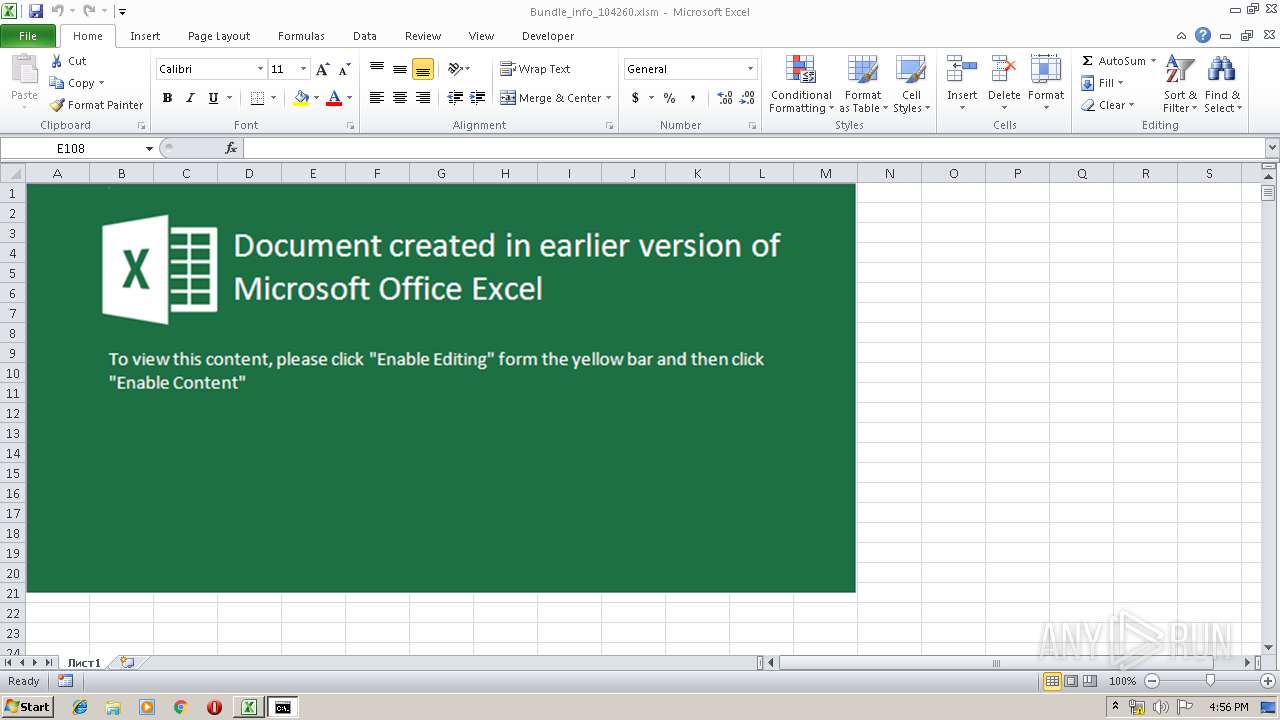
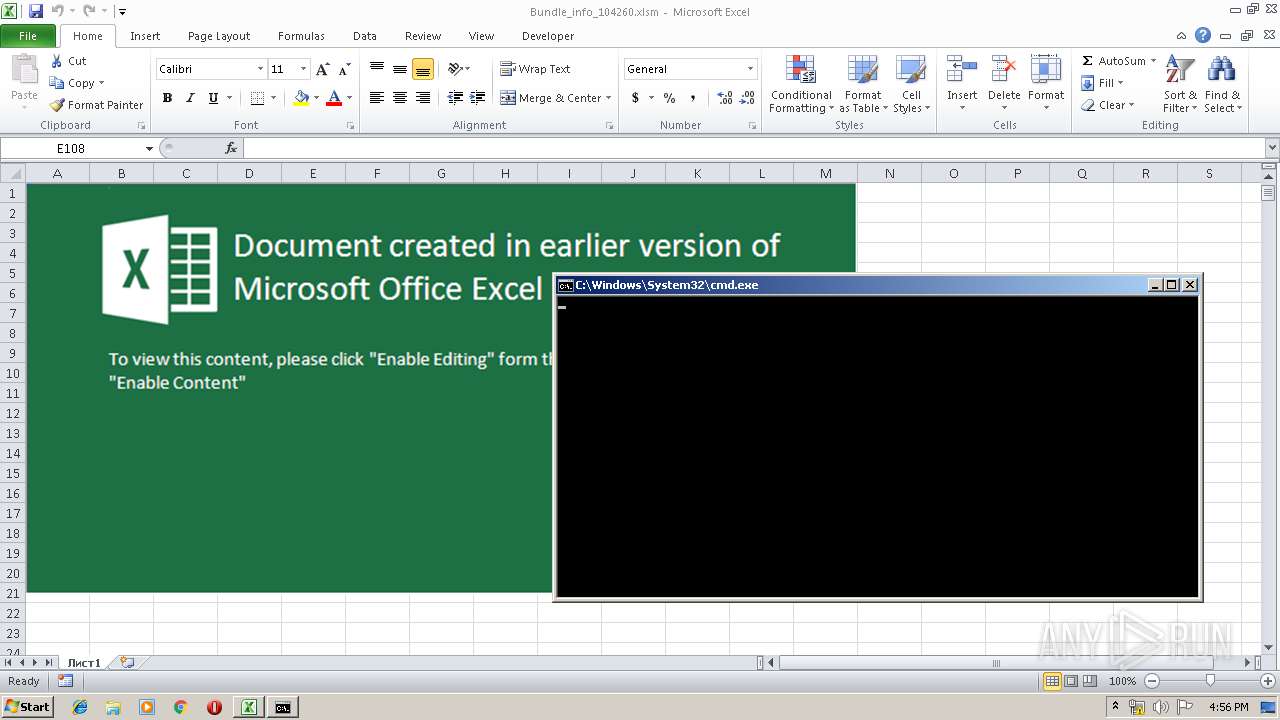
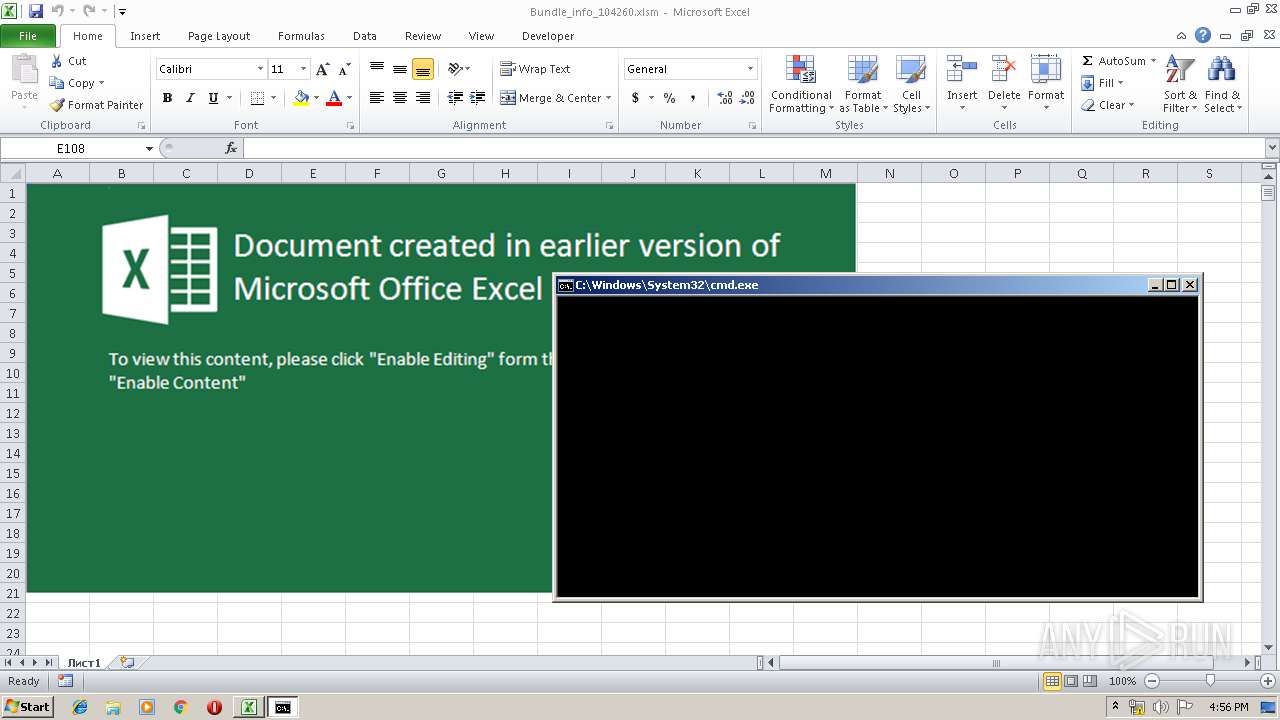
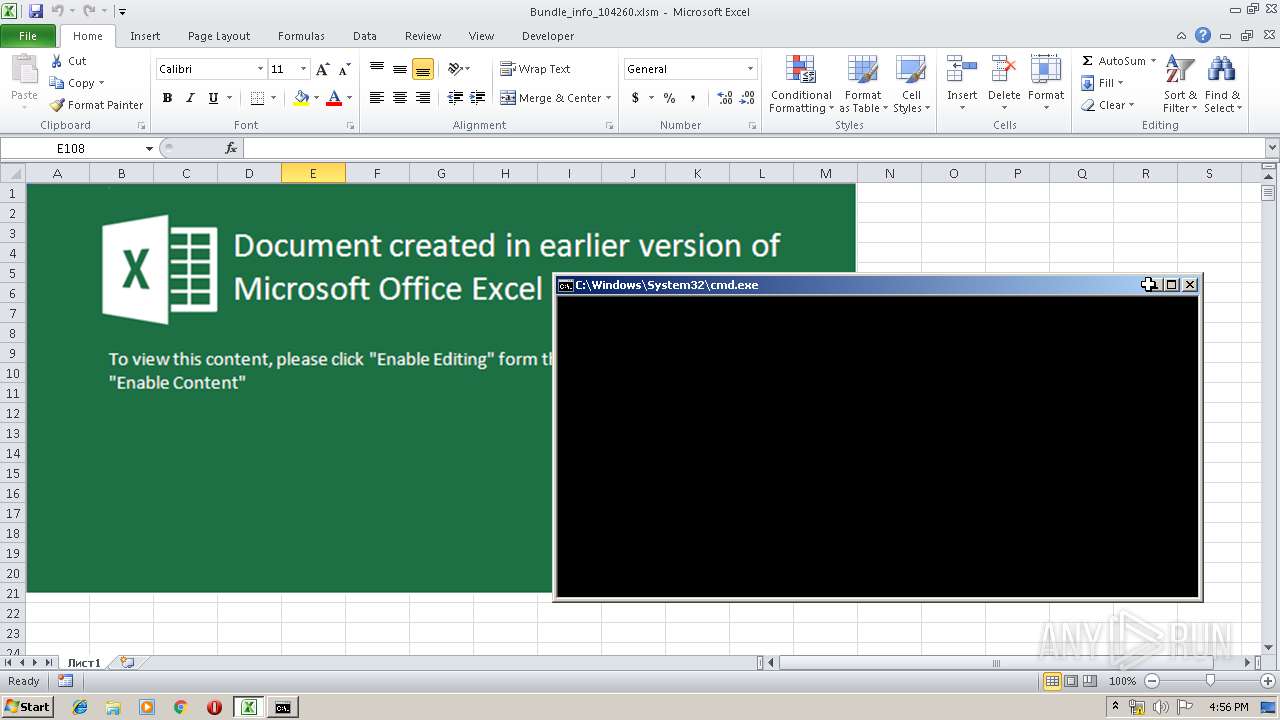
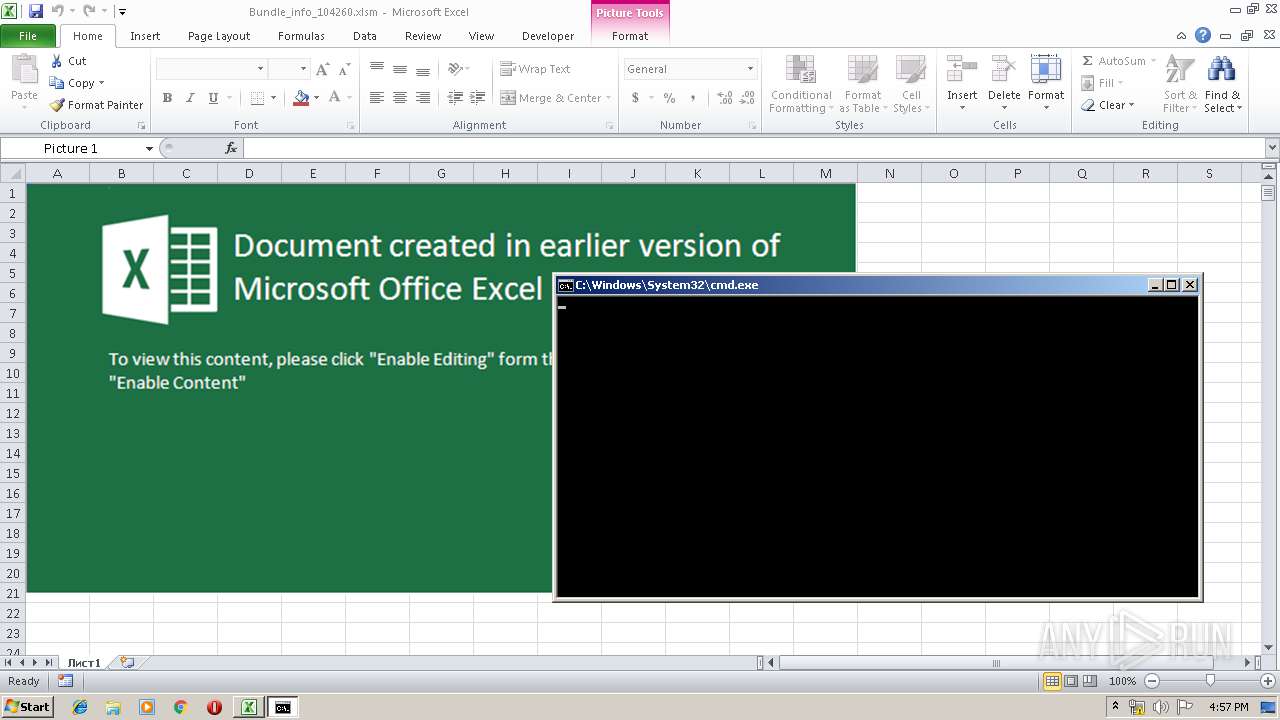
| File name: | Bundle_info_104260.xlsm |
| Full analysis: | https://app.any.run/tasks/99364e5c-4ad5-473b-b477-4cd0f17ec63c |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2019, 15:55:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | B5E137EC53B6535AE241F6A3587ACE59 |
| SHA1: | AB6049931012D9B039890E2D7C964251451D2723 |
| SHA256: | AF8559A867A9BB024FD4DE04D6F7B993D865D6A357F50B2E149289F8764701CC |
| SSDEEP: | 768:8Hug5V4bx2ThbyQY2IBlzG5ke/h0bldSS9:Wdk2Fbi2IBF6ZqdSS9 |
MALICIOUS
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3368)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3368)
SUSPICIOUS
Starts MSHTA.EXE for opening HTA or HTMLS files
- cmd.exe (PID: 2864)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 2540)
Executes application which crashes
- cmd.exe (PID: 2440)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3368)
Reads internet explorer settings
- mshta.exe (PID: 2540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlam | | | Excel Macro-enabled Open XML add-in (42.4) |
|---|---|---|
| .xlsm | | | Excel Microsoft Office Open XML Format document (with Macro) (29.2) |
| .xlsx | | | Excel Microsoft Office Open XML Format document (17.3) |
| .zip | | | Open Packaging Conventions container (8.9) |
| .zip | | | ZIP compressed archive (2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xe69d70d7 |
| ZipCompressedSize: | 413 |
| ZipUncompressedSize: | 1393 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | - |
|---|
XML
| LastModifiedBy: | - |
|---|---|
| CreateDate: | 2006:09:16 00:00:00Z |
| ModifyDate: | 2019:05:16 16:59:30Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | Лист1 |
| Company: | - |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15.03 |
Total processes
39
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1136 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\system32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2440 | "C:\Windows\System32\cmd.exe" /c C:\Users\admin\AppData\Local\Temp\4886uray.exe | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2540 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\AppData\Local\Temp\999.hta" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2864 | cmd.exe /c C:\Users\admin\AppData\Local\Temp\999.hta | C:\Windows\system32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3368 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 069
Read events
965
Write events
97
Delete events
7
Modification events
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | h=> |
Value: 683D3E00280D0000010000000000000000000000 | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 280D000002026690240FD50100000000 | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | h=> |
Value: 683D3E00280D0000010000000000000000000000 | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3368) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\11F441 |
| Operation: | write | Name: | 11F441 |
Value: 04000000280D00003900000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00420075006E0064006C0065005F0069006E0066006F005F003100300034003200360030002E0078006C0073006D00000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0001000000000000006075E391240FD50141F4110041F4110000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3368 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVREDC8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1136 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsFF5C.tmp | — | |
MD5:— | SHA256:— | |||
| 1136 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsFF6D.tmp | — | |
MD5:— | SHA256:— | |||
| 3368 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3368 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\999.hta | html | |
MD5:— | SHA256:— | |||
| 2540 | mshta.exe | C:\Users\admin\AppData\Local\Temp\4886uray.exe | html | |
MD5:3526531CCD6C6A1D2340574A305A18F8 | SHA256:B663321AB439CC53A329EE352C1B855D9998D3AF95524A05795A88B42A9ACF07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
0
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2540 | mshta.exe | GET | 200 | 64.44.133.144:80 | http://64.44.133.144/?3mhZb5 | US | html | 10.6 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2540 | mshta.exe | 64.44.133.144:80 | — | Nexeon Technologies, Inc. | US | suspicious |