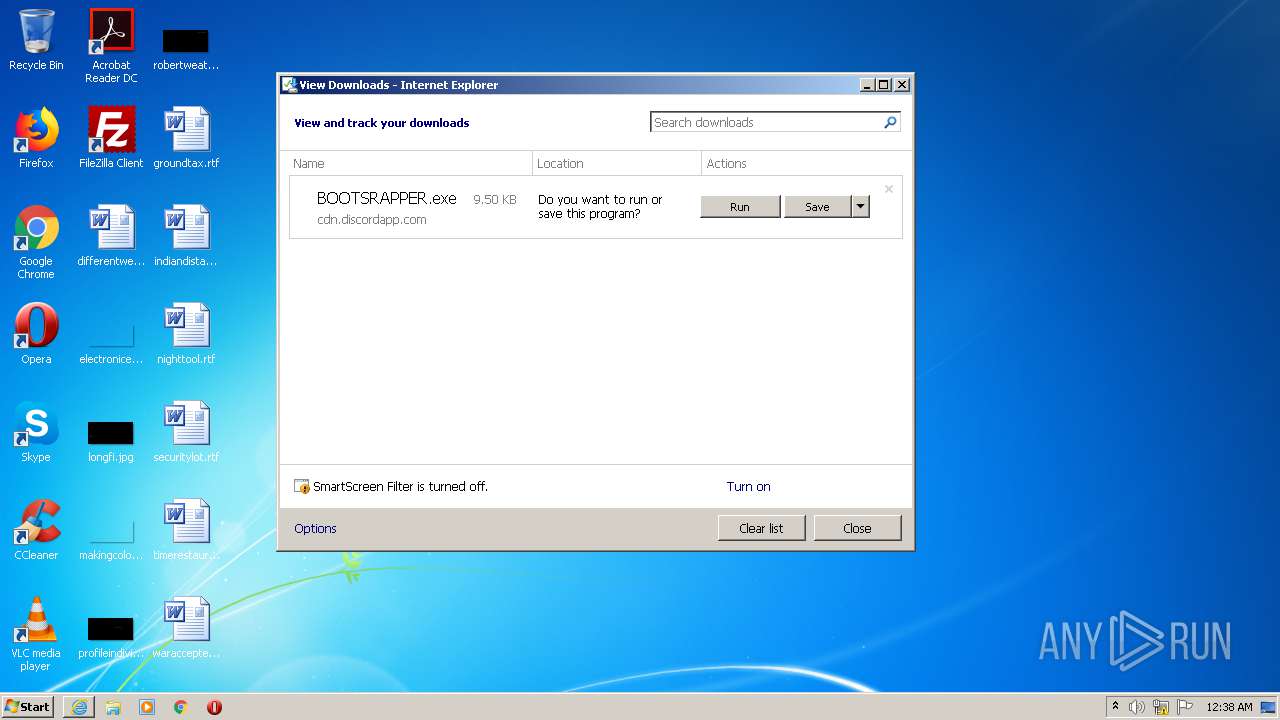
| URL: | https://api.thinksuggest.org/?m=c&t=j&h=Jump&q=_clickout&pid=linkvertisenet&k=https%3A%2F%2Fcdn.discordapp.com%2Fattachments%2F761329835183833148%2F768171536602497034%2FBOOTSRAPPER.exe&subid=klickouts |
| Full analysis: | https://app.any.run/tasks/bdadbee4-f450-4b90-b319-41eedf382ab4 |
| Verdict: | Suspicious activity |
| Analysis date: | October 28, 2020, 00:37:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4D7E74A5412F00685CD59BB657A881AF |
| SHA1: | D101ED33956475EA6125E1813F6686369909960C |
| SHA256: | AFACCCC11352AB63080DF57F67508D9FEE5209BF2487F9108207DBC35BCC1C07 |
| SSDEEP: | 6:2XY9Bn1Vl6G05CLRiQzKDyoVmK8gQ4RRFqkQoMGOM:2XK1Vl6aEQOlVHecRioMGN |
MALICIOUS
Application was dropped or rewritten from another process
- BOOTSRAPPER.exe (PID: 4092)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 1340)
- iexplore.exe (PID: 1036)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1036)
- iexplore.exe (PID: 1340)
- iexplore.exe (PID: 1704)
- iexplore.exe (PID: 2548)
Reads settings of System Certificates
- iexplore.exe (PID: 1340)
- iexplore.exe (PID: 1036)
Application launched itself
- iexplore.exe (PID: 1036)
- iexplore.exe (PID: 1704)
Reads internet explorer settings
- iexplore.exe (PID: 1340)
- iexplore.exe (PID: 2548)
Changes internet zones settings
- iexplore.exe (PID: 1036)
- iexplore.exe (PID: 1704)
Creates files in the user directory
- iexplore.exe (PID: 1340)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1036)
Changes settings of System certificates
- iexplore.exe (PID: 1036)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1036)
Manual execution by user
- explorer.exe (PID: 2084)
- iexplore.exe (PID: 1704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://api.thinksuggest.org/?m=c&t=j&h=Jump&q=_clickout&pid=linkvertisenet&k=https%3A%2F%2Fcdn.discordapp.com%2Fattachments%2F761329835183833148%2F768171536602497034%2FBOOTSRAPPER.exe&subid=klickouts" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1340 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1036 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2084 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2548 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1704 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
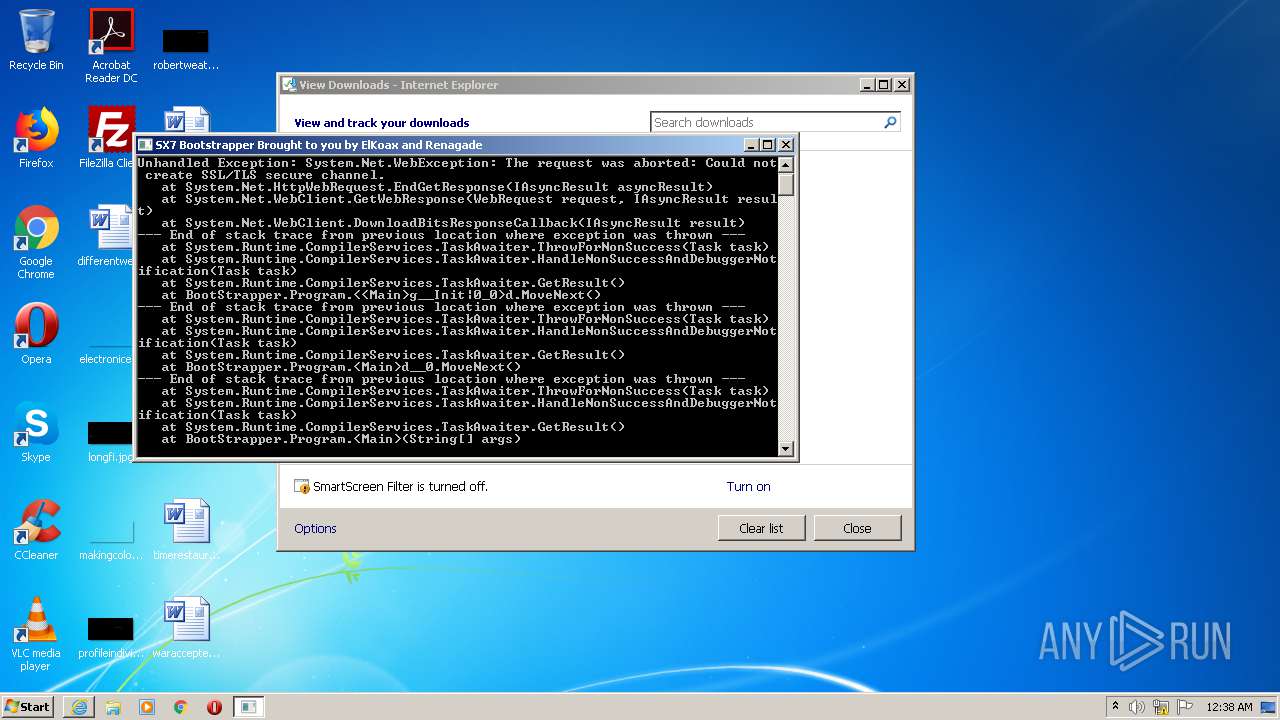
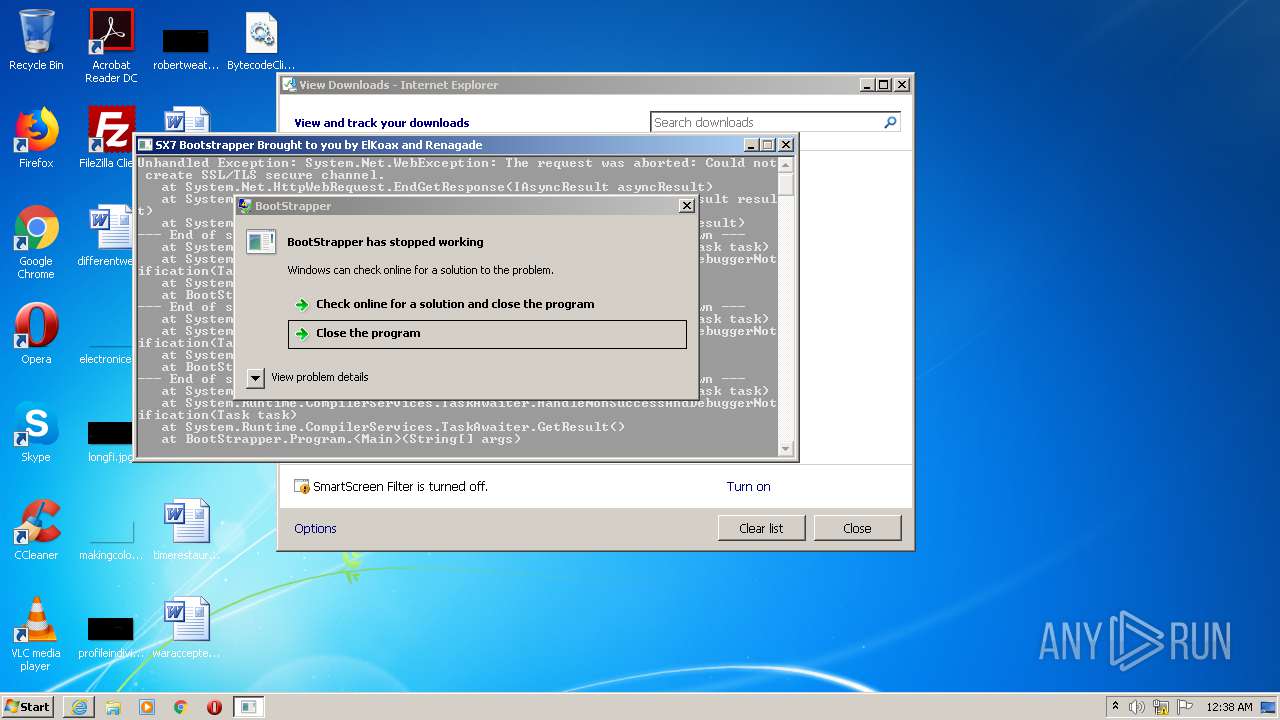
| 4092 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\BOOTSRAPPER.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\BOOTSRAPPER.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: BootStrapper Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 344
Read events
1 187
Write events
155
Delete events
2
Modification events
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2757527534 | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30846146 | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1036) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
19
Text files
5
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1340 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab50B8.tmp | — | |
MD5:— | SHA256:— | |||
| 1340 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar50B9.tmp | — | |
MD5:— | SHA256:— | |||
| 1036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1036 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF244579A185CCA62.TMP | — | |
MD5:— | SHA256:— | |||
| 1340 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\BOOTSRAPPER.exe.kvw4o8w.partial | — | |
MD5:— | SHA256:— | |||
| 1036 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF4C53EF0B23280E8C.TMP | — | |
MD5:— | SHA256:— | |||
| 1036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\BOOTSRAPPER.exe.kvw4o8w.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 1340 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | der | |
MD5:— | SHA256:— | |||
| 1340 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_979AB563CEB98F2581C14ED89B8957D4 | der | |
MD5:— | SHA256:— | |||
| 1340 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\64DCC9872C5635B1B7891B30665E0558_5552C20A2631357820903FD38A8C0F9F | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
25
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1340 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgS02keKM8ero2ceggVTfL88Xg%3D%3D | unknown | der | 527 b | whitelisted |
1340 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
1340 | iexplore.exe | GET | 200 | 192.35.177.64:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
1340 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 313 b | whitelisted |
1340 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQD5g7jF84adhvw3B5kCUueb | US | der | 281 b | whitelisted |
1036 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1340 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
1340 | iexplore.exe | GET | 301 | 176.9.175.234:80 | http://clk.thinksuggest.org/redir/clickGate.php?u=58U9s81D&m=15&p=6A9n9br68J&t=658&s=jdiscorda-34a7bde3ac&url=https%3A%2F%2Fcdn.discordapp.com%2Fattachments%2F761329835183833148%2F768171536602497034%2FBOOTSRAPPER.exe&q=_clickout&r=https%3A%2F%2Fapi.thinksuggest.org%2F%3Fm%3Dc%26t%3Dj%26h%3DJump%26q%3D_clickout%26pid%3Dlinkvertisenet%26k%3Dhttps%253A%252F%252Fcdn.discordapp.com%252Fattachments%252F761329835183833148%252F768171536602497034%252FBOOTSRAPPER.exe%26subid%3Dklickouts | DE | html | 178 b | malicious |
1036 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1340 | iexplore.exe | GET | 200 | 2.16.186.35:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1340 | iexplore.exe | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
1340 | iexplore.exe | 176.9.175.234:443 | api.thinksuggest.org | Hetzner Online GmbH | DE | malicious |
1340 | iexplore.exe | 176.9.175.234:80 | api.thinksuggest.org | Hetzner Online GmbH | DE | malicious |
1036 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1340 | iexplore.exe | 192.35.177.64:80 | crl.identrust.com | IdenTrust | US | malicious |
1340 | iexplore.exe | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
1340 | iexplore.exe | 162.159.129.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
1340 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
4092 | BOOTSRAPPER.exe | 185.221.216.5:443 | koaxyhosting.site | — | — | suspicious |
1036 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.thinksuggest.org |
| suspicious |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
clk.thinksuggest.org |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
cdn.discordapp.com |
| shared |
ocsp.comodoca.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |