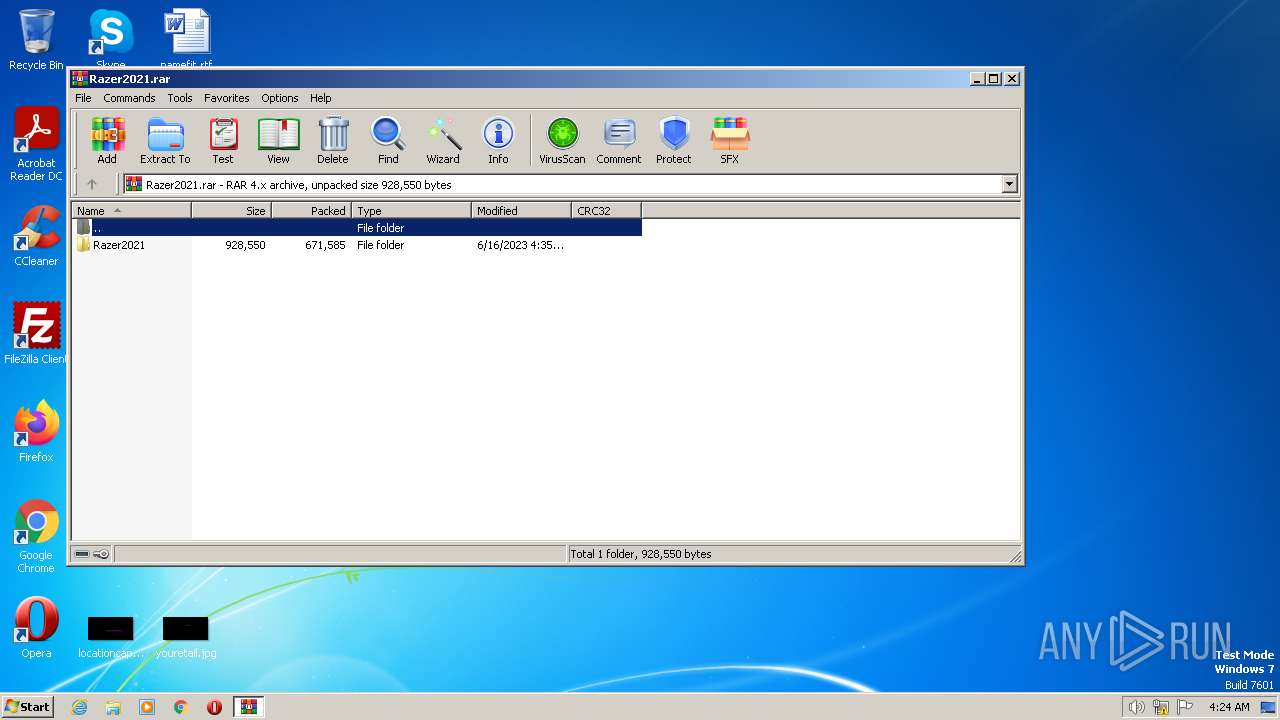
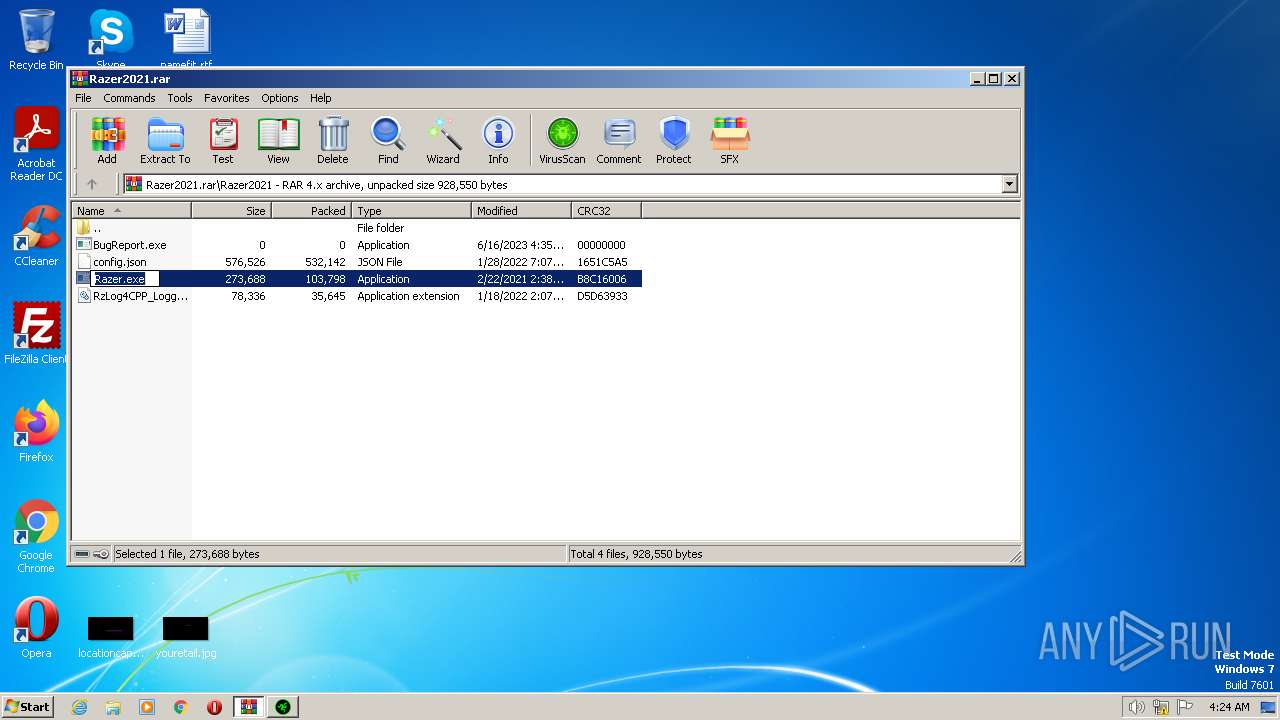
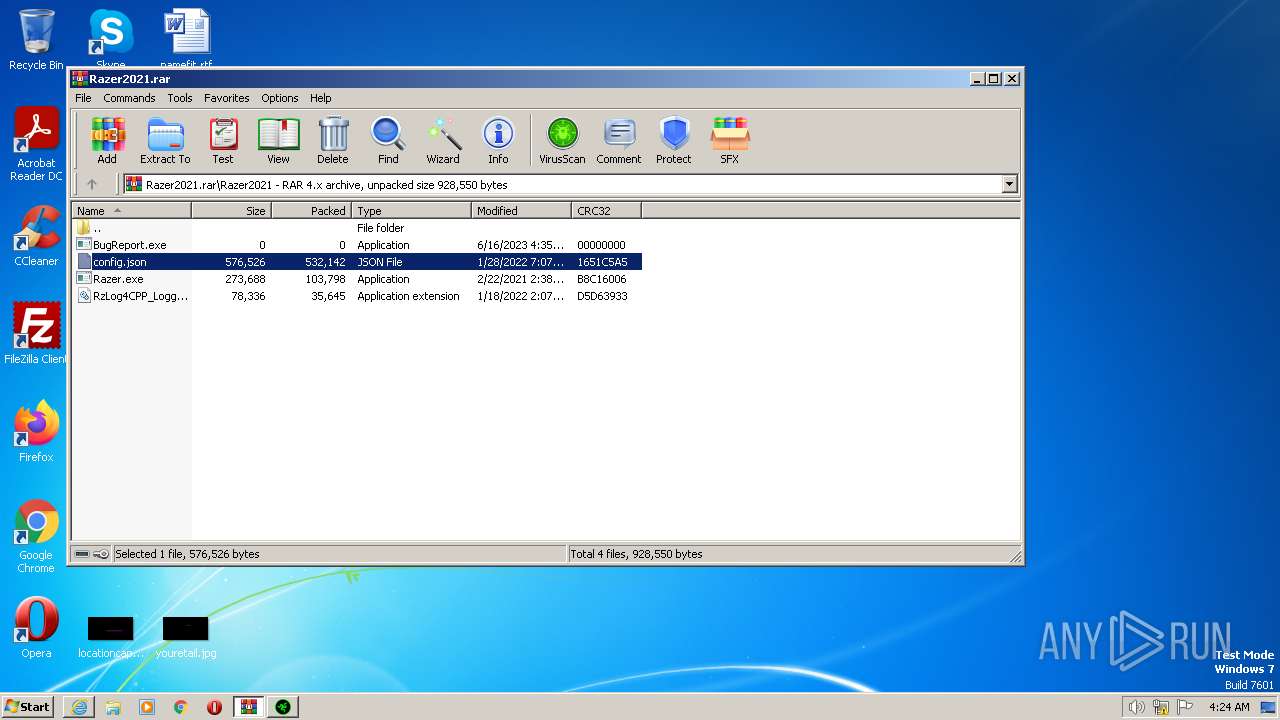
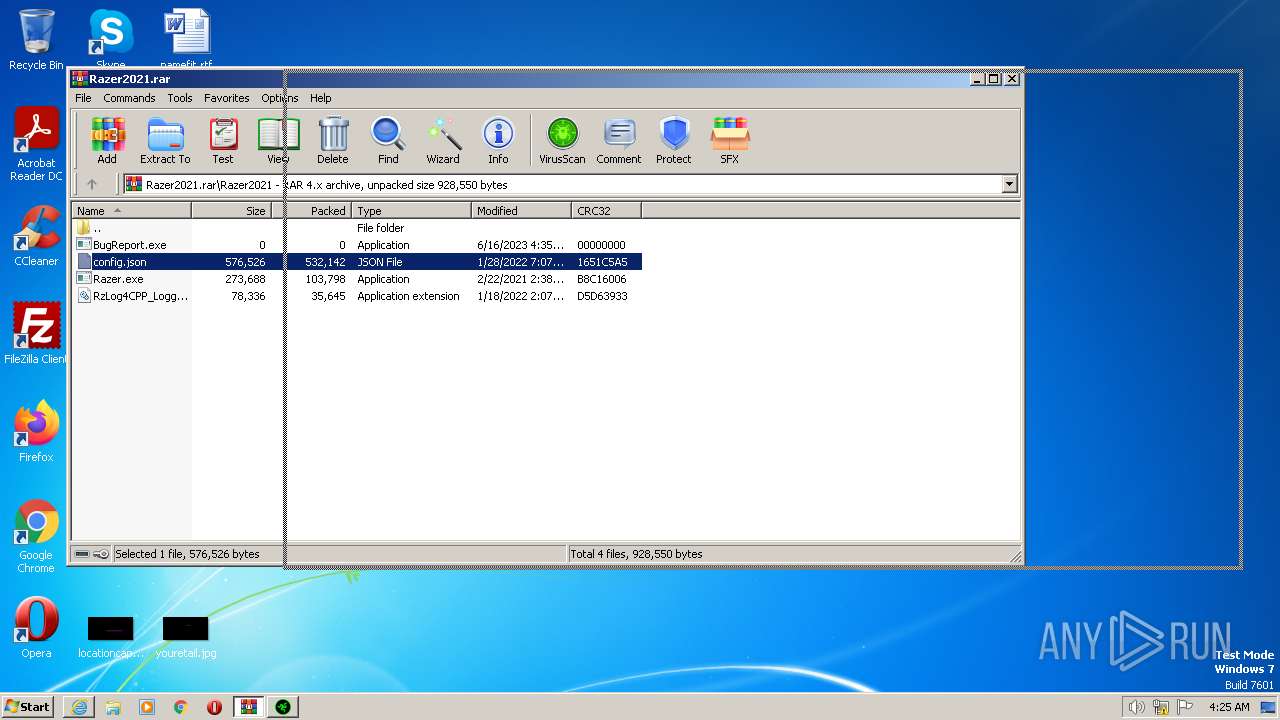
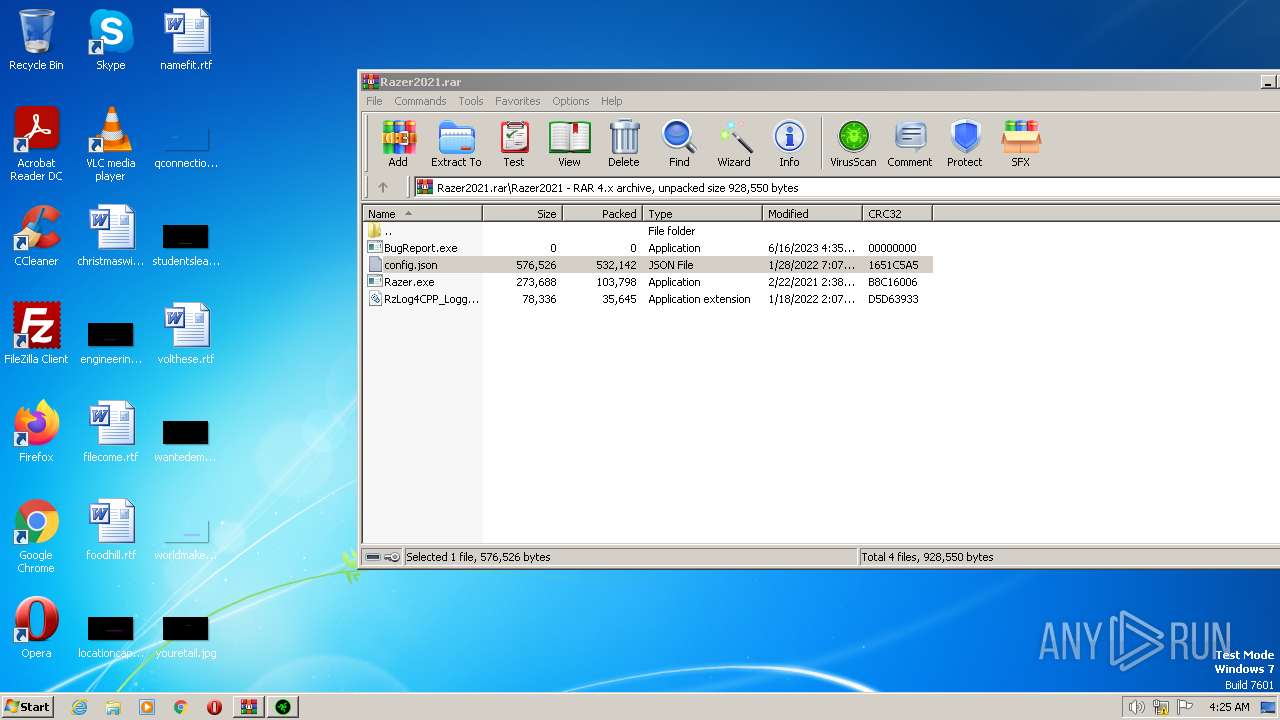
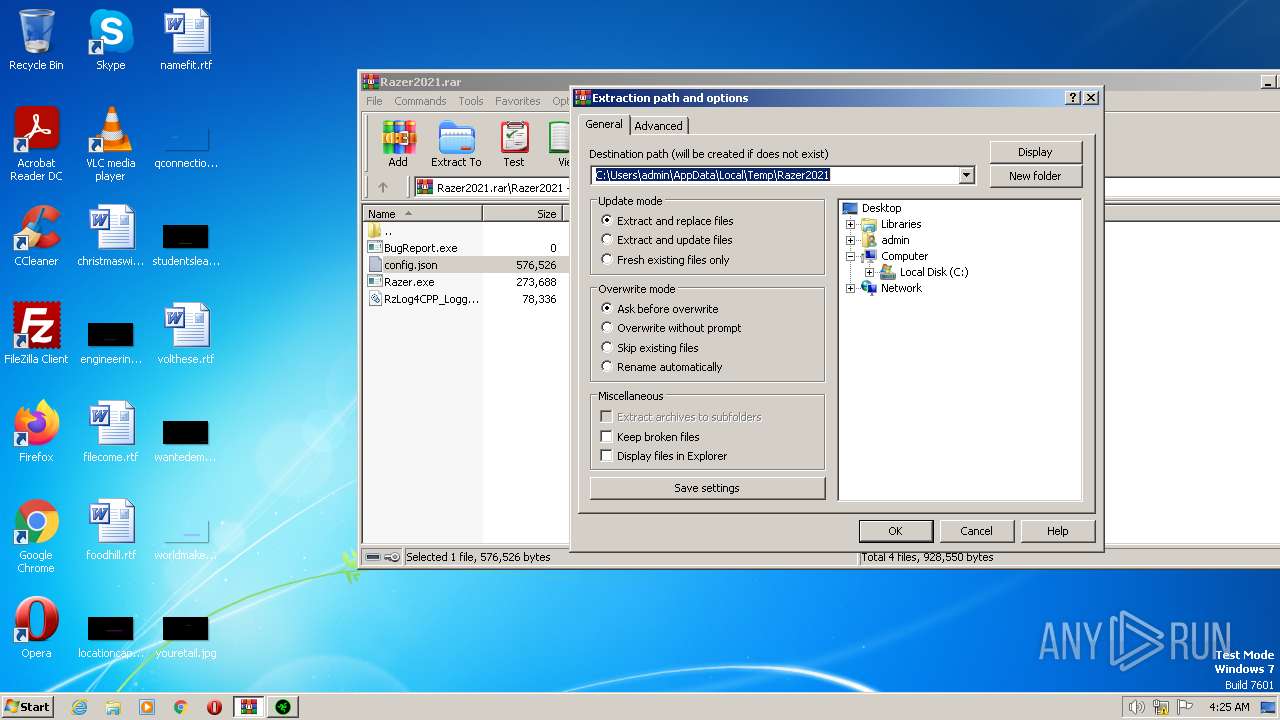
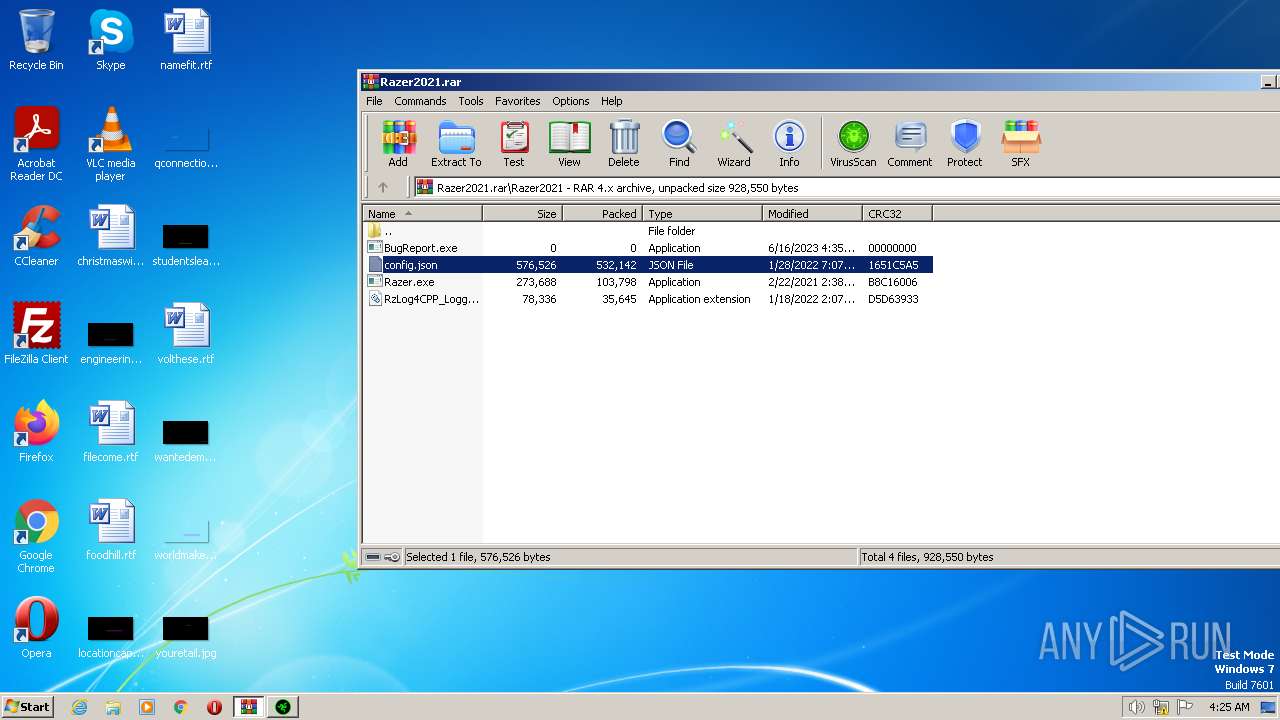
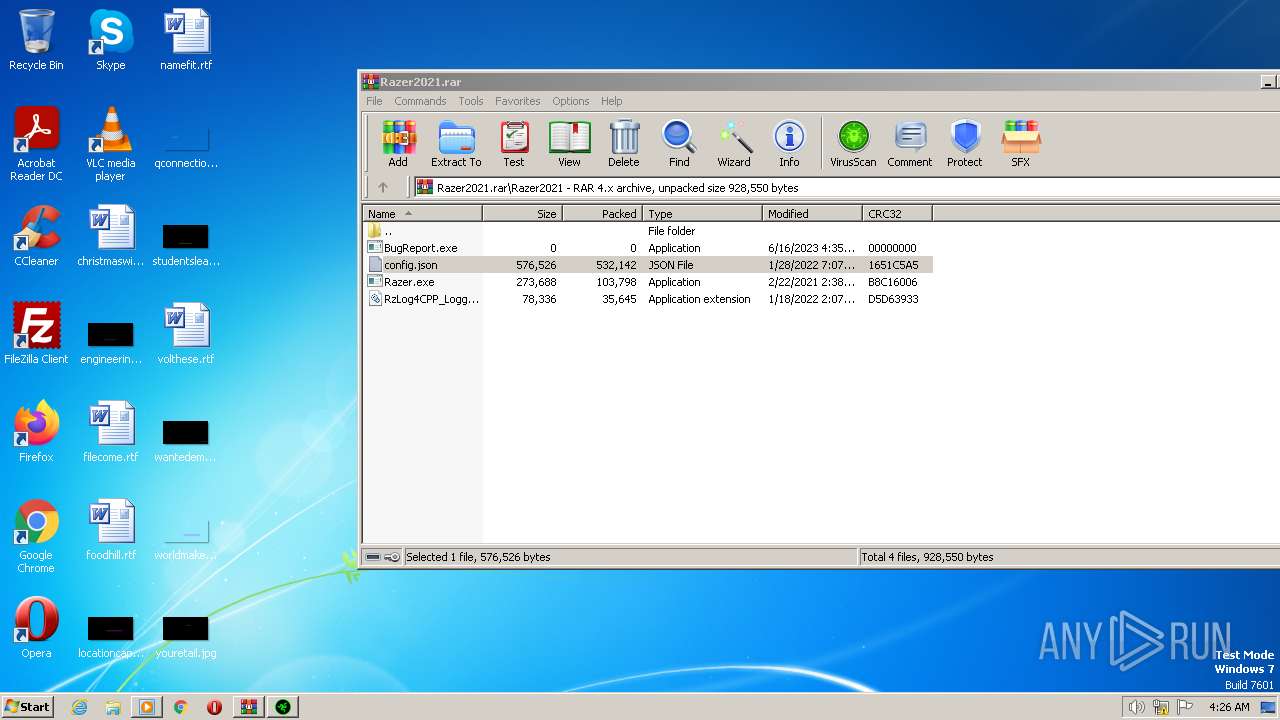
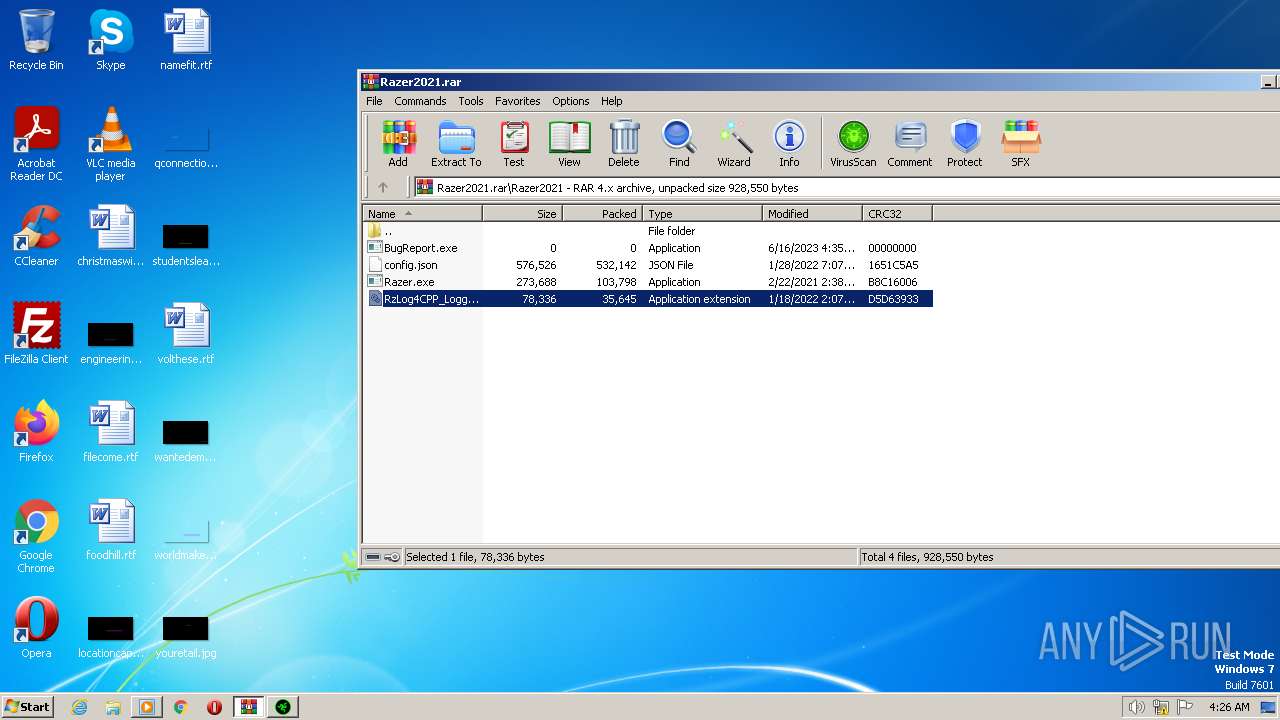
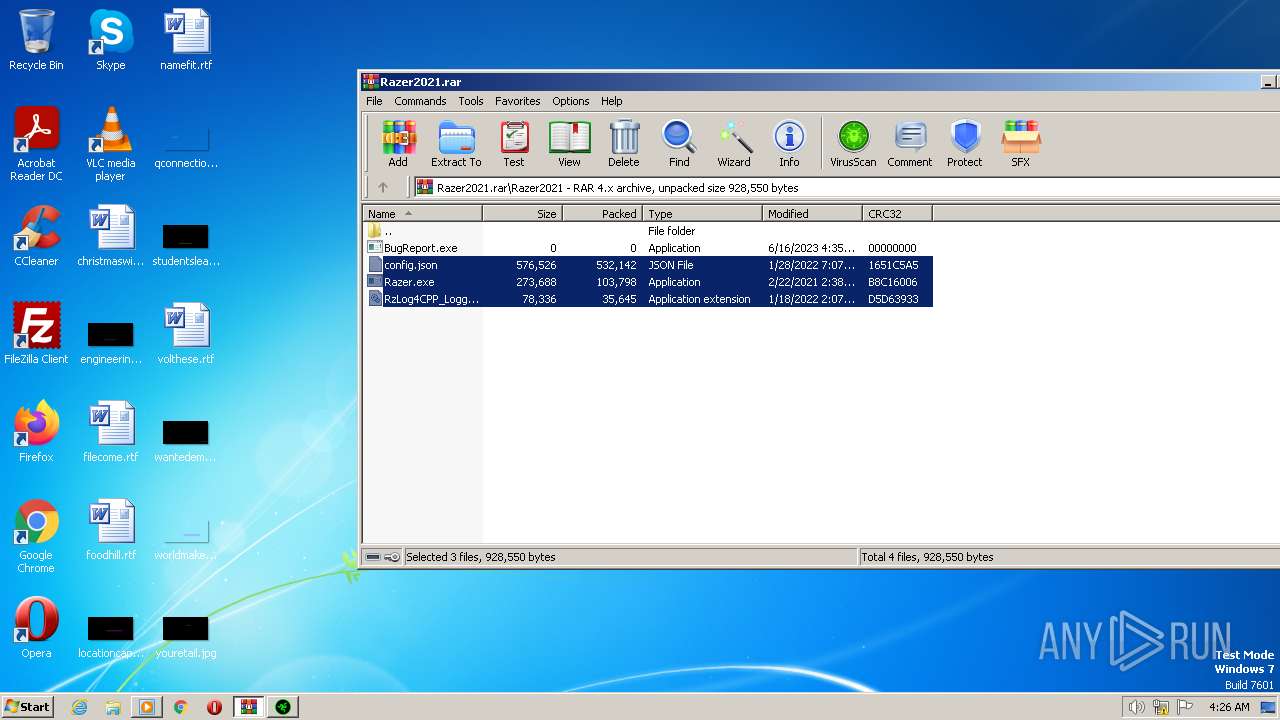
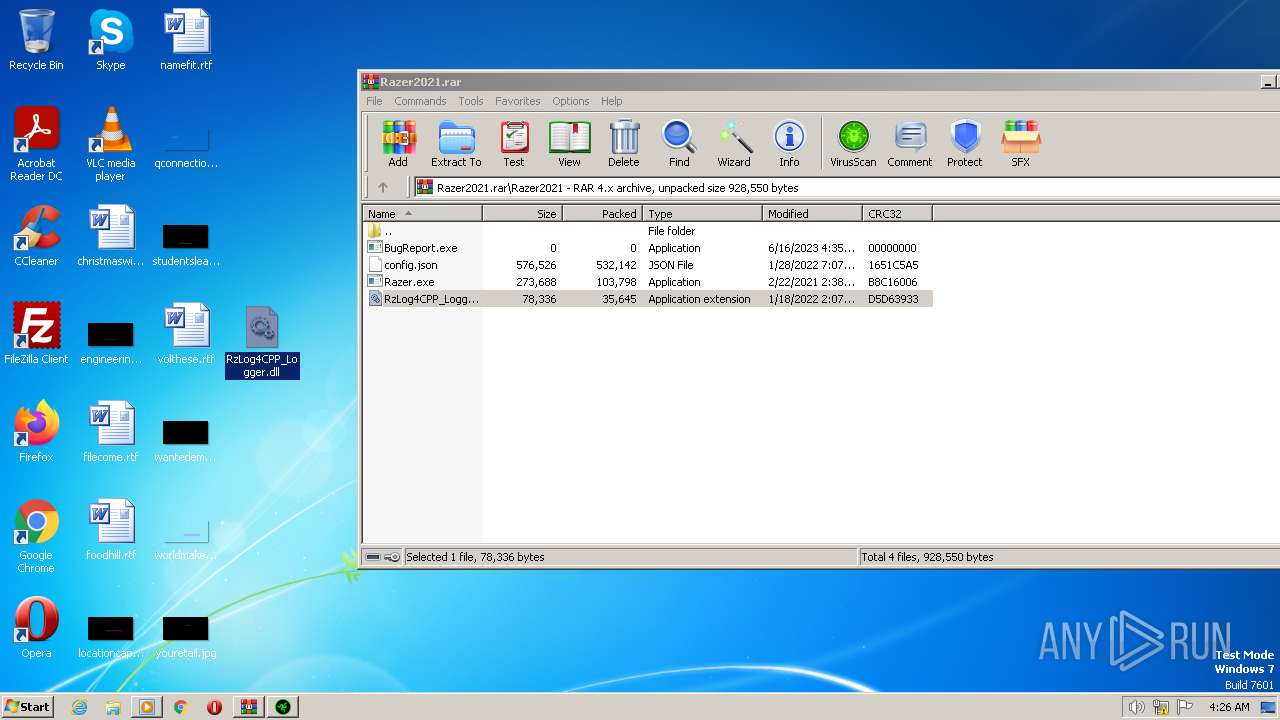
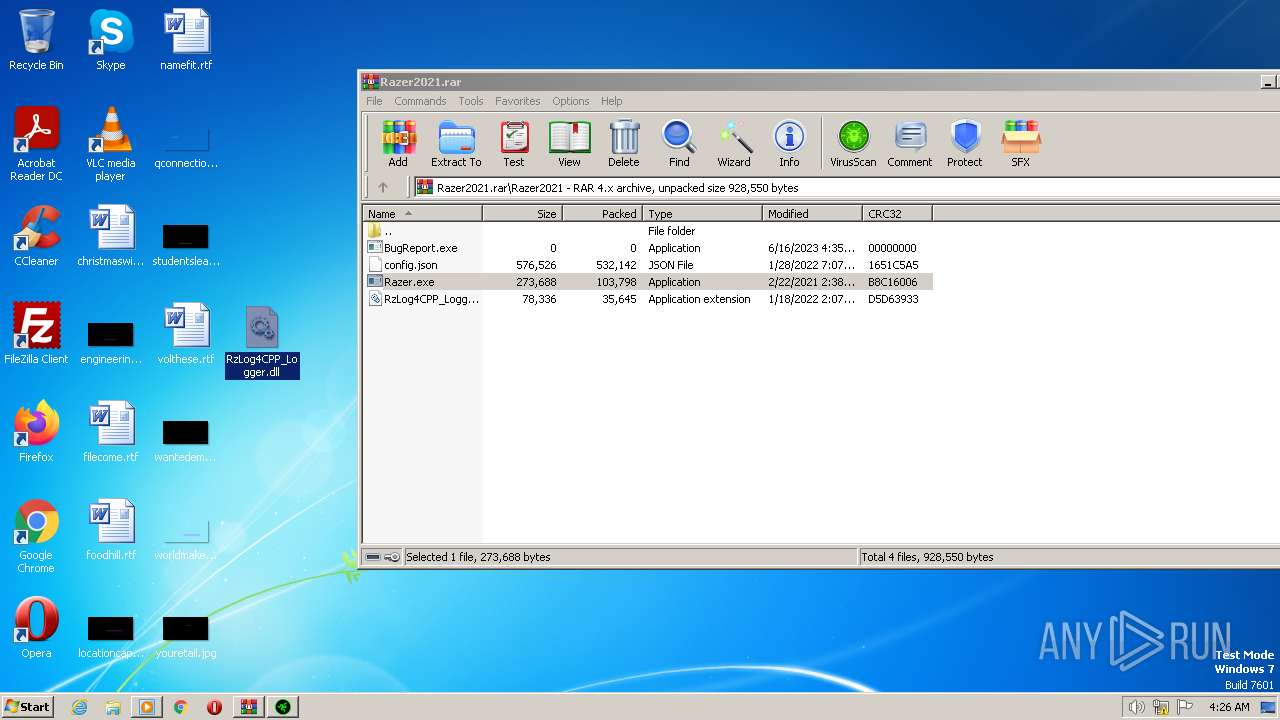
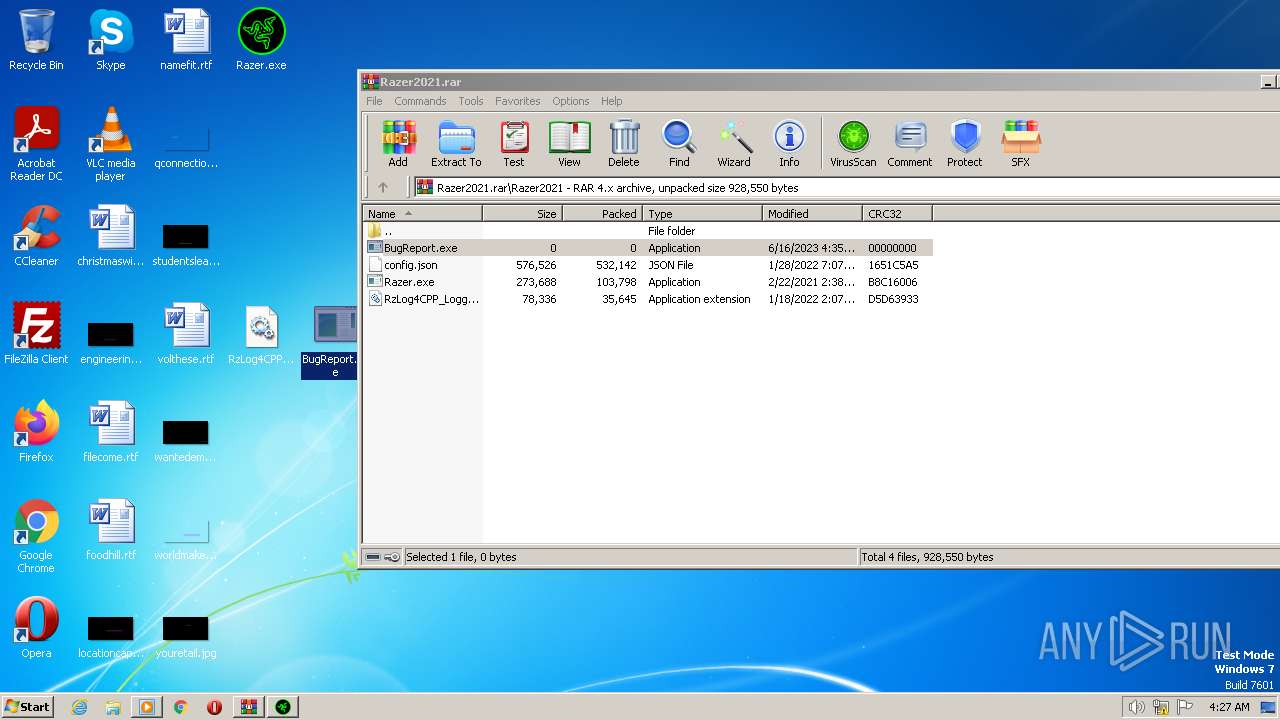
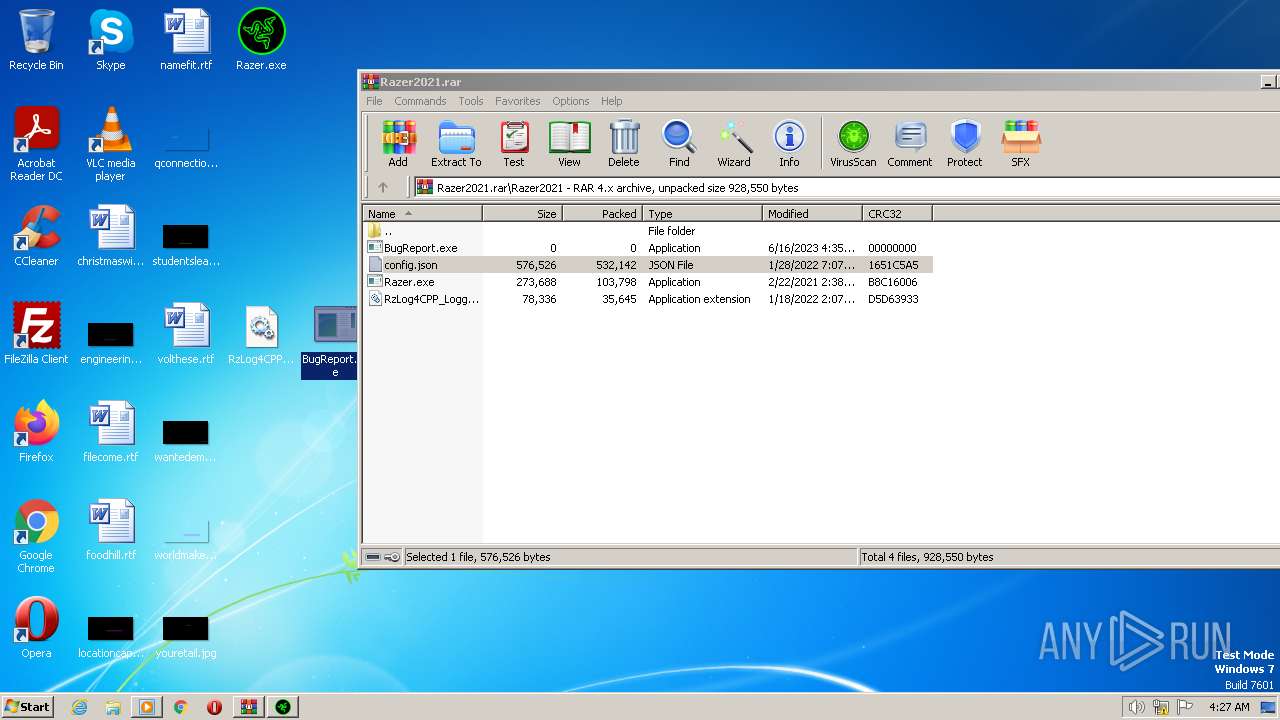
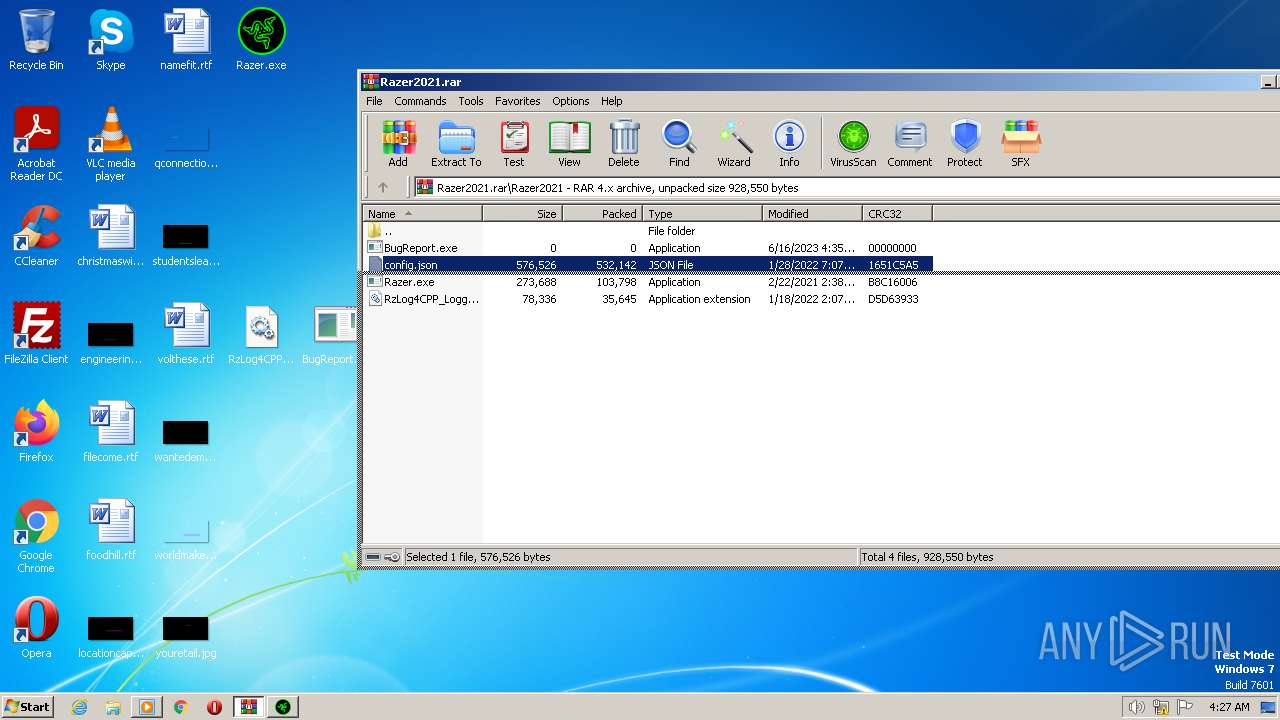
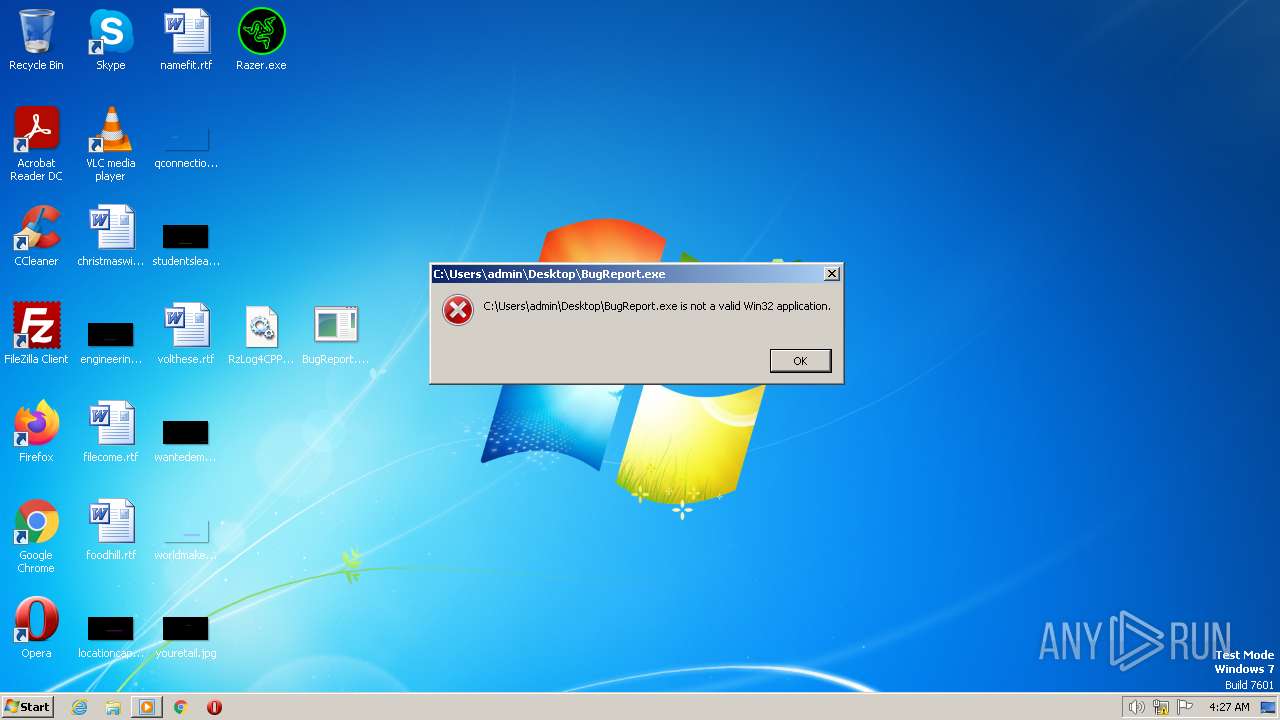
| File name: | Razer2021.rar |
| Full analysis: | https://app.any.run/tasks/6a7a0312-0111-4991-a730-050a7ee09773 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2023, 03:24:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | E74A2C438FCDCC31D4EA8EA2AE785248 |
| SHA1: | 7FF7DE9D197D8127DB6CF4897AC96A6E38A0CF86 |
| SHA256: | AF6C2B9E9B8CFFD00EC9F60AD81CE682394C8B84A166E420DAC5112D3B3B3BA6 |
| SSDEEP: | 12288:rbN032tu+mB8ygdFkgWnfl10cz7K9VBIclp1O/xipqOwdLBgYV5rv/bX5Jy/:ng2MBek/fPiVBxlHWGY5Tba/ |
MALICIOUS
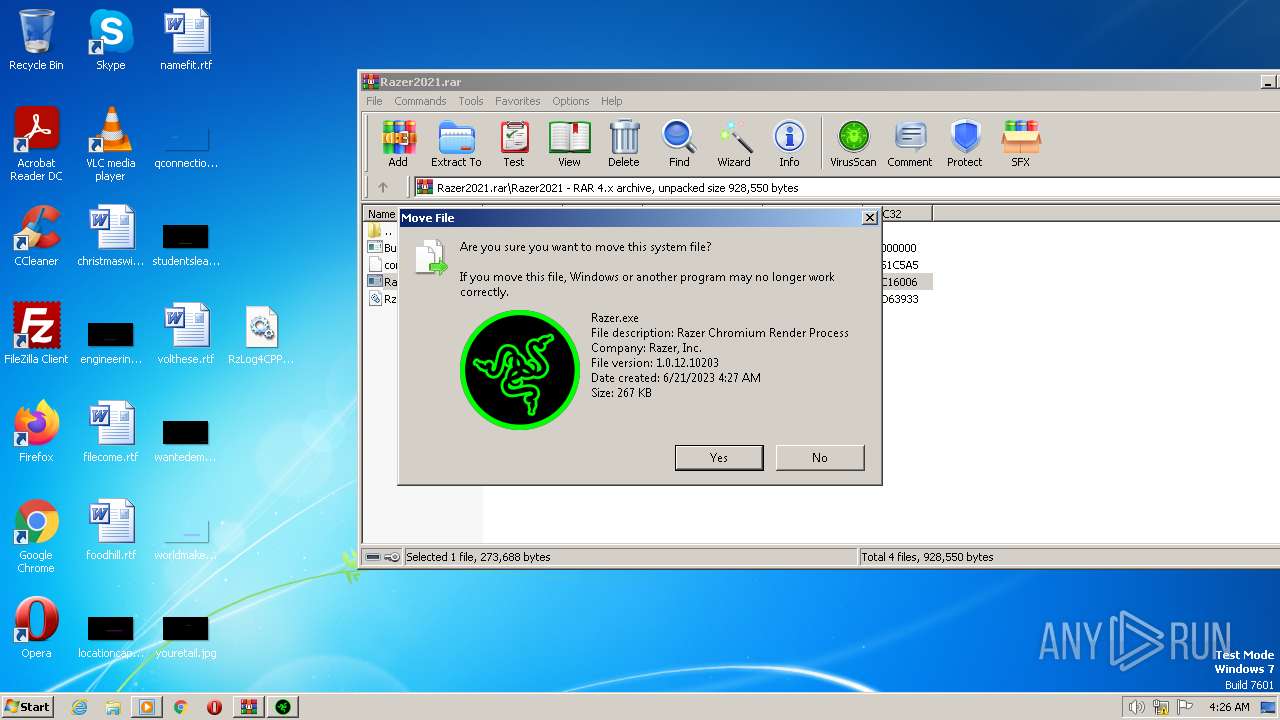
Application was dropped or rewritten from another process
- Razer.exe (PID: 2980)
- Razer.exe (PID: 2356)
Loads dropped or rewritten executable
- Razer.exe (PID: 2356)
SUSPICIOUS
Reads the Internet Settings
- explorer.exe (PID: 1068)
- rundll32.exe (PID: 3452)
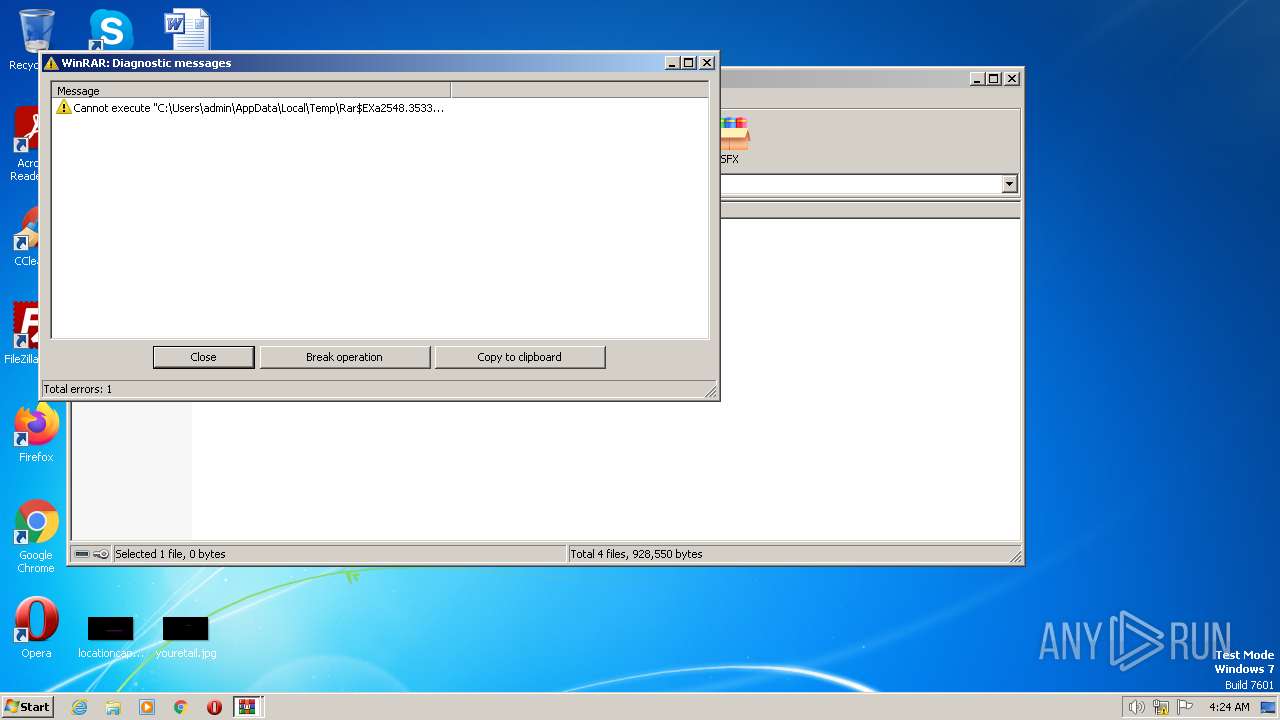
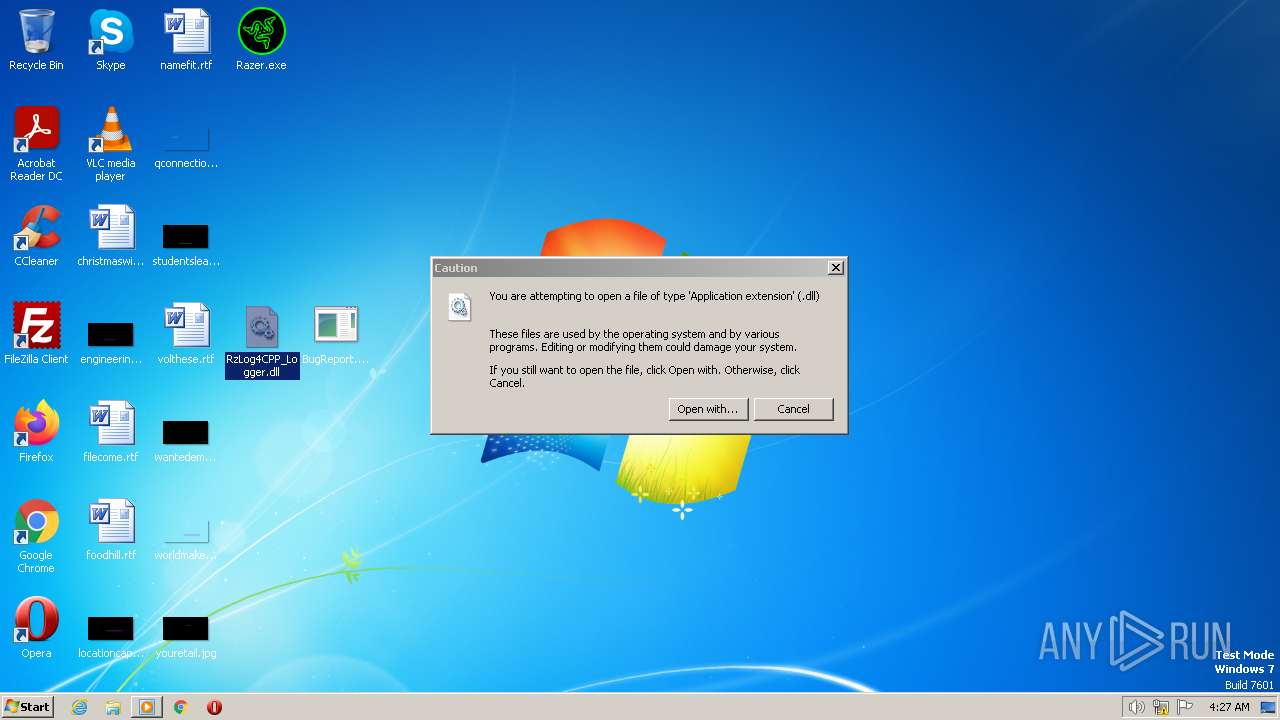
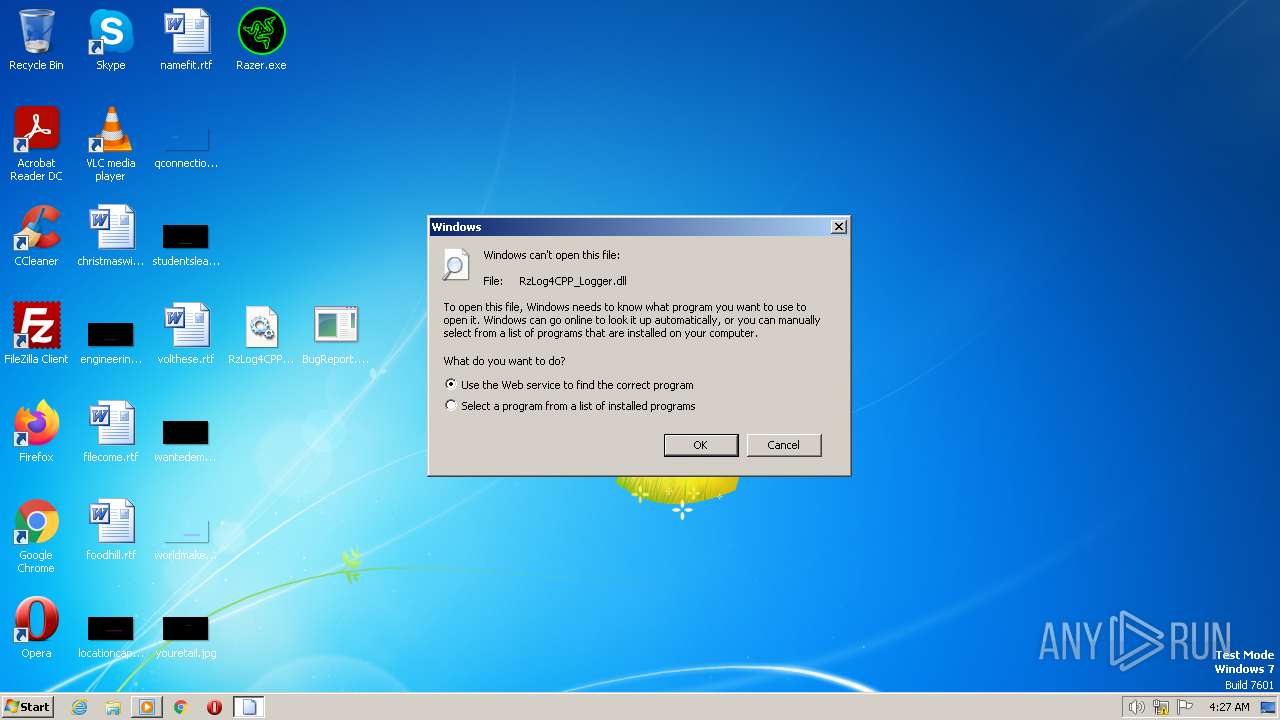
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 2548)
- explorer.exe (PID: 1068)
INFO
Loads dropped or rewritten executable
- Razer.exe (PID: 2980)
Application launched itself
- iexplore.exe (PID: 2876)
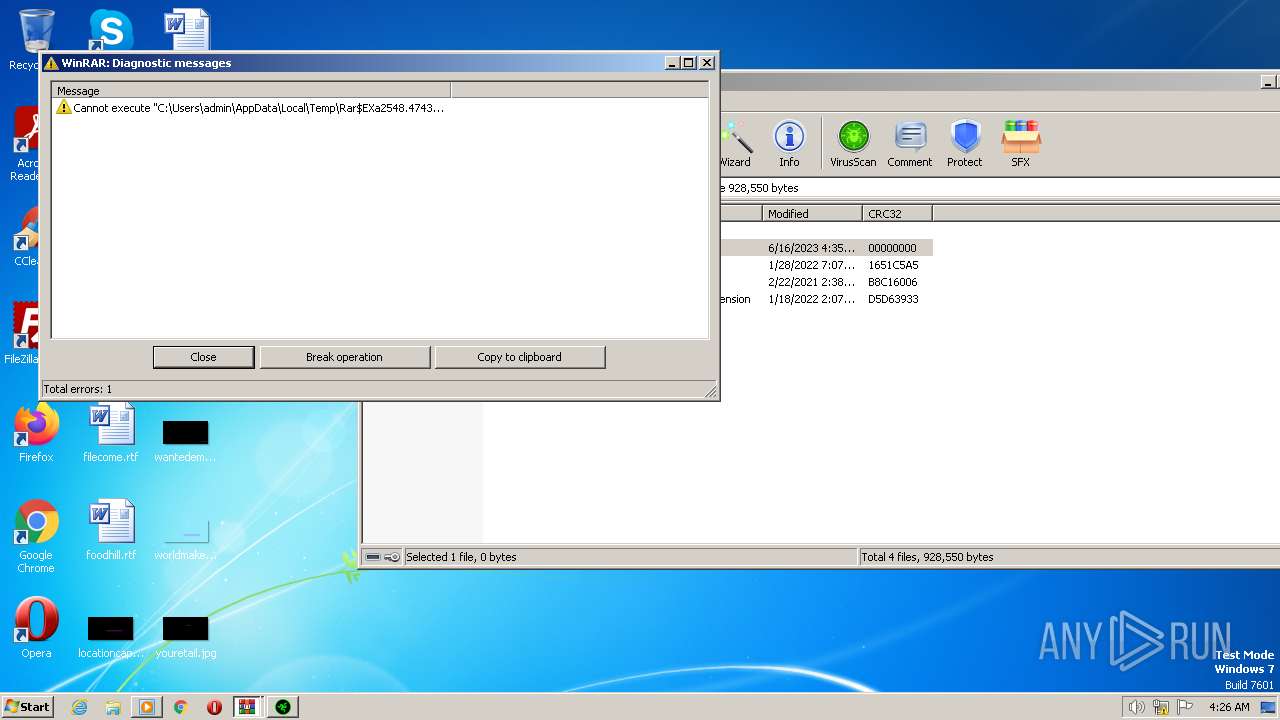
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2548)
Checks supported languages
- Razer.exe (PID: 2356)
- Razer.exe (PID: 2980)
Creates files in the program directory
- Razer.exe (PID: 2980)
The process checks LSA protection
- SearchProtocolHost.exe (PID: 2452)
- explorer.exe (PID: 932)
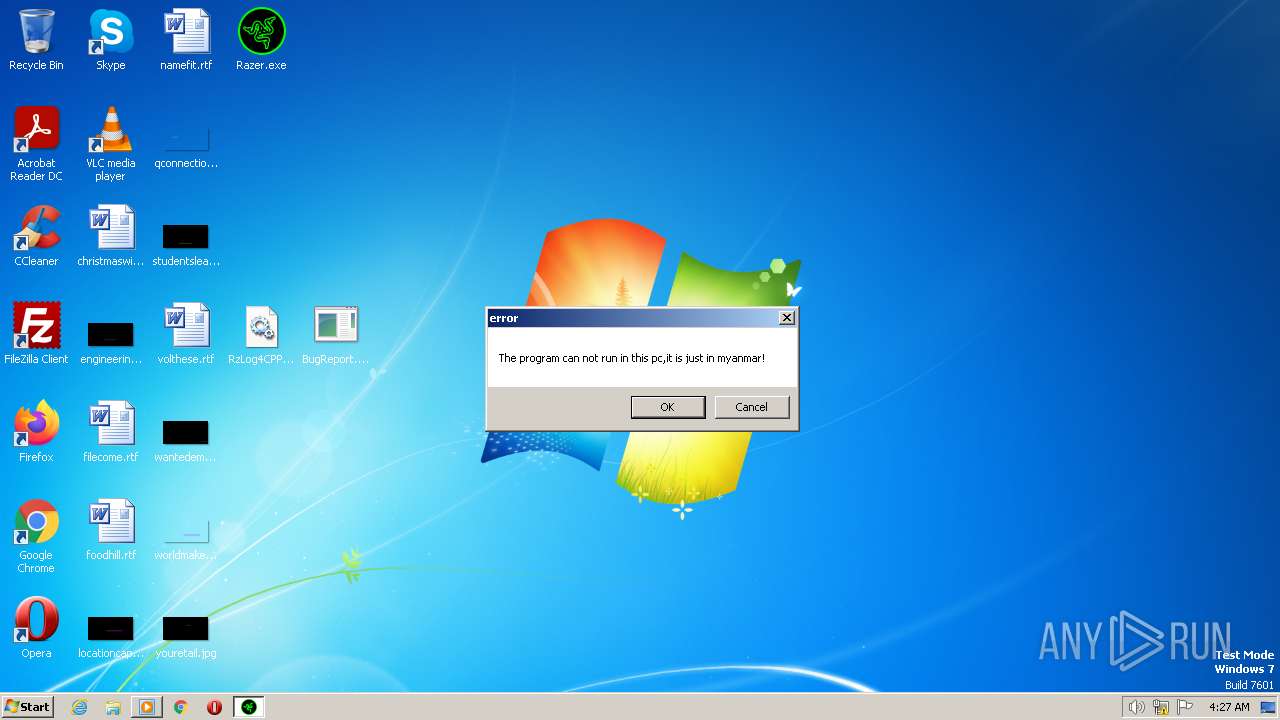
Manual execution by a user
- explorer.exe (PID: 932)
- Razer.exe (PID: 2356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
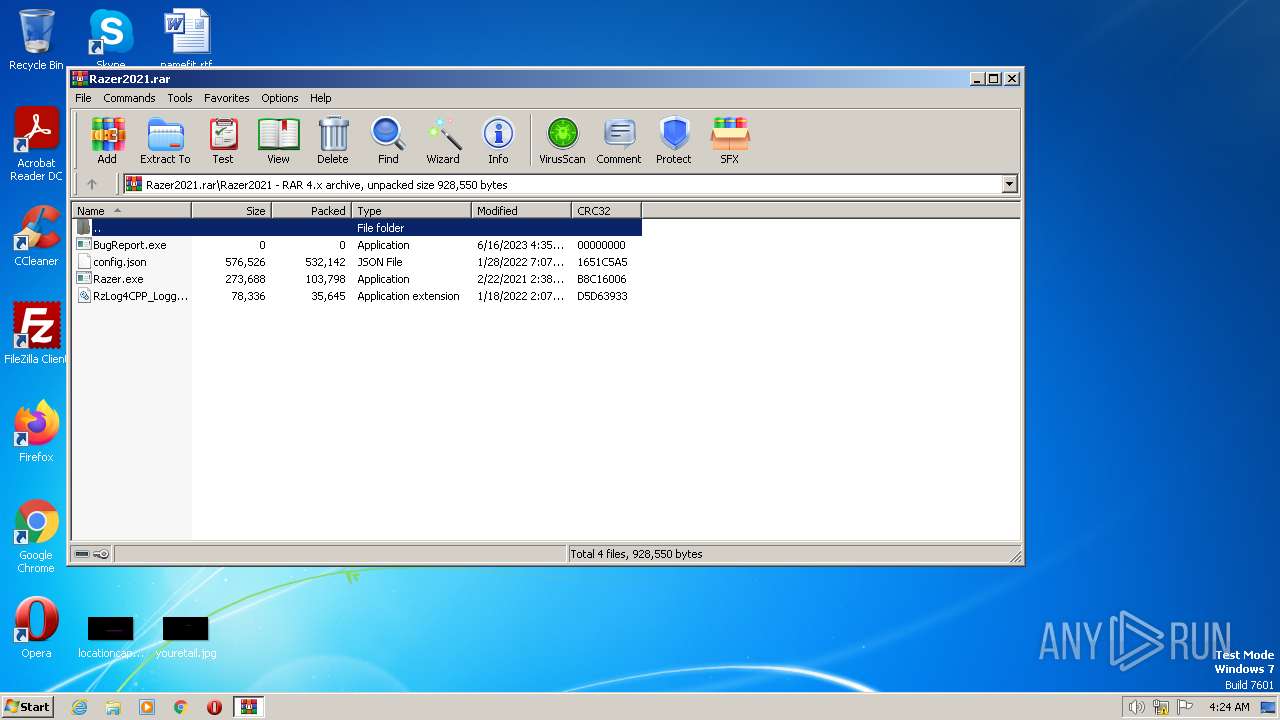
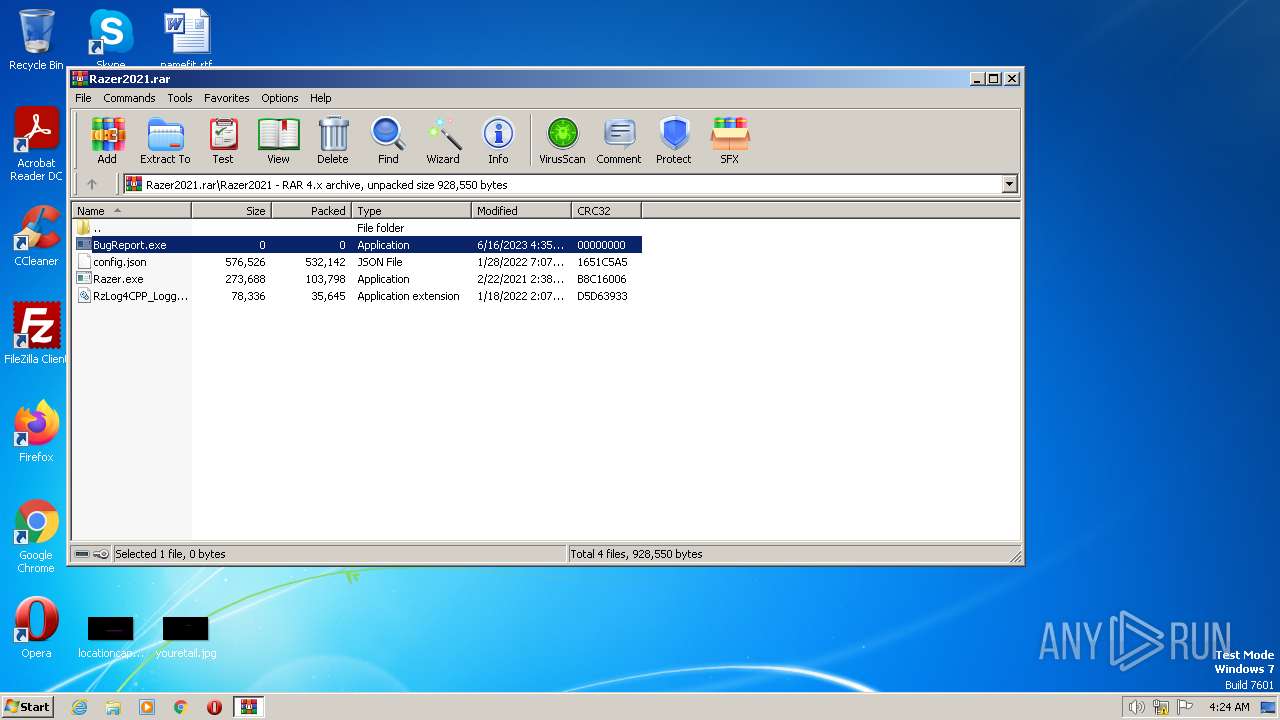
| ArchivedFileName: | Razer2021\BugReport.exe |
|---|---|
| PackingMethod: | Stored |
| ModifyDate: | 2023:06:16 16:35:04 |
| OperatingSystem: | Win32 |
| UncompressedSize: | - |
| CompressedSize: | 49 |
Total processes
54
Monitored processes
12
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 932 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1068 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2876 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2876 CREDAT:1119501 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | |||||||||||||||
| 2356 | "C:\Users\admin\Desktop\Razer.exe" | C:\Users\admin\Desktop\Razer.exe | — | explorer.exe | |||||||||||
User: admin Company: Razer, Inc. Integrity Level: MEDIUM Description: Razer Chromium Render Process Exit code: 0 Version: 1.0.12.10203 Modules
| |||||||||||||||
| 2452 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe7_ Global\UsGthrCtrlFltPipeMssGthrPipe7 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
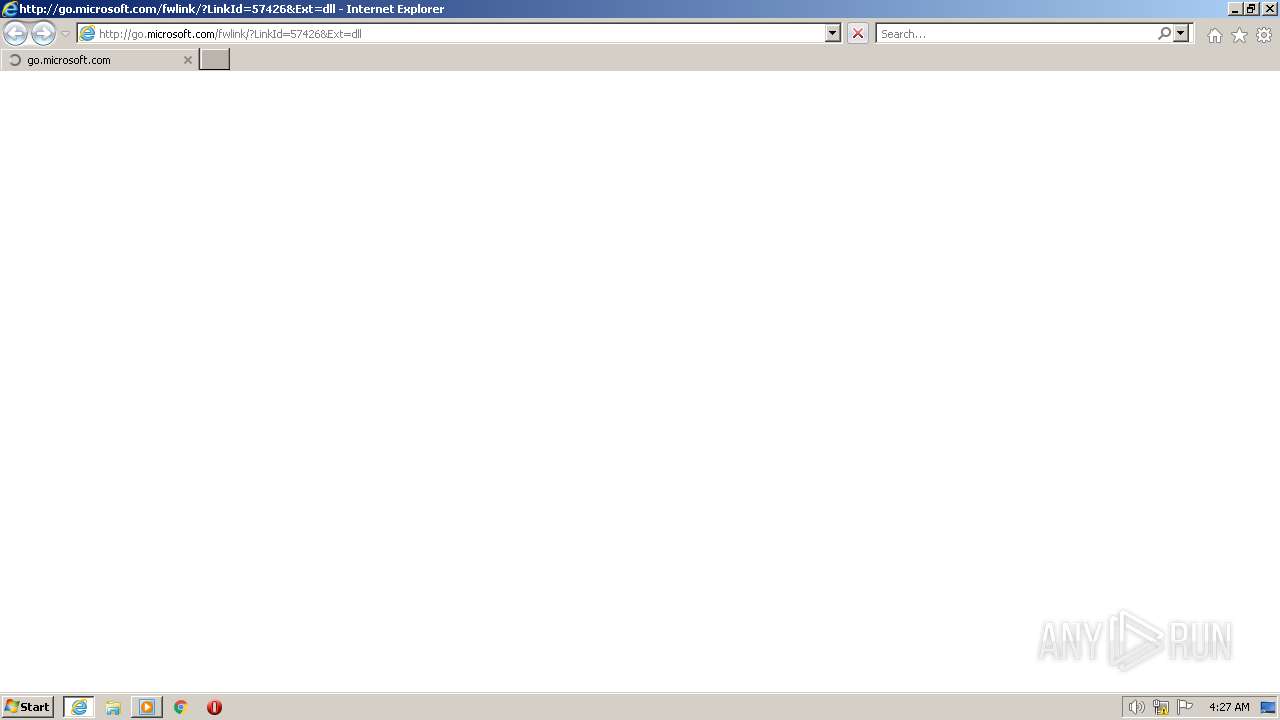
| 2520 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=57426&Ext=dll | C:\Program Files\Internet Explorer\iexplore.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | |||||||||||||||
| 2548 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Razer2021.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2576 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\RzLog4CPP_Logger.dll | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 2876 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=57426&Ext=json | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
