| URL: | https://www.videolan.org/vlc/features.html |
| Full analysis: | https://app.any.run/tasks/68348c22-d0dc-42c8-a1ce-67a4a3fe8f18 |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2024, 21:30:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B271695AEC55580DA96E57BD8DD9111D |
| SHA1: | 1679986ECD6F37DD3237DAF0C0EDD4FD1177A640 |
| SHA256: | AE896557D56B9B8E9FBA74688F15F007CF9B1463DCAB1E33654CD65A6DB3877E |
| SSDEEP: | 3:N8DSLABAKJELoC00AWPIJn:2OLAtJEUm0 |
MALICIOUS
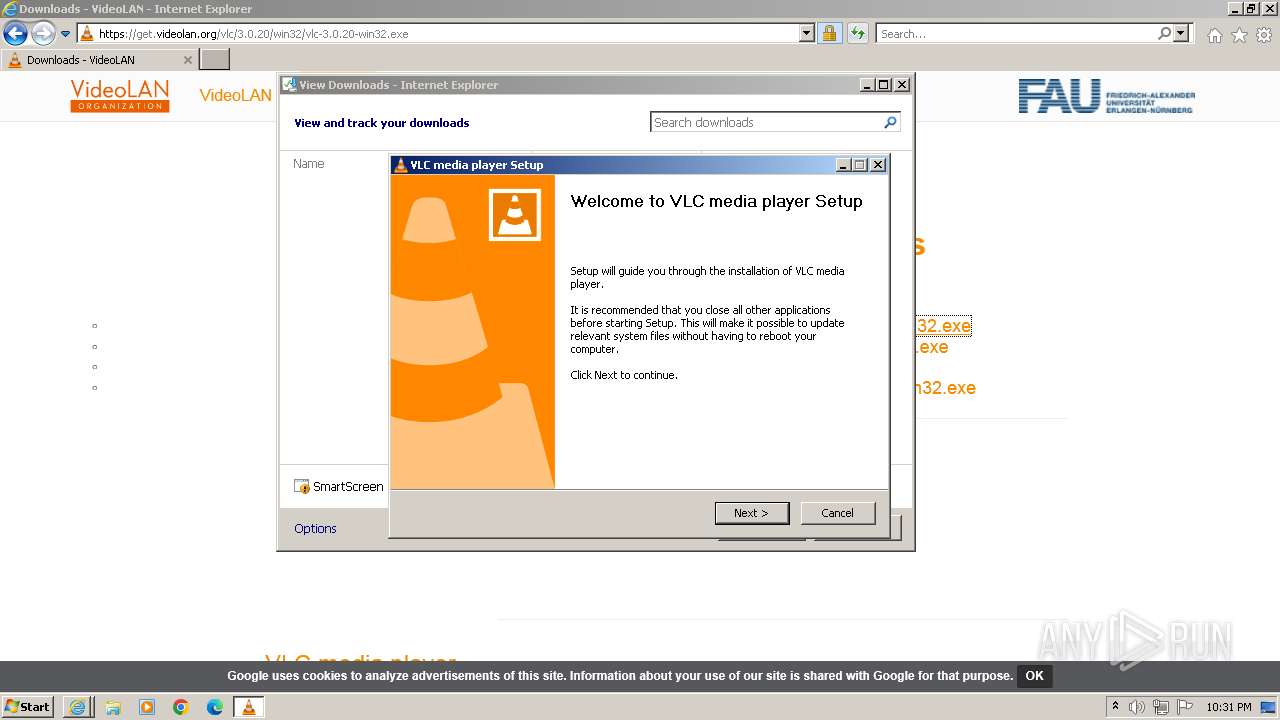
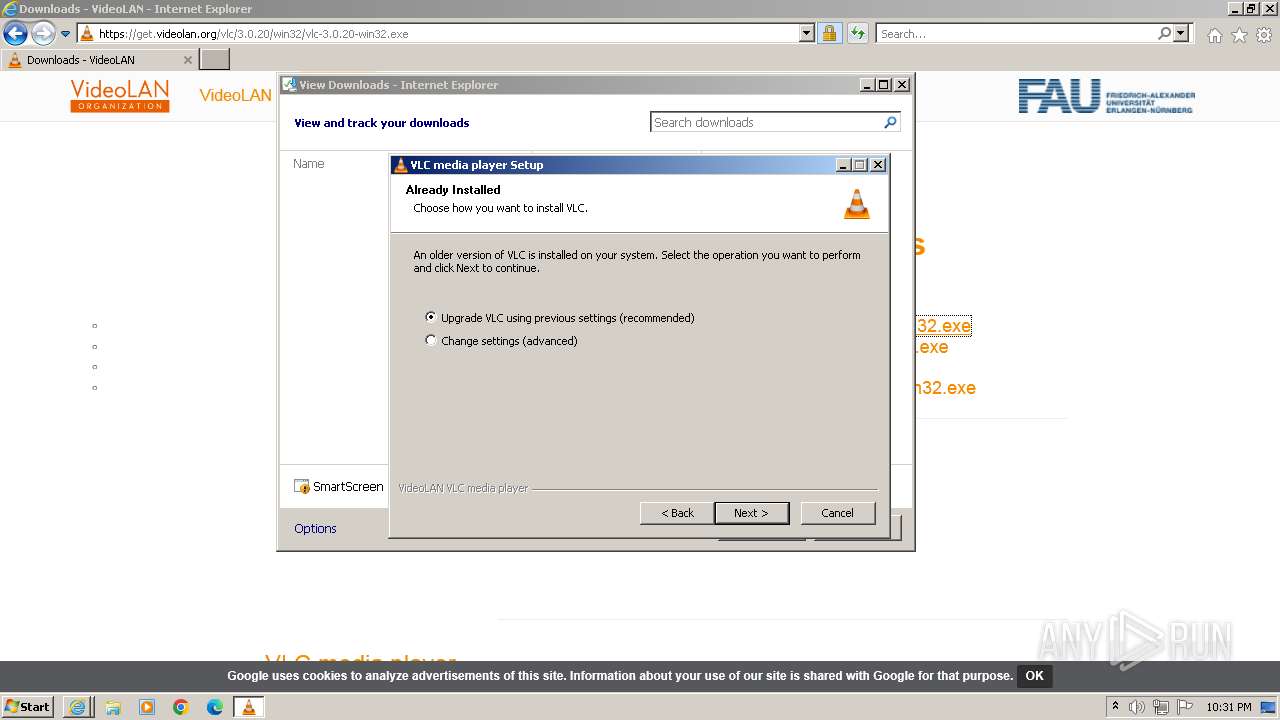
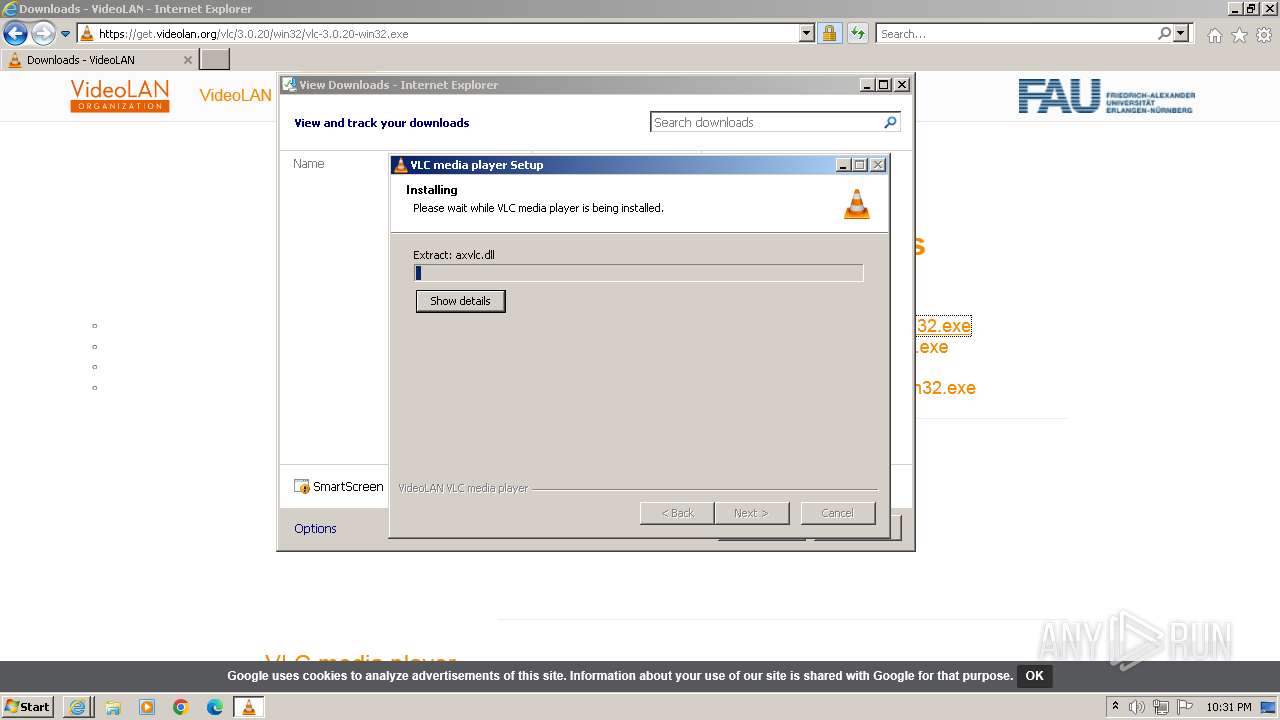
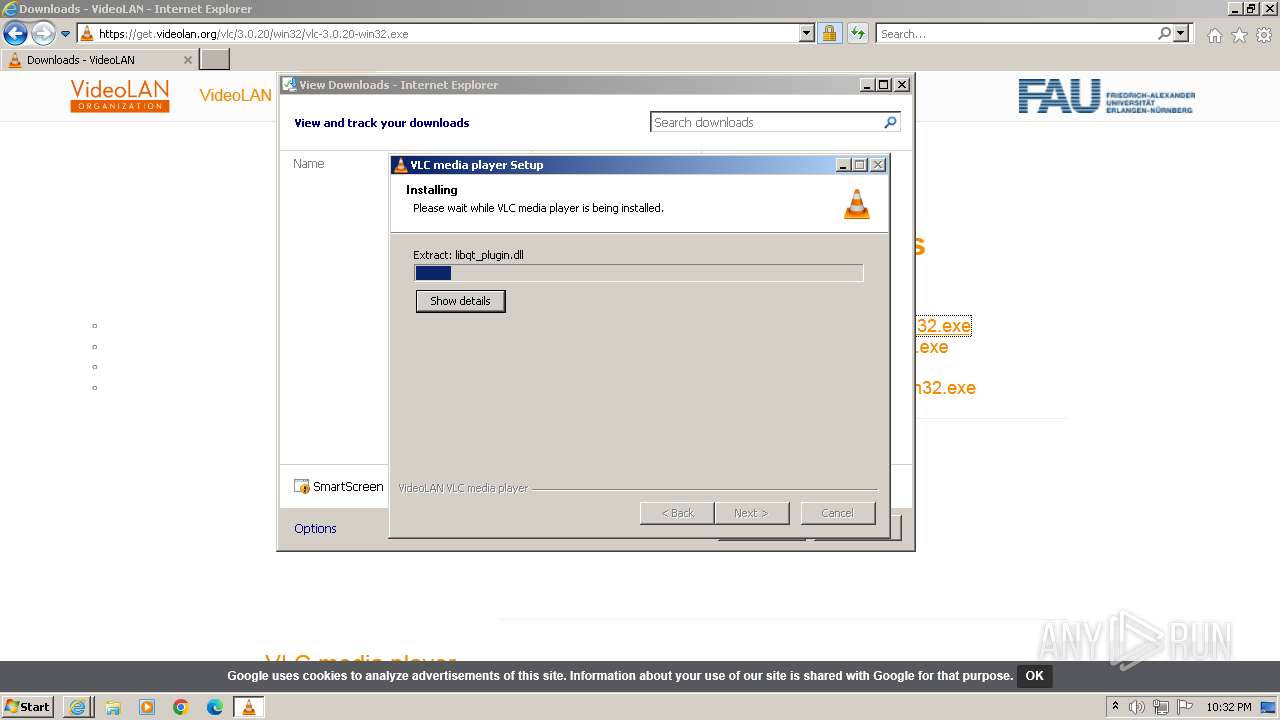
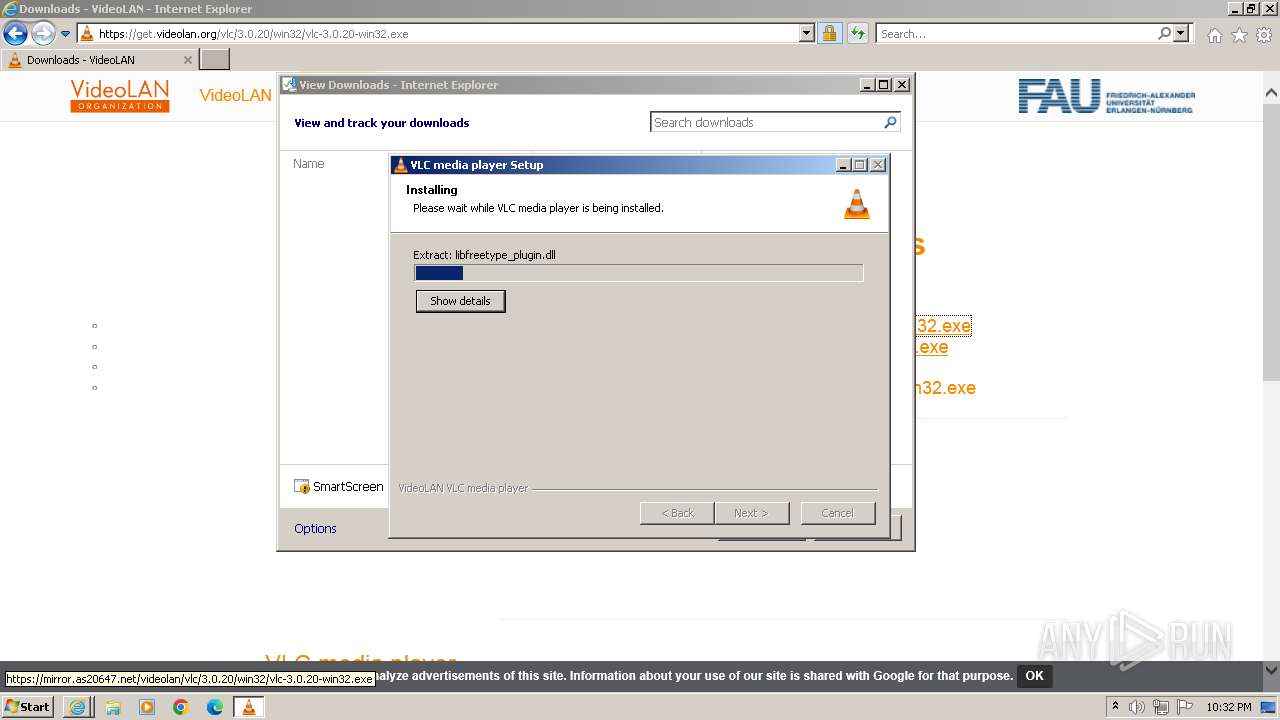
Drops the executable file immediately after the start
- vlc-3.0.20-win32 (1).exe (PID: 568)
SUSPICIOUS
The process creates files with name similar to system file names
- vlc-3.0.20-win32 (1).exe (PID: 568)
Searches for installed software
- vlc-3.0.20-win32 (1).exe (PID: 568)
Malware-specific behavior (creating "System.dll" in Temp)
- vlc-3.0.20-win32 (1).exe (PID: 568)
Executable content was dropped or overwritten
- vlc-3.0.20-win32 (1).exe (PID: 568)
Starts application with an unusual extension
- vlc-3.0.20-win32 (1).exe (PID: 568)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 1644)
Creates/Modifies COM task schedule object
- vlc-3.0.20-win32 (1).exe (PID: 568)
Creates a software uninstall entry
- vlc-3.0.20-win32 (1).exe (PID: 568)
INFO
Application launched itself
- iexplore.exe (PID: 3968)
Checks supported languages
- wmpnscfg.exe (PID: 1664)
- vlc-3.0.20-win32 (1).exe (PID: 568)
- vlc-cache-gen.exe (PID: 2560)
- nsBDB2.tmp (PID: 1128)
- vlc.exe (PID: 2552)
Reads the computer name
- wmpnscfg.exe (PID: 1664)
- vlc-3.0.20-win32 (1).exe (PID: 568)
- vlc.exe (PID: 2552)
Manual execution by a user
- wmpnscfg.exe (PID: 1664)
- explorer.exe (PID: 2736)
Executable content was dropped or overwritten
- iexplore.exe (PID: 4032)
The process uses the downloaded file
- iexplore.exe (PID: 3968)
Drops the executable file immediately after the start
- iexplore.exe (PID: 4032)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3968)
Create files in a temporary directory
- vlc-3.0.20-win32 (1).exe (PID: 568)
Creates files in the program directory
- vlc-3.0.20-win32 (1).exe (PID: 568)
- vlc-cache-gen.exe (PID: 2560)
Reads the machine GUID from the registry
- vlc-3.0.20-win32 (1).exe (PID: 568)
- vlc-cache-gen.exe (PID: 2560)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2696)
Reads the Internet Settings
- explorer.exe (PID: 2696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
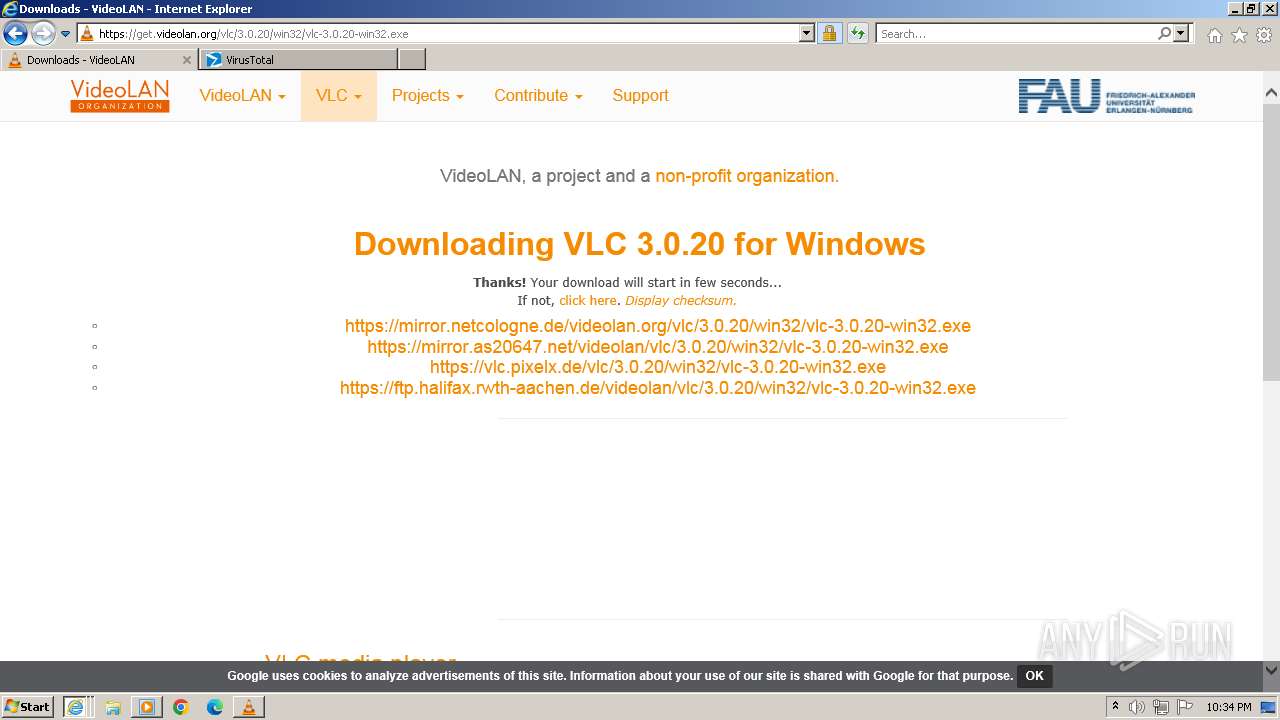
| 568 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\vlc-3.0.20-win32 (1).exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\vlc-3.0.20-win32 (1).exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1128 | "C:\Users\admin\AppData\Local\Temp\nsh46FB.tmp\nsBDB2.tmp" "C:\Program Files\VideoLAN\VLC\vlc-cache-gen.exe" C:\Program Files\VideoLAN\VLC\plugins | C:\Users\admin\AppData\Local\Temp\nsh46FB.tmp\nsBDB2.tmp | — | vlc-3.0.20-win32 (1).exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1644 | "C:\Windows\explorer.exe" "C:\Program Files\VideoLAN\VLC\vlc.exe" | C:\Windows\explorer.exe | — | vlc-3.0.20-win32 (1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1664 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1932 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\vlc-3.0.20-win32 (1).exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\vlc-3.0.20-win32 (1).exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2524 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3968 CREDAT:3216660 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2552 | "C:\Program Files\VideoLAN\VLC\vlc.exe" | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Version: 3.0.20 Modules
| |||||||||||||||
| 2560 | "C:\Program Files\VideoLAN\VLC\vlc-cache-gen.exe" C:\Program Files\VideoLAN\VLC\plugins | C:\Program Files\VideoLAN\VLC\vlc-cache-gen.exe | nsBDB2.tmp | ||||||||||||
User: admin Company: VideoLAN Integrity Level: HIGH Description: VLC media player Exit code: 0 Version: 3.0.20 Modules
| |||||||||||||||
| 2696 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2736 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
51 076
Read events
49 477
Write events
1 328
Delete events
271
Modification events
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31104215 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 208316314 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31104216 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3968) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
382
Suspicious files
272
Text files
247
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
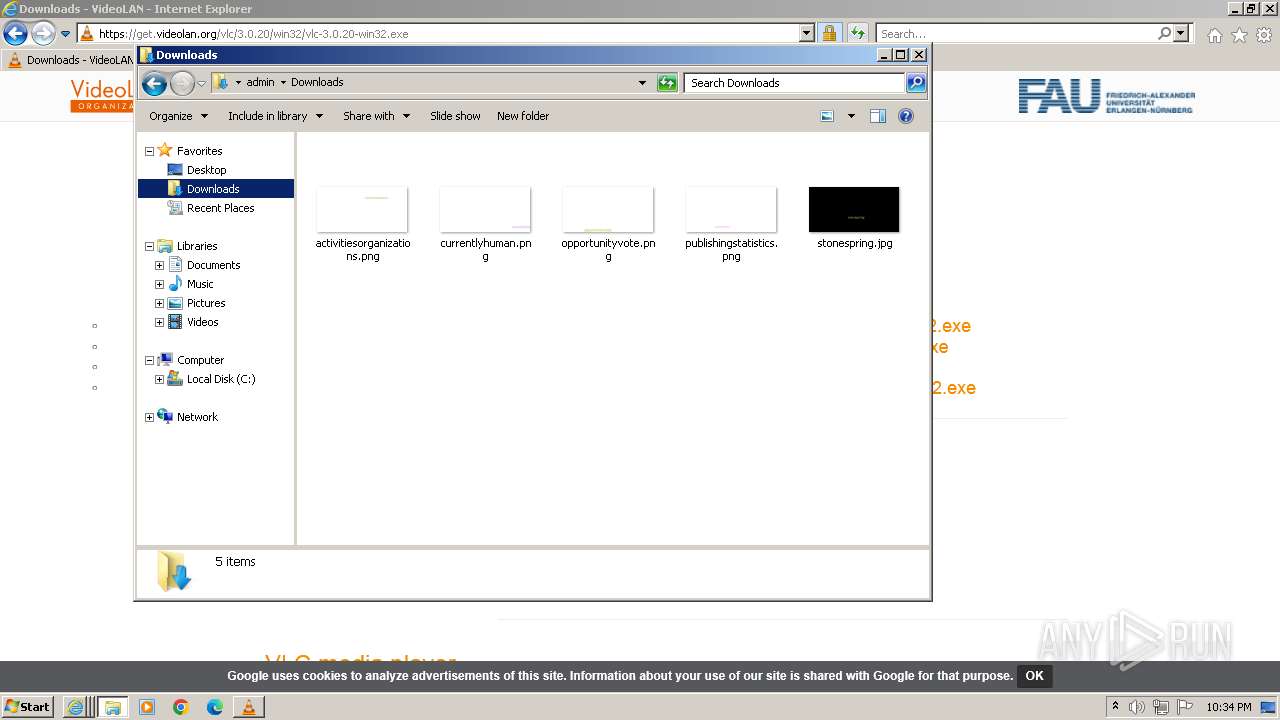
| 4032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:577D0C1C45489D9CAF2B03D96EE1CCEA | SHA256:8456D66F819518BABE4526808306B3E174EA0254736A6FD6230073C321FACCE7 | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\logoGrey[1].png | image | |
MD5:27EC73F81F78D5776C5DCF16D6A0DE23 | SHA256:40E16C50025B79BA208F0989F642ED4E99D291583FD4E31B7A20DEEE4F8AF586 | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\bootstrap.min[1].js | text | |
MD5:08727E57EFBDAC291AEE21A4F2CD66E4 | SHA256:261E9641B228870B00CBC0C9A7692D6165E48E5427B7A6947E8218DA93BE0AAD | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\bootstrap.min[1].css | text | |
MD5:77BD14A5B216BADBC56E5B42AB8D1588 | SHA256:EC2CCA978C1B6B1E195631A1C6743192154FBB9CC960D367AE2B711A8662F9AA | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\style.min[1].css | text | |
MD5:796B15960CD75099E2186356A0CEDBB0 | SHA256:BC43FE25DF7B4457C7153819E531DA1243FD0F2B563F2F67B4B3EE9C00915A72 | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:C377DED89C7FCCC64FE52CFACE7E625B | SHA256:9CE9956AD2CAD04DD73487003108ABE1E7E874B5CCBF34BE2BC31C885D1012F0 | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:4C46ED5FEDAD016479CACC0840EF1DAD | SHA256:A923CAEAC048416A4F6D16993CD0428C085E9E5704190CF6EC6263E25D363969 | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:0E7FA76A648279832C4B7A6A0E752AA5 | SHA256:70B1FE647AD254C4A184D889F139AD8D5CC40417E924469F2A2206BBFB76192C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
91
DNS requests
52
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9b5f474efa3999f3 | unknown | — | — | unknown |
— | — | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f1d6845798772d53 | unknown | — | — | unknown |
4032 | iexplore.exe | GET | 200 | 2.19.217.103:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
4032 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
4032 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | — | — | unknown |
4032 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEAFWoeiRoD5nEA9wbC%2FqWOc%3D | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c21588876f974d24 | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8644b833ad892dd7 | unknown | — | — | unknown |
4032 | iexplore.exe | GET | 200 | 108.138.2.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
3968 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4032 | iexplore.exe | 213.36.253.2:443 | www.videolan.org | Free SAS | FR | unknown |
— | — | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | unknown |
4032 | iexplore.exe | 2.19.217.103:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
4032 | iexplore.exe | 172.217.16.200:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
4032 | iexplore.exe | 142.250.184.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
4032 | iexplore.exe | 142.250.184.238:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
3968 | iexplore.exe | 213.36.253.2:443 | www.videolan.org | Free SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.videolan.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
images.videolan.org |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google-analytics.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc-cache-gen.exe | main libvlc debug: VLC media player - 3.0.20 Vetinari
|
vlc-cache-gen.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc-cache-gen.exe | main libvlc debug: revision 3.0.20-0-g6f0d0ab126
|
vlc-cache-gen.exe | main libvlc debug: configured with /builds/videolan/vlc/extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-shout' '--enable-goom' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-contrib=../contrib/i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' '--enable-qt' '--enable-skins2' '--enable-dvdread' '--enable-caca' 'host_alias=i686-w64-mingw32' 'CFLAGS= -D_WIN32_WINNT=0x0502 -DWINVER=0x502 -D__MSVCRT_VERSION__=0x700 ' 'CXXFLAGS= -D_WIN32_WINNT=0x0502 -DWINVER=0x502 -D__MSVCRT_VERSION__=0x700 ' 'PKG_CONFIG=pkg-config' 'PKG_CONFIG_LIBDIR=/usr/i686-w64-mingw32/lib/pkgconfig:/usr/lib/i686-w64-mingw32/pkgconfig'
|
vlc-cache-gen.exe | main libvlc debug: searching plug-in modules
|
vlc-cache-gen.exe | main libvlc debug: Copyright © 1996-2023 the VideoLAN team
|
vlc-cache-gen.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc-cache-gen.exe | main libvlc debug: using multimedia timers as clock source
|
vlc-cache-gen.exe | main libvlc debug: ignoring plugins cache file
|
vlc-cache-gen.exe | main libvlc debug: saving plugins cache C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|