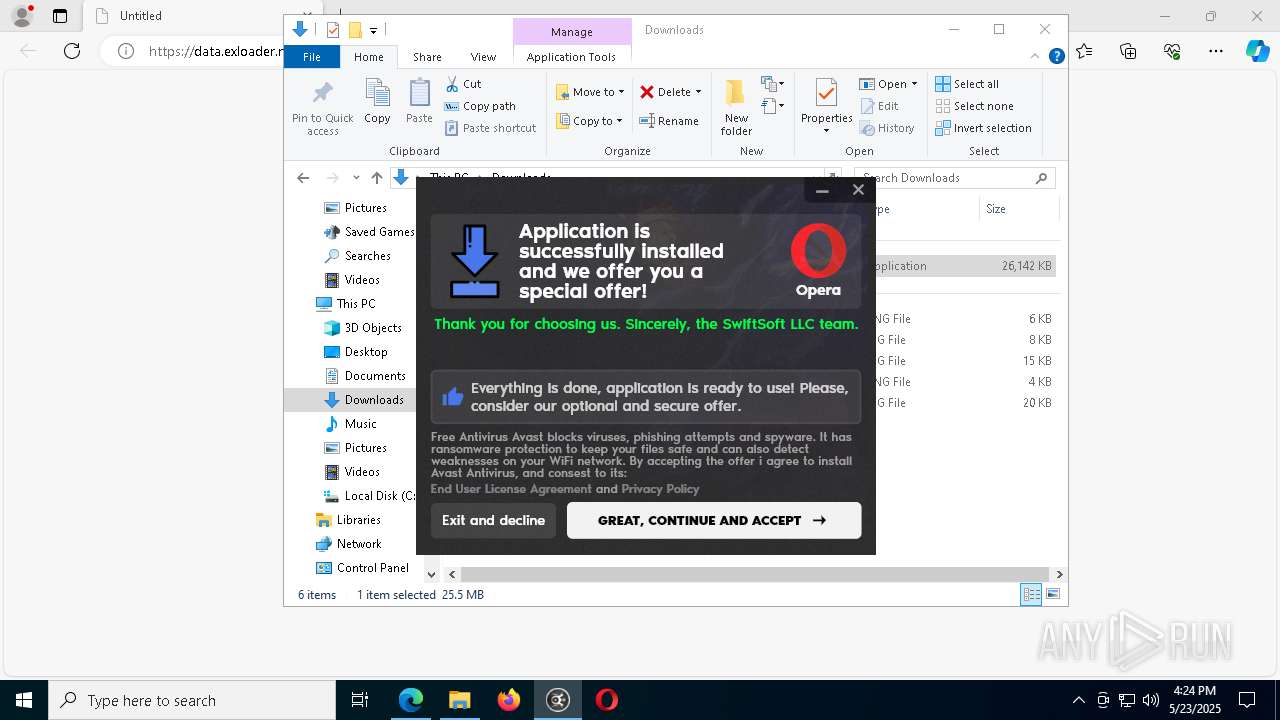
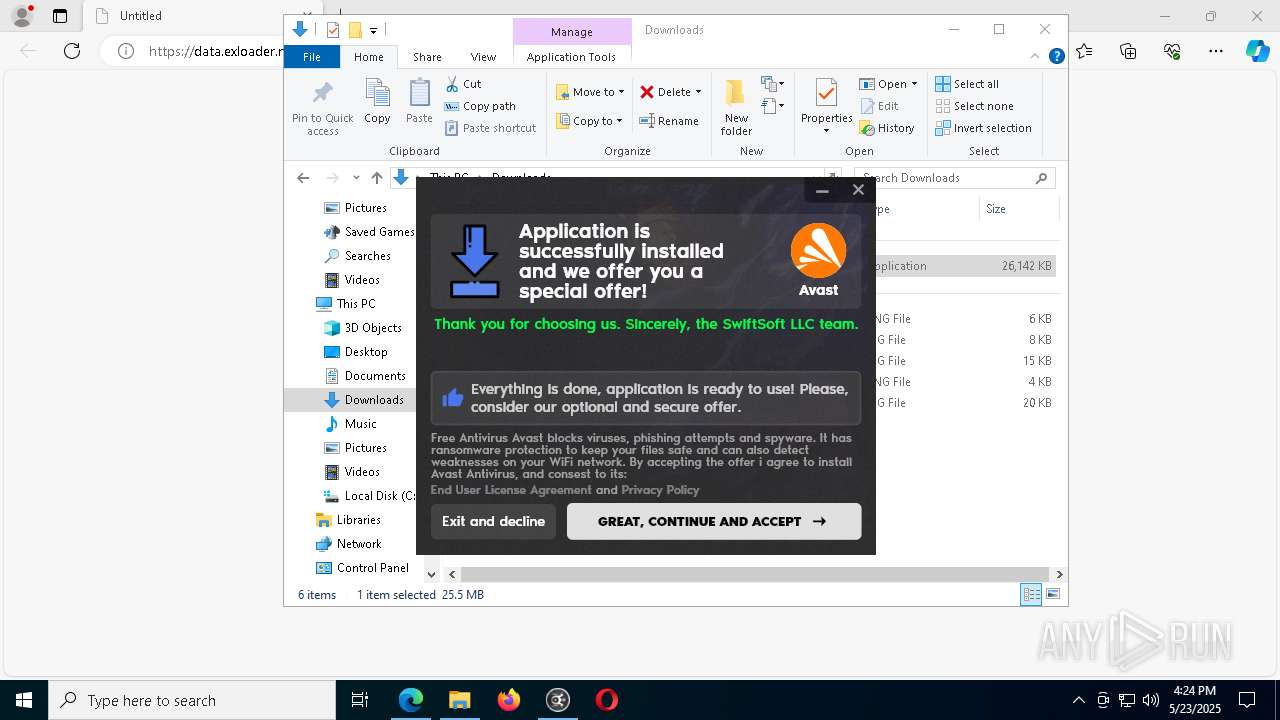
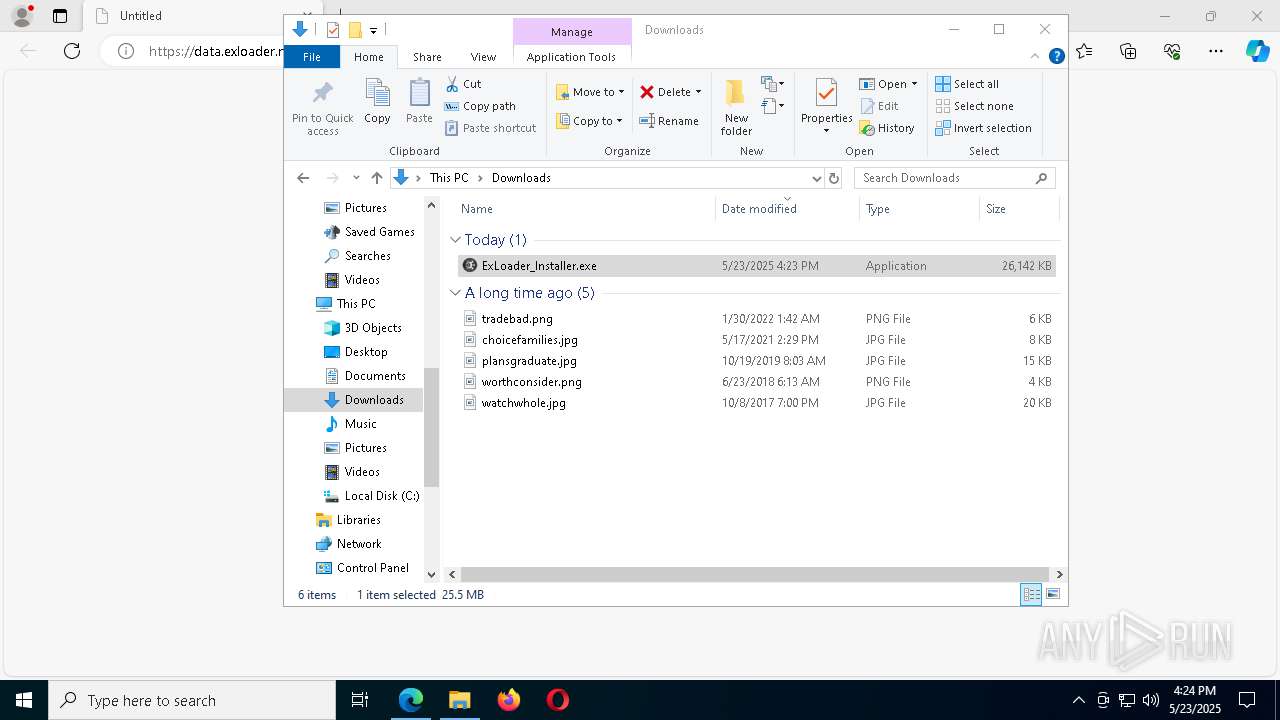
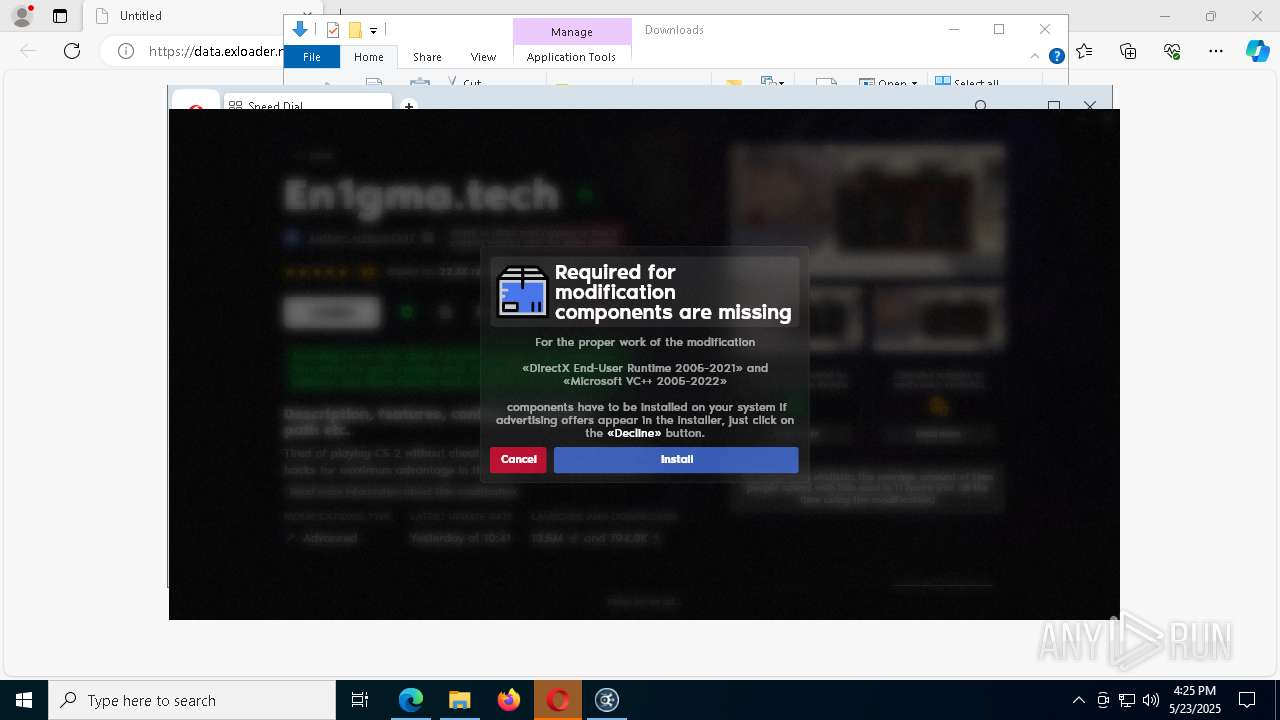
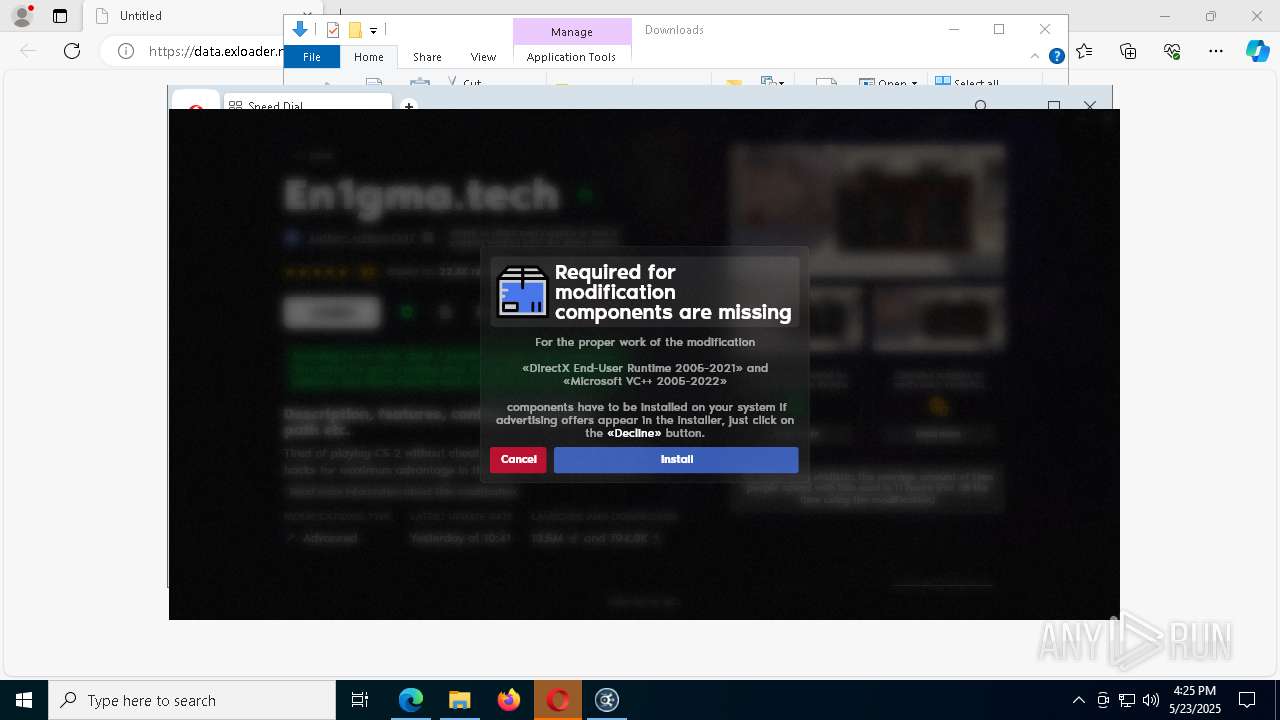
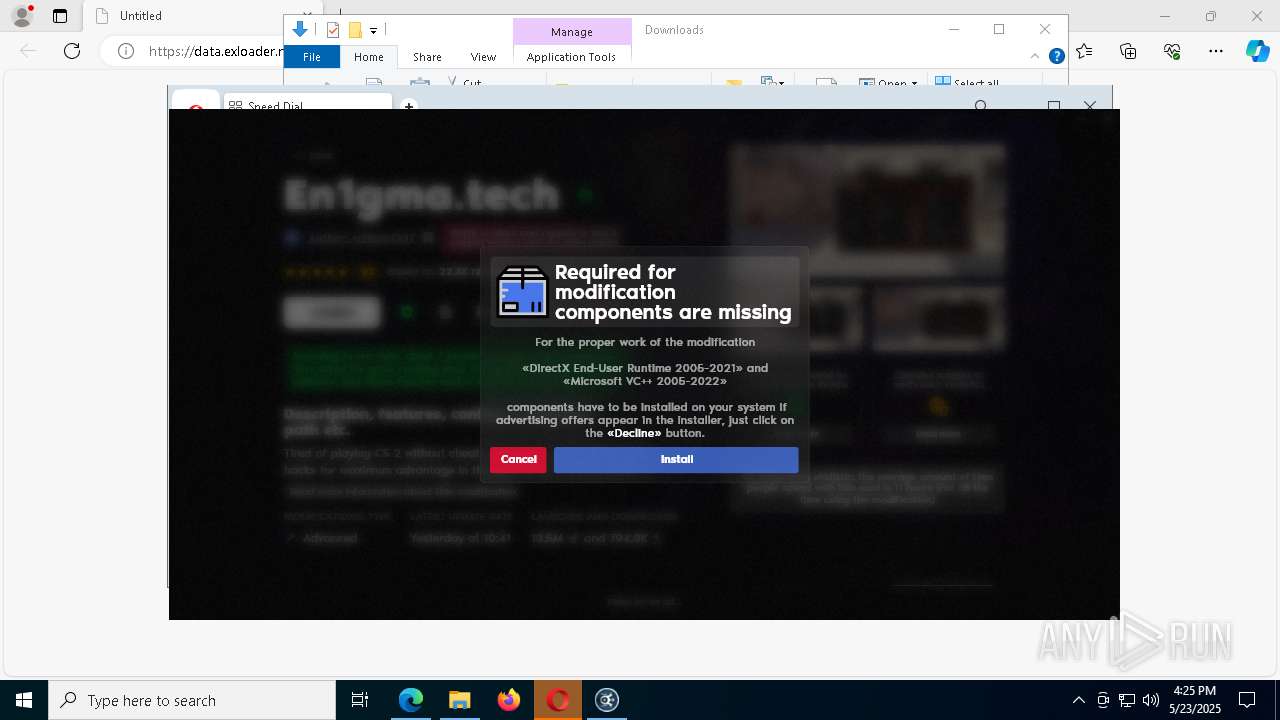
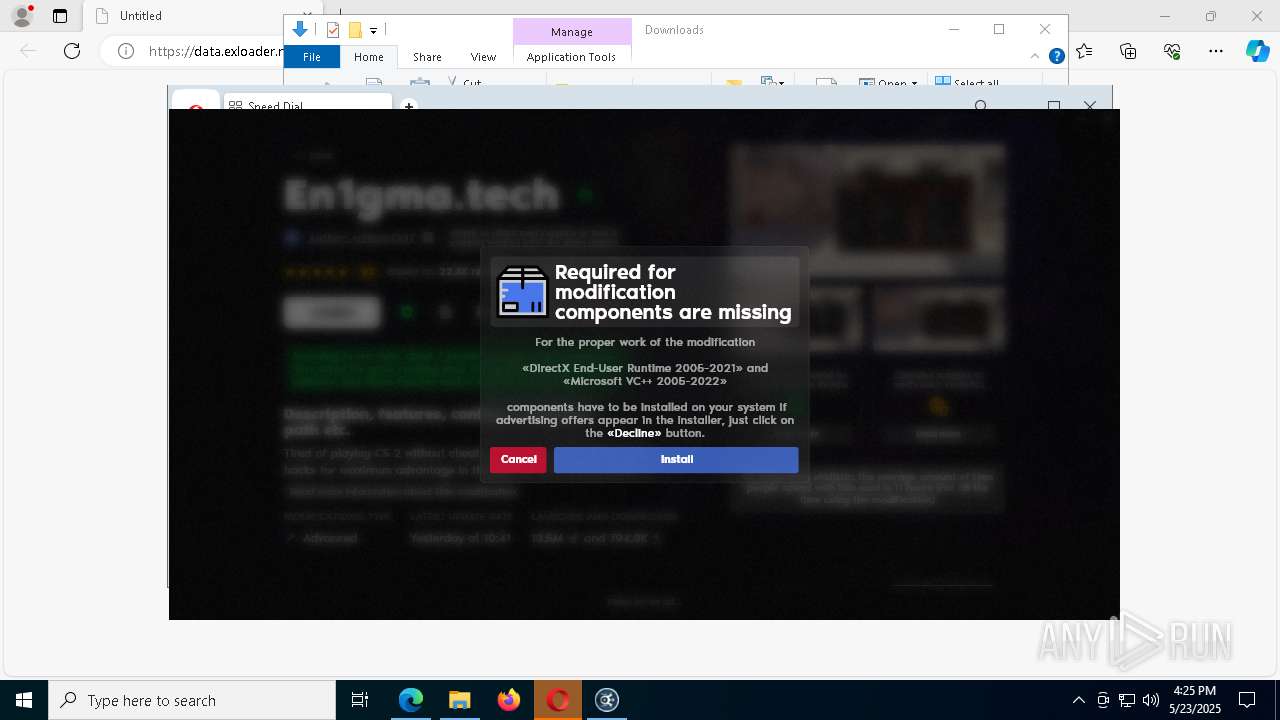
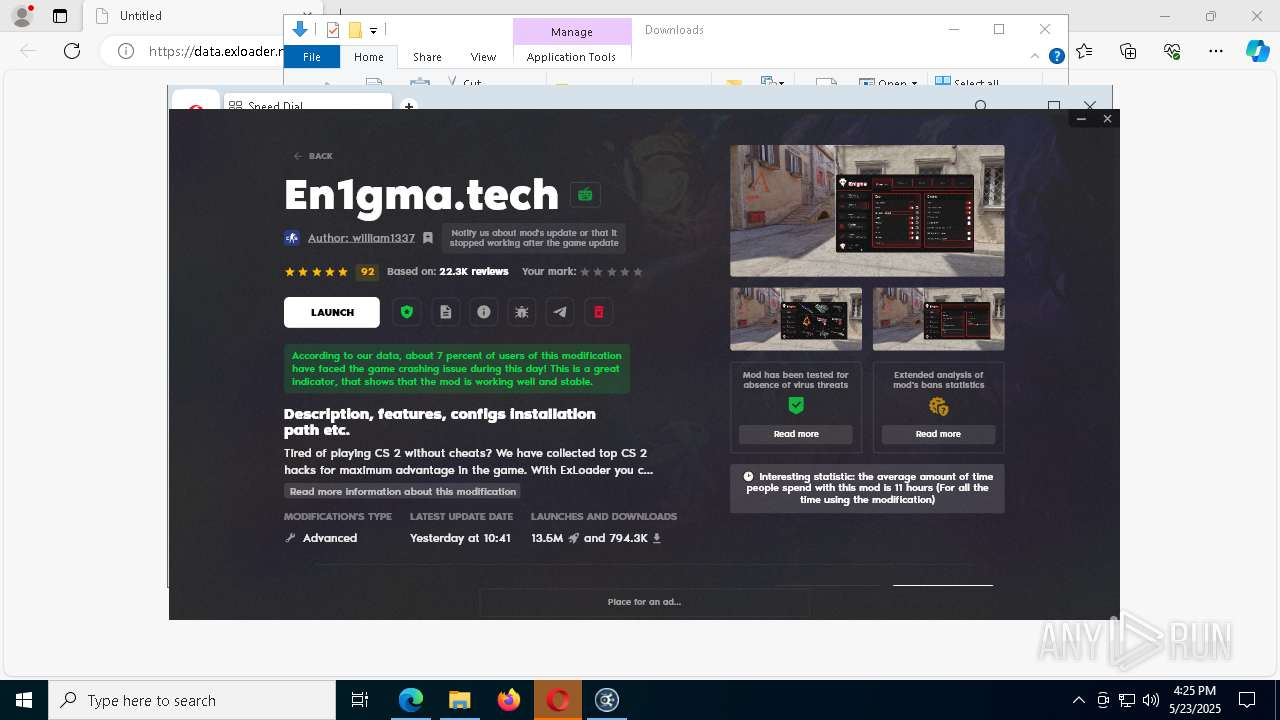
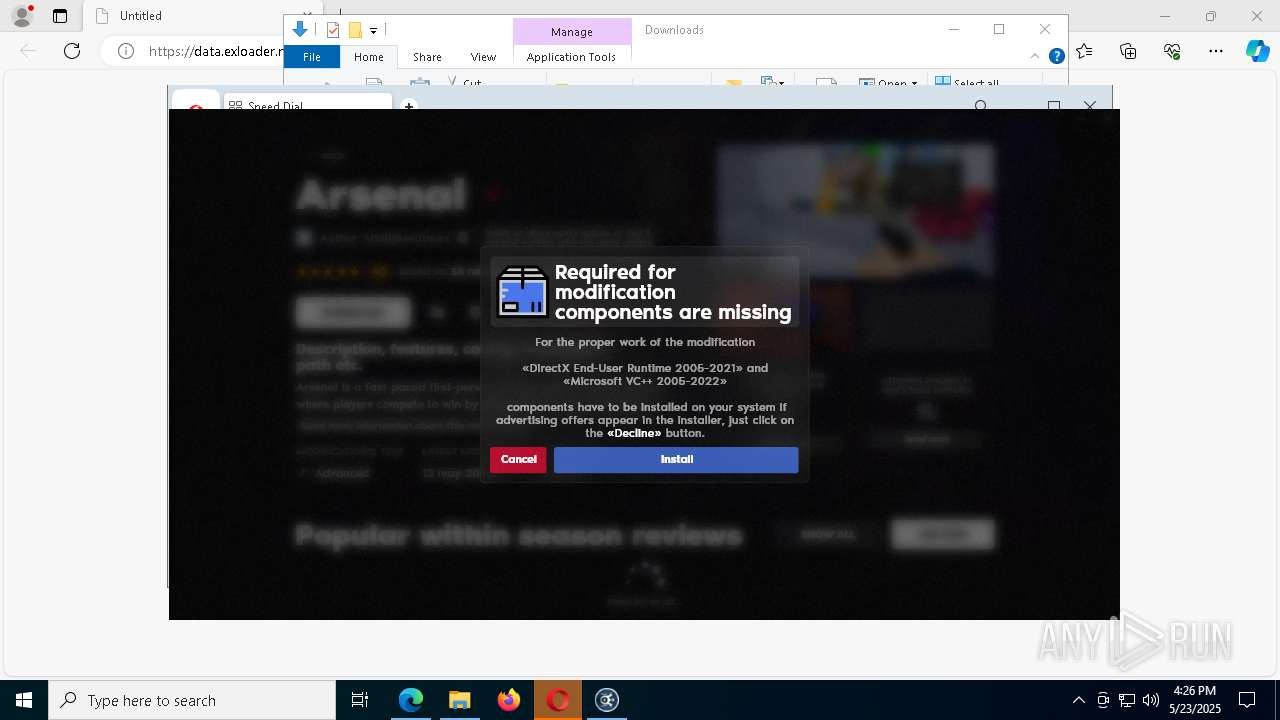
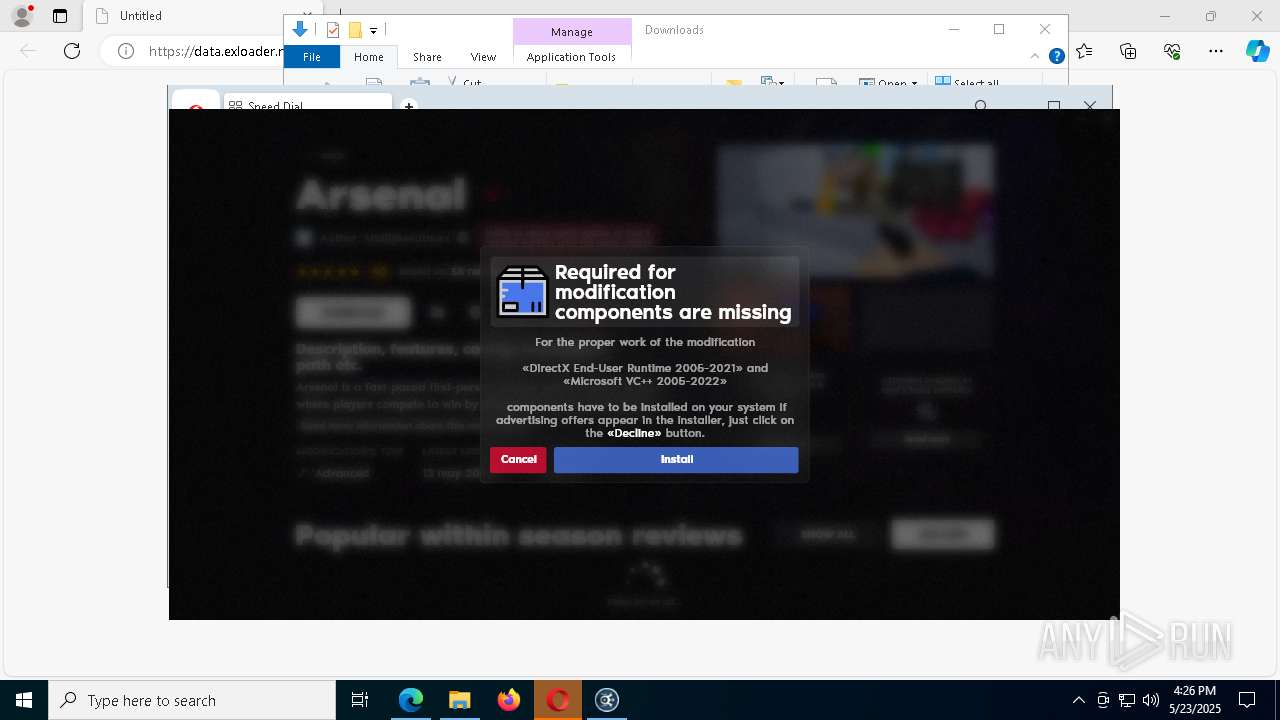
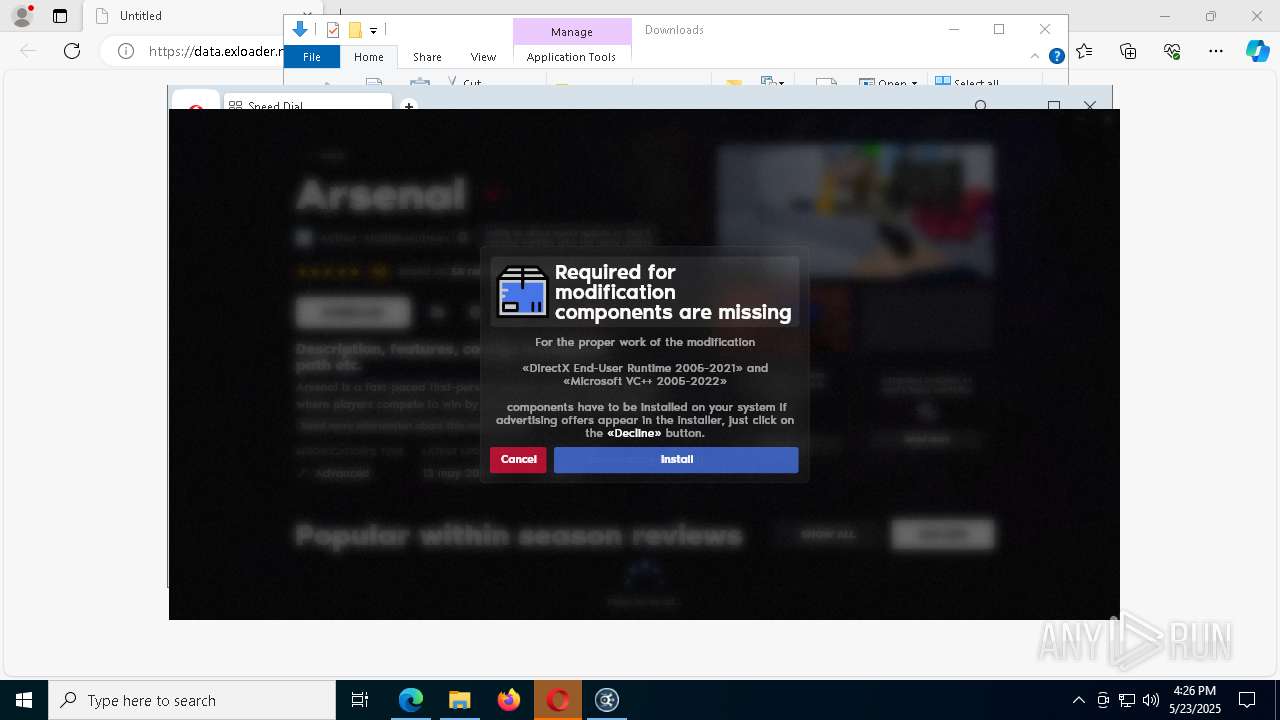
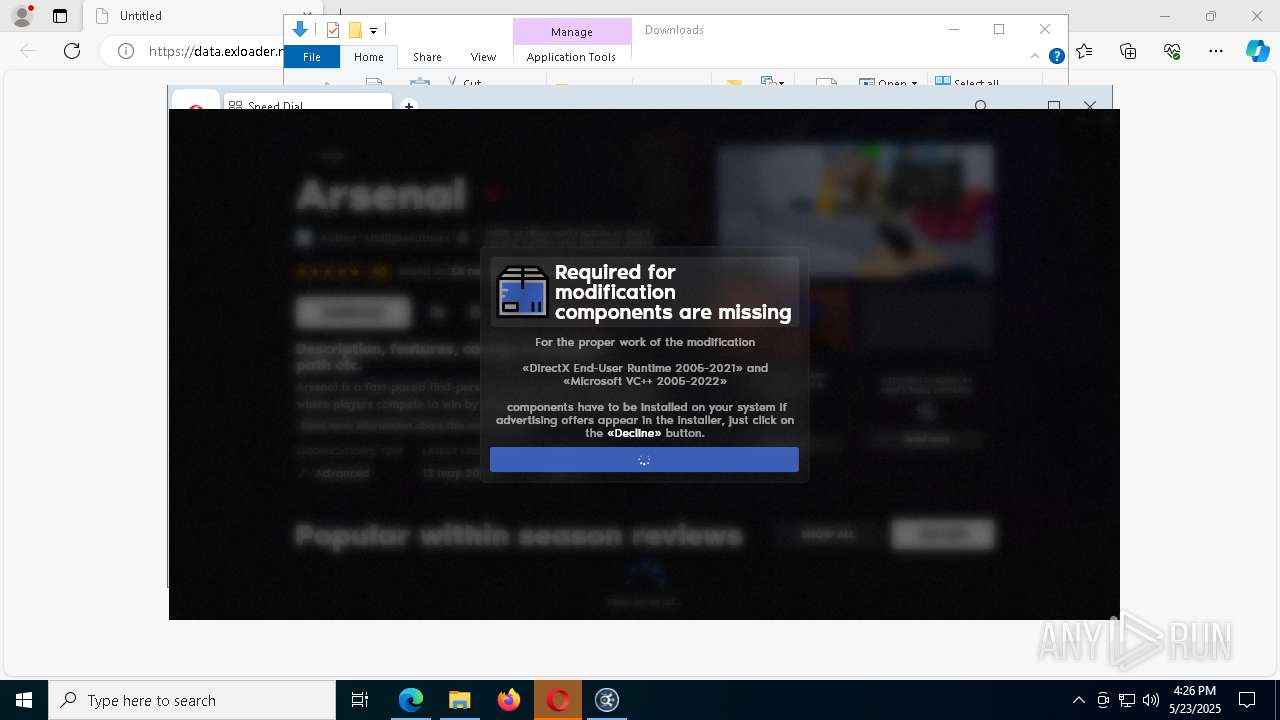
| URL: | https://data.exloader.net/ExLoader_Installer.exe |
| Full analysis: | https://app.any.run/tasks/231194bc-a772-4724-bc4c-be183c3bd182 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2025, 16:23:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6FD005CCEE3E0268FDCEA8275501F139 |
| SHA1: | 78A769A47369A03769EC4CDA0FF639AE0E3CA1A3 |
| SHA256: | AEF6DB8DFBB621976673C6638827FF60C8038EE54C8733E415B8C3E0A311CDFD |
| SSDEEP: | 3:N8ci0FAvEBySBXLNn:2cdjtXLN |
MALICIOUS
Changes Windows Defender settings
- ExLoader_Installer.exe (PID: 1812)
- ExLoader_Installer.exe (PID: 1012)
- configurationshubcomment.exe (PID: 7620)
Adds path to the Windows Defender exclusion list
- ExLoader_Installer.exe (PID: 1812)
- ExLoader_Installer.exe (PID: 1012)
- configurationshubcomment.exe (PID: 7620)
SUSPICIOUS
Executable content was dropped or overwritten
- ExLoader_Installer.exe (PID: 8060)
- OperaSetup.exe (PID: 1348)
- setup.exe (PID: 1532)
- setup.exe (PID: 1680)
- setup.exe (PID: 7804)
- setup.exe (PID: 7912)
- ExLoader_Installer.exe (PID: 8176)
- Assistant_118.0.5461.41_Setup.exe_sfx.exe (PID: 2332)
- ExLoader_Installer.exe (PID: 1012)
- setup.exe (PID: 4284)
- installer.exe (PID: 7768)
- installer.exe (PID: 2140)
- avast_free_antivirus_setup_online.exe (PID: 5452)
- assistant_installer.exe (PID: 1240)
- avast_free_antivirus_online_setup.exe (PID: 8472)
- icarus.exe (PID: 6728)
- icarus.exe (PID: 8660)
- ExLoader.exe (PID: 7396)
- installer.exe (PID: 9448)
- installer.exe (PID: 9408)
- ExLoader_Installer.exe (PID: 1812)
- opera_autoupdate.exe (PID: 9272)
- installer.exe (PID: 8480)
- configurationshubcomment.exe (PID: 7620)
- dxwebsetup.exe (PID: 2656)
- opera.exe (PID: 9888)
- dxwsetup.exe (PID: 9408)
- icarus.exe (PID: 8528)
- engsup.exe (PID: 4200)
- AvEmUpdate.exe (PID: 928)
- AvastSvc.exe (PID: 8424)
The process drops C-runtime libraries
- ExLoader_Installer.exe (PID: 8060)
- ExLoader_Installer.exe (PID: 1812)
- ExLoader_Installer.exe (PID: 8176)
- ExLoader_Installer.exe (PID: 1012)
- icarus.exe (PID: 8660)
- engsup.exe (PID: 4200)
Process drops legitimate windows executable
- ExLoader_Installer.exe (PID: 8060)
- ExLoader_Installer.exe (PID: 1812)
- ExLoader_Installer.exe (PID: 8176)
- Assistant_118.0.5461.41_Setup.exe_sfx.exe (PID: 2332)
- ExLoader_Installer.exe (PID: 1012)
- assistant_installer.exe (PID: 1240)
- icarus.exe (PID: 8660)
- configurationshubcomment.exe (PID: 7620)
- dxwebsetup.exe (PID: 2656)
- dxwsetup.exe (PID: 9408)
- engsup.exe (PID: 4200)
Starts POWERSHELL.EXE for commands execution
- ExLoader_Installer.exe (PID: 1812)
- ExLoader_Installer.exe (PID: 1012)
- configurationshubcomment.exe (PID: 7620)
Script adds exclusion path to Windows Defender
- ExLoader_Installer.exe (PID: 1812)
- ExLoader_Installer.exe (PID: 1012)
- configurationshubcomment.exe (PID: 7620)
Reads security settings of Internet Explorer
- ExLoader_Installer.exe (PID: 8060)
Reads the date of Windows installation
- ExLoader_Installer.exe (PID: 8060)
Connects to unusual port
- ExLoader_Installer.exe (PID: 1812)
- ExLoader_Installer.exe (PID: 1012)
- ExLoader.exe (PID: 7396)
- configurationshubcomment.exe (PID: 7620)
Checks for external IP
- svchost.exe (PID: 2196)
- ExLoader_Installer.exe (PID: 1812)
- avast_free_antivirus_setup_online.exe (PID: 5452)
- ExLoader_Installer.exe (PID: 1012)
- AvEmUpdate.exe (PID: 928)
- AvastSvc.exe (PID: 8424)
Starts itself from another location
- setup.exe (PID: 1532)
- icarus.exe (PID: 6728)
- ExLoader.exe (PID: 7396)
Application launched itself
- setup.exe (PID: 1532)
- setup.exe (PID: 7912)
- assistant_installer.exe (PID: 5360)
- installer.exe (PID: 7768)
- assistant_installer.exe (PID: 1240)
- assistant_installer.exe (PID: 1020)
- browser_assistant.exe (PID: 5608)
- opera.exe (PID: 5096)
- opera.exe (PID: 8784)
- installer.exe (PID: 9408)
- opera_autoupdate.exe (PID: 9632)
- opera_autoupdate.exe (PID: 9272)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 1532)
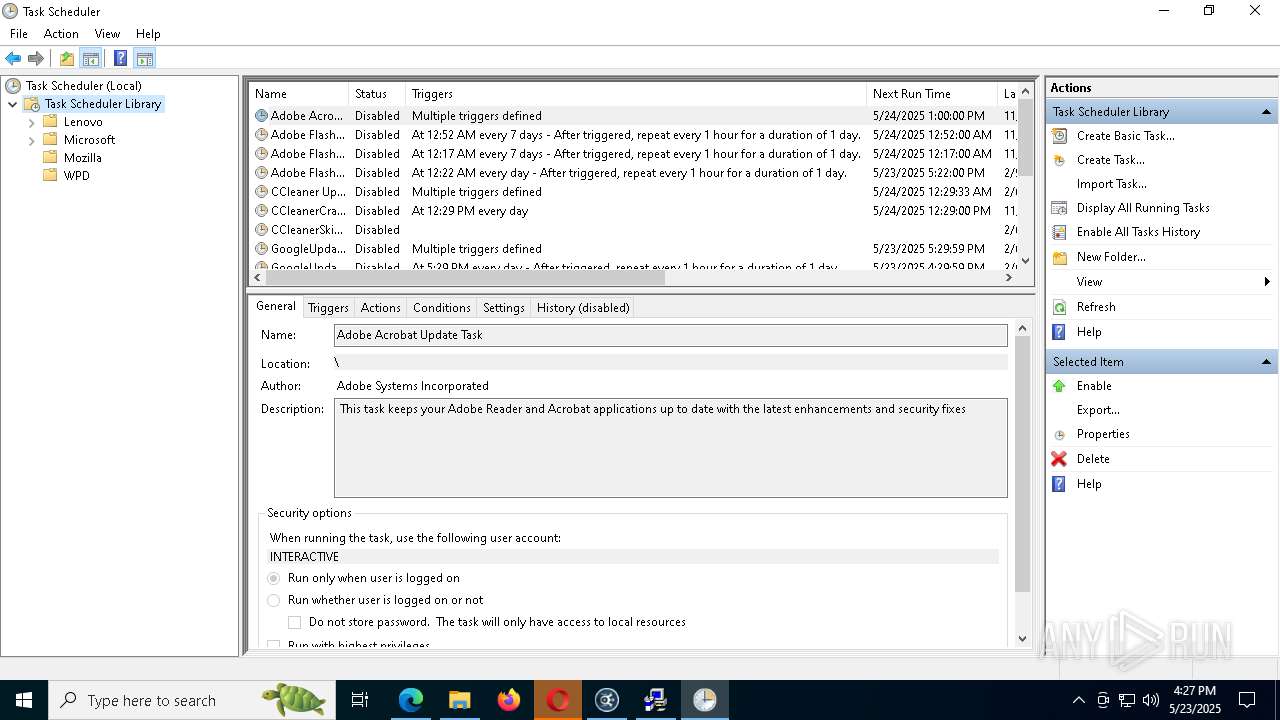
The process executes via Task Scheduler
- opera_autoupdate.exe (PID: 9272)
Starts CMD.EXE for commands execution
- configurationshubcomment.exe (PID: 7620)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 9716)
- cmd.exe (PID: 10144)
The executable file from the user directory is run by the CMD process
- dxwebsetup.exe (PID: 2656)
Drops a system driver (possible attempt to evade defenses)
- icarus.exe (PID: 8660)
- engsup.exe (PID: 4200)
Starts a Microsoft application from unusual location
- dxwsetup.exe (PID: 9408)
Executes as Windows Service
- wsc_proxy.exe (PID: 7828)
- VSSVC.exe (PID: 5892)
- afwServ.exe (PID: 9596)
- AvastSvc.exe (PID: 8424)
- aswidsagent.exe (PID: 10440)
- aswToolsSvc.exe (PID: 4748)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 7356)
- msedge.exe (PID: 4268)
Reads Environment values
- identity_helper.exe (PID: 2504)
Checks supported languages
- identity_helper.exe (PID: 2504)
- ExLoader_Installer.exe (PID: 8060)
- ExLoader_Installer.exe (PID: 1812)
Application launched itself
- msedge.exe (PID: 4268)
Reads the computer name
- identity_helper.exe (PID: 2504)
- ExLoader_Installer.exe (PID: 8060)
- ExLoader_Installer.exe (PID: 1812)
Manual execution by a user
- ExLoader_Installer.exe (PID: 8060)
- ExLoader_Installer.exe (PID: 8176)
- assistant_installer.exe (PID: 1020)
- opera.exe (PID: 8784)
- mmc.exe (PID: 8380)
- mmc.exe (PID: 10188)
Create files in a temporary directory
- ExLoader_Installer.exe (PID: 8060)
- powershell.exe (PID: 732)
The sample compiled with english language support
- ExLoader_Installer.exe (PID: 8060)
- ExLoader_Installer.exe (PID: 1812)
- OperaSetup.exe (PID: 1348)
- setup.exe (PID: 1532)
- setup.exe (PID: 1680)
- setup.exe (PID: 7804)
- setup.exe (PID: 7912)
- ExLoader_Installer.exe (PID: 8176)
- Assistant_118.0.5461.41_Setup.exe_sfx.exe (PID: 2332)
- ExLoader_Installer.exe (PID: 1012)
- setup.exe (PID: 4284)
- installer.exe (PID: 7768)
- assistant_installer.exe (PID: 1240)
- installer.exe (PID: 2140)
- avast_free_antivirus_online_setup.exe (PID: 8472)
- icarus.exe (PID: 6728)
- icarus.exe (PID: 8660)
- ExLoader.exe (PID: 7396)
- avast_free_antivirus_setup_online.exe (PID: 5452)
- installer.exe (PID: 9448)
- installer.exe (PID: 9408)
- installer.exe (PID: 8480)
- configurationshubcomment.exe (PID: 7620)
- opera_autoupdate.exe (PID: 9272)
- dxwebsetup.exe (PID: 2656)
- dxwsetup.exe (PID: 9408)
- icarus.exe (PID: 8528)
- opera.exe (PID: 9888)
- engsup.exe (PID: 4200)
- AvEmUpdate.exe (PID: 928)
- AvastSvc.exe (PID: 8424)
Creates files in the program directory
- ExLoader_Installer.exe (PID: 1812)
Reads the software policy settings
- powershell.exe (PID: 732)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6436)
Process checks computer location settings
- ExLoader_Installer.exe (PID: 8060)
- ExLoader_Installer.exe (PID: 1812)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6436)
Reads security settings of Internet Explorer
- powershell.exe (PID: 732)
The sample compiled with czech language support
- icarus.exe (PID: 8660)
Manages system restore points
- SrTasks.exe (PID: 3080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
372
Monitored processes
226
Malicious processes
15
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2444 --field-trial-handle=2304,i,1093347199380152043,2432316473658972493,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 456 | "C:\Users\admin\AppData\Local\Programs\Opera\opera.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --enable-quic --no-pre-read-main-dll --with-feature:cashback-assistant=on --with-feature:address-bar-dropdown-autocompleted-domains=on --with-feature:address-bar-dropdown-cities=on --with-feature:address-bar-dropdown-keyword-ads=on --with-feature:address-bar-keywords-monetization=on --with-feature:ai-tab-management=on --with-feature:ai-writing-mode-in-context-menu=on --with-feature:amazon-bookmarks-tags-update=on --with-feature:amp-requests-stats=on --with-feature:aria-in-tab-view=on --with-feature:bluesky-in-sidebar=on --with-feature:cashback-assistant=on --with-feature:continue-on-booking=on --with-feature:continue-on-shopping-via-amp=off --with-feature:continue-shopping=on --with-feature:continue-shopping-2=on --with-feature:continue-shopping-amazon-us-associates=off --with-feature:continue-shopping-explore=off --with-feature:continue-shopping-structured-partners=on --with-feature:discord-in-sidebar=on --with-feature:feature-remote-disable-updates-testing-flag=off --with-feature:feature-remote-updates-testing-flag=on --with-feature:hide-navigations-from-extensions=on --with-feature:keywords-from-backend=off --with-feature:native-crypto-wallet=on --with-feature:opera-startpage-special=on --with-feature:proxy-switcher-ui-default-visible=on --with-feature:realtime-impressions-reporting=on --with-feature:run-at-startup-default=on --with-feature:sd-suggestions-external=on --with-feature:shopping-corner=on --with-feature:sitecheck-age=on --with-feature:slack-in-sidebar=on --with-feature:specific-keywords=on --with-feature:startpage-opening-animation=off --with-feature:startpage-sync-banner=on --with-feature:translator=on --with-feature:installer-experiment-test=off --field-trial-handle=1928,i,16167012787344296420,14225943906659409295,262144 --disable-features=CertificateTransparencyAskBeforeEnabling,PlatformSoftwareH264EncoderInGpu,UpdatableKeyPins --variations-seed-version --mojo-platform-channel-handle=7256 /prefetch:8 | C:\Users\admin\AppData\Local\Programs\Opera\opera.exe | — | opera.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: LOW Description: Opera Internet Browser Exit code: 0 Version: 119.0.5497.40 Modules
| |||||||||||||||
| 536 | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -command Add-MpPreference -ExclusionPath "\"C:\Users\admin\AppData\Local\Temp\"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ExLoader_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe -command "$WshShell = New-Object -comObject WScript.Shell $Shortcut = $WshShell.CreateShortcut(\"c:\users\admin\desktop\ExLoader.lnk\") $Shortcut.TargetPath = \"C:\Program Files\ExLoader\ExLoader.exe\" $Shortcut.Save()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ExLoader_Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --no-appcompat-clear --mojo-platform-channel-handle=6556 --field-trial-handle=2304,i,1093347199380152043,2432316473658972493,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 872 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=2832 --field-trial-handle=2304,i,1093347199380152043,2432316473658972493,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 924 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6496 --field-trial-handle=2304,i,1093347199380152043,2432316473658972493,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Avast Software\Avast\AvEmUpdate.exe" /installer | C:\Program Files\Avast Software\Avast\AvEmUpdate.exe | icarus.exe | ||||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: Avast Emergency Update Exit code: 0 Version: 25.4.10068.0 Modules
| |||||||||||||||
| 1012 | "C:\Users\admin\AppData\Local\Temp\RarSFX1\ExLoader_Installer.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX1\ExLoader_Installer.exe | ExLoader_Installer.exe | ||||||||||||
User: admin Company: com.swiftsoft Integrity Level: HIGH Description: Installer for unified library of in-game modifications. Exit code: 0 Version: 1.8.10+1611 Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\AppData\Local\Programs\Opera\assistant\assistant_installer.exe" --installfolder="C:\Users\admin\AppData\Local\Programs\Opera\assistant" --run-assistant --allusers=0 | C:\Users\admin\AppData\Local\Programs\Opera\assistant\assistant_installer.exe | — | explorer.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Browser Assistant Installer Exit code: 0 Version: 118.0.5461.41 Modules
| |||||||||||||||
Total events
346 848
Read events
345 079
Write events
1 621
Delete events
148
Modification events
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E3A6574D66942F00 | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 696E634D66942F00 | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197234 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F82CFEBF-14A0-4F87-A238-6FFA7C1EA912} | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197234 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {44D3F6A4-2164-49A7-9DDC-03E6EBA4B2AE} | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 82D38D4D66942F00 | |||
| (PID) Process: | (4268) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
933
Suspicious files
3 029
Text files
1 704
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10aa6b.TMP | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10aa6b.TMP | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10aa7a.TMP | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10aad8.TMP | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10ab17.TMP | — | |
MD5:— | SHA256:— | |||
| 4268 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF10ab17.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
266
TCP/UDP connections
328
DNS requests
355
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3100 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3100 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1532 | setup.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
1532 | setup.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEA17ZgsSl63KHstWnAbUez0%3D | unknown | — | — | whitelisted |
1532 | setup.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAsA6S1NbXMfyjBZx8seGIY%3D | unknown | — | — | whitelisted |
1532 | setup.exe | GET | 200 | 142.250.184.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
1532 | setup.exe | GET | 200 | 142.250.184.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6816 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4268 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7356 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7356 | msedge.exe | 172.67.22.232:443 | data.exloader.net | CLOUDFLARENET | US | unknown |
7356 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
data.exloader.net |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1812 | ExLoader_Installer.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (ipapi .co in DNS lookup) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (ipapi .co in DNS lookup) |
1012 | ExLoader_Installer.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
5452 | avast_free_antivirus_setup_online.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
AvastSvc.exe | [2025-05-23 16:27:59.863] [error ] [dnsdoh ] [ 8424:10388] [131A00: 73] failed to restore usage statistics
Exception: corrupted file
|
AvastSvc.exe | [2025-05-23 16:28:00.715] [error ] [tasks ] [ 8424: 8112] [554EF0: 412] task Burger::EventConsumer::OnFlush: failed without a caller check.
Exception: Identity of Burger client was not set.
|
AvastSvc.exe | [2025-05-23 16:28:00.751] [error ] [JsonComms ] [ 8424:10308] [113BC3: 163] app.fwserv.reporting_get request failed (dwResult = 1653)
|
AvastSvc.exe | [2025-05-23 16:28:00.758] [error ] [gui_cache ] [ 8424:10732] [7CCDBE: 952] failed to update shepherd
|
AvastSvc.exe | [2025-05-23 16:28:01.106] [info ] [nsf_urlinfo] [ 8424:10388] [6706BC: 39] Initialize UrlInfoMgr
|
AvastSvc.exe | [2025-05-23 16:28:01.105] [info ] [nsf_urlinfo] [ 8424:10388] [83C6A9: 46] Starting UrlInfo
|
AvastSvc.exe | [2025-05-23 16:28:01.121] [info ] [nsf_urlinfo] [ 8424:10388] [6706BC: 72] UrlInfoMgr initialized
|
AvastSvc.exe | [2025-05-23 16:28:20.833] [error ] [gui_cache ] [ 8424:10732] [7CCDBE: 952] failed to update shepherd
|