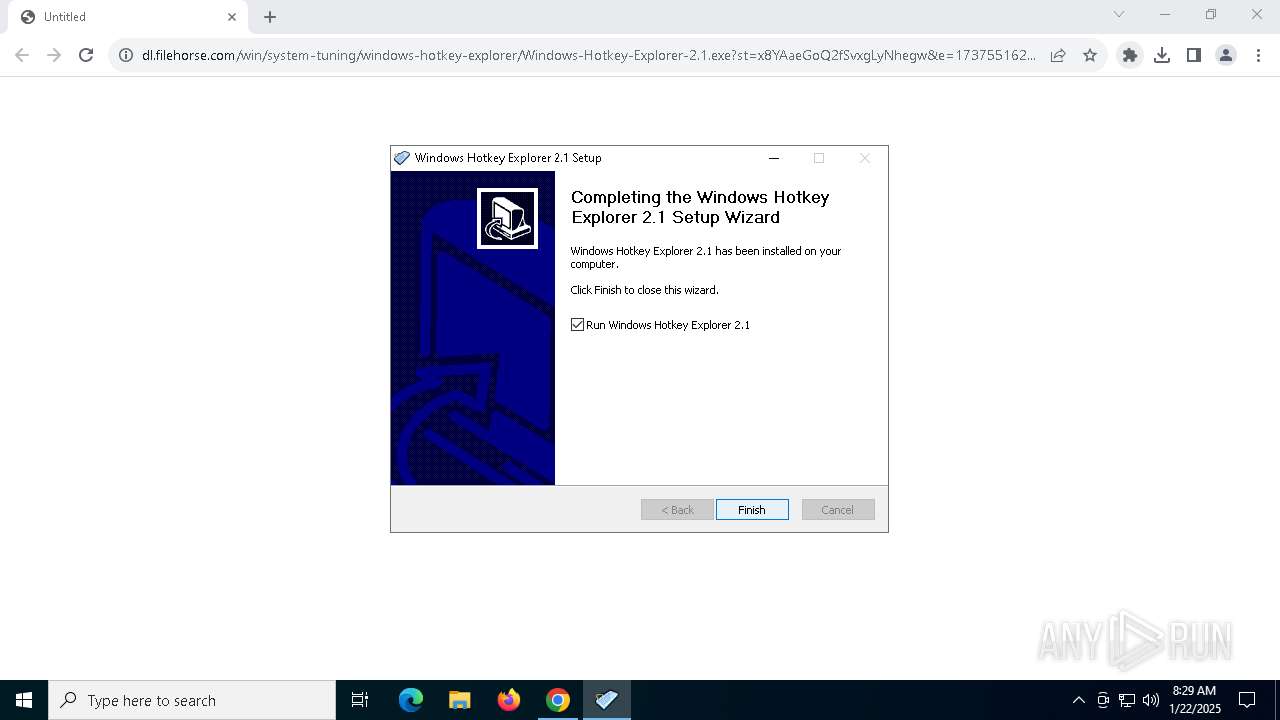
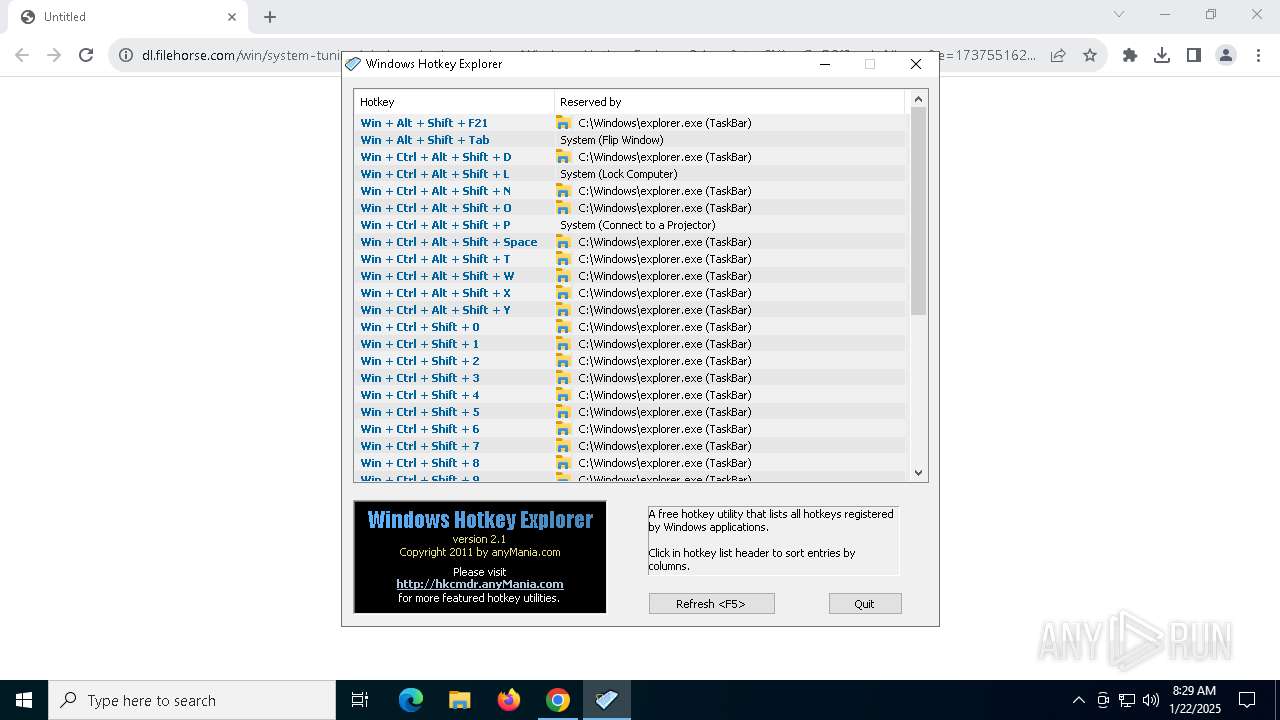
| URL: | https://dl.filehorse.com/win/system-tuning/windows-hotkey-explorer/Windows-Hotkey-Explorer-2.1.exe?st=x8YAaeGoQ2fSvxgLyNhegw&e=1737551623&fn=hkexplr_inst.exe |
| Full analysis: | https://app.any.run/tasks/55be4dc8-5944-4a90-b0fa-a2120e743877 |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2025, 08:28:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 34F381109068B7F5741A02DFEFF02663 |
| SHA1: | D7CCF2EA4BD0046CA1B992655F4E50AB650A5619 |
| SHA256: | AE775F3CBD7F9D0776AAC10E4D0E52B3ECAFD74EDA1462E9B710D155EAF4489F |
| SSDEEP: | 3:N8RtYbGGSM+UudKbOARJVVA5gX/6g6bEHPodClRtUTGfwriRJ:2zYbGFRibJJ3P6g6gHPA+RkGfwrY |
MALICIOUS
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 7576)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- hkexplr_inst (1).exe (PID: 4624)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 1416)
- GameBar.exe (PID: 9096)
- sapisvr.exe (PID: 8652)
- NarratorQuickStart.exe (PID: 6960)
- MicrosoftEdgeUpdate.exe (PID: 7576)
- ShellExperienceHost.exe (PID: 8608)
- MicrosoftEdgeUpdate.exe (PID: 6992)
Malware-specific behavior (creating "System.dll" in Temp)
- hkexplr_inst (1).exe (PID: 4624)
The process creates files with name similar to system file names
- hkexplr_inst (1).exe (PID: 4624)
- WerFault.exe (PID: 10104)
- WerFault.exe (PID: 7004)
Creates a software uninstall entry
- hkexplr_inst (1).exe (PID: 4624)
- setup.exe (PID: 5920)
Executable content was dropped or overwritten
- hkexplr_inst (1).exe (PID: 4624)
- wv237F6.tmp (PID: 10008)
- quickassist.exe (PID: 3436)
- MicrosoftEdgeUpdate.exe (PID: 7576)
- MicrosoftEdge_X64_132.0.2957.115.exe (PID: 10716)
- setup.exe (PID: 5920)
Starts application with an unusual extension
- quickassist.exe (PID: 3436)
Starts a Microsoft application from unusual location
- wv237F6.tmp (PID: 10008)
- MicrosoftEdgeUpdate.exe (PID: 7576)
Process drops legitimate windows executable
- wv237F6.tmp (PID: 10008)
- MicrosoftEdgeUpdate.exe (PID: 7576)
- setup.exe (PID: 5920)
- MicrosoftEdge_X64_132.0.2957.115.exe (PID: 10716)
Reads the date of Windows installation
- sapisvr.exe (PID: 8652)
There is functionality for taking screenshot (YARA)
- hkexplr.exe (PID: 1224)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3608)
- MicrosoftEdgeUpdate.exe (PID: 5960)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 11092)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 9892)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 7576)
Checks Windows Trust Settings
- MicrosoftEdgeUpdate.exe (PID: 6992)
Application launched itself
- setup.exe (PID: 5920)
- MicrosoftEdgeUpdate.exe (PID: 6992)
Searches for installed software
- setup.exe (PID: 5920)
INFO
Creates files in the program directory
- hkexplr_inst (1).exe (PID: 4624)
The process uses the downloaded file
- chrome.exe (PID: 1480)
- chrome.exe (PID: 5092)
- chrome.exe (PID: 7056)
- sapisvr.exe (PID: 8652)
Executable content was dropped or overwritten
- chrome.exe (PID: 1480)
- firefox.exe (PID: 4804)
Checks supported languages
- hkexplr_inst (1).exe (PID: 4624)
- ShellExperienceHost.exe (PID: 1416)
- hkcmdrx64.exe (PID: 6344)
- hkexplr.exe (PID: 1224)
- hkcmdrx64.exe (PID: 1620)
- GameBar.exe (PID: 9096)
- sapisvr.exe (PID: 8652)
- wv237F6.tmp (PID: 10008)
- MicrosoftEdgeUpdate.exe (PID: 7576)
- NarratorQuickStart.exe (PID: 6960)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3608)
- MicrosoftEdgeUpdate.exe (PID: 5960)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 9892)
- MicrosoftEdgeUpdate.exe (PID: 8408)
- MicrosoftEdgeUpdate.exe (PID: 3568)
- ShellExperienceHost.exe (PID: 8608)
- identity_helper.exe (PID: 11092)
- MicrosoftEdge_X64_132.0.2957.115.exe (PID: 10716)
- setup.exe (PID: 5920)
Reads the computer name
- hkexplr_inst (1).exe (PID: 4624)
- hkcmdrx64.exe (PID: 1620)
- ShellExperienceHost.exe (PID: 1416)
- hkcmdrx64.exe (PID: 6344)
- hkexplr.exe (PID: 1224)
- sapisvr.exe (PID: 8652)
- GameBar.exe (PID: 9096)
- MicrosoftEdgeUpdate.exe (PID: 7576)
- NarratorQuickStart.exe (PID: 6960)
- MicrosoftEdgeUpdate.exe (PID: 5960)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 9892)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 11092)
- MicrosoftEdgeUpdate.exe (PID: 8408)
- MicrosoftEdgeUpdate.exe (PID: 3568)
- MicrosoftEdgeUpdate.exe (PID: 6992)
- ShellExperienceHost.exe (PID: 8608)
- identity_helper.exe (PID: 11092)
- MicrosoftEdge_X64_132.0.2957.115.exe (PID: 10716)
- setup.exe (PID: 5920)
Manual execution by a user
- msedge.exe (PID: 5252)
- rundll32.exe (PID: 6824)
- firefox.exe (PID: 4164)
- osk.exe (PID: 4308)
- sapisvr.exe (PID: 7484)
- osk.exe (PID: 7748)
- msedge.exe (PID: 7956)
- quickassist.exe (PID: 3436)
- sapisvr.exe (PID: 8652)
- quickassist.exe (PID: 7360)
Create files in a temporary directory
- hkexplr_inst (1).exe (PID: 4624)
- wv237F6.tmp (PID: 10008)
- quickassist.exe (PID: 3436)
- MicrosoftEdgeUpdate.exe (PID: 7576)
Creates files or folders in the user directory
- hkexplr_inst (1).exe (PID: 4624)
- quickassist.exe (PID: 3436)
- WerFault.exe (PID: 10104)
- WerFault.exe (PID: 7004)
- ShellExperienceHost.exe (PID: 8608)
- MicrosoftEdgeUpdate.exe (PID: 6992)
- setup.exe (PID: 3508)
- setup.exe (PID: 5920)
- MicrosoftEdge_X64_132.0.2957.115.exe (PID: 10716)
Application launched itself
- chrome.exe (PID: 1480)
- firefox.exe (PID: 4164)
- firefox.exe (PID: 4804)
- msedge.exe (PID: 5252)
Reads security settings of Internet Explorer
- quickassist.exe (PID: 3436)
- HelpPane.exe (PID: 8596)
Reads the software policy settings
- quickassist.exe (PID: 3436)
- HelpPane.exe (PID: 8596)
- WerFault.exe (PID: 10104)
- MicrosoftEdgeUpdate.exe (PID: 8408)
- MicrosoftEdgeUpdate.exe (PID: 6992)
Checks proxy server information
- quickassist.exe (PID: 3436)
- WerFault.exe (PID: 10104)
- WerFault.exe (PID: 7004)
- MicrosoftEdgeUpdate.exe (PID: 8408)
- MicrosoftEdgeUpdate.exe (PID: 6992)
The sample compiled with english language support
- quickassist.exe (PID: 3436)
- wv237F6.tmp (PID: 10008)
- MicrosoftEdgeUpdate.exe (PID: 7576)
- setup.exe (PID: 5920)
- MicrosoftEdge_X64_132.0.2957.115.exe (PID: 10716)
Process checks computer location settings
- ShellExperienceHost.exe (PID: 1416)
- sapisvr.exe (PID: 8652)
- ShellExperienceHost.exe (PID: 8608)
- setup.exe (PID: 5920)
Reads the machine GUID from the registry
- ShellExperienceHost.exe (PID: 1416)
- MicrosoftEdgeUpdate.exe (PID: 6992)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 8408)
- identity_helper.exe (PID: 11092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
294
Monitored processes
107
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{60A90A2F-858D-42AF-8929-82BE9D99E8A1} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5496 --field-trial-handle=1864,i,850654234730832726,16875704735457903759,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1224 | "C:\Program Files (x86)\hkexplr\hkexplr.exe" | C:\Program Files (x86)\hkexplr\hkexplr.exe | — | hkexplr_inst (1).exe | |||||||||||
User: admin Company: anyMania.com Integrity Level: HIGH Description: Windows Hotkey Explorer Version: 2, 1, 0, 0 Modules
| |||||||||||||||
| 1292 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4292 -childID 2 -isForBrowser -prefsHandle 4284 -prefMapHandle 2972 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1320 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8f1e42b9-4bb2-4fd8-8033-ed507f9e81b1} 4804 "\\.\pipe\gecko-crash-server-pipe.4804" 1f2fc165a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1416 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Exit code: 3221226525 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://dl.filehorse.com/win/system-tuning/windows-hotkey-explorer/Windows-Hotkey-Explorer-2.1.exe?st=x8YAaeGoQ2fSvxgLyNhegw&e=1737551623&fn=hkexplr_inst.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1620 | "C:\Program Files (x86)\hkexplr\hkcmdrx64.exe" -Embedding | C:\Program Files (x86)\hkexplr\hkcmdrx64.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Description: hkcmdrx64 Module Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2372 --field-trial-handle=2092,i,1986937962120770296,4509674728052072728,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3124 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7932 --field-trial-handle=2092,i,1986937962120770296,4509674728052072728,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3436 | "C:\WINDOWS\system32\quickassist.exe" ms-quick-assist: | C:\Windows\System32\quickassist.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Quick Assist Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
64 132
Read events
58 780
Write events
5 279
Delete events
73
Modification events
| (PID) Process: | (1480) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1480) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1480) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1480) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1480) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7056) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000063CCCEB3A76CDB01 | |||
| (PID) Process: | (4624) hkexplr_inst (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Windows Hotkey Explorer |
| Operation: | write | Name: | DisplayName |
Value: Windows Hotkey Explorer | |||
| (PID) Process: | (4624) hkexplr_inst (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Windows Hotkey Explorer |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\hkexplr\uninstall.exe" | |||
| (PID) Process: | (4624) hkexplr_inst (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Windows Hotkey Explorer |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (4624) hkexplr_inst (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Windows Hotkey Explorer |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
264
Suspicious files
1 091
Text files
226
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF138485.TMP | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF138485.TMP | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF138495.TMP | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF138495.TMP | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1384c3.TMP | — | |
MD5:— | SHA256:— | |||
| 1480 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1384c3.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
93
TCP/UDP connections
213
DNS requests
298
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4804 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5256 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6100 | SystemSettings.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5256 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6100 | SystemSettings.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4804 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
4804 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
3436 | quickassist.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3436 | quickassist.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.21.65.154:443 | — | Akamai International B.V. | NL | unknown |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1576 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1480 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6472 | chrome.exe | 95.211.20.181:443 | dl.filehorse.com | LeaseWeb Netherlands B.V. | NL | malicious |
6472 | chrome.exe | 142.250.110.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6472 | chrome.exe | 216.58.206.78:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
1176 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
dl.filehorse.com |
| malicious |
accounts.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
10348 | svchost.exe | Misc activity | ET INFO Packed Executable Download |
7380 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7380 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
7380 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7380 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
Process | Message |
|---|---|
quickassist.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|