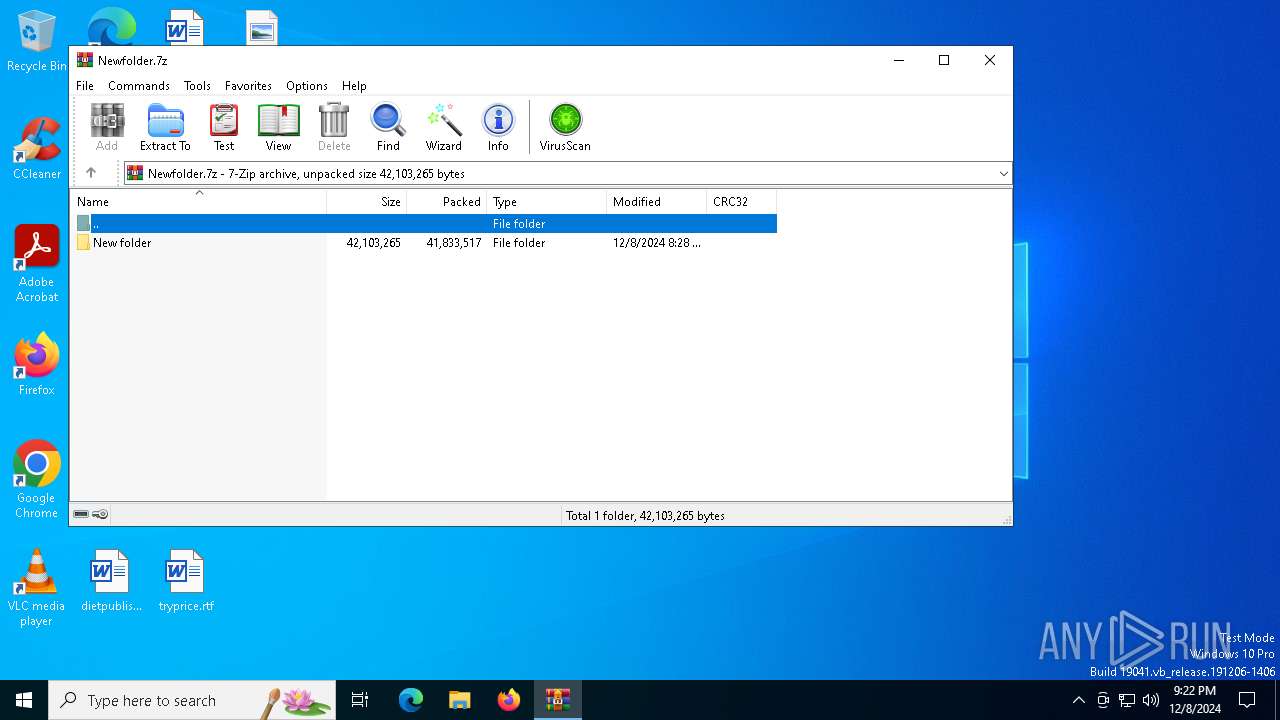
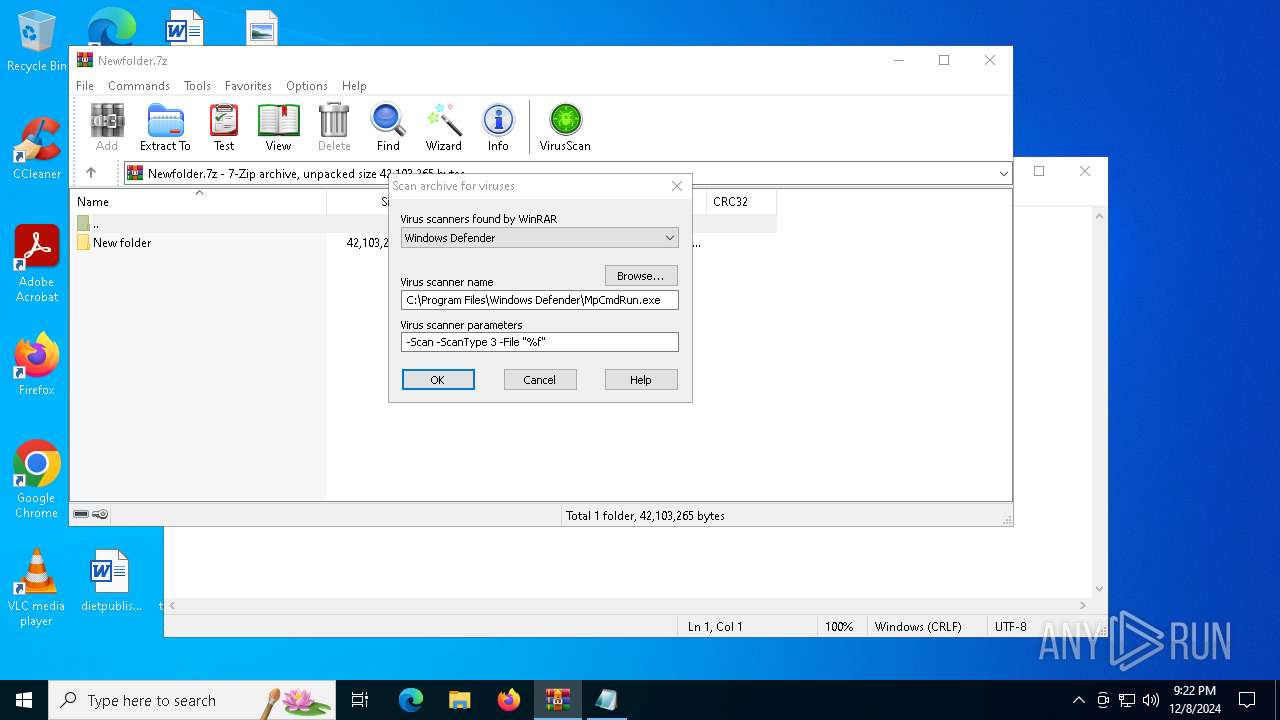
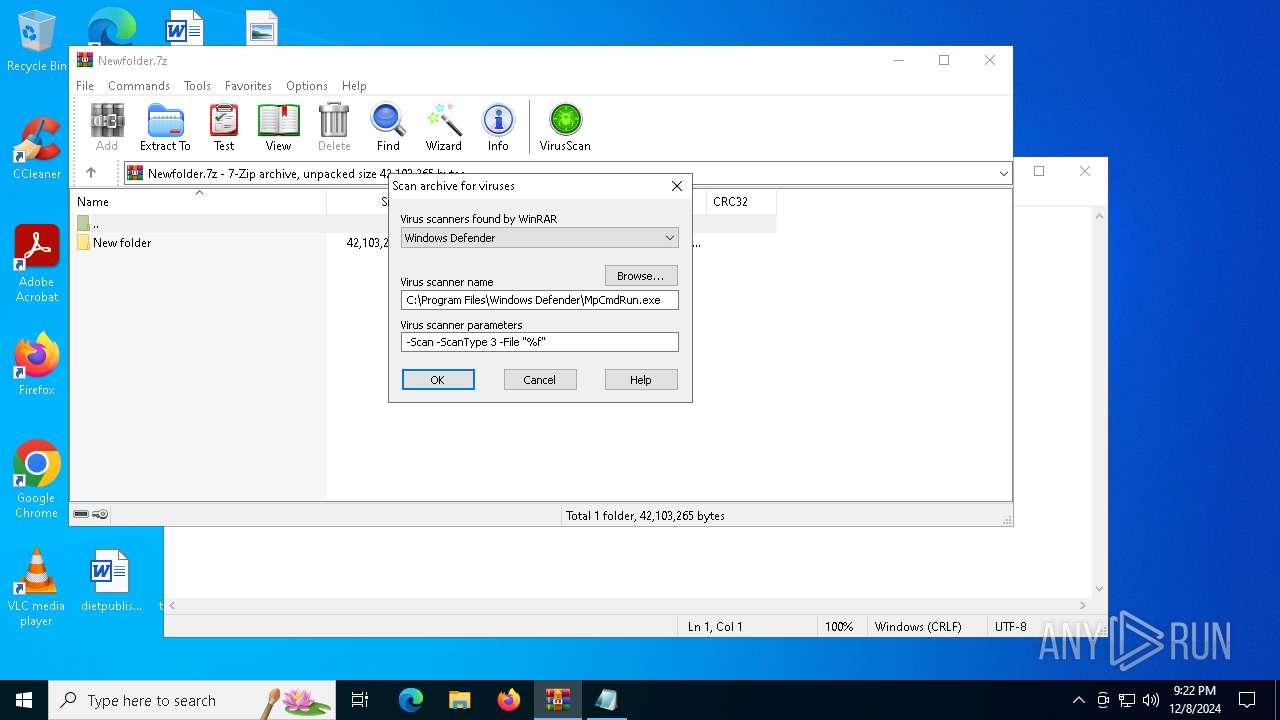
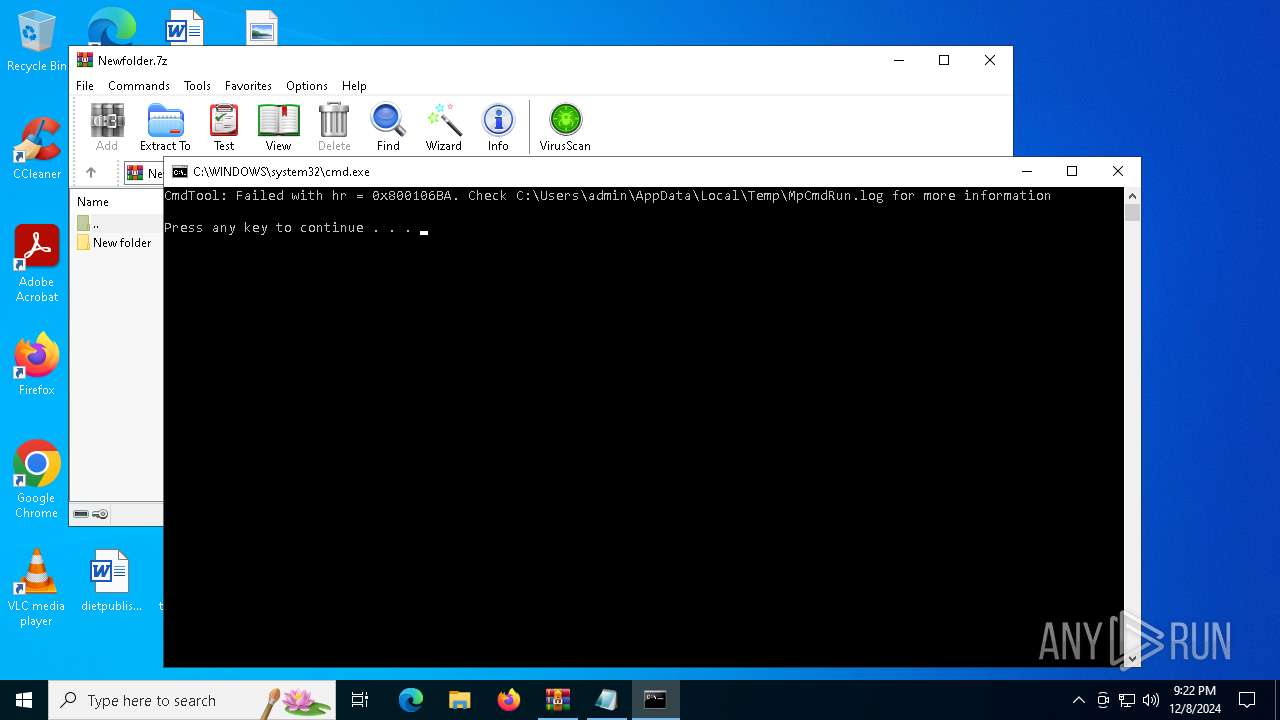
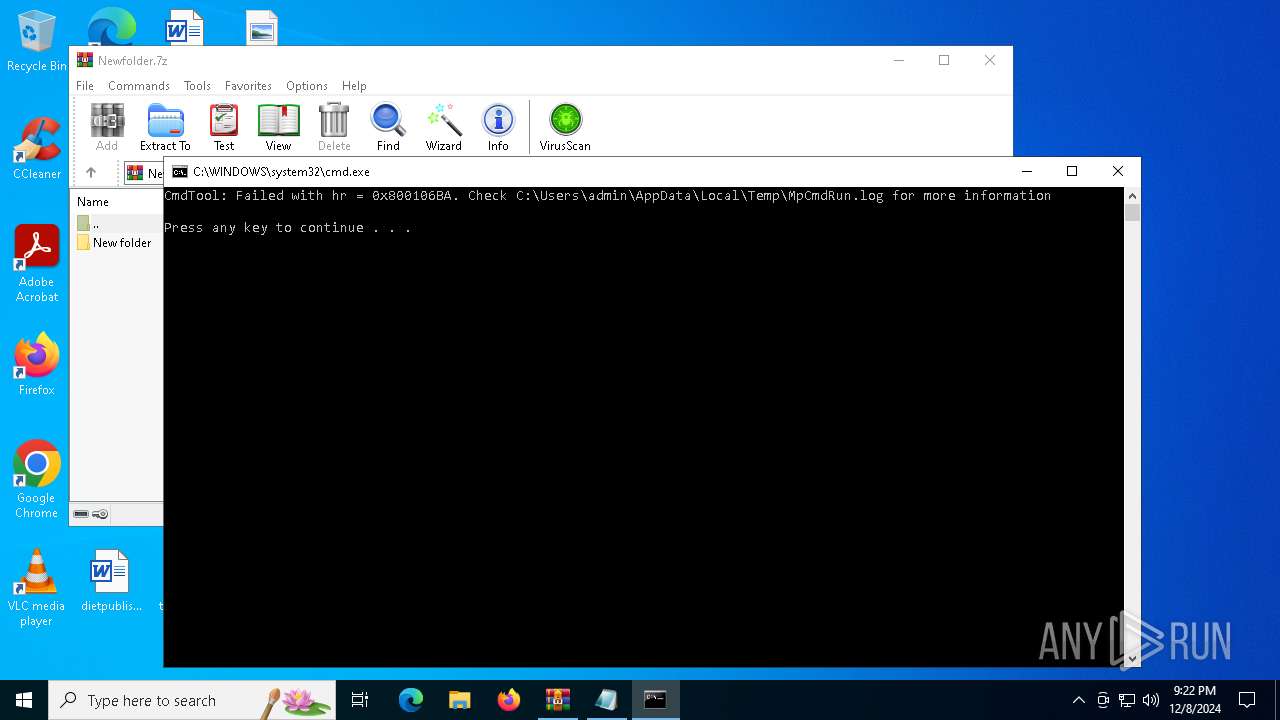
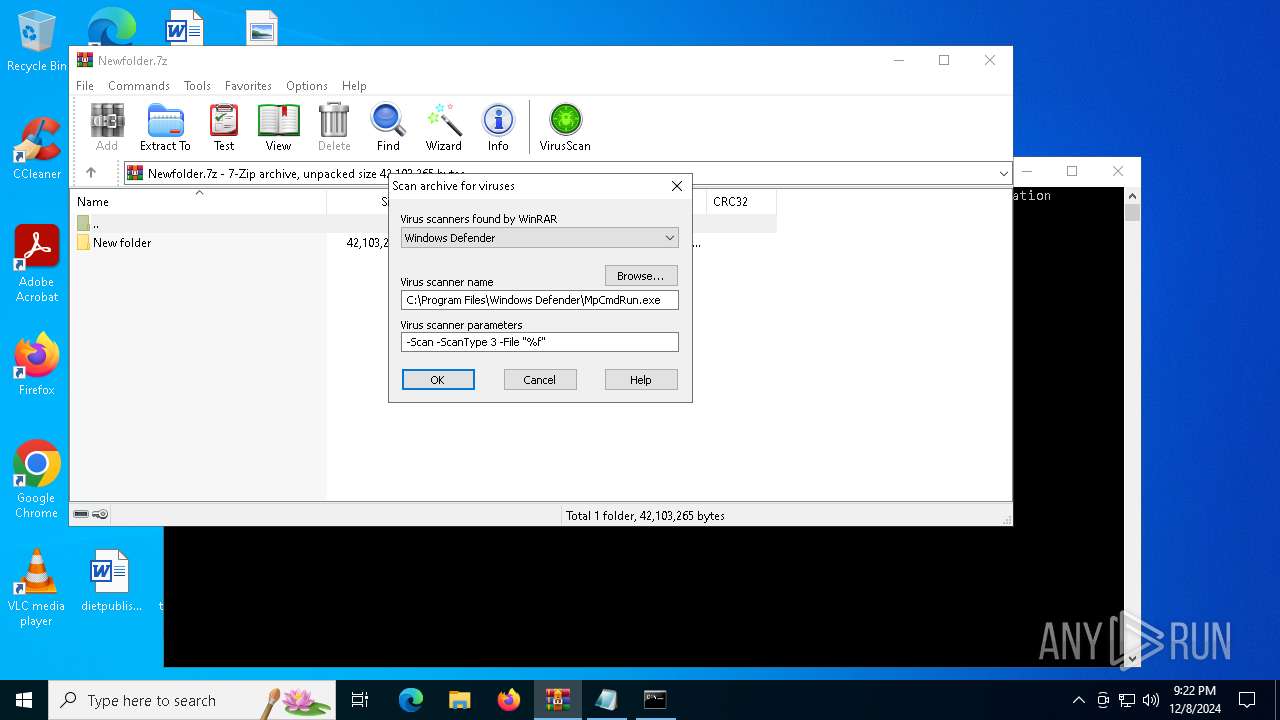
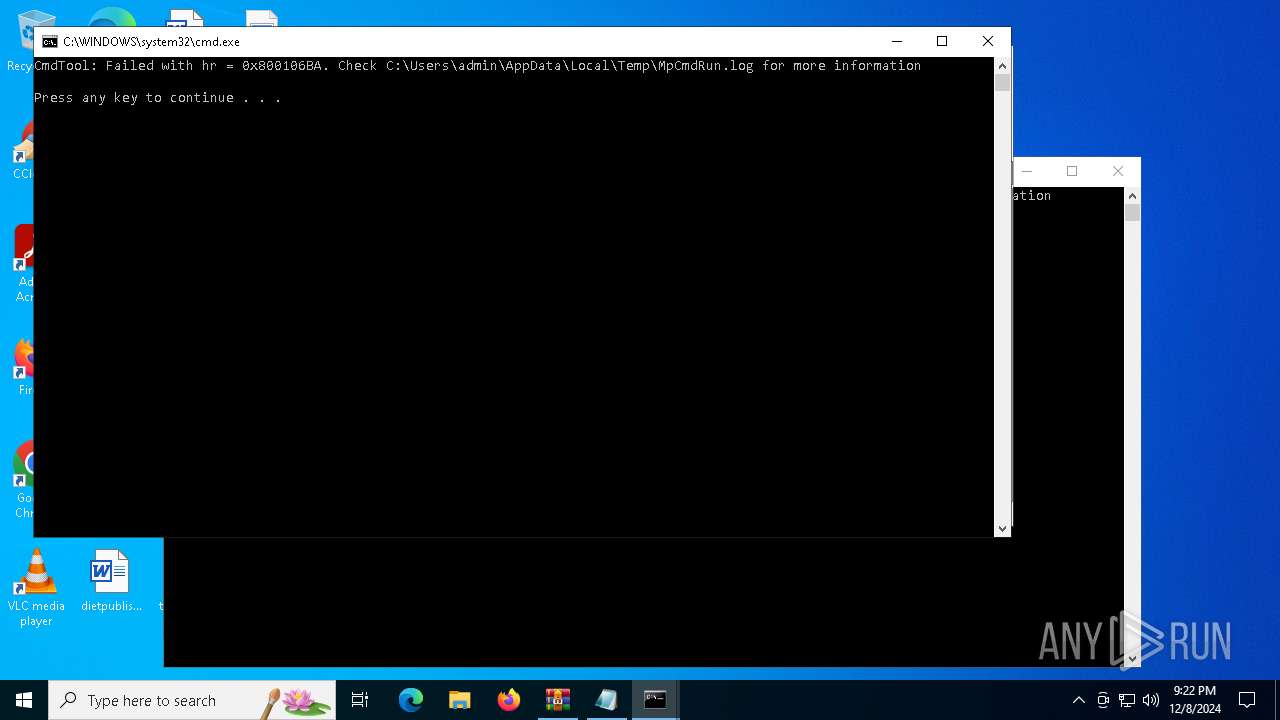
| File name: | Newfolder.7z |
| Full analysis: | https://app.any.run/tasks/99eec6fb-e535-449e-9fc1-45ac62cd3bd2 |
| Verdict: | Malicious activity |
| Analysis date: | December 08, 2024, 21:21:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 8988DC64384813A1E98203DF0AF16479 |
| SHA1: | A479C174501274F4FE33523BCCC5D16BA1BBABAA |
