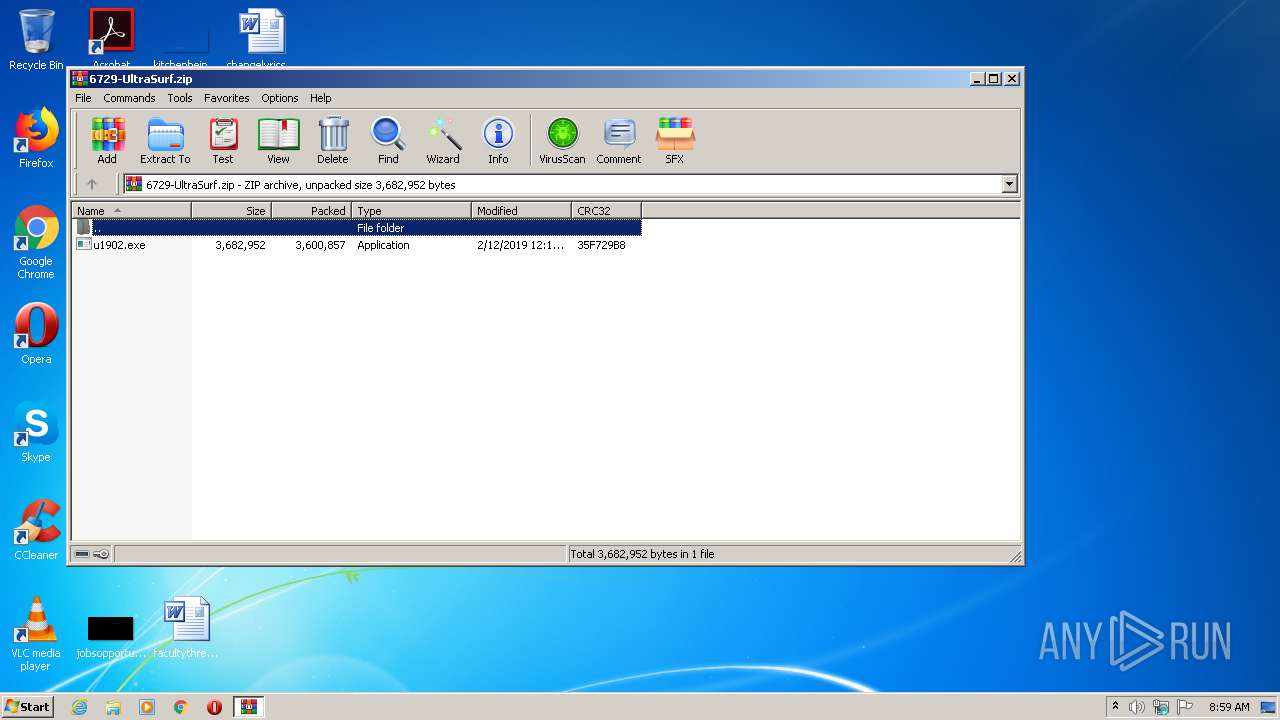
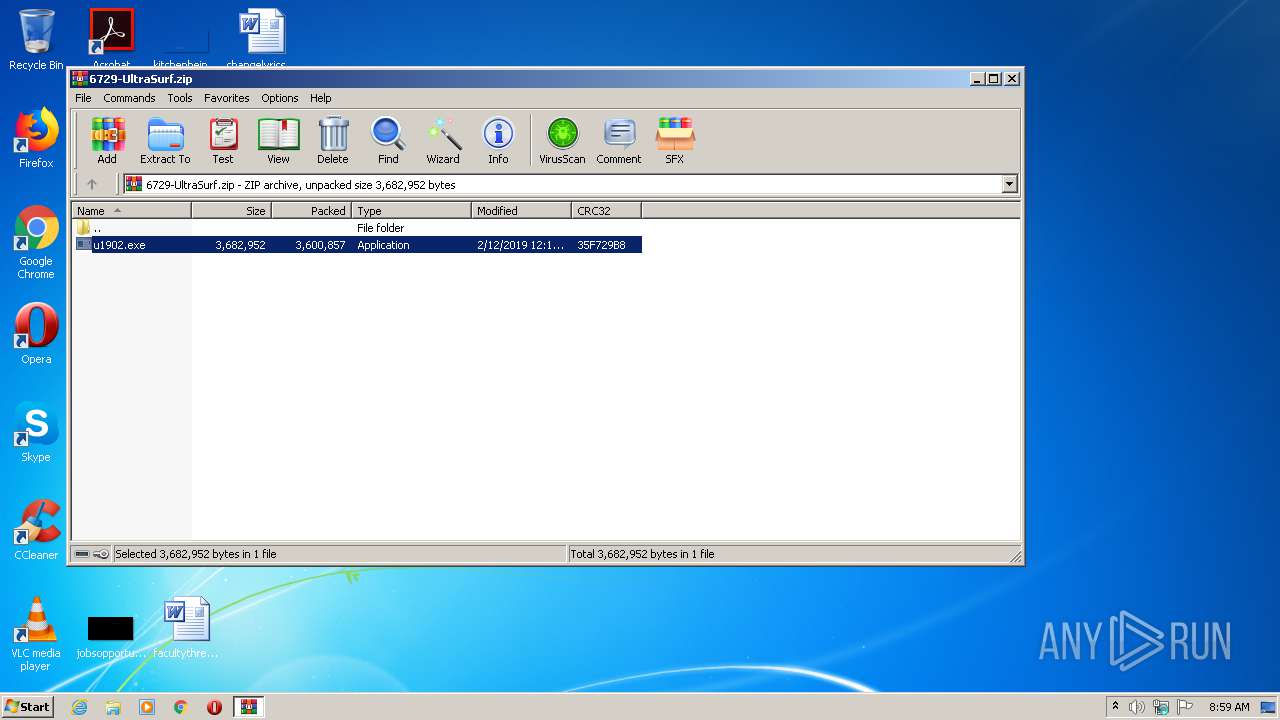
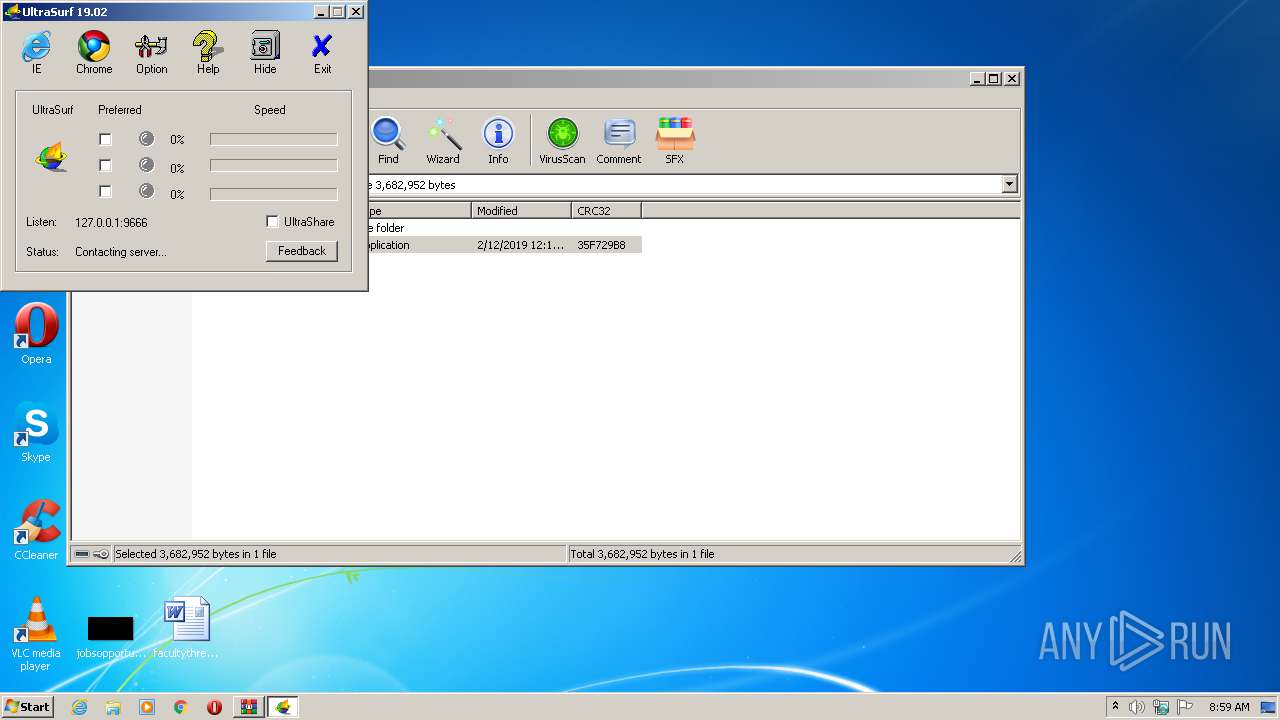
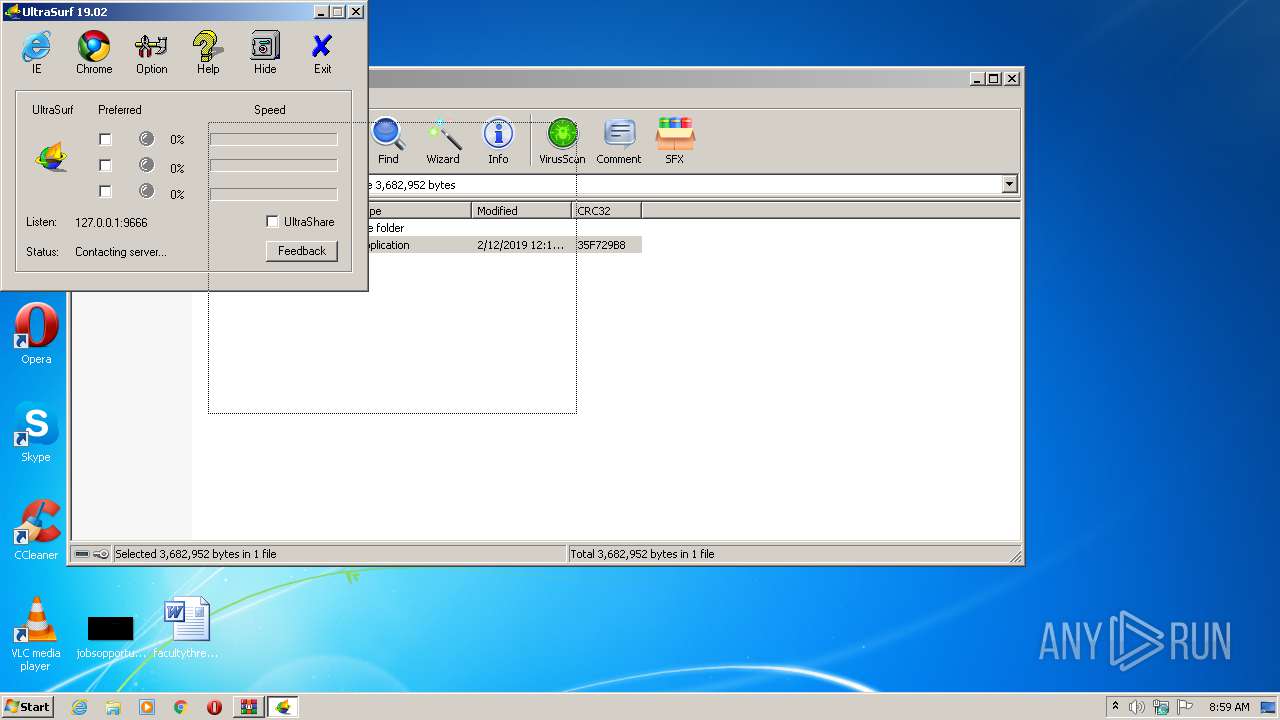
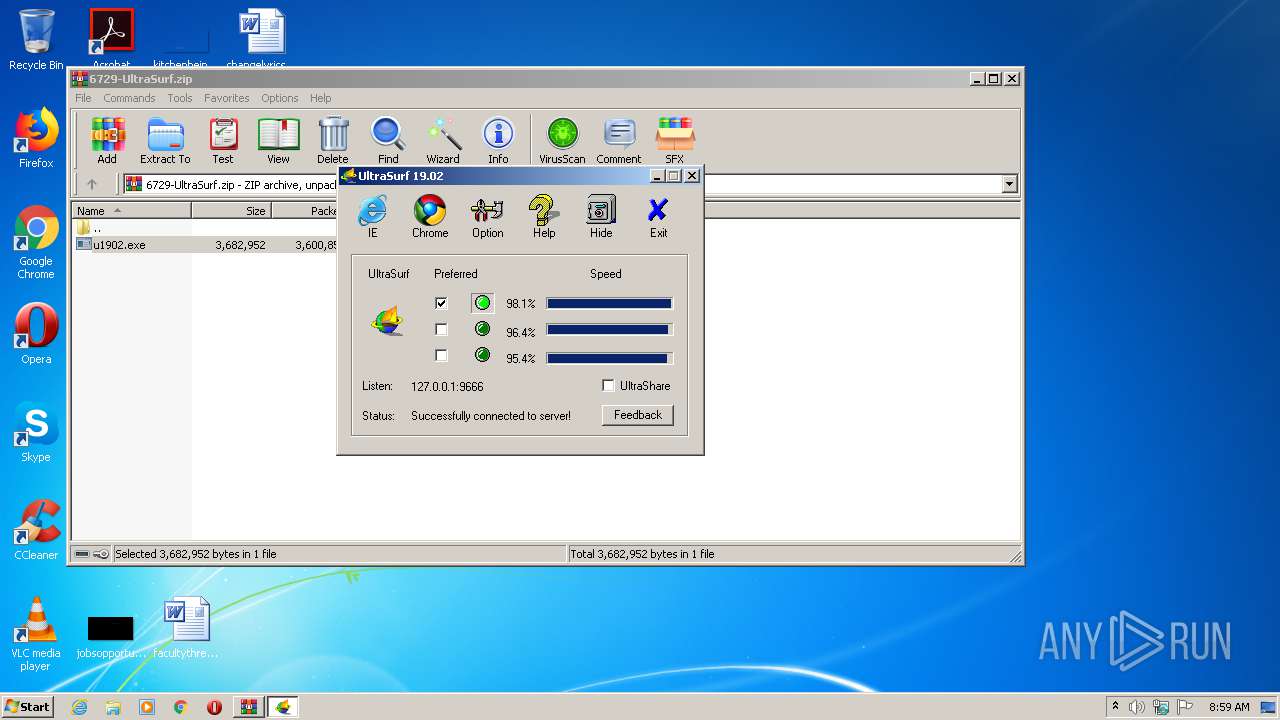
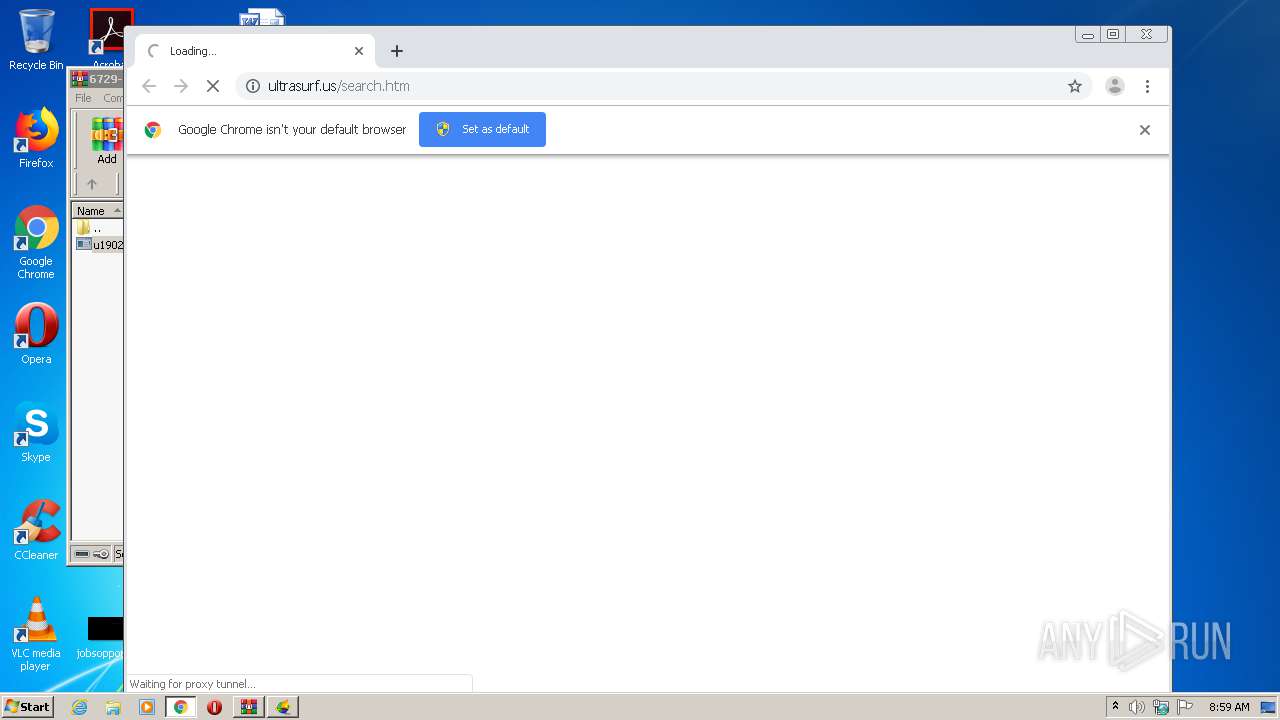
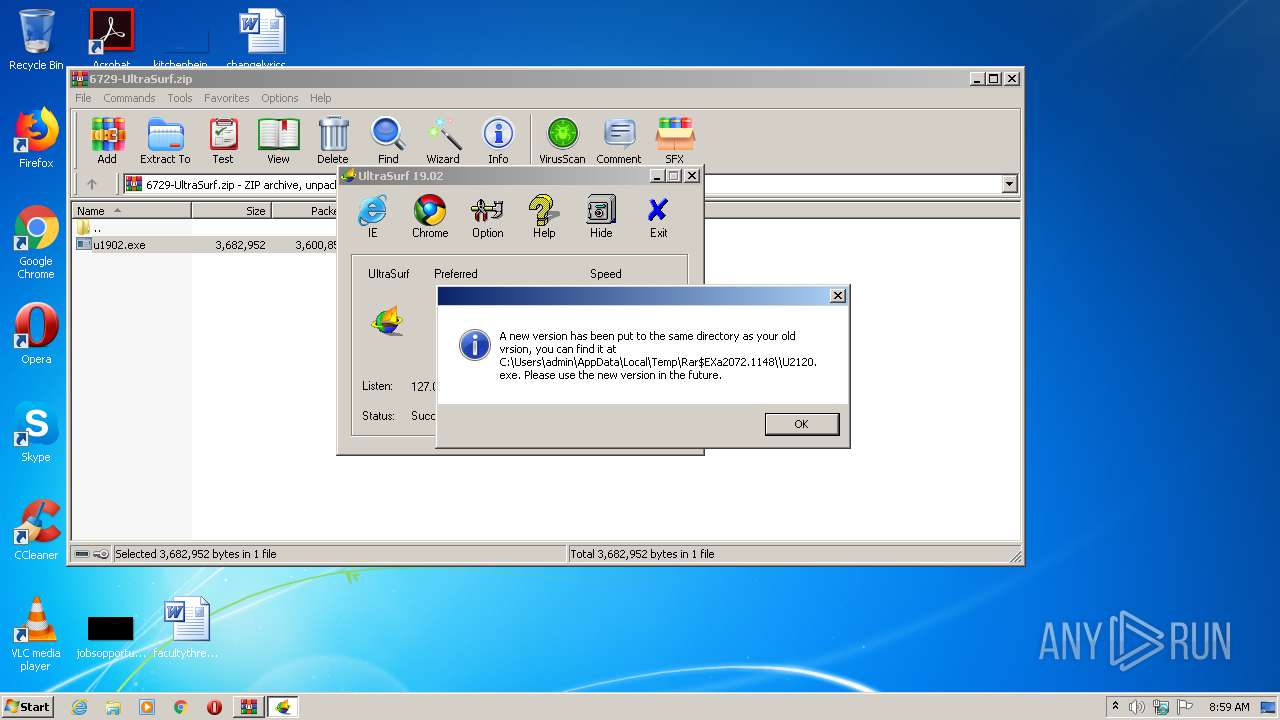
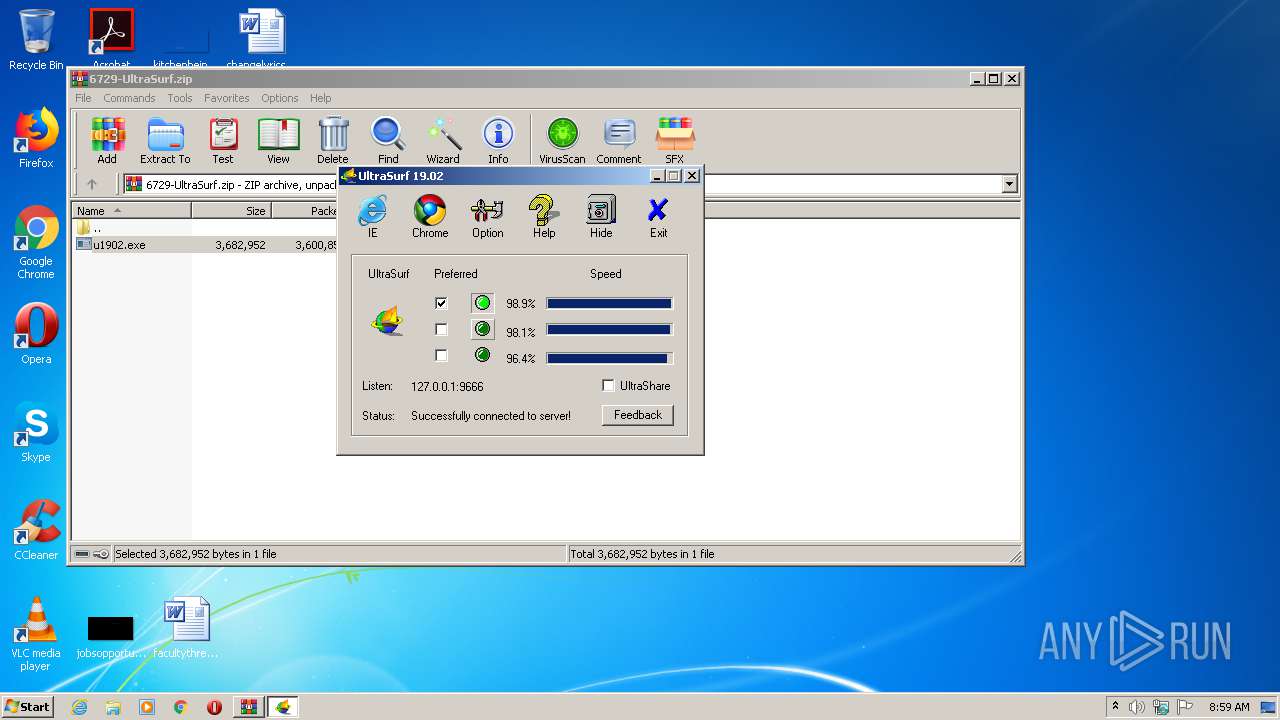
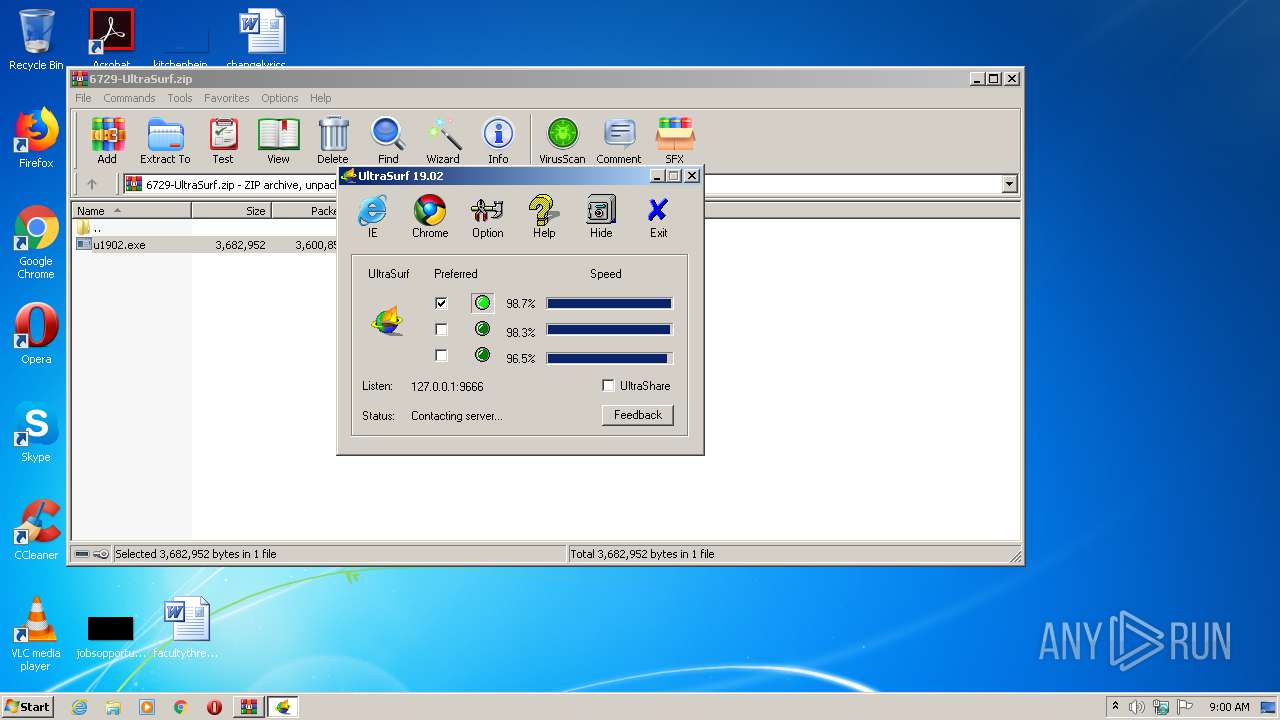
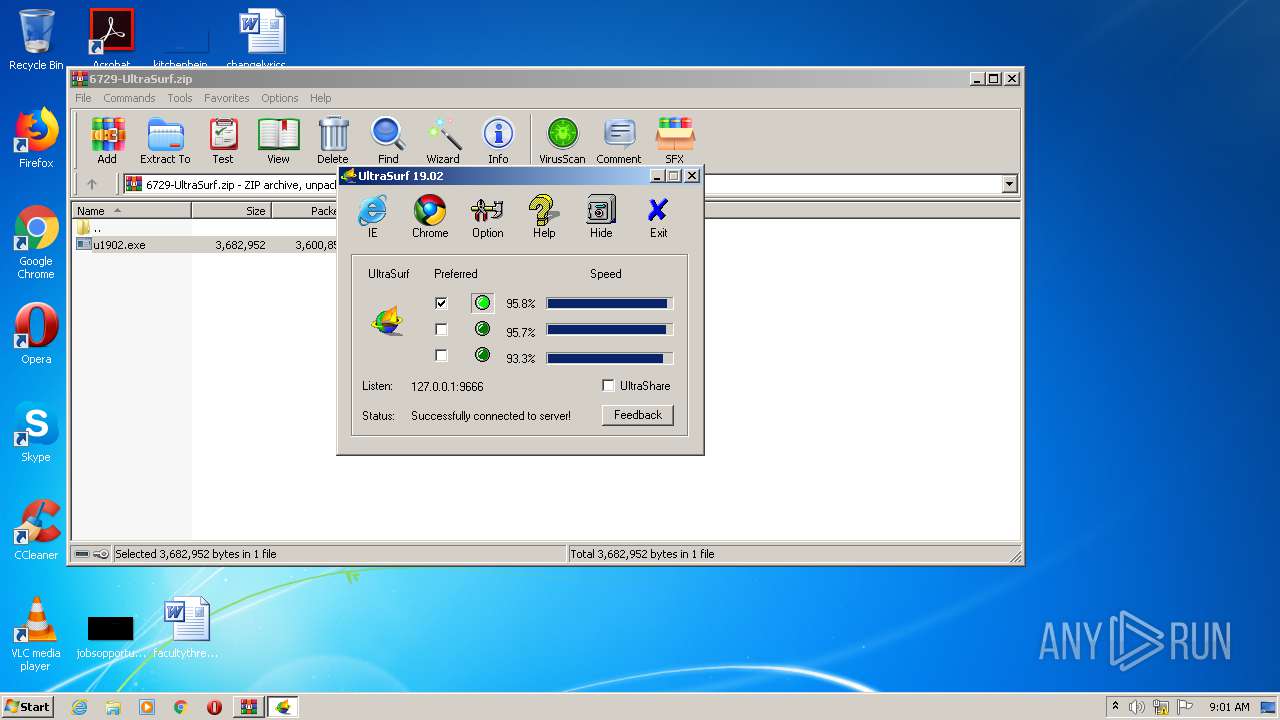
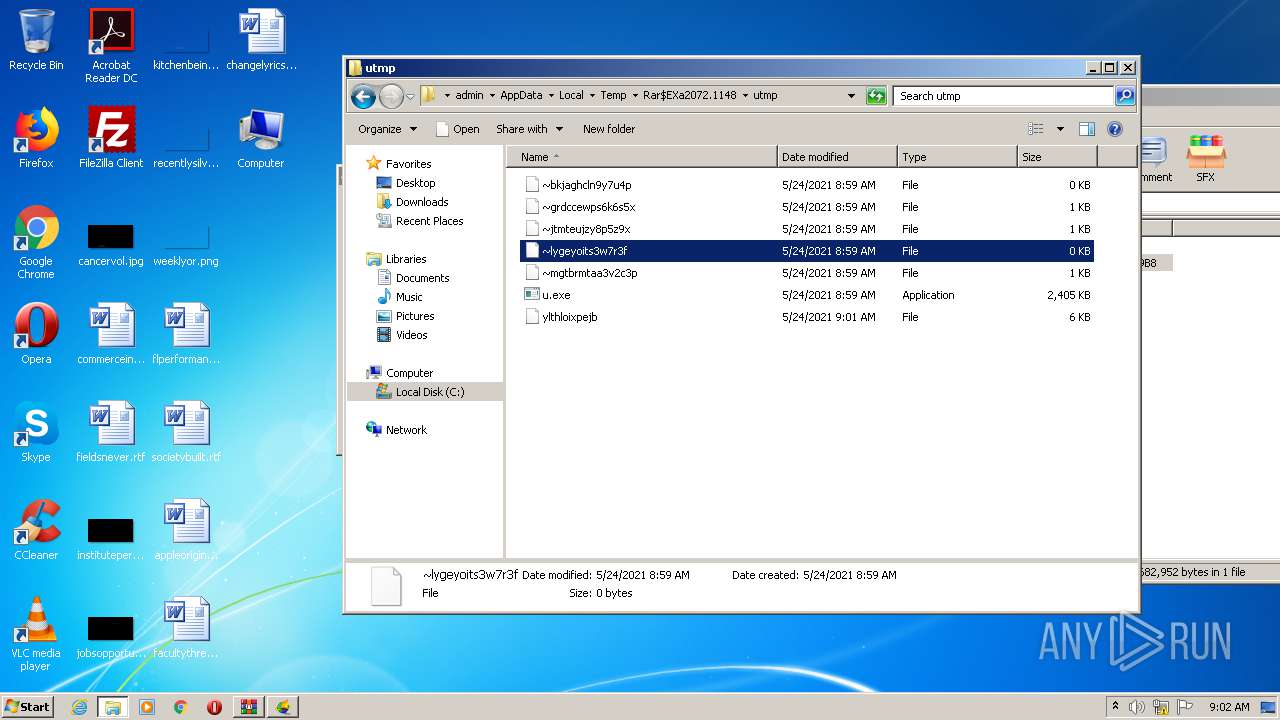
| File name: | 6729-UltraSurf.zip |
| Full analysis: | https://app.any.run/tasks/c8b407c7-5d5f-4fb3-8f3e-06f33d75a782 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2021, 07:59:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | AE3A28953440346B20FAA79632EAF927 |
| SHA1: | BD36C949019300EF4D2015C5421B80B277DAD49B |
| SHA256: | AEFFD5219863CB9406D03738732220D71482EDEB46B1C98E41C06E707E751E3F |
| SSDEEP: | 49152:M96rGdEXpU7Tic/phot/uDB4TS9+VGmfGWPKCob7UyCp3mfE/MOu01rP72/Jodty:CJ+Xm37zdYu+L+PwTMwrPS/GlwRzpJfd |
MALICIOUS
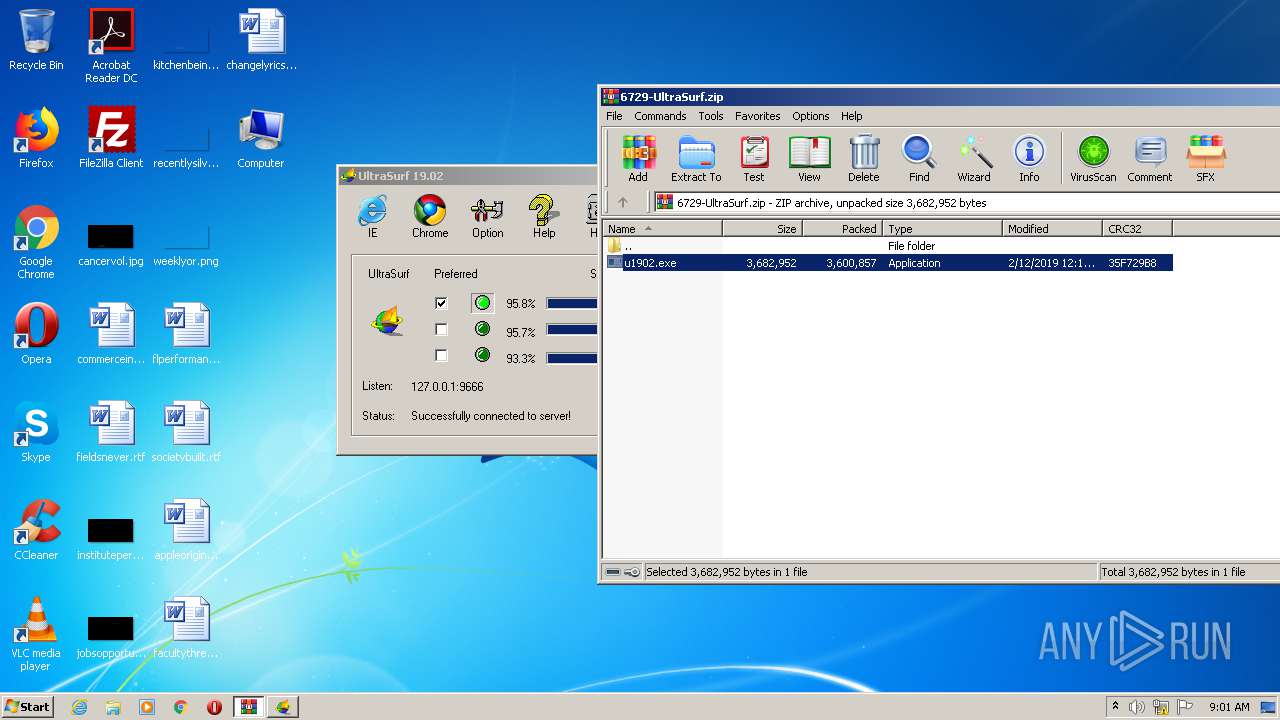
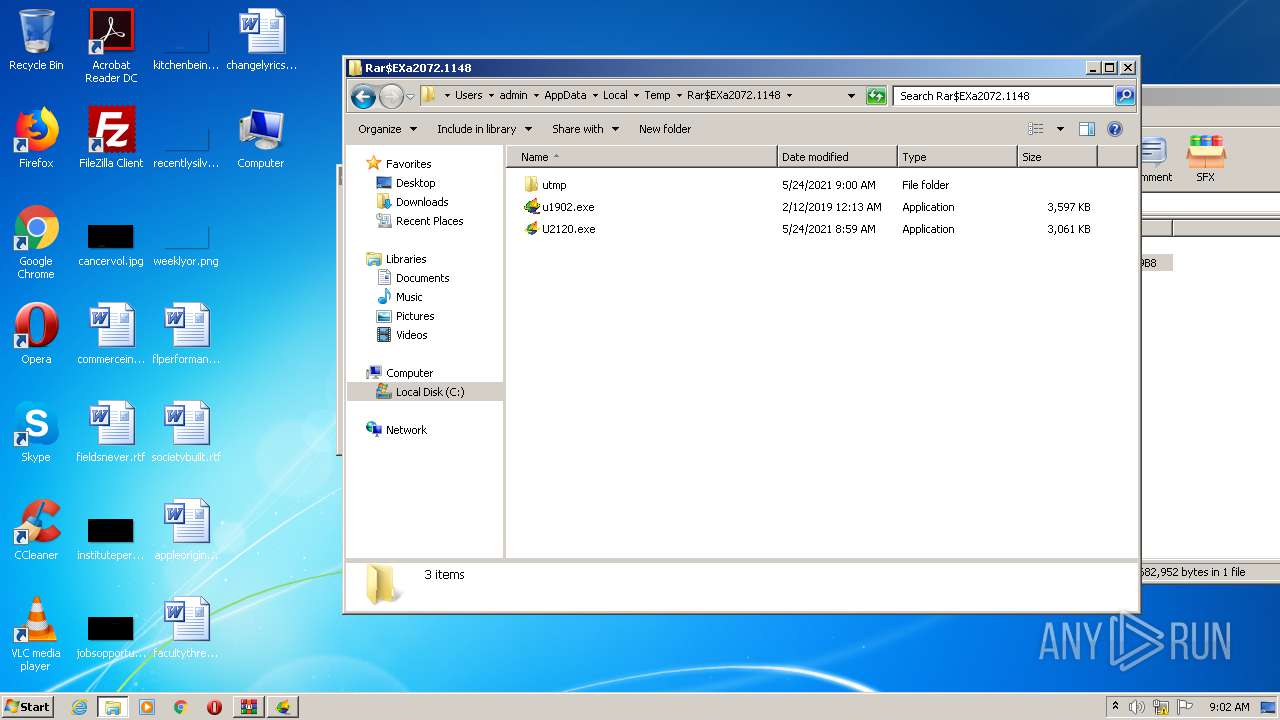
Drops executable file immediately after starts
- u1902.exe (PID: 2424)
Application was dropped or rewritten from another process
- u.exe (PID: 2616)
- u1902.exe (PID: 2424)
- u.exe (PID: 992)
- u.exe (PID: 3084)
- u.exe (PID: 2140)
Changes internet zones settings
- u1902.exe (PID: 2424)
SUSPICIOUS
Drops a file with too old compile date
- u1902.exe (PID: 2424)
- u.exe (PID: 2616)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2072)
- u1902.exe (PID: 2424)
- u.exe (PID: 2616)
Executed via COM
- DllHost.exe (PID: 548)
- DllHost.exe (PID: 648)
INFO
Application launched itself
- chrome.exe (PID: 3984)
Reads the hosts file
- chrome.exe (PID: 3984)
- chrome.exe (PID: 1504)
Reads settings of System Certificates
- chrome.exe (PID: 1504)
Manual execution by user
- rundll32.exe (PID: 2940)
- u.exe (PID: 3084)
- notepad++.exe (PID: 1776)
- notepad++.exe (PID: 2416)
- u.exe (PID: 2140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
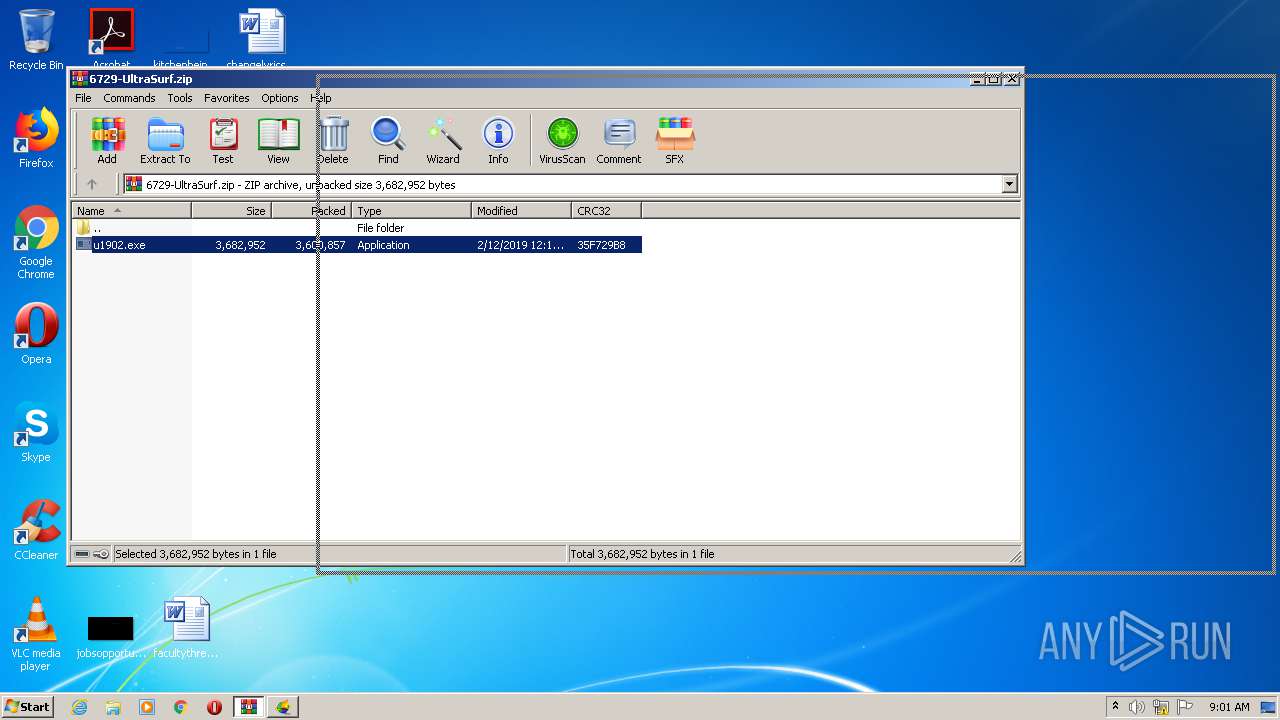
| ZipFileName: | u1902.exe |
|---|---|
| ZipUncompressedSize: | 3682952 |
| ZipCompressedSize: | 3600857 |
| ZipCRC: | 0x35f729b8 |
| ZipModifyDate: | 2019:02:12 00:13:12 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
68
Monitored processes
22
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | C:\Windows\system32\DllHost.exe /Processid:{F9717507-6651-4EDB-BFF7-AE615179BCCF} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6b27a9d0,0x6b27a9e0,0x6b27a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 648 | C:\Windows\system32\DllHost.exe /Processid:{F9717507-6651-4EDB-BFF7-AE615179BCCF} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\u.exe -L="127.0.0.1:9666" -CID="18777450", -ProgPath="C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\\" -TmpPath="C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\\" -ConnMode=0 -version="1902100" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\u.exe | u1902.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,3478480588049031378,8550659770364457954,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=13759724300069575904 --mojo-platform-channel-handle=1648 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3996 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
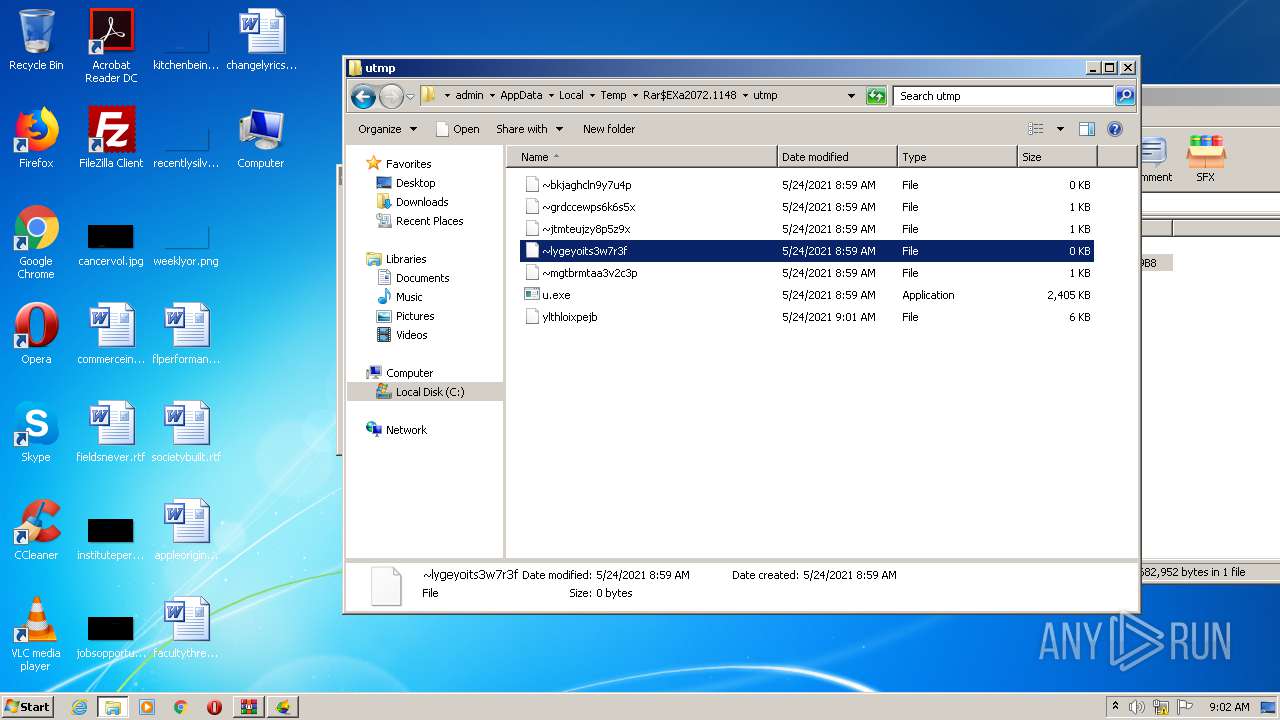
| 1776 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\~lygeyoits3w7r3f" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\6729-UltraSurf.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2140 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\u.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\u.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,3478480588049031378,8550659770364457954,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7438819299277641918 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1816 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 090
Read events
864
Write events
222
Delete events
4
Modification events
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\6729-UltraSurf.zip | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
3
Suspicious files
20
Text files
71
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60AB5CF4-F90.pma | — | |
MD5:— | SHA256:— | |||
| 3984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\fb4eb435-96d0-4a32-96ad-51a397ca21d6.tmp | — | |
MD5:— | SHA256:— | |||
| 2616 | u.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\ylthloixpejb | binary | |
MD5:— | SHA256:— | |||
| 3984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2424 | u1902.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\~jtmteujzy8p5z9x | binary | |
MD5:— | SHA256:— | |||
| 2424 | u1902.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2072.1148\utmp\~mgtbrmtaa3v2c3p | binary | |
MD5:— | SHA256:— | |||
| 2424 | u1902.exe | C:\Users\admin\PUTTY.RND | binary | |
MD5:— | SHA256:— | |||
| 3984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF13cdb3.TMP | text | |
MD5:— | SHA256:— | |||
| 3984 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF13cd46.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
35
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2616 | u.exe | 52.84.180.98:443 | dq33tynpwunh.cloudfront.net | Amazon.com, Inc. | US | unknown |
992 | u.exe | 52.84.180.98:443 | dq33tynpwunh.cloudfront.net | Amazon.com, Inc. | US | unknown |
992 | u.exe | 64.62.219.62:443 | — | Hurricane Electric, Inc. | US | unknown |
992 | u.exe | 74.82.60.20:443 | — | Hurricane Electric, Inc. | US | unknown |
992 | u.exe | 65.49.2.63:443 | — | Hurricane Electric, Inc. | US | unknown |
992 | u.exe | 65.49.68.25:443 | — | Hurricane Electric, Inc. | US | unknown |
992 | u.exe | 111.242.190.162:443 | — | Data Communication Business Group | TW | unknown |
992 | u.exe | 36.237.135.221:443 | — | Data Communication Business Group | TW | unknown |
992 | u.exe | 61.224.156.228:443 | — | Data Communication Business Group | TW | unknown |
992 | u.exe | 112.104.27.84:443 | — | Digital United Inc. | TW | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.septa.org |
| shared |
dq33tynpwunh.cloudfront.net |
| suspicious |
www.google.com |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
ajax.microsoft.com |
| whitelisted |
mail.google.com |
| shared |
do.skype.com |
| whitelisted |
www.tsx.com |
| whitelisted |
www.gmail.com |
| shared |
notepad-plus-plus.org |
| whitelisted |