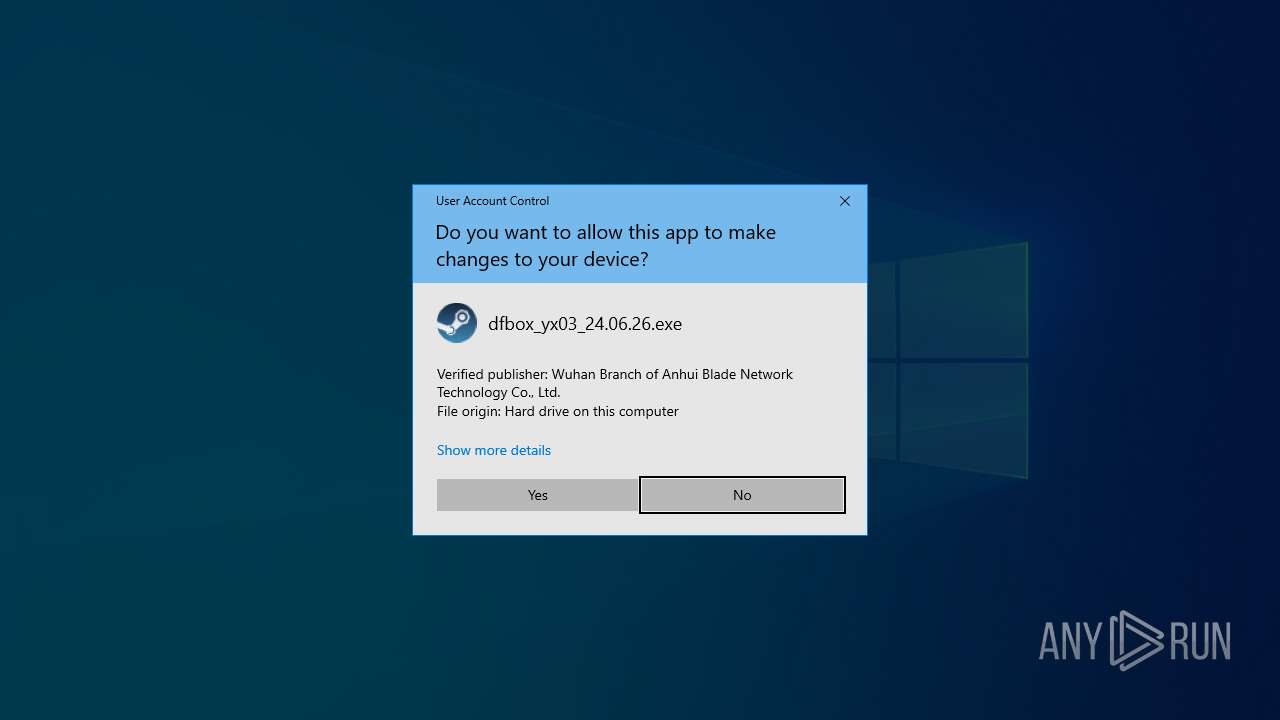
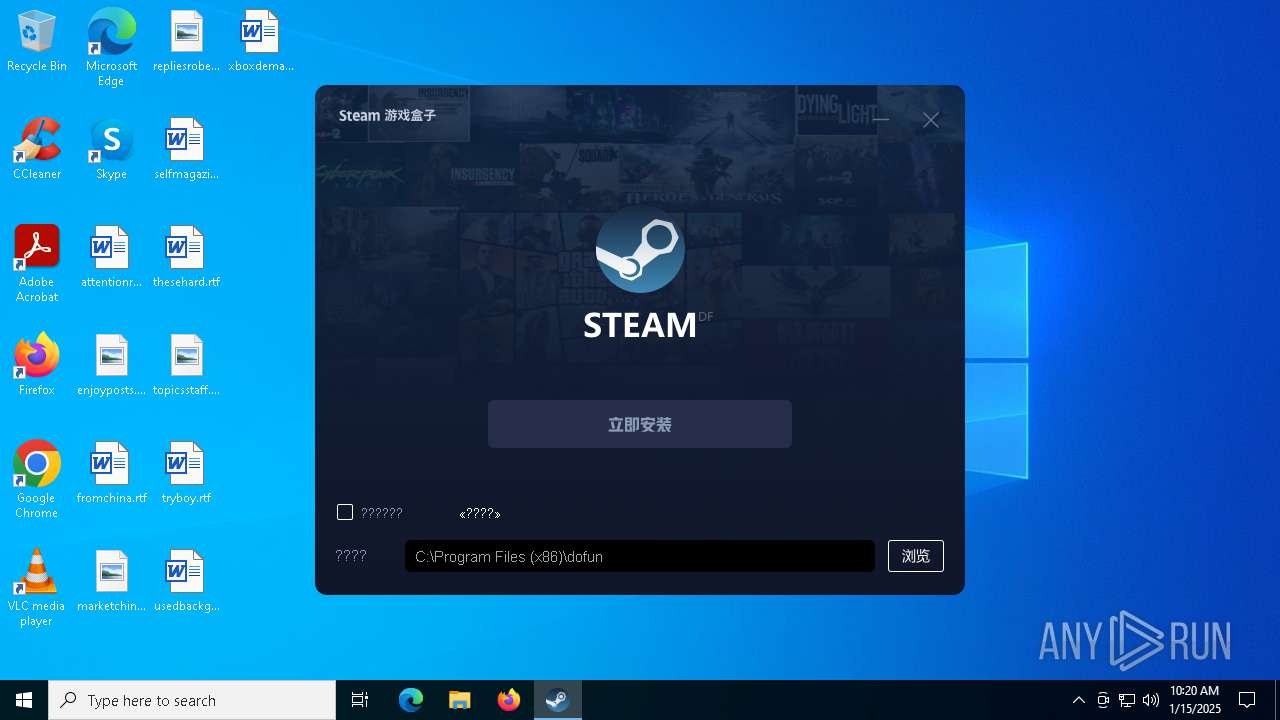
| File name: | dfbox_yx03_24.06.26.exe |
| Full analysis: | https://app.any.run/tasks/42631bf8-0d27-489e-9ee2-3215e4f63f55 |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2025, 10:20:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 5D44913A4E27B440D4CD867713D2CBF6 |
| SHA1: | 80BDD11F20F304B2017F65D486911DFC6CCB963C |
| SHA256: | AEA6391AD35D83D7871B82EA10D59CC470CD79DC44143D7D8172C183C4BD22E0 |
| SSDEEP: | 98304:pD19DlBMq71K4KrWNhQlWo6OU+IZUxYNF2lqd00CNDRwQXmtOI41xnv+rapDFAN7:C02CEs |
MALICIOUS
Adds path to the Windows Defender exclusion list
- dfbox_yx03_24.06.26.exe (PID: 7032)
SUSPICIOUS
The process hide an interactive prompt from the user
- dfbox_yx03_24.06.26.exe (PID: 7032)
Mutex name with non-standard characters
- dfbox_yx03_24.06.26.exe (PID: 7032)
Starts POWERSHELL.EXE for commands execution
- dfbox_yx03_24.06.26.exe (PID: 7032)
Executable content was dropped or overwritten
- dfbox_yx03_24.06.26.exe (PID: 7032)
Script adds exclusion path to Windows Defender
- dfbox_yx03_24.06.26.exe (PID: 7032)
INFO
Creates files in the program directory
- dfbox_yx03_24.06.26.exe (PID: 7032)
Reads the computer name
- dfbox_yx03_24.06.26.exe (PID: 7032)
Checks supported languages
- dfbox_yx03_24.06.26.exe (PID: 7032)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7088)
The process uses the downloaded file
- powershell.exe (PID: 7088)
Create files in a temporary directory
- dfbox_yx03_24.06.26.exe (PID: 7032)
The sample compiled with chinese language support
- dfbox_yx03_24.06.26.exe (PID: 7032)
The sample compiled with english language support
- dfbox_yx03_24.06.26.exe (PID: 7032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:27 09:11:45+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.28 |
| CodeSize: | 3772416 |
| InitializedDataSize: | 1099776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x342aa0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
128
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6496 | "C:\Users\admin\AppData\Local\Temp\dfbox_yx03_24.06.26.exe" | C:\Users\admin\AppData\Local\Temp\dfbox_yx03_24.06.26.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7032 | "C:\Users\admin\AppData\Local\Temp\dfbox_yx03_24.06.26.exe" | C:\Users\admin\AppData\Local\Temp\dfbox_yx03_24.06.26.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 7088 | powershell -inputformat none -outputformat none -NonInteractive -Command "Add-MpPreference -ExclusionPath 'C:\Program Files (x86)\dofun\yx03'" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | dfbox_yx03_24.06.26.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 522
Read events
5 522
Write events
0
Delete events
0
Modification events
Executable files
51
Suspicious files
58
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jxzfvylq.p2x.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7088 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:342B1ACD9A2DD41B301707BF74333CF9 | SHA256:49625CB31374DF5B8284F052EAAACD9E8C1D7940402DC1B17383666A911D1E89 | |||
| 7032 | dfbox_yx03_24.06.26.exe | C:\Users\admin\AppData\Local\Temp\df\steamlauncher.exe | executable | |
MD5:BB8E5913C84E65F0DE7ED252FFE4C5DD | SHA256:BF9DEE4EC27794BF826EC11D936C66B442B73ECDFD6FD888D6F6463A67DCE27B | |||
| 7032 | dfbox_yx03_24.06.26.exe | C:\Users\admin\AppData\Local\Temp\df\zlibwapi.dll | compressed | |
MD5:FF000CC9C68A61E6D376BE2090C1CD89 | SHA256:1D2951435BBE15309577B84149BAB1792492AEB458E778AF975656324196460F | |||
| 7088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mxambdnz.nmc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7032 | dfbox_yx03_24.06.26.exe | C:\Users\admin\AppData\Local\Temp\df\zlibwapi.dll.tmp | executable | |
MD5:FC361FC06DB5909F9FA44486D304A769 | SHA256:1C5FEF2229D73B6E19BC3CC9A5D0FFB1D7F777EC198AA80B4A592AFEFEE312A9 | |||
| 7088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lifceqbl.vet.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7032 | dfbox_yx03_24.06.26.exe | C:\Users\admin\AppData\Local\Temp\df\temp\zlib.dll.tmp | executable | |
MD5:E6A9D06F099392E66BF7723B7411A52C | SHA256:666202BF511D4B283152B5E9CFA02FD20BB4055EE731167C5735E6E339C76823 | |||
| 7032 | dfbox_yx03_24.06.26.exe | C:\Users\admin\AppData\Local\Temp\df\temp\zlibwapi.dll.tmp | executable | |
MD5:FC361FC06DB5909F9FA44486D304A769 | SHA256:1C5FEF2229D73B6E19BC3CC9A5D0FFB1D7F777EC198AA80B4A592AFEFEE312A9 | |||
| 7032 | dfbox_yx03_24.06.26.exe | C:\Users\admin\AppData\Local\Temp\df\zip.dll.tmp | executable | |
MD5:62A737469595B6922DAF7DB0CD8A3E06 | SHA256:92A16ED6F94BB89FC0D3B8C02953B99AB1120E5B068DB908C8481D5EA1AD9A31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
39
DNS requests
22
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6260 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7032 | dfbox_yx03_24.06.26.exe | POST | 200 | 39.105.192.231:80 | http://client.88gog.com/api/user/public/client/channel/resource | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.114:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.114:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.227.202:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download.88gog.com |
| unknown |
client.88gog.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
7032 | dfbox_yx03_24.06.26.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
1 ETPRO signatures available at the full report