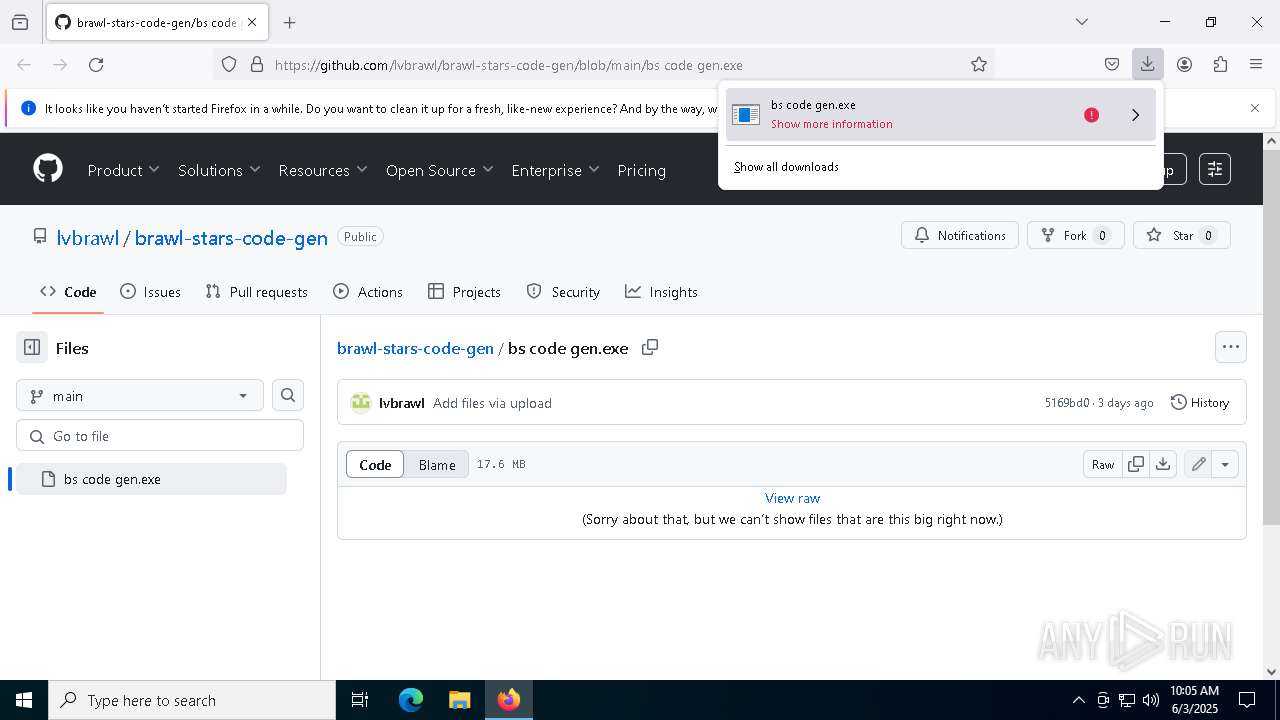
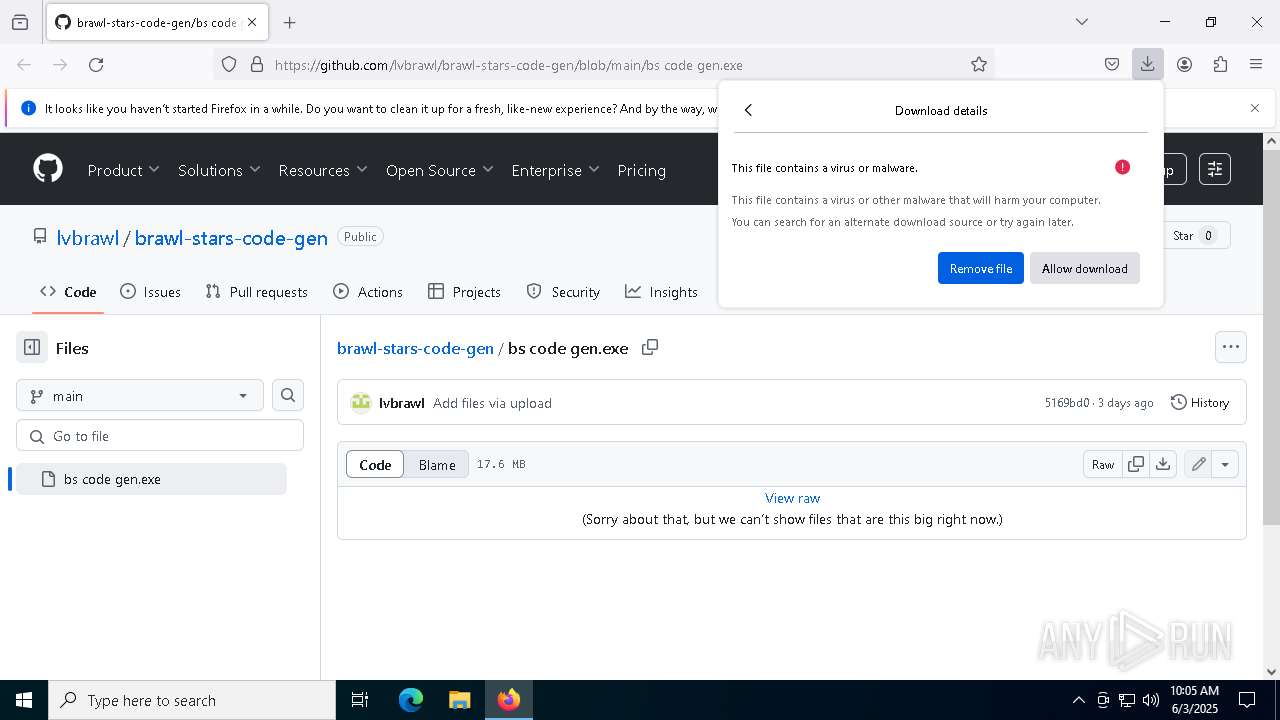
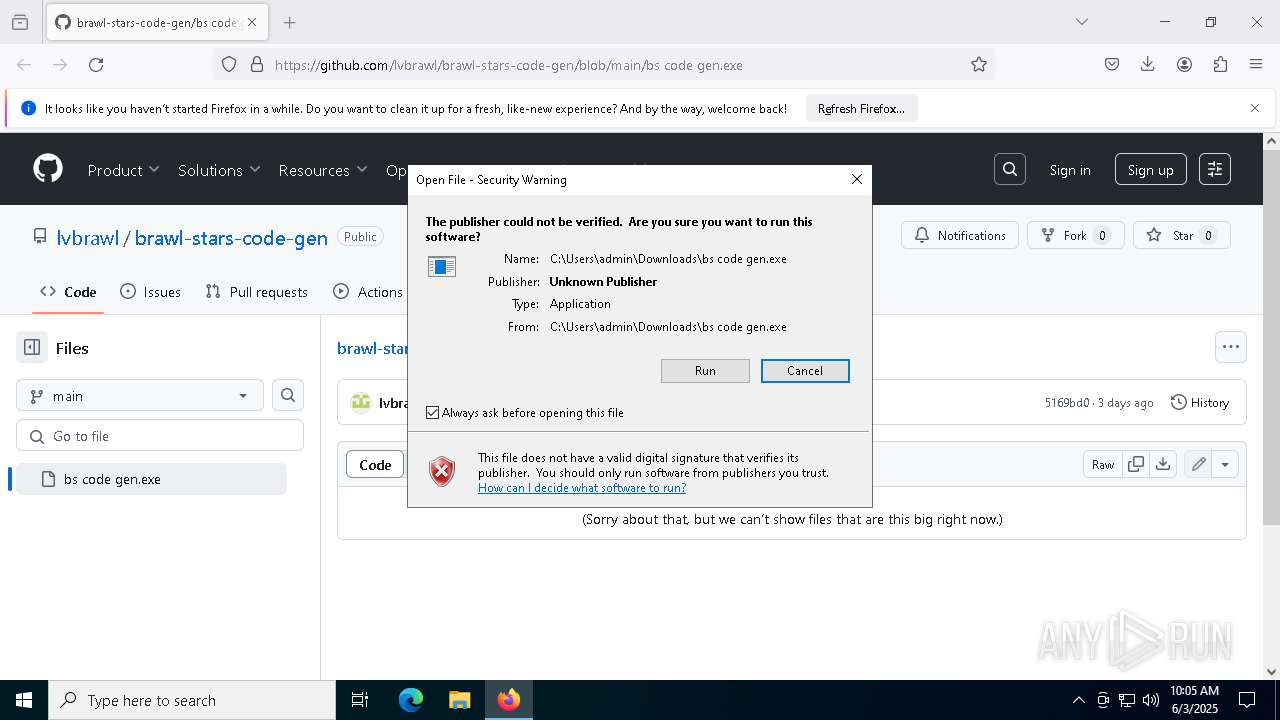
| URL: | https://github.com/lvbrawl/brawl-stars-code-gen/blob/main/bs%20code%20gen.exe |
| Full analysis: | https://app.any.run/tasks/70799ae7-aa38-4f24-9ed0-f651c8c2415d |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | June 03, 2025, 10:05:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 934C732FB5BF29ABFA622A50750078DB |
| SHA1: | 6FA24F66BABD737E549A56CB8B28CBDDE58DE02C |
| SHA256: | AF777317FF2B254CC10DAD1D5F0CD642BA244BE21D5BA1DE752DF3F485CD6245 |
| SSDEEP: | 3:N8tEd5T64uKvCrcTER2ysKBAGXkAn:2uBUrcTsXrX |
MALICIOUS
Create files in the Startup directory
- bs code gen.exe (PID: 4608)
Actions looks like stealing of personal data
- bs code gen.exe (PID: 4608)
Steals credentials from Web Browsers
- bs code gen.exe (PID: 4608)
Suspicious data exfiltration via CURL detected
- cmd.exe (PID: 9208)
- bs code gen.exe (PID: 4608)
- cmd.exe (PID: 11260)
- cmd.exe (PID: 7440)
- cmd.exe (PID: 8248)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 11160)
- cmd.exe (PID: 8676)
- cmd.exe (PID: 8668)
SUSPICIOUS
Process drops legitimate windows executable
- bs code gen.exe (PID: 1244)
Executable content was dropped or overwritten
- bs code gen.exe (PID: 1244)
- bs code gen.exe (PID: 4608)
Process drops python dynamic module
- bs code gen.exe (PID: 1244)
Application launched itself
- bs code gen.exe (PID: 1244)
The process drops C-runtime libraries
- bs code gen.exe (PID: 1244)
Loads Python modules
- bs code gen.exe (PID: 4608)
Get information on the list of running processes
- bs code gen.exe (PID: 4608)
- cmd.exe (PID: 7324)
Starts CMD.EXE for commands execution
- bs code gen.exe (PID: 4608)
Data upload via CURL
- curl.exe (PID: 10040)
- curl.exe (PID: 7508)
- curl.exe (PID: 6560)
- curl.exe (PID: 8444)
- curl.exe (PID: 8620)
- curl.exe (PID: 11224)
- curl.exe (PID: 8804)
- curl.exe (PID: 8832)
Checks for external IP
- svchost.exe (PID: 2196)
- bs code gen.exe (PID: 4608)
Execution of CURL command
- bs code gen.exe (PID: 4608)
INFO
Checks supported languages
- bs code gen.exe (PID: 1244)
- bs code gen.exe (PID: 4608)
- curl.exe (PID: 10040)
- curl.exe (PID: 11224)
- curl.exe (PID: 7508)
- curl.exe (PID: 6560)
- curl.exe (PID: 8444)
- curl.exe (PID: 8620)
- curl.exe (PID: 8804)
- curl.exe (PID: 8832)
Reads the computer name
- bs code gen.exe (PID: 1244)
- bs code gen.exe (PID: 4608)
- curl.exe (PID: 10040)
- curl.exe (PID: 7508)
- curl.exe (PID: 11224)
- curl.exe (PID: 8804)
- curl.exe (PID: 8832)
Application launched itself
- firefox.exe (PID: 1168)
- firefox.exe (PID: 7320)
Executable content was dropped or overwritten
- firefox.exe (PID: 7320)
The sample compiled with english language support
- bs code gen.exe (PID: 1244)
Create files in a temporary directory
- bs code gen.exe (PID: 1244)
- bs code gen.exe (PID: 4608)
Launching a file from the Downloads directory
- firefox.exe (PID: 7320)
Creates files or folders in the user directory
- bs code gen.exe (PID: 4608)
Checks proxy server information
- bs code gen.exe (PID: 4608)
- slui.exe (PID: 9204)
Launching a file from the Startup directory
- bs code gen.exe (PID: 4608)
Execution of CURL command
- cmd.exe (PID: 9208)
- cmd.exe (PID: 11260)
- cmd.exe (PID: 7440)
- cmd.exe (PID: 8248)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 11160)
- cmd.exe (PID: 8676)
- cmd.exe (PID: 8668)
Reads the software policy settings
- slui.exe (PID: 7748)
- slui.exe (PID: 9204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
186
Monitored processes
48
Malicious processes
12
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://github.com/lvbrawl/brawl-stars-code-gen/blob/main/bs%20code%20gen.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | "C:\Users\admin\Downloads\bs code gen.exe" | C:\Users\admin\Downloads\bs code gen.exe | firefox.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2148 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1912 -parentBuildID 20240213221259 -prefsHandle 1848 -prefMapHandle 1836 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {a4bb1da1-cce9-487c-97b7-c9e201ccf786} 7320 "\\.\pipe\gecko-crash-server-pipe.7320" 1b65ddbee10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4608 | "C:\Users\admin\Downloads\bs code gen.exe" | C:\Users\admin\Downloads\bs code gen.exe | bs code gen.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4784 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2476 -childID 1 -isForBrowser -prefsHandle 2836 -prefMapHandle 2832 -prefsLen 26911 -prefMapSize 244583 -jsInitHandle 1280 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {140a5543-c7ce-4948-a8f6-17e6e6a3b18a} 7320 "\\.\pipe\gecko-crash-server-pipe.7320" 1b66276ff50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6028 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2148 -parentBuildID 20240213221259 -prefsHandle 2140 -prefMapHandle 2136 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {725e08f1-799f-428b-94ca-9b9d45b79f23} 7320 "\\.\pipe\gecko-crash-server-pipe.7320" 1b650d81310 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
21 383
Read events
21 381
Write events
2
Delete events
0
Modification events
| (PID) Process: | (7320) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7320) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
78
Suspicious files
150
Text files
54
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7320 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:22DA36CA5BA1D055ADE237F52DC825A7 | SHA256:7438A5D5298BFA0ABAB51E6B35EAC0F26B830BCEFBDBEB5F07721DBA34F89E0D | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:47EB38594AC3E6863AC4AE1B5D3D5D91 | SHA256:DB3DF44ACAD19AC168FD530875D67B3B631A898ACE76FAFBB000D49399FFBAA9 | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:C09FF302D57C404B61E6A89B0B9F36E7 | SHA256:6A5B4F82595799346D0E501FE6CC8629E0FD6ED27B74D0E6CB5073DDB2E3C40B | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | dbf | |
MD5:4006DDC2918B16C7EF5516C58373842B | SHA256:269EA23B77EDE0874628BD8611BCC5A3E87E0C44CA8A821C0D028B929D4F468F | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:1CF6EA1AB7E0D37600AD0551F2EC97C3 | SHA256:82586DE1D6338D1873D1983330CDB69D0922A3CB5D6A631861CB5886AD429F92 | |||
| 7320 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:1CF6EA1AB7E0D37600AD0551F2EC97C3 | SHA256:82586DE1D6338D1873D1983330CDB69D0922A3CB5D6A631861CB5886AD429F92 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
113
DNS requests
136
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7636 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7320 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7320 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7320 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
7320 | firefox.exe | POST | 200 | 2.16.202.121:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7320 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
7320 | firefox.exe | POST | 200 | 2.16.202.121:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7320 | firefox.exe | POST | 200 | 2.16.241.8:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7636 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5056 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7320 | firefox.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
7320 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
7320 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
mc.prod.ads.prod.webservices.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
4608 | bs code gen.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
4608 | bs code gen.exe | Misc activity | ET INFO External IP Lookup Domain (geolocation-db .com) in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain in DNS Lookup (geolocation-db .com) |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
4608 | bs code gen.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |