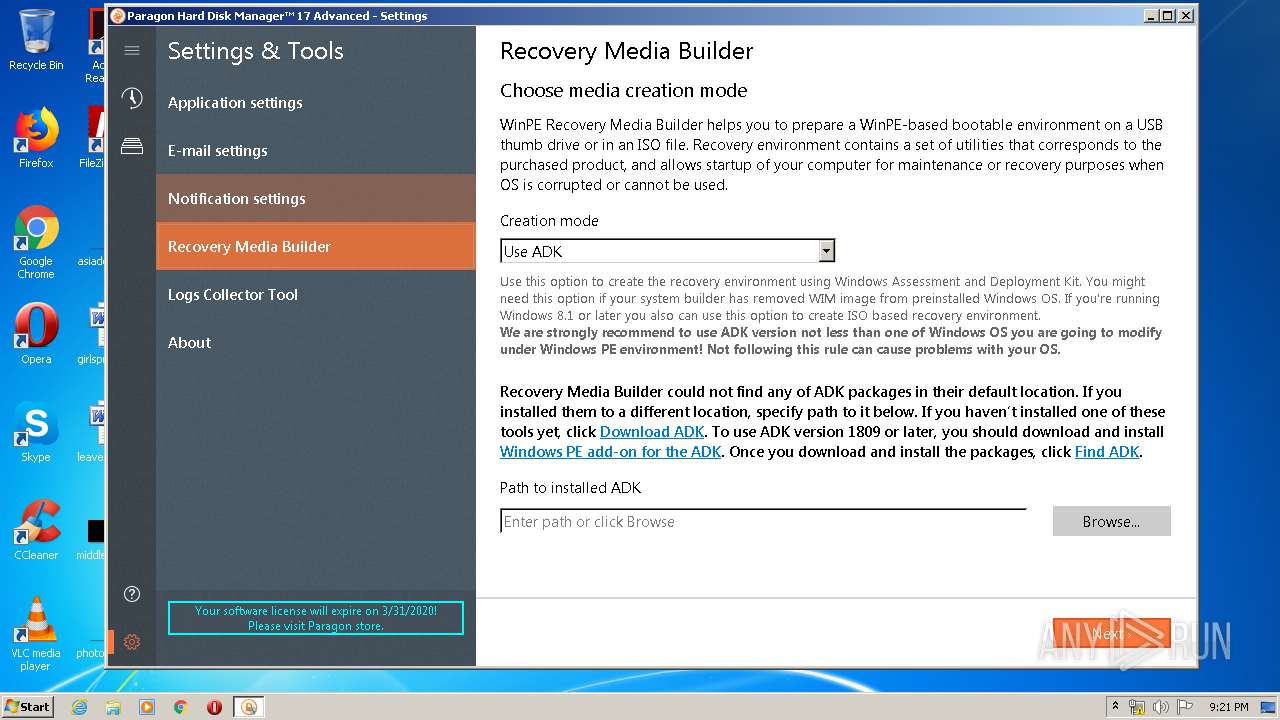
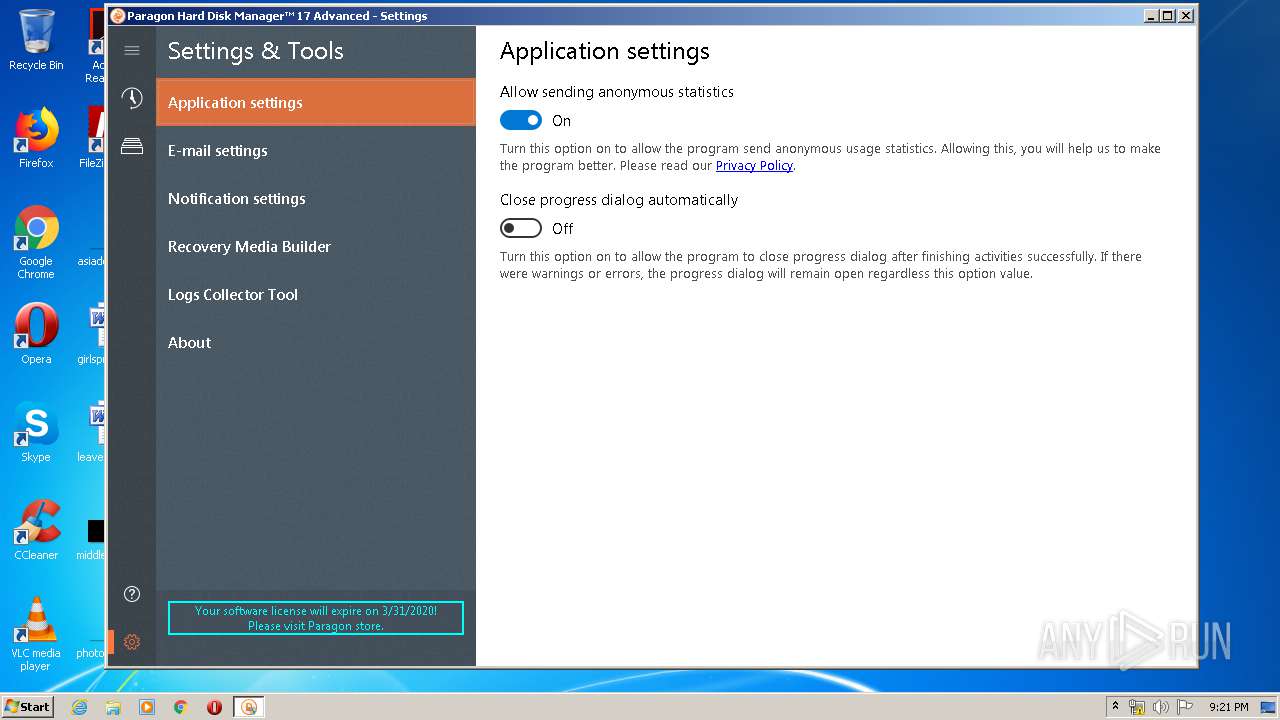
| URL: | https://dl.paragon-software.com/esd/795_PEU/17.10.12/hdm17advanced_x86_trial.exe |
| Full analysis: | https://app.any.run/tasks/0965f9bf-62c1-408e-9487-b4408a2294ff |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2020, 21:16:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6C74EF29835A0177232A72FBDF21D9F1 |
| SHA1: | DE849C1944F6FF66D709812041079FF0191948A2 |
| SHA256: | AE9877557402EE3548E000BDDCFFD2CD958EE35B36161613C5D45364978437EF |
| SSDEEP: | 3:N8RSXeHFwGJu+KNrYcSMO4An:2+PGzjvN |
MALICIOUS
Application was dropped or rewritten from another process
- hdm17advanced_x86_trial.exe (PID: 2804)
- hdm17advanced_x86_trial.exe (PID: 3224)
- winfuse_uimsetup.exe (PID: 2860)
- hdm17.exe (PID: 2056)
- hdm17advanced_x86_trial.exe (PID: 1296)
- hdm17advanced_x86.exe (PID: 2404)
Loads dropped or rewritten executable
- hdm17advanced_x86_trial.exe (PID: 1296)
- WUDFHost.exe (PID: 3348)
- winfuse_uimsetup.exe (PID: 2860)
- DrvInst.exe (PID: 304)
- hdm17.exe (PID: 2056)
Changes settings of System certificates
- MsiExec.exe (PID: 1028)
- winfuse_uimsetup.exe (PID: 2860)
- msiexec.exe (PID: 3272)
Changes the autorun value in the registry
- hdm17advanced_x86.exe (PID: 2404)
Loads the Task Scheduler COM API
- hdm17.exe (PID: 2056)
SUSPICIOUS
Starts itself from another location
- hdm17advanced_x86_trial.exe (PID: 1296)
Creates files in the program directory
- hdm17advanced_x86.exe (PID: 2404)
- hdm17.exe (PID: 2056)
Executable content was dropped or overwritten
- chrome.exe (PID: 2676)
- hdm17advanced_x86_trial.exe (PID: 3224)
- hdm17advanced_x86_trial.exe (PID: 1296)
- winfuse_uimsetup.exe (PID: 2860)
- DrvInst.exe (PID: 404)
- DrvInst.exe (PID: 304)
- msiexec.exe (PID: 3272)
- DrvInst.exe (PID: 1136)
- DrvInst.exe (PID: 2468)
- DrvInst.exe (PID: 3660)
- DrvInst.exe (PID: 3832)
- hdm17advanced_x86.exe (PID: 2404)
Creates files in the Windows directory
- hdm17advanced_x86_trial.exe (PID: 1296)
- winfuse_uimsetup.exe (PID: 2860)
- DrvInst.exe (PID: 404)
- DrvInst.exe (PID: 304)
- WUDFHost.exe (PID: 3348)
- DrvInst.exe (PID: 1136)
- DrvInst.exe (PID: 2468)
- DrvInst.exe (PID: 3660)
- DrvInst.exe (PID: 3832)
- hdm17.exe (PID: 2056)
- hdm17advanced_x86_trial.exe (PID: 3224)
Adds / modifies Windows certificates
- MsiExec.exe (PID: 1028)
- winfuse_uimsetup.exe (PID: 2860)
- msiexec.exe (PID: 3272)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 404)
Executed via COM
- DrvInst.exe (PID: 404)
- DrvInst.exe (PID: 304)
- DrvInst.exe (PID: 2468)
- DrvInst.exe (PID: 3660)
- DrvInst.exe (PID: 1136)
- DrvInst.exe (PID: 3832)
- vdsldr.exe (PID: 2192)
Removes files from Windows directory
- DrvInst.exe (PID: 404)
- DrvInst.exe (PID: 304)
- DrvInst.exe (PID: 1136)
- DrvInst.exe (PID: 2468)
- DrvInst.exe (PID: 3660)
- DrvInst.exe (PID: 3832)
- hdm17advanced_x86_trial.exe (PID: 1296)
- hdm17advanced_x86_trial.exe (PID: 3224)
- hdm17.exe (PID: 2056)
Creates files in the driver directory
- DrvInst.exe (PID: 404)
- DrvInst.exe (PID: 304)
- DrvInst.exe (PID: 1136)
- DrvInst.exe (PID: 2468)
- DrvInst.exe (PID: 3660)
- DrvInst.exe (PID: 3832)
Executed as Windows Service
- vssvc.exe (PID: 4084)
- vds.exe (PID: 440)
Low-level read access rights to disk partition
- hdm17.exe (PID: 2056)
- vds.exe (PID: 440)
Creates a software uninstall entry
- hdm17advanced_x86.exe (PID: 2404)
INFO
Reads the hosts file
- chrome.exe (PID: 2676)
- chrome.exe (PID: 3152)
Application launched itself
- chrome.exe (PID: 2676)
- msiexec.exe (PID: 3272)
Reads Internet Cache Settings
- chrome.exe (PID: 2676)
Dropped object may contain Bitcoin addresses
- hdm17advanced_x86_trial.exe (PID: 1296)
- msiexec.exe (PID: 3272)
Reads settings of System Certificates
- winfuse_uimsetup.exe (PID: 2860)
- chrome.exe (PID: 3152)
Creates a software uninstall entry
- msiexec.exe (PID: 3272)
Creates files in the program directory
- msiexec.exe (PID: 3272)
Low-level read access rights to disk partition
- vssvc.exe (PID: 4084)
Searches for installed software
- DrvInst.exe (PID: 404)
- DrvInst.exe (PID: 1136)
- DrvInst.exe (PID: 3660)
Manual execution by user
- hdm17.exe (PID: 2056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
78
Monitored processes
33
Malicious processes
13
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | DrvInst.exe "2" "211" "ROOT\PARAGONBLOCKDEVICE\0000" "C:\Windows\INF\oem4.inf" "winfuse_blockmounter.inf:Paragon.NTx86:blockmounter:24.65.0.0:wudf\paragonblockdev" "67370f437" "000003FC" "000005D8" "000005DC" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 404 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{152f50e4-466f-348c-757f-2271abe21624}\winfuse_blockmounter.inf" "0" "67370f437" "000003FC" "WinSta0\Default" "00000554" "208" "c:\program files\paragon software\universal image mounter" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 440 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | C:\Windows\system32\MsiExec.exe -Embedding E92427DC45529F9D85326B57C1468EFE M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1136 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{6214ea26-7978-0d13-55c9-2938a4466e44}\uimbus.inf" "0" "648d7e42b" "000003BC" "WinSta0\Default" "000002C8" "208" "c:\program files\paragon software\universal image mounter" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1296 | "C:\Windows\Temp\{59D91000-FF21-4383-A2FD-33DEB8622A2F}\.cr\hdm17advanced_x86_trial.exe" -burn.clean.room="C:\Users\admin\Downloads\hdm17advanced_x86_trial.exe" -burn.filehandle.attached=148 -burn.filehandle.self=156 | C:\Windows\Temp\{59D91000-FF21-4383-A2FD-33DEB8622A2F}\.cr\hdm17advanced_x86_trial.exe | hdm17advanced_x86_trial.exe | ||||||||||||
User: admin Company: Paragon Software GmbH Integrity Level: HIGH Description: Paragon Hard Disk Manager™ 17 Advanced Exit code: 0 Version: 17.10.12.5173 Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Paragon Software\Hard Disk Manager 17 Advanced\program\hdm17.exe" | C:\Program Files\Paragon Software\Hard Disk Manager 17 Advanced\program\hdm17.exe | explorer.exe | ||||||||||||
User: admin Company: Paragon Software GmbH Integrity Level: HIGH Description: A part of Paragon System Utilities Exit code: 0 Modules
| |||||||||||||||
| 2192 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2404 | "C:\Windows\Temp\{DCB7F870-4B13-4049-8B18-6F9B5D6F6ECD}\.be\hdm17advanced_x86.exe" -q -burn.elevated BurnPipe.{482E1888-7BF2-42F2-9E2E-442F4AD3CC8C} {B33E2CAA-13B6-4045-94A0-F1C003E85A7E} 1296 | C:\Windows\Temp\{DCB7F870-4B13-4049-8B18-6F9B5D6F6ECD}\.be\hdm17advanced_x86.exe | hdm17advanced_x86_trial.exe | ||||||||||||
User: admin Company: Paragon Software GmbH Integrity Level: HIGH Description: Paragon Hard Disk Manager™ 17 Advanced Exit code: 0 Version: 17.10.12.5173 Modules
| |||||||||||||||
| 2424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,12215625952044961603,16437872658597225210,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10678948225951494988 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2252 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
5 362
Read events
2 472
Write events
2 861
Delete events
29
Modification events
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2916) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2676-13229299003507500 |
Value: 259 | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2676-13229299003507500 |
Value: 259 | |||
Executable files
202
Suspicious files
102
Text files
855
Unknown types
173
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E76843B-A74.pma | — | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\843e1954-4623-4cea-8c14-6b62f7a6f0de.tmp | — | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2676 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa66ea0.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
11
DNS requests
7
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3152 | chrome.exe | 143.204.201.38:443 | dl.paragon-software.com | — | US | malicious |
3152 | chrome.exe | 172.217.23.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
3152 | chrome.exe | 216.239.32.117:443 | www.google.com | Google Inc. | US | whitelisted |
3152 | chrome.exe | 172.217.21.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3152 | chrome.exe | 172.217.22.67:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3152 | chrome.exe | 172.217.23.110:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3152 | chrome.exe | 172.217.21.206:443 | — | Google Inc. | US | whitelisted |
3272 | msiexec.exe | 8.241.88.126:80 | — | Level 3 Communications, Inc. | US | unknown |
3152 | chrome.exe | 216.58.207.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
dl.paragon-software.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
hdm17advanced_x86_trial.exe | QFSFileEngine::open: No file name specified
|
hdm17advanced_x86_trial.exe | QFSFileEngine::open: No file name specified
|
hdm17advanced_x86_trial.exe | QFSFileEngine::open: No file name specified
|
DrvInst.exe | WudfUpdate: installing version (1,9,0,7600).
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\drivers\wudfpf.sys version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\drivers\wudfrd.sys version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\wudfsvc.dll version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\wudfplatform.dll version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\wudfx.dll version (1.9.0.7601)
|
DrvInst.exe | WudfUpdate: Found binary %WINDIR%\system32\wudfhost.exe version (1.9.0.7601)
|