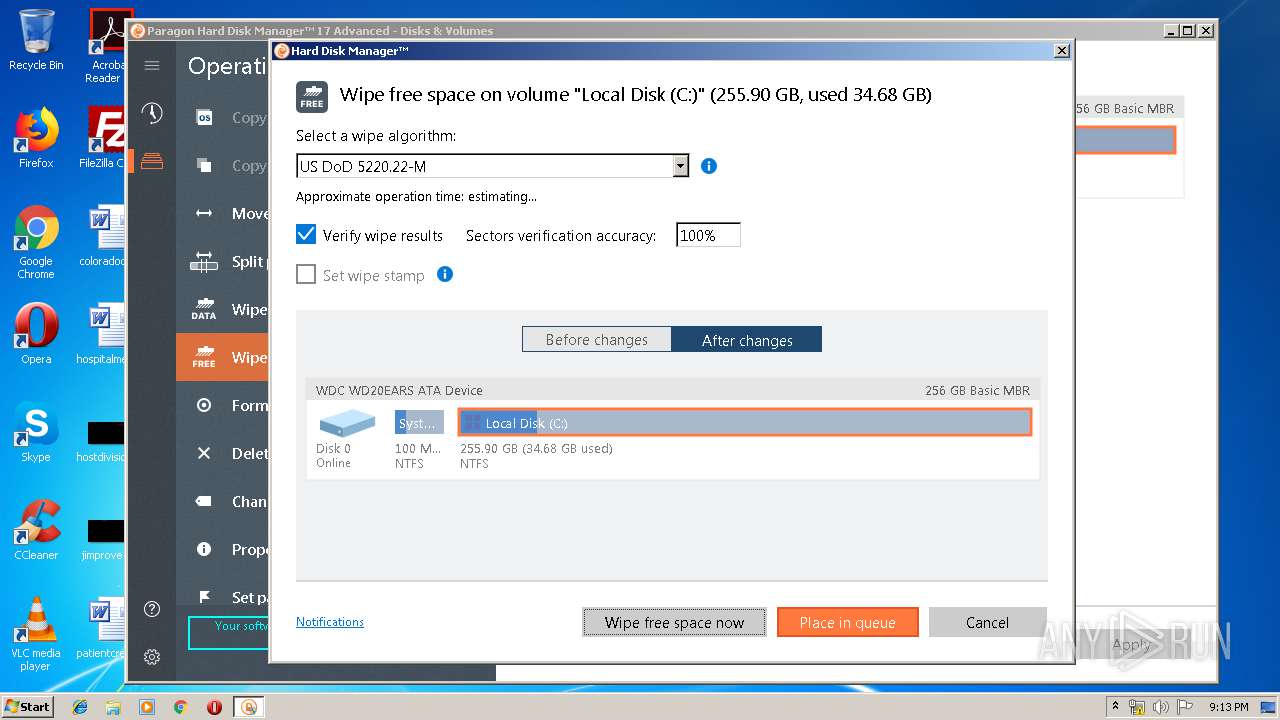
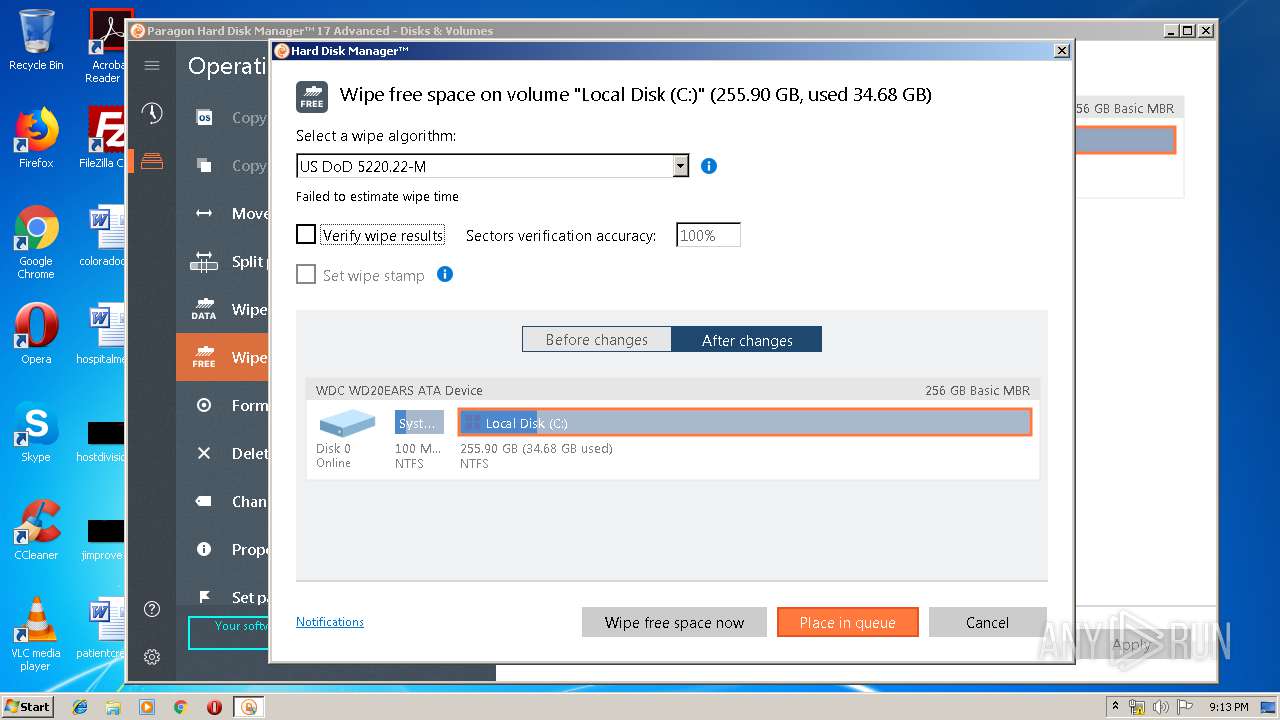
| URL: | https://dl.paragon-software.com/esd/795_PEU/17.10.12/hdm17advanced_x86_trial.exe |
| Full analysis: | https://app.any.run/tasks/181eea2a-f8b7-4503-af41-40e9a6595700 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2020, 21:09:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6C74EF29835A0177232A72FBDF21D9F1 |
| SHA1: | DE849C1944F6FF66D709812041079FF0191948A2 |
| SHA256: | AE9877557402EE3548E000BDDCFFD2CD958EE35B36161613C5D45364978437EF |
| SSDEEP: | 3:N8RSXeHFwGJu+KNrYcSMO4An:2+PGzjvN |
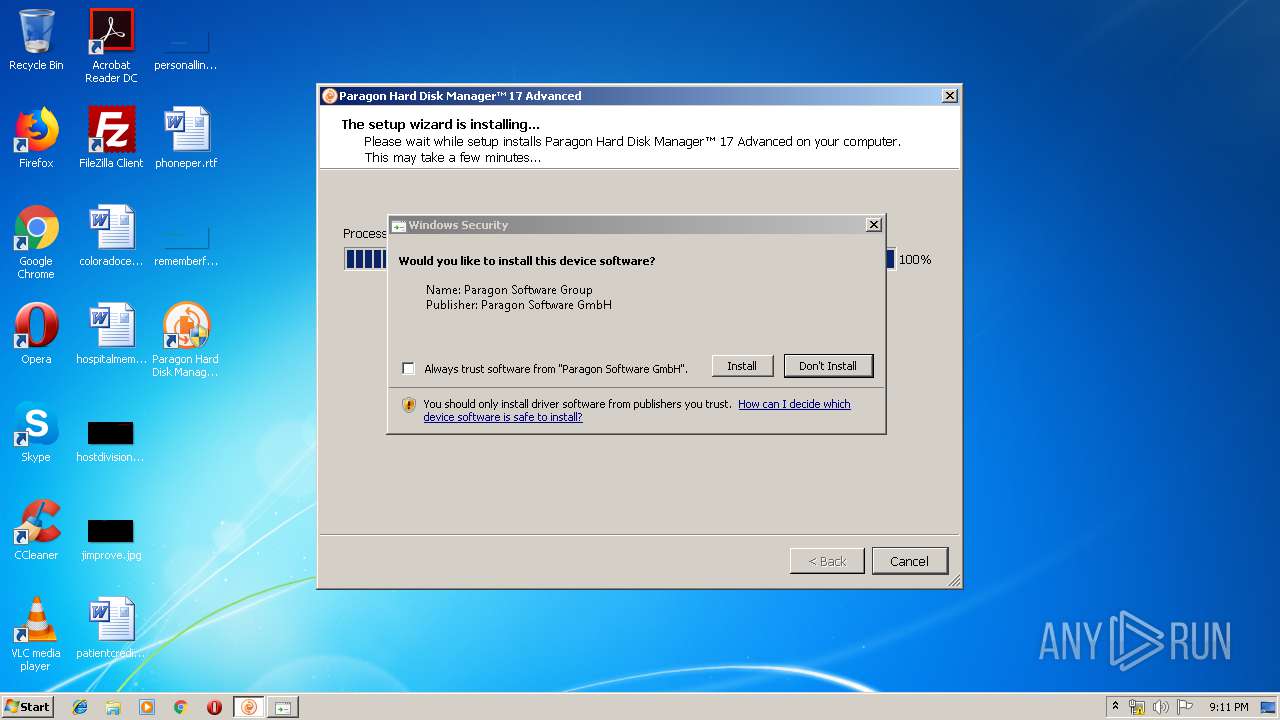
MALICIOUS
Application was dropped or rewritten from another process
- hdm17advanced_x86_trial.exe (PID: 2124)
- hdm17advanced_x86_trial.exe (PID: 2304)
- hdm17advanced_x86_trial.exe (PID: 2028)
- hdm17advanced_x86.exe (PID: 3308)
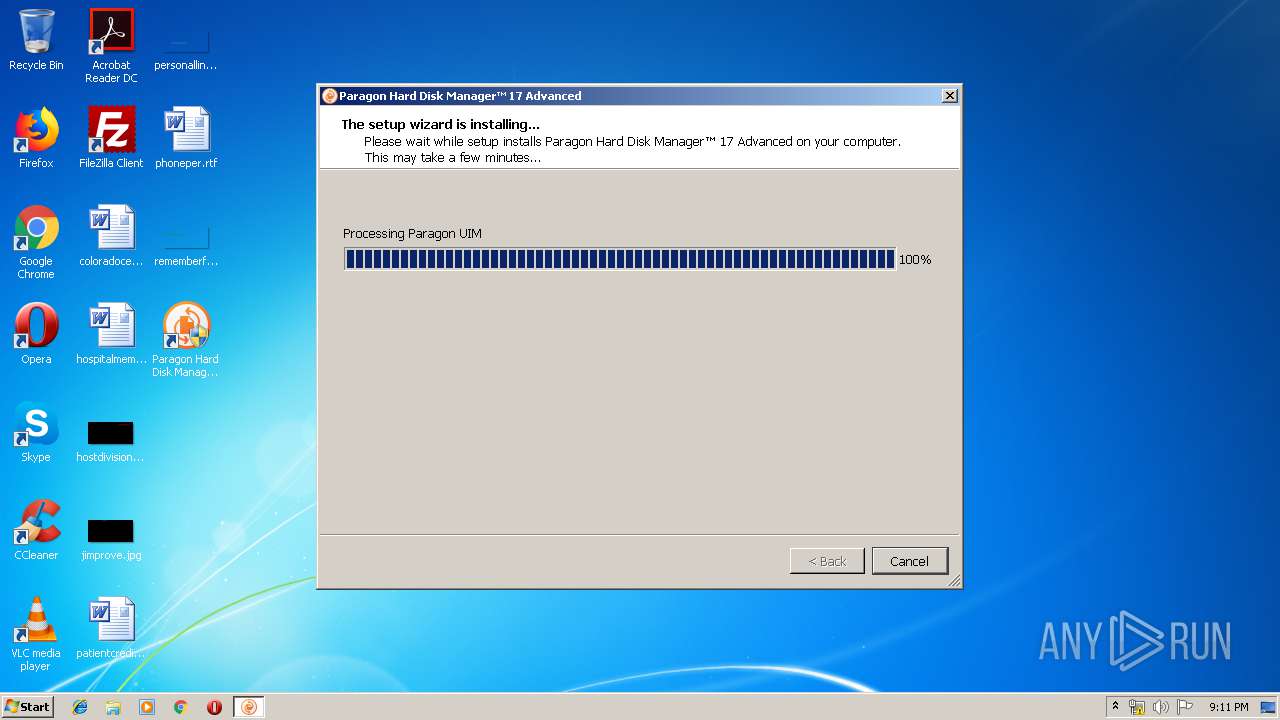
- winfuse_uimsetup.exe (PID: 2984)
- hdm17.exe (PID: 1344)
Loads dropped or rewritten executable
- hdm17advanced_x86_trial.exe (PID: 2028)
- WUDFHost.exe (PID: 3404)
- DrvInst.exe (PID: 3880)
- winfuse_uimsetup.exe (PID: 2984)
- hdm17.exe (PID: 1344)
Changes the autorun value in the registry
- hdm17advanced_x86.exe (PID: 3308)
Changes settings of System certificates
- MsiExec.exe (PID: 2588)
- winfuse_uimsetup.exe (PID: 2984)
Loads the Task Scheduler COM API
- hdm17.exe (PID: 1344)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2772)
- hdm17advanced_x86_trial.exe (PID: 2304)
- hdm17advanced_x86_trial.exe (PID: 2028)
- hdm17advanced_x86.exe (PID: 3308)
- winfuse_uimsetup.exe (PID: 2984)
- DrvInst.exe (PID: 2728)
- DrvInst.exe (PID: 3880)
- msiexec.exe (PID: 3228)
- DrvInst.exe (PID: 1956)
- DrvInst.exe (PID: 836)
- DrvInst.exe (PID: 820)
- DrvInst.exe (PID: 496)
Creates files in the Windows directory
- hdm17advanced_x86_trial.exe (PID: 2304)
- hdm17advanced_x86_trial.exe (PID: 2028)
- winfuse_uimsetup.exe (PID: 2984)
- DrvInst.exe (PID: 2728)
- DrvInst.exe (PID: 3880)
- WUDFHost.exe (PID: 3404)
- DrvInst.exe (PID: 1956)
- DrvInst.exe (PID: 836)
- DrvInst.exe (PID: 496)
- DrvInst.exe (PID: 820)
- hdm17.exe (PID: 1344)
Starts itself from another location
- hdm17advanced_x86_trial.exe (PID: 2028)
Creates a software uninstall entry
- hdm17advanced_x86.exe (PID: 3308)
Creates files in the program directory
- hdm17advanced_x86.exe (PID: 3308)
- hdm17.exe (PID: 1344)
Executed via COM
- DrvInst.exe (PID: 2728)
- DrvInst.exe (PID: 3880)
- DrvInst.exe (PID: 1956)
- DrvInst.exe (PID: 820)
- DrvInst.exe (PID: 496)
- DrvInst.exe (PID: 836)
- vdsldr.exe (PID: 2516)
Adds / modifies Windows certificates
- MsiExec.exe (PID: 2588)
- winfuse_uimsetup.exe (PID: 2984)
Removes files from Windows directory
- DrvInst.exe (PID: 2728)
- DrvInst.exe (PID: 3880)
- DrvInst.exe (PID: 1956)
- DrvInst.exe (PID: 820)
- DrvInst.exe (PID: 836)
- DrvInst.exe (PID: 496)
- hdm17.exe (PID: 1344)
- hdm17advanced_x86_trial.exe (PID: 2028)
- hdm17advanced_x86_trial.exe (PID: 2304)
Creates files in the driver directory
- DrvInst.exe (PID: 2728)
- DrvInst.exe (PID: 3880)
- DrvInst.exe (PID: 1956)
- DrvInst.exe (PID: 820)
- DrvInst.exe (PID: 836)
- DrvInst.exe (PID: 496)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 2728)
Executed as Windows Service
- vssvc.exe (PID: 3028)
- vds.exe (PID: 3804)
Low-level read access rights to disk partition
- hdm17.exe (PID: 1344)
- vds.exe (PID: 3804)
INFO
Reads the hosts file
- chrome.exe (PID: 2772)
- chrome.exe (PID: 1268)
Reads Internet Cache Settings
- chrome.exe (PID: 2772)
Application launched itself
- chrome.exe (PID: 2772)
- msiexec.exe (PID: 3228)
Dropped object may contain Bitcoin addresses
- hdm17advanced_x86_trial.exe (PID: 2028)
- msiexec.exe (PID: 3228)
Creates a software uninstall entry
- msiexec.exe (PID: 3228)
Creates files in the program directory
- msiexec.exe (PID: 3228)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3028)
Searches for installed software
- DrvInst.exe (PID: 2728)
- DrvInst.exe (PID: 1956)
- DrvInst.exe (PID: 836)
Reads settings of System Certificates
- hdm17.exe (PID: 1344)
Manual execution by user
- hdm17.exe (PID: 1344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
80
Monitored processes
33
Malicious processes
14
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | DrvInst.exe "2" "211" "ROOT\UIM\0001" "C:\Windows\INF\oem6.inf" "uimdevim.inf:UIM_Plugin.NTx86:Plugin_Inst:0.6.0.0:uim\plugin_devim" "68ba390a3" "000005DC" "000005E8" "000005E4" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | C:\Windows\system32\MsiExec.exe -Embedding 744DC727F1DFC0DC32F417B1DF5C6A85 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 820 | DrvInst.exe "2" "211" "ROOT\UIM\0000" "C:\Windows\INF\oem5.inf" "uimbus.inf:UIM_Adapter.NTx86:UimBus_Inst:0.6.0.0:root\uim_bus" "648d7e42b" "000002F0" "000005F0" "000005E0" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 836 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{00855470-b1ad-429e-b5c1-2801b2f52436}\uimdevim.inf" "0" "68ba390a3" "000005DC" "WinSta0\Default" "00000338" "208" "c:\program files\paragon software\universal image mounter" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,12678004809850984392,2457709190507191991,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=13764086145109686041 --mojo-platform-channel-handle=1560 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Paragon Software\Hard Disk Manager 17 Advanced\program\hdm17.exe" | C:\Program Files\Paragon Software\Hard Disk Manager 17 Advanced\program\hdm17.exe | explorer.exe | ||||||||||||
User: admin Company: Paragon Software GmbH Integrity Level: HIGH Description: A part of Paragon System Utilities Exit code: 0 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1008,12678004809850984392,2457709190507191991,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=1386603058058431497 --mojo-platform-channel-handle=1032 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1008,12678004809850984392,2457709190507191991,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=15163215967963536041 --mojo-platform-channel-handle=3412 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1956 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{0af4a082-289f-5d9b-812b-d413b8398143}\uimbus.inf" "0" "648d7e42b" "000005A4" "WinSta0\Default" "000002F0" "208" "c:\program files\paragon software\universal image mounter" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | "C:\Windows\Temp\{15687F16-8B3D-40CC-A029-1BCE1452402D}\.cr\hdm17advanced_x86_trial.exe" -burn.clean.room="C:\Users\admin\Downloads\hdm17advanced_x86_trial.exe" -burn.filehandle.attached=148 -burn.filehandle.self=156 | C:\Windows\Temp\{15687F16-8B3D-40CC-A029-1BCE1452402D}\.cr\hdm17advanced_x86_trial.exe | hdm17advanced_x86_trial.exe | ||||||||||||
User: admin Company: Paragon Software GmbH Integrity Level: HIGH Description: Paragon Hard Disk Manager™ 17 Advanced Exit code: 0 Version: 17.10.12.5173 Modules
| |||||||||||||||
Total events
3 809
Read events
2 076
Write events
1 704
Delete events
29
Modification events
| (PID) Process: | (2812) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2772-13223768967499000 |
Value: 259 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1512-13197841398593750 |
Value: 0 | |||
| (PID) Process: | (2772) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
204
Suspicious files
102
Text files
1 037
Unknown types
174
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\14bcb546-144b-4eba-8333-1ae56cbc7799.tmp | — | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF39a9d7.TMP | text | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF39a9a8.TMP | text | |
MD5:— | SHA256:— | |||
| 2772 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF39a9c7.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