21 734
Read events
21 328
Write events
404
Delete events
2
Modification events
| (PID) Process: | (1068) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000003D77C3133A5D7248BA6D7744BB9A3E16000000000200000000001066000000010000200000004A9CAAC251DD88A0E7E33FFB23F636A225CB7CC4485369C7C9B03862A811D096000000000E8000000002000020000000659B7585C71088AEEB1875008044DFB4B07623A0B20C3E867A78A9695191E29230000000F9C4E47AAD7D214C673E4CDC8385C59DDC5AE0E28396FCF21F9D028C590E79749BDDC16862F8E26B3D4F8E8966EEF17C4000000006EE6EDF8BC2D3544F7C9D682CF07277A50A34FA9DF6D8FB7B39CA5834F62523E20C12EF252EC87A75BE0FA4A5D7BD80B713248892E659363C3419474A1FEA18 | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
12
Suspicious files
37
Text files
160
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2548.35713\Razer2021\RzLog4CPP_Logger.dll | executable | |
MD5:DCE843E0B7B64B3B1526616073BC60F5 | SHA256:C7B7FD75CAAA8B3AD3192599A2CEBEF0A1FDA51EBBB8CA6700D25744C7AE759E | |||
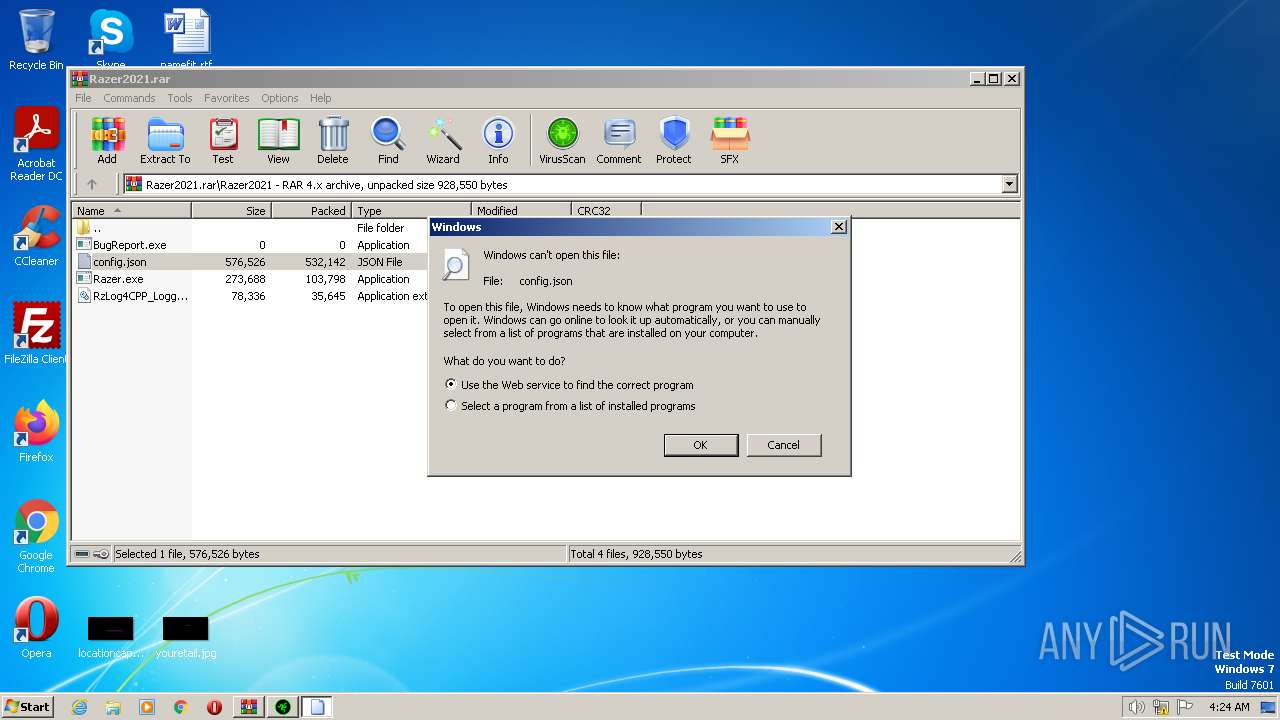
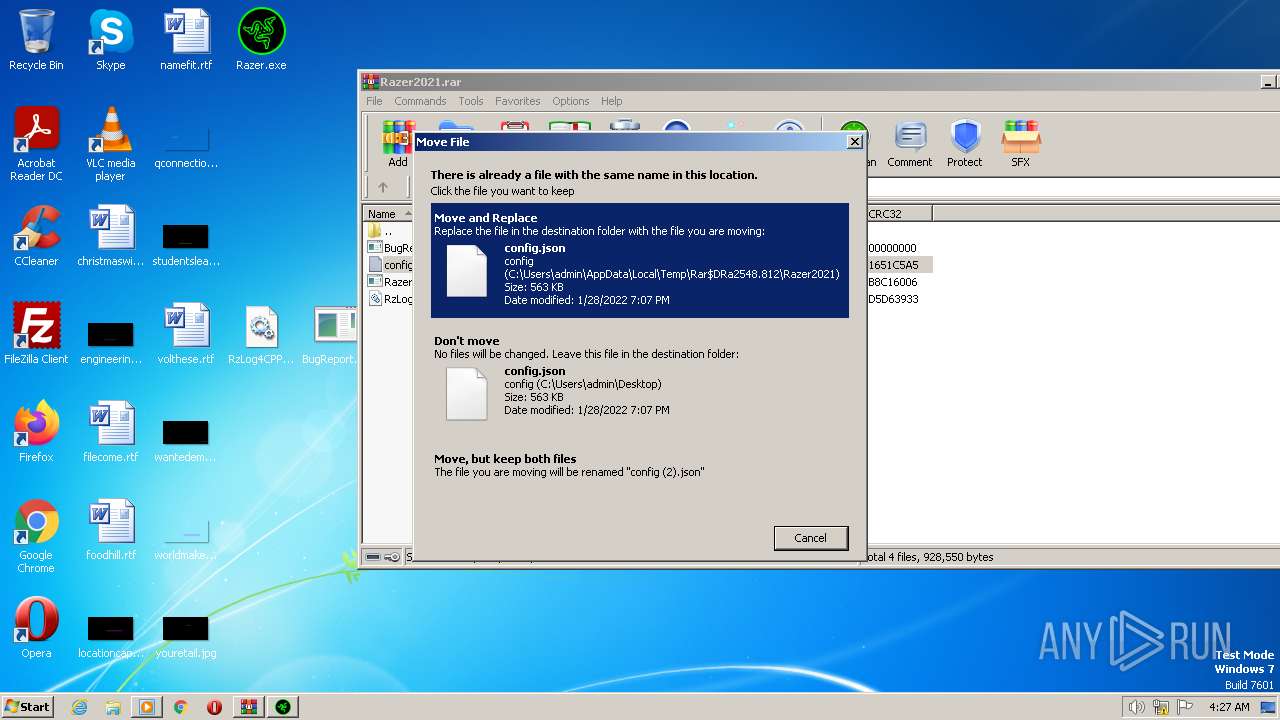
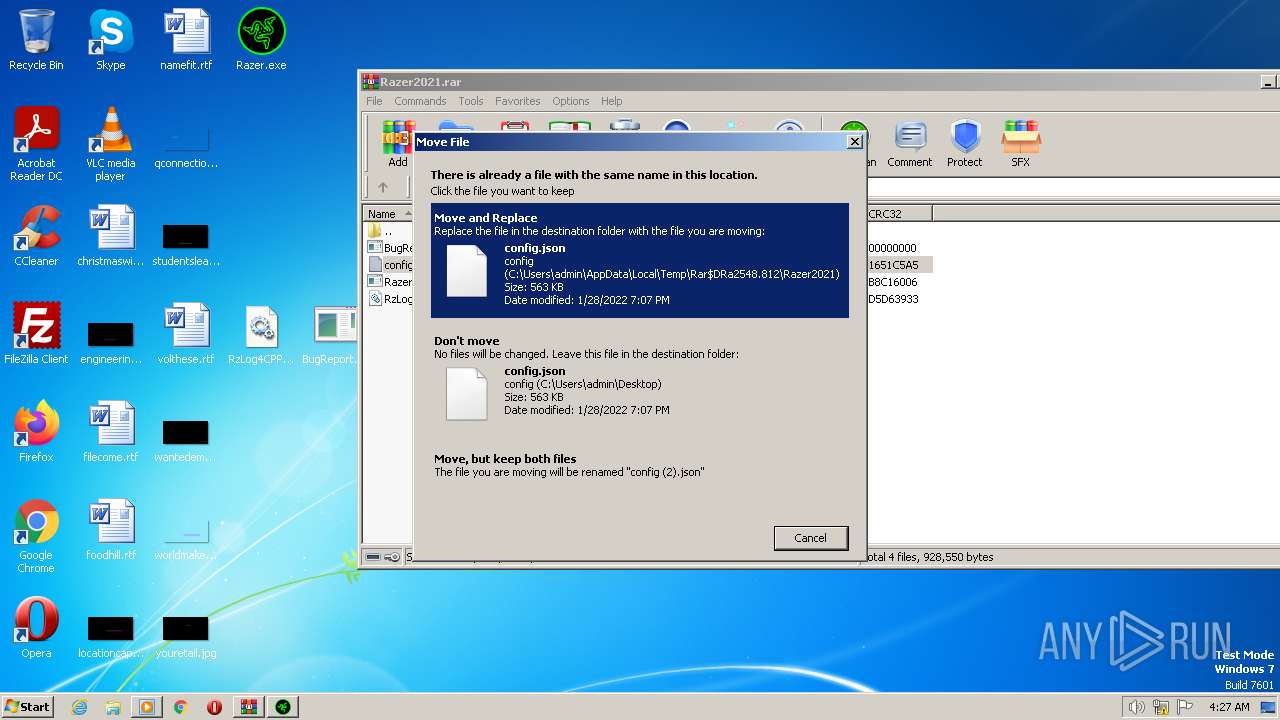
| 2548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2548.36724\config.json | binary | |
MD5:D24623F73A5A5FC7647E32AFB8089A97 | SHA256:15F5EB40D365F70710248C68C6614E21BAFB21D8B2F43E746EEB869F12387990 | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:A02F8F0114D7EABFC1B2154B28CA6C7F | SHA256:3CB8682B92B0C7A67E71CB52683E91E5E88E0AE79EF836C23D1654B0ACB477EA | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver64BD.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_E503B048B745DFA14B81FCFC68D6DECE | binary | |
MD5:51D36B998103E8B12F3A96BF99DB184F | SHA256:3A415E1E85CF58AB8F2A453616E891E8437E411A1F2378F880D8EC9C3F48B13D | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:2290D25AF6FECA0EB2570712698CF221 | SHA256:CE517D336A9C336CA9DF6018AEEDC13CC5A980976A541910EC53597E6BAF3D30 | |||
| 2548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2548.35713\Razer2021\config.json | binary | |
MD5:D24623F73A5A5FC7647E32AFB8089A97 | SHA256:15F5EB40D365F70710248C68C6614E21BAFB21D8B2F43E746EEB869F12387990 | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
56
DNS requests
28
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1356 | iexplore.exe | GET | — | 89.117.169.177:80 | http://notepad-plus-plus.org/ | LT | — | — | whitelisted |
— | — | GET | 301 | 2.16.241.10:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=dll | unknown | — | — | whitelisted |
2876 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2876 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | binary | 1.47 Kb | whitelisted |
2876 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
1356 | iexplore.exe | GET | 301 | 23.32.238.185:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=json | US | — | — | whitelisted |
1356 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
2876 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?435d617acd2c2b36 | US | compressed | 4.70 Kb | whitelisted |
2876 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | binary | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4008 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2876 | iexplore.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
2876 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1356 | iexplore.exe | 104.102.40.139:443 | go.microsoft.com | AKAMAI-AS | DE | malicious |
2876 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1356 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2876 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
shell.windows.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1356 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
— | — | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |