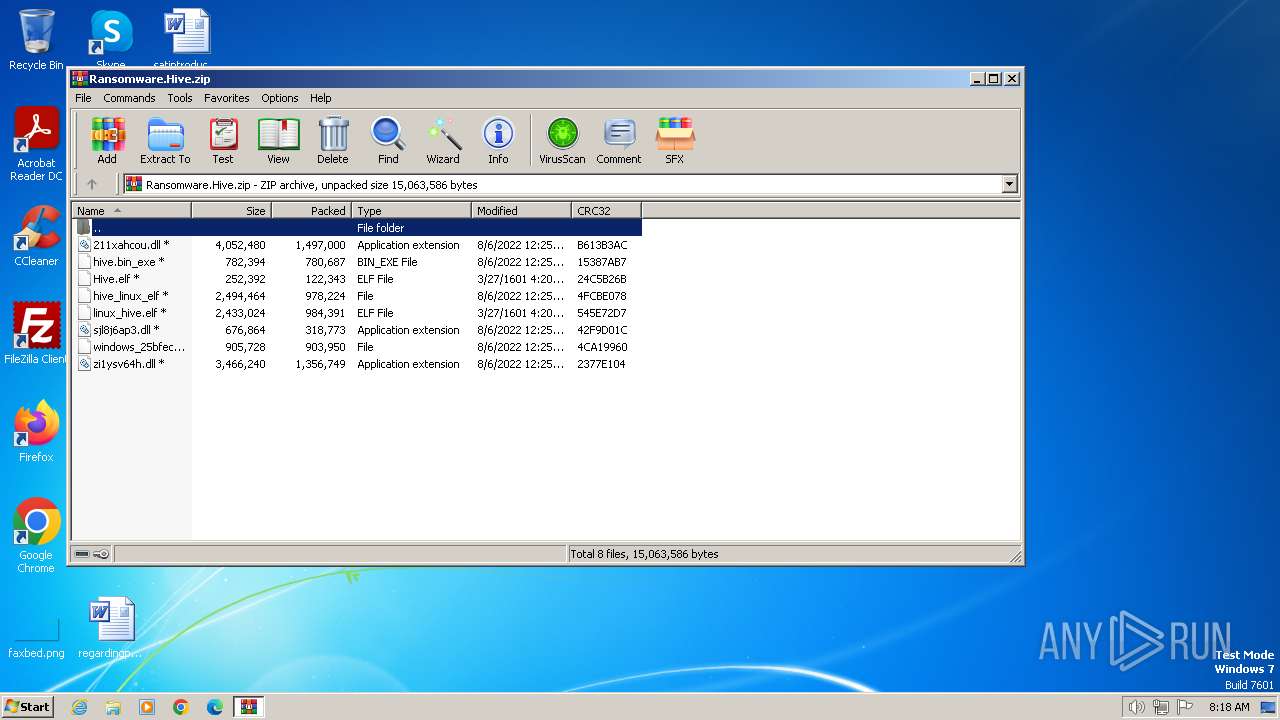
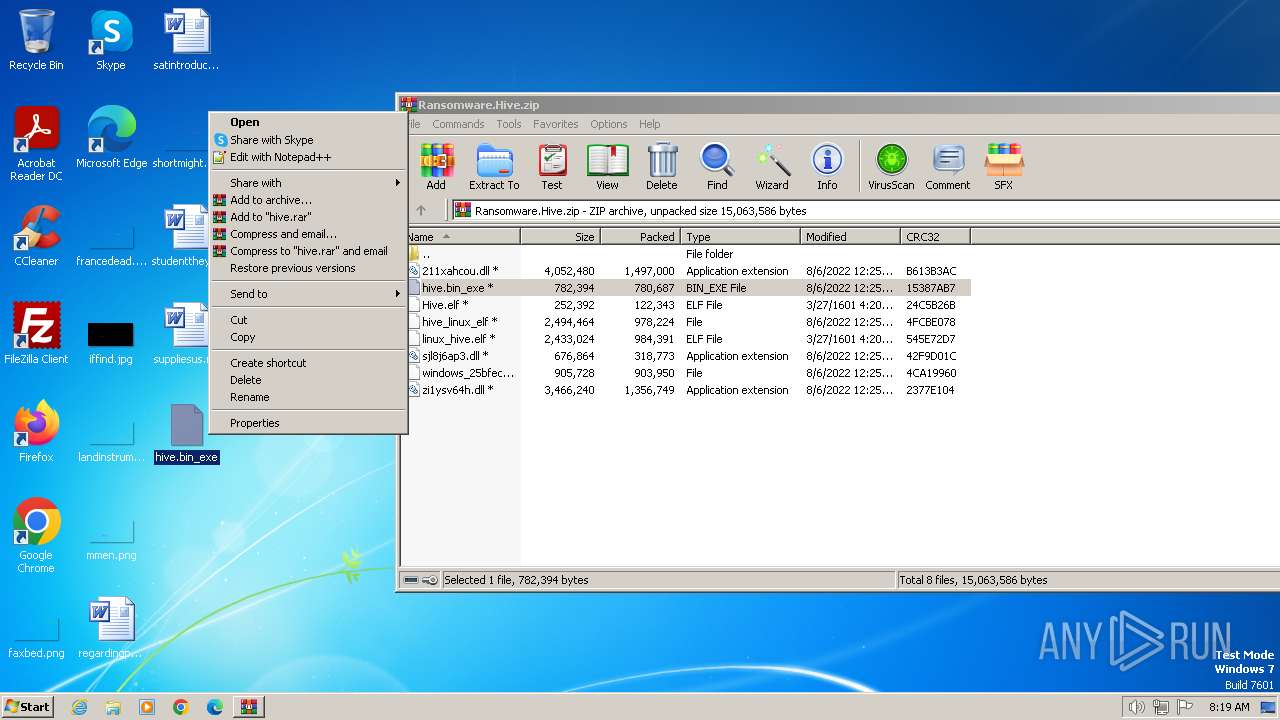
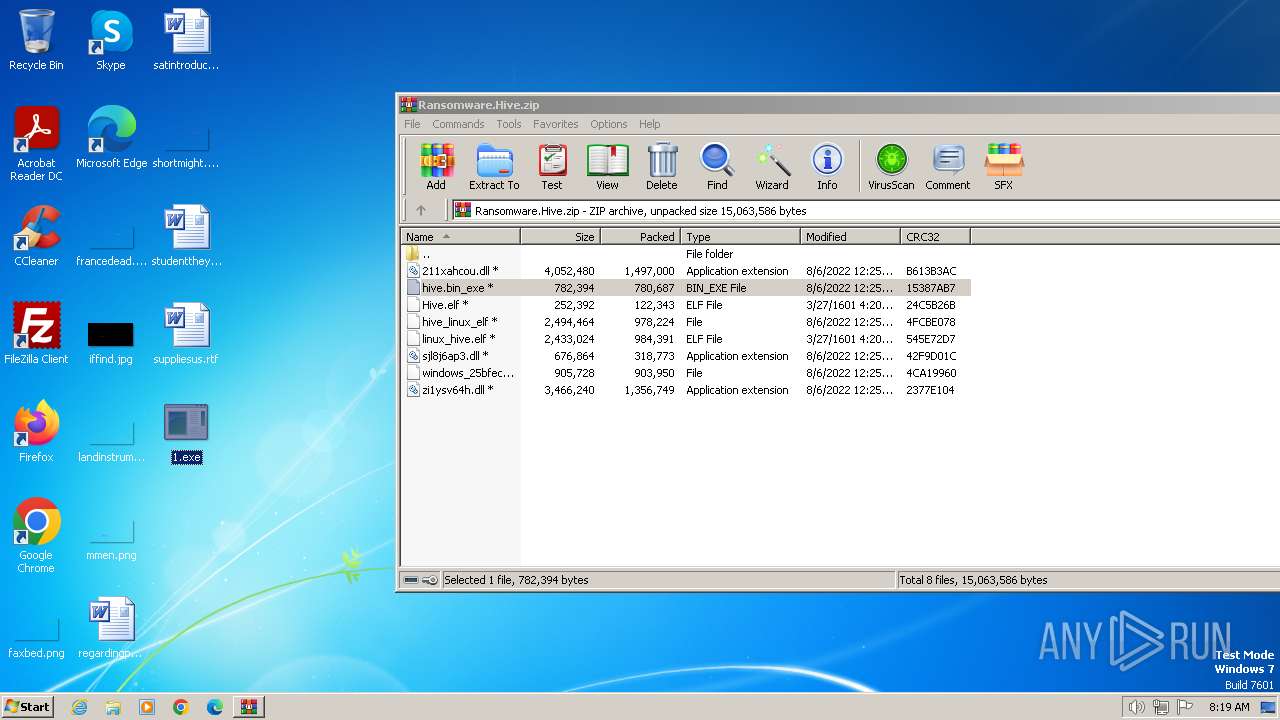
| File name: | Ransomware.Hive.zip |
| Full analysis: | https://app.any.run/tasks/ec801fa4-1a60-4700-b43c-b0afce88f873 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2024, 08:18:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 33DC6CF9108FA7A395D632C29021791C |
| SHA1: | 61CCFFBFB8F2458BE139AA1D3C9DD715F25CD06D |
| SHA256: | AF9E8F301A3677B457345921D7EE765A842ECEB7DF107714EAFFC6193BFC6BBE |
| SSDEEP: | 196608:xUPLIETGA/+0vcL5o/Vu0vlQ77Z0SOJM7j:xmJ6ANa6/Vu0q3+SOw |
MALICIOUS
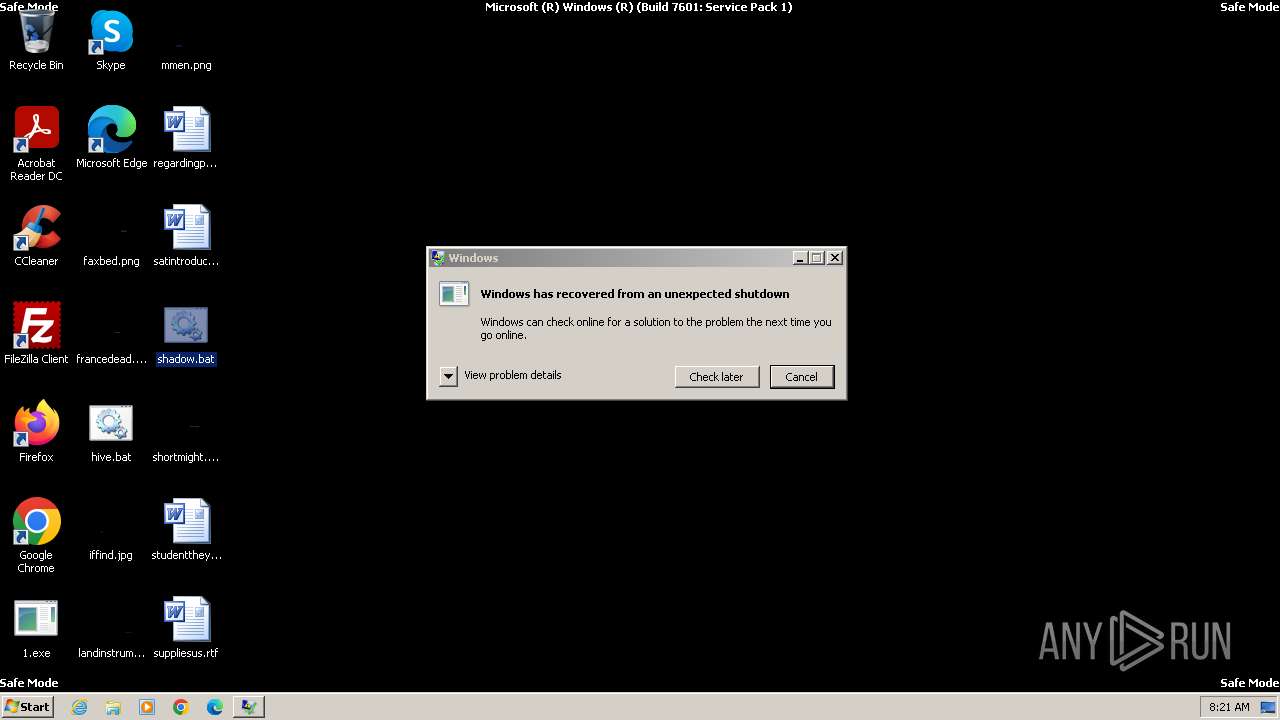
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3700)
- 1.exe (PID: 3304)
Deletes shadow copies
- cmd.exe (PID: 2792)
- cmd.exe (PID: 844)
SUSPICIOUS
Executing commands from a ".bat" file
- 1.exe (PID: 3304)
- 1.exe (PID: 3960)
Starts CMD.EXE for commands execution
- 1.exe (PID: 3304)
- 1.exe (PID: 3960)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2668)
- cmd.exe (PID: 2672)
Executable content was dropped or overwritten
- 1.exe (PID: 3304)
- 1.exe (PID: 3960)
Executes as Windows Service
- VSSVC.exe (PID: 128)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3288)
- 1.exe (PID: 3304)
- 1.exe (PID: 3960)
Reads the computer name
- wmpnscfg.exe (PID: 3288)
- 1.exe (PID: 3304)
- 1.exe (PID: 3960)
Manual execution by a user
- 1.exe (PID: 3304)
- 1.exe (PID: 3960)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3700)
Creates files or folders in the user directory
- 1.exe (PID: 3304)
Creates files in the program directory
- 1.exe (PID: 3960)
Dropped object may contain TOR URL's
- 1.exe (PID: 3960)
- 1.exe (PID: 3304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2022:08:06 14:25:50 |
| ZipCRC: | 0x15387ab7 |
| ZipCompressedSize: | 780687 |
| ZipUncompressedSize: | 782394 |
| ZipFileName: | hive.bin_exe |
Total processes
88
Monitored processes
42
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 844 | C:\Windows\system32\cmd.exe /c shadow.bat >NUL 2>NUL | C:\Windows\System32\cmd.exe | — | 1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1036 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1340 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1624 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 711
Read events
4 699
Write events
12
Delete events
0
Modification events
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ransomware.Hive.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
60
Suspicious files
16
Text files
814
Unknown types
156
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3304 | 1.exe | C:\Users\admin\AppData\Local\VirtualStore\8nA8ackAXsGhP37KPvajsw.key.hive | — | |
MD5:— | SHA256:— | |||
| 3304 | 1.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccLR.cab.8nA8ackAXsGhP37KPvajs4JCcJyBmuAITikm2pUXMlk.hive | — | |
MD5:— | SHA256:— | |||
| 3304 | 1.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccLR.cab.8nA8ackAXsGhP37KPvajs_gv7pJQjaVOIgquebmL2wA.hive | — | |
MD5:— | SHA256:— | |||
| 3304 | 1.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\desktop.ini.8nA8ackAXsGhP37KPvajs6Lzr65sqDkc4IxMdNW-wgs.hive | text | |
MD5:A526B9E7C716B3489D8CC062FBCE4005 | SHA256:E1B9CE9B57957B1A0607A72A057D6B7A9B34EA60F3F8AA8F38A3AF979BD23066 | |||
| 3700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3700.41924\hive.bin_exe | executable | |
MD5:2F9FC82898D718F2ABE99C4A6FA79E69 | SHA256:88F7544A29A2CEB175A135D9FA221CBFD3E8C71F32DD6B09399717F85EA9AFD1 | |||
| 3304 | 1.exe | C:\MSOCache\HOW_TO_DECRYPT.txt | text | |
MD5:80207D0F8EA42BDFEAF9F5C586230ACA | SHA256:25EDEFB3B0678DFE0D927FF48CE67254359BA379DF9468F634D02C026F0E7131 | |||
| 3304 | 1.exe | C:\MSOCache\All Users\HOW_TO_DECRYPT.txt | text | |
MD5:80207D0F8EA42BDFEAF9F5C586230ACA | SHA256:25EDEFB3B0678DFE0D927FF48CE67254359BA379DF9468F634D02C026F0E7131 | |||
| 3304 | 1.exe | C:\Users\admin\Desktop\hive.bat | text | |
MD5:BA80A2F3445765F6C6120CA6DD794F17 | SHA256:A40FDE5BE434D3AA782ADA5DEABE126AB4EA0D0FC0445407393C650DDEB6C622 | |||
| 3304 | 1.exe | C:\Users\admin\Desktop\shadow.bat | text | |
MD5:DF5552357692E0CBA5E69F8FBF06ABB6 | SHA256:D158F9D53E7C37EADD3B5CC1B82D095F61484E47EDA2C36D9D35F31C0B4D3FF8 | |||
| 3304 | 1.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\HOW_TO_DECRYPT.txt | text | |
MD5:80207D0F8EA42BDFEAF9F5C586230ACA | SHA256:25EDEFB3B0678DFE0D927FF48CE67254359BA379DF9468F634D02C026F0E7131 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |