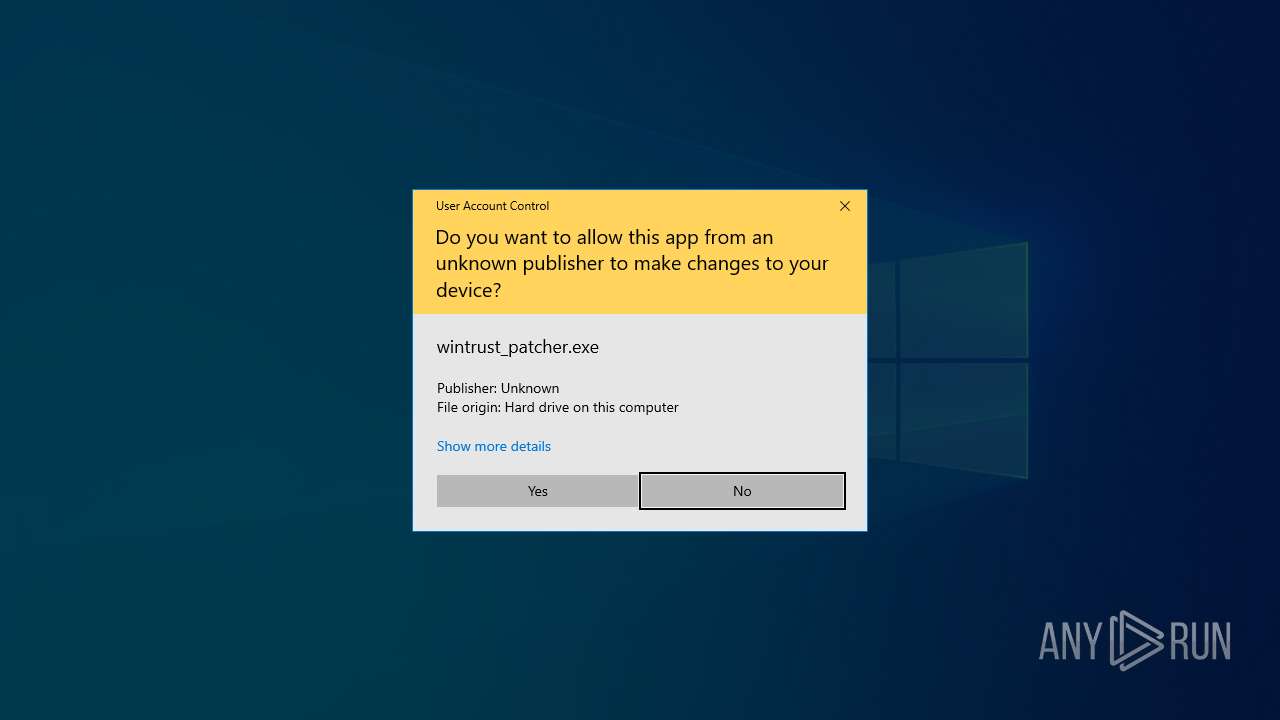
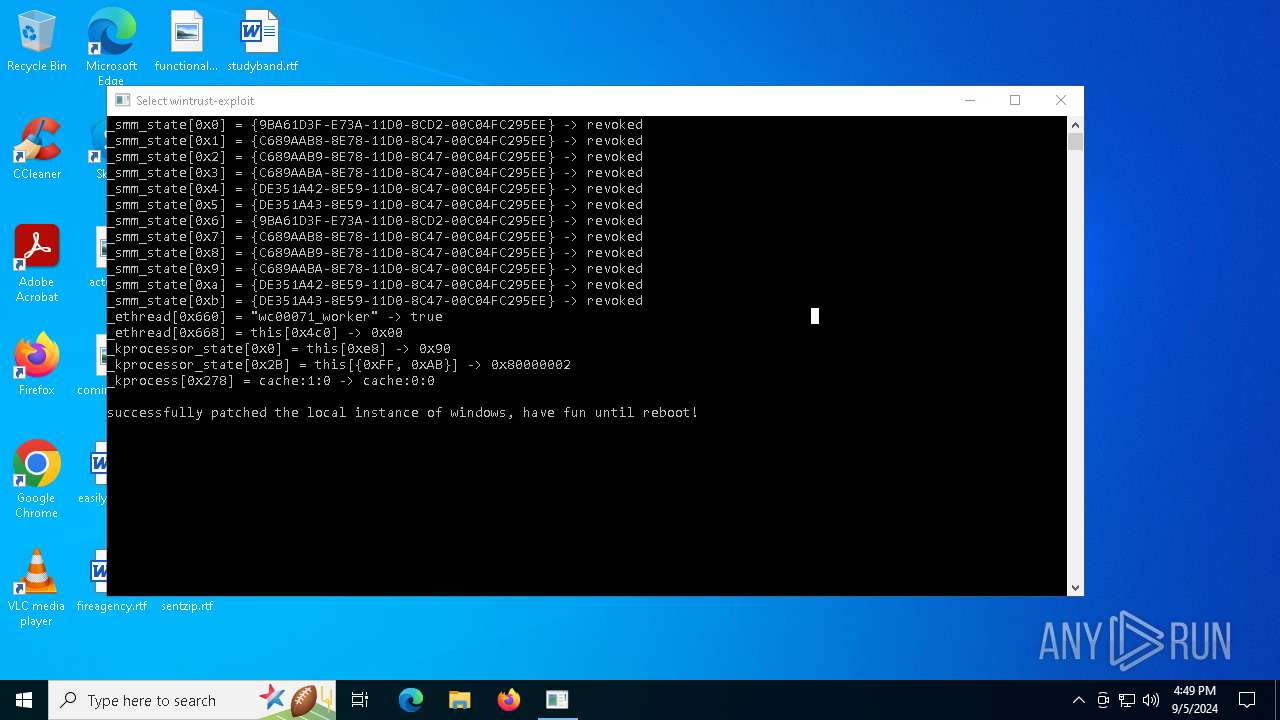
| File name: | wintrust_patcher.exe |
| Full analysis: | https://app.any.run/tasks/445a426e-eb25-4c06-b762-96861018ee28 |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2024, 16:47:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 1B30E9ACE90F8DCCEA88E5CC1C645DFD |
| SHA1: | 44F2021FD0379551CAB04BE1BCF2CB7339A9FBB9 |
| SHA256: | AF64F3897E951E11D9C2EB6C64173CF1EF780367B412B3A17F61CA6633457147 |
| SSDEEP: | 12288:vvdO0Z1hOkSqmHigpSMEHJHtqi7w3fEHqzDBPgZS9b/E9NoN:vv80Z1hOkHsEH9tDsb4ZSx/E9 |
MALICIOUS
Application was injected by another process
- csrss.exe (PID: 620)
Runs injected code in another process
- wintrust_patcher.exe (PID: 6656)
SUSPICIOUS
Reads security settings of Internet Explorer
- GameBar.exe (PID: 4952)
- StartMenuExperienceHost.exe (PID: 5480)
Uses TASKKILL.EXE to kill process
- wintrust_patcher.exe (PID: 6656)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 5480)
- SearchApp.exe (PID: 6960)
The process executes via Task Scheduler
- explorer.exe (PID: 6728)
INFO
Reads the computer name
- wintrust_patcher.exe (PID: 6656)
- GameBar.exe (PID: 4952)
- TextInputHost.exe (PID: 5780)
- StartMenuExperienceHost.exe (PID: 5480)
- SearchApp.exe (PID: 6960)
Reads security settings of Internet Explorer
- explorer.exe (PID: 6728)
Checks supported languages
- TextInputHost.exe (PID: 5780)
- GameBar.exe (PID: 4952)
- StartMenuExperienceHost.exe (PID: 5480)
- wintrust_patcher.exe (PID: 6656)
- SearchApp.exe (PID: 6960)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 5480)
- SearchApp.exe (PID: 6960)
Checks proxy server information
- SearchApp.exe (PID: 6960)
- explorer.exe (PID: 6728)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 6960)
Reads the software policy settings
- SearchApp.exe (PID: 6960)
Creates files or folders in the user directory
- explorer.exe (PID: 6728)
Reads Environment values
- SearchApp.exe (PID: 6960)
Sends debugging messages
- StartMenuExperienceHost.exe (PID: 5480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:05 12:38:50+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 334848 |
| InitializedDataSize: | 273920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2f200 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
150
Monitored processes
16
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,20480,768 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1860 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2820 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | explorer.exe | C:\Windows\explorer.exe | — | wintrust_patcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4952 | "C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe" -ServerName:App.AppXbdkk0yrkwpcgeaem8zk81k8py1eaahny.mca | C:\Program Files\WindowsApps\Microsoft.XboxGamingOverlay_2.34.28001.0_x64__8wekyb3d8bbwe\GameBar.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 4976 | "C:\Users\admin\Desktop\wintrust_patcher.exe" | C:\Users\admin\Desktop\wintrust_patcher.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5048 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5292 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wintrust_patcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5480 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5780 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
Total events
26 169
Read events
25 884
Write events
259
Delete events
26
Modification events
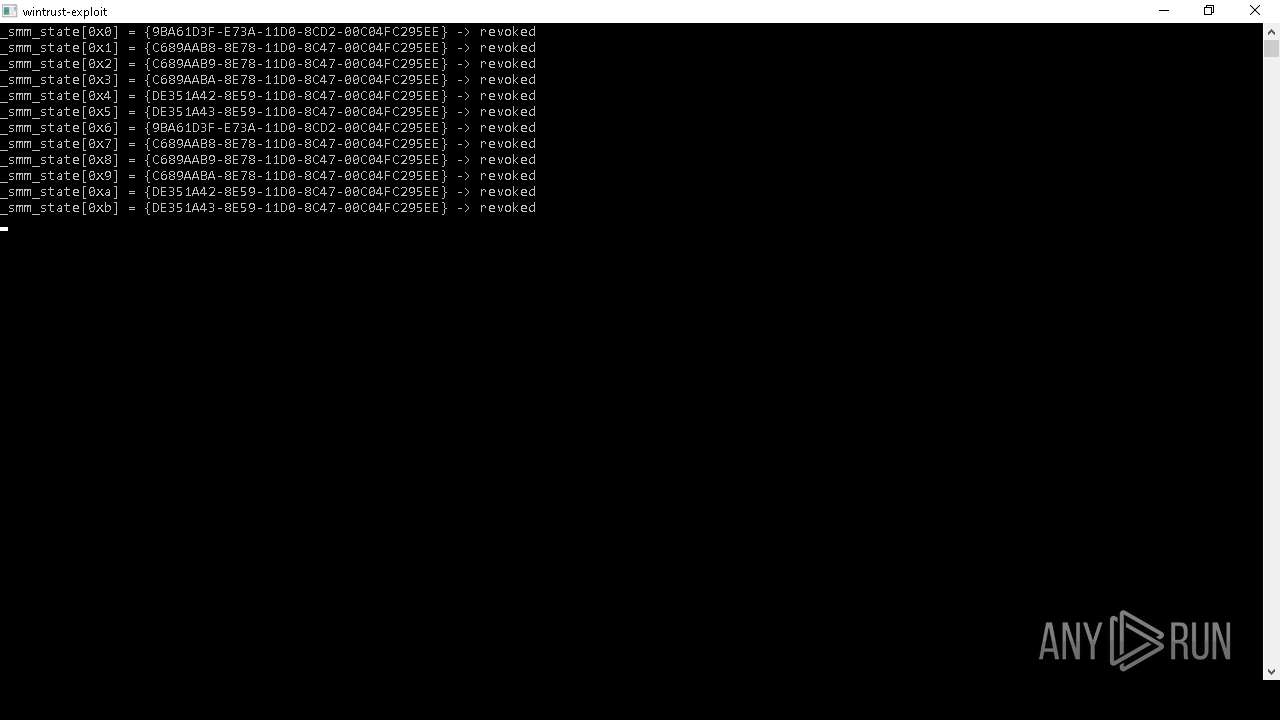
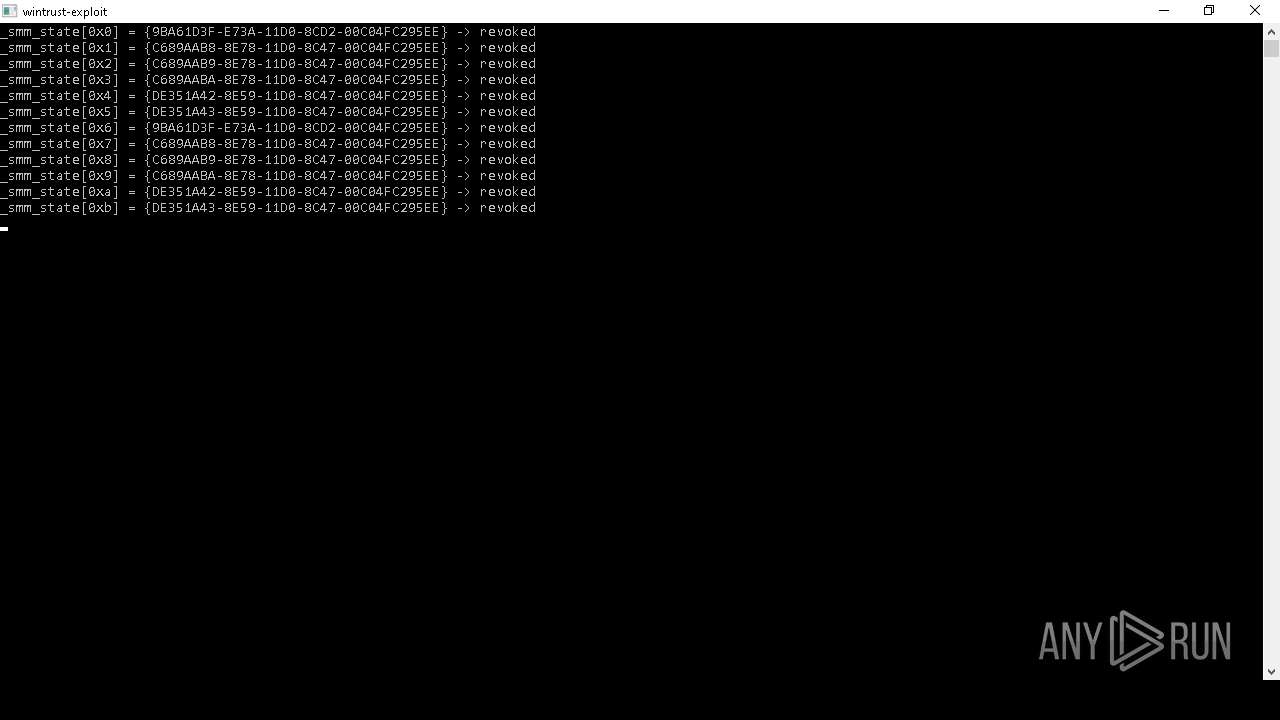
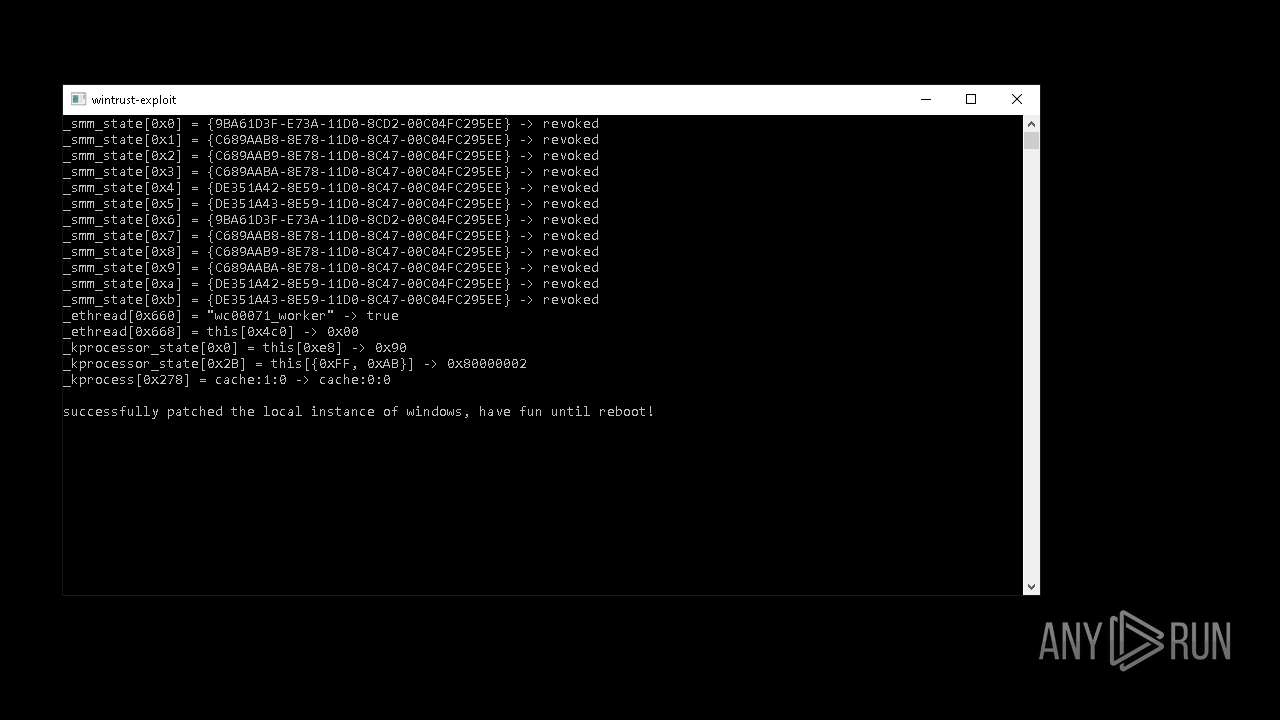
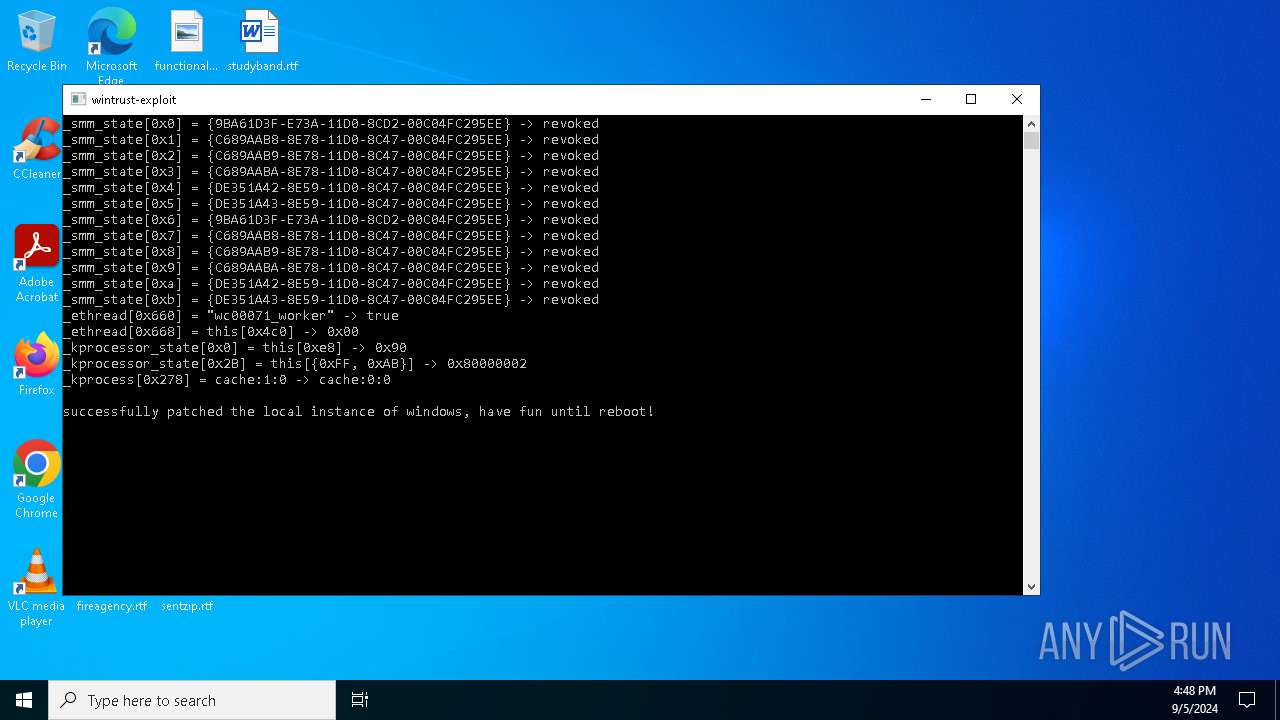
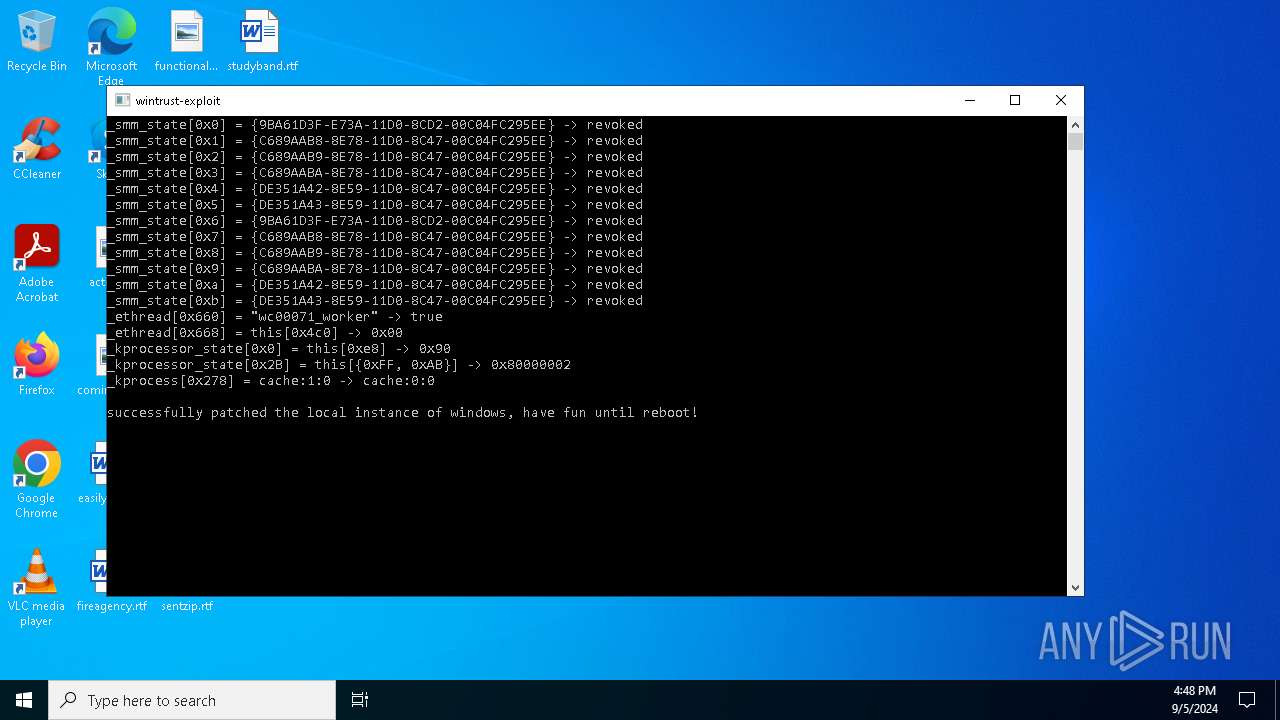
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{9BA61D3F-E73A-11D0-8CD2-00C04FC295EE} |
| Operation: | write | Name: | FuncName |
Value: DbgUiContinue | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{9BA61D3F-E73A-11D0-8CD2-00C04FC295EE} |
| Operation: | write | Name: | Dll |
Value: ntdll.dll | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{C689AAB8-8E78-11D0-8C47-00C04FC295EE} |
| Operation: | write | Name: | FuncName |
Value: DbgUiContinue | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{C689AAB8-8E78-11D0-8C47-00C04FC295EE} |
| Operation: | write | Name: | Dll |
Value: ntdll.dll | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{C689AAB9-8E78-11D0-8C47-00C04FC295EE} |
| Operation: | write | Name: | FuncName |
Value: DbgUiContinue | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{C689AAB9-8E78-11D0-8C47-00C04FC295EE} |
| Operation: | write | Name: | Dll |
Value: ntdll.dll | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{C689AABA-8E78-11D0-8C47-00C04FC295EE} |
| Operation: | write | Name: | FuncName |
Value: DbgUiContinue | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{C689AABA-8E78-11D0-8C47-00C04FC295EE} |
| Operation: | write | Name: | Dll |
Value: ntdll.dll | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{DE351A42-8E59-11D0-8C47-00C04FC295EE} |
| Operation: | write | Name: | FuncName |
Value: DbgUiContinue | |||
| (PID) Process: | (6656) wintrust_patcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{DE351A42-8E59-11D0-8C47-00C04FC295EE} |
| Operation: | write | Name: | Dll |
Value: ntdll.dll | |||
Executable files
1
Suspicious files
56
Text files
196
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\QNBBNqWD9F_Blep-UqQSqnMp-FI[1].css | text | |
MD5:77373397A17BD1987DFCA2E68D022ECF | SHA256:A319AF2E953E7AFDA681B85A62F629A5C37344AF47D2FCD23AB45E1D99497F13 | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\2vFjm7OuCr69owbTTGwUpaL64HQ.gz[1].js | text | |
MD5:E2D80435A17A30FC6CC456072629DBAA | SHA256:C4A1457E54DE445920E2CD90AF97D2F04563C7F235884BF151858769D5371C70 | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:C3CE93DEEAF8BA7D67D672B5057DBA53 | SHA256:FD4017A42C31292F7AF8E7A994518F53647284A0EE3E5D8114070C26F98122ED | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\4-xJy3tX6bM2BGl5zKioiEcQ1TU[1].css | text | |
MD5:94D8383805B336E533D1D234AAA98A21 | SHA256:699D6C87C646D3875C45FAB214BFE2E385B54F325F25818C72C2C45C1A5F6897 | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\4bnLx4S3ZRMpYV30k3R5vRy8JVg[1].js | text | |
MD5:97540BC45CFB7C7C4D859A7E1CE839BA | SHA256:4AE944B4A382D05A8A5B657105ADD88DD8B8F59D6309567E179CA64DF19F6075 | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\57PGj0svtg0ZIpoZH9o5Ed_b31E.gz[1].js | text | |
MD5:3C3306A0146D10C7CAF2E5AE0E82C680 | SHA256:9699943EC559B77B414C3ED01BE8DC7BFB597D0B95525EA1DFE5643353619BCA | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\0jUdtV12Tn_stZnlwEN7jHJWY2Y.gz[1].js | text | |
MD5:8C0F73D4C854DC52B555898FEF7EDB54 | SHA256:B652F917E744E7A4EADB5DF108D622FD18C793E80445FAA69B1BFFC97BE2529E | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\T1ni9CBvrTdDXEh6rqJISWeu4Uc[1].css | text | |
MD5:F023E6FBB7BA77CA3622C89775AC28BC | SHA256:F8B6906C129A7E5AE0BEA2D9AAF3299E1ED58224E3A2E6966FC1F7B8F38A7CB0 | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\-lxTjronWiCCazqIxFTp4HrDoXc.gz[1].js | text | |
MD5:8465A334065673EB6A6487C8D87539DB | SHA256:84ED6C495B322B0F2213CC33EC6C652D84D82E010C928B1141DB2290D4365F3D | |||
| 6960 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\65\1p7Pm8MlCViA2LDR4P2jaN0n9x8.gz[1].js | text | |
MD5:84E5E30D4685F53F1FAB2C084CC2A0B9 | SHA256:97427B4768906C726FD8DB3E9DE92D6117B6E2B6FF58ECAEBB7FFD4C6C81A1D2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
54
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4956 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4956 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6960 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
6192 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6268 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3540 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |