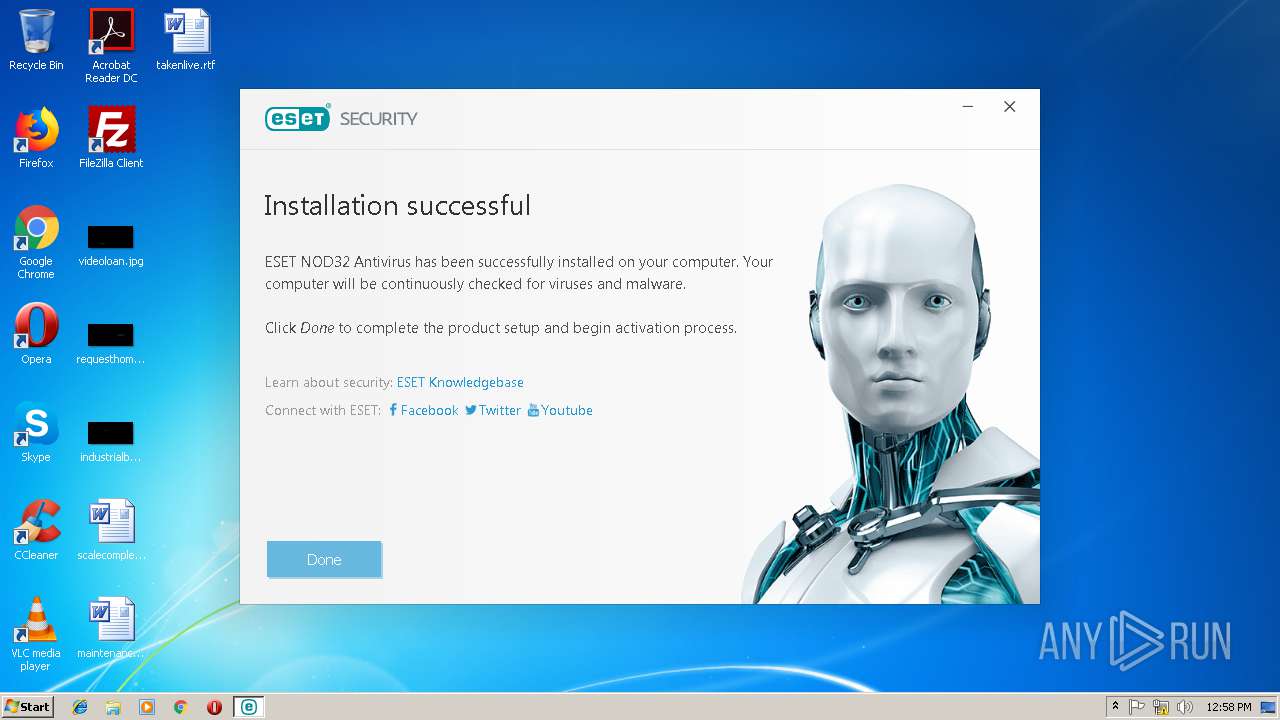
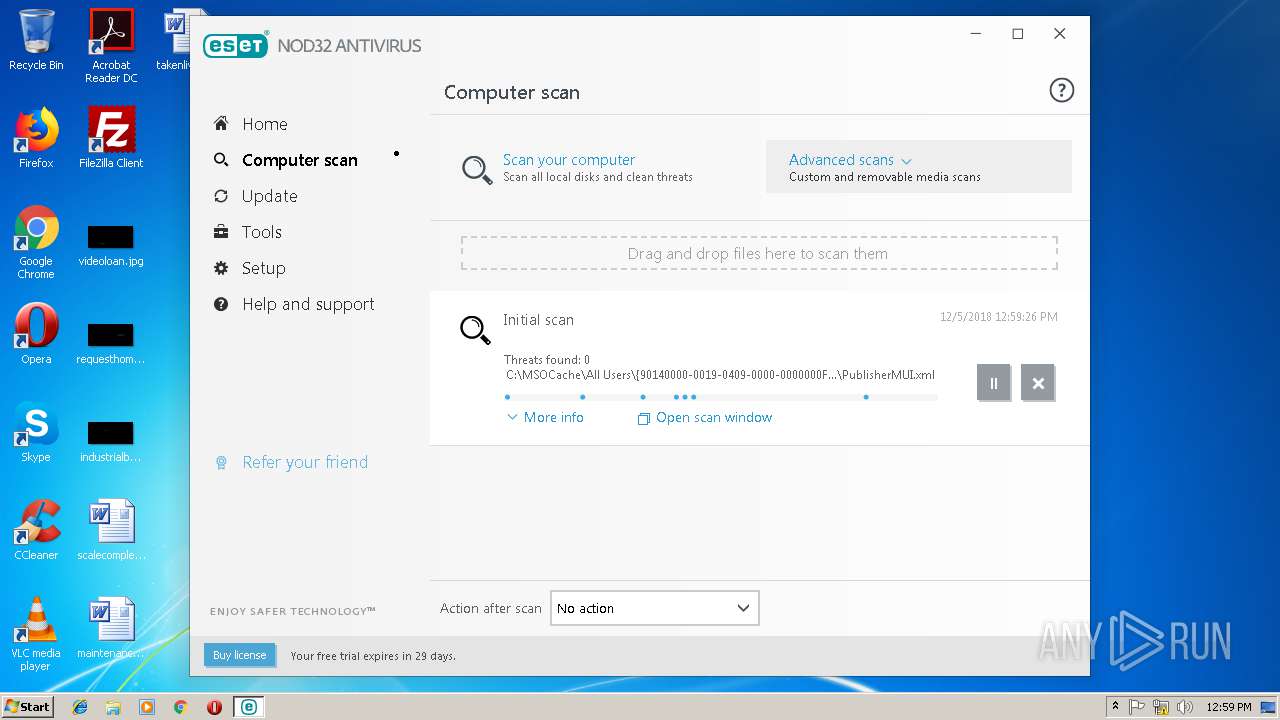
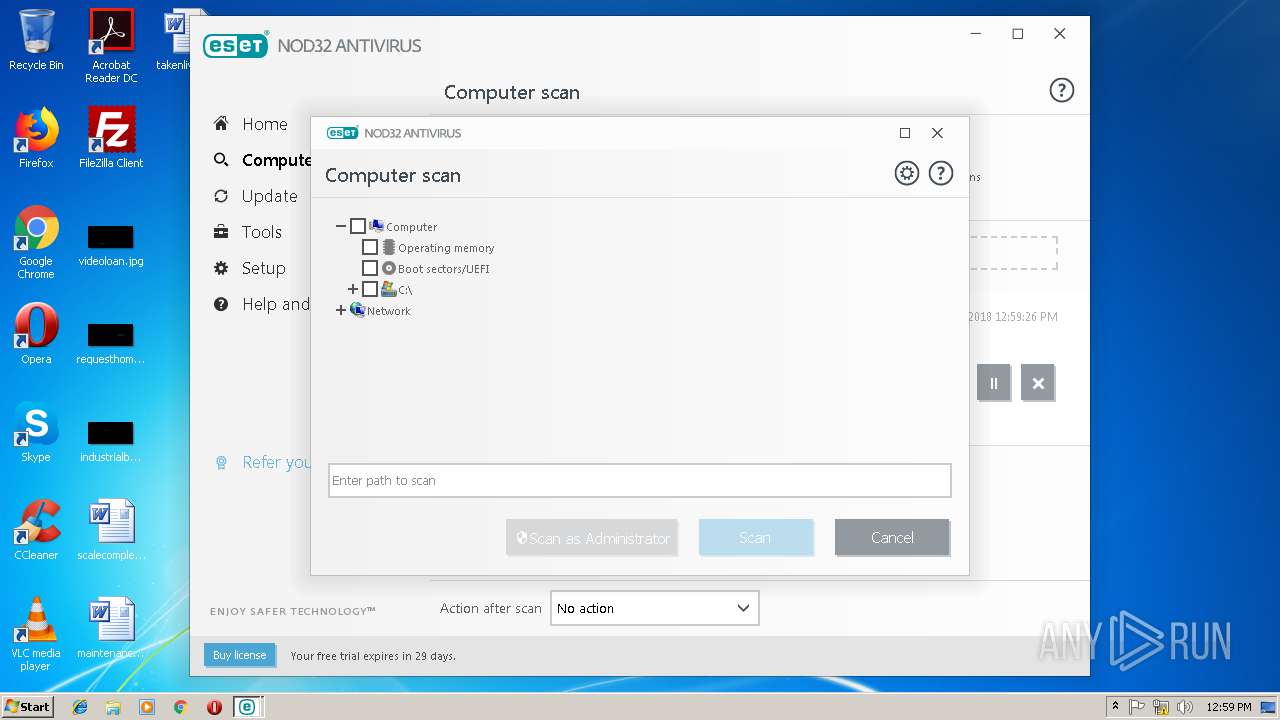
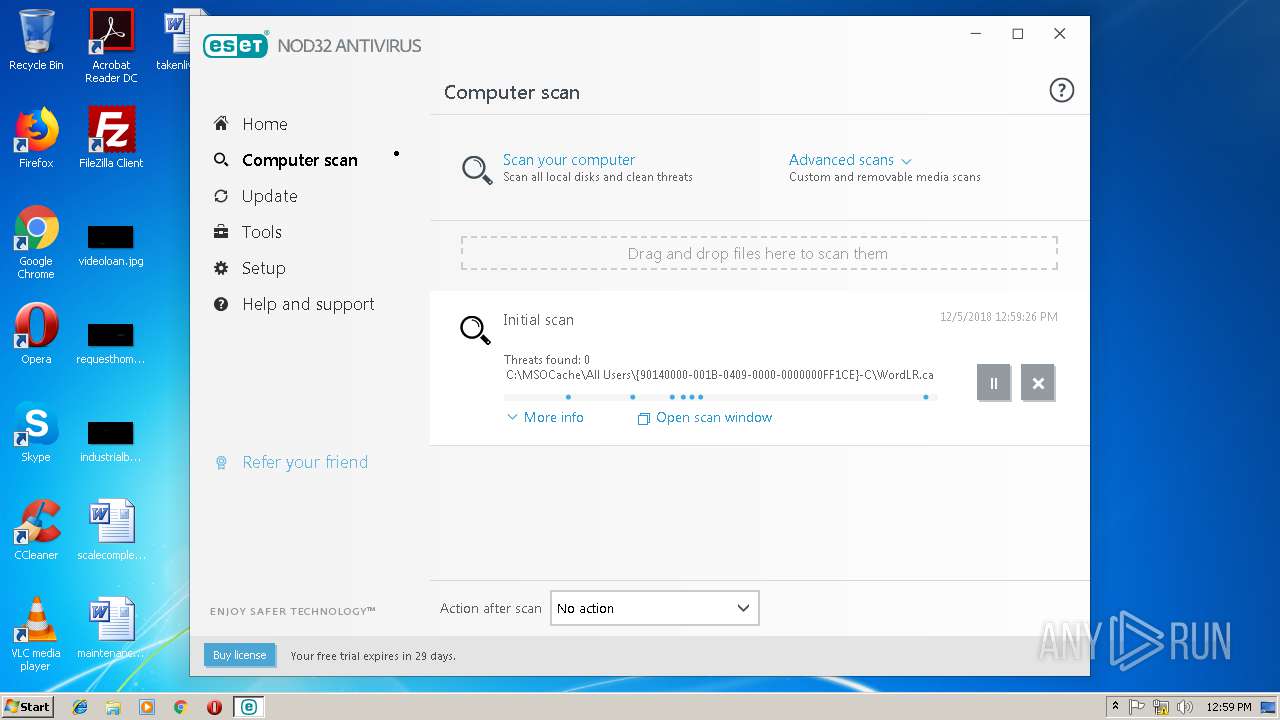
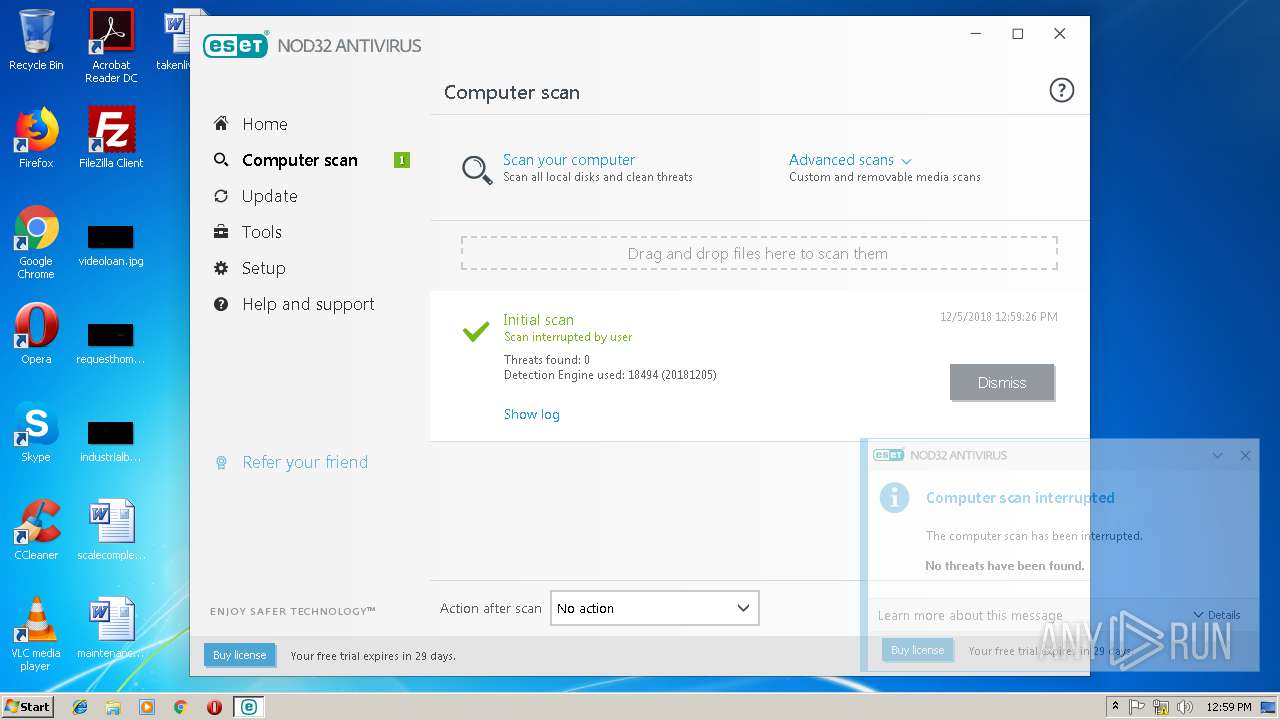
| URL: | https://download.eset.com/com/eset/apps/home/eav/windows/latest/eav_nt32_enu.exe |
| Full analysis: | https://app.any.run/tasks/ee463243-49a7-4cd8-a8b1-978bfd22fe0c |
| Verdict: | Malicious activity |
| Threats: | Trojans are a group of malicious programs distinguished by their ability to masquerade as benign software. Depending on their type, trojans possess a variety of capabilities, ranging from maintaining full remote control over the victim’s machine to stealing data and files, as well as dropping other malware. At the same time, the main functionality of each trojan family can differ significantly depending on its type. The most common trojan infection chain starts with a phishing email. |
| Analysis date: | December 05, 2018, 12:56:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 138845DD114E66AF62BAB6553DC0DD03 |
| SHA1: | 7ADBCD317C087C9E38A8E2832A66C99930B912A6 |
| SHA256: | AFB80F8ECD46CD539ACF24FFEB8EF7344C43E9B357B4FFF07772DFFCE6FB05EA |
| SSDEEP: | 3:N8SElsRLKIIyAsSAbhdJERAW/Mque4An:2SKstKKSAbhdKRQP1An |
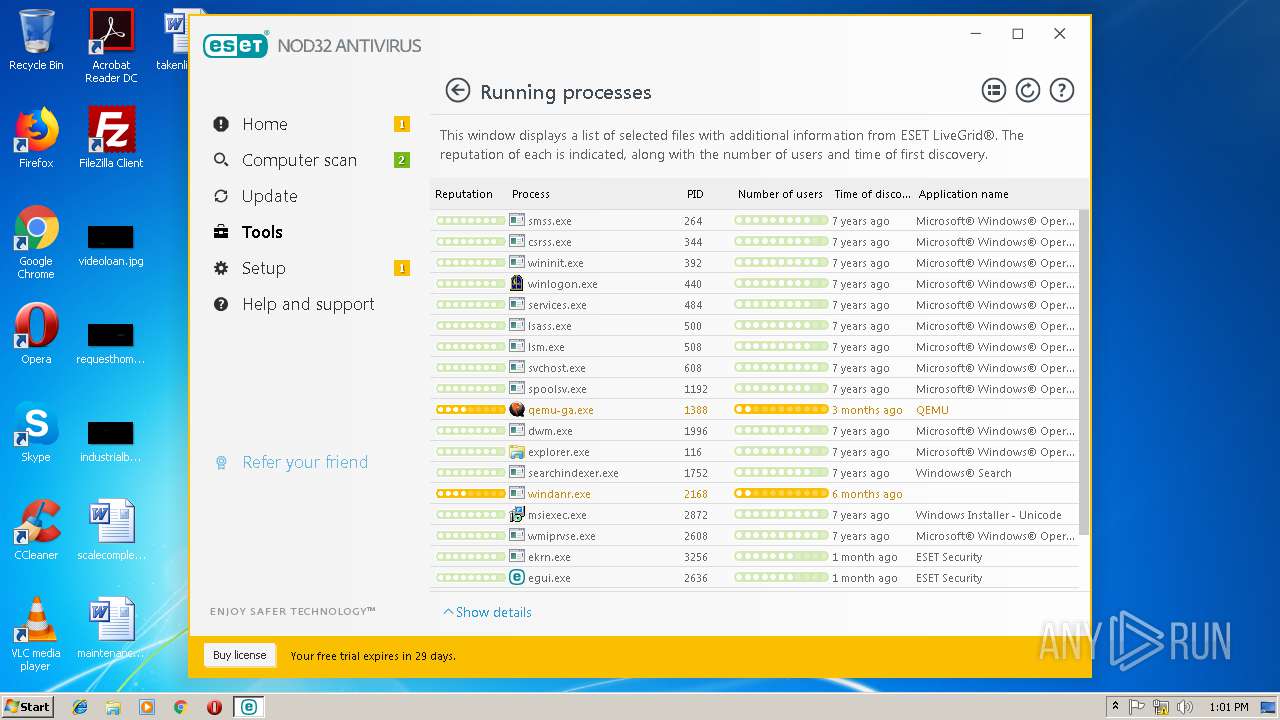
MALICIOUS
Loads dropped or rewritten executable
- eav_nt32_enu[1].exe (PID: 2280)
- InstHelper.exe (PID: 3960)
- ekrn.exe (PID: 3256)
- egui.exe (PID: 2636)
- SysInspector.exe (PID: 2204)
Application was dropped or rewritten from another process
- BootHelper.exe (PID: 3916)
- eav_nt32_enu[1].exe (PID: 2280)
- InstHelper.exe (PID: 3960)
- egui.exe (PID: 2636)
- CertImporter-1501.exe (PID: 2712)
- CertImporter-1501.exe (PID: 3628)
- eeclnt.exe (PID: 3476)
- eeclnt.exe (PID: 2956)
- ekrn.exe (PID: 3256)
- eeclnt.exe (PID: 3604)
- SysInspector.exe (PID: 2204)
Loads the Task Scheduler COM API
- ekrn.exe (PID: 3256)
Changes settings of System certificates
- ekrn.exe (PID: 3256)
Actions looks like stealing of personal data
- ekrn.exe (PID: 3256)
SUSPICIOUS
Executable content was dropped or overwritten
- eav_nt32_enu[1].exe (PID: 3560)
- eav_nt32_enu[1].exe (PID: 2280)
- MsiExec.exe (PID: 3864)
- MsiExec.exe (PID: 2468)
- DrvInst.exe (PID: 4000)
- msiexec.exe (PID: 2872)
- DrvInst.exe (PID: 3196)
- ekrn.exe (PID: 3256)
- DrvInst.exe (PID: 3892)
Uses TASKKILL.EXE to kill process
- MsiExec.exe (PID: 2468)
Creates COM task schedule object
- MsiExec.exe (PID: 2468)
- MsiExec.exe (PID: 3864)
Creates files in the driver directory
- DrvInst.exe (PID: 4000)
- ekrn.exe (PID: 3256)
- DrvInst.exe (PID: 3196)
- DrvInst.exe (PID: 3892)
- DrvInst.exe (PID: 1524)
Creates files in the Windows directory
- DrvInst.exe (PID: 4000)
- DrvInst.exe (PID: 3196)
- DrvInst.exe (PID: 3892)
- ekrn.exe (PID: 3256)
- DrvInst.exe (PID: 1524)
Removes files from Windows directory
- DrvInst.exe (PID: 4000)
- DrvInst.exe (PID: 3196)
- DrvInst.exe (PID: 3892)
- ekrn.exe (PID: 3256)
- DrvInst.exe (PID: 1524)
- SysInspector.exe (PID: 2204)
Creates or modifies windows services
- ekrn.exe (PID: 3256)
Searches for installed software
- CertImporter-1501.exe (PID: 2712)
- CertImporter-1501.exe (PID: 3628)
- ekrn.exe (PID: 3256)
- SysInspector.exe (PID: 2204)
Writes to a desktop.ini file (may be used to cloak folders)
- ekrn.exe (PID: 3256)
Loads DLL from Mozilla Firefox
- CertImporter-1501.exe (PID: 2712)
Creates files in the user directory
- CertImporter-1501.exe (PID: 2712)
Low-level read access rights to disk partition
- ekrn.exe (PID: 3256)
Adds / modifies Windows certificates
- ekrn.exe (PID: 3256)
Creates files in the program directory
- ekrn.exe (PID: 3256)
Reads the cookies of Mozilla Firefox
- ekrn.exe (PID: 3256)
Reads the cookies of Google Chrome
- ekrn.exe (PID: 3256)
Changes the autorun value in the registry
- msiexec.exe (PID: 2872)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2836)
Application launched itself
- iexplore.exe (PID: 2836)
- msiexec.exe (PID: 2872)
Reads Internet Cache Settings
- iexplore.exe (PID: 3376)
- iexplore.exe (PID: 2836)
Reads settings of System Certificates
- eav_nt32_enu[1].exe (PID: 2280)
- ekrn.exe (PID: 3256)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2060)
- MsiExec.exe (PID: 3864)
- MsiExec.exe (PID: 2468)
Creates files in the program directory
- MsiExec.exe (PID: 2468)
- MsiExec.exe (PID: 3864)
- msiexec.exe (PID: 2872)
Reads Microsoft Office registry keys
- ekrn.exe (PID: 3256)
Creates a software uninstall entry
- msiexec.exe (PID: 2872)
- MsiExec.exe (PID: 2468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
74
Monitored processes
24
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1524 | DrvInst.exe "4" "8" "C:\Windows\TEMP\{081bdfeb-296e-63c3-7c69-474307705422}\edevmon.inf" "0" "68c1400ab" "000004C0" "WinSta0\Default" "000003F0" "208" "C:\Program Files\ESET\ESET Security\Drivers\edevmon" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2060 | C:\Windows\system32\MsiExec.exe -Embedding D92747631CB4AAA8852954FC51A5DC27 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2204 | "C:\Program Files\ESET\ESET Security\SysInspector.exe" /gen="C:\Windows\TEMP\SysInspector-USER-PC-181205-130152.xml" /supersilent /wantcloud | C:\Program Files\ESET\ESET Security\SysInspector.exe | — | ekrn.exe | |||||||||||
User: SYSTEM Company: ESET Integrity Level: SYSTEM Description: ESET SysInspector - System Analyzer Tool Exit code: 0 Version: 10.6.205.0 Modules
| |||||||||||||||
| 2280 | "C:\Users\admin\AppData\Local\Temp\eset\bts.session\{823031BE-FAF1-F4D4-B973-D52AA1F42769}\eav_nt32_enu[1].exe" --bts-container 3560 "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\eav_nt32_enu[1].exe" | C:\Users\admin\AppData\Local\Temp\eset\bts.session\{823031BE-FAF1-F4D4-B973-D52AA1F42769}\eav_nt32_enu[1].exe | eav_nt32_enu[1].exe | ||||||||||||
User: admin Company: ESET Integrity Level: HIGH Description: ESET Security Exit code: 0 Version: 10.6.205.0 Modules
| |||||||||||||||
| 2468 | C:\Windows\system32\MsiExec.exe -Embedding A722C1E95D72BC128C17A4BB71E117E1 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2636 | "C:\Program Files\ESET\ESET Security\egui.exe" /hide | C:\Program Files\ESET\ESET Security\egui.exe | — | ekrn.exe | |||||||||||
User: admin Company: ESET Integrity Level: MEDIUM Description: ESET Main GUI Exit code: 0 Version: 10.6.205.0 Modules
| |||||||||||||||
| 2712 | "C:\Program Files\ESET\ESET Security\CertImporter-1501.exe" ImportCertificate 1 "C:\Users\admin\AppData\Roaming" | C:\Program Files\ESET\ESET Security\CertImporter-1501.exe | — | ekrn.exe | |||||||||||
User: admin Company: ESET Integrity Level: MEDIUM Description: ESET SSL filtering certificate importer Exit code: 0 Version: 1.0.10.0 Modules
| |||||||||||||||
| 2724 | C:\Windows\system32\DllHost.exe /Processid:{B366DEBE-645B-43A5-B865-DDD82C345492} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Internet Explorer\iexplore.exe" https://download.eset.com/com/eset/apps/home/eav/windows/latest/eav_nt32_enu.exe | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2872 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 816
Read events
3 692
Write events
1 099
Delete events
25
Modification events
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {3E9B349D-F88D-11E8-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2836) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C00030005000C00380039006901 | |||
Executable files
252
Suspicious files
146
Text files
314
Unknown types
49
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFD4A46DE845DB0895.TMP | — | |
MD5:— | SHA256:— | |||
| 3376 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\eav_nt32_enu[1].exe | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\eav_nt32_enu[1].exe | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFB8939D236B90754D.TMP | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{3E9B349D-F88D-11E8-BAD8-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{3E9B349E-F88D-11E8-BAD8-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3376 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\JavaDeployReg.log | text | |
MD5:— | SHA256:— | |||
| 3376 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012018120520181206\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2836 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2836 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3376 | iexplore.exe | 91.228.167.110:443 | download.eset.com | ESET, spol. s r.o. | SK | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.eset.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3256 | ekrn.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious loader with tiny header |