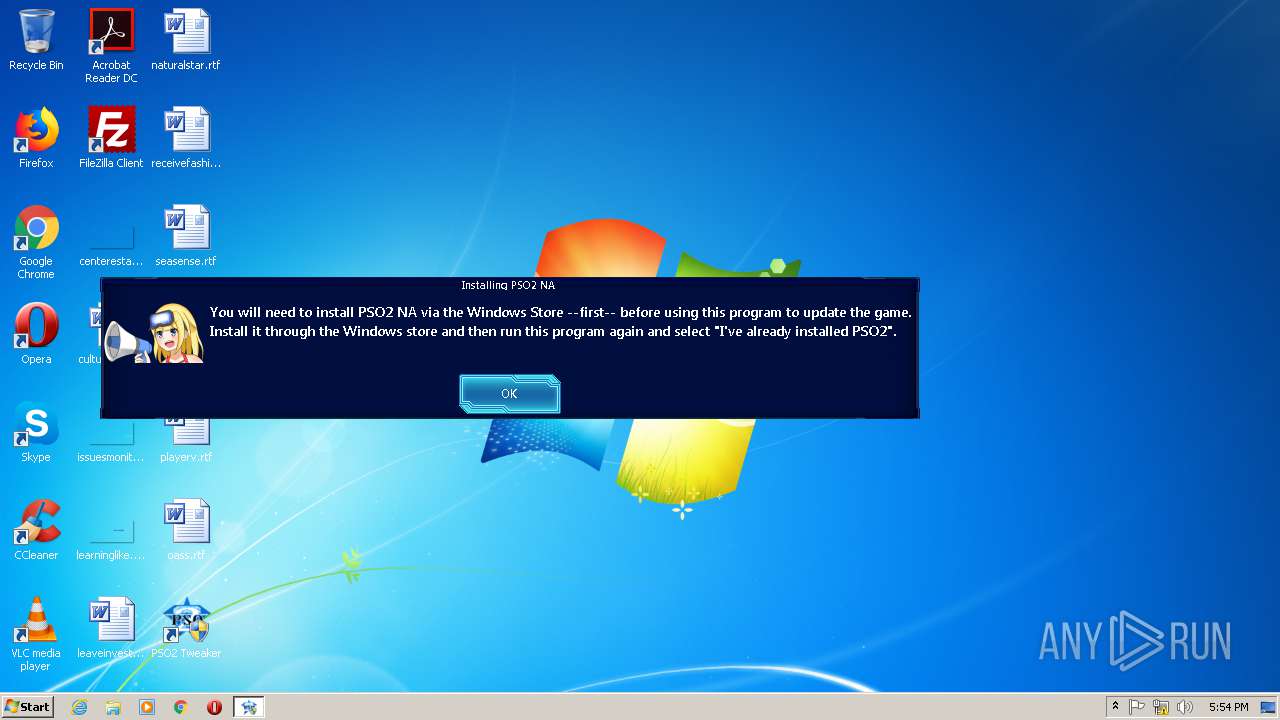
Application was dropped or rewritten from another process
- PSO2_Tweaker_Installerv6_2.exe (PID: 2020)
- PSO2_Tweaker_Installerv6_2.exe (PID: 3816)
- PSO2 Tweaker.exe (PID: 1384)
- PSO2 Tweaker.exe (PID: 1768)
SUSPICIOUS
Executable content was dropped or overwritten
- firefox.exe (PID: 3256)
- PSO2_Tweaker_Installerv6_2.exe (PID: 2020)
Creates files in the program directory
- firefox.exe (PID: 3256)
- PSO2_Tweaker_Installerv6_2.exe (PID: 2020)
Creates a software uninstall entry
- PSO2_Tweaker_Installerv6_2.exe (PID: 2020)
Application launched itself
- PSO2 Tweaker.exe (PID: 1768)
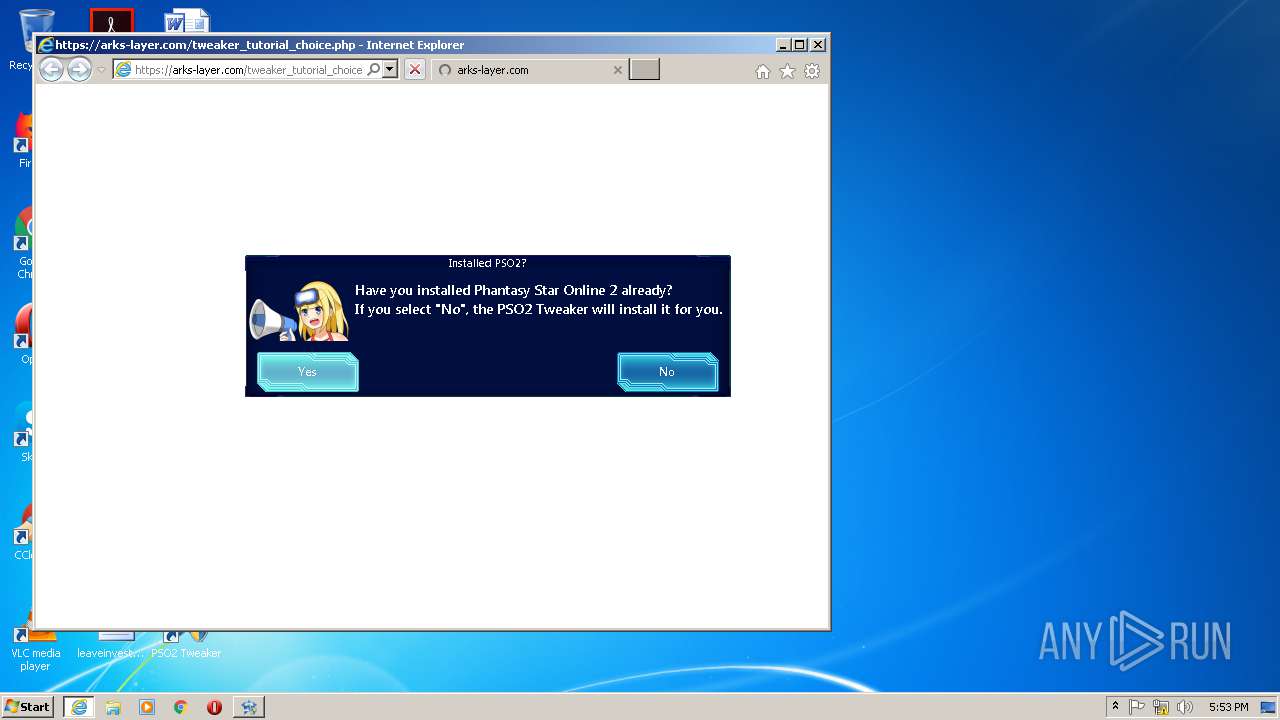
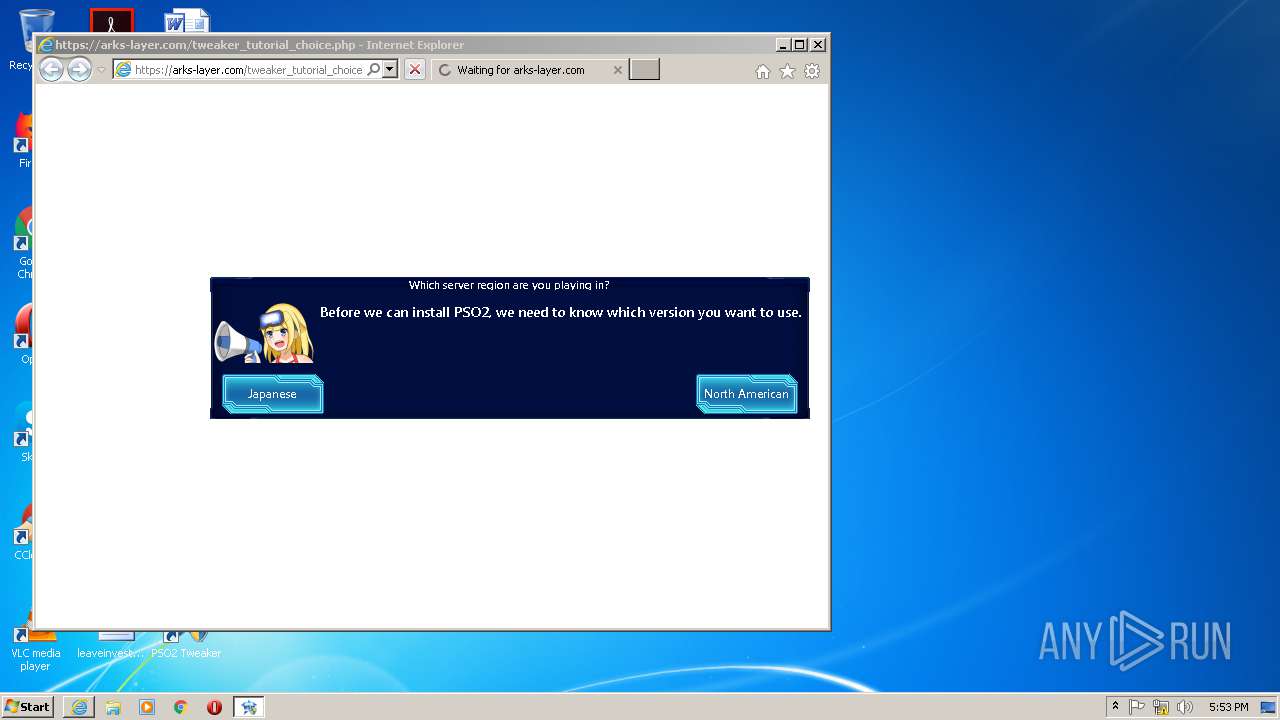
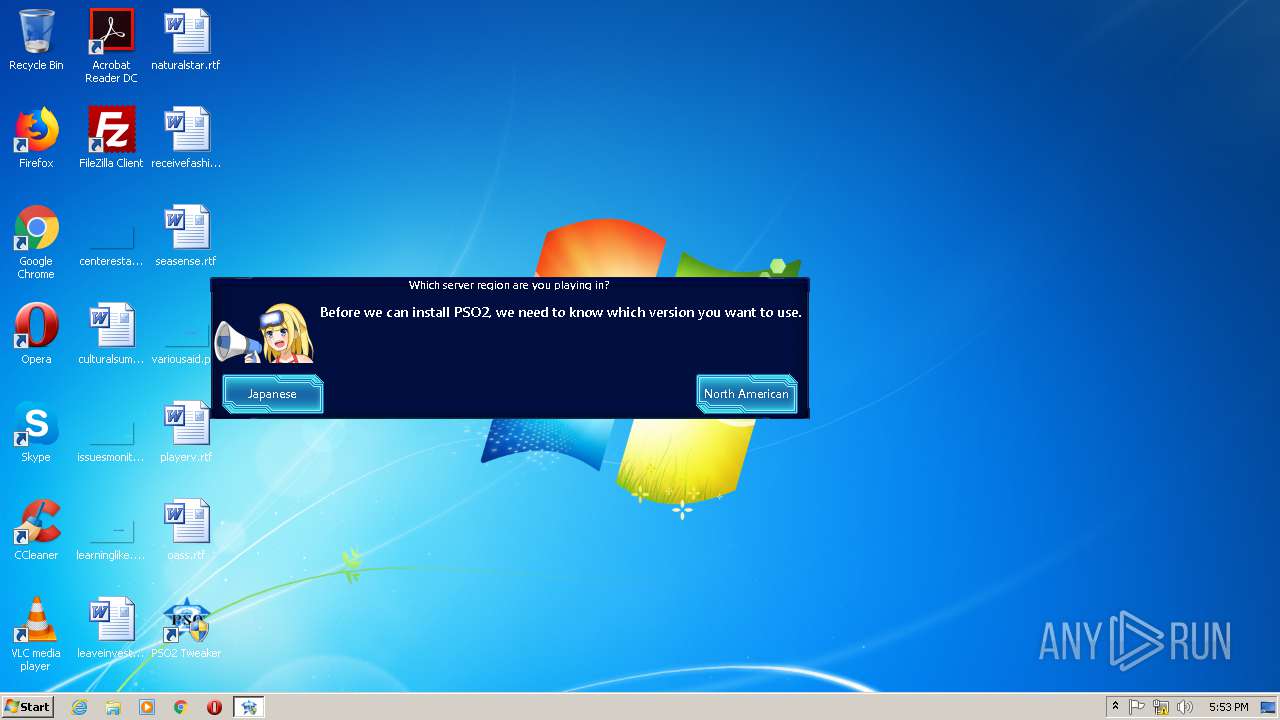
Starts Internet Explorer
- PSO2 Tweaker.exe (PID: 1384)
Reads Environment values
- PSO2 Tweaker.exe (PID: 1384)
Creates files in the user directory
- PSO2 Tweaker.exe (PID: 1384)
INFO
Application launched itself
- firefox.exe (PID: 3256)
- iexplore.exe (PID: 348)
Manual execution by user
- firefox.exe (PID: 2348)
Reads CPU info
- firefox.exe (PID: 3256)
Reads Internet Cache Settings
- firefox.exe (PID: 3256)
- pingsender.exe (PID: 2316)
- iexplore.exe (PID: 3812)
- iexplore.exe (PID: 348)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3256)
Creates files in the user directory
- firefox.exe (PID: 3256)
- iexplore.exe (PID: 3812)
Reads settings of System Certificates
- pingsender.exe (PID: 2316)
- iexplore.exe (PID: 3812)
Changes internet zones settings
- iexplore.exe (PID: 348)
Reads internet explorer settings
- iexplore.exe (PID: 3812)
Changes settings of System certificates
- iexplore.exe (PID: 3812)
- pingsender.exe (PID: 2316)
Adds / modifies Windows certificates
- pingsender.exe (PID: 2316)
- iexplore.exe (PID: 3812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| viewport: | width=device-width, initial-scale=1, user-scalable=no |
|---|---|
| mobileWebAppCapable: | yes |
| HTTPEquivXUACompatible: | IE=edge |
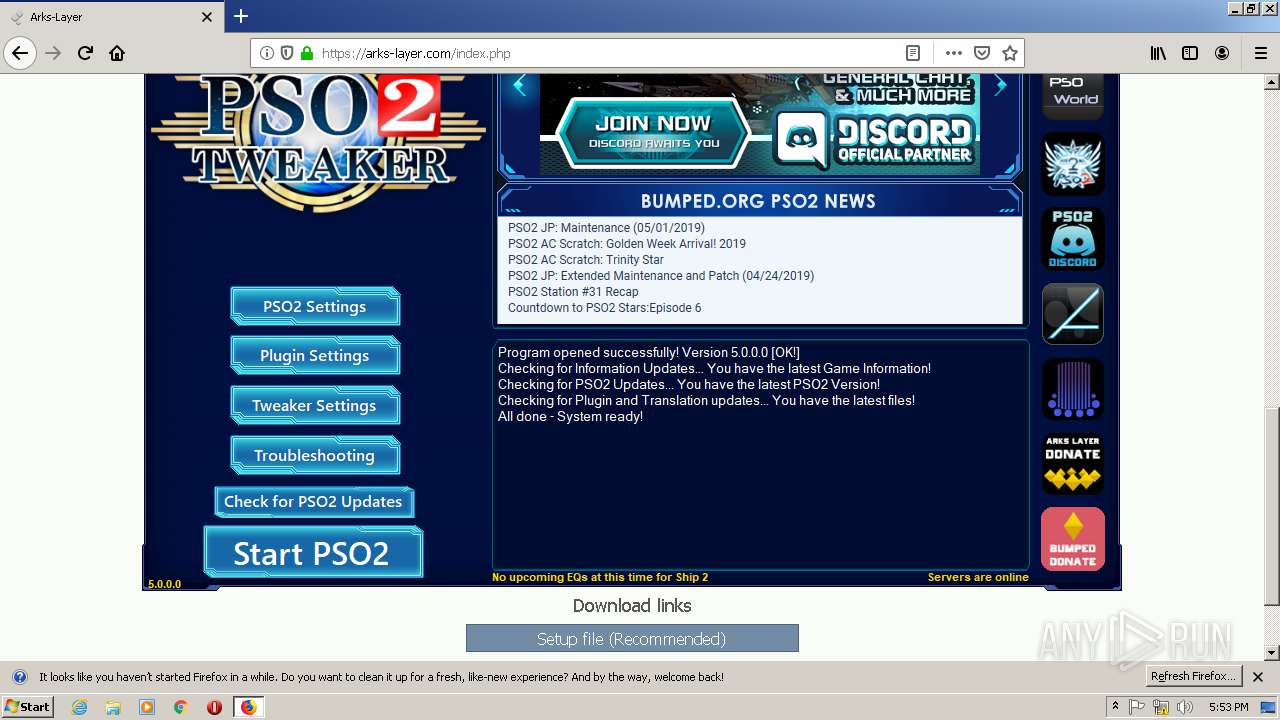
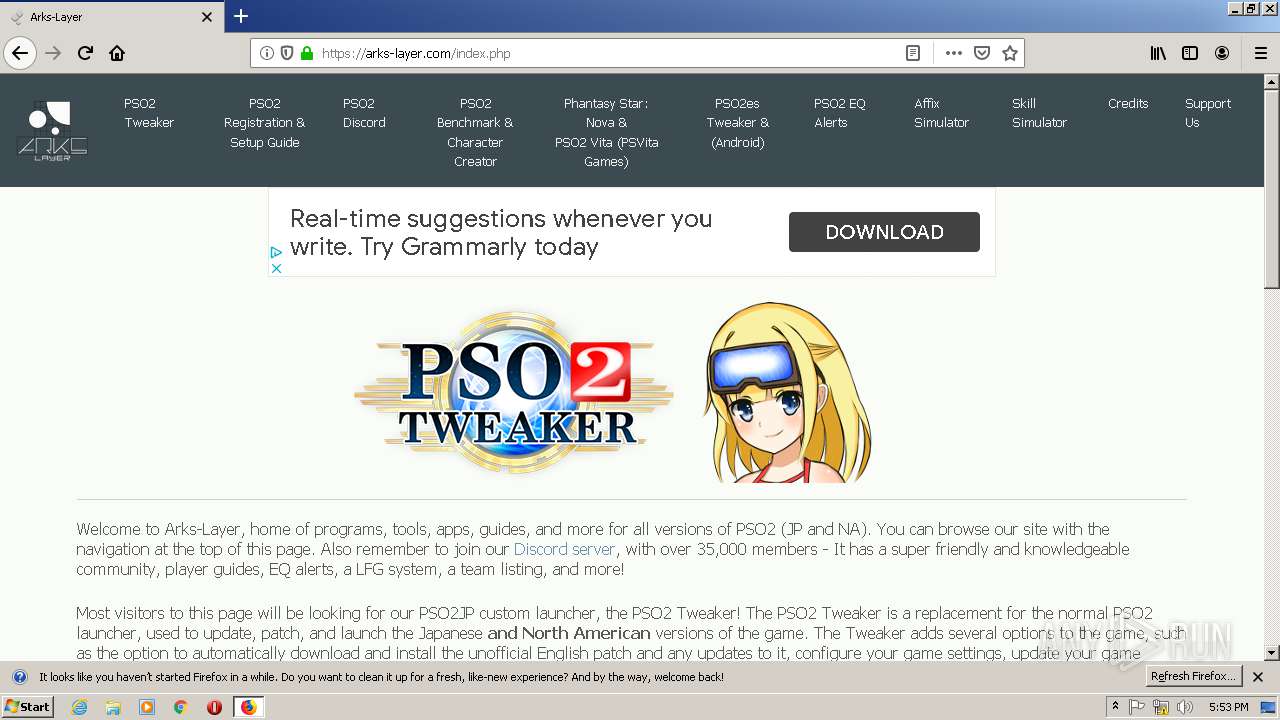
| Title: | Arks-Layer |
| Description: | Home of the PSO2 Tweaker, English patches, Tools, Simulators, Guides, and much more! We support both versions of PSO2 - JP and NA! |
Total processes
56
Monitored processes
14
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | "C:\Program Files\Internet Explorer\iexplore.exe" https://arks-layer.com/tweaker_tutorial_choice.php | C:\Program Files\Internet Explorer\iexplore.exe | — | PSO2 Tweaker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1384 | "C:\PSO2 Tweaker\PSO2 Tweaker.exe" | C:\PSO2 Tweaker\PSO2 Tweaker.exe | — | PSO2 Tweaker.exe | |||||||||||
User: admin Company: Arks-Layer Integrity Level: HIGH Description: PSO2 Tweaker Exit code: 0 Version: 6.0.0.2 Modules
| |||||||||||||||
| 1768 | "C:\PSO2 Tweaker\PSO2 Tweaker.exe" | C:\PSO2 Tweaker\PSO2 Tweaker.exe | — | PSO2_Tweaker_Installerv6_2.exe | |||||||||||
User: admin Company: Arks-Layer Integrity Level: HIGH Description: PSO2 Tweaker Exit code: 0 Version: 6.0.0.2 Modules
| |||||||||||||||
| 2020 | "C:\Users\admin\Downloads\PSO2_Tweaker_Installerv6_2.exe" | C:\Users\admin\Downloads\PSO2_Tweaker_Installerv6_2.exe | firefox.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2252 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3256.0.14375939\90878258" -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3256 "\\.\pipe\gecko-crash-server-pipe.3256" 1172 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2316 | "C:\Program Files\Mozilla Firefox\pingsender.exe" https://incoming.telemetry.mozilla.org/submit/telemetry/1175f9e9-116a-4016-b0eb-5afa8edde64b/main/Firefox/68.0.1/release/20190717172542?v=4 C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\saved-telemetry-pings\1175f9e9-116a-4016-b0eb-5afa8edde64b | C:\Program Files\Mozilla Firefox\pingsender.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2400 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3256.20.496238486\567406842" -childID 3 -isForBrowser -prefsHandle 3728 -prefMapHandle 3736 -prefsLen 7298 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3256 "\\.\pipe\gecko-crash-server-pipe.3256" 3748 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 2800 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\theming.php | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3256 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
Total events
6 719
Read events
1 452
Write events
4 076
Delete events
1 191
Modification events
| (PID) Process: | (3256) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: AED3850000000000 | |||
| (PID) Process: | (2348) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: ADD3850000000000 | |||
| (PID) Process: | (3256) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (3256) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3256) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3256) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3256) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2020) PSO2_Tweaker_Installerv6_2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (2316) pingsender.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2316) pingsender.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
5
Suspicious files
205
Text files
94
Unknown types
103
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3256 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | — | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 3256 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4 | jsonlz4 | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
92
DNS requests
132
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3256 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3256 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 472 b | whitelisted |
3256 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
3256 | firefox.exe | POST | 200 | 52.222.157.101:80 | http://ocsp.sca1b.amazontrust.com/ | US | der | 471 b | whitelisted |
3256 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
3256 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
3256 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
3256 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
3256 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
3256 | firefox.exe | POST | 200 | 172.217.22.99:80 | http://ocsp.pki.goog/gts1o1 | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3256 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3256 | firefox.exe | 52.26.114.88:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3256 | firefox.exe | 172.217.22.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3256 | firefox.exe | 172.217.16.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3256 | firefox.exe | 52.222.149.186:443 | content-signature-2.cdn.mozilla.net | Amazon.com, Inc. | US | whitelisted |
3256 | firefox.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
3256 | firefox.exe | 216.58.210.14:443 | www.youtube.com | Google Inc. | US | whitelisted |
3256 | firefox.exe | 2.16.186.49:443 | shavar.services.mozilla.com | Akamai International B.V. | — | whitelisted |
3256 | firefox.exe | 172.217.22.46:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
3256 | firefox.exe | 216.58.212.131:443 | www.google.co.uk | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
d228z91au11ukj.cloudfront.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1044 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1044 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |