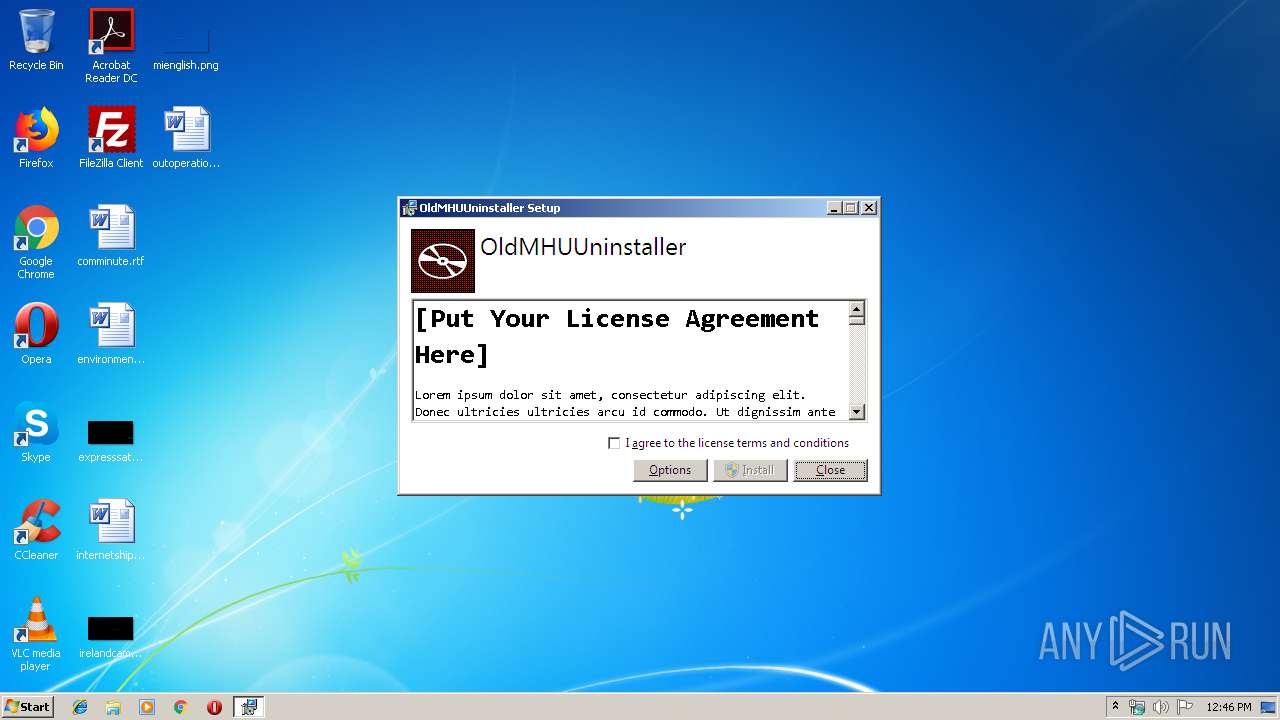
| File name: | OldMHUUninstaller.exe |
| Full analysis: | https://app.any.run/tasks/52208145-7d32-4bc2-9e43-d81f14358659 |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2019, 11:46:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1329ADE03F58927B4D53BCD2EFA29BDD |
| SHA1: | 1EAA403052201E0C9896D0FE3D0A8ECE0085F37F |
| SHA256: | AE4718EA01D1D749A5A0F3791F3EC1AD3A7029302A6B28EF19988DB60C3A6137 |
| SSDEEP: | 12288:u79g/k9Ygb25zyaaEqrHqm/A3er7y19vfrFKYuO:agwYgb25FJsqIAuf693h |
MALICIOUS
Loads dropped or rewritten executable
- OldMHUUninstaller.exe (PID: 1140)
Changes the autorun value in the registry
- OldMHUUninstaller.exe (PID: 2712)
SUSPICIOUS
Executable content was dropped or overwritten
- OldMHUUninstaller.exe (PID: 3076)
- msiexec.exe (PID: 3668)
- OldMHUUninstaller.exe (PID: 2712)
- OldMHUUninstaller.exe (PID: 1140)
Starts itself from another location
- OldMHUUninstaller.exe (PID: 3076)
- OldMHUUninstaller.exe (PID: 1140)
Creates a software uninstall entry
- OldMHUUninstaller.exe (PID: 2712)
Creates files in the program directory
- OldMHUUninstaller.exe (PID: 2712)
Searches for installed software
- OldMHUUninstaller.exe (PID: 2712)
Executed via COM
- DrvInst.exe (PID: 3172)
Executed as Windows Service
- vssvc.exe (PID: 3924)
INFO
Creates a software uninstall entry
- msiexec.exe (PID: 3668)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3924)
Adds / modifies Windows certificates
- DrvInst.exe (PID: 3172)
Changes settings of System certificates
- DrvInst.exe (PID: 3172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:05:01 16:33:52+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14.1 |
| CodeSize: | 302080 |
| InitializedDataSize: | 161280 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2e1fd |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.2.0.0 |
| ProductVersionNumber: | 3.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Plantronics, Inc. |
| FileDescription: | OldMHUUninstaller |
| FileVersion: | 3.2.0.0 |
| InternalName: | setup |
| LegalCopyright: | Copyright (c) Plantronics, Inc.. All rights reserved. |
| OriginalFileName: | OldMHUUninstaller.exe |
| ProductName: | OldMHUUninstaller |
| ProductVersion: | 3.2.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-May-2017 14:33:52 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | Plantronics, Inc. |
| FileDescription: | OldMHUUninstaller |
| FileVersion: | 3.2.0.0 |
| InternalName: | setup |
| LegalCopyright: | Copyright (c) Plantronics, Inc.. All rights reserved. |
| OriginalFilename: | OldMHUUninstaller.exe |
| ProductName: | OldMHUUninstaller |
| ProductVersion: | 3.2.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 7 |
| Time date stamp: | 01-May-2017 14:33:52 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00049A67 | 0x00049C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.56282 |
.rdata | 0x0004B000 | 0x0001EC60 | 0x0001EE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.10841 |
.data | 0x0006A000 | 0x00001730 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.15458 |
.wixburn8 | 0x0006C000 | 0x00000038 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.553262 |
.tls | 0x0006D000 | 0x00000009 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0006E000 | 0x00003A6C | 0x00003C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.5363 |
.reloc | 0x00072000 | 0x00003DEC | 0x00003E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.79026 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.30829 | 1234 | Latin 1 / Western European | English - United States | RT_MANIFEST |
Imports
ADVAPI32.dll |
Cabinet.dll (delay-loaded) |
GDI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
RPCRT4.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
42
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1140 | "C:\Users\admin\AppData\Local\Temp\{9507F7AB-8B18-492D-ABC8-35BB2A0A251A}\.cr\OldMHUUninstaller.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\OldMHUUninstaller.exe" -burn.filehandle.attached=148 -burn.filehandle.self=156 | C:\Users\admin\AppData\Local\Temp\{9507F7AB-8B18-492D-ABC8-35BB2A0A251A}\.cr\OldMHUUninstaller.exe | OldMHUUninstaller.exe | ||||||||||||
User: admin Company: Plantronics, Inc. Integrity Level: MEDIUM Description: OldMHUUninstaller Exit code: 0 Version: 3.2.0.0 Modules
| |||||||||||||||
| 2712 | "C:\Users\admin\AppData\Local\Temp\{0A0695A1-AB64-47C6-92E9-16FA73377C99}\.be\OldMHUUninstaller.exe" -q -burn.elevated BurnPipe.{1E2D319C-A8EA-4019-8078-B6EA3D0997E7} {E429EA38-8E94-4542-A872-56A69543A3F9} 1140 | C:\Users\admin\AppData\Local\Temp\{0A0695A1-AB64-47C6-92E9-16FA73377C99}\.be\OldMHUUninstaller.exe | OldMHUUninstaller.exe | ||||||||||||
User: admin Company: Plantronics, Inc. Integrity Level: HIGH Description: OldMHUUninstaller Exit code: 0 Version: 3.2.0.0 Modules
| |||||||||||||||
| 3076 | "C:\Users\admin\AppData\Local\Temp\OldMHUUninstaller.exe" | C:\Users\admin\AppData\Local\Temp\OldMHUUninstaller.exe | explorer.exe | ||||||||||||
User: admin Company: Plantronics, Inc. Integrity Level: MEDIUM Description: OldMHUUninstaller Exit code: 0 Version: 3.2.0.0 Modules
| |||||||||||||||
| 3172 | DrvInst.exe "1" "200" "STORAGE\VolumeSnapshot\HarddiskVolumeSnapshot18" "" "" "6792c44eb" "00000000" "000005C4" "000003A0" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3668 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3924 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
918
Read events
639
Write events
265
Delete events
14
Modification events
| (PID) Process: | (1140) OldMHUUninstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1140) OldMHUUninstaller.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2712) OldMHUUninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000005CD83B831421D501980A0000D00A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2712) OldMHUUninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000005CD83B831421D501980A0000D00A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3924) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B87196831421D501540F00001C0E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3924) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000B87196831421D501540F0000E0090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3924) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000012D498831421D501540F0000140E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3924) vssvc.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000012D498831421D501540F0000DC090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2712) OldMHUUninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 20 | |||
| (PID) Process: | (2712) OldMHUUninstaller.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000F6858A831421D501980A0000D00A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
7
Suspicious files
5
Text files
67
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2712 | OldMHUUninstaller.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1140 | OldMHUUninstaller.exe | C:\Users\admin\AppData\Local\Temp\{0A0695A1-AB64-47C6-92E9-16FA73377C99}\OldMHUUninstallerMSI | — | |
MD5:— | SHA256:— | |||
| 2712 | OldMHUUninstaller.exe | C:\ProgramData\Package Cache\.unverified\OldMHUUninstallerMSI | — | |
MD5:— | SHA256:— | |||
| 3668 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF5BDA971CB6822788.TMP | — | |
MD5:— | SHA256:— | |||
| 3668 | msiexec.exe | C:\Windows\Installer\MSI4A22.tmp | — | |
MD5:— | SHA256:— | |||
| 3668 | msiexec.exe | C:\Config.Msi\1547d3.rbs | — | |
MD5:— | SHA256:— | |||
| 3668 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFD4EDF3E4A427E133.TMP | — | |
MD5:— | SHA256:— | |||
| 3076 | OldMHUUninstaller.exe | C:\Users\admin\AppData\Local\Temp\{9507F7AB-8B18-492D-ABC8-35BB2A0A251A}\.cr\OldMHUUninstaller.exe | executable | |
MD5:— | SHA256:— | |||
| 1140 | OldMHUUninstaller.exe | C:\Users\admin\AppData\Local\Temp\{0A0695A1-AB64-47C6-92E9-16FA73377C99}\.be\OldMHUUninstaller.exe | executable | |
MD5:— | SHA256:— | |||
| 3924 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report