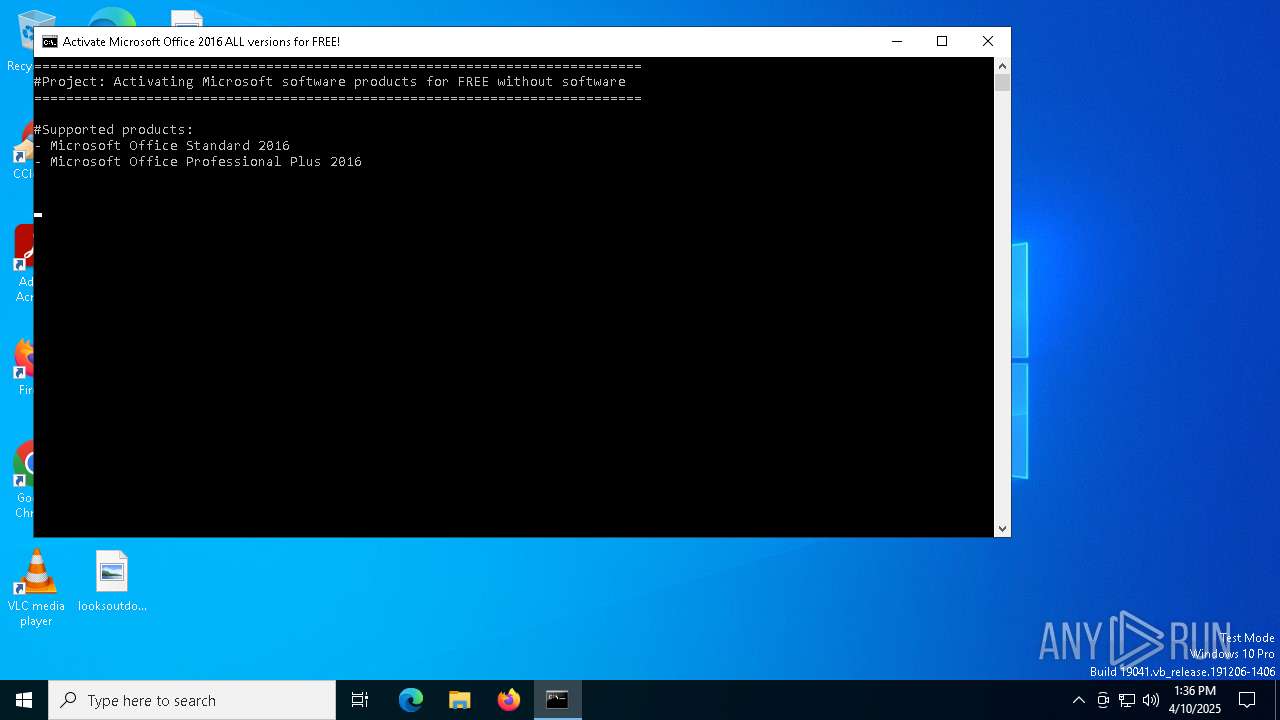
| File name: | 1click.cmd |
| Full analysis: | https://app.any.run/tasks/a18c5d89-9564-4a6d-8cea-bf70102e9fde |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2025, 13:36:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (1298), with CRLF line terminators |
| MD5: | 94C3F6B998627923D7869277E6FFDEE1 |
| SHA1: | 7B7F366DFF9655543E146E4950F2AB9B85B77987 |
| SHA256: | ADE548F8424282341FB2E5FAAD4D0CC206898983D3E62107635A653E5BA9727C |
| SSDEEP: | 48:Wigr61lOqoXucXuuAh4qhKgzq1zpHD17Pp5xfmxbZlT/8ZxGg0q4Y:jgr61lOqKumuDvsJJP1MZlAP0LY |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process executes VB scripts
- cmd.exe (PID: 7288)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6264)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 7388)
- cscript.exe (PID: 7384)
- cscript.exe (PID: 7888)
- cscript.exe (PID: 7840)
- cscript.exe (PID: 7900)
- cscript.exe (PID: 7876)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4920)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6264)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 7388)
- cscript.exe (PID: 4920)
- cscript.exe (PID: 7384)
- cscript.exe (PID: 7840)
- cscript.exe (PID: 7888)
- cscript.exe (PID: 7876)
- cscript.exe (PID: 7900)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6264)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 7388)
- cscript.exe (PID: 4920)
- cscript.exe (PID: 7384)
- cscript.exe (PID: 7888)
- cscript.exe (PID: 7840)
- cscript.exe (PID: 7876)
- cscript.exe (PID: 7900)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 6264)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 7388)
- cscript.exe (PID: 4920)
- cscript.exe (PID: 7384)
- cscript.exe (PID: 7888)
- cscript.exe (PID: 7840)
- cscript.exe (PID: 7876)
- cscript.exe (PID: 7900)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6264)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 7388)
- cscript.exe (PID: 4920)
- cscript.exe (PID: 7384)
- cscript.exe (PID: 7888)
- cscript.exe (PID: 7840)
- cscript.exe (PID: 7876)
- cscript.exe (PID: 7900)
Executes application which crashes
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6264)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 5508)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6264)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 7388)
- cscript.exe (PID: 7384)
- cscript.exe (PID: 7888)
- cscript.exe (PID: 4920)
- cscript.exe (PID: 7840)
- cscript.exe (PID: 7876)
- cscript.exe (PID: 7900)
The process creates files with name similar to system file names
- WerFault.exe (PID: 8060)
- WerFault.exe (PID: 7260)
- WerFault.exe (PID: 7424)
- WerFault.exe (PID: 5556)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6264)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 5508)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7288)
Application launched itself
- cmd.exe (PID: 7288)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 7840)
INFO
Reads security settings of Internet Explorer
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 7900)
Reads the software policy settings
- cscript.exe (PID: 7952)
- cscript.exe (PID: 8152)
- cscript.exe (PID: 4300)
- cscript.exe (PID: 6036)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 7388)
- cscript.exe (PID: 7900)
Creates files or folders in the user directory
- WerFault.exe (PID: 8060)
- WerFault.exe (PID: 5556)
- WerFault.exe (PID: 7424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
162
Monitored processes
27
Malicious processes
14
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3768 | find /i "successful" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | C:\WINDOWS\system32\cmd.exe /c dir /b ..\root\Licenses16\proplusvl_mak*.xrm-ms | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | cscript ospp.vbs /inslic:"..\root\Licenses16\ProPlusVL_MAK-pl.xrm-ms" | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4920 | cscript //nologo ospp.vbs /unpkey:DRTFM | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5508 | cscript ospp.vbs /inslic:"..\root\Licenses16\ProPlusVL_MAK-ul-phn.xrm-ms" | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5556 | C:\WINDOWS\system32\WerFault.exe -u -p 8152 -s 1540 | C:\Windows\System32\WerFault.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6036 | cscript ospp.vbs /inslic:"..\root\Licenses16\ProPlusVL_MAK-ul-oob.xrm-ms" | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6264 | cscript ospp.vbs /inslic:"..\root\Licenses16\ProPlusVL_MAK-ppd.xrm-ms" | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6324 | C:\WINDOWS\system32\WerFault.exe -u -p 6036 -s 1488 | C:\Windows\System32\WerFault.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6392 | C:\WINDOWS\system32\WerFault.exe -u -p 6264 -s 1328 | C:\Windows\System32\WerFault.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
51 997
Read events
51 997
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
2
Text files
12
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8060 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_01b59542-3f86-4f0a-bb98-d354a25d3cd6\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5556 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_d533fa49-eeb2-437c-85ea-b088ed80e8de\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7260 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_3fff7c1c-0516-4b9d-8bd2-c2d1ee23149d\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6392 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_9766ac0f-c3a8-4d6a-877b-b8674ddebe4b\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7372 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | der | |
MD5:86BEC7A51419CF6F8277608E79B2B807 | SHA256:1AE99C253A484A9CB6814FB52AFD40E347DFE2CD6273E50B245695B87C1BC6E5 | |||
| 8060 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCE8E.tmp.WERInternalMetadata.xml | xml | |
MD5:42B83A4F22A3E434CCFD141DF44FCA70 | SHA256:ABE149A60465CCFB1EF14BFF4C6E86E63759BAE28DA2992A21169F86270A1619 | |||
| 8060 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCE00.tmp.dmp | dmp | |
MD5:4E3B2A4BF51B120C814F5F74AED1EAEE | SHA256:069A49BC183E1339A73BEFD12C5A88F9BEA7DB6BCA909F3E2B30E33B2D8CA945 | |||
| 5556 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD332.tmp.xml | xml | |
MD5:DE4C79C93DEDBA518E1E8BEE5F4CD8A2 | SHA256:73AE0F20CD04CA8CEFAC841F2C0472F2835B2D679C3132F7B4C21C24590AC528 | |||
| 6324 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cscript.exe_62b6f5ddb4f9b32f9faaaa562a56d6d8f11b6a_d25c8a3a_8544eb85-bb52-460c-bda9-6db4c97457e9\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7260 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD8A1.tmp.xml | xml | |
MD5:71C0DC948578597C76A37AA832D0D25E | SHA256:004A99EA28997E8C0648F4623F53F002B04DB31E31427C02456736D1B6642B3C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
17
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7196 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7196 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.20:80 | — | Akamai International B.V. | DE | unknown |
— | — | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7464 | WmiPrvSE.exe | 40.91.76.224:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |