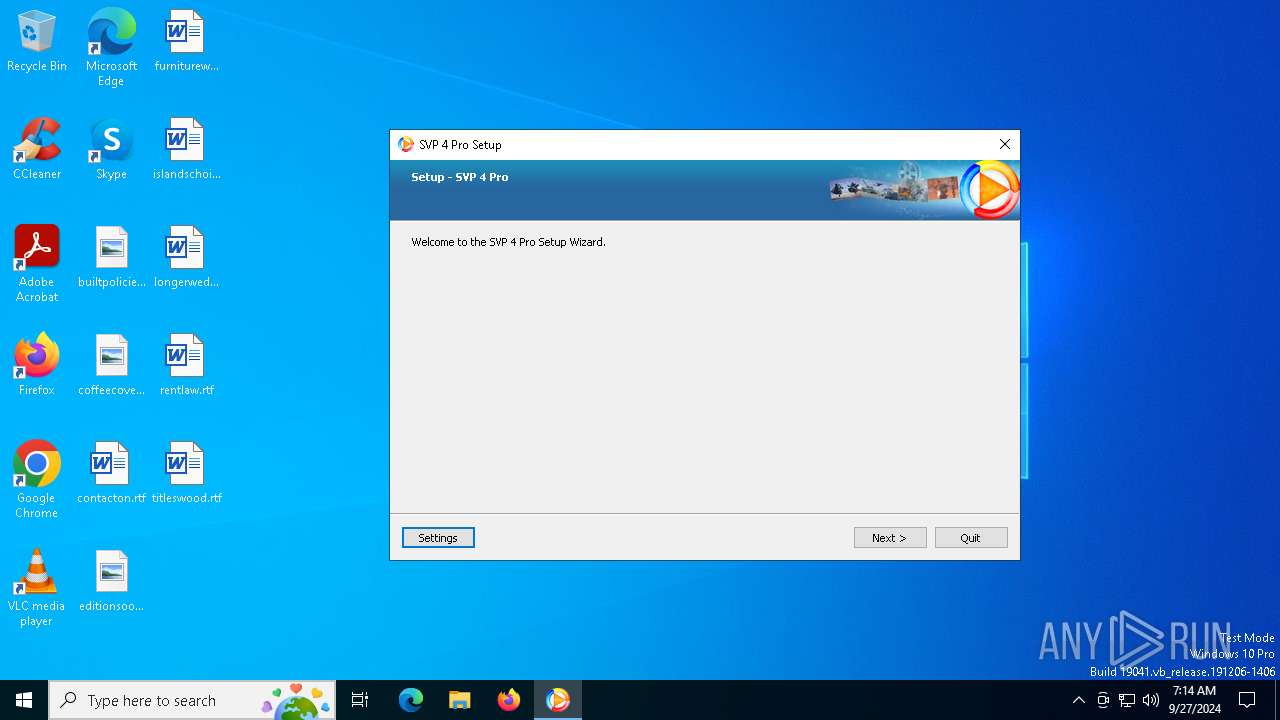
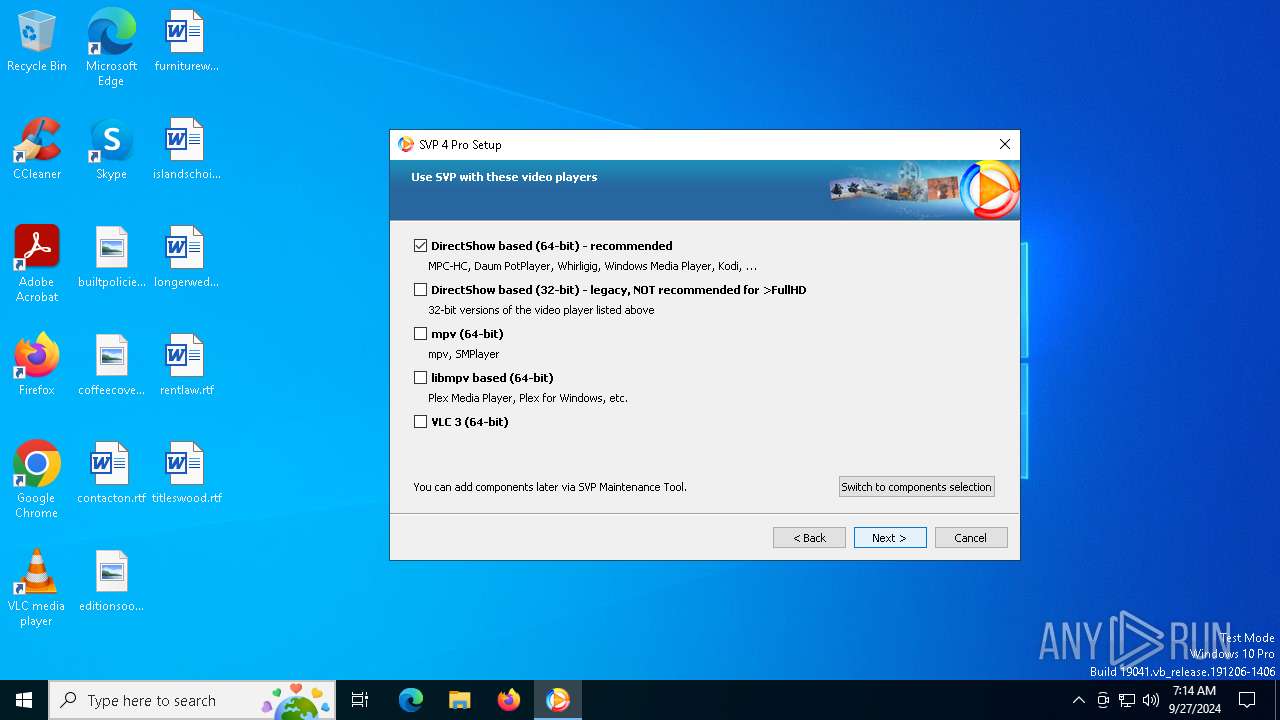
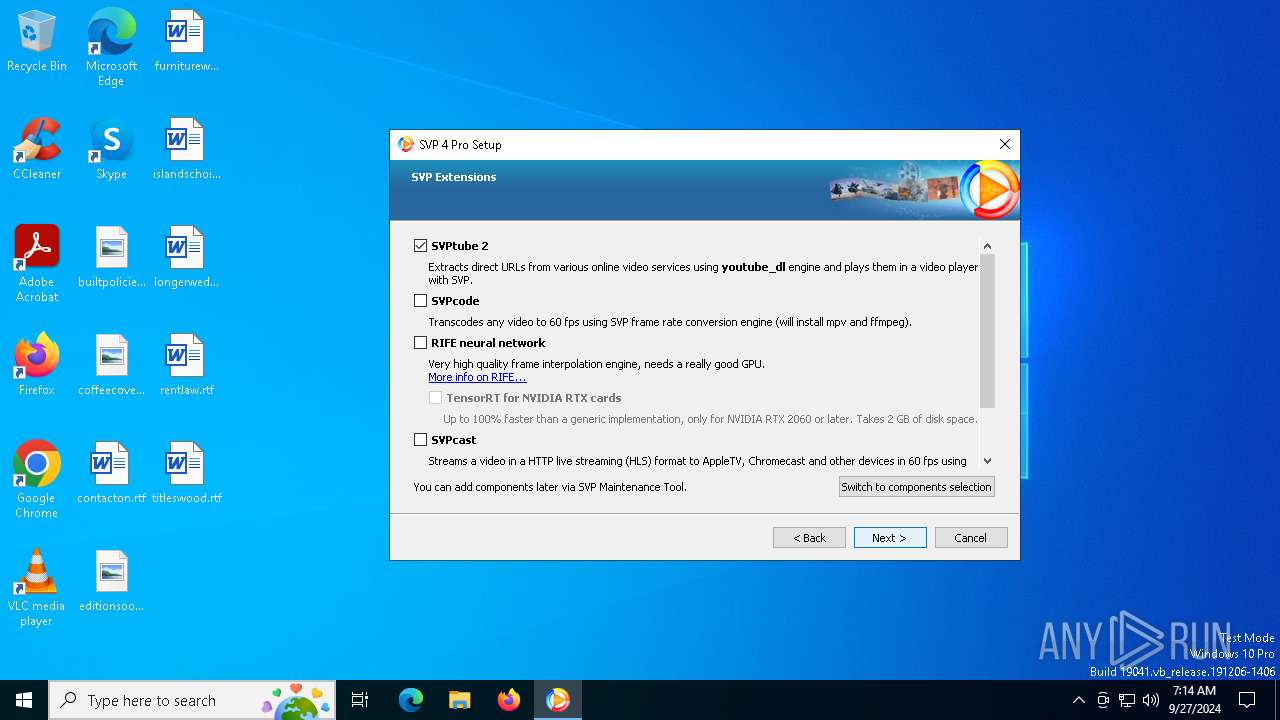
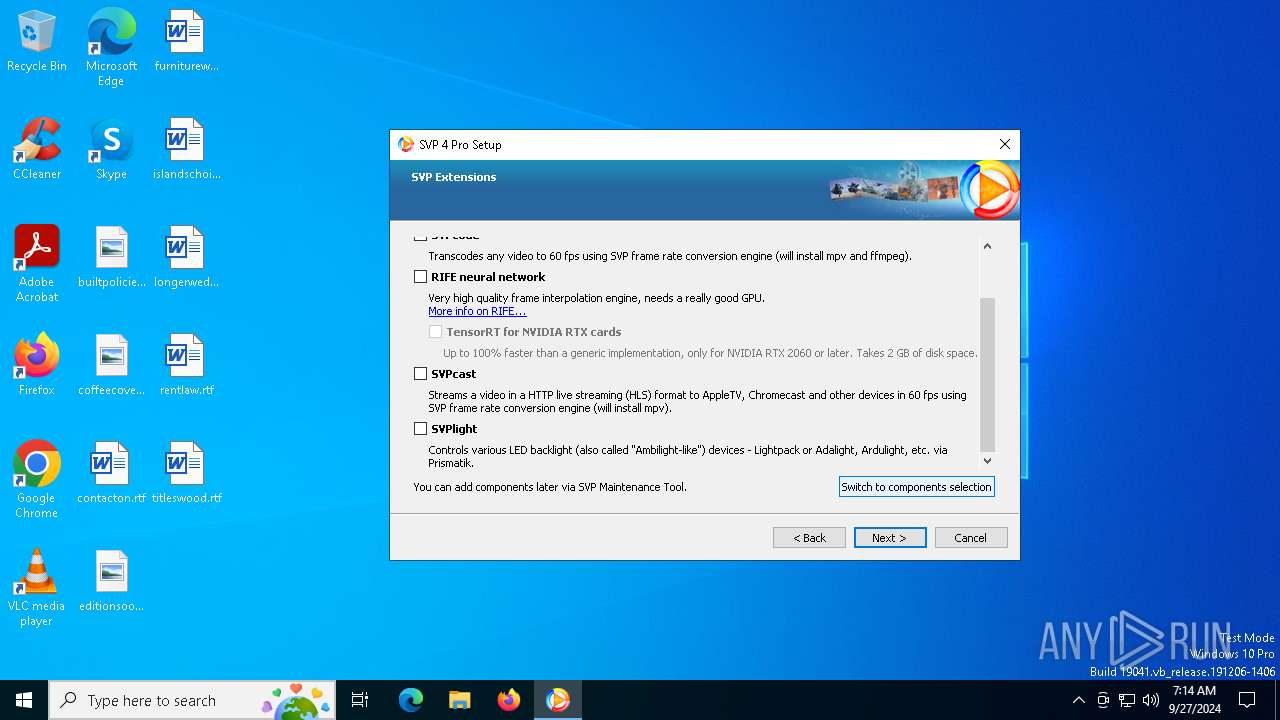
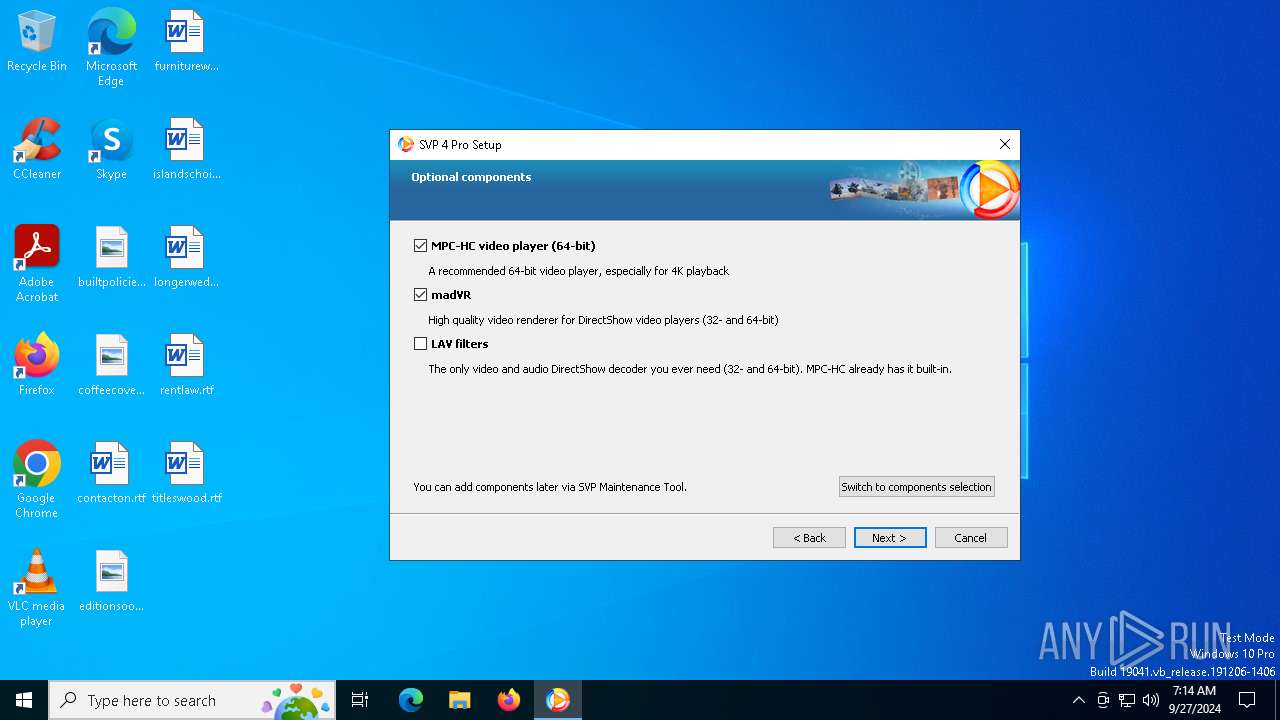
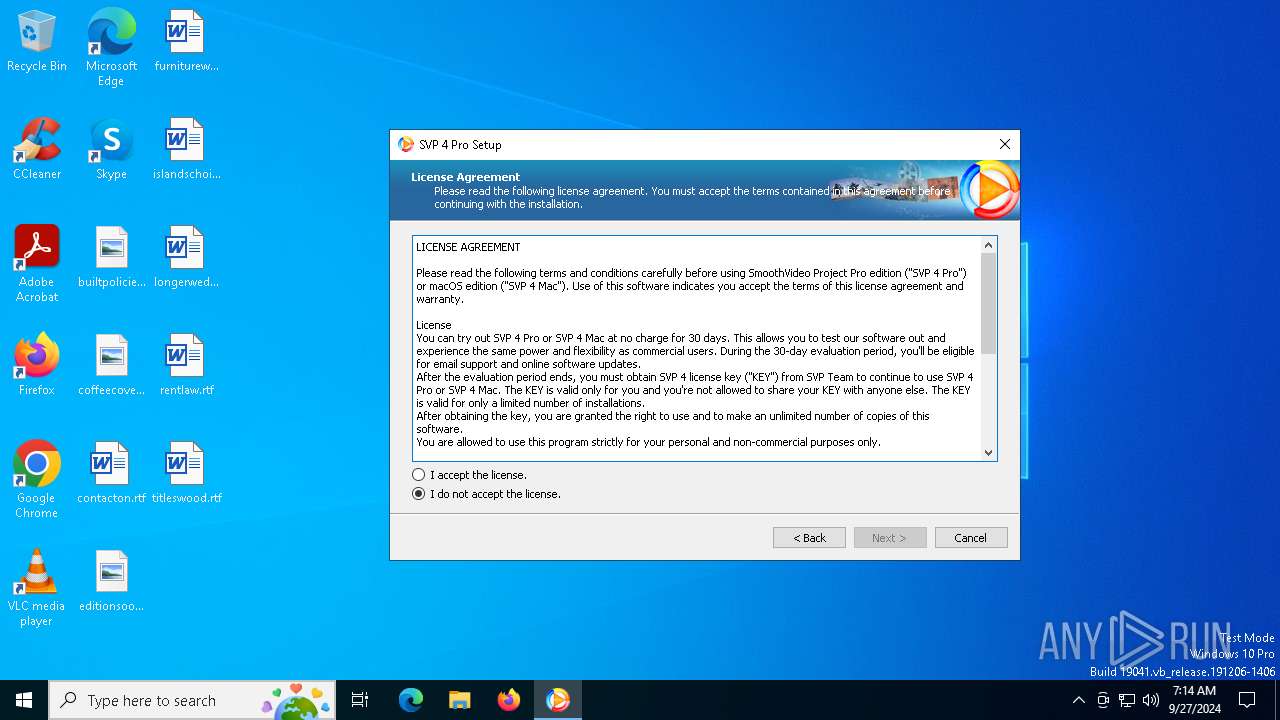
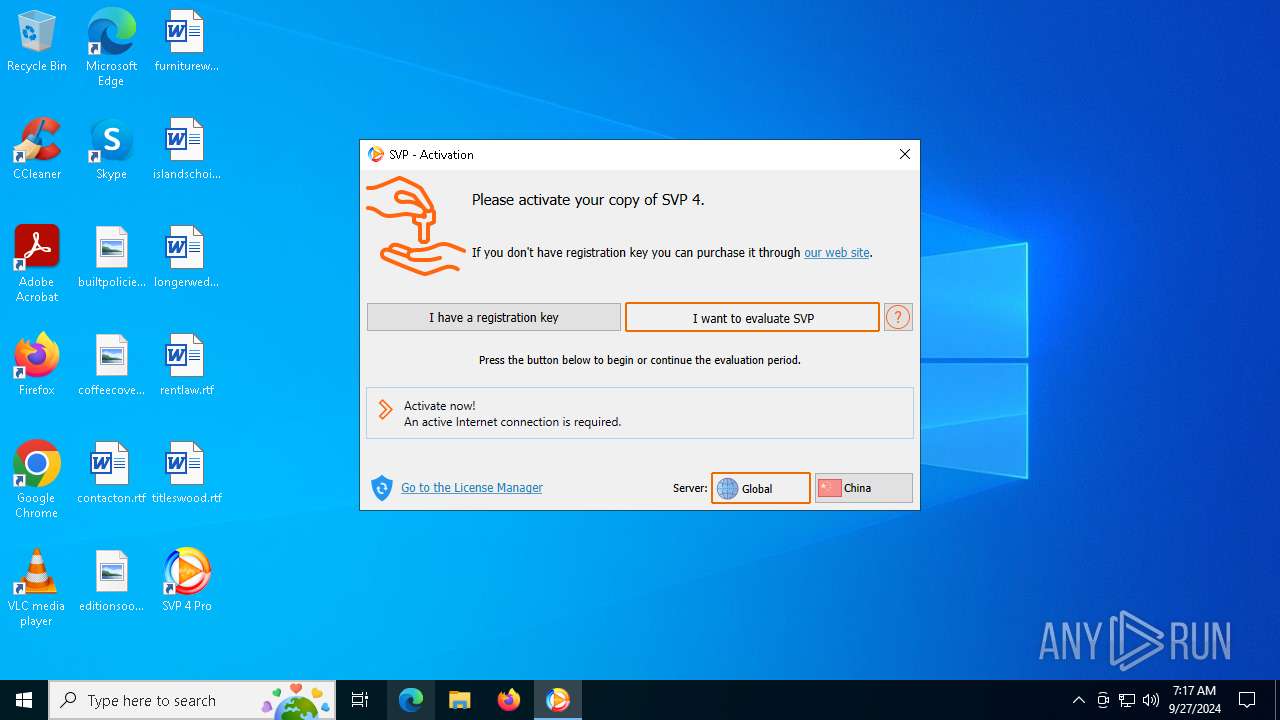
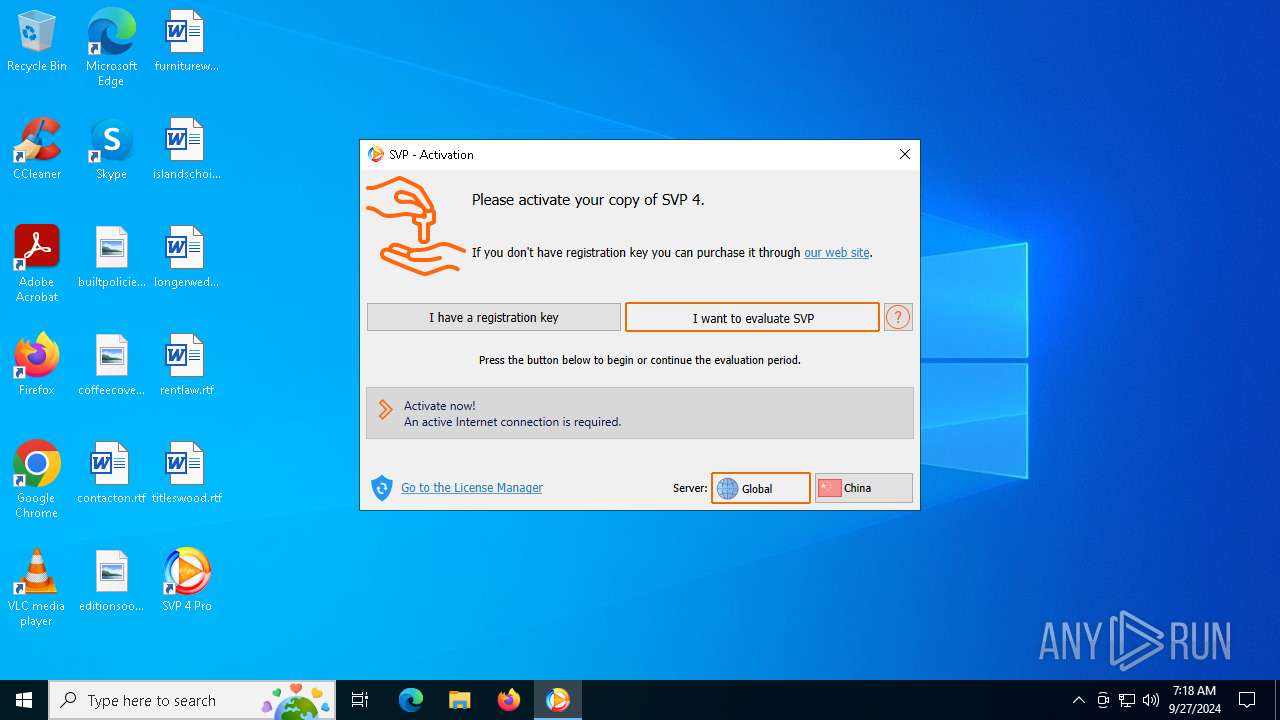
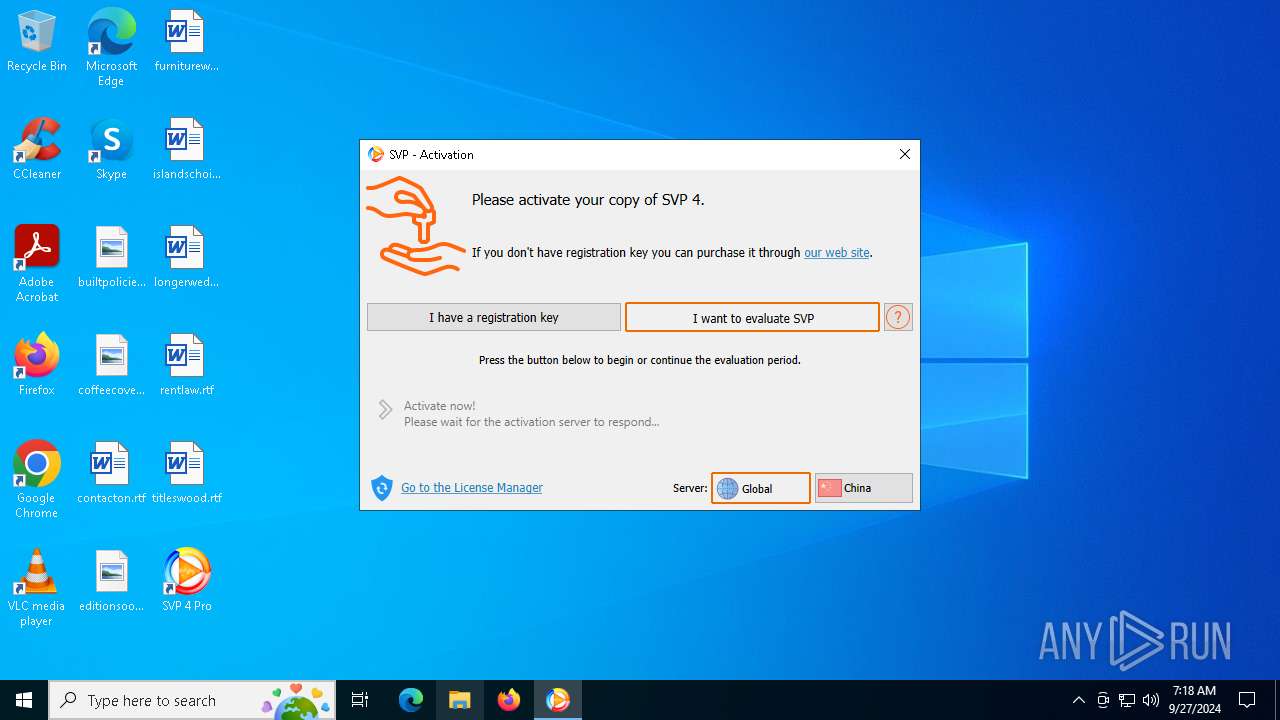
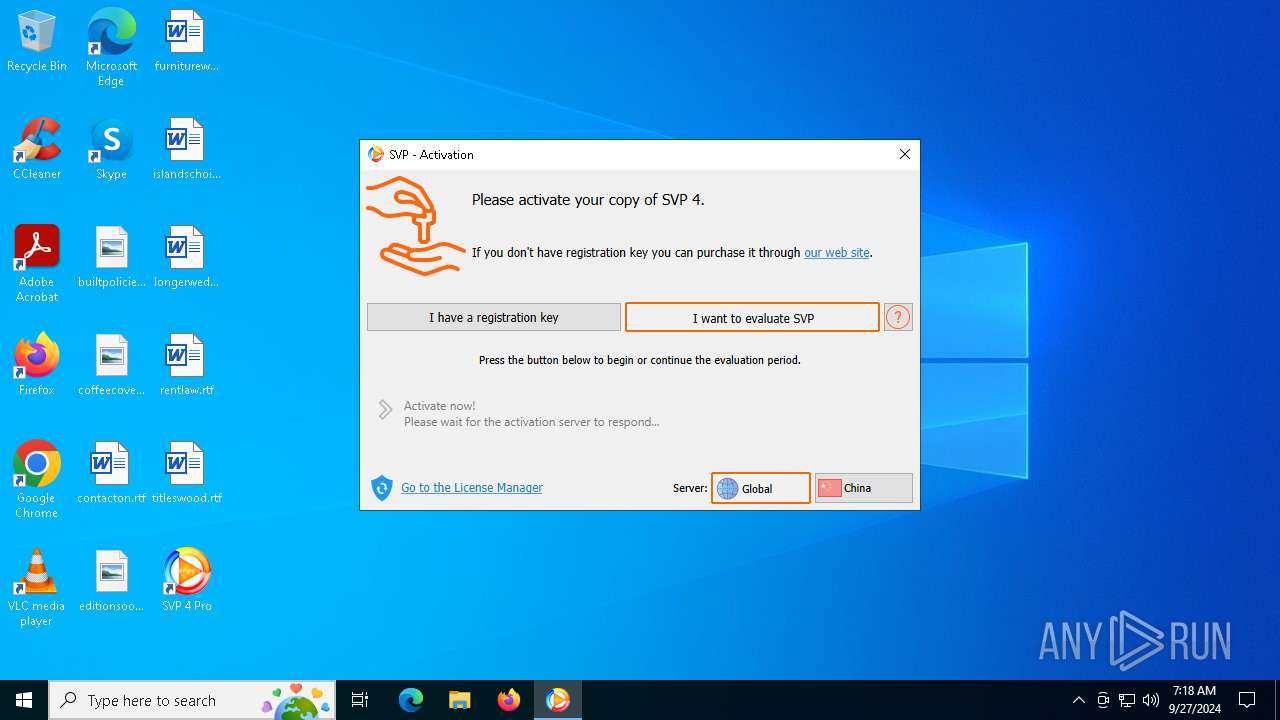
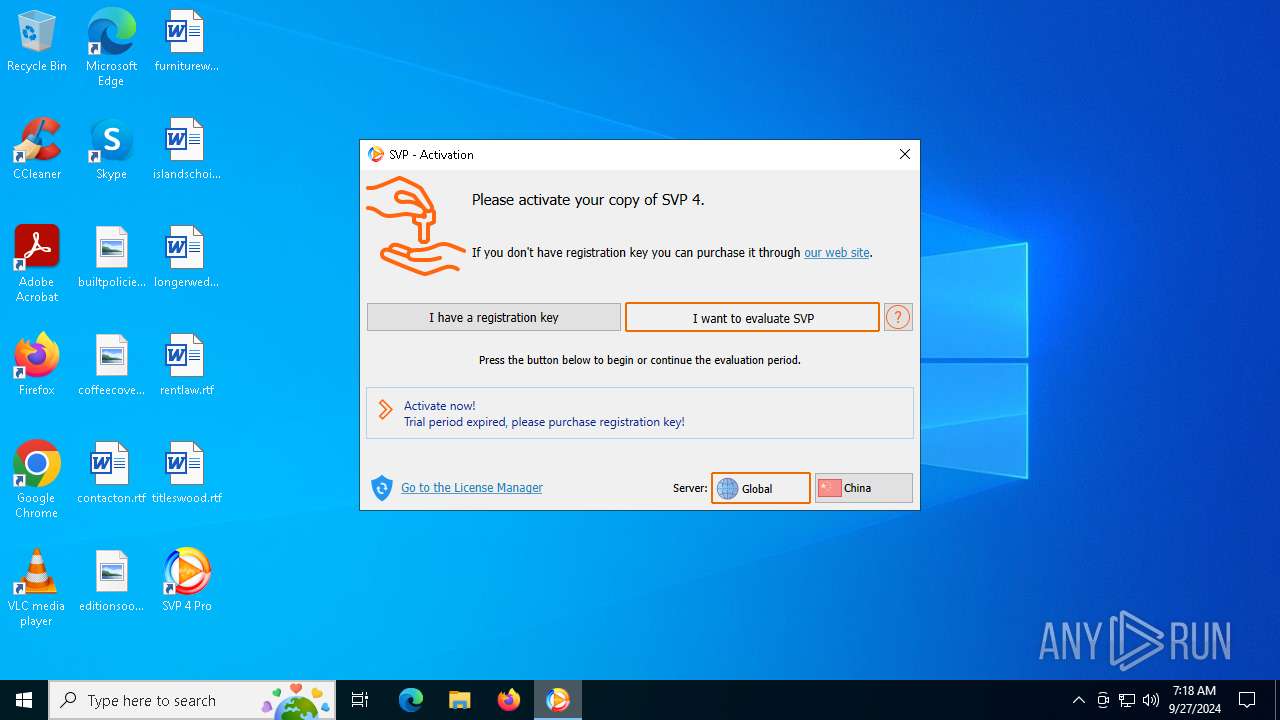
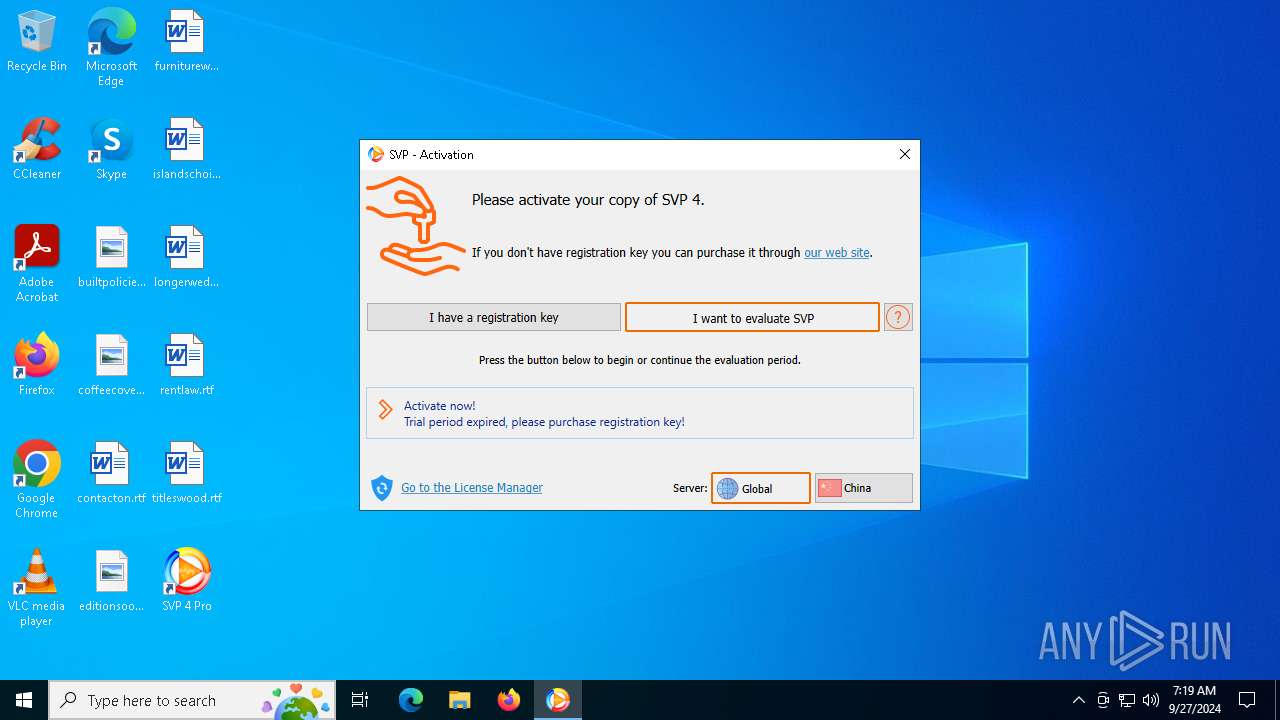
| File name: | svp4-online.exe |
| Full analysis: | https://app.any.run/tasks/4fe10da4-79dc-48bc-b4d3-1bd33402de21 |
| Verdict: | Malicious activity |
| Analysis date: | September 27, 2024, 07:14:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, UPX compressed |
| MD5: | 18230A8B9AE48E9528FBC869F0BC130E |
| SHA1: | 91615995AECC5EC3A41B6524C4A87AD1D6550339 |
| SHA256: | AF00663D7C687C1CC73D9C0BF6B1ABC28F783BCB27A87B0262486FCC2F900625 |
| SSDEEP: | 98304:LqkPl5ioMi990qQbY14zU6pcr49HYunQ6GlOKW088DMcncoL2tnRyMQQALYhAORt:v5XznKLK1f01N6ZG |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 2976)
- cmd.exe (PID: 6744)
- cmd.exe (PID: 6684)
SUSPICIOUS
Process drops legitimate windows executable
- svp4-online.exe (PID: 6920)
- svp4-online.exe (PID: 2252)
- vcredist_2022_x86.exe (PID: 2136)
- vcredist_2022_x86.exe (PID: 5172)
- VC_redist.x86.exe (PID: 1092)
- msiexec.exe (PID: 5376)
- vcredist_2022_x64.exe (PID: 6544)
- VC_redist.x86.exe (PID: 6880)
- vcredist_2022_x64.exe (PID: 3800)
- VC_redist.x64.exe (PID: 6552)
- VC_redist.x64.exe (PID: 6692)
Application launched itself
- svp4-online.exe (PID: 6920)
- VC_redist.x86.exe (PID: 4152)
- VC_redist.x86.exe (PID: 6764)
- VC_redist.x64.exe (PID: 4716)
- VC_redist.x64.exe (PID: 736)
Starts a Microsoft application from unusual location
- vcredist_2022_x86.exe (PID: 2136)
- vcredist_2022_x86.exe (PID: 5172)
- VC_redist.x86.exe (PID: 1092)
- vcredist_2022_x64.exe (PID: 3800)
- vcredist_2022_x64.exe (PID: 6544)
- VC_redist.x64.exe (PID: 6552)
Executable content was dropped or overwritten
- svp4-online.exe (PID: 2252)
- vcredist_2022_x86.exe (PID: 2136)
- vcredist_2022_x86.exe (PID: 5172)
- VC_redist.x86.exe (PID: 1092)
- VC_redist.x86.exe (PID: 6764)
- VC_redist.x86.exe (PID: 6880)
- vcredist_2022_x64.exe (PID: 6544)
- vcredist_2022_x64.exe (PID: 3800)
- VC_redist.x64.exe (PID: 6552)
- VC_redist.x64.exe (PID: 736)
- VC_redist.x64.exe (PID: 6692)
- AviSynthPlus.exe (PID: 2820)
- AviSynthPlus.tmp (PID: 2328)
- cscript.exe (PID: 3596)
Executing commands from a ".bat" file
- svp4-online.exe (PID: 2252)
Starts CMD.EXE for commands execution
- svp4-online.exe (PID: 2252)
Executes as Windows Service
- VSSVC.exe (PID: 2768)
The process drops C-runtime libraries
- msiexec.exe (PID: 5376)
Starts itself from another location
- vcredist_2022_x86.exe (PID: 5172)
- vcredist_2022_x64.exe (PID: 3800)
The process executes VB scripts
- svp4-online.exe (PID: 2252)
INFO
Create files in a temporary directory
- svp4-online.exe (PID: 6920)
UPX packer has been detected
- svp4-online.exe (PID: 6920)
- svp4-online.exe (PID: 2252)
Reads the computer name
- svp4-online.exe (PID: 6920)
Checks supported languages
- svp4-online.exe (PID: 6920)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5376)
Manages system restore points
- SrTasks.exe (PID: 5052)
Application launched itself
- msedge.exe (PID: 6976)
- msedge.exe (PID: 6872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:06:19 15:53:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 9625600 |
| InitializedDataSize: | 225280 |
| UninitializedDataSize: | 16867328 |
| EntryPoint: | 0x1944110 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 385.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileVersion: | 3.1 |
Total processes
232
Monitored processes
98
Malicious processes
5
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | cscript //Nologo C:\Users\admin\AppData\Local\Temp\deferredrenameFx6920.vbs | C:\Windows\SysWOW64\cscript.exe | — | svp4-online.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 472 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3284 --field-trial-handle=2260,i,6955207330171190545,12841471097716269657,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 492 | regsvr32.exe avisynth_filter_64.ax /s | C:\Windows\SysWOW64\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -burn.clean.room="C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -burn.filehandle.attached=536 -burn.filehandle.self=556 -uninstall -quiet -burn.related.upgrade -burn.ancestors={5af95fd8-a22e-458f-acee-c61bd787178e} -burn.filehandle.self=1112 -burn.embedded BurnPipe.{664D643B-A0C9-4D5B-AA13-C4C2435EE766} {E360C041-D896-4554-AD4E-17157D961D44} 6552 | C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe | VC_redist.x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 788 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2224 --field-trial-handle=2184,i,223957947737806325,14048620763506902120,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 864 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6524 --field-trial-handle=2184,i,223957947737806325,14048620763506902120,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1528 --field-trial-handle=2184,i,223957947737806325,14048620763506902120,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 936 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4428 --field-trial-handle=2260,i,6955207330171190545,12841471097716269657,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1092 | "C:\WINDOWS\Temp\{711FC794-EFFE-4FD9-AE9E-E2C7CA106C63}\.be\VC_redist.x86.exe" -q -burn.elevated BurnPipe.{24E605D2-ADAE-4DCF-BD9A-B0CD97EDE3A7} {556CBDCC-FB02-4B66-9EA7-9CF15D7BF1CB} 5172 | C:\Windows\Temp\{711FC794-EFFE-4FD9-AE9E-E2C7CA106C63}\.be\VC_redist.x86.exe | vcredist_2022_x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.40.33810 Exit code: 0 Version: 14.40.33810.0 Modules
| |||||||||||||||
| 1124 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 341
Read events
28 514
Write events
1 203
Delete events
624
Modification events
| (PID) Process: | (4296) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{E5E2C1A6-C90F-4247-8BF5-604FB180A932}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (4296) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{90C56868-7D47-4AA2-A42D-06406A6DB35F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (4296) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{E58206EF-C9F2-4F8C-BF0B-975C28552700}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (4296) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{083863F1-70DE-11D0-BD40-00A0C911CE86}\Instance\{E5E2C1A6-C90F-4247-8BF5-604FB180A932} |
| Operation: | write | Name: | FriendlyName |
Value: AviSynth Filter | |||
| (PID) Process: | (4296) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{083863F1-70DE-11D0-BD40-00A0C911CE86}\Instance\{E5E2C1A6-C90F-4247-8BF5-604FB180A932} |
| Operation: | write | Name: | CLSID |
Value: {E5E2C1A6-C90F-4247-8BF5-604FB180A932} | |||
| (PID) Process: | (4296) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{083863F1-70DE-11D0-BD40-00A0C911CE86}\Instance\{E5E2C1A6-C90F-4247-8BF5-604FB180A932} |
| Operation: | write | Name: | FilterData |
Value: 020000000100200002000000000000003070693300000000000000000E0000000000000000000000307479330000000000020000100200003174793300000000000200002002000032747933000000000002000030020000337479330000000000020000400200003474793300000000000200005002000035747933000000000002000060020000367479330000000000020000700200003774793300000000000200008002000038747933000000000002000090020000397479330000000000020000A00200003A7479330000000000020000B00200003B7479330000000000020000C00200003C7479330000000000020000D00200003D7479330000000000020000E00200003170693308000000000000000E0000000000000000000000307479330000000000020000100200003174793300000000000200002002000032747933000000000002000030020000337479330000000000020000400200003474793300000000000200005002000035747933000000000002000060020000367479330000000000020000700200003774793300000000000200008002000038747933000000000002000090020000397479330000000000020000A00200003A7479330000000000020000B00200003B7479330000000000020000C00200003C7479330000000000020000D00200003D7479330000000000020000E00200007669647300001000800000AA00389B714E56313200001000800000AA00389B715956313200001000800000AA00389B714934323000001000800000AA00389B714959555600001000800000AA00389B715030313000001000800000AA00389B715030313600001000800000AA00389B715955593200001000800000AA00389B715032313000001000800000AA00389B715032313600001000800000AA00389B715956323400001000800000AA00389B715934313000001000800000AA00389B715934313600001000800000AA00389B717DEB36E44F52CE119F530020AF0BA7707EEB36E44F52CE119F530020AF0BA770 | |||
| (PID) Process: | (6928) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E5E2C1A6-C90F-4247-8BF5-604FB180A932}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (6928) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{90C56868-7D47-4AA2-A42D-06406A6DB35F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (6928) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E58206EF-C9F2-4F8C-BF0B-975C28552700}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (6928) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{083863F1-70DE-11D0-BD40-00A0C911CE86}\Instance\{E5E2C1A6-C90F-4247-8BF5-604FB180A932} |
| Operation: | write | Name: | FriendlyName |
Value: AviSynth Filter | |||
Executable files
207
Suspicious files
293
Text files
1 587
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\opt.mpv_dll64-0.34.0-325-meta.7z | compressed | |
MD5:FE08E4DDE803A74653EE935666FAEE9E | SHA256:B59392FE0E0A036273C0A95AF9EBA34ECB721A91D449DB33E5442279FEE28F18 | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\Updates.xml | html | |
MD5:05C9CFCE41B9D7D4AB63EABC2540E85F | SHA256:4449D9BE775D7EBD9D4F1C1A94DFA9FFE296C1D30CE114F34EDED4EAF2C87877 | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\opt.mpcvr-0.8.5-2268-meta.7z | compressed | |
MD5:CC0C7130EE768C409F86B04A703B8944 | SHA256:36F05EA99793F96EDC48B8D8DB6FD18F6198B5CAB94D3248DA9744027F877CD9 | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\deps.python32-3.8.10-meta.7z | compressed | |
MD5:F864BC933395BADA622754D797D72956 | SHA256:F051212A0FFE7F81F83A35C8ED7F56BCEFDF8ACDD223904B753711ADD72C615A | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\svp4-online.Hp6920 | html | |
MD5:05C9CFCE41B9D7D4AB63EABC2540E85F | SHA256:4449D9BE775D7EBD9D4F1C1A94DFA9FFE296C1D30CE114F34EDED4EAF2C87877 | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\opt.vps_portable64-64-meta.7z | compressed | |
MD5:0E77B3AC072334E31B844E0CD0728D39 | SHA256:4C87FEF17DA097039C7DE8802DF2FADB174DA6094F20A9CA804C5DB91DE1A320 | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\deps.avisynth_plus-4003-meta.7z | compressed | |
MD5:B31FA6569E66856982ED96071FF56F0D | SHA256:64E784E6B0BB641DBA5FB1D523C0A59E3C1059B509B169643F600362E4CBC4CA | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\core-4.0.0-6-meta.7z | compressed | |
MD5:1BA0B5D4B173D70DDB383C4FDAE438BD | SHA256:128798634CA0F034F623BB7AB489D1216410FAFE64D8009148935556DD3A117C | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\core.vlc64-1.0.0.190-meta.7z | compressed | |
MD5:B3CD23582E59EDA27AA77AFDD7A728F1 | SHA256:13E88732454E22659CC4CBDE5BC299EA5799FA12A858D8802E3668FEAB362DB9 | |||
| 6920 | svp4-online.exe | C:\Users\admin\AppData\Local\Temp\remoterepo-Dqv5Pk\core.qt-5.15.1-meta.7z | compressed | |
MD5:6D52420201A53EB9A958E1B7AF8CAF42 | SHA256:3ABD8B22684603A43E7124D6DC1178D967557DFDC313D71ABA34248B9C3E4E2F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
76
TCP/UDP connections
148
DNS requests
81
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6920 | svp4-online.exe | GET | 200 | 172.67.75.26:80 | http://cdn.svp-team.com/repo/full/Updates.xml?full=main&95576015 | unknown | — | — | whitelisted |
6920 | svp4-online.exe | GET | 200 | 172.67.75.26:80 | http://cdn.svp-team.com/repo/full/core.vlc64/1.0.0.190meta.7z | unknown | — | — | whitelisted |
6920 | svp4-online.exe | GET | 200 | 172.67.75.26:80 | http://cdn.svp-team.com/repo/full/opt.madvr/0.92.17meta.7z | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6920 | svp4-online.exe | GET | 200 | 172.67.75.26:80 | http://cdn.svp-team.com/repo/full/core.qt/5.15.1meta.7z | unknown | — | — | whitelisted |
6920 | svp4-online.exe | GET | 200 | 172.67.75.26:80 | http://cdn.svp-team.com/repo/full/opt.reclock/1.9.0.6meta.7z | unknown | — | — | whitelisted |
6920 | svp4-online.exe | GET | 200 | 172.67.75.26:80 | http://cdn.svp-team.com/repo/full/deps.python32/3.8.10meta.7z | unknown | — | — | whitelisted |
6572 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6920 | svp4-online.exe | GET | 200 | 172.67.75.26:80 | http://cdn.svp-team.com/repo/full/deps.ffdshow32/4533meta.7z | unknown | — | — | whitelisted |
6920 | svp4-online.exe | GET | 200 | 172.67.75.26:80 | http://cdn.svp-team.com/repo/full/deps/1.0.0meta.7z | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
740 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4472 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2808 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6572 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6572 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6920 | svp4-online.exe | 172.67.75.26:80 | cdn.svp-team.com | CLOUDFLARENET | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cdn.svp-team.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
SVPManager.exe | 07:16:28.652 [I]: Main: starting up SVP 4 Pro [4.6.0.273]...
|
SVPManager.exe | 07:16:28.652 [W]: Main: running as Administrator
|
SVPManager.exe | 07:16:28.652 [I]: Main: args: -main -quit
|
SVPManager.exe | 07:16:28.652 [I]: Main: working dir is C:\Program Files (x86)\SVP 4\
|
SVPManager.exe | 07:16:28.652 [I]: Main: data dir set to C:\Users\admin\AppData\Roaming\SVP4\
|
SVPManager.exe | 07:16:28.652 [W]: Settings: creating main.cfg with default values
|
SVPManager.exe | 07:16:28.652 [I]: Settings: loading main.cfg OK
|
SVPManager.exe | 07:16:28.652 [W]: Settings: creating ui.cfg with default values
|
SVPManager.exe | 07:16:28.652 [I]: Settings: loading ui.cfg OK
|
SVPManager.exe | 07:16:28.652 [W]: Settings: creating frc.cfg with default values
|