| SHA256: | AE6F1C1D92203532D5791FC0CE79D837F18ED37F28BE9924585AD227190B8CC2 |
| SSDEEP: | 393216:Jm4kA7hHuLIVXECdG8HpadFkVL3QLjwrKsvWC4vldaG+:79hO8VUCdBdLgLWKHhvldm |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6480)
Antivirus name has been found in the command line (generic signature)
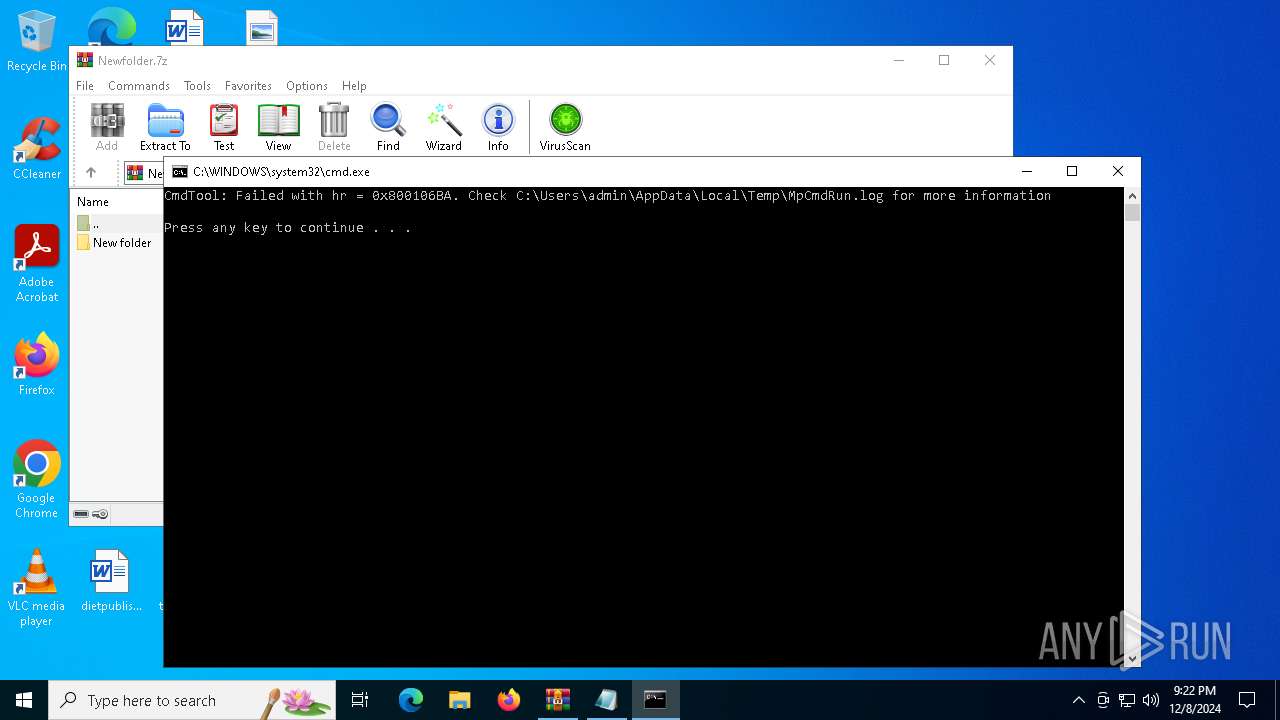
- MpCmdRun.exe (PID: 7092)
- MpCmdRun.exe (PID: 3152)
SUSPICIOUS
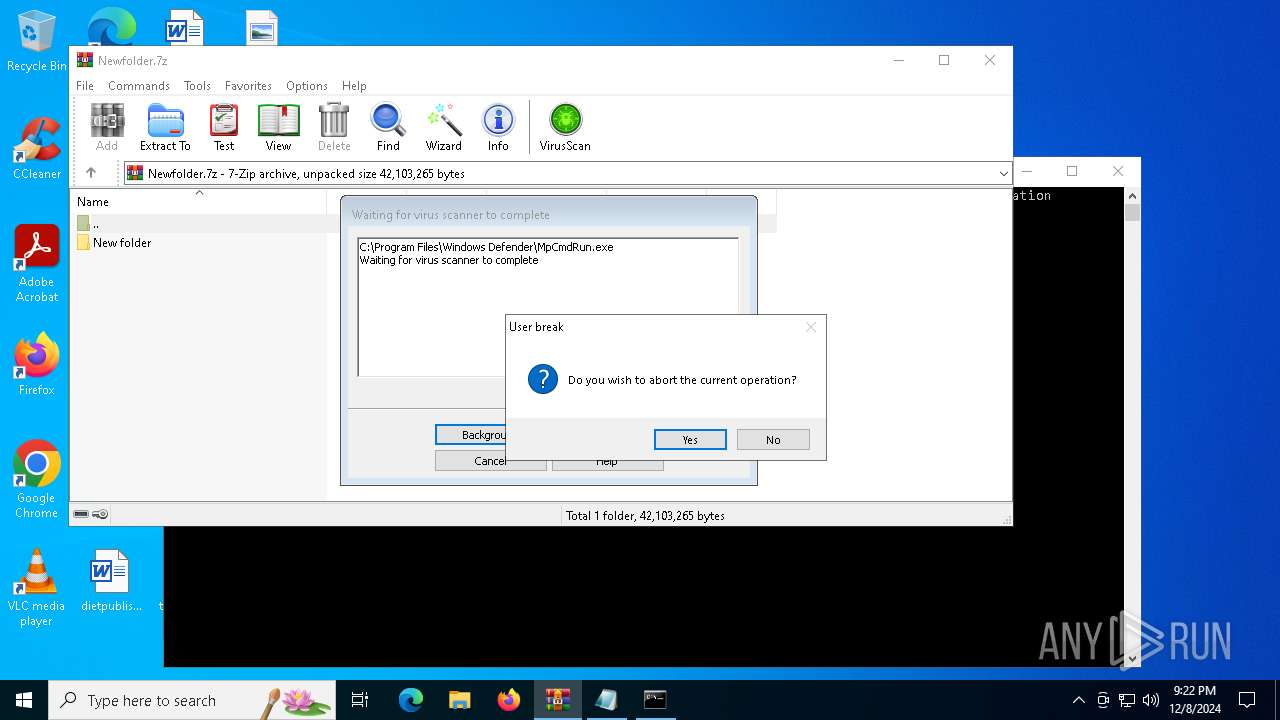
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6480)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6480)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6480)
INFO
Reads the computer name
- BRUTOFORCE SEED V12.7.8.exe (PID: 6756)
- MpCmdRun.exe (PID: 7092)
- MpCmdRun.exe (PID: 3152)
Create files in a temporary directory
- BRUTOFORCE SEED V12.7.8.exe (PID: 6756)
- MpCmdRun.exe (PID: 7092)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6860)
The process uses the downloaded file
- WinRAR.exe (PID: 6480)
Manual execution by a user
- BRUTOFORCE SEED V12.7.8.exe (PID: 6756)
- notepad.exe (PID: 6860)
Checks supported languages
- BRUTOFORCE SEED V12.7.8.exe (PID: 6756)
- MpCmdRun.exe (PID: 7092)
- MpCmdRun.exe (PID: 3152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:12:08 20:28:43+00:00 |
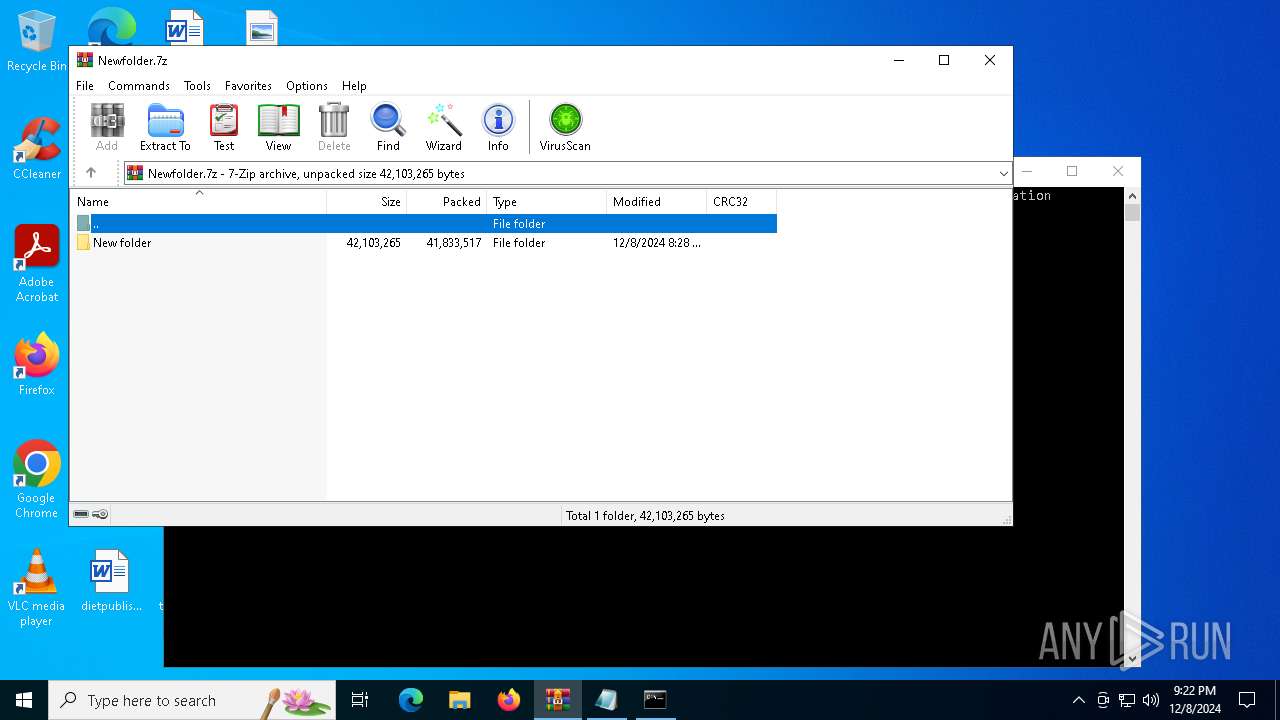
| ArchivedFileName: | New folder |
