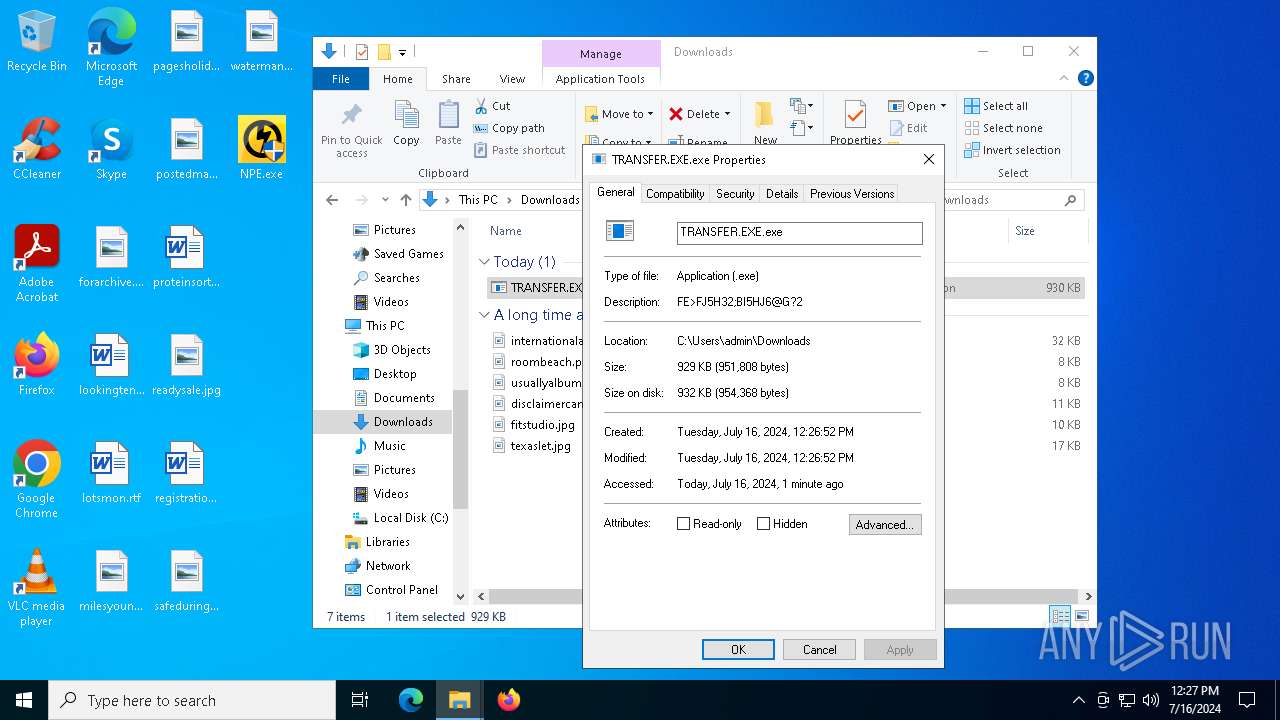
| File name: | TRANSFER.EXE |
| Full analysis: | https://app.any.run/tasks/2b5061ff-0923-4264-86ec-002cc79978c5 |
| Verdict: | Malicious activity |
| Analysis date: | July 16, 2024, 12:26:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | E12879DEBDCCA74CAFC2EA315FC9C67F |
| SHA1: | F6F838F06BFC88FD4C3C72D5707986A4E6004CEA |
| SHA256: | AEA48D054D3C5D517A680E92DEA37A34B84543C343EC9227B6B637A1DCC74E91 |
| SSDEEP: | 24576:WwHeBPwakitMvlMam53l1a8xmNXxEBx2k2zeeTlxuo/+b:VHeBPwakitMvlMam53l1a8xmJxEBx2kR |
MALICIOUS
Drops the executable file immediately after the start
- TRANSFER.EXE.exe (PID: 6272)
- NPE.exe (PID: 6380)
Creates a writable file in the system directory
- NPE.exe (PID: 6380)
SUSPICIOUS
Reads security settings of Internet Explorer
- NPE.exe (PID: 6380)
Drops a system driver (possible attempt to evade defenses)
- NPE.exe (PID: 6380)
Creates files in the driver directory
- NPE.exe (PID: 6380)
Executable content was dropped or overwritten
- NPE.exe (PID: 6380)
Checks for external IP
- InstallUtil.exe (PID: 2060)
INFO
Reads the computer name
- TRANSFER.EXE.exe (PID: 6272)
- NPE.exe (PID: 6380)
- InstallUtil.exe (PID: 2060)
Checks supported languages
- NPE.exe (PID: 6380)
- TRANSFER.EXE.exe (PID: 6272)
- InstallUtil.exe (PID: 2060)
Creates files or folders in the user directory
- NPE.exe (PID: 6380)
Reads the machine GUID from the registry
- NPE.exe (PID: 6380)
- InstallUtil.exe (PID: 2060)
- TRANSFER.EXE.exe (PID: 6272)
Reads the software policy settings
- NPE.exe (PID: 6380)
- InstallUtil.exe (PID: 2060)
Creates files in the program directory
- NPE.exe (PID: 6380)
Reads product name
- NPE.exe (PID: 6380)
Reads Environment values
- InstallUtil.exe (PID: 2060)
- NPE.exe (PID: 6380)
Checks proxy server information
- NPE.exe (PID: 6380)
- InstallUtil.exe (PID: 2060)
Disables trace logs
- InstallUtil.exe (PID: 2060)
Manual execution by a user
- NPE.exe (PID: 2708)
- NPE.exe (PID: 6380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1978:09:03 00:51:17+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 949248 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe99fe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.13.18.22 |
| ProductVersionNumber: | 9.13.18.22 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | 9FI83;>G7EF8H2:BB?I< |
| CompanyName: | >56875A?4=7H6<3C47IBEDH |
| FileDescription: | FE>FJ5H32;BI5HJ6@G?2 |
| FileVersion: | 9.13.18.22 |
| InternalName: | Transfer Copy.exe |
| LegalCopyright: | Copyright © 2016 >56875A?4=7H6<3C47IBEDH |
| OriginalFileName: | Transfer Copy.exe |
| ProductName: | FE>FJ5H32;BI5HJ6@G?2 |
| ProductVersion: | 9.13.18.22 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
142
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2060 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | TRANSFER.EXE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
