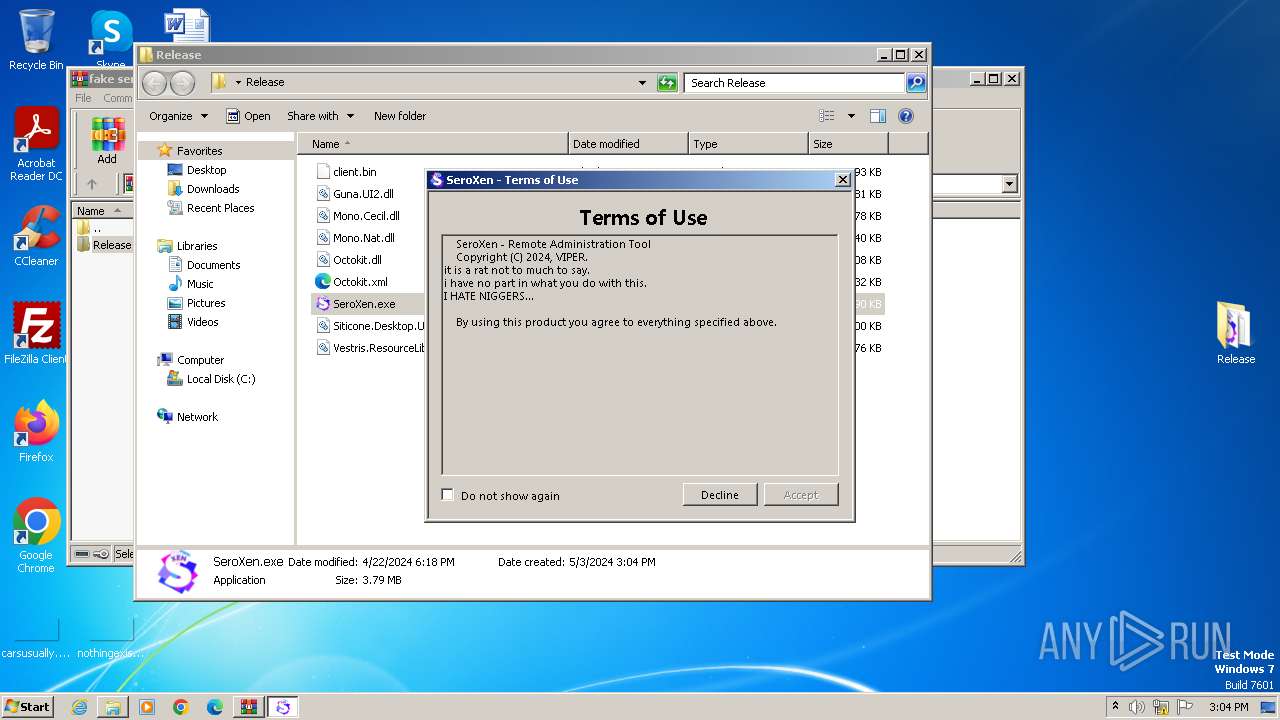
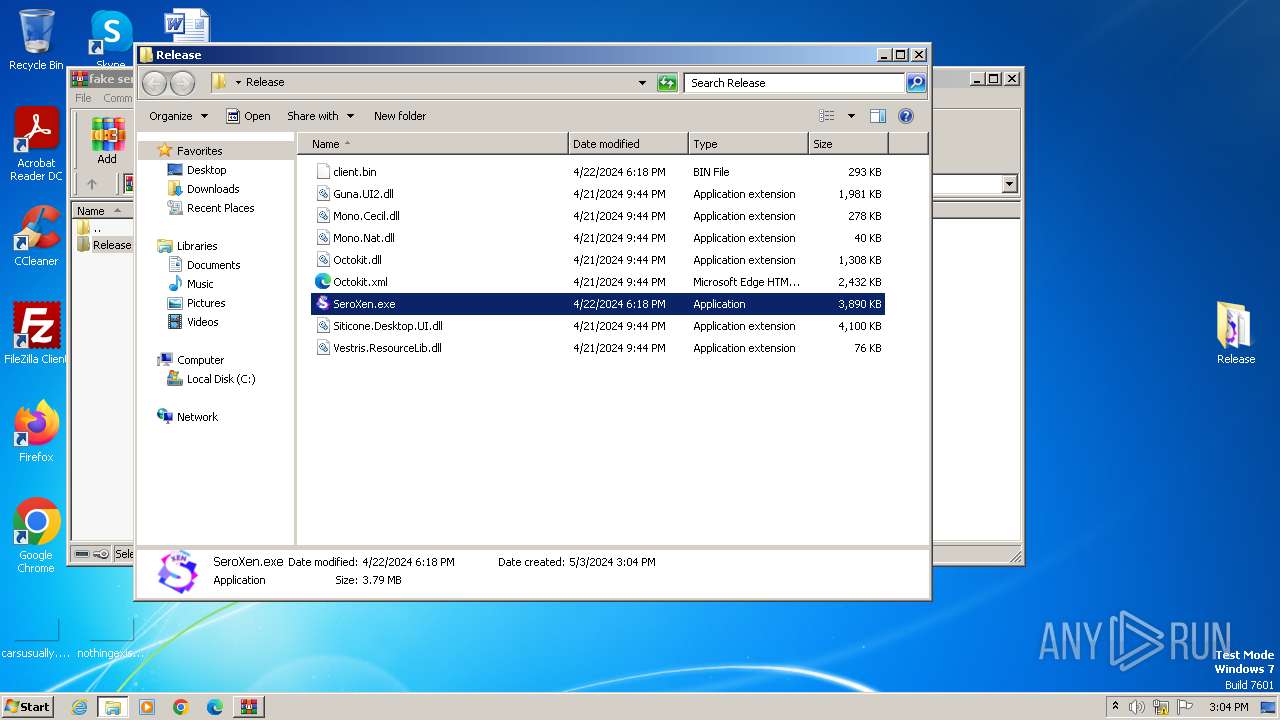
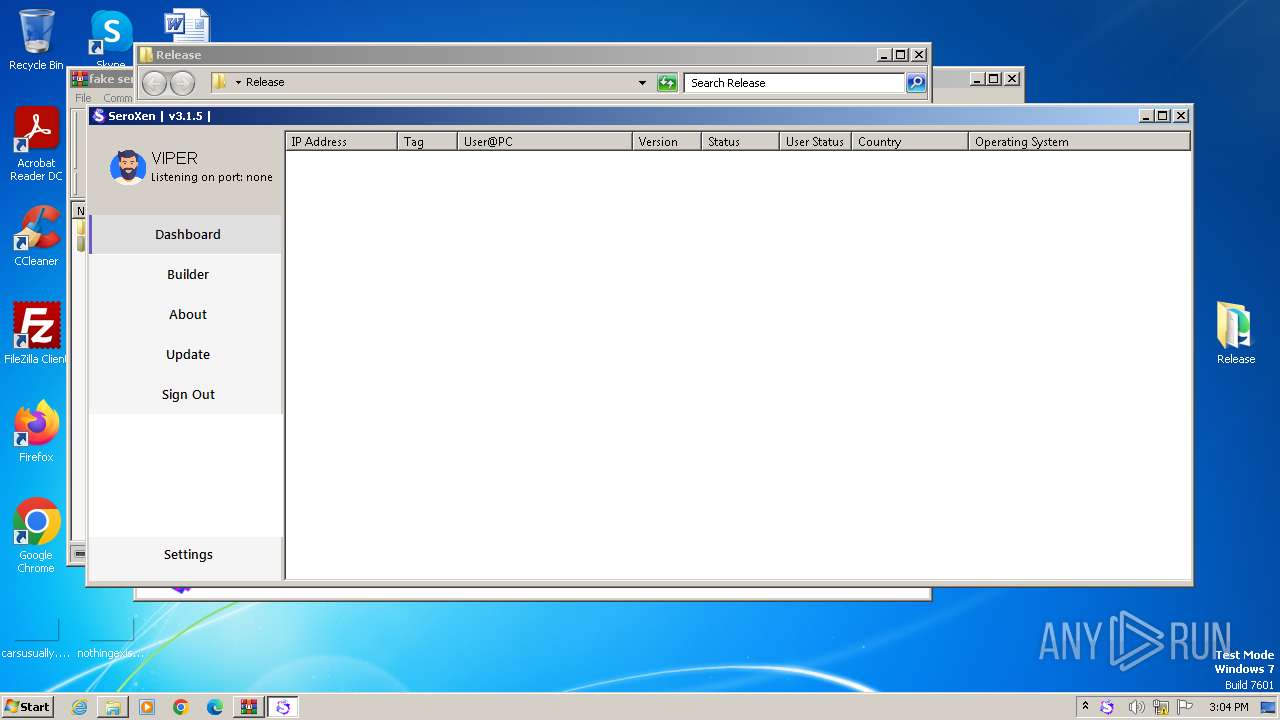
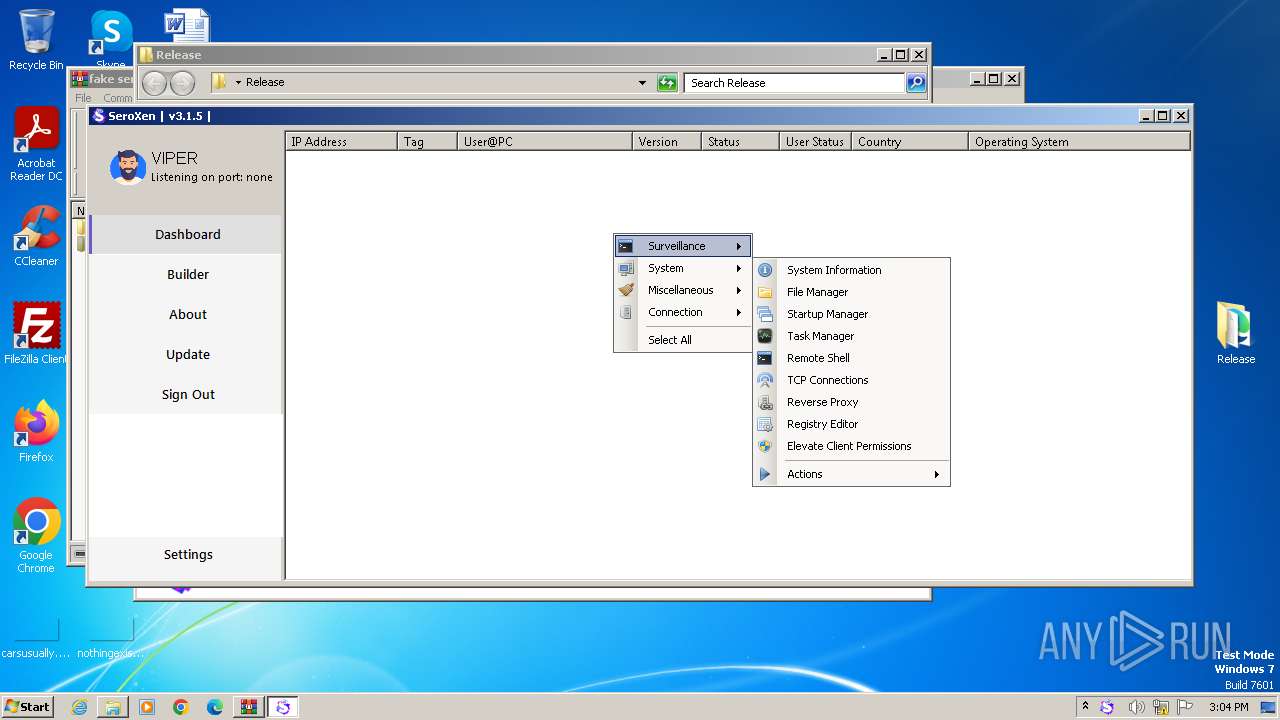
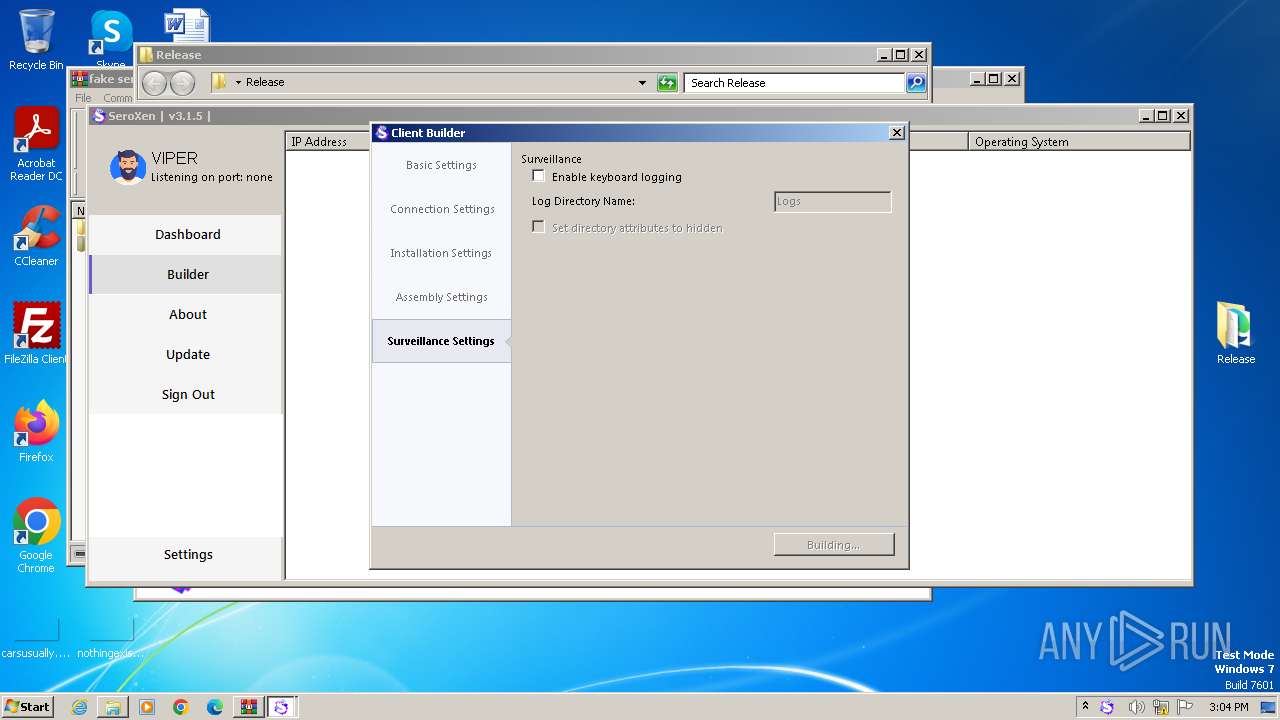
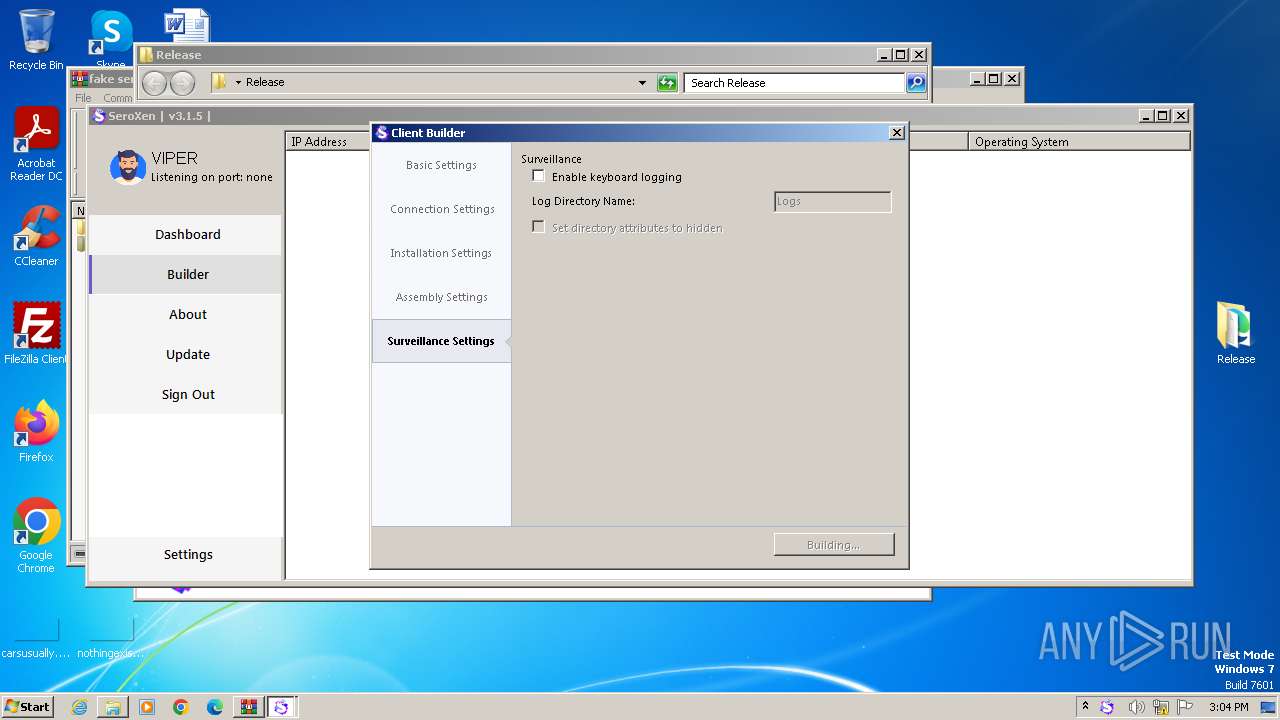
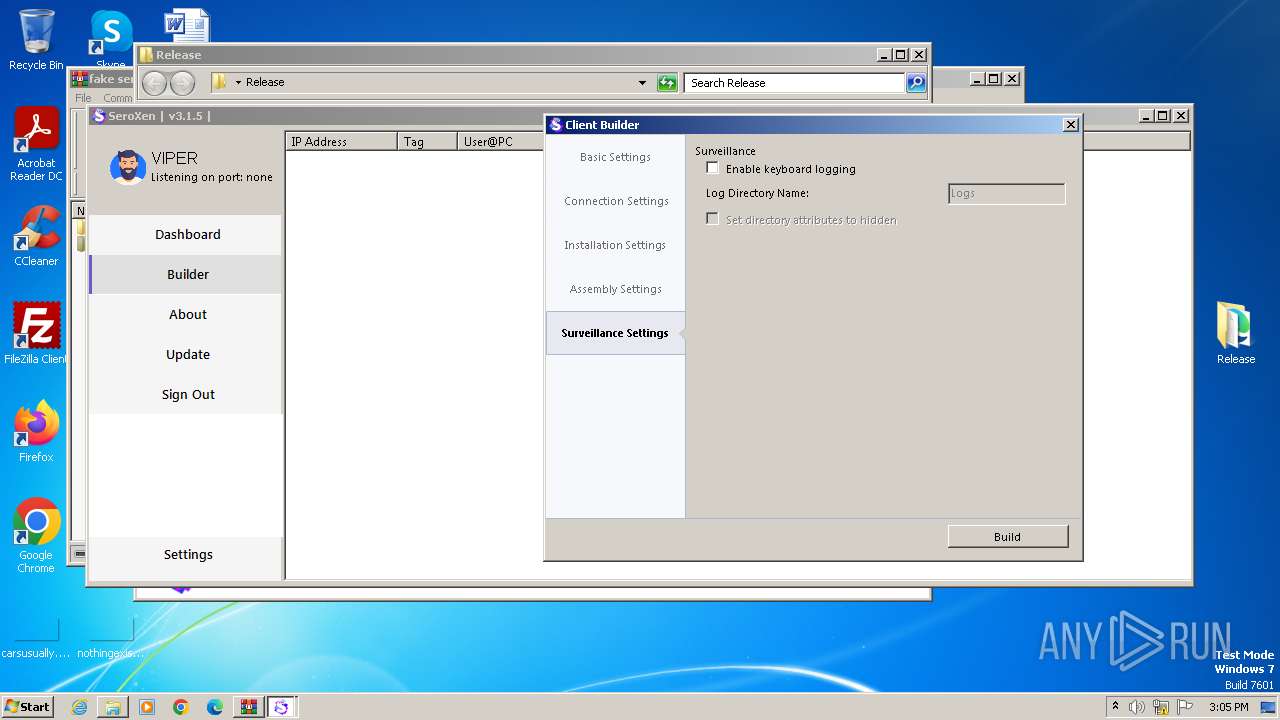
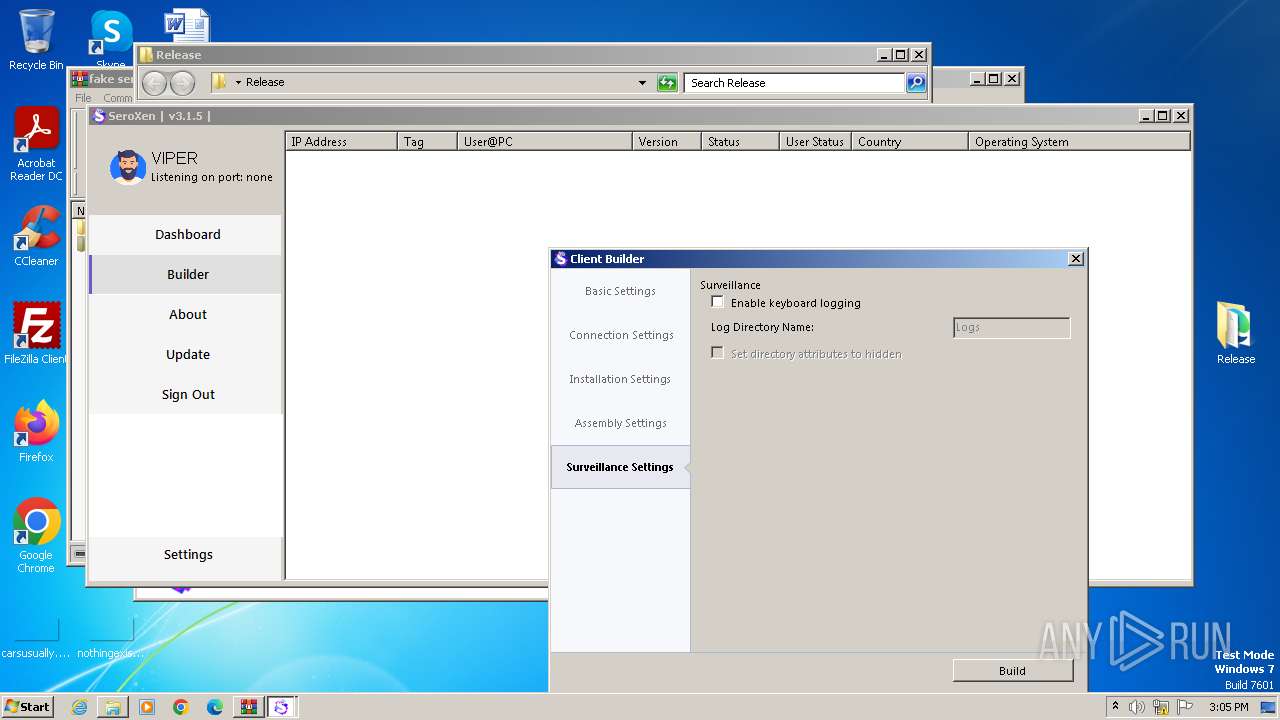
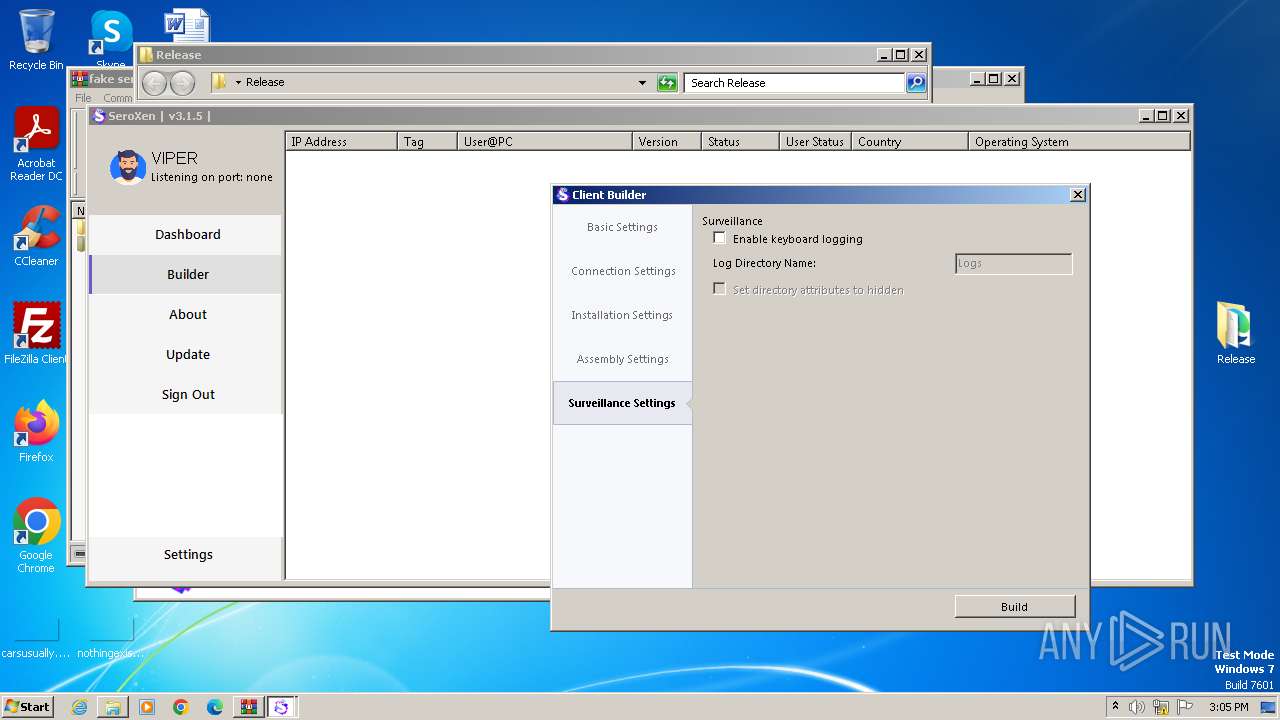
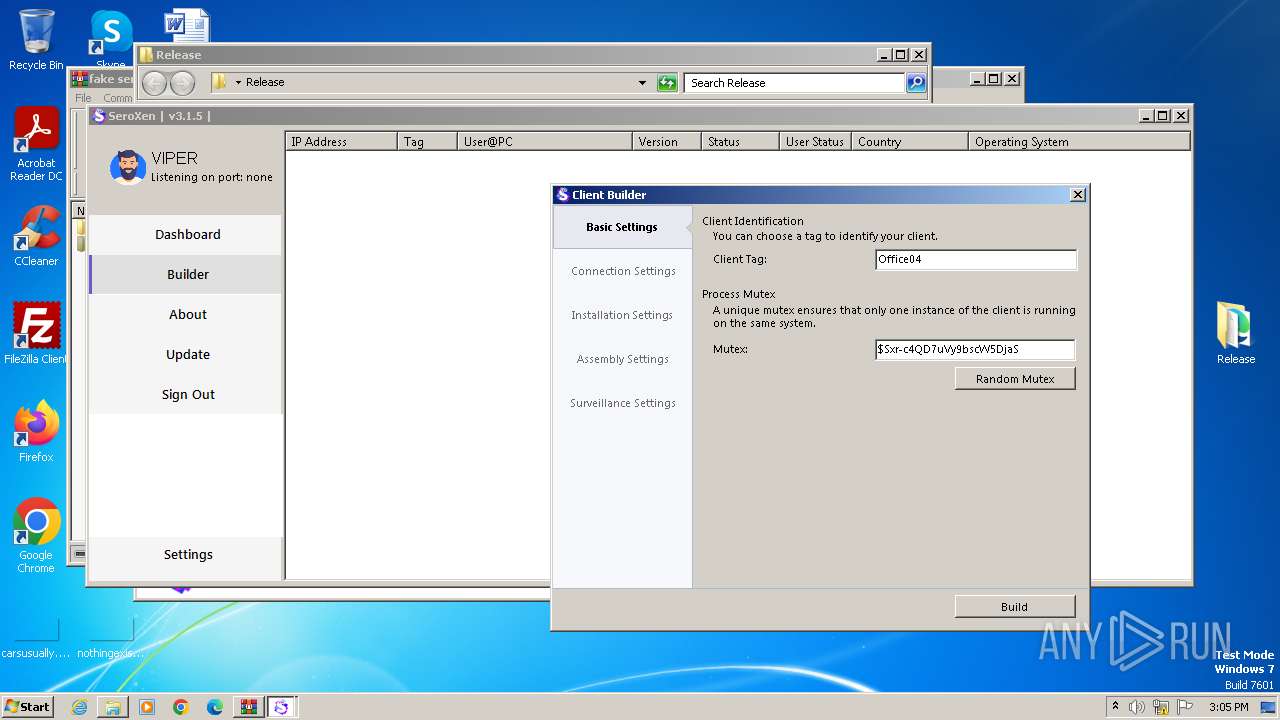
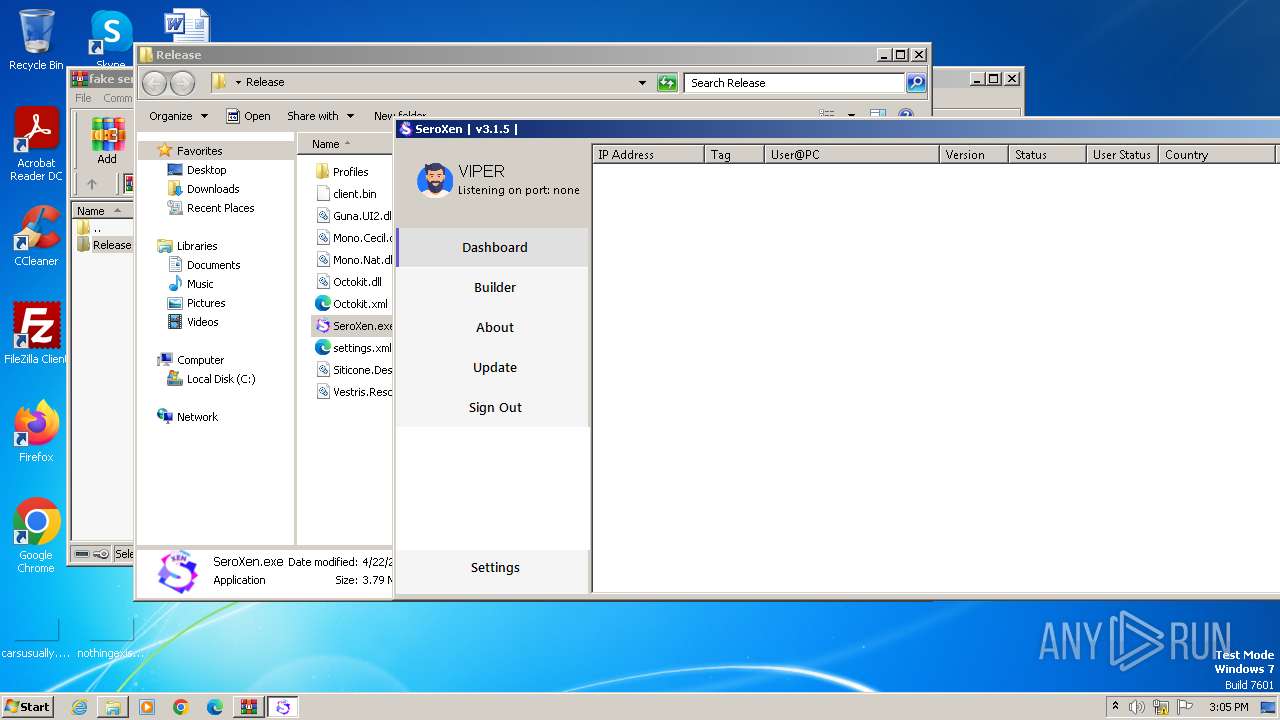
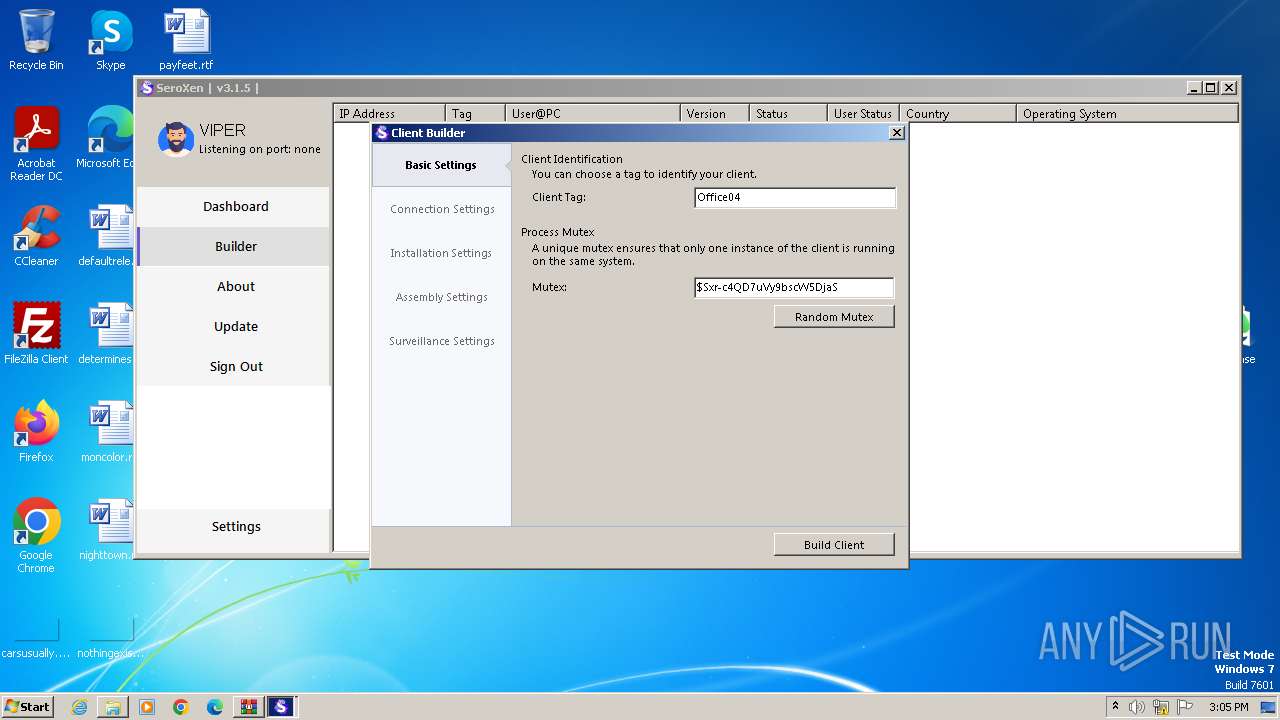
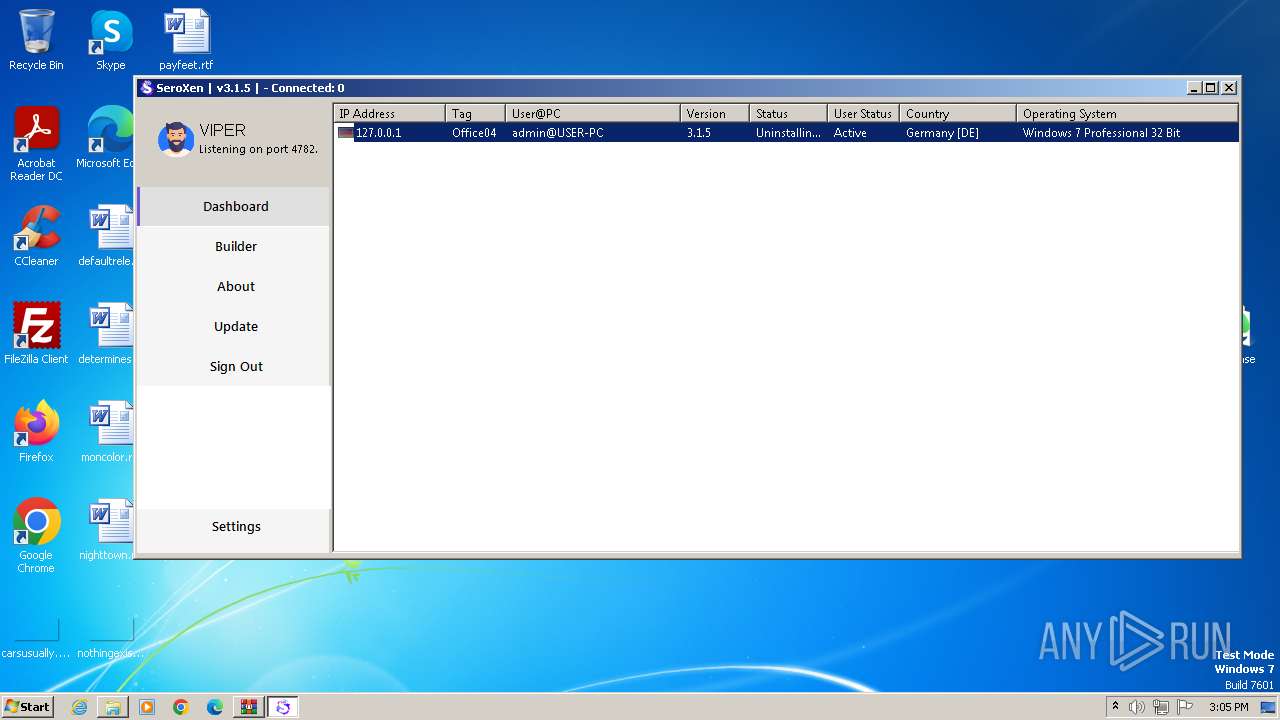
| File name: | fake seroxen.zip |
| Full analysis: | https://app.any.run/tasks/9bb733b5-b3c8-4acd-8f86-745ee34794e1 |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2024, 14:03:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 1D01684673818CAFD6C43F5BB3313F03 |
| SHA1: | 9CA43FC6ED78F49535E38F981110B60358B2313D |
| SHA256: | AE7995D71C7584722F8DA4C96AD645CDF2BDA646BE5B44ADB27D0F345F6FD43D |
| SSDEEP: | 98304:hI7eJTyVC2vO7y4onYmxL4bOEq/5ES4s6zL286/hH2G9lxCmvuKsWiqzSO3d6RzY:AZxtCAE+/ |
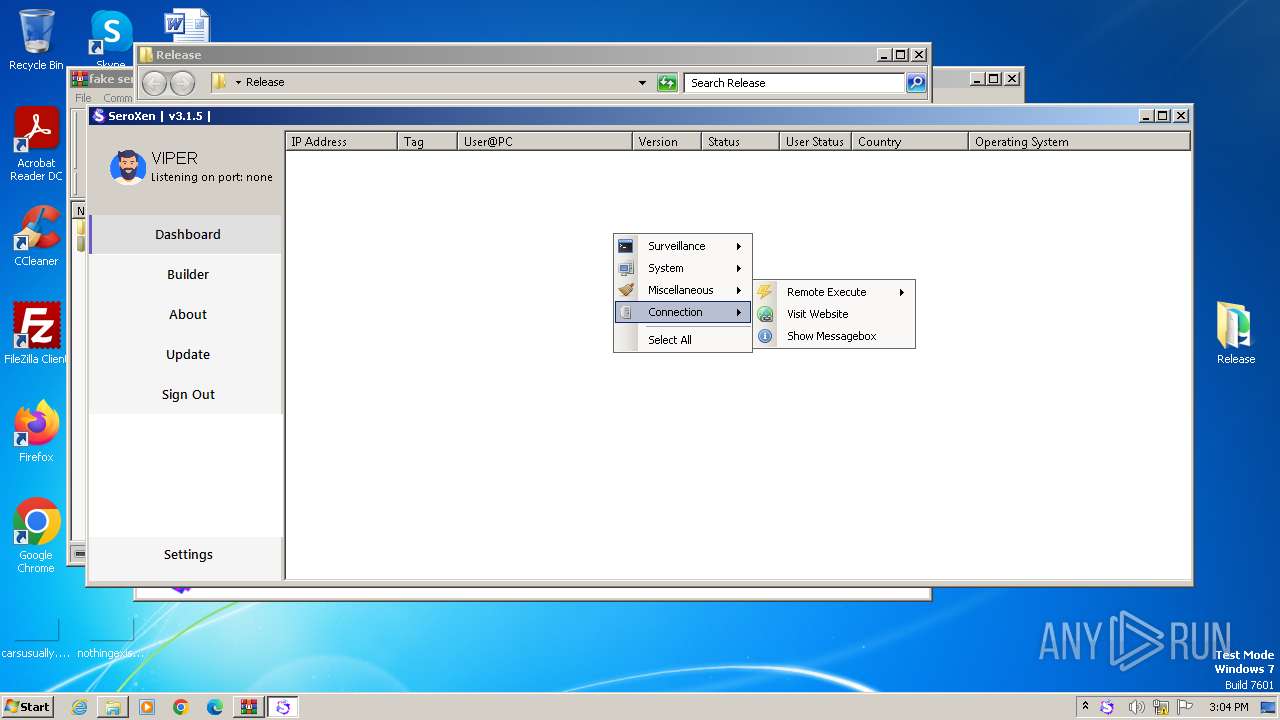
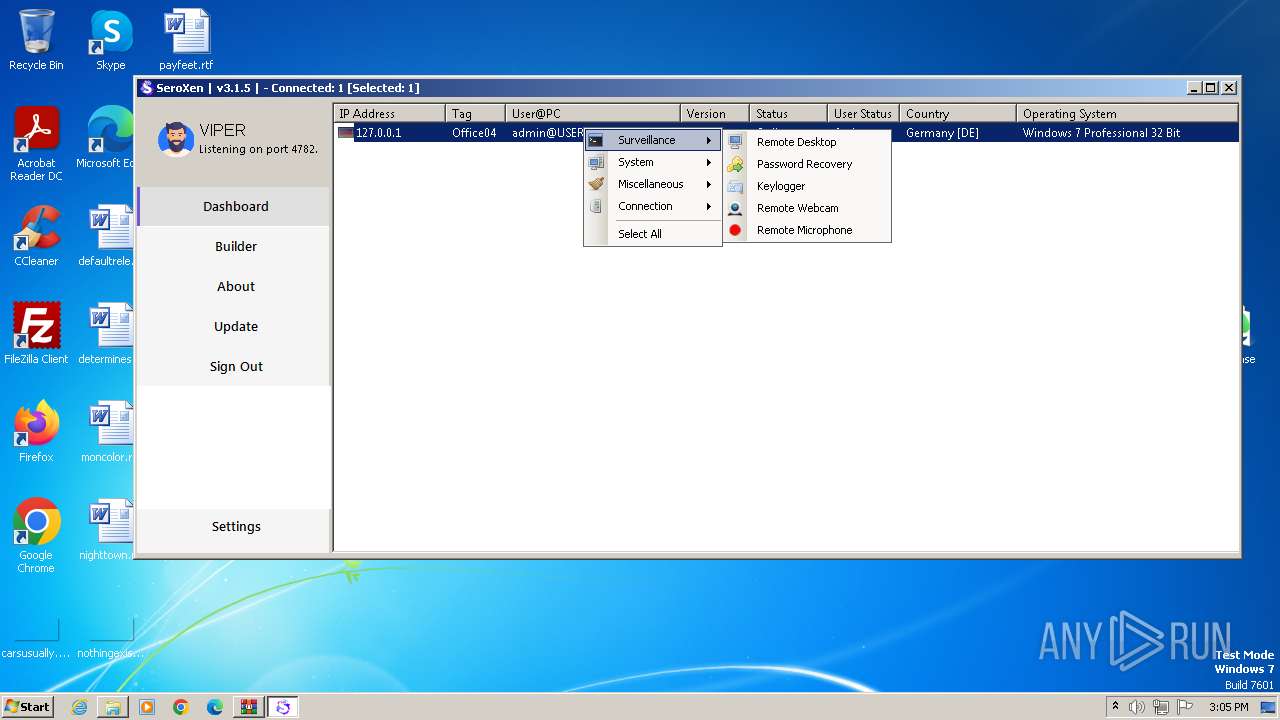
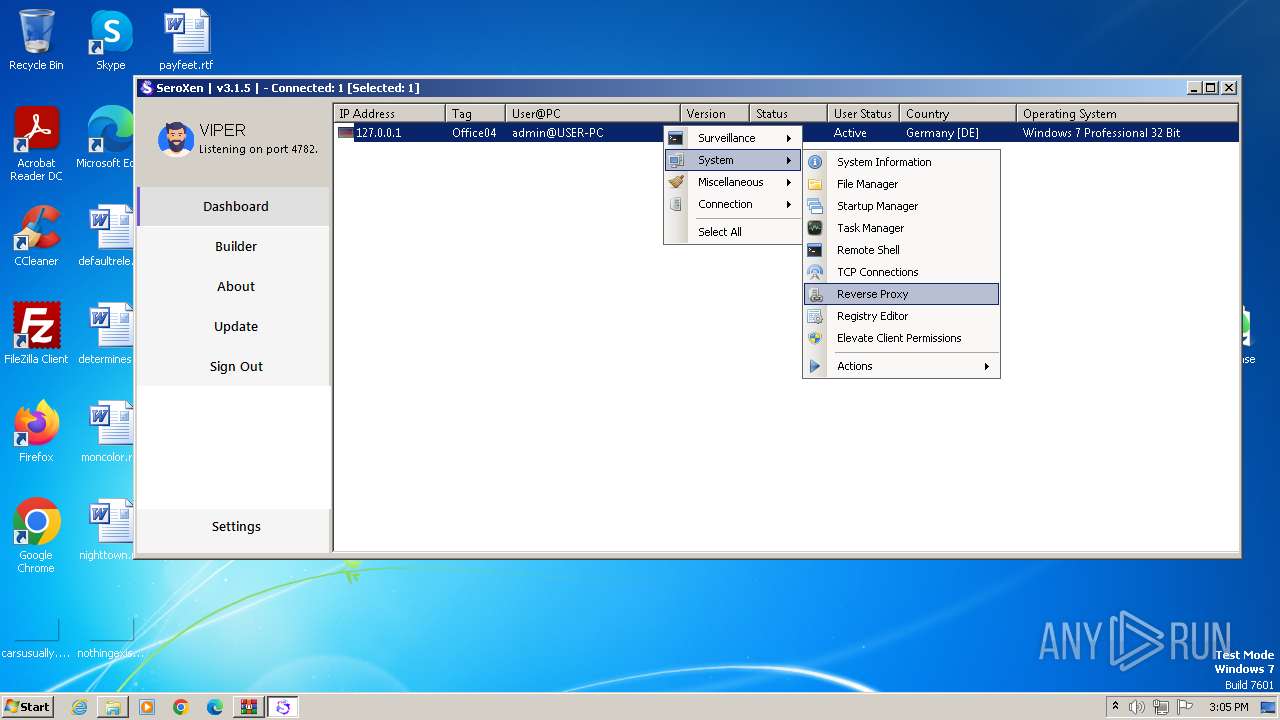
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3996)
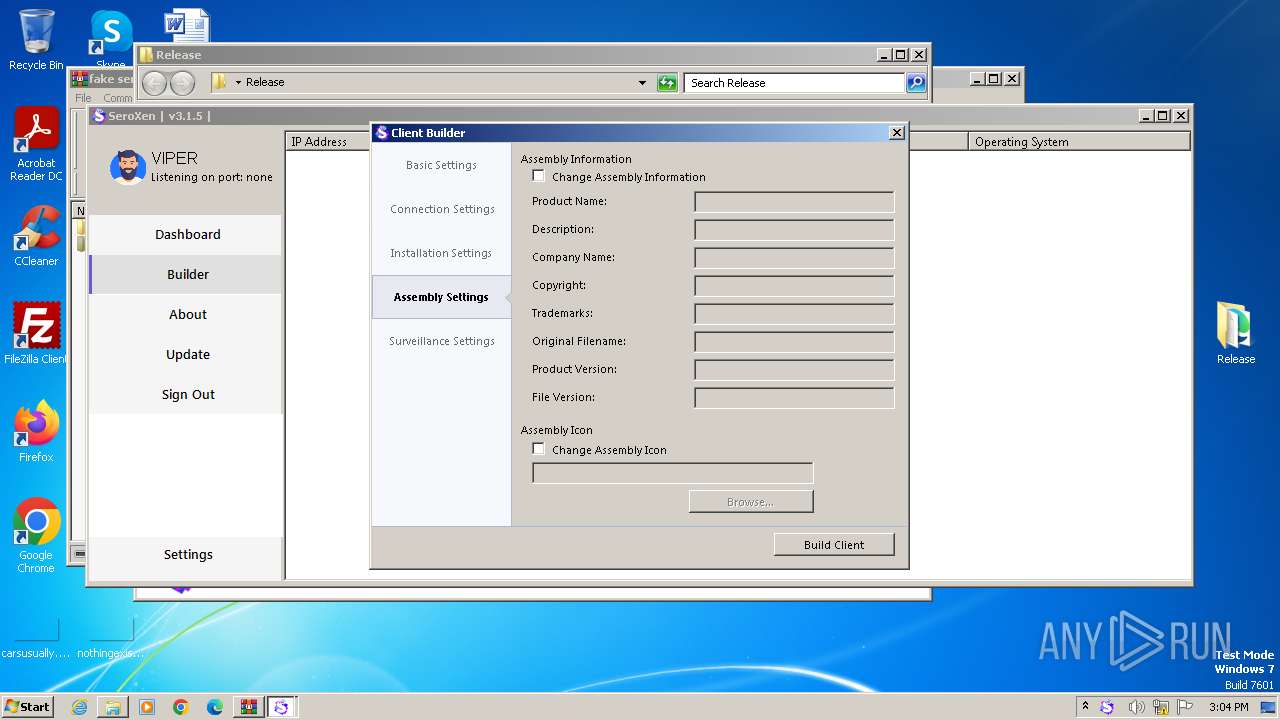
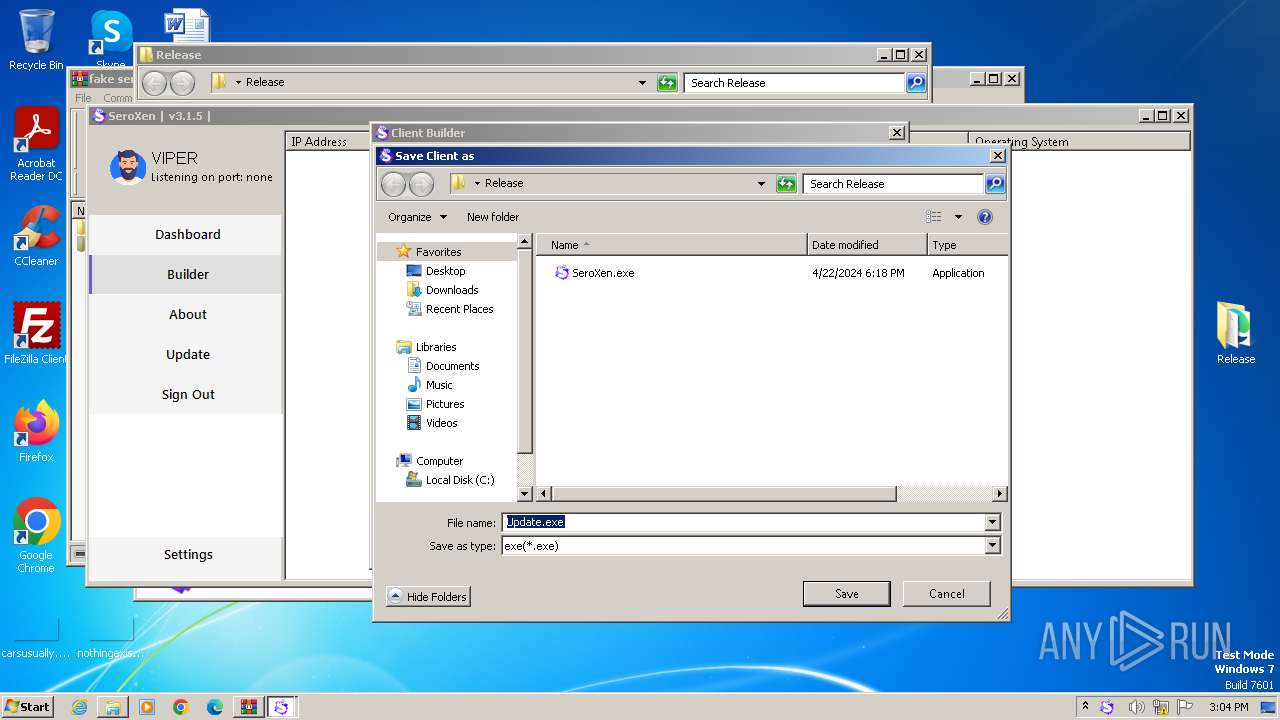
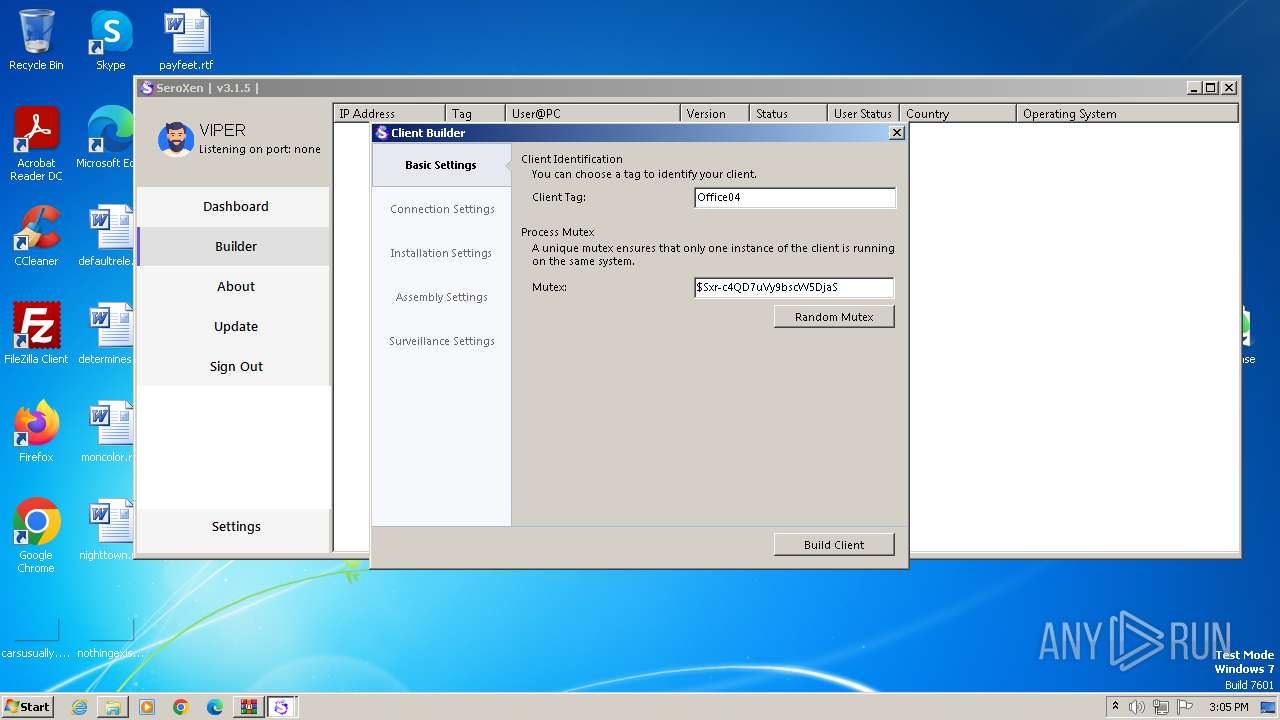
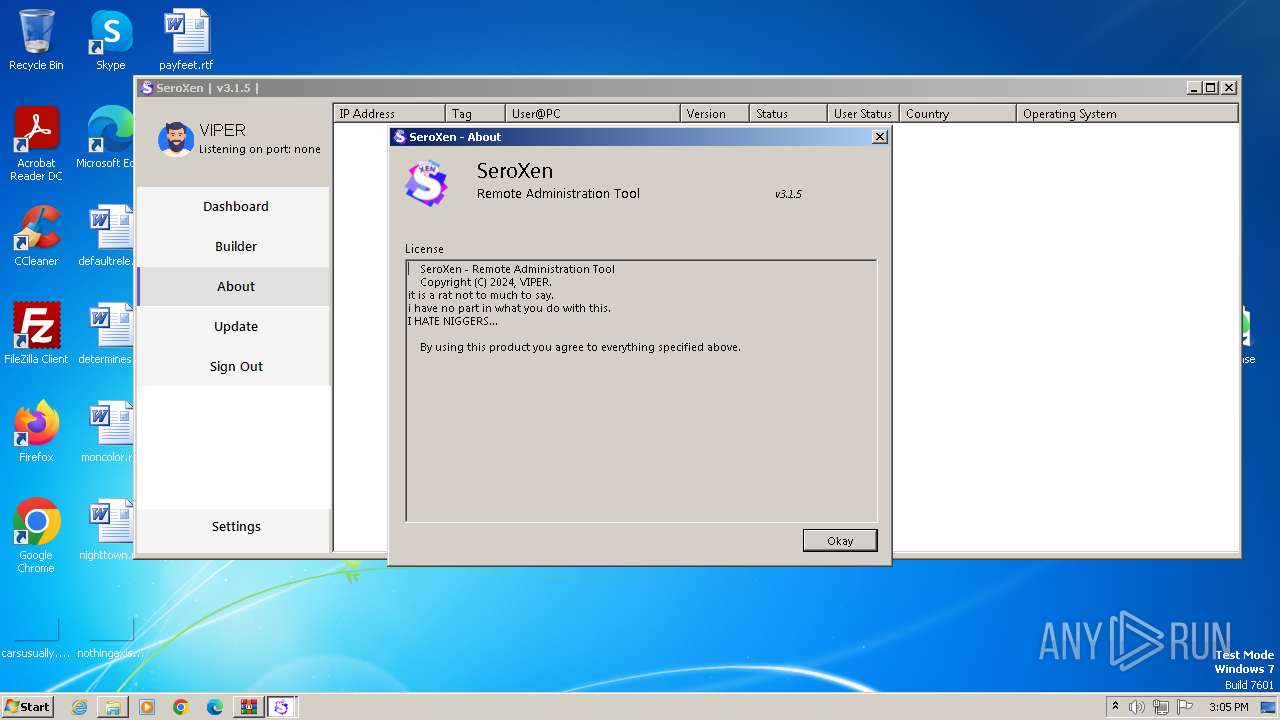
- SeroXen.exe (PID: 4092)
- Update.exe (PID: 728)
Bypass User Account Control (DelegateExecute)
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
SUSPICIOUS
Reads the Internet Settings
- SeroXen.exe (PID: 4092)
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 2484)
Executable content was dropped or overwritten
- SeroXen.exe (PID: 4092)
- Update.exe (PID: 728)
Starts itself from another location
- Update.exe (PID: 728)
Changes default file association
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
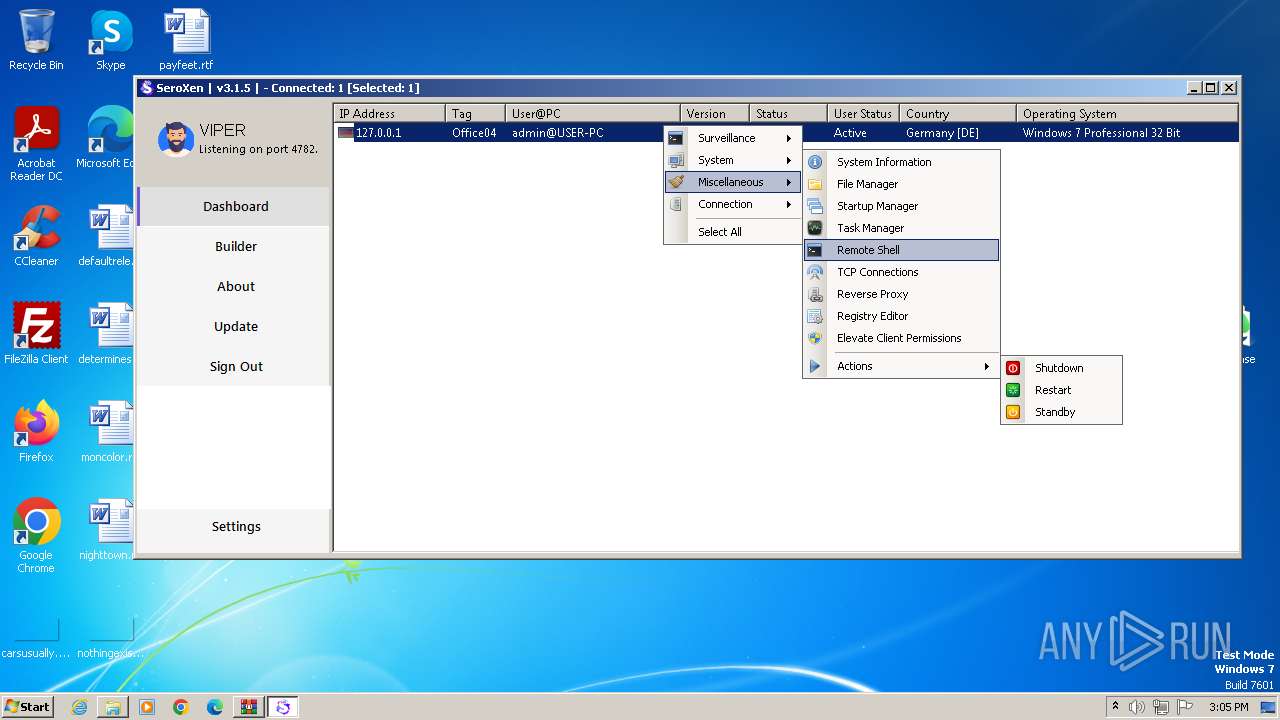
Starts CMD.EXE for commands execution
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
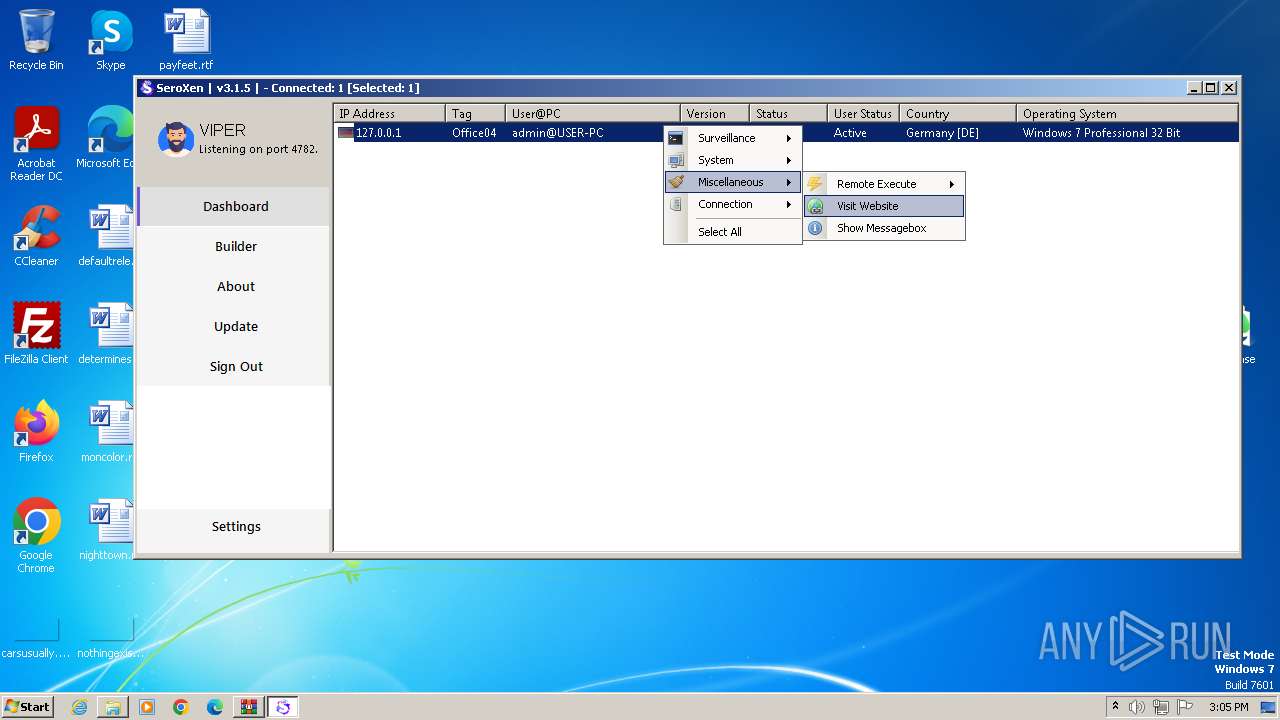
Checks for external IP
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
Device Retrieving External IP Address Detected
- Client.exe (PID: 1948)
Potential Corporate Privacy Violation
- Client.exe (PID: 1948)
Reads security settings of Internet Explorer
- Client.exe (PID: 1948)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 676)
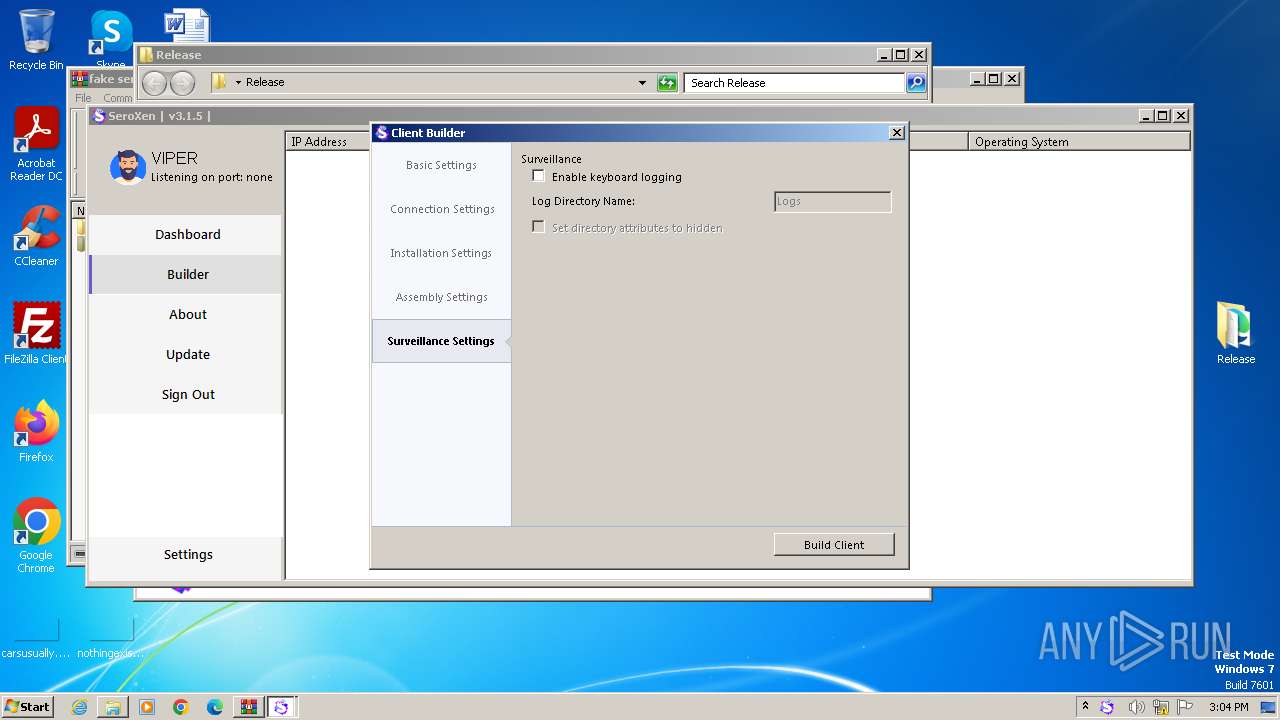
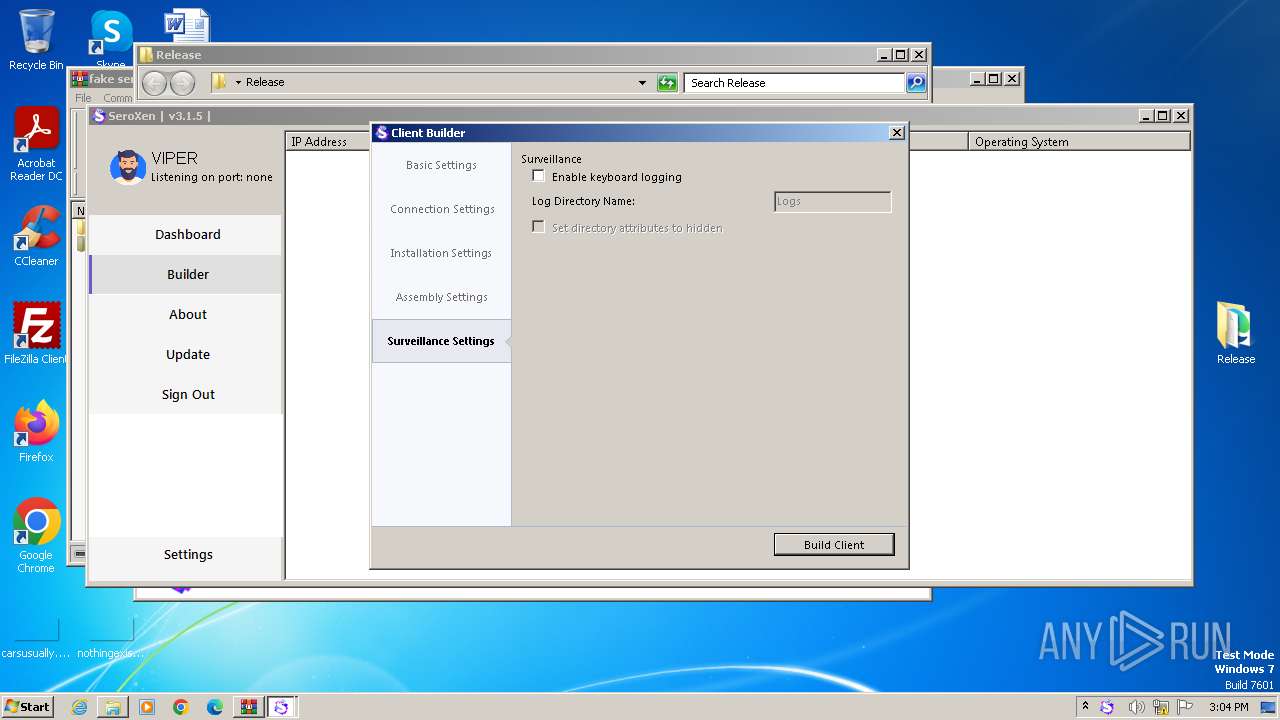
Executing commands from a ".bat" file
- Client.exe (PID: 1948)
Starts application with an unusual extension
- cmd.exe (PID: 676)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3996)
Checks supported languages
- SeroXen.exe (PID: 4092)
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
- wmpnscfg.exe (PID: 736)
- chcp.com (PID: 956)
Reads the computer name
- SeroXen.exe (PID: 4092)
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
- wmpnscfg.exe (PID: 736)
Manual execution by a user
- SeroXen.exe (PID: 4092)
- Update.exe (PID: 728)
- wmpnscfg.exe (PID: 736)
Reads the machine GUID from the registry
- SeroXen.exe (PID: 4092)
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
Reads Environment values
- Update.exe (PID: 728)
- Client.exe (PID: 1948)
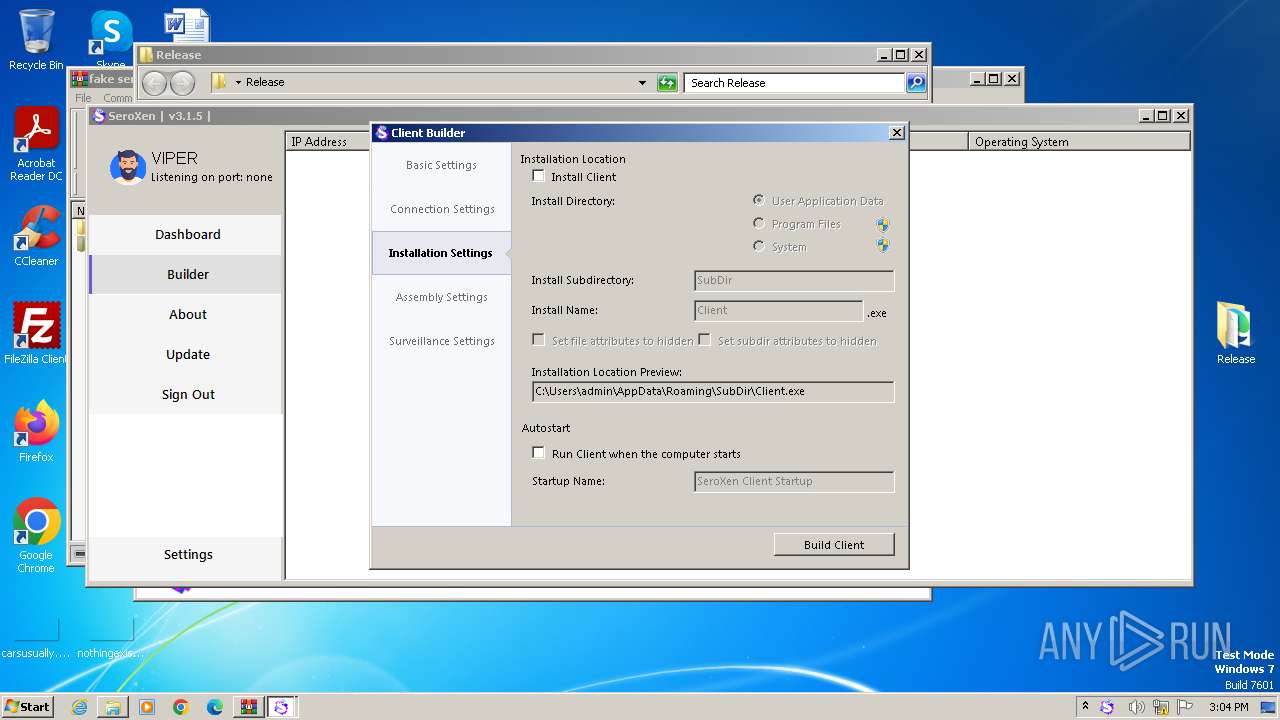
Creates files or folders in the user directory
- Update.exe (PID: 728)
Create files in a temporary directory
- Client.exe (PID: 1948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:04:22 10:18:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Release/ |
Total processes
61
Monitored processes
16
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
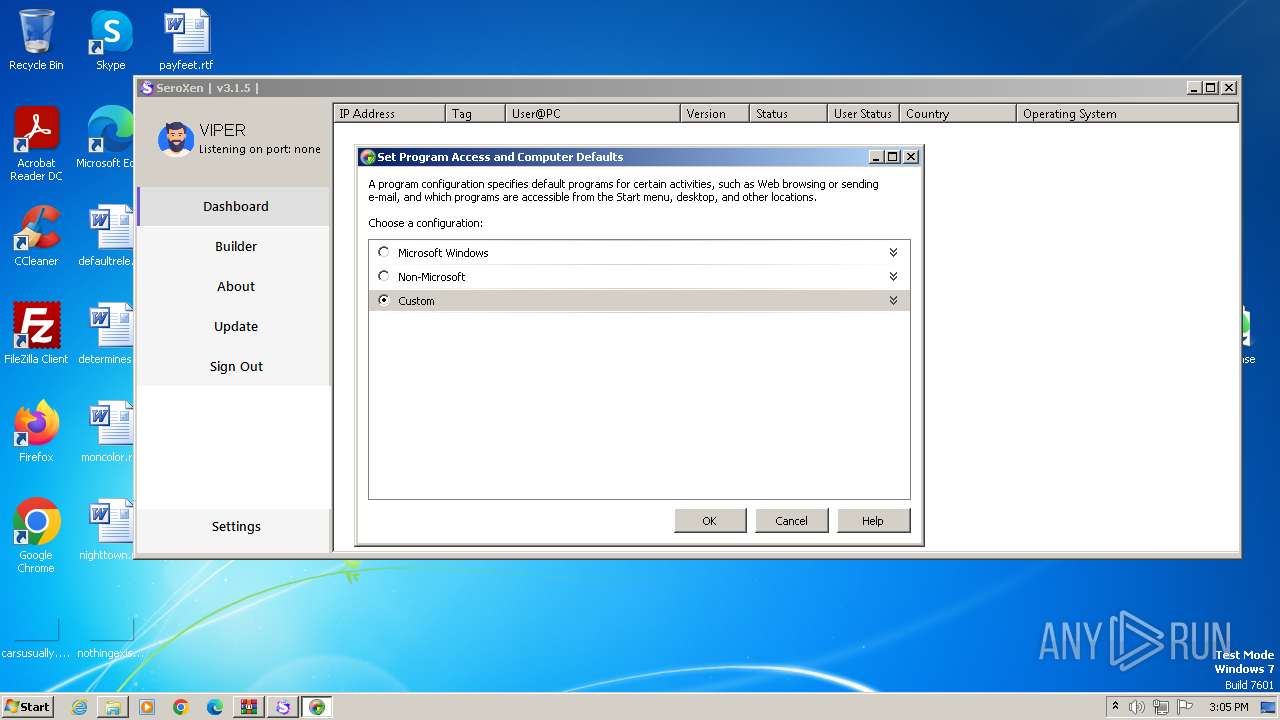
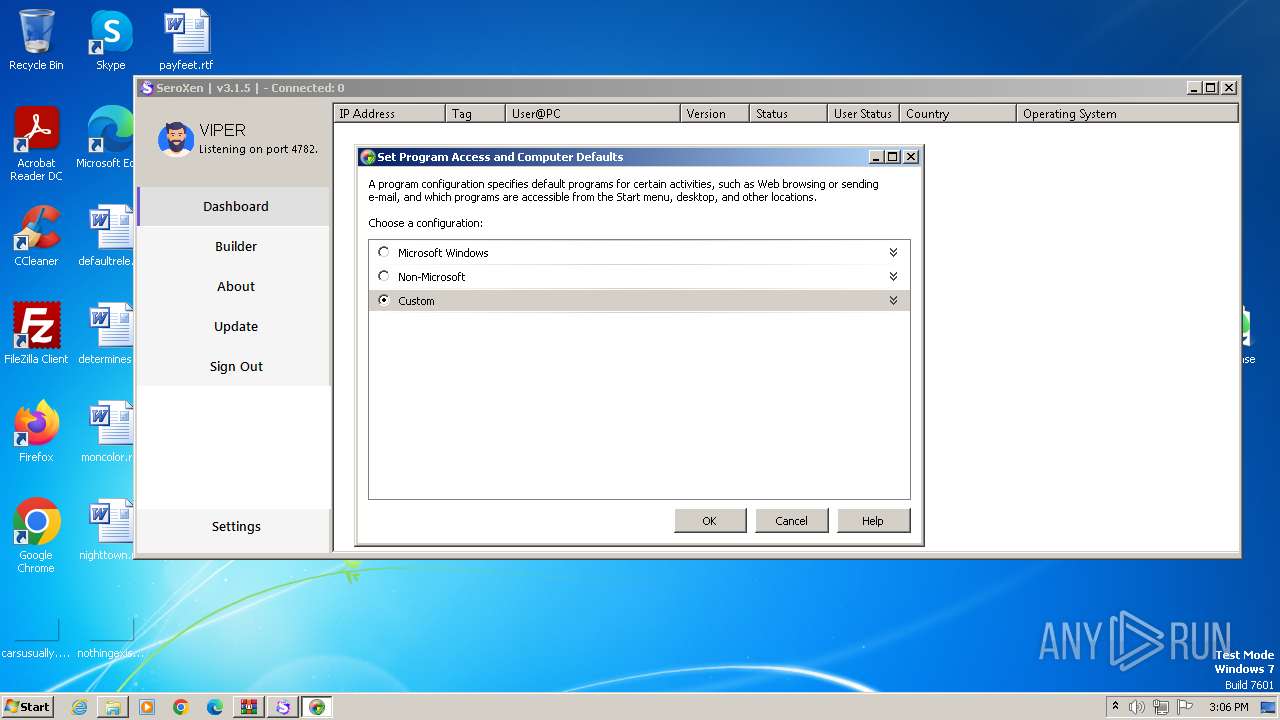
| 580 | computerdefaults.exe | C:\Windows\System32\ComputerDefaults.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Set Program Access and Computer Defaults Control Panel Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 676 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\dTIp2RzHgISi.bat" " | C:\Windows\System32\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
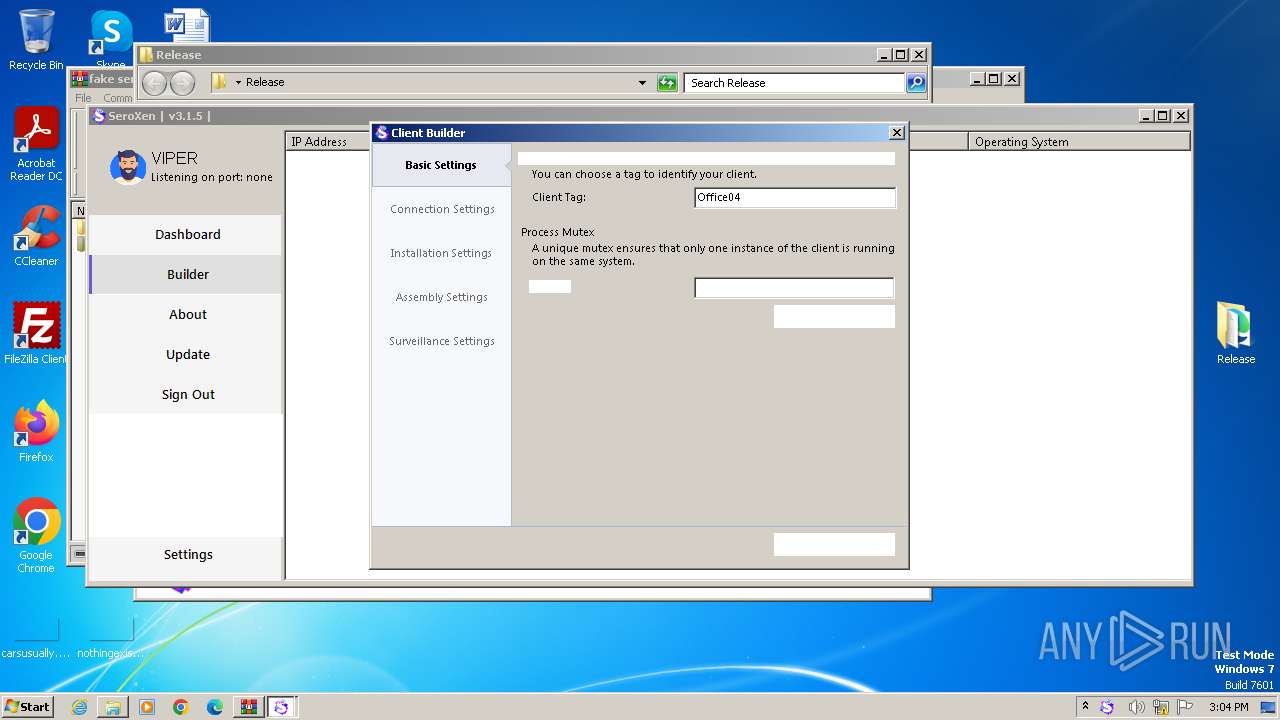
| 728 | "C:\Users\admin\Desktop\Update.exe" | C:\Users\admin\Desktop\Update.exe | explorer.exe | ||||||||||||
User: admin Company: GitHub Integrity Level: MEDIUM Description: Update Exit code: 4294967295 Version: 3.1.5 Modules
| |||||||||||||||
| 736 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 924 | "C:\Windows\system32\ComputerDefaults.exe" | C:\Windows\System32\ComputerDefaults.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Set Program Access and Computer Defaults Control Panel Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 956 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1796 | "cmd.exe" /c start computerdefaults.exe | C:\Windows\System32\cmd.exe | — | Update.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
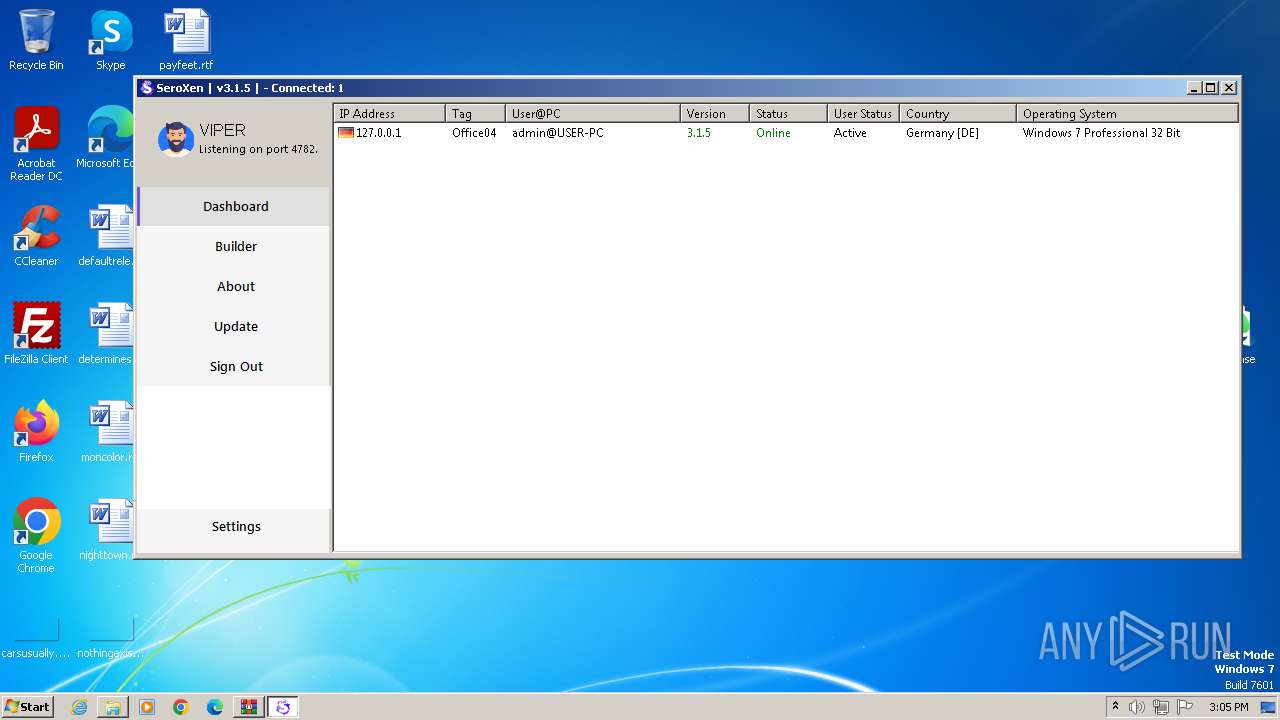
| 1948 | "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | Update.exe | ||||||||||||
User: admin Company: GitHub Integrity Level: MEDIUM Description: Update Exit code: 4294967295 Version: 3.1.5 Modules
| |||||||||||||||
| 2248 | "C:\Windows\system32\ComputerDefaults.exe" | C:\Windows\System32\ComputerDefaults.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Set Program Access and Computer Defaults Control Panel Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
20 783
Read events
20 646
Write events
131
Delete events
6
Modification events
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\fake seroxen.zip | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
10
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
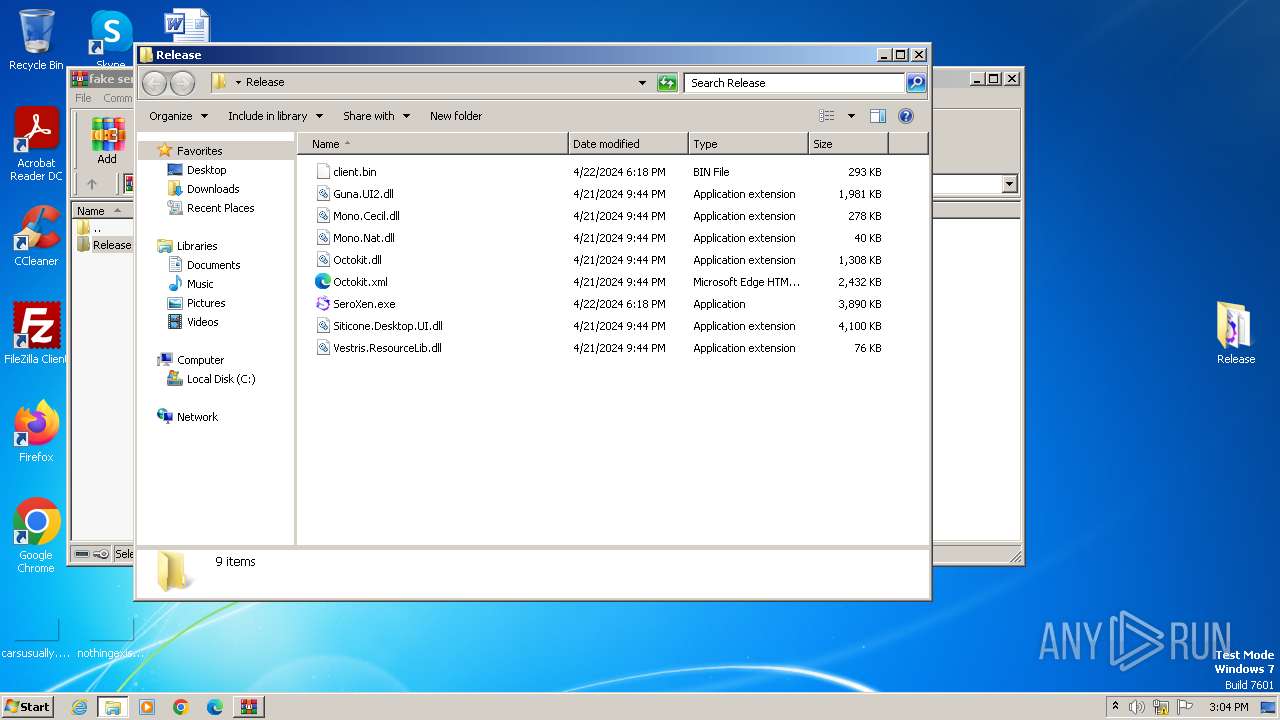
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.35362\Release\Guna.UI2.dll | executable | |
MD5:83E9DF5D534F50280251D662861BF476 | SHA256:836E1CC306EAB0817A10C613A9C99D4DCBD604624B8B90F551D410DC164EEF82 | |||
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.35362\Release\Mono.Nat.dll | executable | |
MD5:BF929442B12D4B5F9906B29834BF7DB1 | SHA256:B33435AC7CDEFCF7C2ADF96738C762A95414EB7A4967EF6B88DCDA14D58BFEE0 | |||
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.35362\Release\SeroXen.exe | executable | |
MD5:E9308E5EF39EF2C9B8E4B72C23ABC690 | SHA256:3097C065663067E0C648F7B78C85119947B636293F7FDDDEEAF51A1BE9D704AF | |||
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.35362\Release\Mono.Cecil.dll | executable | |
MD5:8DF4D6B5DC1629FCEFCDC20210A88EAC | SHA256:3E4288B32006FE8499B43A7F605BB7337931847A0AA79A33217A1D6D1A6C397E | |||
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.35362\Release\client.bin | executable | |
MD5:C5CB7F04D3461EFA49DA4BA79B0295F3 | SHA256:B158F718405A2DF94AD3AAC1B4D695ED2E990D90D4537FC621C8A31D19A6052B | |||
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.35362\Release\Octokit.xml | xml | |
MD5:26A2F8988DE45E32C7C0D022D9EABE0D | SHA256:674C4C92687B1826E6D1E1D6554905C2245BEB06F11CBFC473E2B0A4A90B087B | |||
| 4092 | SeroXen.exe | C:\Users\admin\Desktop\Release\settings.xml | text | |
MD5:6632F523CC273EC7FD960EED89668A10 | SHA256:5252A21898FD0CFE4BEED5A8BFB4BCCF74A7C8C44035BA1EB2AEE9D33E4ED4B4 | |||
| 1948 | Client.exe | C:\Users\admin\AppData\Local\Temp\dTIp2RzHgISi.bat | text | |
MD5:C47DD453E93226D6688993BEFD42BCD4 | SHA256:4304FF824BC93A2E78F84C60C9CF8248D47B7B81D6A05188299D1572B8E69F36 | |||
| 3996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3996.35362\Release\Vestris.ResourceLib.dll | executable | |
MD5:64E9CB25AEEFEEBA3BB579FB1A5559BC | SHA256:34CAB594CE9C9AF8E12A6923FC16468F5B87E168777DB4BE2F04DB883C1DB993 | |||
| 4092 | SeroXen.exe | C:\Users\admin\Desktop\Update.exe | executable | |
MD5:DC571A12BFF7E808F7A210178737677B | SHA256:FF9C4CC2317EAE9FA0FFF4AD345D95ECFB29C318A8FBF4F4D41178BEC02C7121 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
7
DNS requests
1
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
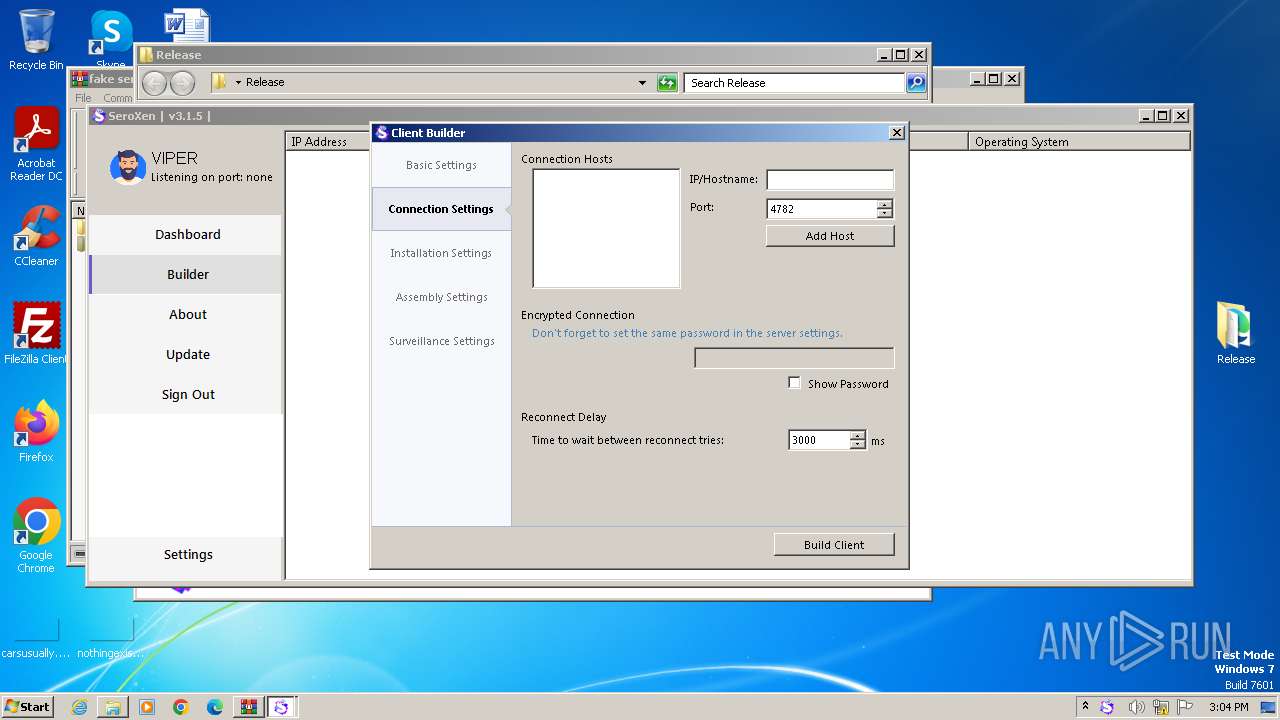
1948 | Client.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | unknown |
728 | Update.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4092 | SeroXen.exe | 192.168.100.2:5351 | — | — | — | whitelisted |
4092 | SeroXen.exe | 239.255.255.250:1900 | — | — | — | unknown |
728 | Update.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
1948 | Client.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | A Network Trojan was detected | ET MALWARE Common RAT Connectivity Check Observed |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
1948 | Client.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1948 | Client.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
1948 | Client.exe | A Network Trojan was detected | ET MALWARE Common RAT Connectivity Check Observed |