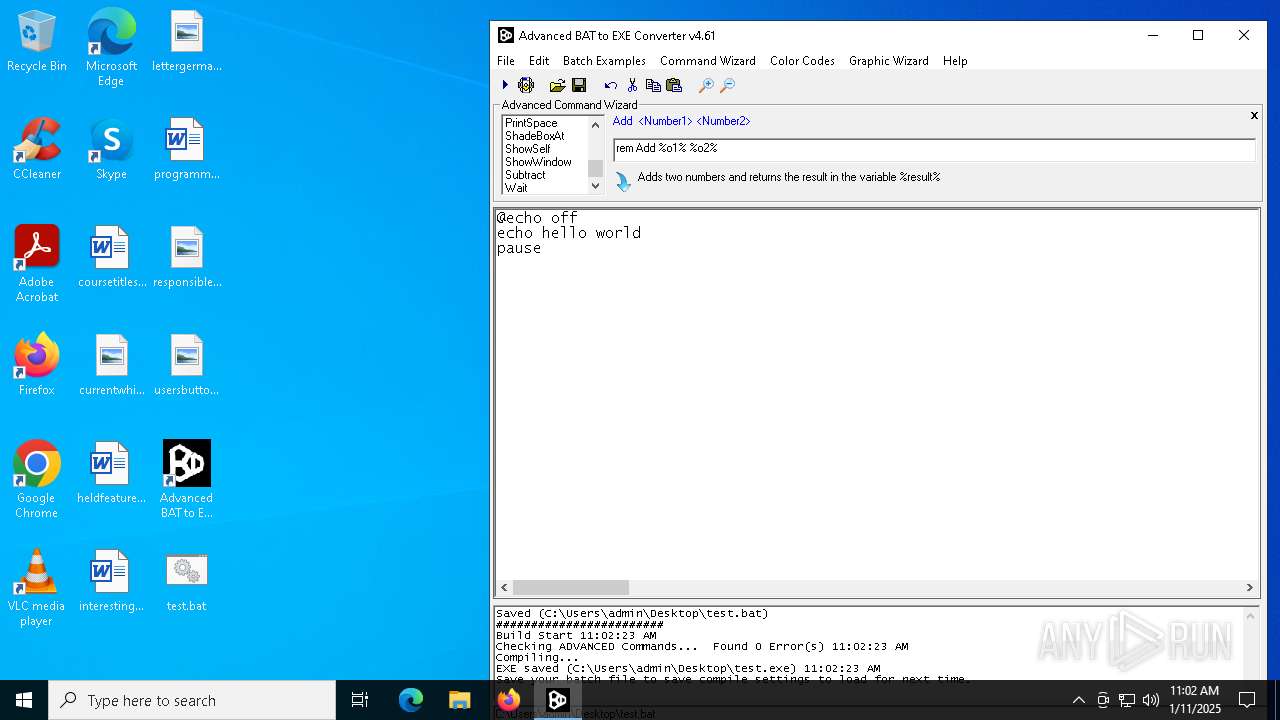
| download: | /downloads/advbattoexeconverter.exe |
| Full analysis: | https://app.any.run/tasks/49399028-cd2c-4996-89bf-3052cae6d214 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2025, 11:01:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 83BB1B476C7143552853A2CF983C1142 |
| SHA1: | 8FF8ED5C533D70A7D933EC45264DD700145ACD8C |
| SHA256: | AF09248CB756488850F9E6F9A7A00149005BF47A9B2087B792FF6BD937297FFB |
| SSDEEP: | 24576:mwEZo54ixhR4ox33t4rTdpdBXsuHqrACpGcaGGSL1EahRV3KCLPqTjqugyDPDTl4:mwEZoqixhR4U33t4r5pdBXsuHqrACpGY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- advbattoexeconverter.exe (PID: 6160)
- aB2Econv.exe (PID: 7164)
Searches for installed software
- advbattoexeconverter.exe (PID: 6160)
Creates/Modifies COM task schedule object
- advbattoexeconverter.exe (PID: 6160)
The process creates files with name similar to system file names
- advbattoexeconverter.exe (PID: 6160)
Process drops legitimate windows executable
- advbattoexeconverter.exe (PID: 6160)
Reads security settings of Internet Explorer
- aB2Econv.exe (PID: 7164)
- ShellExperienceHost.exe (PID: 5548)
Creates a software uninstall entry
- advbattoexeconverter.exe (PID: 6160)
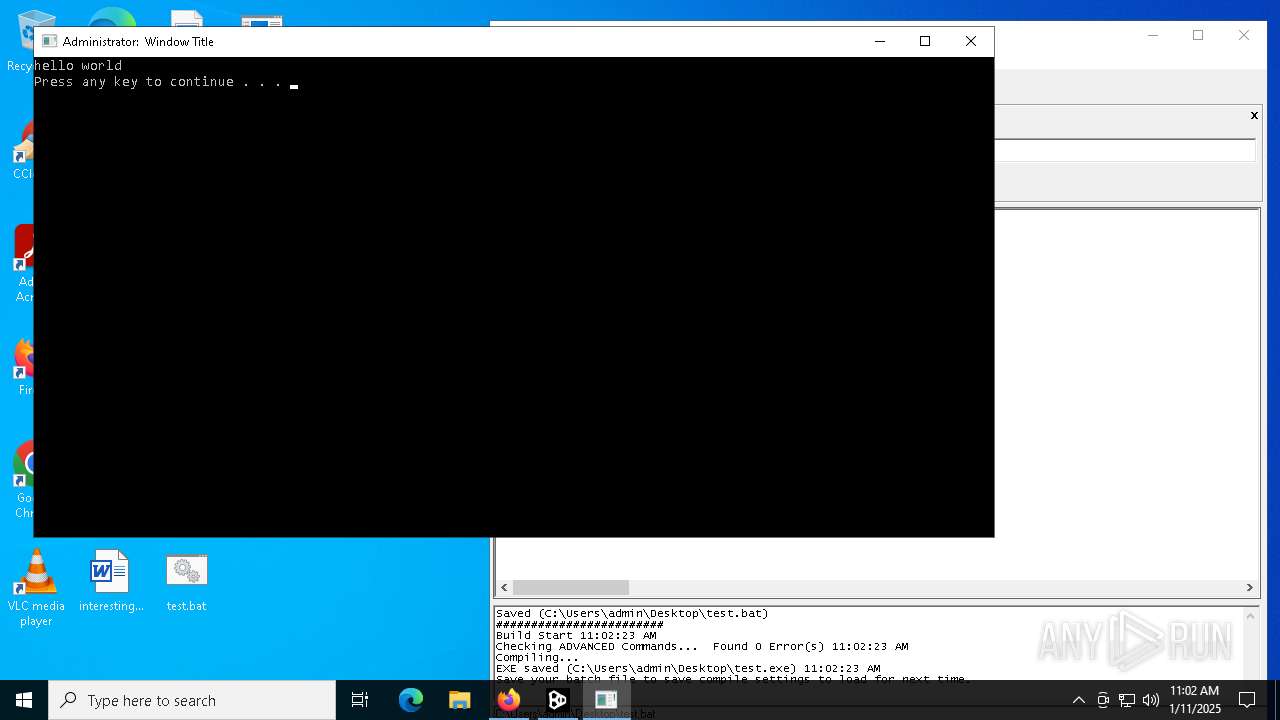
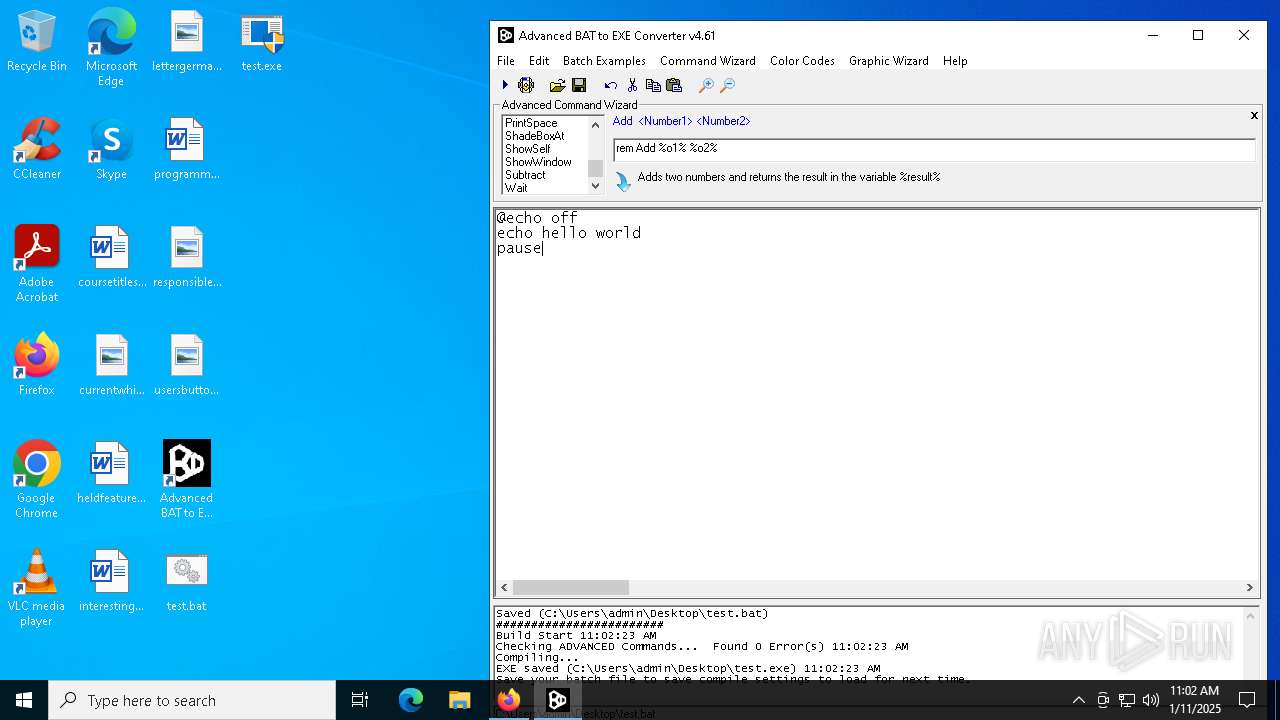
Starts CMD.EXE for commands execution
- test.exe (PID: 6968)
- cmd.exe (PID: 6268)
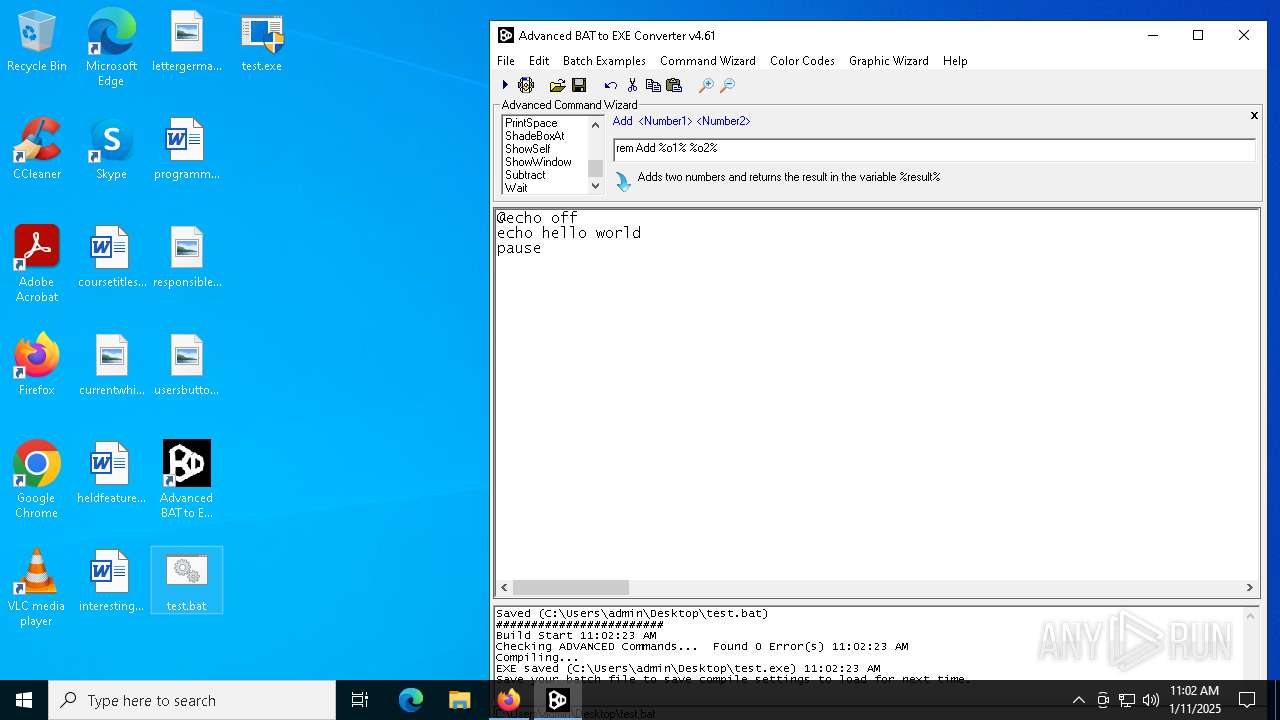
Executing commands from a ".bat" file
- test.exe (PID: 6968)
- cmd.exe (PID: 6268)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6640)
INFO
Reads the computer name
- advbattoexeconverter.exe (PID: 6160)
- aB2Econv.exe (PID: 7164)
- setupinf.exe (PID: 6820)
- ShellExperienceHost.exe (PID: 5548)
Checks supported languages
- advbattoexeconverter.exe (PID: 6160)
- setupinf.exe (PID: 6820)
- aB2Econv.exe (PID: 7164)
- test.exe (PID: 6968)
- mode.com (PID: 3840)
- ShellExperienceHost.exe (PID: 5548)
Creates files in the program directory
- advbattoexeconverter.exe (PID: 6160)
The sample compiled with english language support
- advbattoexeconverter.exe (PID: 6160)
Create files in a temporary directory
- advbattoexeconverter.exe (PID: 6160)
- aB2Econv.exe (PID: 7164)
- setupinf.exe (PID: 6820)
- test.exe (PID: 6968)
Creates files or folders in the user directory
- advbattoexeconverter.exe (PID: 6160)
Manual execution by a user
- aB2Econv.exe (PID: 7164)
- test.exe (PID: 2976)
- firefox.exe (PID: 5548)
- test.exe (PID: 6968)
Application launched itself
- firefox.exe (PID: 3820)
- firefox.exe (PID: 5548)
Starts MODE.COM to configure console settings
- mode.com (PID: 3840)
Creates a new folder
- cmd.exe (PID: 6664)
- cmd.exe (PID: 6388)
Sends debugging messages
- ShellExperienceHost.exe (PID: 5548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.3) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2006:04:05 08:55:39+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 3 |
| CodeSize: | 3584 |
| InitializedDataSize: | 94720 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1226 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
169
Monitored processes
38
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1476 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5728 -childID 6 -isForBrowser -prefsHandle 5624 -prefMapHandle 5164 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1256 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {4474e297-3b8b-47c7-9cc8-f8a166c2b442} 3820 "\\.\pipe\gecko-crash-server-pipe.3820" 2695844b850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1544 | C:\WINDOWS\system32\cmd.exe /c if exist "C:\Users\admin\AppData\Local\Temp\wtmpd\tmp65434.exe" del "C:\Users\admin\AppData\Local\Temp\wtmpd\tmp65434.exe" | C:\Windows\SysWOW64\cmd.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4852 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 5008 -prefMapHandle 5004 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ab237bb8-d10e-4a99-a5fd-04dda4475658} 3820 "\\.\pipe\gecko-crash-server-pipe.3820" 26953e12910 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2756 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4324 -childID 2 -isForBrowser -prefsHandle 4316 -prefMapHandle 4312 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1256 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b8b92ecc-dea0-492f-83ee-7f980f7fd3ba} 3820 "\\.\pipe\gecko-crash-server-pipe.3820" 26953c3aa10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2976 | "C:\Users\admin\Desktop\test.exe" | C:\Users\admin\Desktop\test.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3040 | attrib +h C:\Users\admin\AppData\Local\Temp\wtmpd | C:\Windows\SysWOW64\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3420 | C:\WINDOWS\system32\cmd.exe /c title Window Title | C:\Windows\SysWOW64\cmd.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3820 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3828 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5864 -childID 7 -isForBrowser -prefsHandle 4880 -prefMapHandle 5008 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1256 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ac074158-1d16-44be-898b-89ddfef16fac} 3820 "\\.\pipe\gecko-crash-server-pipe.3820" 2695253d150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3840 | mode con:cols=0120 lines=0030 | C:\Windows\SysWOW64\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 961
Read events
30 800
Write events
149
Delete events
12
Modification events
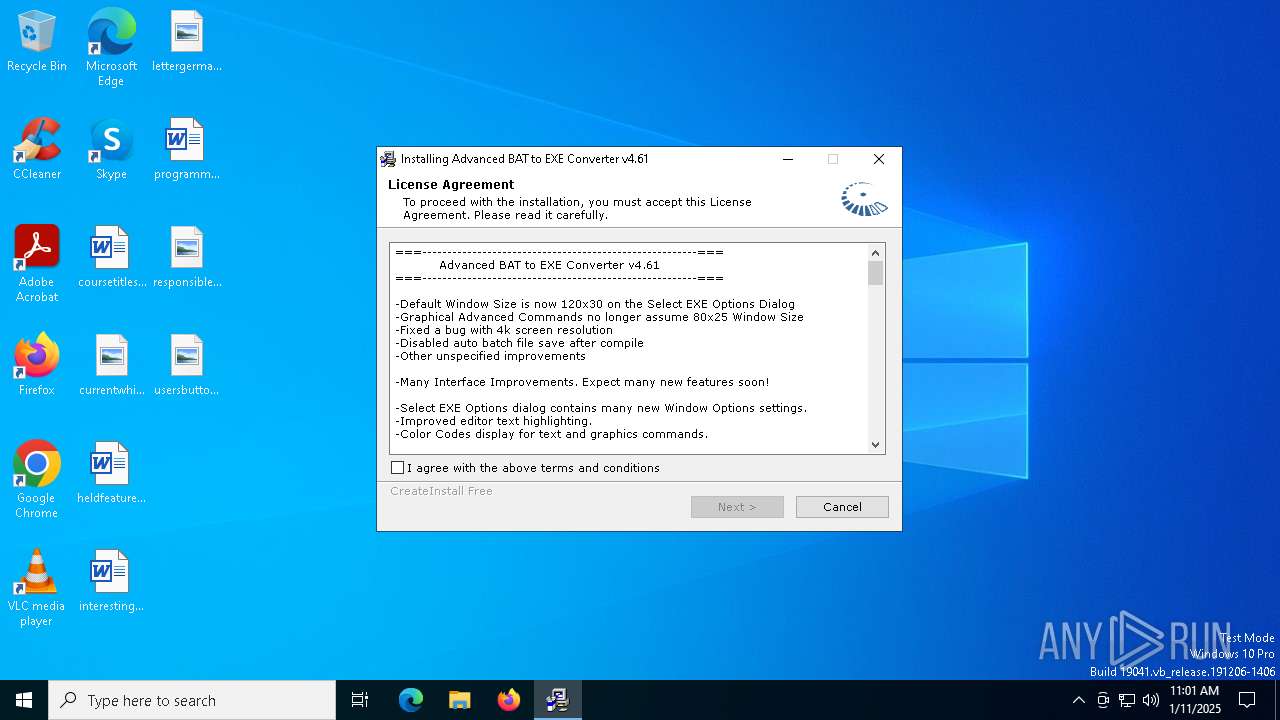
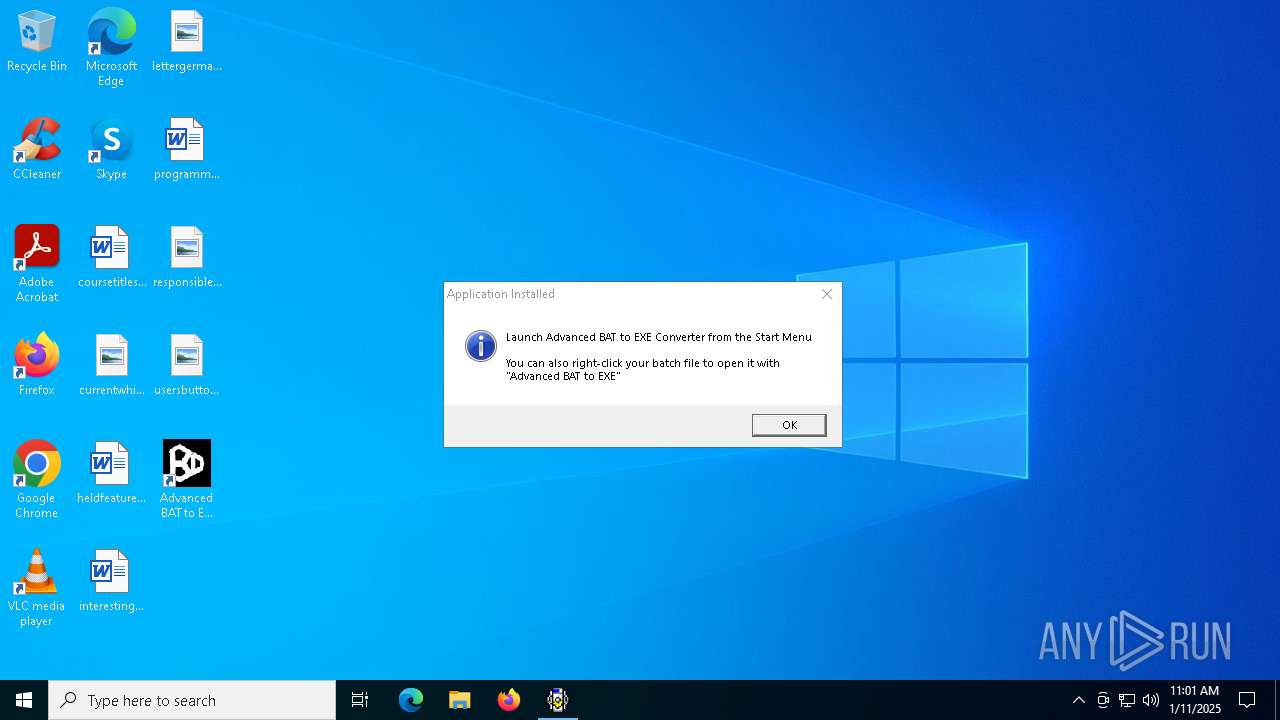
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Advanced BAT to EXE Converter v4.61 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\uninstall.exe | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Advanced BAT to EXE Converter v4.61 |
| Operation: | write | Name: | DisplayName |
Value: Advanced BAT to EXE Converter v4.61 | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Advanced BAT to EXE Converter v4.61 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\uninstall.exe | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{3B7C8860-D78F-101B-B9B5-04021C009402} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{3B7C8860-D78F-101B-B9B5-04021C009402}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{78E5A540-1850-11CF-9D53-00AA003C9CB6} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{78E5A540-1850-11CF-9D53-00AA003C9CB6}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{AFC634B0-4B8B-11CF-8989-00AA00688B10} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{AFC634B0-4B8B-11CF-8989-00AA00688B10}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (6160) advbattoexeconverter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{2334D2B1-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.2 | |||
Executable files
18
Suspicious files
204
Text files
81
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6160 | advbattoexeconverter.exe | C:\Users\admin\AppData\Local\Temp\gentee00\gentee.dll | executable | |
MD5:30439E079A3D603C461D2C2F4F8CB064 | SHA256:D6D0535175FB2302E5B5A498119823C37F6BDDFF4AB24F551AA7E038C343077A | |||
| 6160 | advbattoexeconverter.exe | C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\ab2econv461\advex12.bat | text | |
MD5:C80C479A65D8D67B2A7297E2DBC904A1 | SHA256:BE86A962F60741B76980D354C3311264004A477151B8E1C01C653B20CF1EE261 | |||
| 6160 | advbattoexeconverter.exe | C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\ab2econv461\advex13.bat | text | |
MD5:DFCEF268A64779EA33D4DE7A52DB2B0B | SHA256:E822AC686AD7B9620F11F774D657136D40447929A937694CAC6034CECBB0DF8B | |||
| 6160 | advbattoexeconverter.exe | C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\ab2econv461\advex4.bat | text | |
MD5:BCA4E6068A17C95977A6C13F834EA2DC | SHA256:075618D56331C60472C85355A53CD0E81C63761DBDB26079D8D79754E7026A3B | |||
| 6160 | advbattoexeconverter.exe | C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\ab2econv461\advex17.bat | text | |
MD5:FB1C4A19F305FB70DE38EA65C4D6159E | SHA256:CEC607F9C3E088EA72550E518C7A2FD7EE69958B9A82D4A268984FBBBFE6A00F | |||
| 6160 | advbattoexeconverter.exe | C:\Users\admin\AppData\Local\Temp\gentee00\guig.dll | executable | |
MD5:F78EE6369ADA1FB02B776498146CC903 | SHA256:F1073319D4868D38E0AE983AD42A00CDC53BE93B31275B4B55AF676976C1AA3F | |||
| 6160 | advbattoexeconverter.exe | C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\ab2econv461\advex10.bat | text | |