Total processes
125
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3152 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6480.27942" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6480 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Newfolder.7z | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6756 | "C:\Users\admin\Desktop\BRUTOFORCE SEED V12.7.8.exe" | C:\Users\admin\Desktop\BRUTOFORCE SEED V12.7.8.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
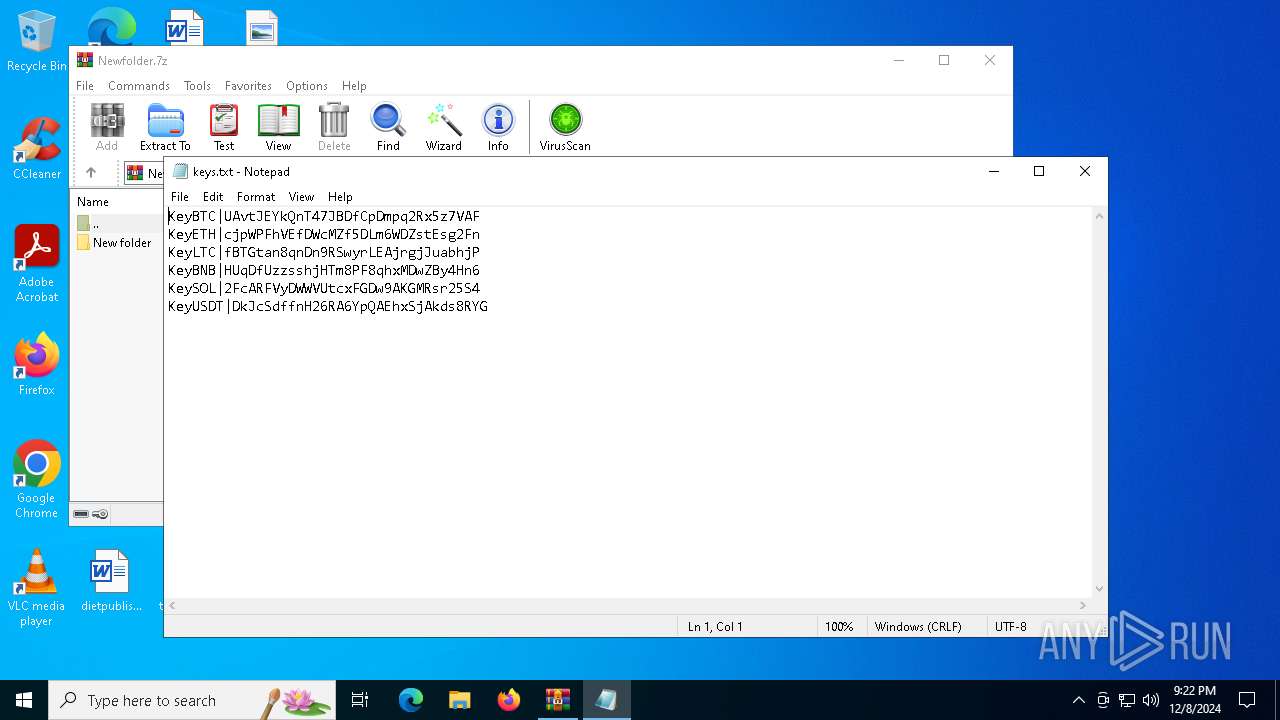
| 6860 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\keys.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7032 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6480.24716\Rar$Scan16387.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7092 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6480.24716" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7156 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6480.27942\Rar$Scan48606.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 905
Read events
1 895
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Newfolder.7z | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
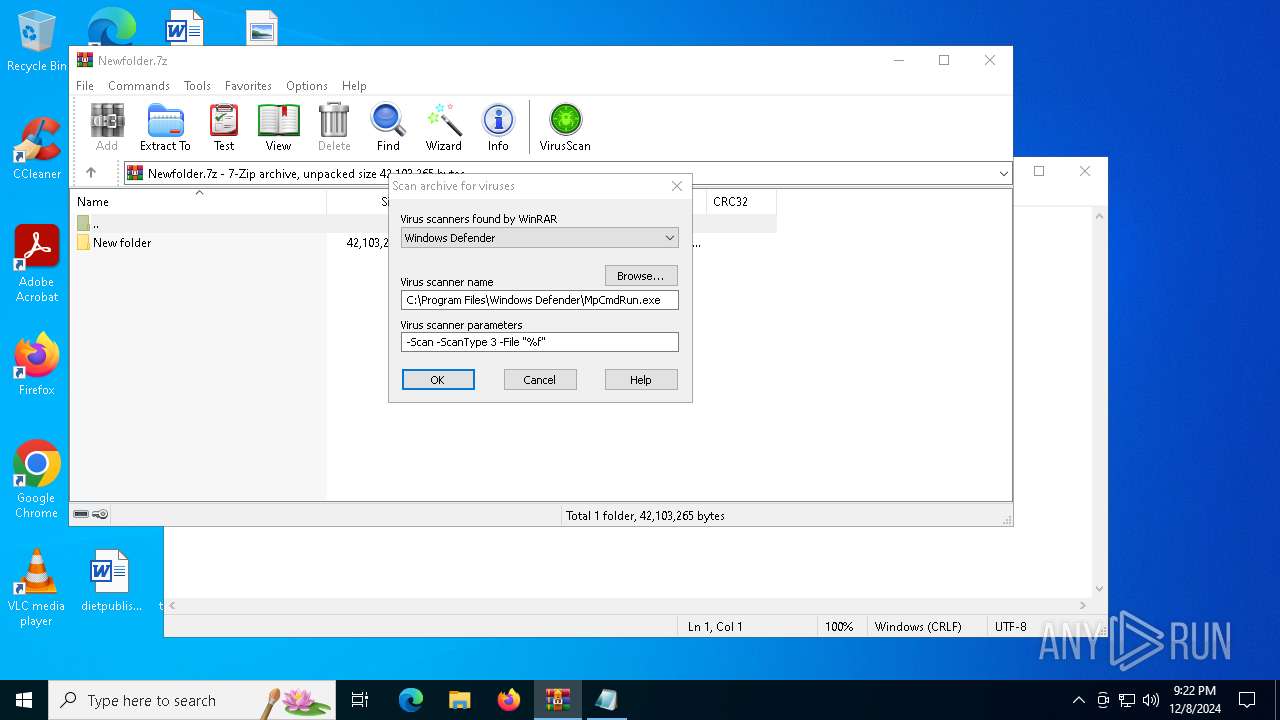
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
0
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6756 | BRUTOFORCE SEED V12.7.8.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\BRUTOFORCE SEED V12.6.1.EXE | — | |
MD5:— | SHA256:— | |||
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6480.24716\Newfolder.7z\New folder\BRUTOFORCE SEED V12.7.8.exe | — | |
MD5:— | SHA256:— | |||
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6480.27942\Newfolder.7z\New folder\BRUTOFORCE SEED V12.7.8.exe | — | |
MD5:— | SHA256:— | |||
| 7092 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:804D902A5A3570708BF8DEB570E753BF | SHA256:231C55638CC895C237F03D713D8DBD7CA11D09F1BF7B8BB8AE0CE731CA82ACEE | |||
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6480.24716\Newfolder.7z\New folder\keys.txt | text | |
MD5:68AE0AA0D5CCF15A4061A88A631A1B91 | SHA256:E18EACB17D6E550C1D07F9368F9DC8F75B7689C026FA420F37632FEC6333A02D | |||
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6480.24716\Rar$Scan16387.bat | text | |
MD5:0CFA2B3D341A2A30D5FE9BC42D94E208 | SHA256:85C17028559D69A3E6DBA02D5F83D4A631E264DBF52BC1D03B80122E84E20DA0 | |||
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6480.27942\Newfolder.7z\New folder\keys.txt | text | |
MD5:68AE0AA0D5CCF15A4061A88A631A1B91 | SHA256:E18EACB17D6E550C1D07F9368F9DC8F75B7689C026FA420F37632FEC6333A02D | |||
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6480.27942\Rar$Scan48606.bat | text | |
MD5:94DC872CC26F76B1F09AB474DAECFAD1 | SHA256:B3A57F52597ABD29FBCD259310E3ACAF8A60D021C3F3487D7FE65B2DE7752B28 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5880 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5880 | svchost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5880 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.204.138:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5880 | svchost.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5880 | svchost.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |