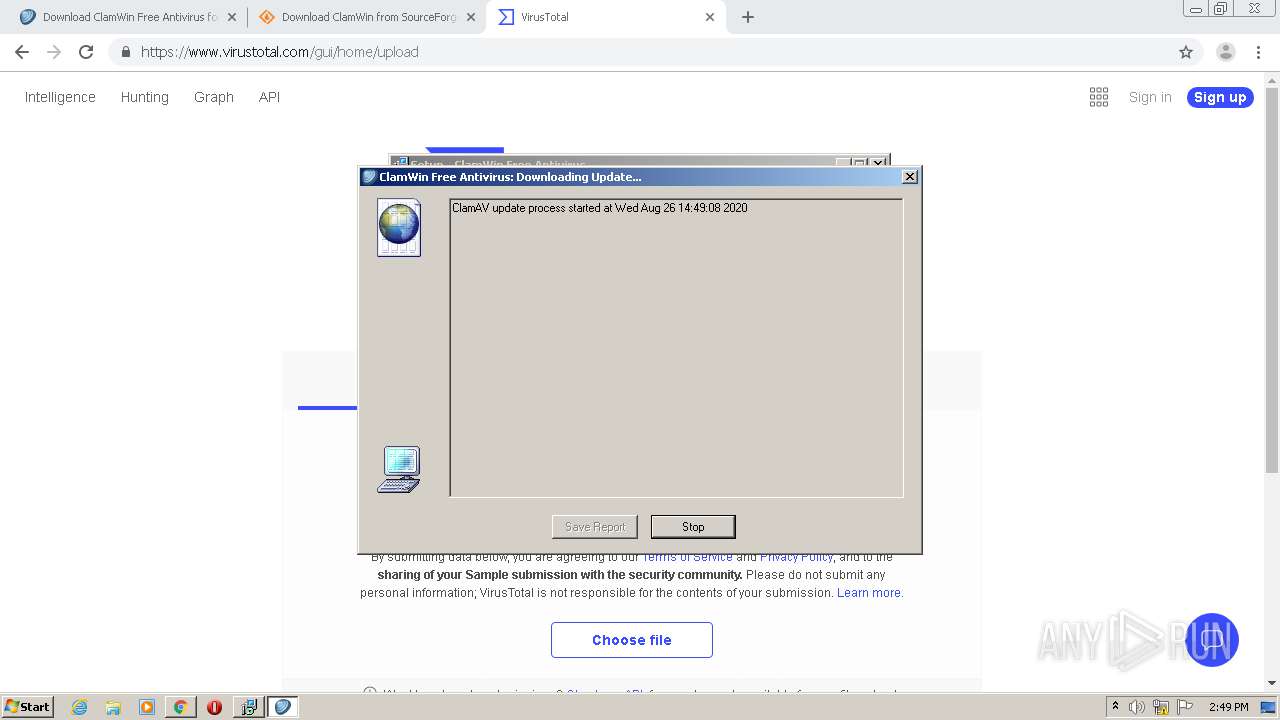
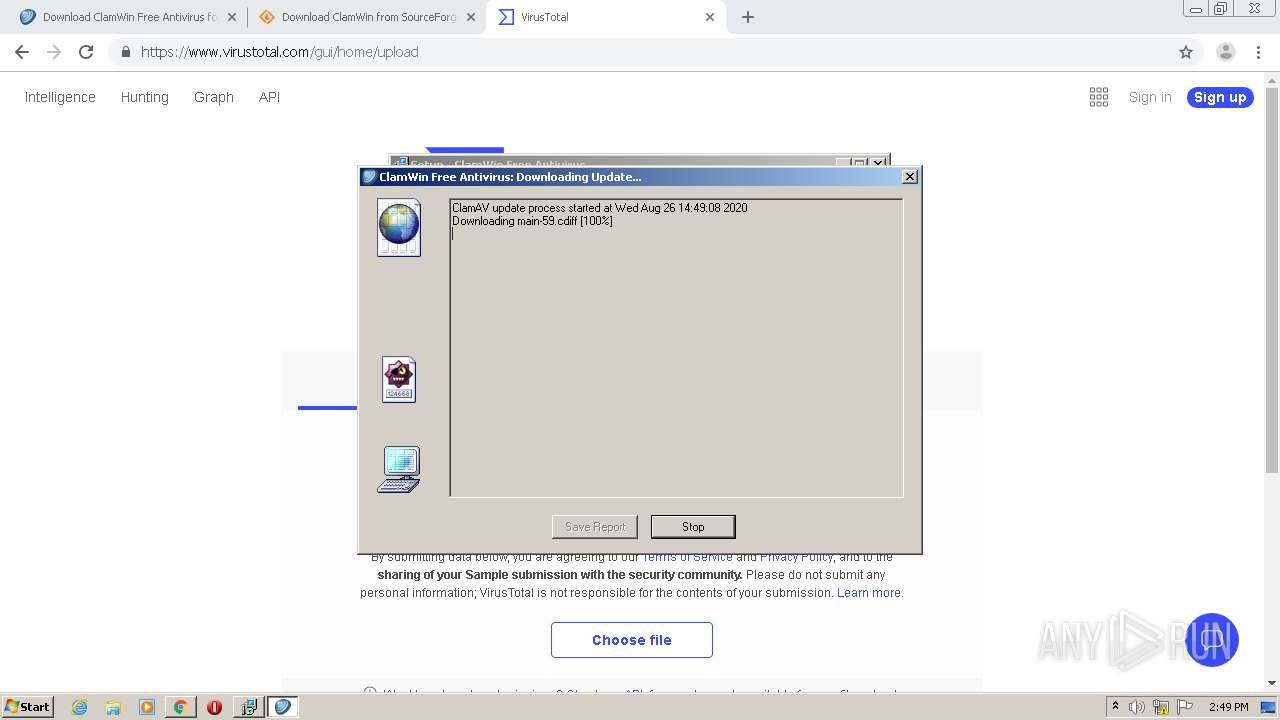
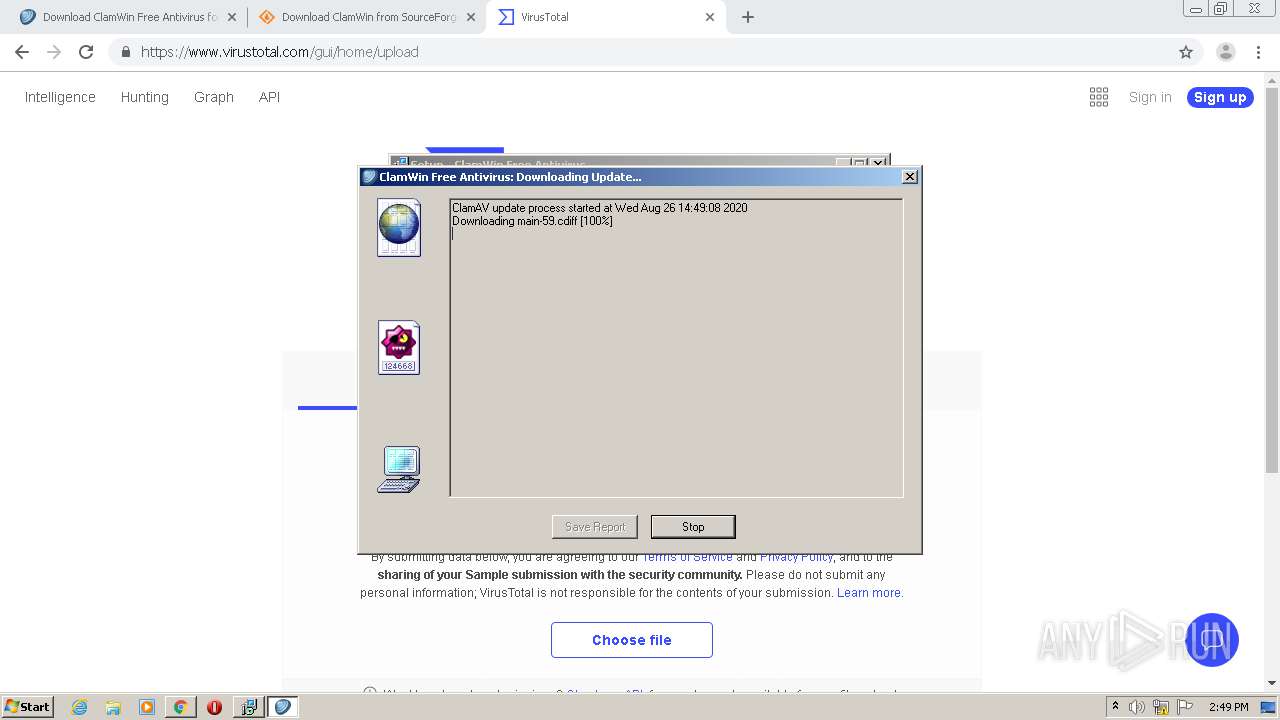
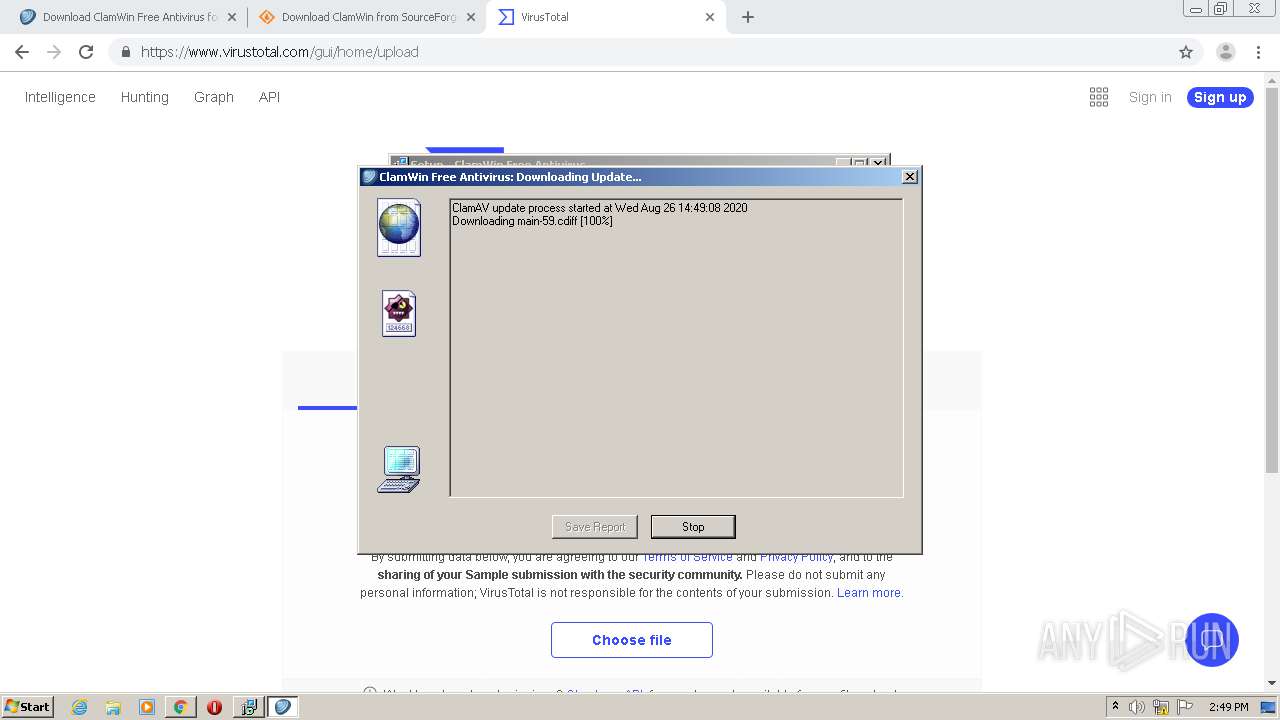
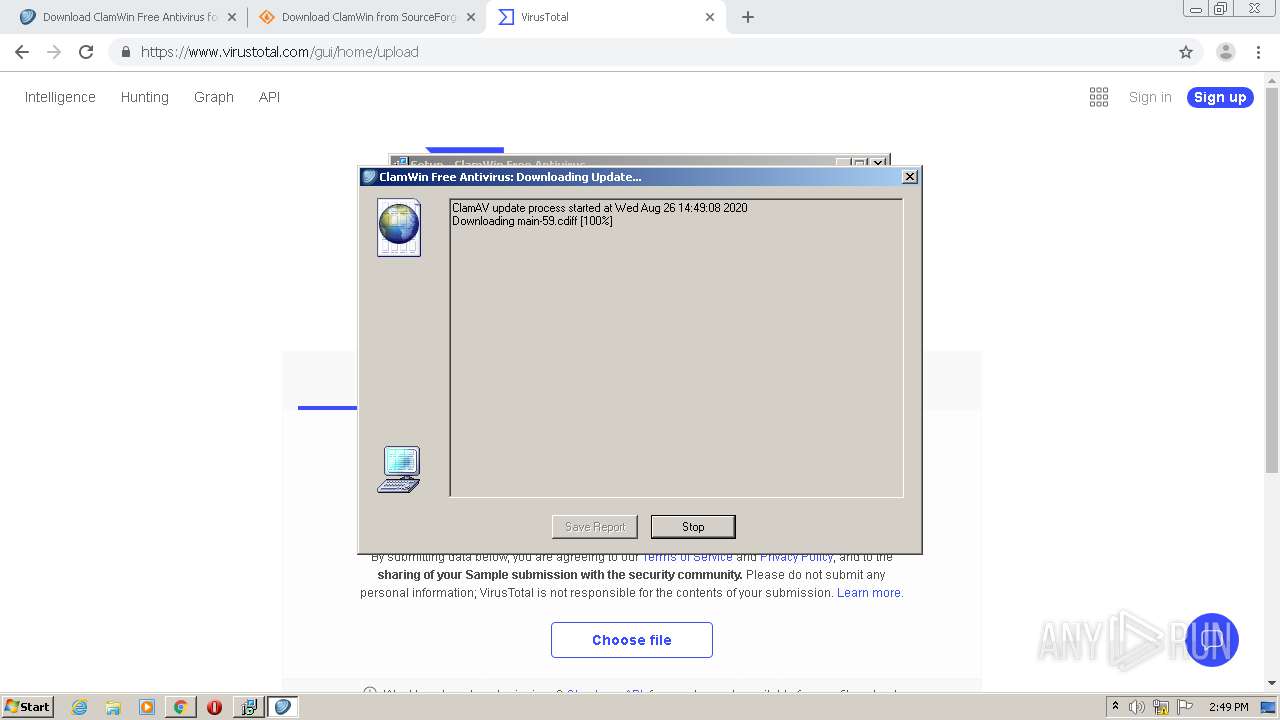
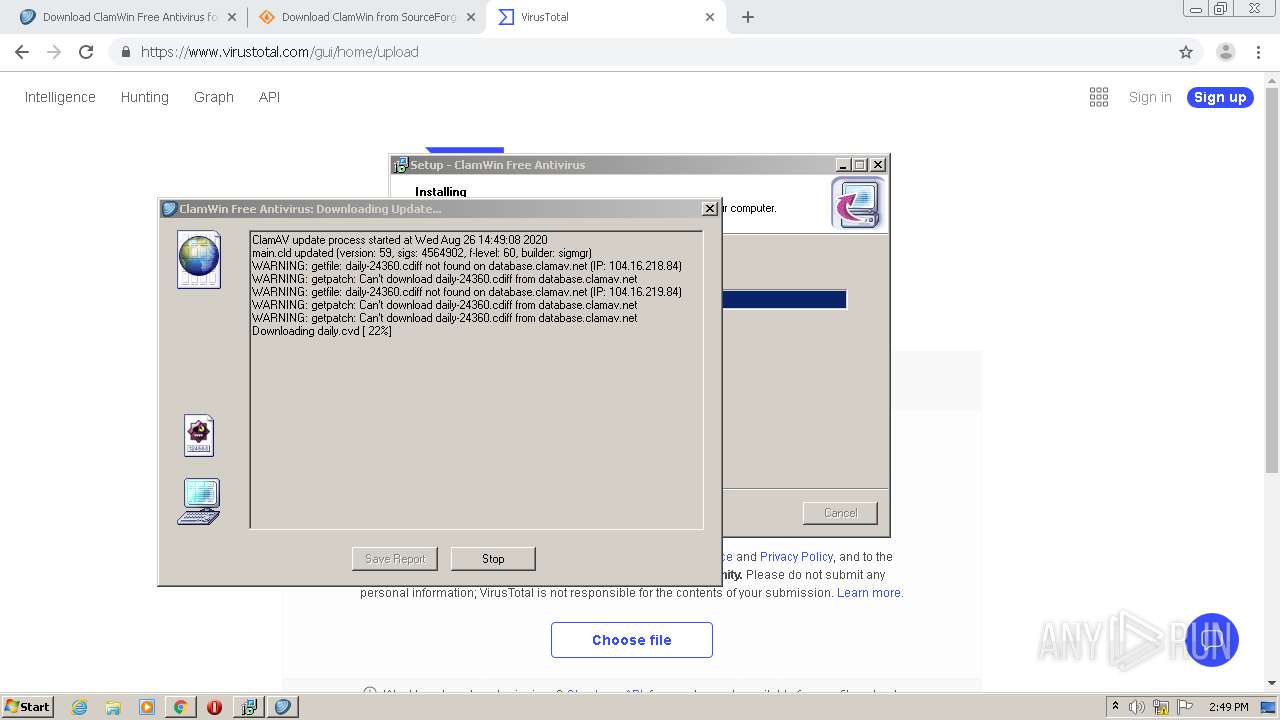
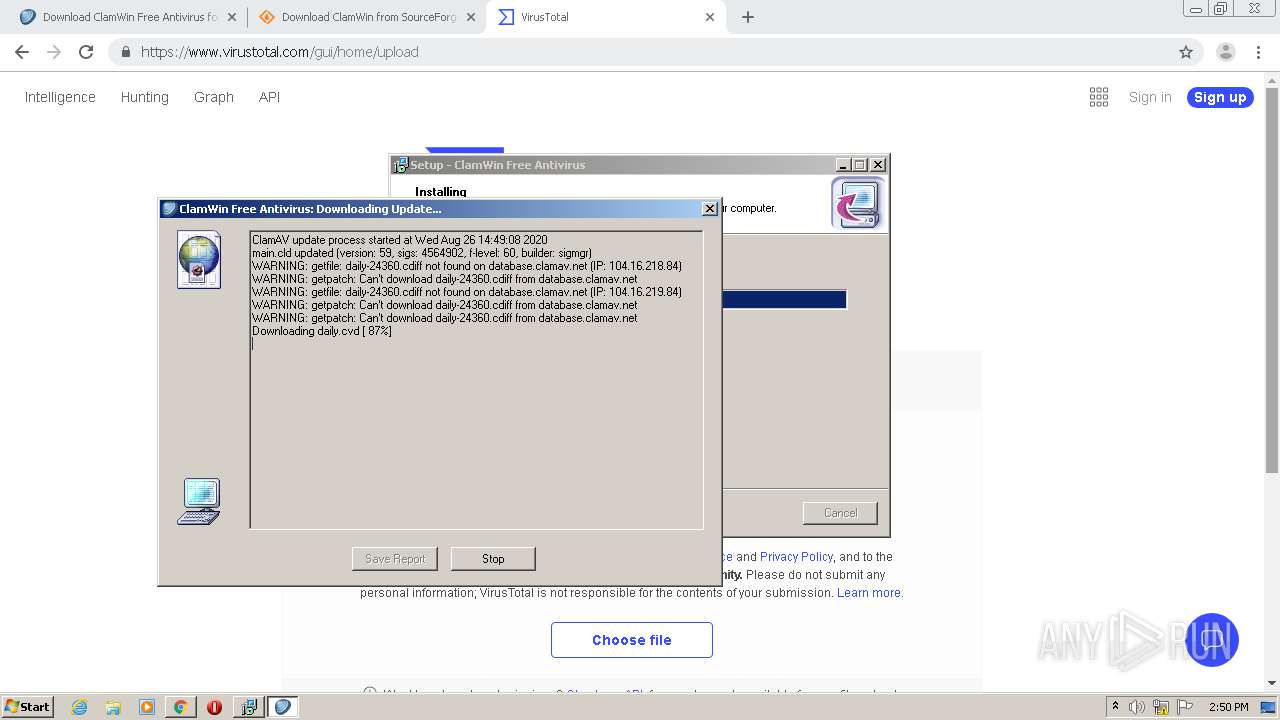
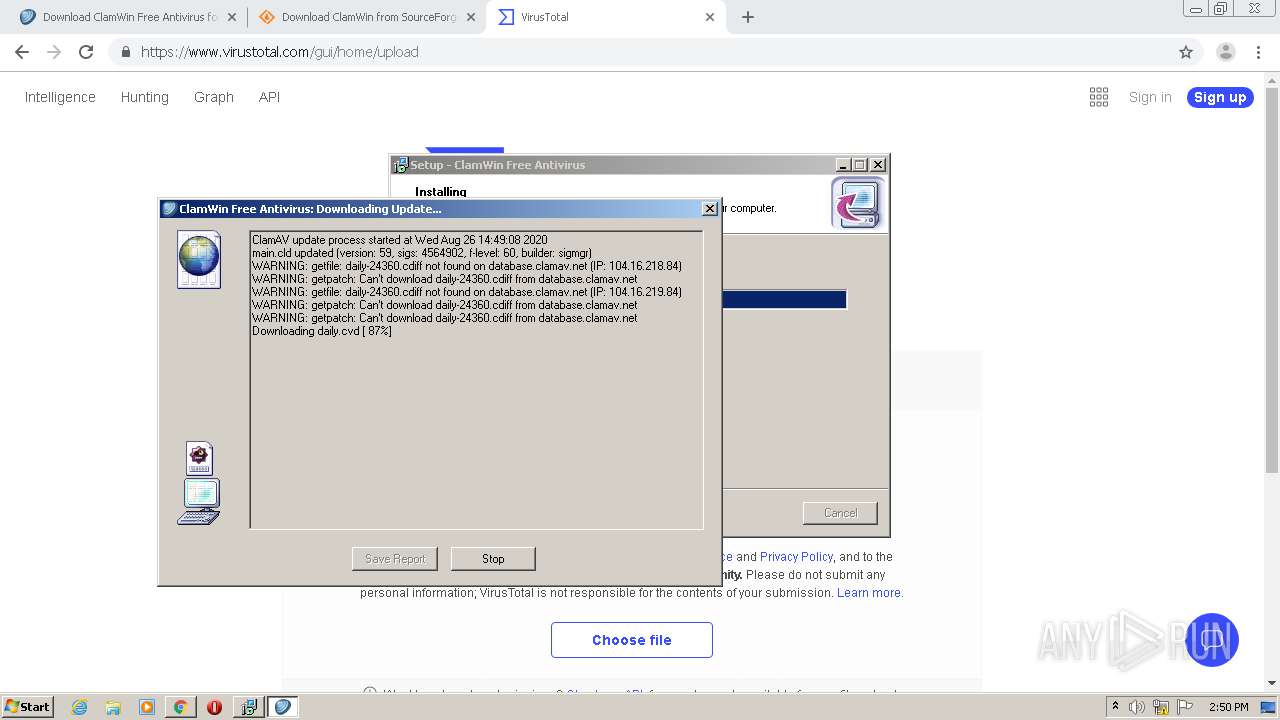
| URL: | http://www.clamwin.com/content/view/18/46/ |
| Full analysis: | https://app.any.run/tasks/7461d281-a436-40cf-a301-dce2c03ddd1a |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2020, 13:45:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | ECDD9D426435A1D83CF48140060C772B |
| SHA1: | D9E5A9A522E515CEB1DAC04450278FAF8B24D877 |
| SHA256: | AF537F4D02D5ACB97DEBC2742B65B8DDA38D1F87CD6F94EE98D2D6DC7CD6FEAF |
| SSDEEP: | 3:N1KJS4gOK2KL8skZ:Cc4PK2QMZ |
MALICIOUS
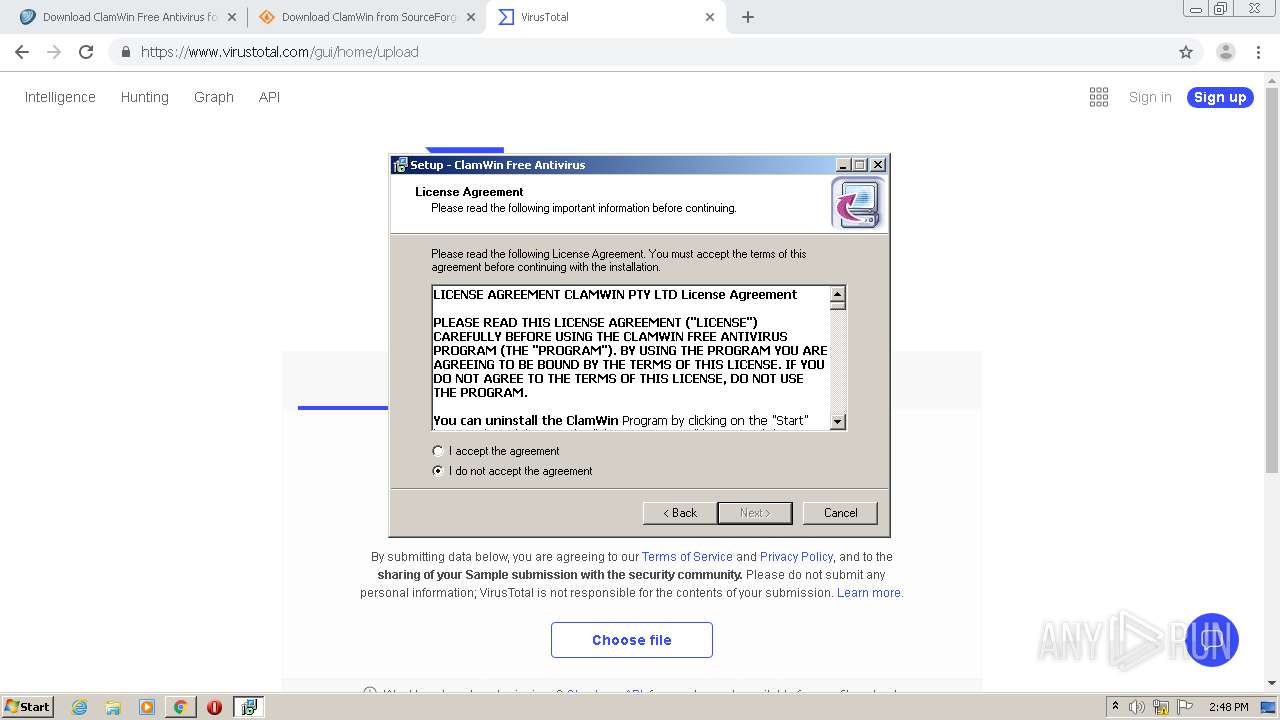
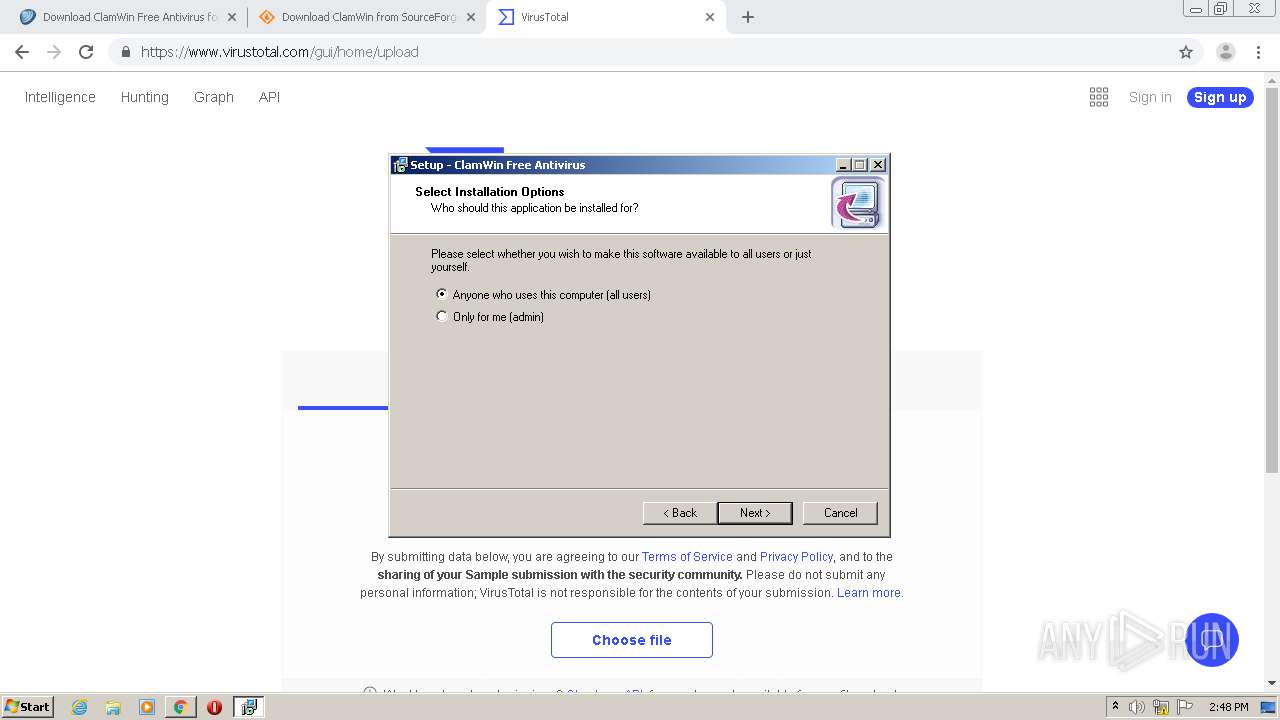
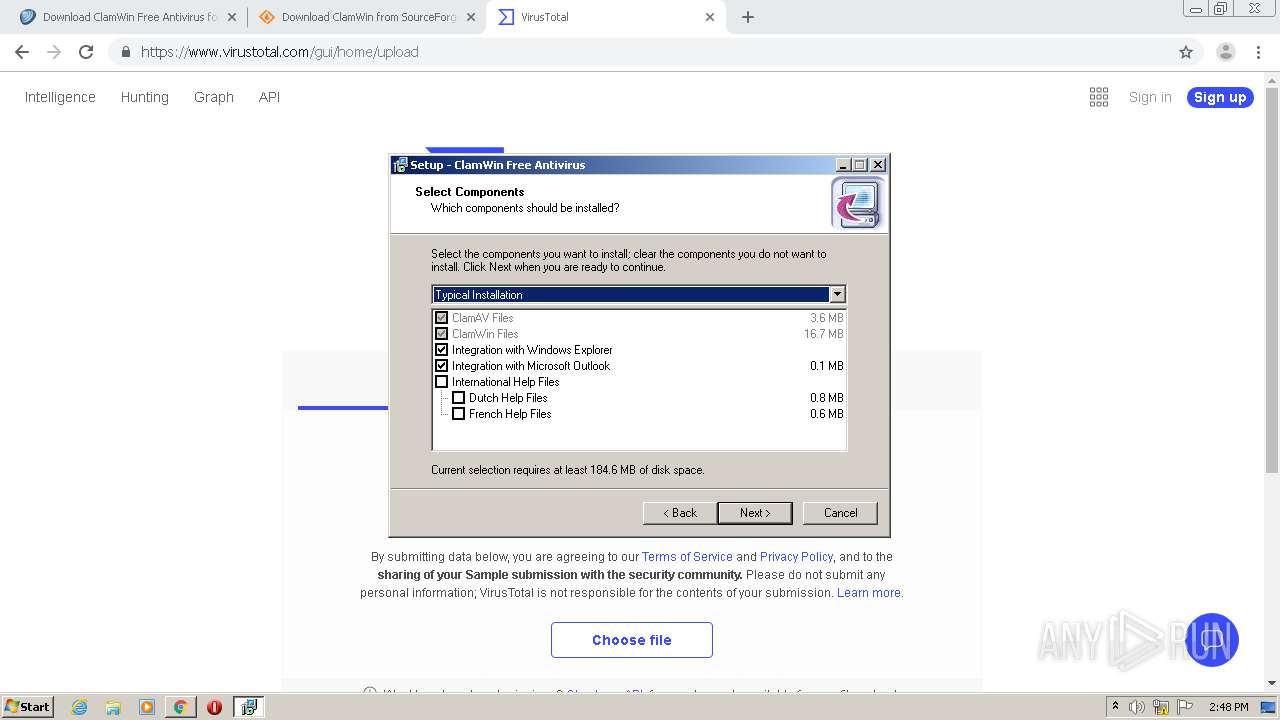
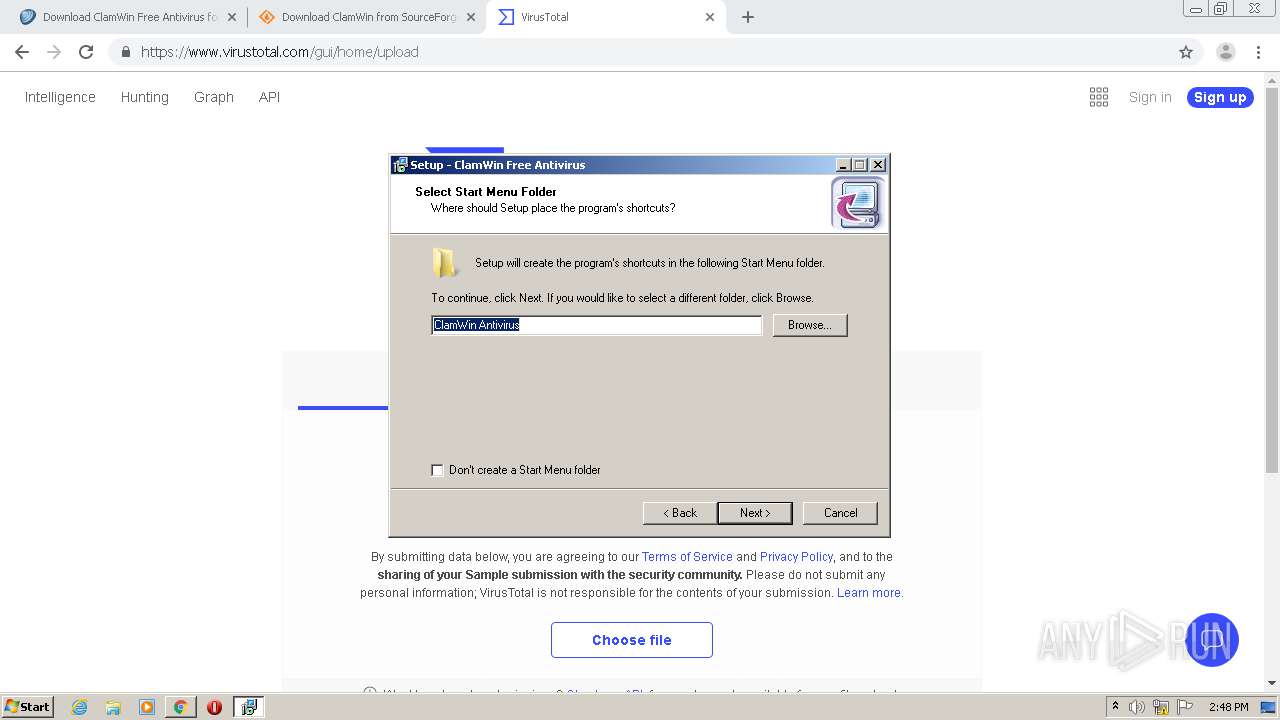
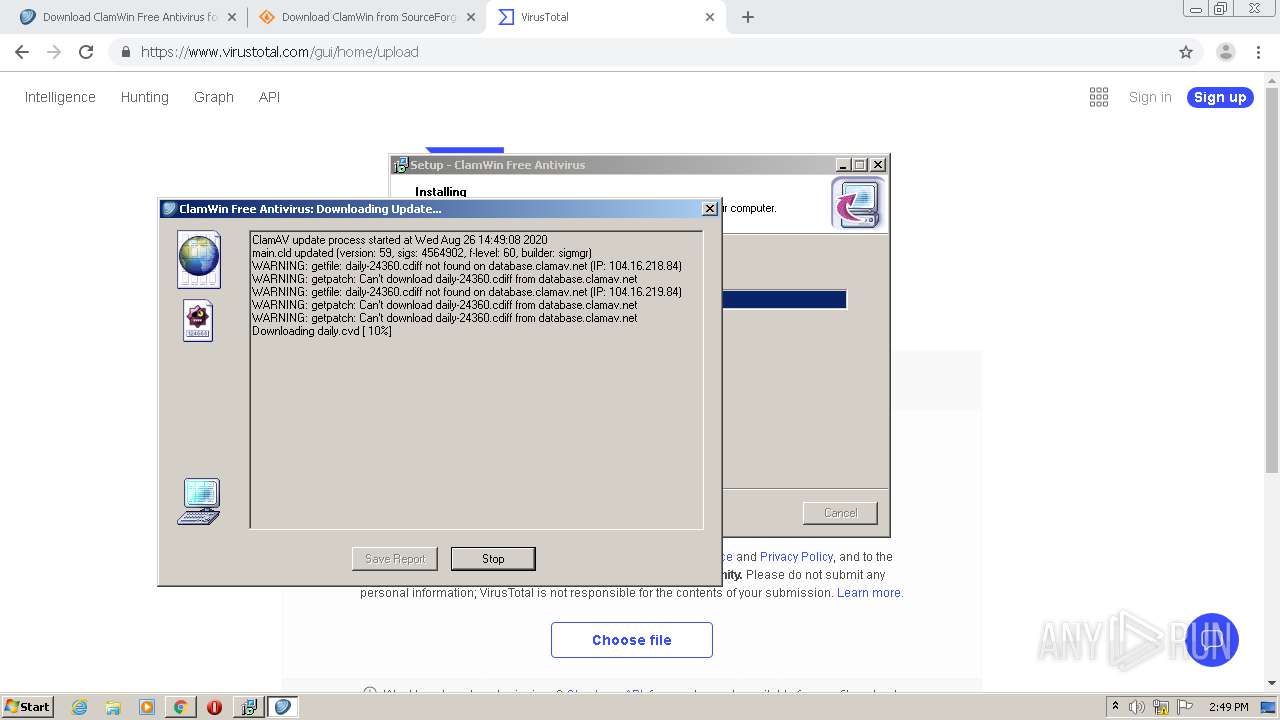
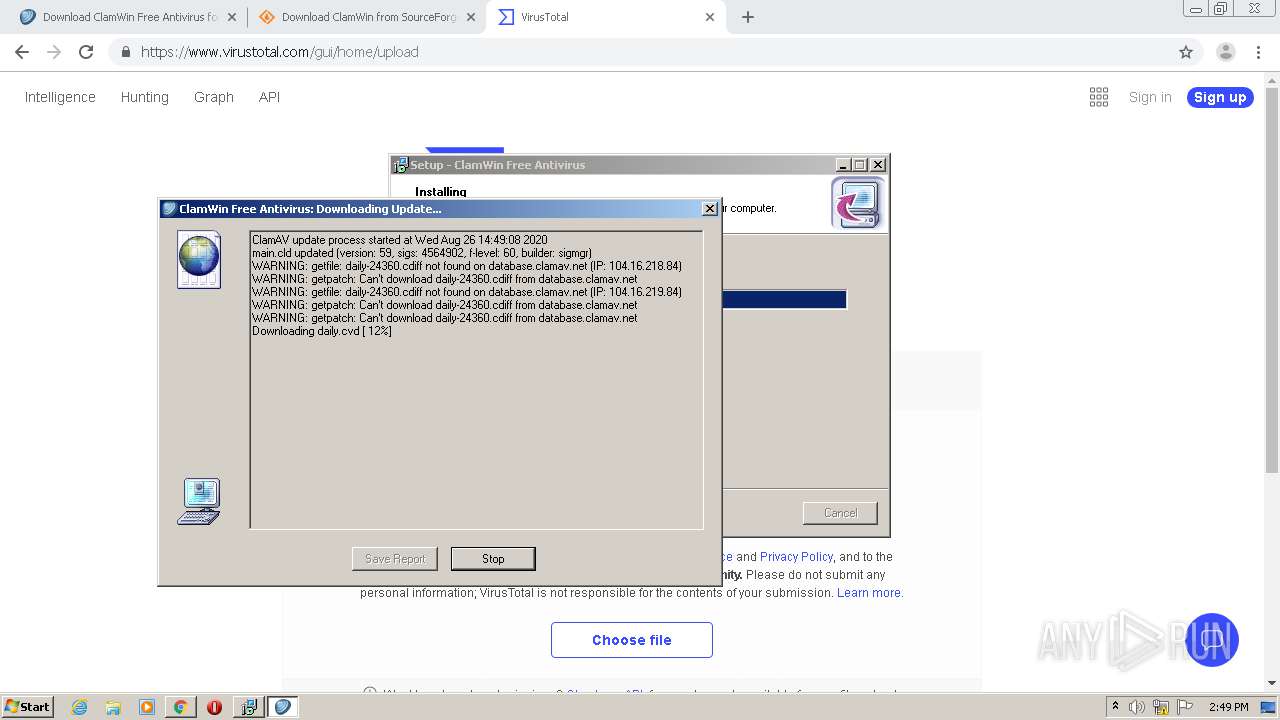
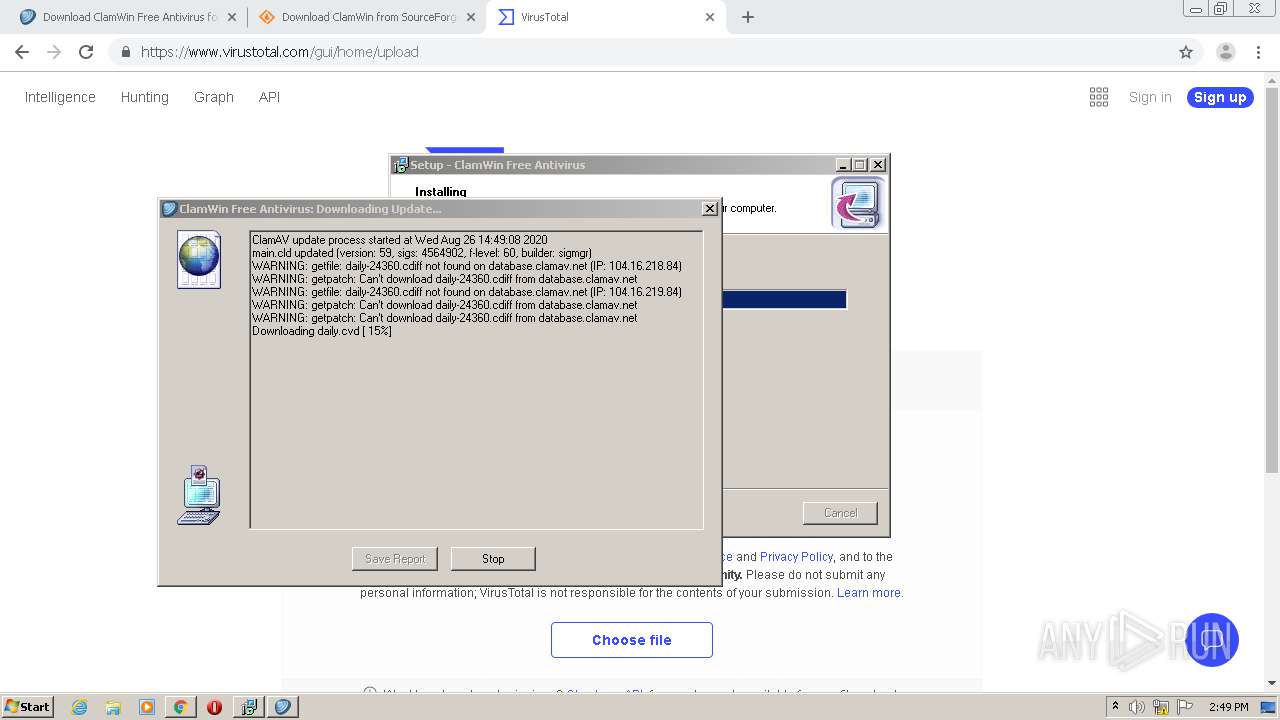
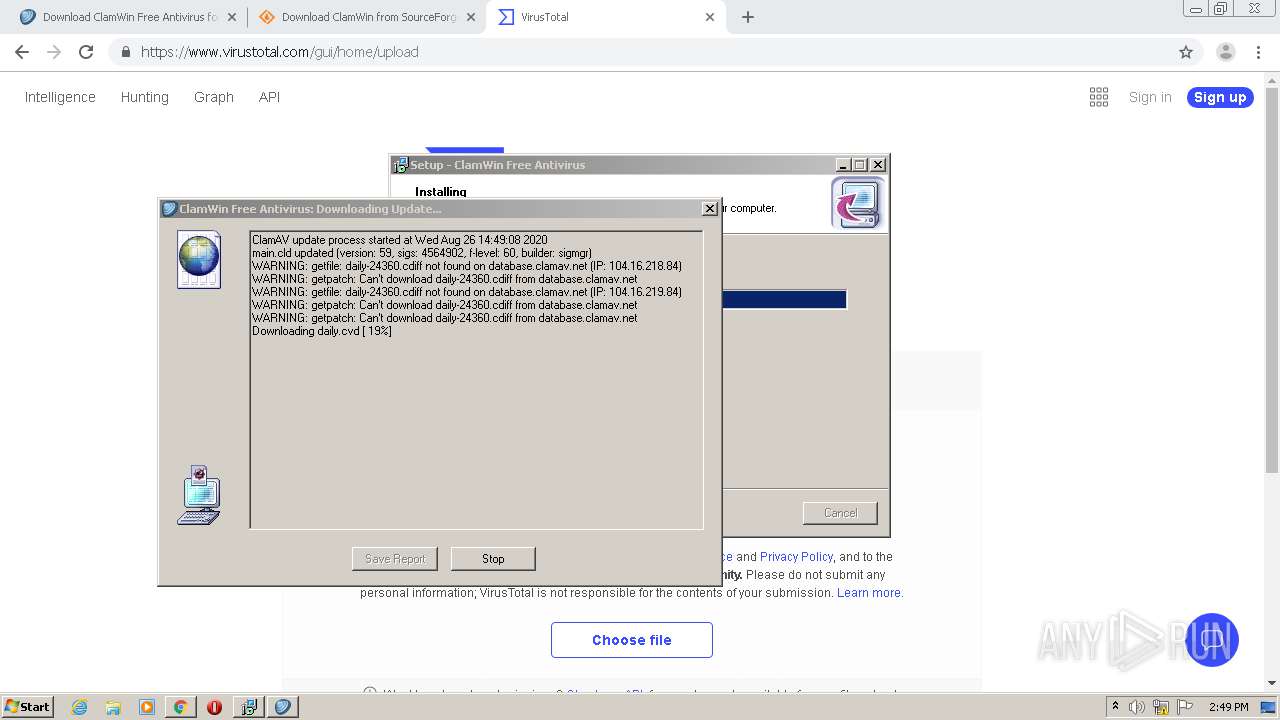
Application was dropped or rewritten from another process
- clamwin-0.99.4-setup.exe (PID: 1932)
- clamwin-0.99.4-setup.exe (PID: 2868)
- ClamWin.exe (PID: 1572)
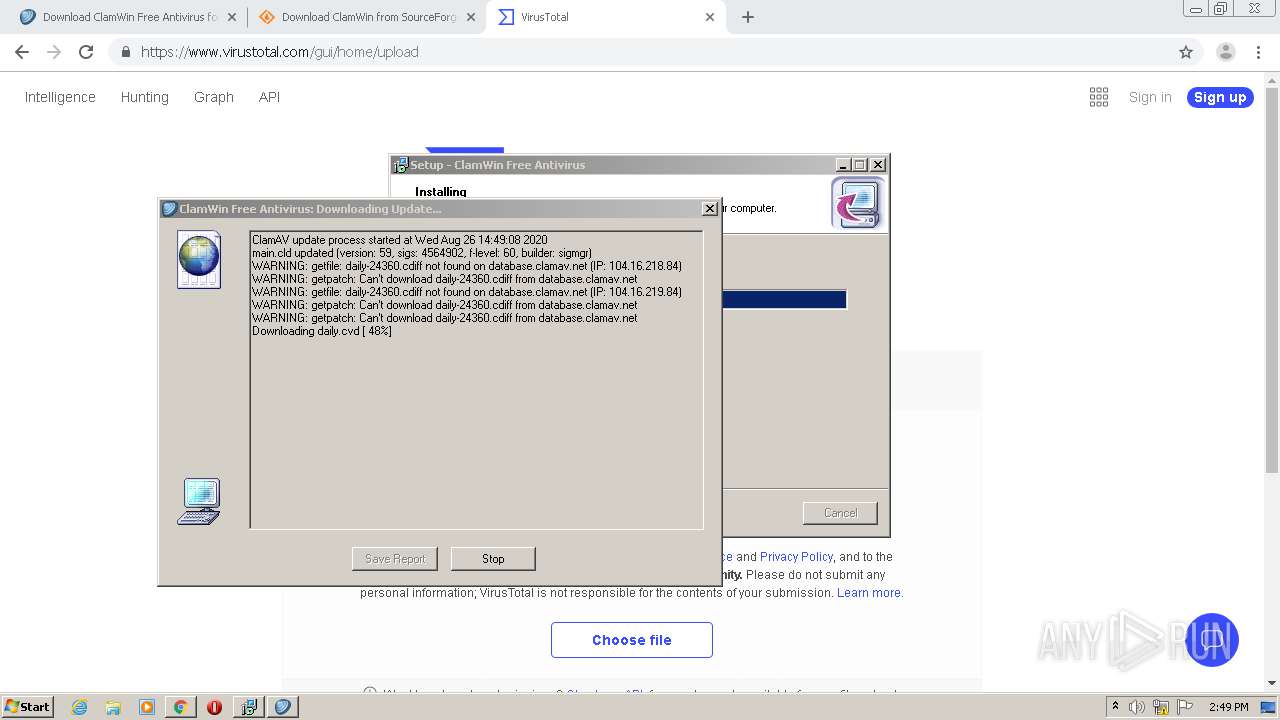
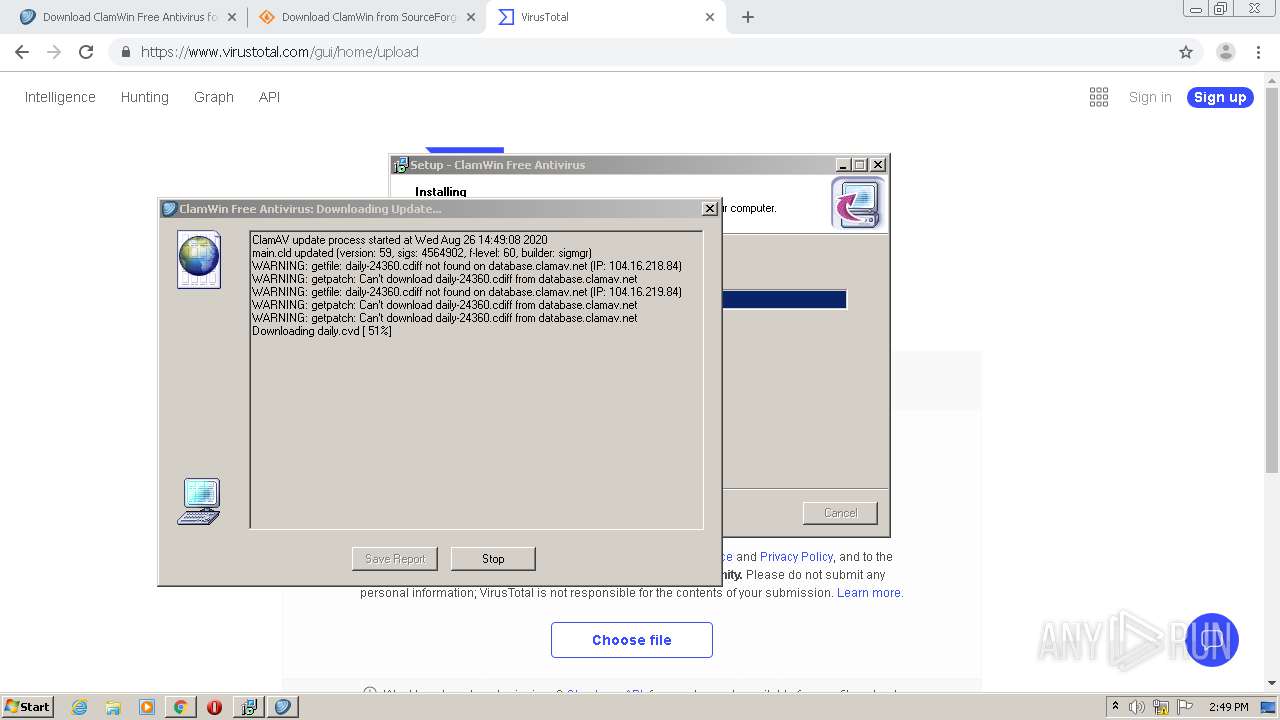
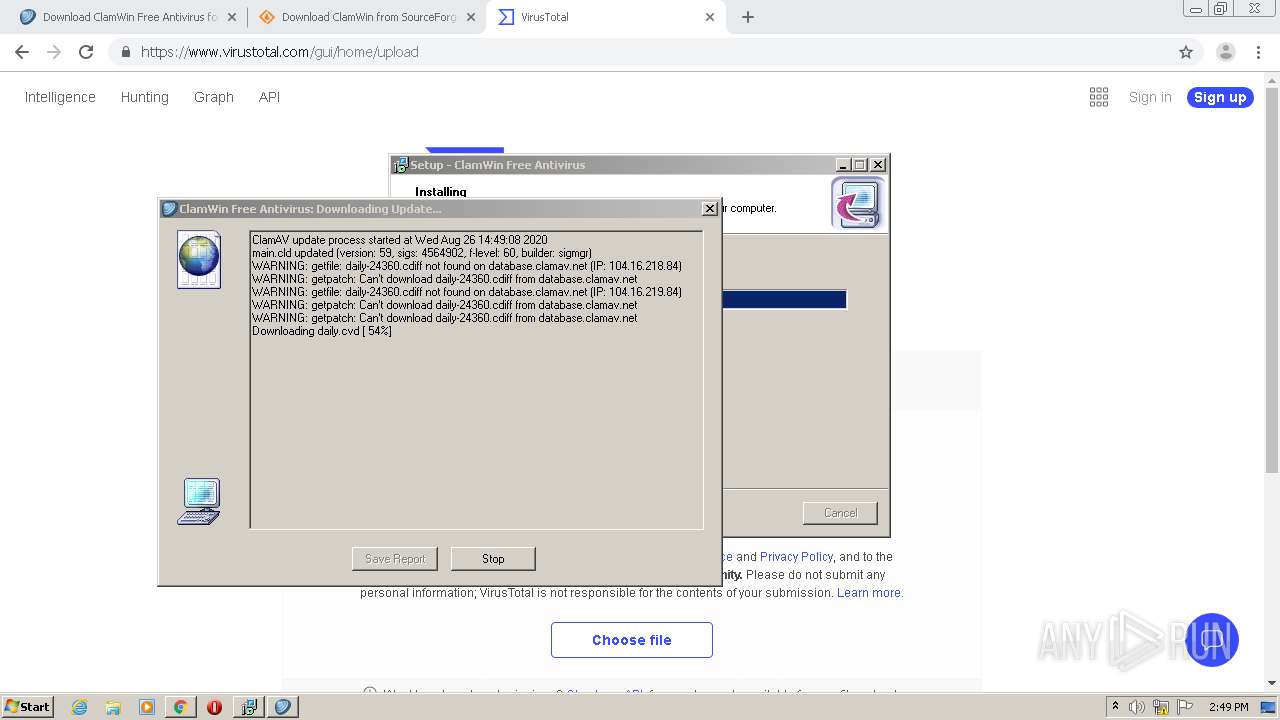
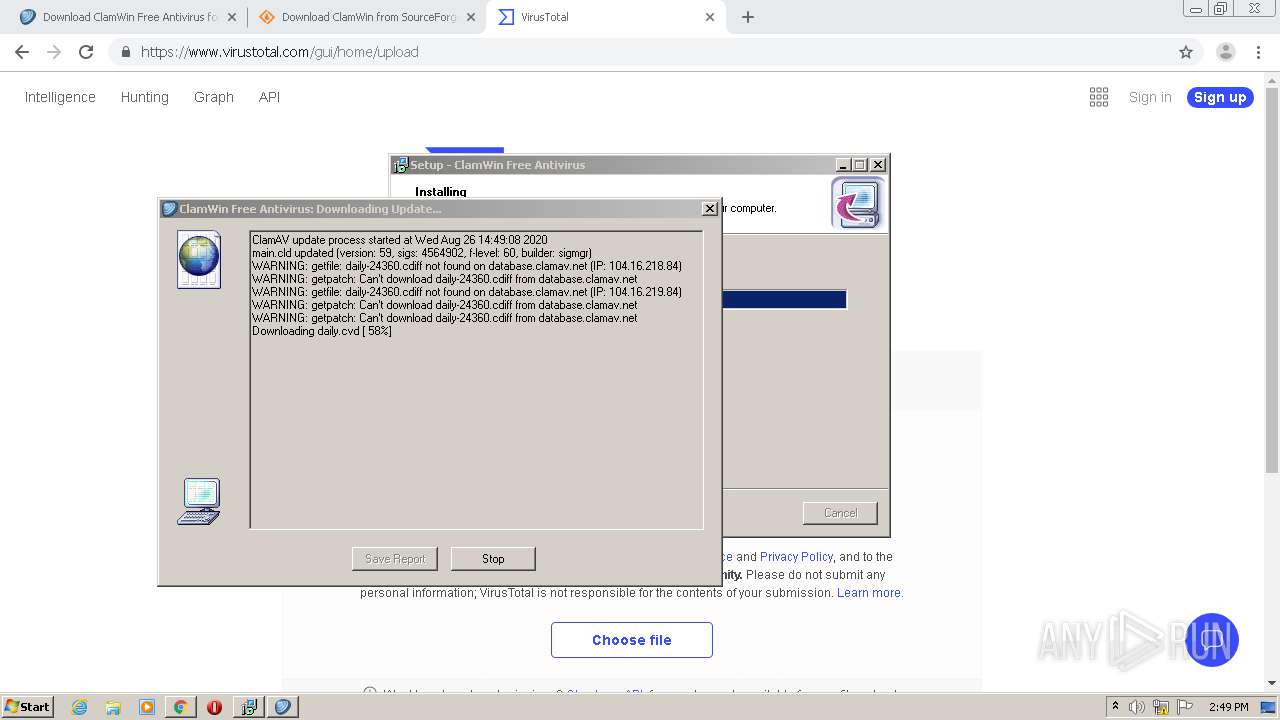
- freshclam.exe (PID: 3500)
Changes the autorun value in the registry
- is-C6ELO.tmp (PID: 1120)
Loads dropped or rewritten executable
- ClamWin.exe (PID: 1572)
- freshclam.exe (PID: 3500)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2284)
- is-C6ELO.tmp (PID: 1120)
- clamwin-0.99.4-setup.exe (PID: 2868)
Creates COM task schedule object
- is-C6ELO.tmp (PID: 1120)
Loads Python modules
- ClamWin.exe (PID: 1572)
Creates files in the user directory
- ClamWin.exe (PID: 1572)
Creates files in the program directory
- freshclam.exe (PID: 3500)
INFO
Application launched itself
- chrome.exe (PID: 2284)
Reads the hosts file
- chrome.exe (PID: 2284)
- chrome.exe (PID: 2748)
Reads settings of System Certificates
- chrome.exe (PID: 2748)
Reads Internet Cache Settings
- chrome.exe (PID: 2284)
Application was dropped or rewritten from another process
- is-C6ELO.tmp (PID: 1120)
Creates a software uninstall entry
- is-C6ELO.tmp (PID: 1120)
Creates files in the program directory
- is-C6ELO.tmp (PID: 1120)
Loads dropped or rewritten executable
- is-C6ELO.tmp (PID: 1120)
Dropped object may contain Bitcoin addresses
- is-C6ELO.tmp (PID: 1120)
- freshclam.exe (PID: 3500)
Dropped object may contain TOR URL's
- freshclam.exe (PID: 3500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
74
Monitored processes
29
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=996,13740272638243324401,1032148062369920167,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6221462815127756548 --mojo-platform-channel-handle=2980 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,13740272638243324401,1032148062369920167,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8196741891216924456 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3724 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
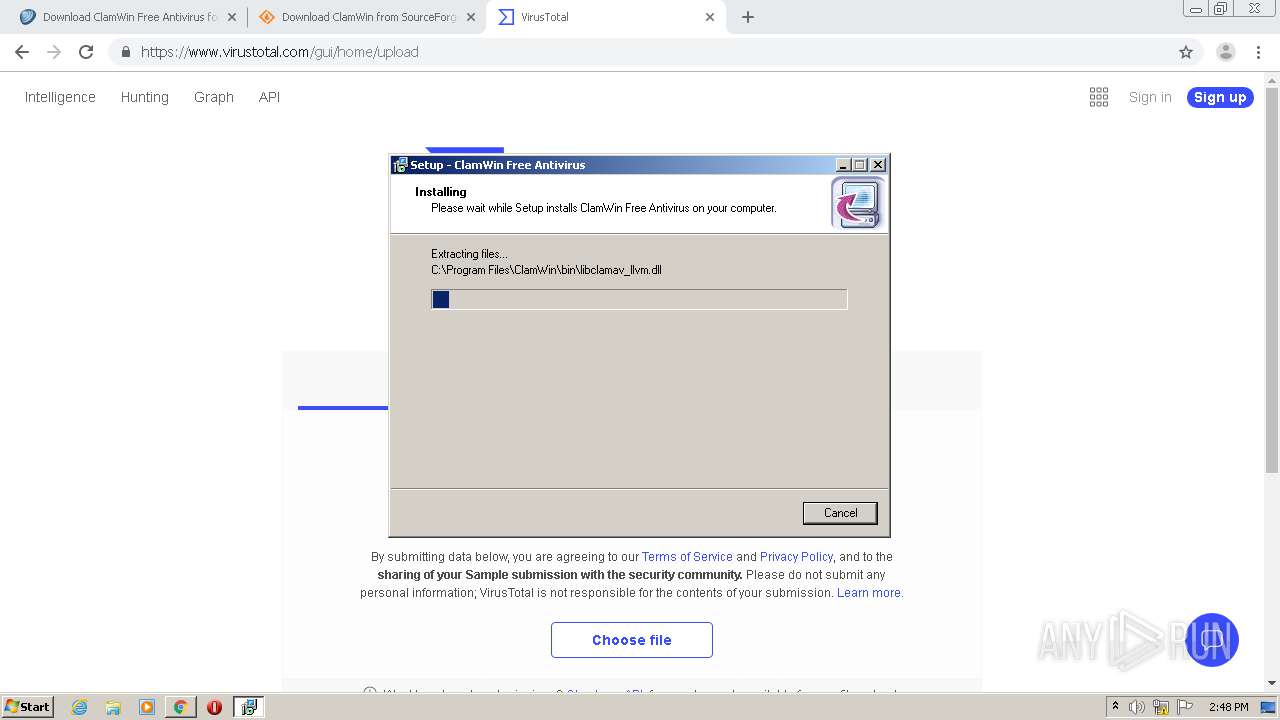
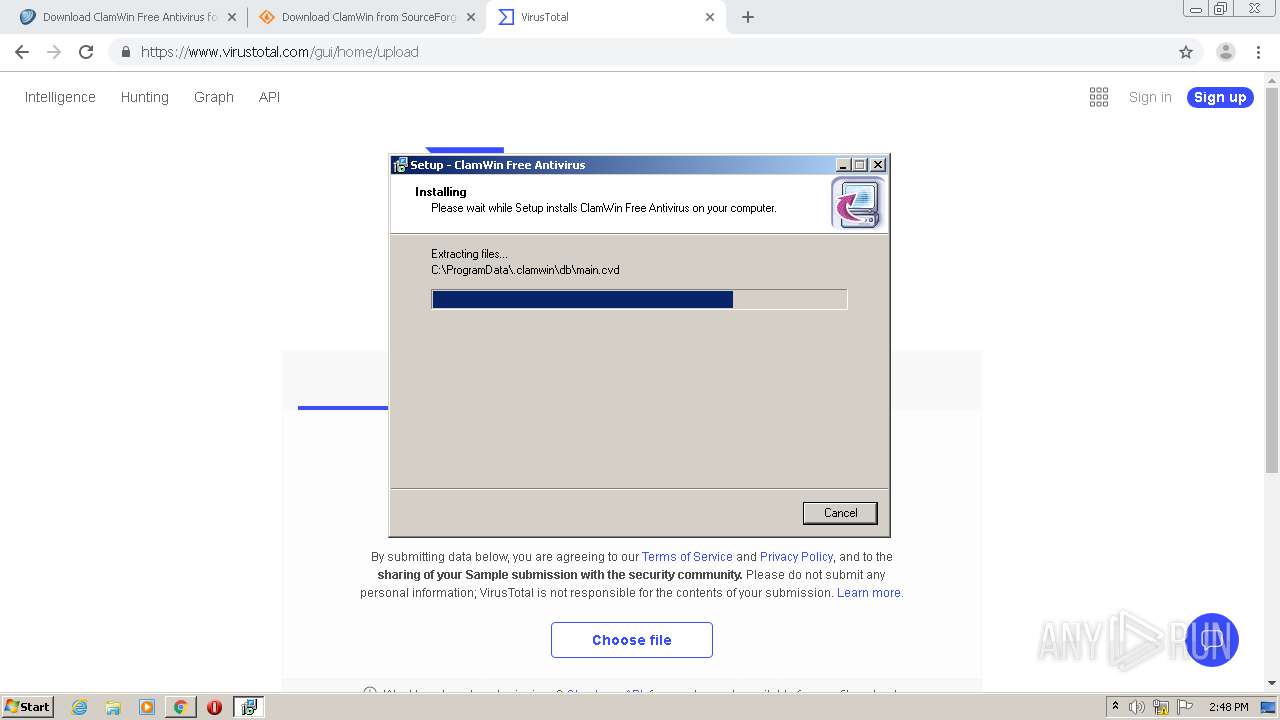
| 1120 | "C:\Users\admin\AppData\Local\Temp\is-13IMC.tmp\is-C6ELO.tmp" /SL4 $C0122 "C:\Users\admin\Downloads\clamwin-0.99.4-setup.exe" 172395663 52736 | C:\Users\admin\AppData\Local\Temp\is-13IMC.tmp\is-C6ELO.tmp | clamwin-0.99.4-setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.47.0.0 Modules
| |||||||||||||||
| 1564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=996,13740272638243324401,1032148062369920167,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=5747154143217692082 --mojo-platform-channel-handle=3436 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
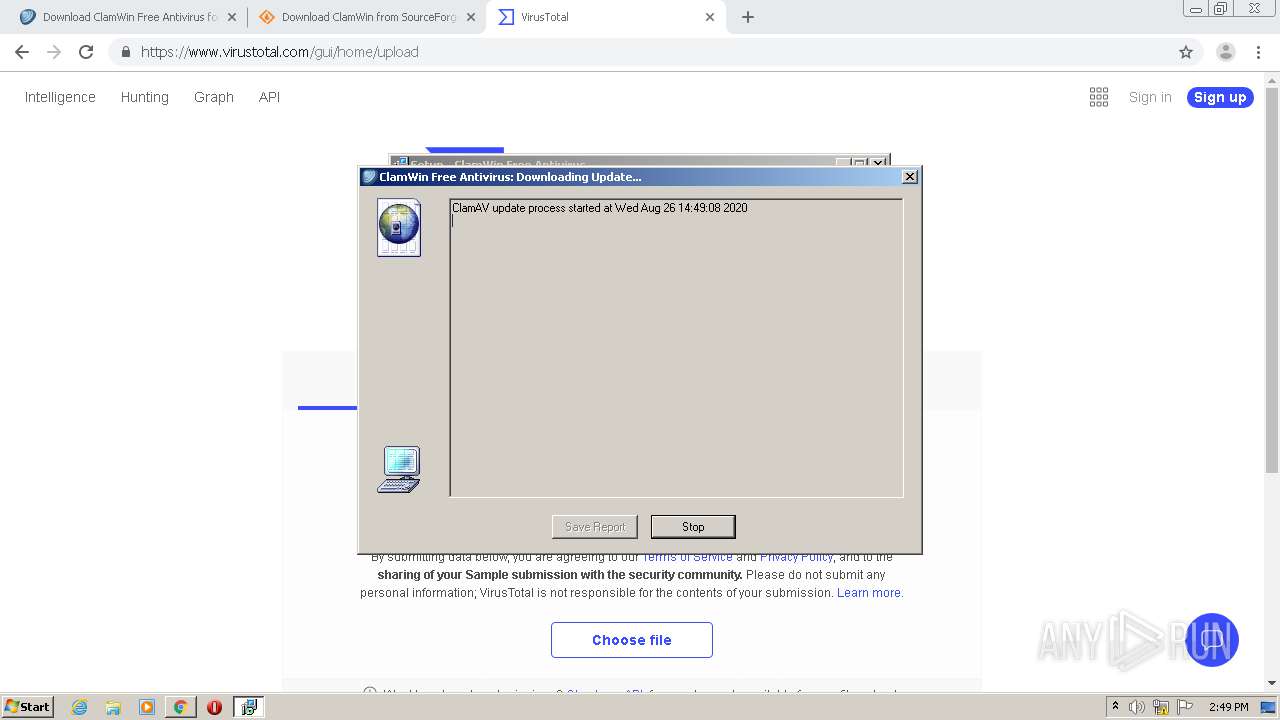
| 1572 | "C:\Program Files\ClamWin\bin\ClamWin.exe" --mode=update --close | C:\Program Files\ClamWin\bin\ClamWin.exe | — | is-C6ELO.tmp | |||||||||||
User: admin Company: alch Integrity Level: HIGH Description: ClamWin Antivirus Exit code: 0 Version: 0.99.4.0 Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,13740272638243324401,1032148062369920167,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9798612552681130707 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3280 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
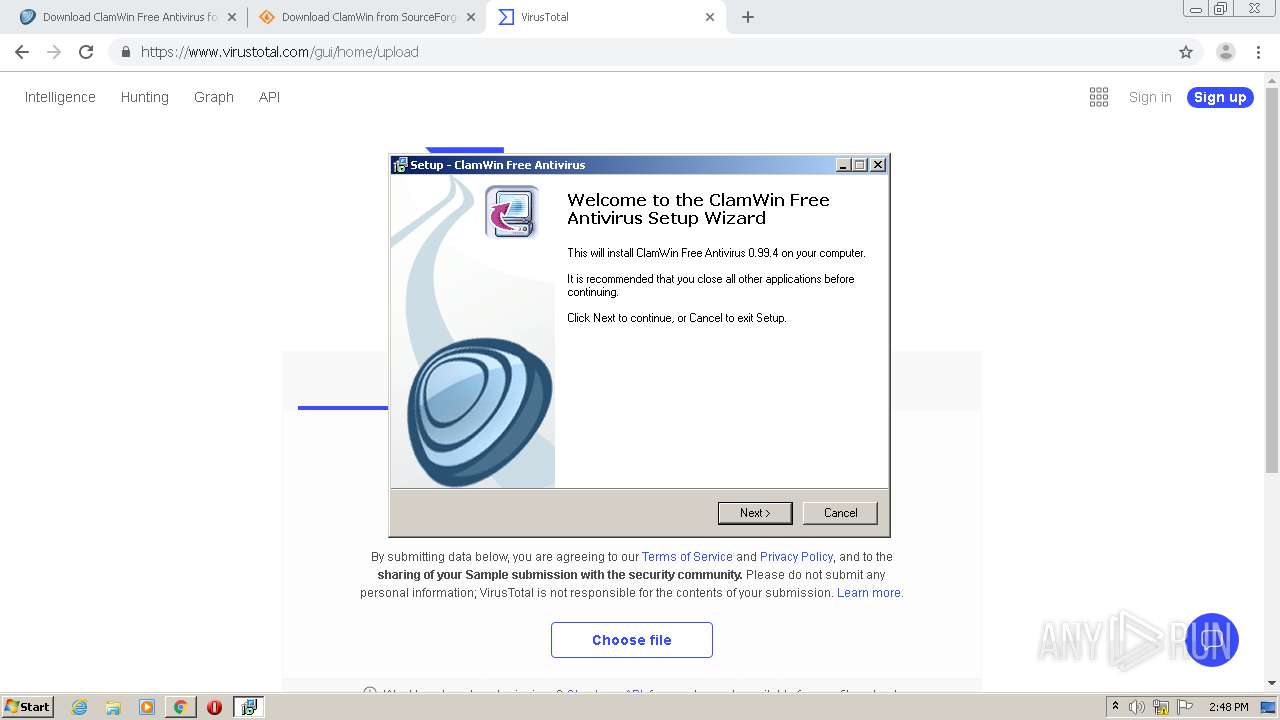
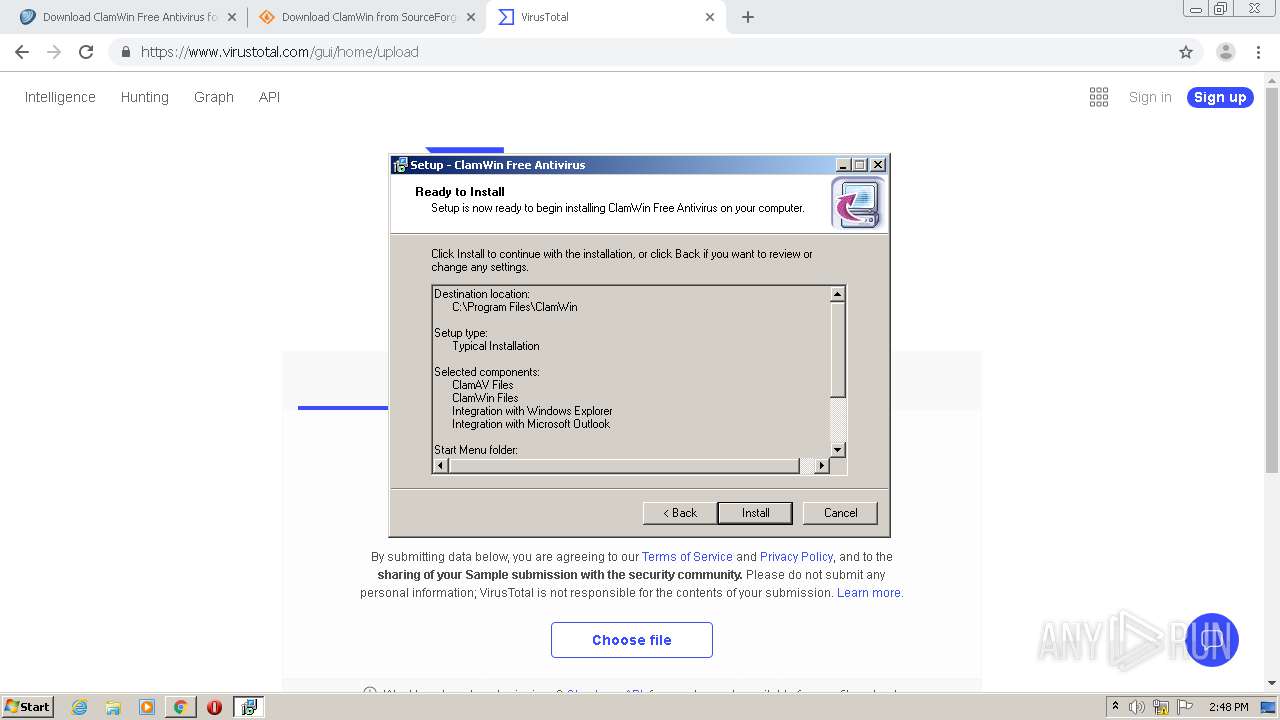
| 1932 | "C:\Users\admin\Downloads\clamwin-0.99.4-setup.exe" | C:\Users\admin\Downloads\clamwin-0.99.4-setup.exe | — | chrome.exe | |||||||||||
User: admin Company: alch Integrity Level: MEDIUM Description: ClamWin Free Antivirus Setup Exit code: 3221226540 Version: Modules
| |||||||||||||||
| 2196 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,13740272638243324401,1032148062369920167,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6404508949639530196 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3728 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
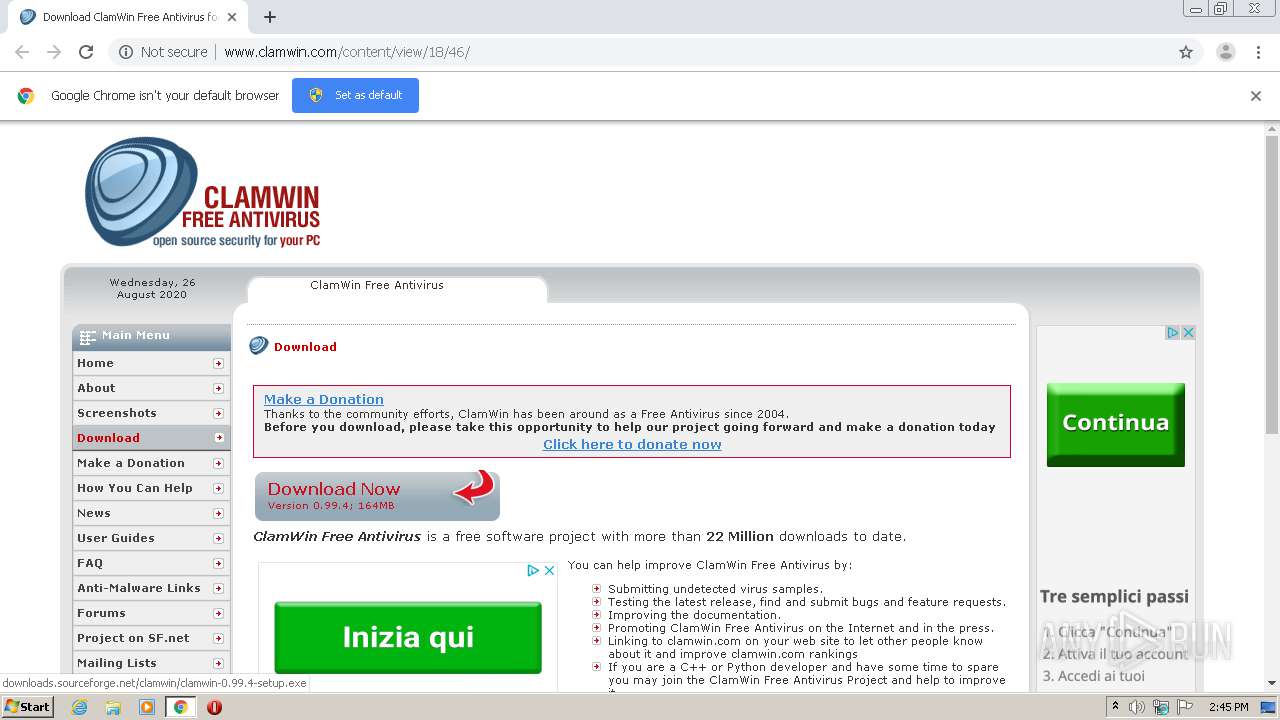
| 2284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "http://www.clamwin.com/content/view/18/46/" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,13740272638243324401,1032148062369920167,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=164961004609822121 --renderer-client-id=18 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=948 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 503
Read events
1 366
Write events
133
Delete events
4
Modification events
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2988) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2284-13242923121662250 |
Value: 259 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2832-13239195546717773 |
Value: 0 | |||
| (PID) Process: | (2284) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
55
Suspicious files
132
Text files
150
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\67ff5461-18eb-4abe-8cff-c2e4a5a02d4f.tmp | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFe31aa.TMP | text | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFe31ba.TMP | text | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFe33ae.TMP | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFe31aa.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
145
DNS requests
78
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/templates/ClamWin/sflogo.html | US | html | 219 b | unknown |
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/content/view/18/46/ | US | xml | 12.0 Kb | unknown |
2748 | chrome.exe | GET | 200 | 172.217.23.98:80 | http://pagead2.googlesyndication.com/pagead/show_ads.js | US | text | 32.0 Kb | whitelisted |
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/templates/ClamWin/images/mainbody_r_border.gif | US | image | 49 b | unknown |
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/templates/ClamWin/images/mainbody_b_border.gif | US | image | 288 b | unknown |
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/templates/ClamWin/images/corner3_n.gif | US | image | 761 b | unknown |
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/templates/ClamWin/images/mainbody_rb_corner_12.gif | US | image | 1021 b | unknown |
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/templates/ClamWin/images/dot.gif | US | image | 43 b | unknown |
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/templates/ClamWin/images/clamwin_logo.png | US | image | 7.71 Kb | unknown |
2748 | chrome.exe | GET | 200 | 51.141.164.70:80 | http://www.clamwin.com/templates/ClamWin/css/template_css.css | US | text | 6.59 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2748 | chrome.exe | 172.217.16.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2748 | chrome.exe | 172.217.18.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
2748 | chrome.exe | 51.141.164.70:80 | www.clamwin.com | Microsoft Corporation | US | unknown |
2748 | chrome.exe | 172.217.23.98:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
2748 | chrome.exe | 172.217.23.174:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
2748 | chrome.exe | 172.217.23.100:443 | www.google.com | Google Inc. | US | whitelisted |
2748 | chrome.exe | 172.217.23.98:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
2748 | chrome.exe | 216.58.207.34:443 | adservice.google.it | Google Inc. | US | whitelisted |
2748 | chrome.exe | 172.217.16.130:443 | adservice.google.com | Google Inc. | US | whitelisted |
2748 | chrome.exe | 216.58.205.238:443 | cse.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.clamwin.com |
| unknown |
accounts.google.com |
| shared |
pagead2.googlesyndication.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.google.com |
| malicious |
adservice.google.it |
| whitelisted |
adservice.google.com |
| whitelisted |
cse.google.com |
| whitelisted |
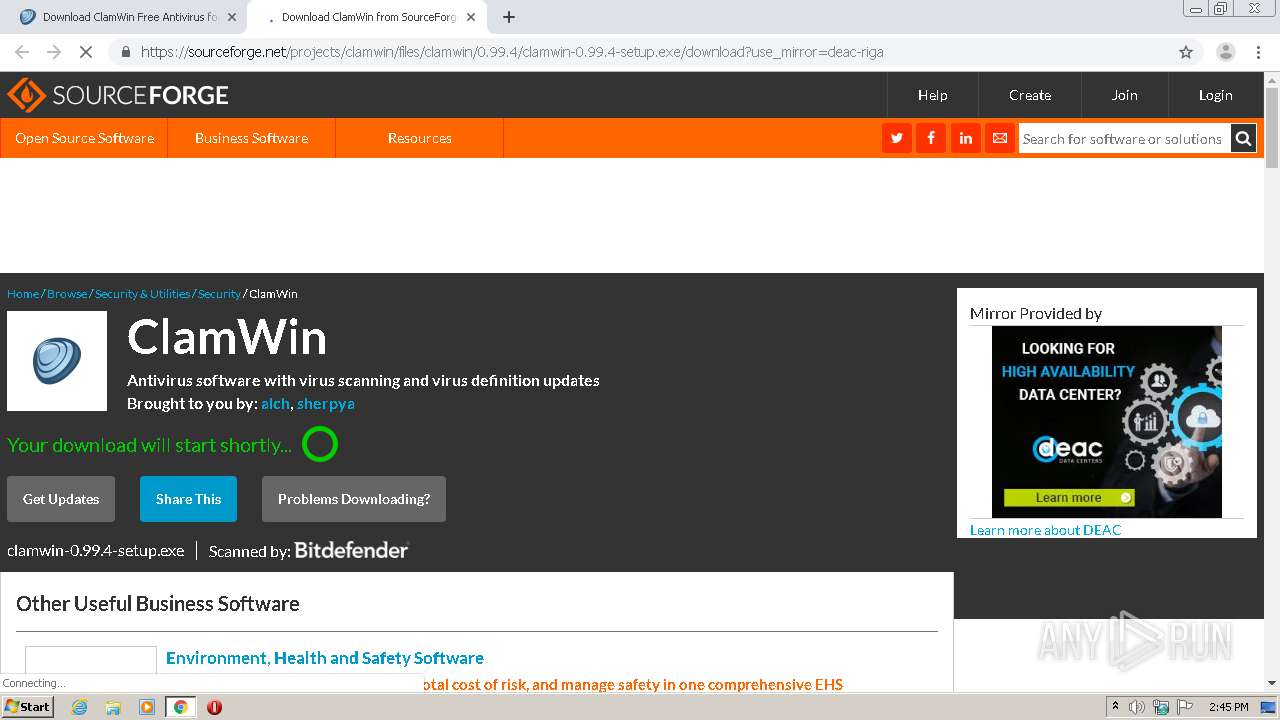
downloads.sourceforge.net |
| whitelisted |