MD5:AA4032C2BD2BBB123112740B6EDD7EDB | SHA256:2758DE5C4570F7381DEF913123FCBCF264758B58C8A7E3B74660B74491B4A946 | |||
| 6160 | advbattoexeconverter.exe | C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\ab2econv461\advex3.bat | text | |
MD5:A4615F826E2D1621F2EEE3F2B8BC2B32 | SHA256:D4A0B446785C3E07ECAAEFB6B437E4B9FC762A43EDE531441D8E12A85F75CDBE | |||
| 6160 | advbattoexeconverter.exe | C:\Users\admin\AppData\Local\Temp\gentee00\setup_temp.gea | bs | |
MD5:3DC143330890C13033E4E3F6E0EBA0A9 | SHA256:3198B133043C225DAEE8BDDD1D77CD24D846BA53D03FBBB9245DA7DD45BC465D | |||
| 6160 | advbattoexeconverter.exe | C:\Program Files (x86)\Advanced BAT to EXE Converter v4.61\ab2econv461\advex2.bat | text | |
MD5:4CBD7C0365E171071BD9690CD2BC0EAB | SHA256:3CC6B05A85D9D7901600786364C3C7C83DCC971A05E097628E827295E454C6DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
133
DNS requests
147
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6276 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7008 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7008 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3820 | firefox.exe | POST | 200 | 184.24.77.57:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
3820 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3820 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4300 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
1176 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |