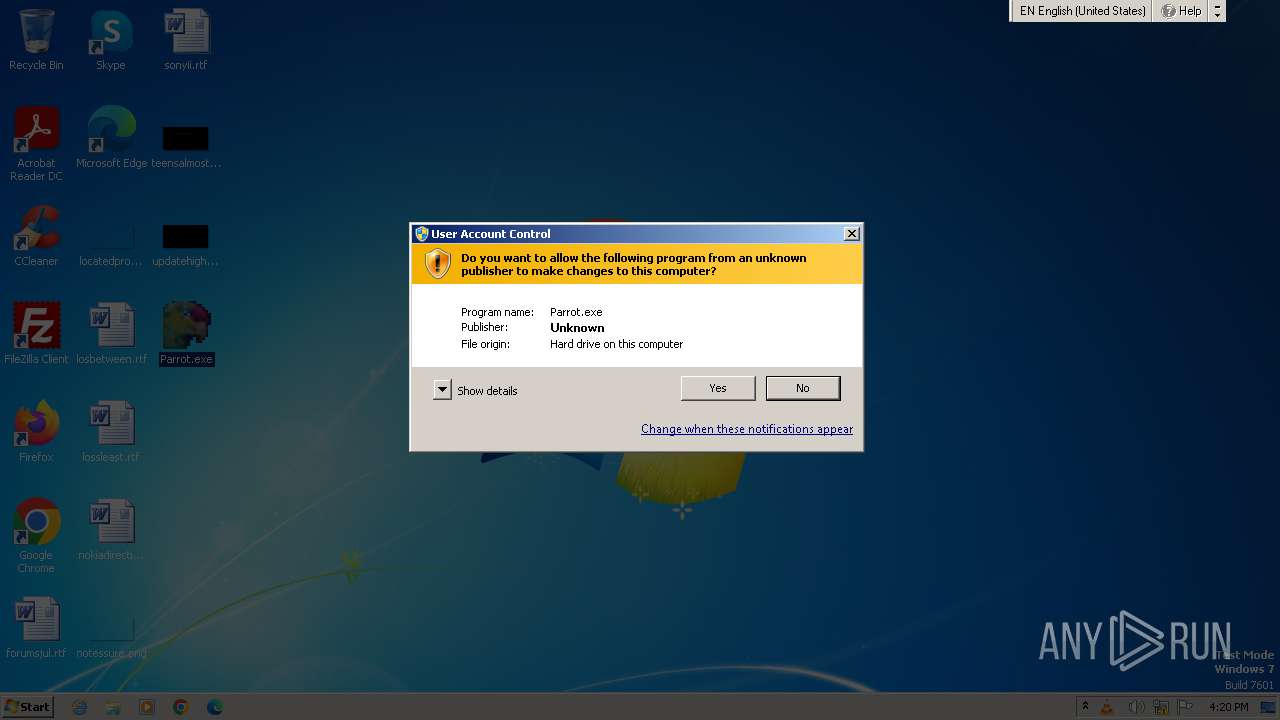
| File name: | Parrot.exe |
| Full analysis: | https://app.any.run/tasks/3a3c8f60-b76e-432f-b4fc-ede13a776679 |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2024, 15:19:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 73D35451DBFBBA5AC051D36F095A629F |
| SHA1: | 0A1C087E6F91506F96E284B89D99A283D650DE07 |
| SHA256: | AF983D2BF8F90FE563159983521B110E8560A409391254CB8BA7662DF88FA3C3 |
| SSDEEP: | 1536:oASnrpNHt9bUYoWdbdb+VEkr+WXdHvcD:oVp5tRUY7HW9cD |
MALICIOUS
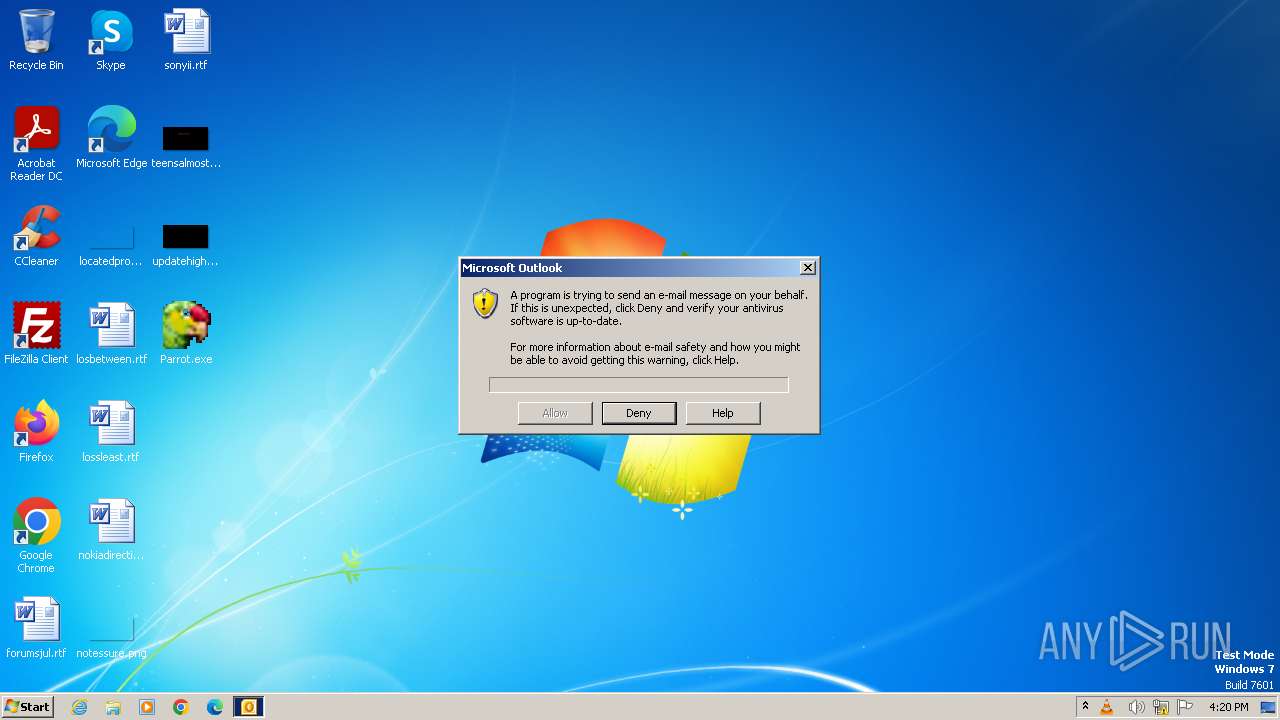
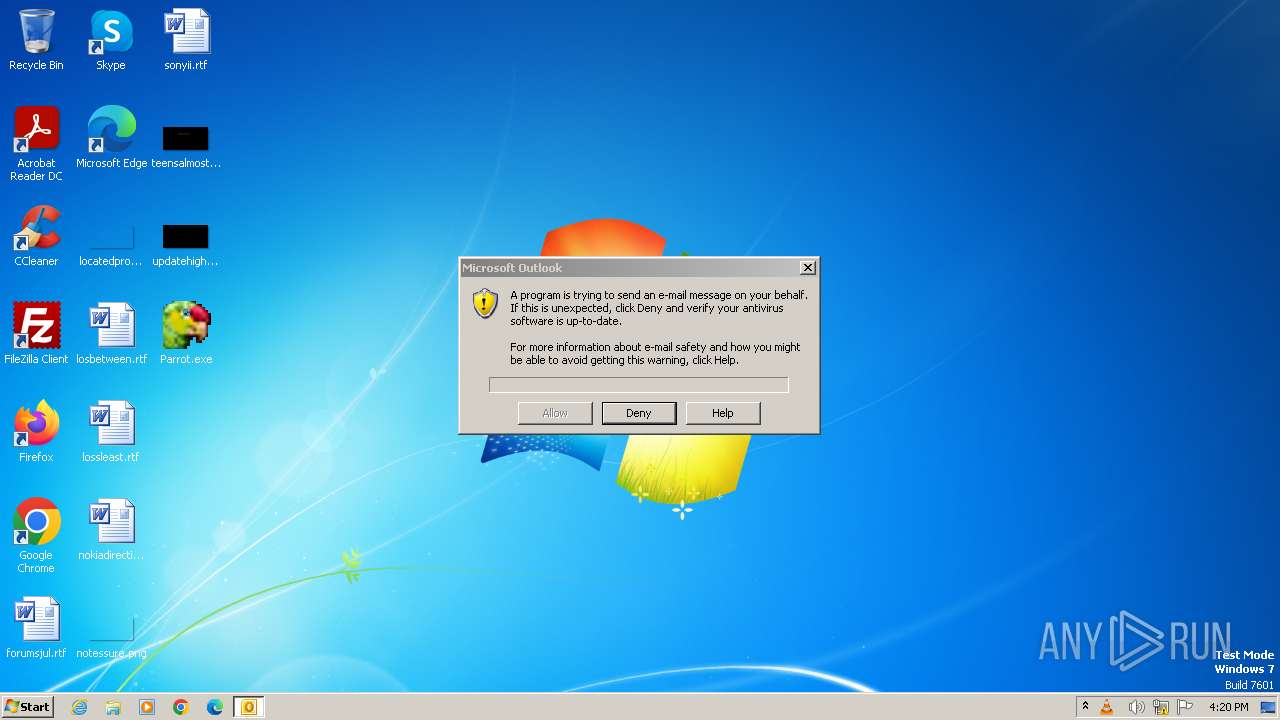
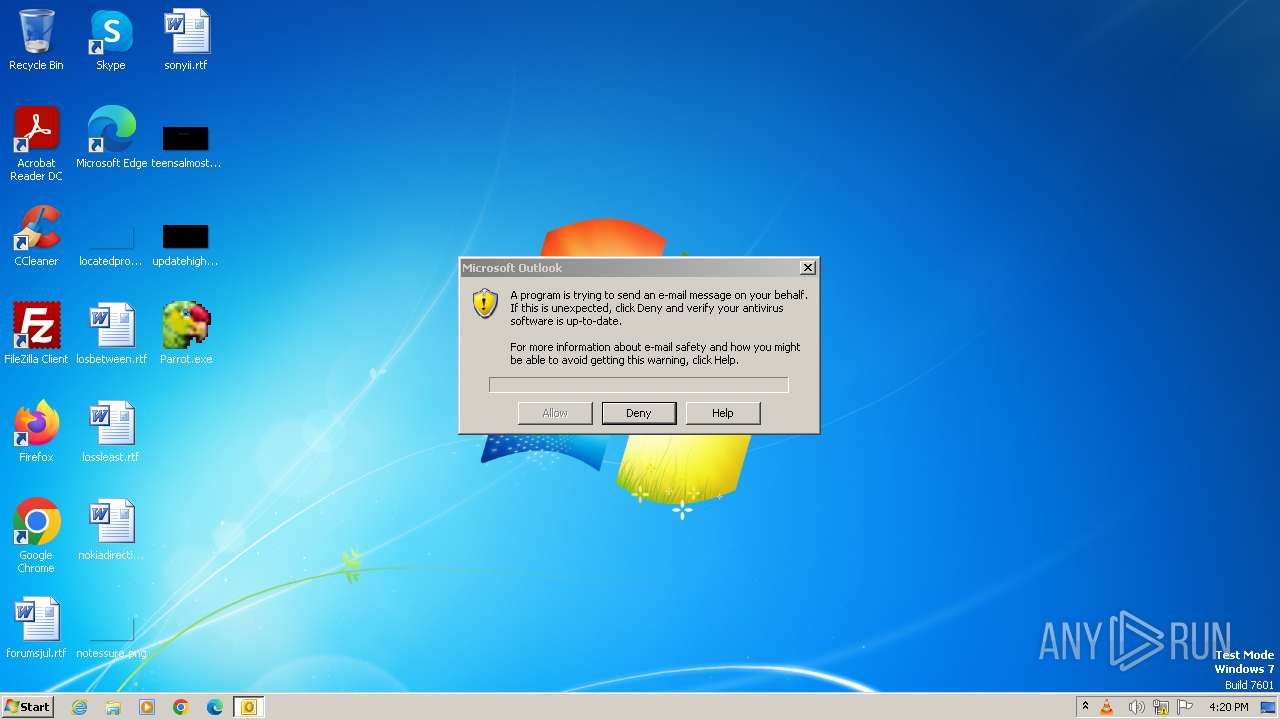
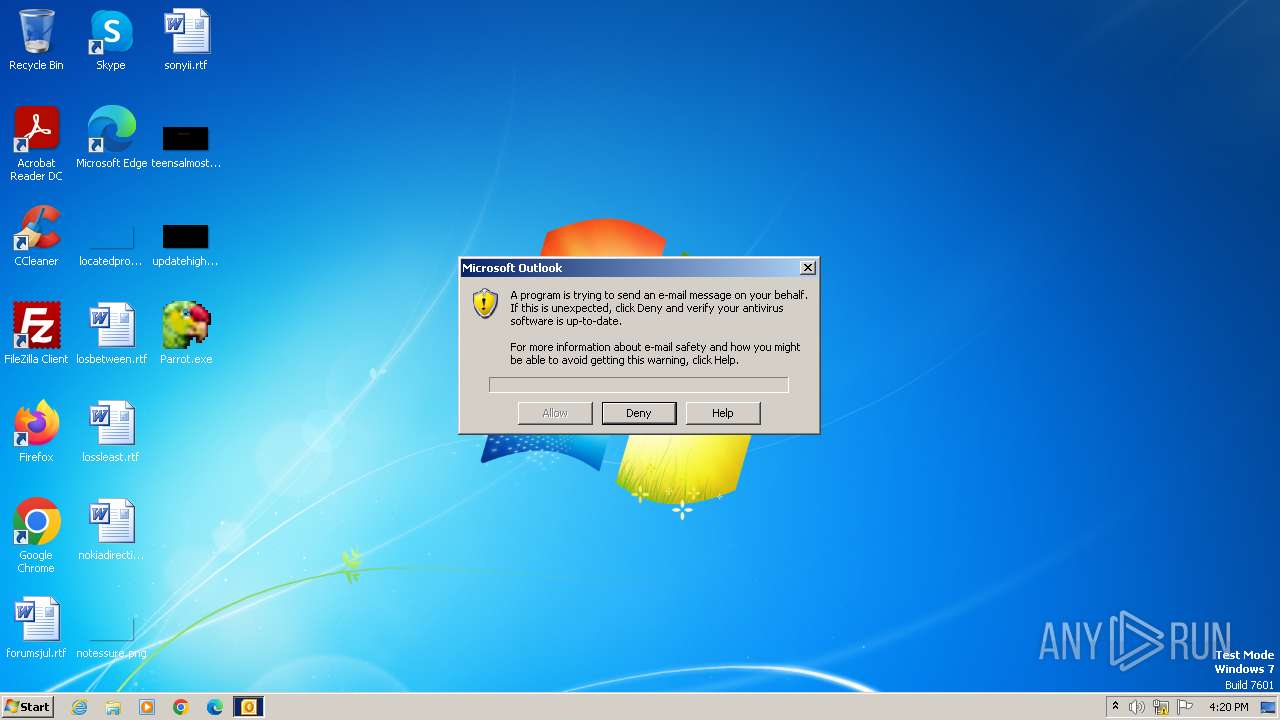
Drops the executable file immediately after the start
- Parrot.exe (PID: 3964)
- Parrot.exe (PID: 1284)
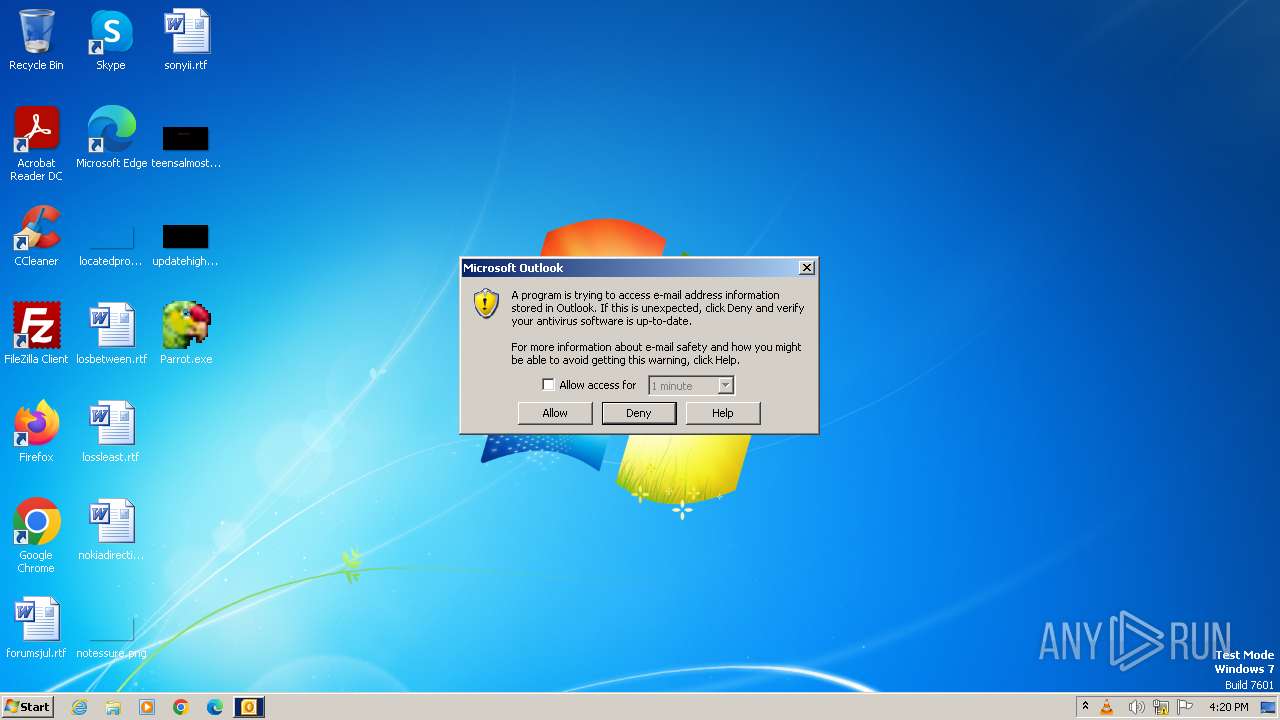
Creates a writable file in the system directory
- OUTLOOK.EXE (PID: 2252)
Deletes a file (SCRIPT)
- wscript.exe (PID: 2064)
SUSPICIOUS
Creates file in the systems drive root
- Parrot.exe (PID: 3964)
- Parrot.exe (PID: 1284)
- wscript.exe (PID: 2064)
- OUTLOOK.EXE (PID: 2252)
Process drops legitimate windows executable
- Parrot.exe (PID: 3964)
- Parrot.exe (PID: 1284)
Executable content was dropped or overwritten
- Parrot.exe (PID: 3964)
- Parrot.exe (PID: 1284)
- OUTLOOK.EXE (PID: 2252)
Reads the Internet Settings
- Parrot.exe (PID: 3964)
- Parrot.exe (PID: 1284)
Reads security settings of Internet Explorer
- Parrot.exe (PID: 1284)
The process executes VB scripts
- Parrot.exe (PID: 1284)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 2064)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2064)
INFO
Checks supported languages
- Parrot.exe (PID: 3964)
- vlc.exe (PID: 4060)
- Parrot.exe (PID: 1284)
- vlc.exe (PID: 1948)
Reads the computer name
- Parrot.exe (PID: 3964)
- vlc.exe (PID: 4060)
- Parrot.exe (PID: 1284)
Creates files or folders in the user directory
- Parrot.exe (PID: 3964)
Manual execution by a user
- Parrot.exe (PID: 1284)
Drops the executable file immediately after the start
- OUTLOOK.EXE (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (73.3) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (11.6) |
| .exe | | | Win32 Executable (generic) (7.9) |
| .exe | | | Generic Win/DOS Executable (3.5) |
| .exe | | | DOS Executable Generic (3.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1971:05:17 09:08:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1024 |
| InitializedDataSize: | 48640 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x10800 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 3.1 |
| Subsystem: | Windows GUI |
Total processes
45
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1284 | "C:\Users\admin\Desktop\Parrot.exe" | C:\Users\admin\Desktop\Parrot.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
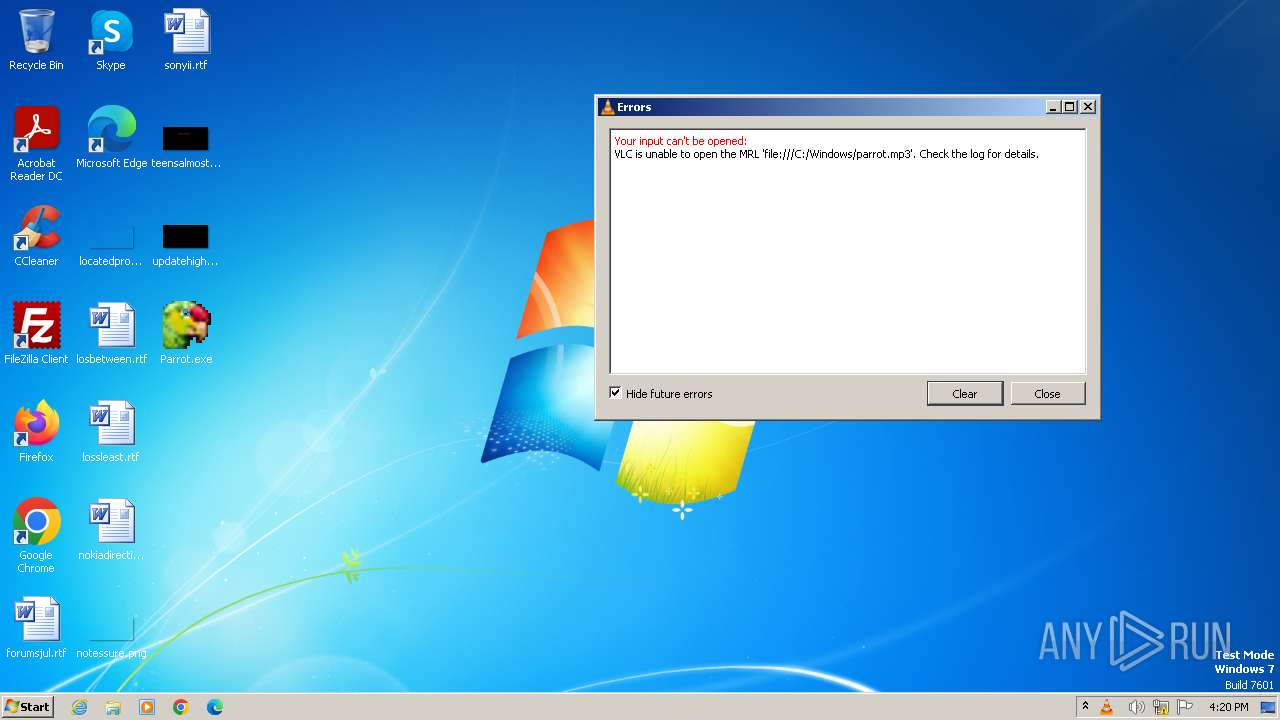
| 1948 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Windows\parrot.mp3" | C:\Program Files\VideoLAN\VLC\vlc.exe | Parrot.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: HIGH Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 2064 | "C:\Windows\System32\WScript.exe" "C:\mail.vbs" | C:\Windows\System32\wscript.exe | — | Parrot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2252 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3964 | "C:\Users\admin\Desktop\Parrot.exe" | C:\Users\admin\Desktop\Parrot.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4060 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Windows\parrot.mp3" | C:\Program Files\VideoLAN\VLC\vlc.exe | Parrot.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Version: 3.0.11 Modules
| |||||||||||||||
Total events
18 262
Read events
18 113
Write events
120
Delete events
29
Modification events
| (PID) Process: | (1284) Parrot.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1284) Parrot.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1284) Parrot.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1284) Parrot.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2252) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
Executable files
37
Suspicious files
8
Text files
8
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | Parrot.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\bfsvc.prt | executable | |
MD5:DBD14D0DB0382DFE96D7B5007DDD5ABE | SHA256:788E9846912F38F0D5F0A88758ABA80AF788DA40E96178635E6432CFF0D87A37 | |||
| 3964 | Parrot.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\HelpPane.prt | executable | |
MD5:3B55B2000DEBDC210693530B669B9966 | SHA256:972BA0531FFB90A5B9A0151AA5606D76C0123D8E74AC01F29E68A383D4ED8DEC | |||
| 3964 | Parrot.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\explorer.prt | executable | |
MD5:6DDCA324434FFA506CF7DC4E51DB7935 | SHA256:11D69FB388FF59E5BA6CA217CA04ECDE6A38FA8FB306AA5F1B72E22BB7C3A25A | |||
| 3964 | Parrot.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\hh.prt | executable | |
MD5:050AB578E032A7C9CA722F632A4018AC | SHA256:B4F3CD7DD365CA2757997CCC9907835AE659EB90CED73C4BE6B78A159A8E5AD3 | |||
| 3964 | Parrot.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\winhelp.prt | executable | |
MD5:8E6F7D51A5CB299C25621C6C1AB57E84 | SHA256:7AD523A8F7183DDD809F6F3251E0E2E6ADFC969FAB5484ED13C497D92C7ABBC6 | |||
| 4060 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | text | |
MD5:7C7360125E53D387C073170E8D195DAB | SHA256:472A53B0877D954E16D08C2C739F20627E6C72F7DDC3B4B6B24A13C538CB7273 | |||
| 3964 | Parrot.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\hello.mp3 | binary | |
MD5:7C7D4823EB64A043C78ABCF6AE666A6B | SHA256:284F82EE688DAB1CD1D65A4DFFB7BF5E01522998C670B436A59642B48B90F4ED | |||
| 4060 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.Hp4060 | text | |
MD5:7C7360125E53D387C073170E8D195DAB | SHA256:472A53B0877D954E16D08C2C739F20627E6C72F7DDC3B4B6B24A13C538CB7273 | |||
| 3964 | Parrot.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\winhlp32.prt | executable | |
MD5:1D420D66250BCAAAED05724FB34008CF | SHA256:8D39AC4C416CAE32A6787326D2CAE0B0CD075915B75229572FA5D90FBB3DFE52 | |||
| 3964 | Parrot.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\parrot.mp3 | wav | |
MD5:AB4EE6036A4BD4DB7808838411C44AC9 | SHA256:B5F09E2DE74CBCC29B92612DED3ED2E24FDF5C6704D3CCB888A663DCB8C75DA4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2252 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_concat_plugin.dll
|