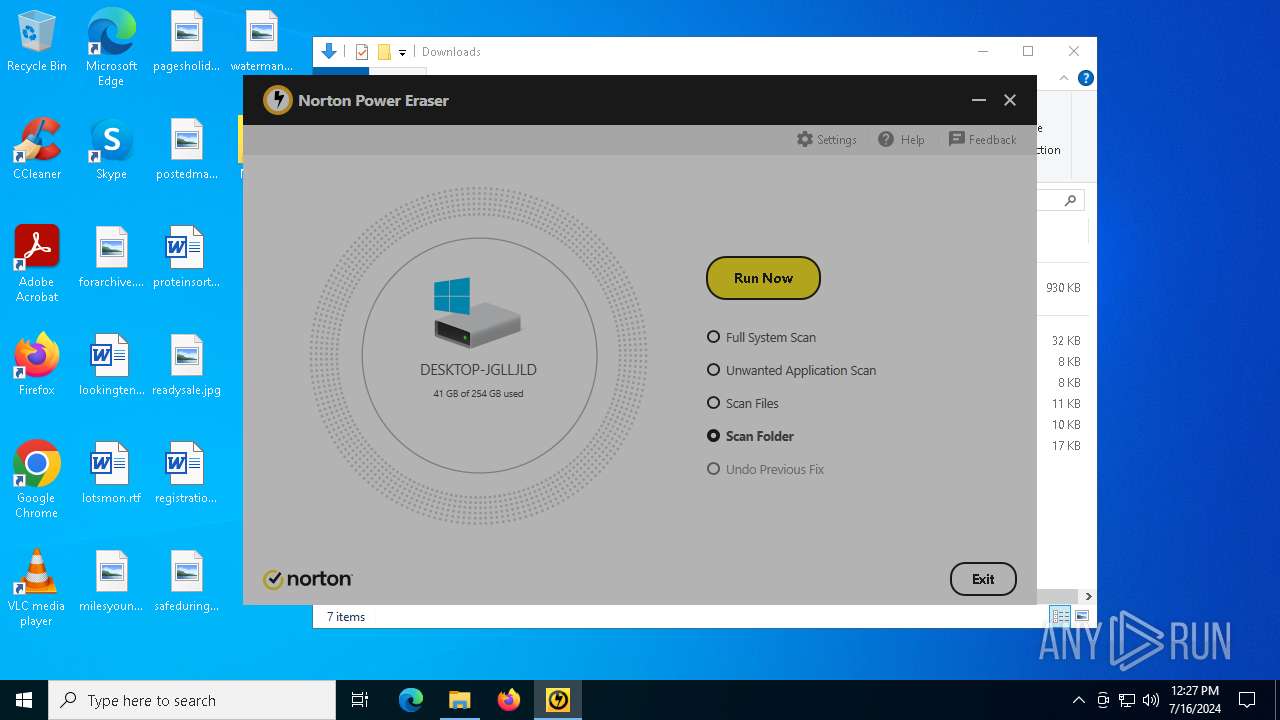
| 2708 | "C:\Users\admin\Desktop\NPE.exe" | C:\Users\admin\Desktop\NPE.exe | — | explorer.exe | |||||||||||
User: admin Company: NortonLifeLock Inc. Integrity Level: MEDIUM Description: Norton Power Eraser Exit code: 3221226540 Version: 6.6.0.2153 Modules
| |||||||||||||||
| 4448 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | "C:\Users\admin\Downloads\TRANSFER.EXE.exe" | C:\Users\admin\Downloads\TRANSFER.EXE.exe | — | explorer.exe | |||||||||||
User: admin Company: >56875A?4=7H6<3C47IBEDH Integrity Level: MEDIUM Description: FE>FJ5H32;BI5HJ6@G?2 Version: 9.13.18.22 Modules
| |||||||||||||||
| 6380 | "C:\Users\admin\Desktop\NPE.exe" | C:\Users\admin\Desktop\NPE.exe | explorer.exe | ||||||||||||
User: admin Company: NortonLifeLock Inc. Integrity Level: HIGH Description: Norton Power Eraser Version: 6.6.0.2153 Modules
| |||||||||||||||
| 6680 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6704 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 085
Read events
10 982
Write events
99
Delete events
4
Modification events
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps\NPE.exe |
| Operation: | write | Name: | DumpType |
Value: 0 | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps\NPE.exe |
| Operation: | write | Name: | DumpCount |
Value: 4 | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps\NPE.exe |
| Operation: | write | Name: | DumpFlags |
Value: 0 | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\LocalDumps\NPE.exe |
| Operation: | write | Name: | DumpFolder |
Value: C:\Users\admin\AppData\Local\NPE\LocalDumps | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\WMI\Autologger\NPETraceSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E000000000000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000500000000000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (6380) NPE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6380 | NPE.exe | C:\ProgramData\Norton\NPE\NPEsettings.dat.log | binary | |
MD5:E93F257844761964F1B5EAA6B1655A5C | SHA256:FE0049308C49BD527521EF3083F1885E219F187ABACEFC797B7735660F1EC0F8 | |||
| 6380 | NPE.exe | C:\Users\admin\AppData\Local\NPE\ErrMgmt\SQCLIENT.dat | binary | |
MD5:CC2B0E03038DE107ACC56A9A1880B4BE | SHA256:BDB39C942686F84584CF1764A05480DE47CE50B867436095EF12155A5412A0F8 | |||
| 6380 | NPE.exe | C:\Users\admin\AppData\Local\NPE\ErrMgmt\SQCLIENT.dat.log | abr | |
MD5:6D83F9A8767590553954972293ABBD5B | SHA256:236581906522EF2FC12370E585A49B8716F2A736ED3B9F5C82D5B1F1A83ABB41 | |||
| 6380 | NPE.exe | C:\WINDOWS\System32\drivers\SMR540.SYS | executable | |
MD5:836BF59E8E3F6BBA0BD958B63FC3A6A2 | SHA256:48C18955D0BB46AAF2F95B31CD5F34478DB9E3A25B7600BC3F1DDC43241C0A5E | |||
| 6380 | NPE.exe | C:\WINDOWS\TEMP\FB7A7A2B.tmp | binary | |
MD5:DC4EE428EB6DC11F0955C66E92F85779 | SHA256:7BBF1547FA62E5B93F0F0F1F172FBC1BC2804EAAC81E2F486FDCF2F22B2E1B70 | |||
| 6380 | NPE.exe | C:\ProgramData\Norton\NPE\NPEsettings.dat | binary | |
MD5:FC37525B224BCB336F39926D2356FE1D | SHA256:1ADAC96ABE6BD4141934F3EB98F89B01724804038B57BAE926C34F4B085C38B7 | |||
| 6380 | NPE.exe | C:\ProgramData\Norton\{086A63F0-6B13-4F29-9695-134E7A01E963}\LC.INI | text | |
MD5:1028F278A81D9795DA3C6A70463730FD | SHA256:302B4E7C6A73838E1BDDAE580CA0491A8E8AC5FC51D69E960BF8C4C8986C9D7F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
87
DNS requests
32
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2052 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2052 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2212 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2848 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2848 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3596 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5988 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2060 | InstallUtil.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.171:443 | — | Akamai International B.V. | GB | unknown |
2064 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
900 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 2.23.209.171:443 | — | Akamai International B.V. | GB | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2052 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2052 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2060 | InstallUtil.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2168 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2060 | InstallUtil.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2060 | InstallUtil.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
Process | Message |
|---|---|
NPE.exe | Information at updateCurrentLangCode (res:main_frame.tis(714))
main_frame.tis : 'updateCurrentLangCode' called
|
NPE.exe | Information at updatePageDirection (res:main_frame.tis(753))
main_frame.tis : 'updatePageDirection' called
|
NPE.exe | Information at updateProductName (res:main_frame.tis(761))
main_frame.tis : 'updateProductName' called
|
NPE.exe | Information at self.ready (res:main_frame.tis(13))
'main_frame.tis' loaded
|
NPE.exe | Information at showEulaPage (res:main_frame.tis(146))
'showEulaPage()' called
|
NPE.exe | Information at loadFrameContent (res:main_frame.tis(33))
'loadFrameContent(eula)' called
|
NPE.exe | Information at self.ready (res:eula.tis(8))
'eula.tis' loaded
|
NPE.exe | Information at setup (res:eula.tis(16))
'eula.tis: setup()' called
|
NPE.exe | Information at setup (res:eula.tis(22))
Initial Language ID: 1033
|
NPE.exe | Information at assignEULA (res:eula.tis(79))
Assigning Language ID: 1033
|