| File name: | 1click.cmd |
| Full analysis: | https://app.any.run/tasks/277e49f4-ffe9-4772-b4d0-3eecf8c74816 |
| Verdict: | Malicious activity |
| Analysis date: | January 11, 2019, 11:07:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 94C3F6B998627923D7869277E6FFDEE1 |
| SHA1: | 7B7F366DFF9655543E146E4950F2AB9B85B77987 |
| SHA256: | ADE548F8424282341FB2E5FAAD4D0CC206898983D3E62107635A653E5BA9727C |
| SSDEEP: | 48:Wigr61lOqoXucXuuAh4qhKgzq1zpHD17Pp5xfmxbZlT/8ZxGg0q4Y:jgr61lOqKumuDvsJJP1MZlAP0LY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- cmd.exe (PID: 2980)
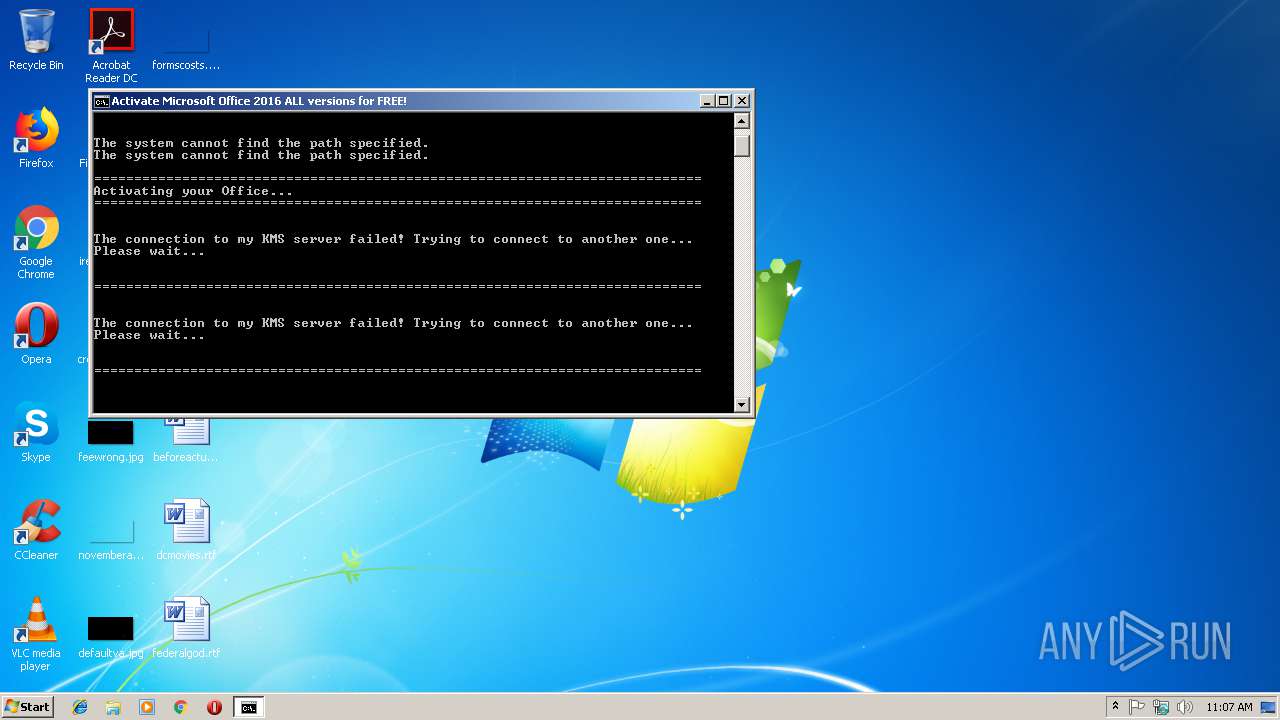
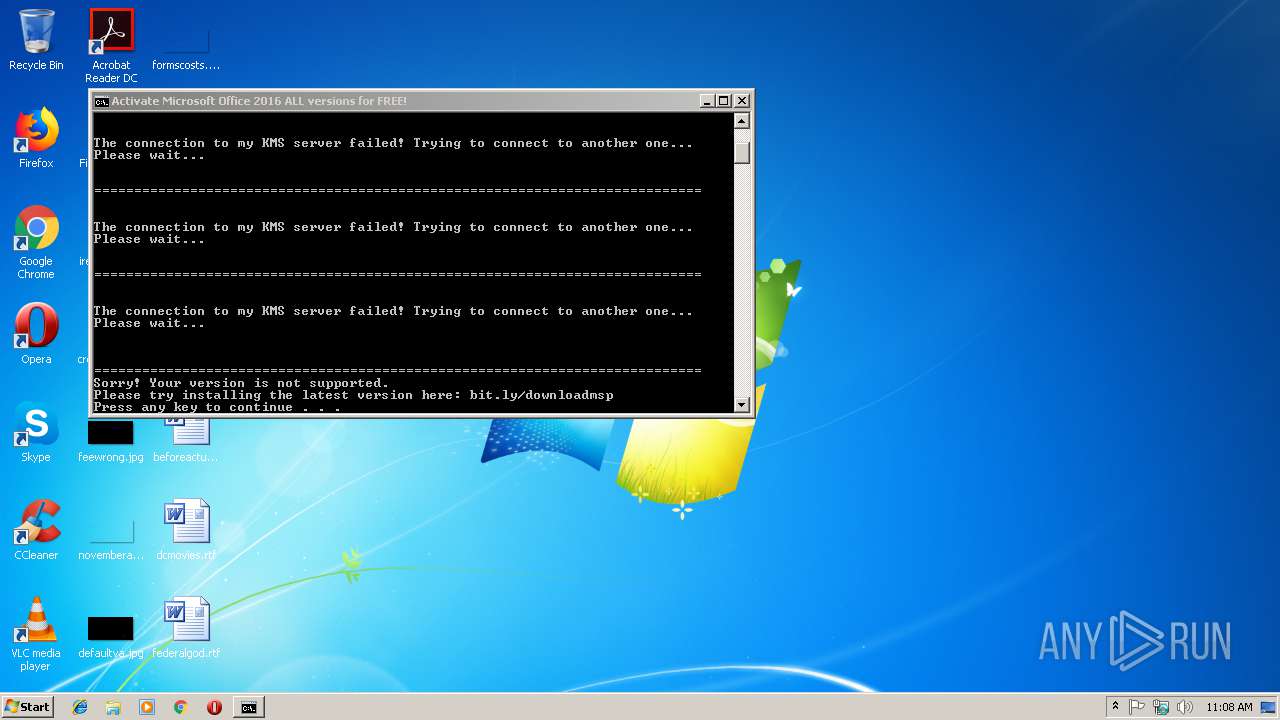
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2980)
Executes scripts
- cmd.exe (PID: 2980)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3336)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
19
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
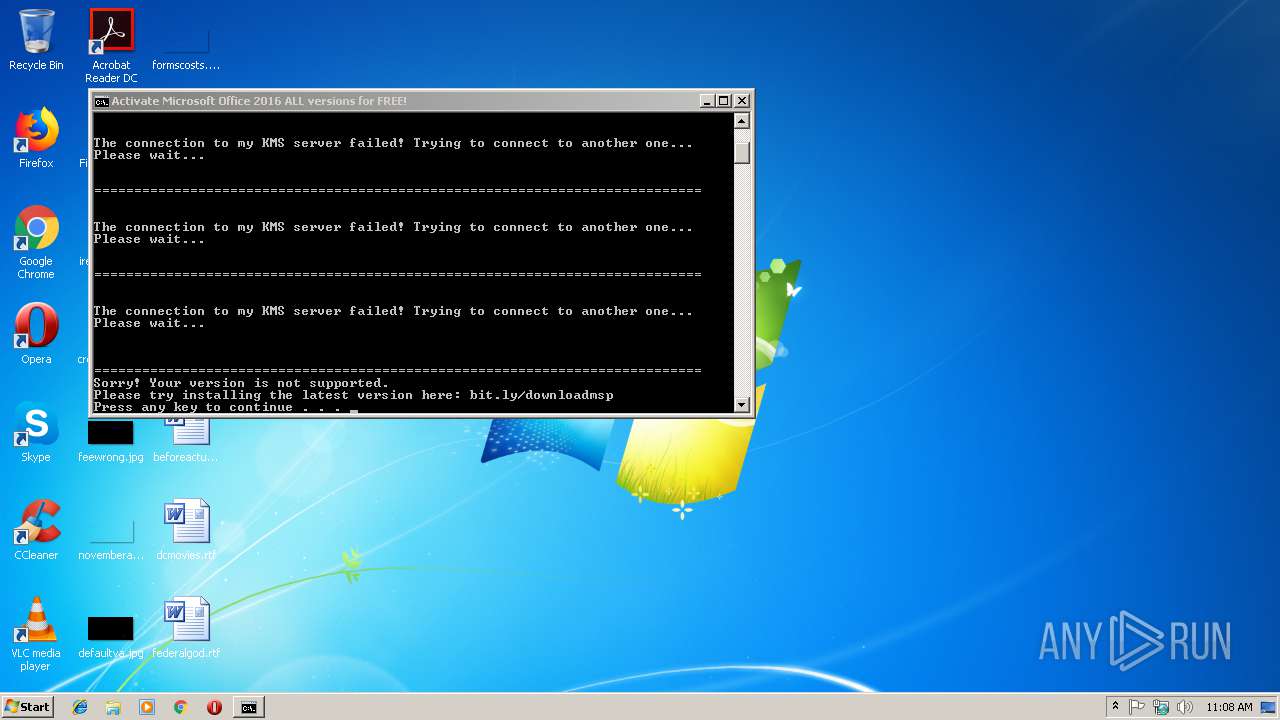
| 312 | cscript //nologo ospp.vbs /sethst:kms8.MSGuides.com | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2228 | cscript //nologo ospp.vbs /inpkey:XQNVK-8JYDB-WJ9W3-YJ8YR-WFG99 | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2252 | cscript //nologo ospp.vbs /unpkey:WFG99 | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2456 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2548 | cscript //nologo ospp.vbs /act | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2656 | find /i "successful" | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2728 | cscript //nologo ospp.vbs /sethst:kms7.MSGuides.com | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2872 | cscript //nologo ospp.vbs /unpkey:DRTFM | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2980 | cmd /c ""C:\Users\admin\AppData\Local\Temp\1click.cmd" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3232 | cscript //nologo ospp.vbs /act | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
722
Read events
666
Write events
45
Delete events
11
Modification events
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | /(' |
Value: 2F282700080D0000010000000000000000000000 | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1311440927 | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1311441040 | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1311441041 | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 080D00002AD015FF9DA9D40100000000 | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | &*' |
Value: 262A2700080D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | &*' |
Value: 262A2700080D000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3336) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3336 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2C8F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3336 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\federalgod.rtf.LNK | — | |
MD5:— | SHA256:— | |||
| 3336 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{9731030F-DFC8-405B-AB60-C461802A78A6}.tmp | — | |
MD5:— | SHA256:— | |||
| 3336 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{76182A57-D995-48B2-851D-9E4853DEB758}.tmp | — | |
MD5:— | SHA256:— | |||
| 3336 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3336 | WINWORD.EXE | C:\Users\admin\Desktop\~$deralgod.rtf | pgc | |
MD5:— | SHA256:— | |||
| 3336 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report