16
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3228 | msiexec.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.4 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | chrome.exe | 143.204.214.112:443 | dl.paragon-software.com | — | US | suspicious |
1268 | chrome.exe | 216.58.206.4:443 | www.google.com | Google Inc. | US | whitelisted |
1268 | chrome.exe | 216.58.206.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1268 | chrome.exe | 143.204.214.109:443 | dl.paragon-software.com | — | US | unknown |
1268 | chrome.exe | 172.217.18.110:443 | clients1.google.com | Google Inc. | US | whitelisted |
1268 | chrome.exe | 172.217.18.174:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3228 | msiexec.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 62.159.194.50:443 | my.paragon-software.com | Deutsche Telekom AG | DE | unknown |
1268 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
1268 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl.paragon-software.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
my.paragon-software.com |
| unknown |
Threats
Process | Message |
|---|---|
hdm17advanced_x86_trial.exe | QFSFileEngine::open: No file name specified
|
hdm17advanced_x86_trial.exe | QFSFileEngine::open: No file name specified
|
hdm17advanced_x86_trial.exe | QFSFileEngine::open: No file name specified
|
DrvInst.exe | WudfUpdate: installing version (1,9,0,7600).
|
DrvInst.exe | WudfUpdate: Checking for presence of previous UMDF installation.
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\wudfsvc.dll version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\drivers\wudfpf.sys version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\wudfplatform.dll version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\drivers\wudfrd.sys version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\wudfhost.exe version (1.9.0.7601)
|