| File name: | Partnership Agreement for YouTube Cooperation.exe |
| Full analysis: | https://app.any.run/tasks/333a543a-2520-4612-8373-58e3329aab33 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2025, 19:05:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | AF2E854BE4057C5FC602E25CF73BF8DA |
| SHA1: | 857A2F89A91A47D7D82B16C568AC7598B9015554 |
| SHA256: | ADDC2DDEADC5ED50F191FDCD5400231DA59517AC8DCB470A616CD408ED81A14A |
| SSDEEP: | 49152:gwMgfPAESYUJ/jiJ8aQSCodp6ryRvL0ZqfEJZbcx3u09qm8q2ORcw82MgELQpWhH:mgwewOzQXo7HL0dJsu09qmPP/MgELQp8 |
MALICIOUS
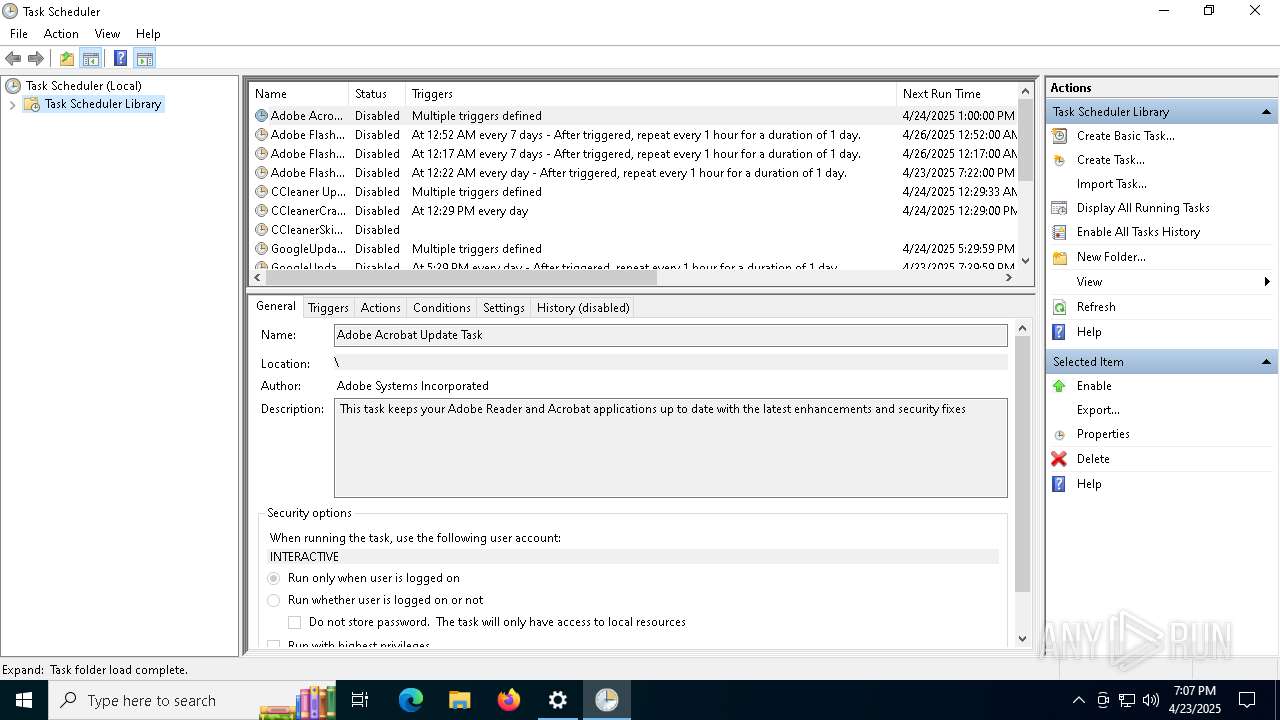
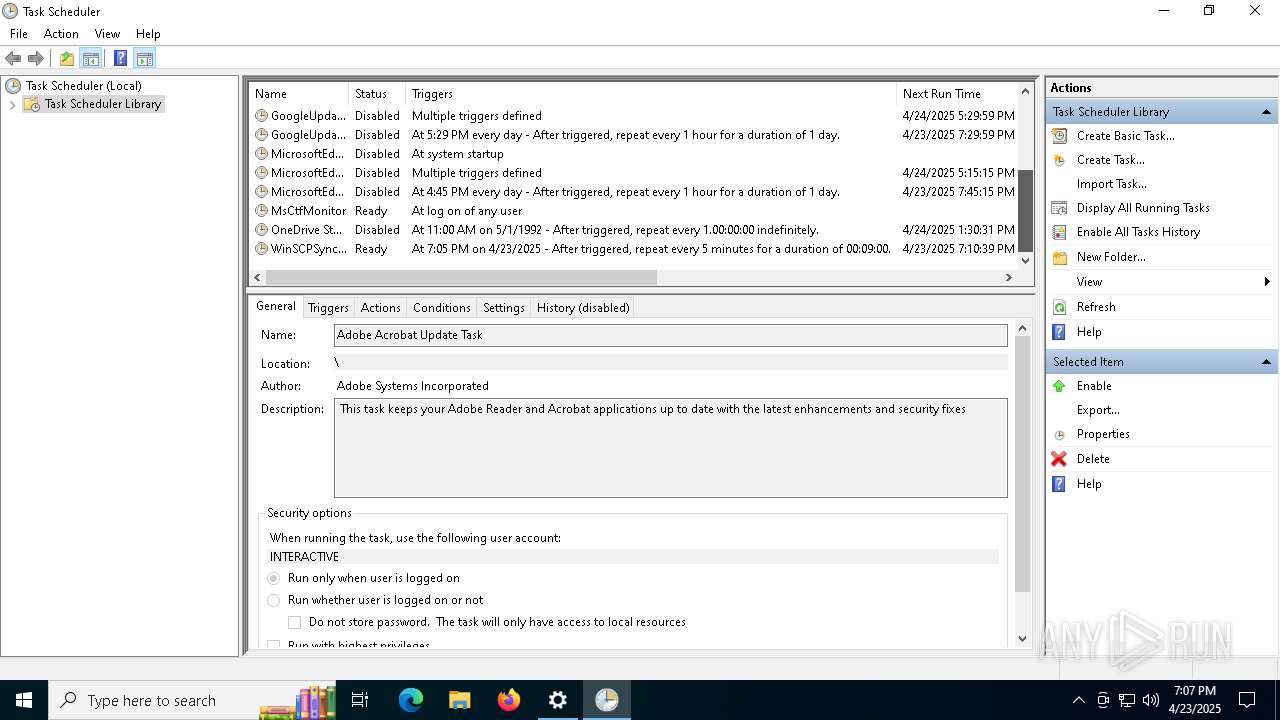
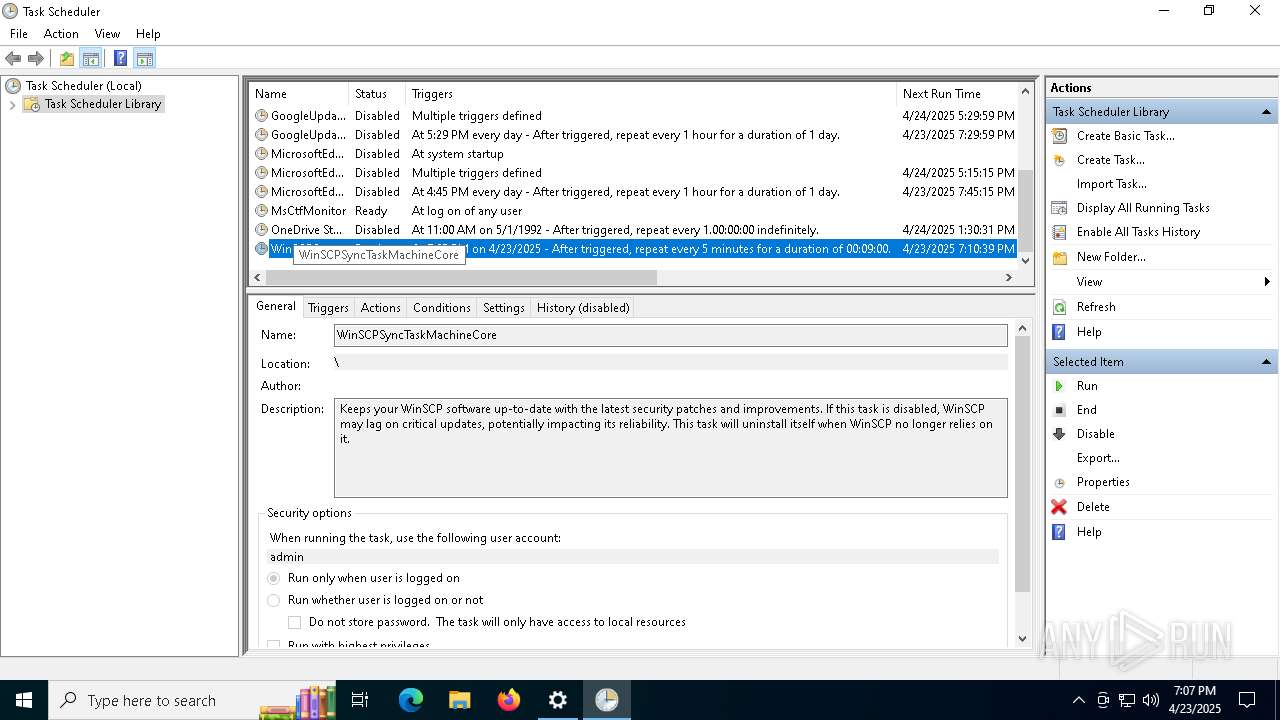
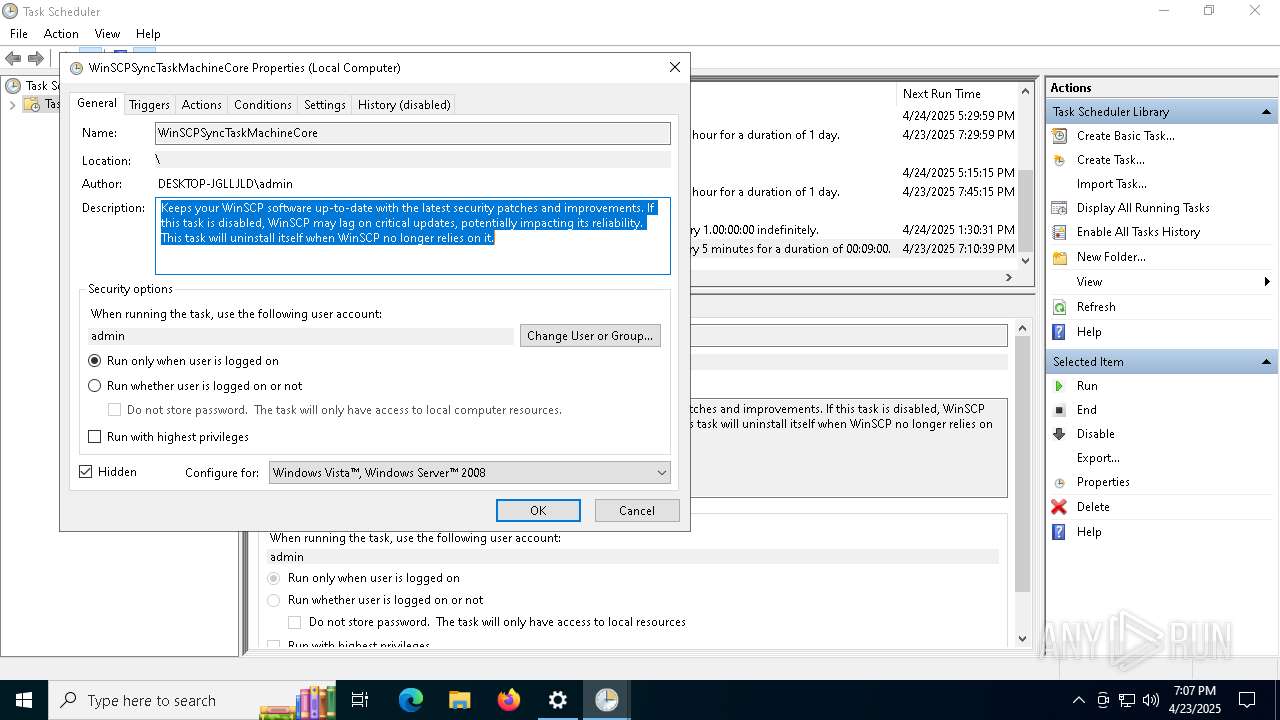
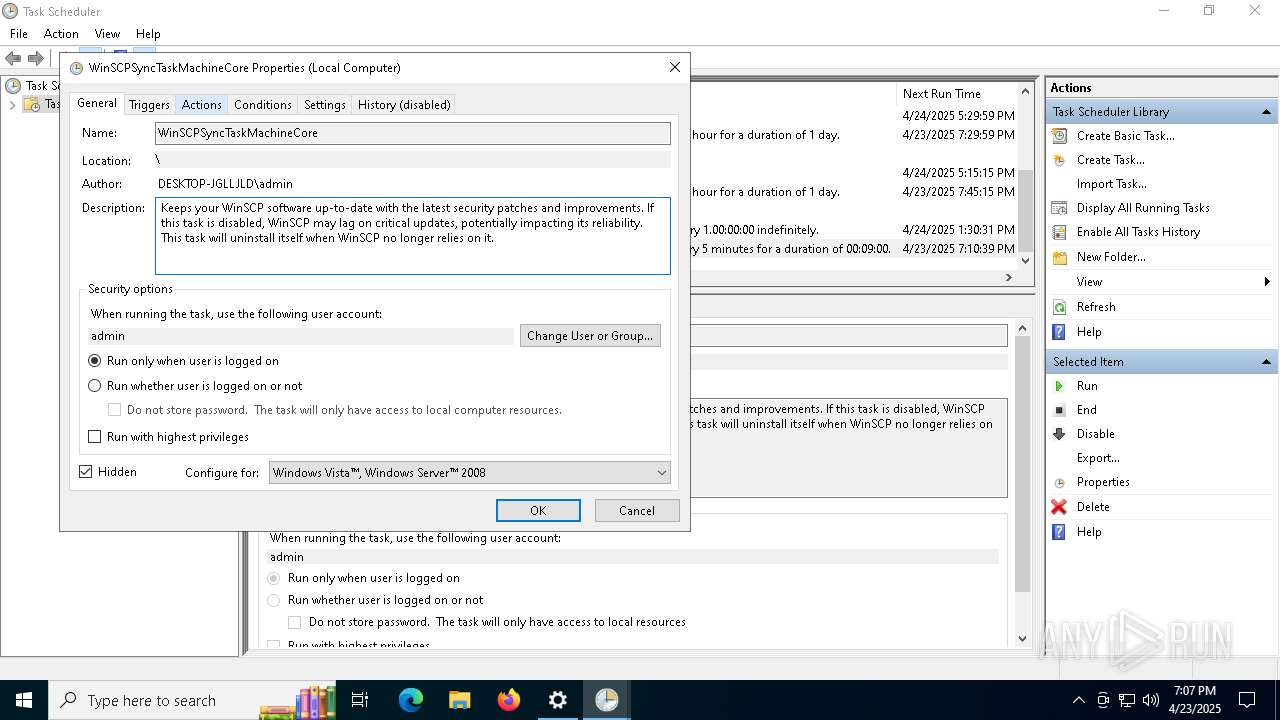
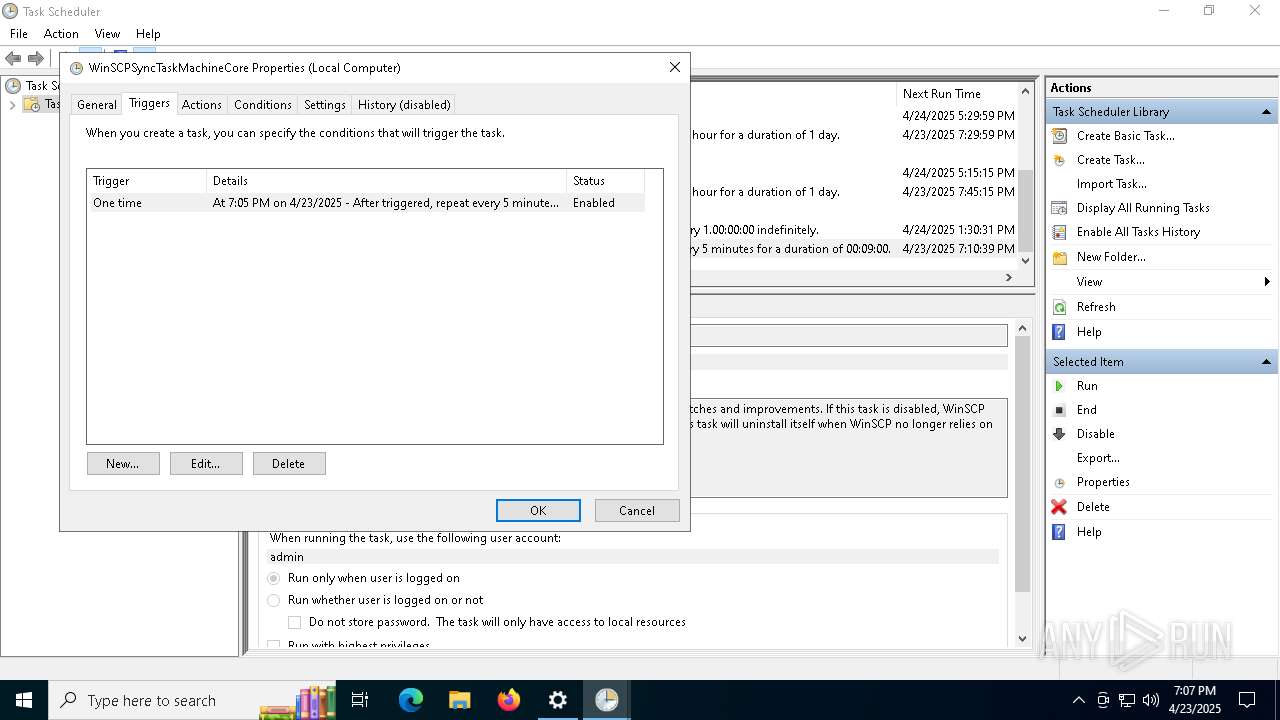
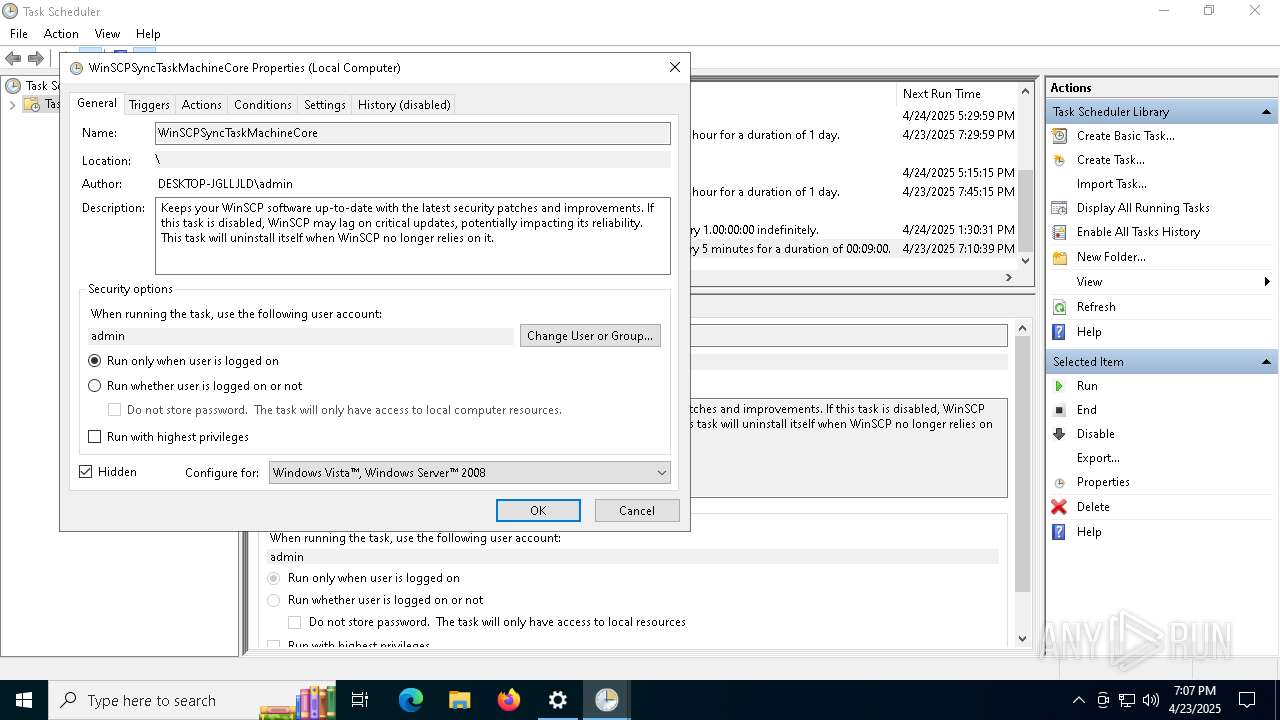
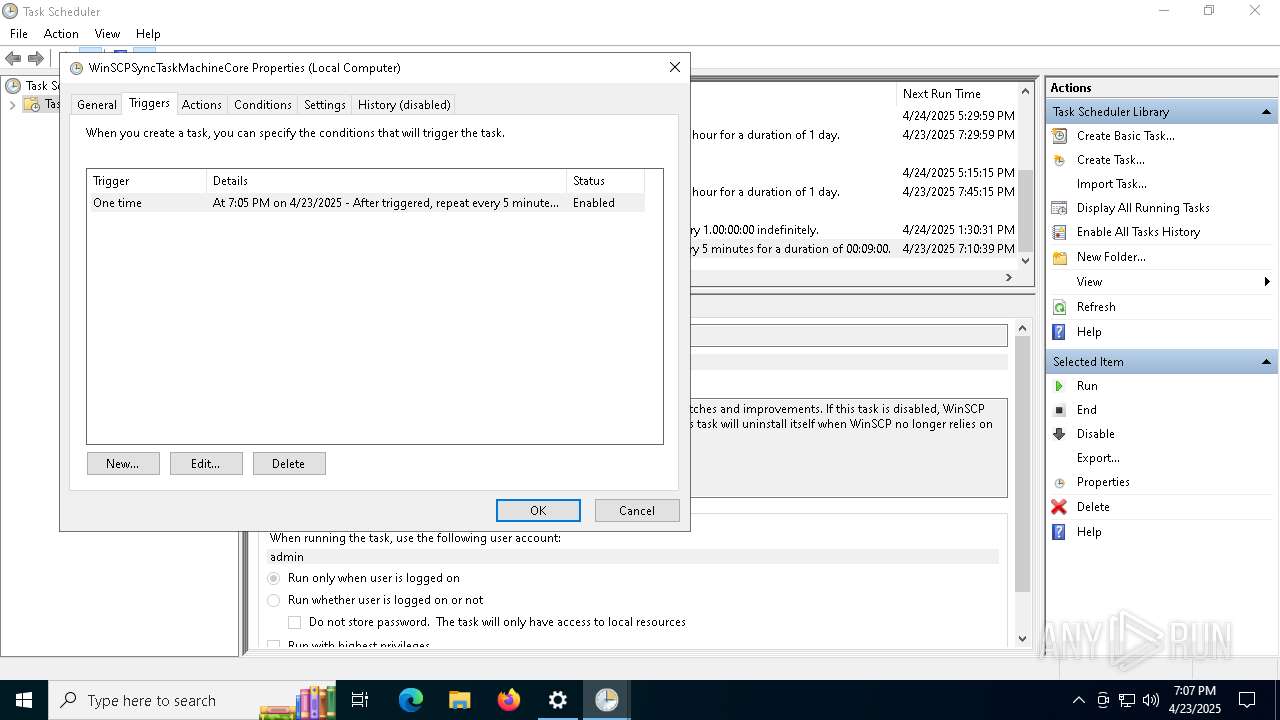
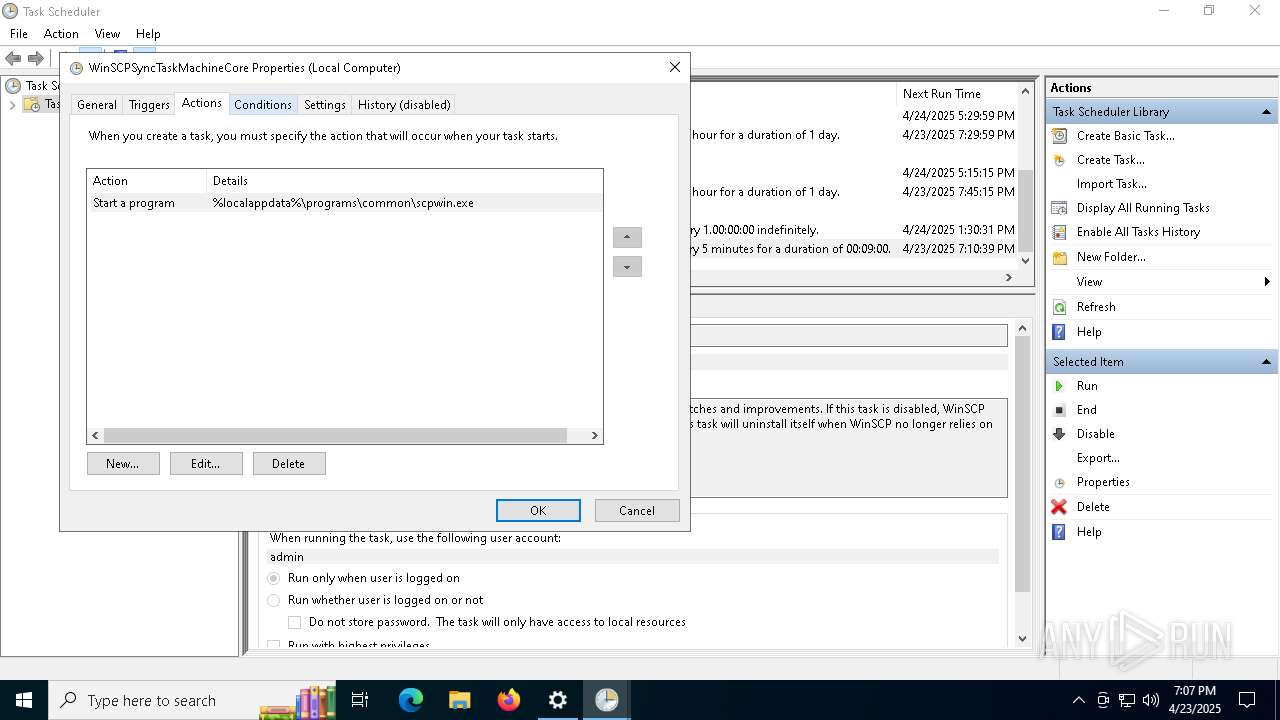
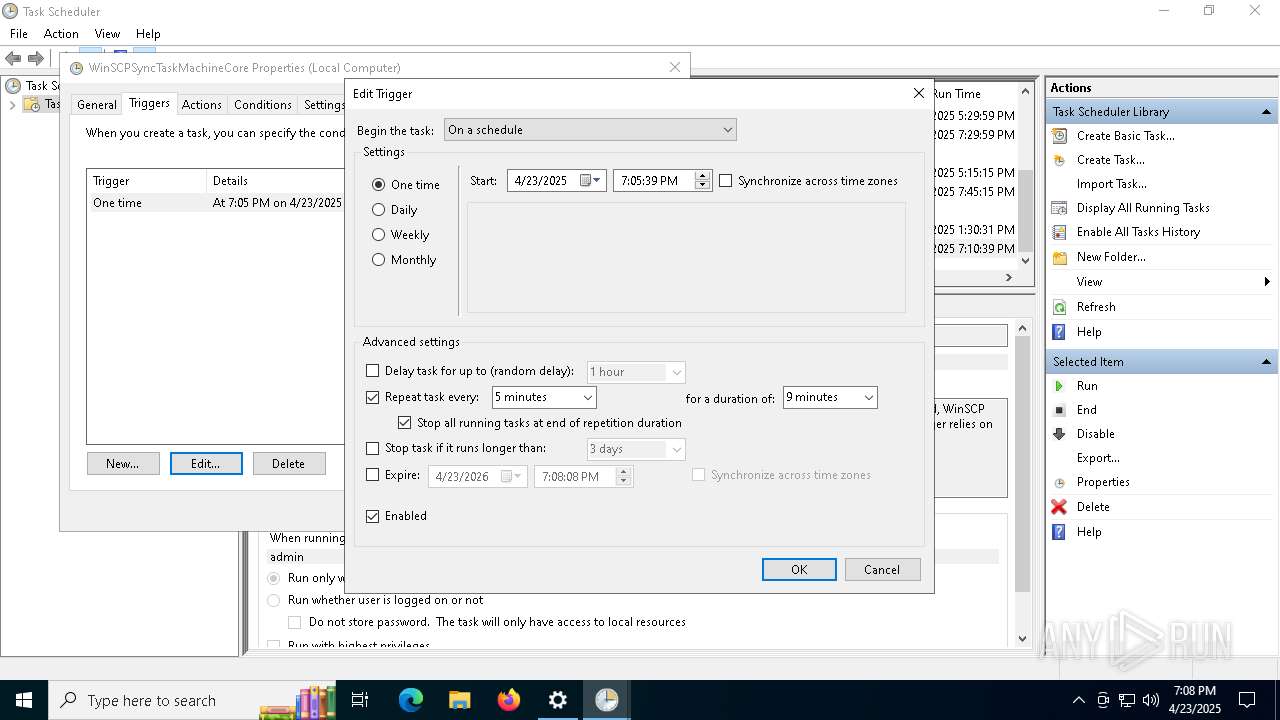
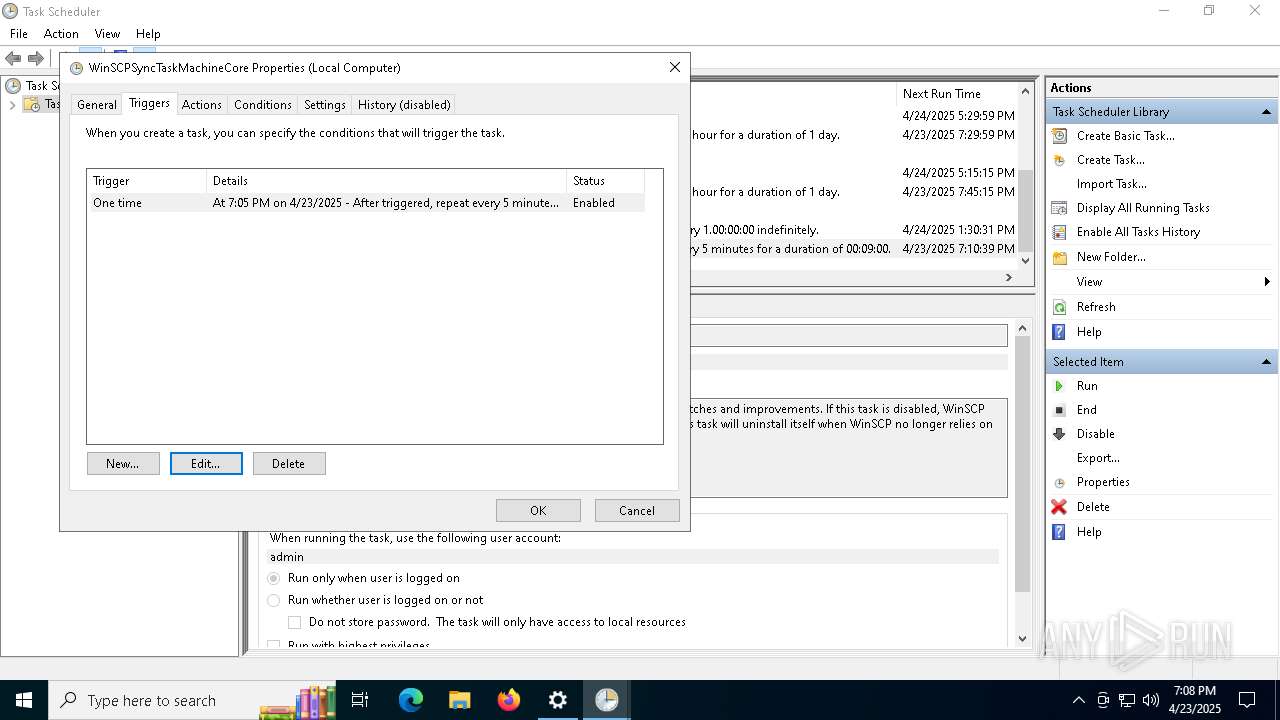
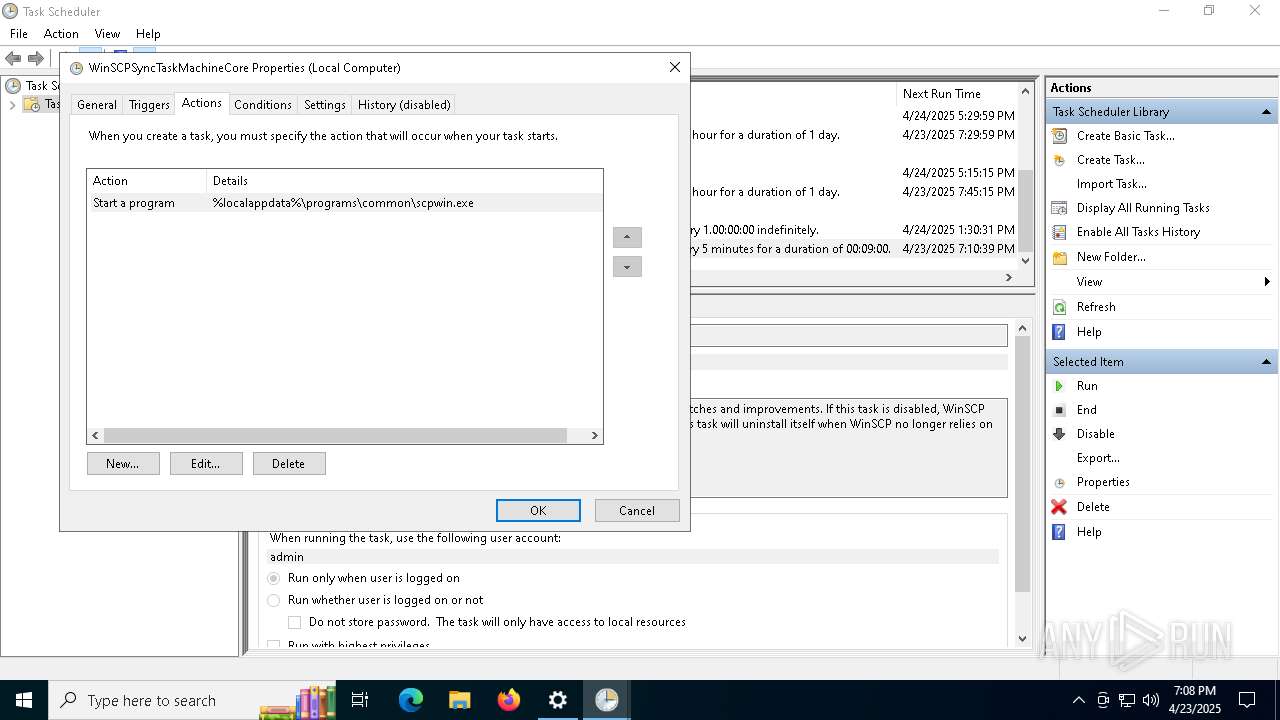
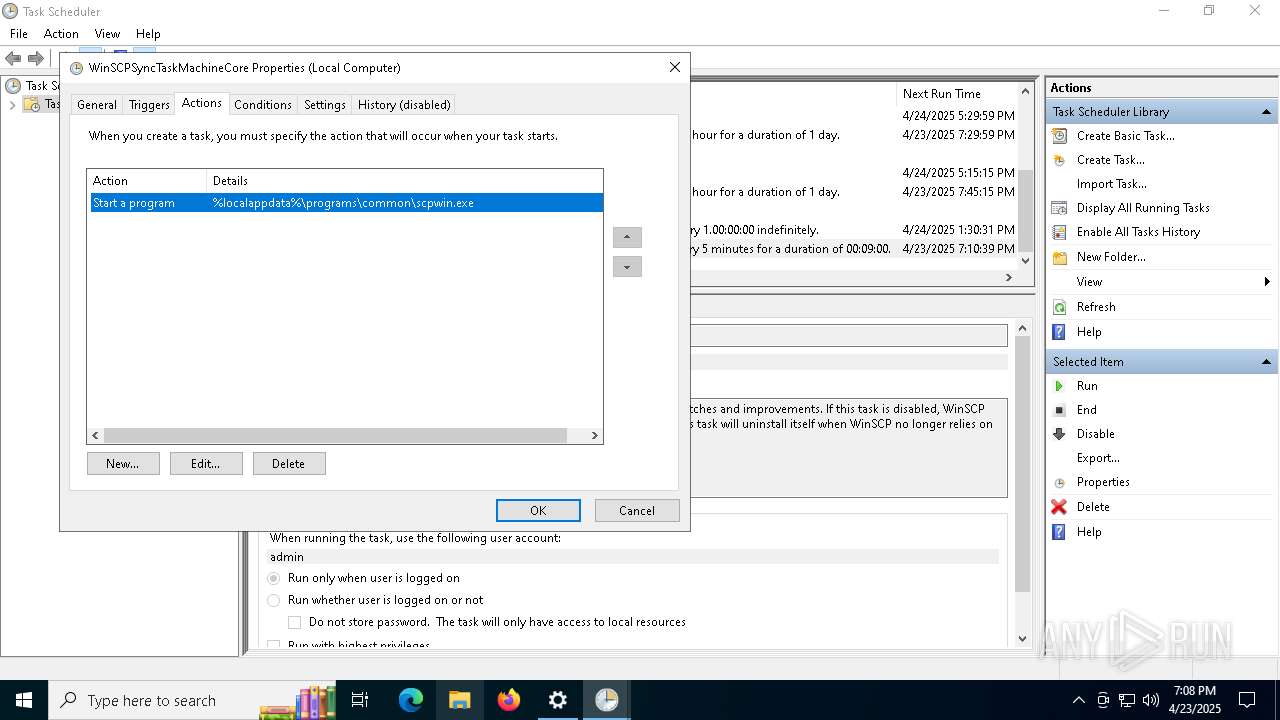
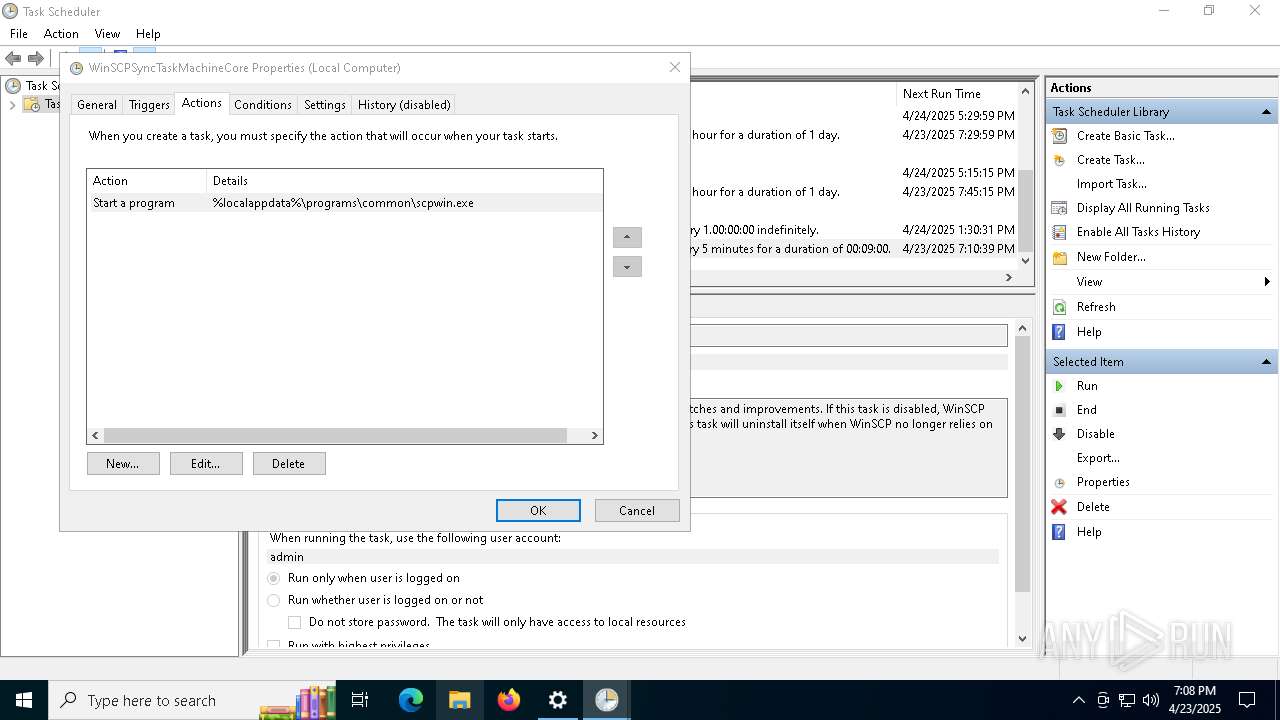
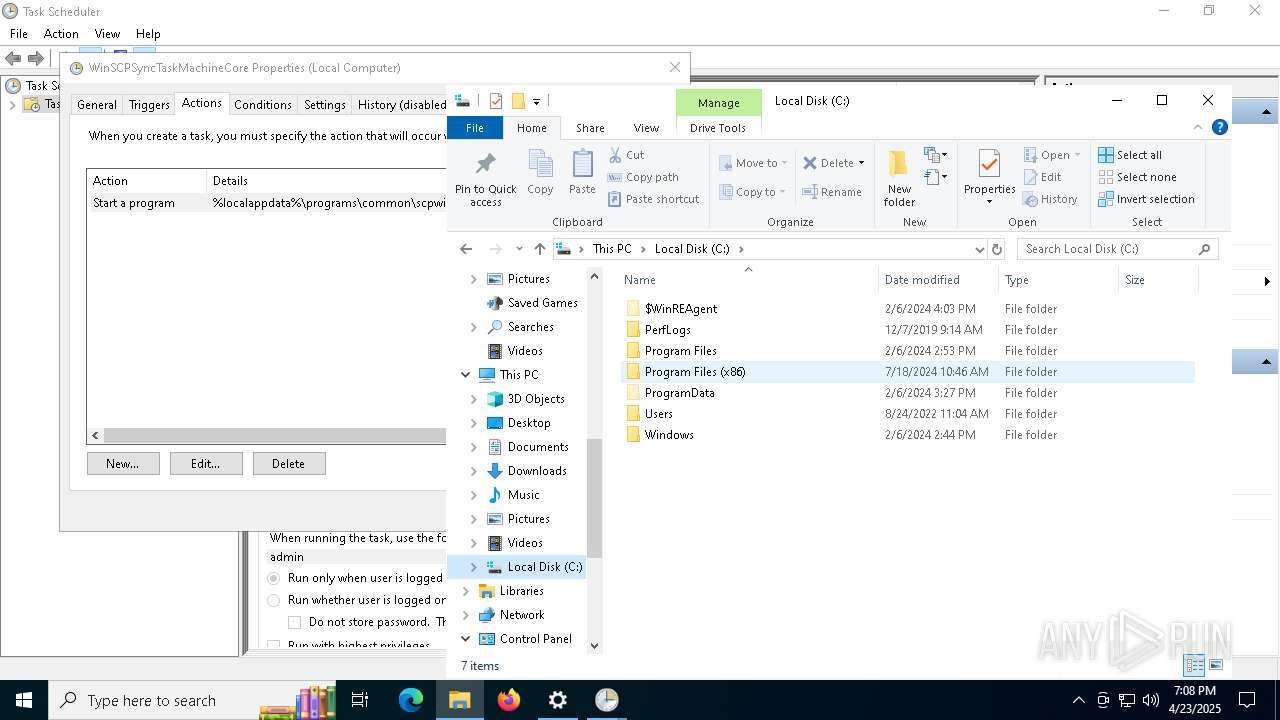
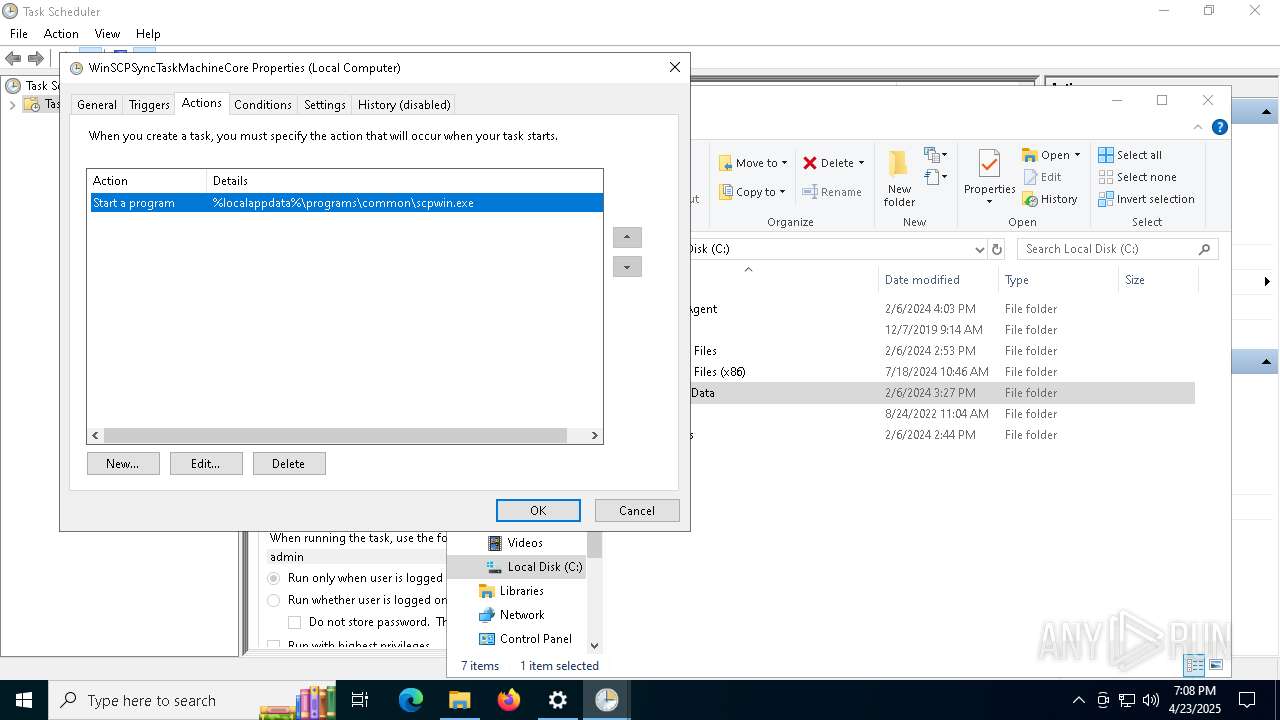
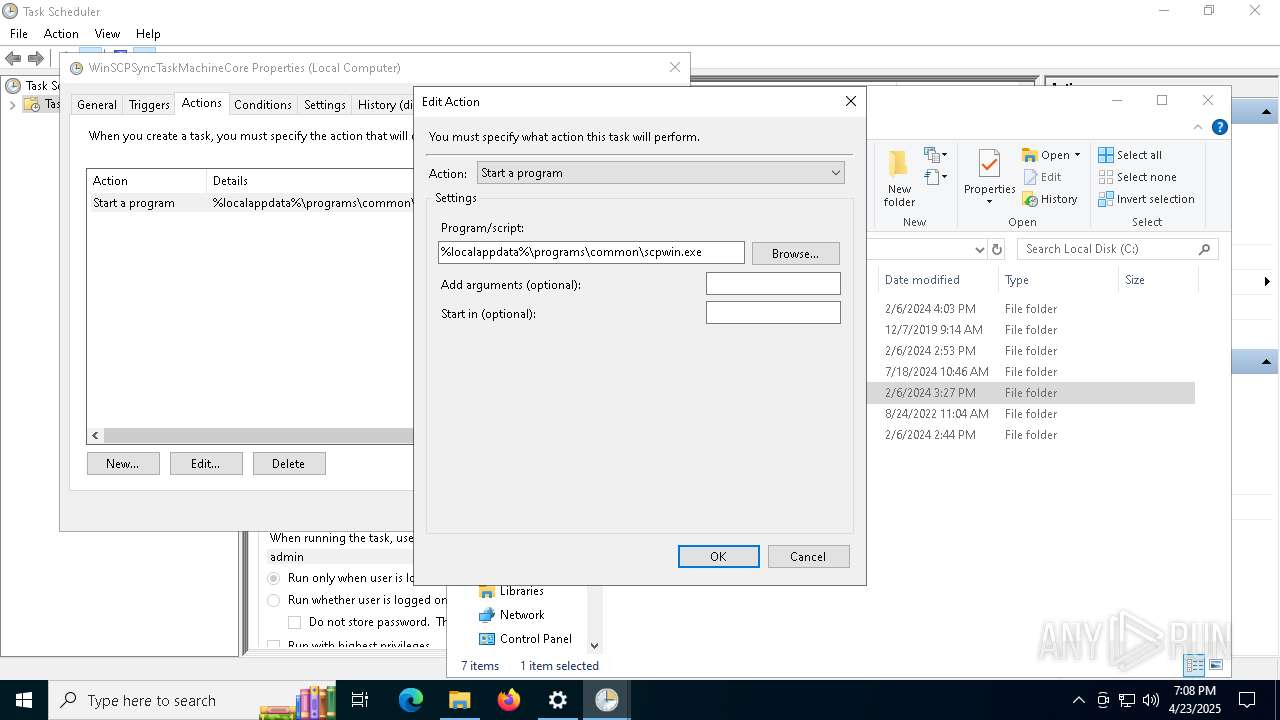
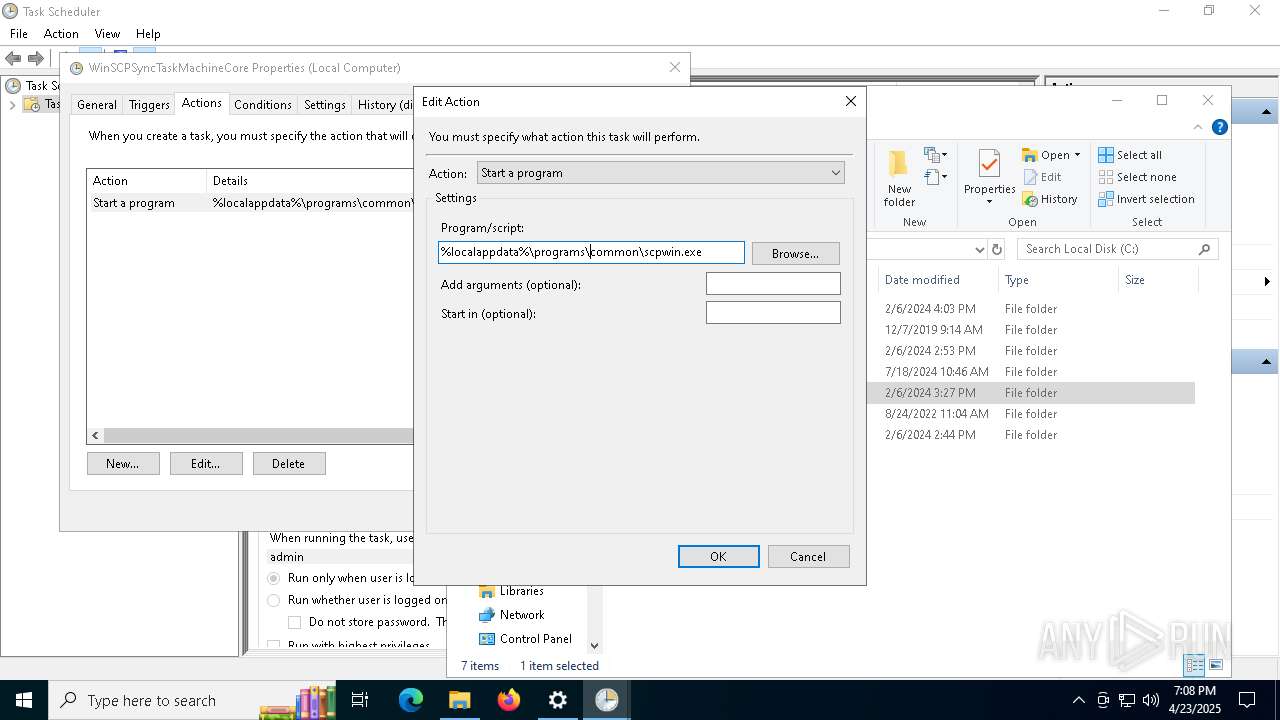
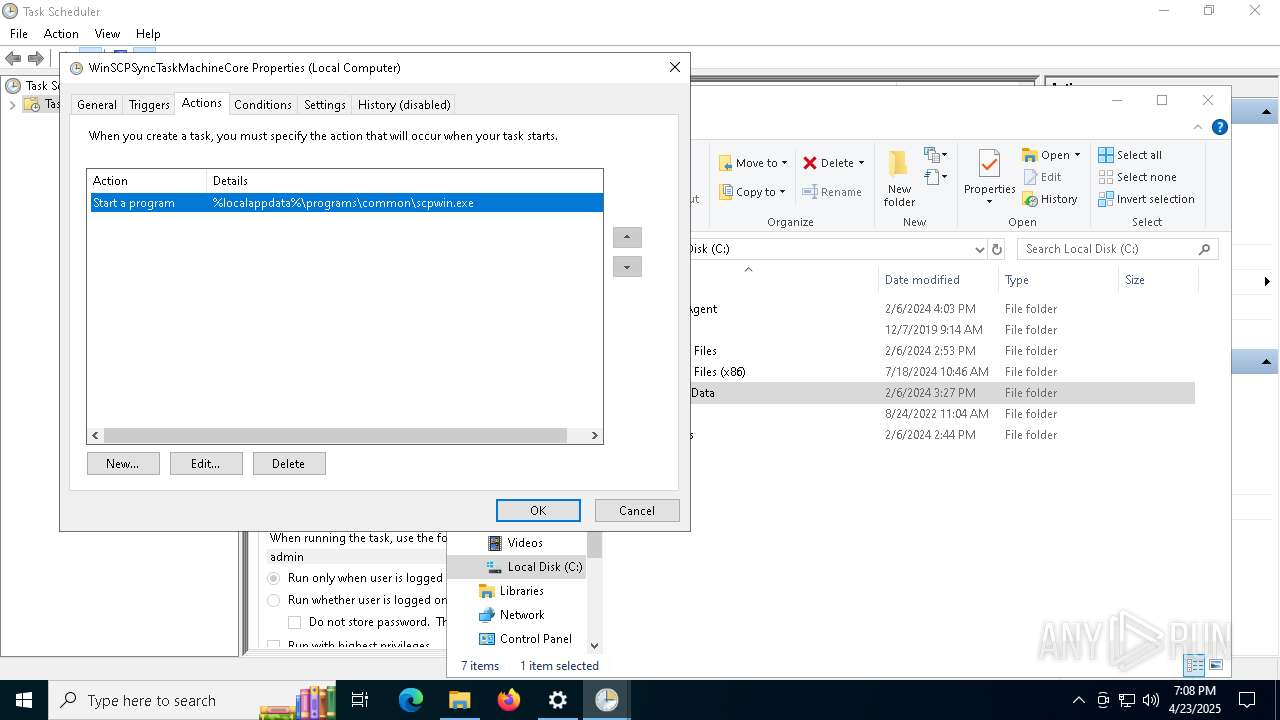
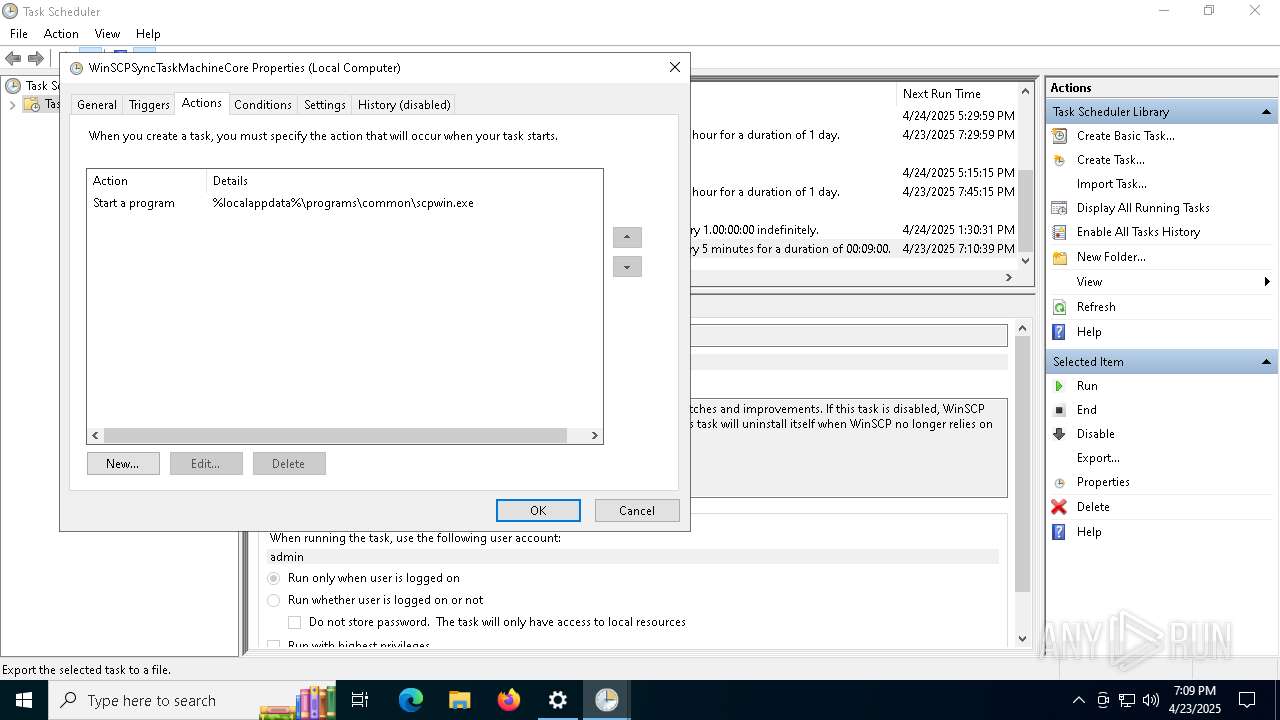
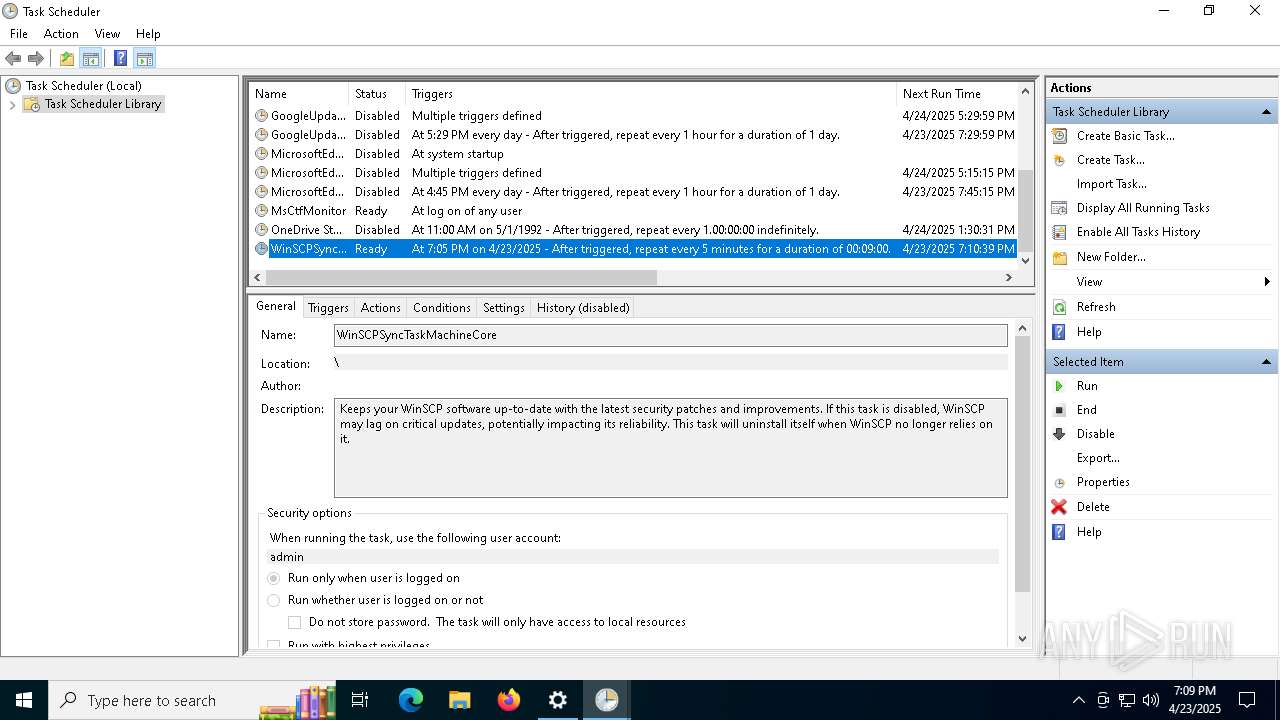
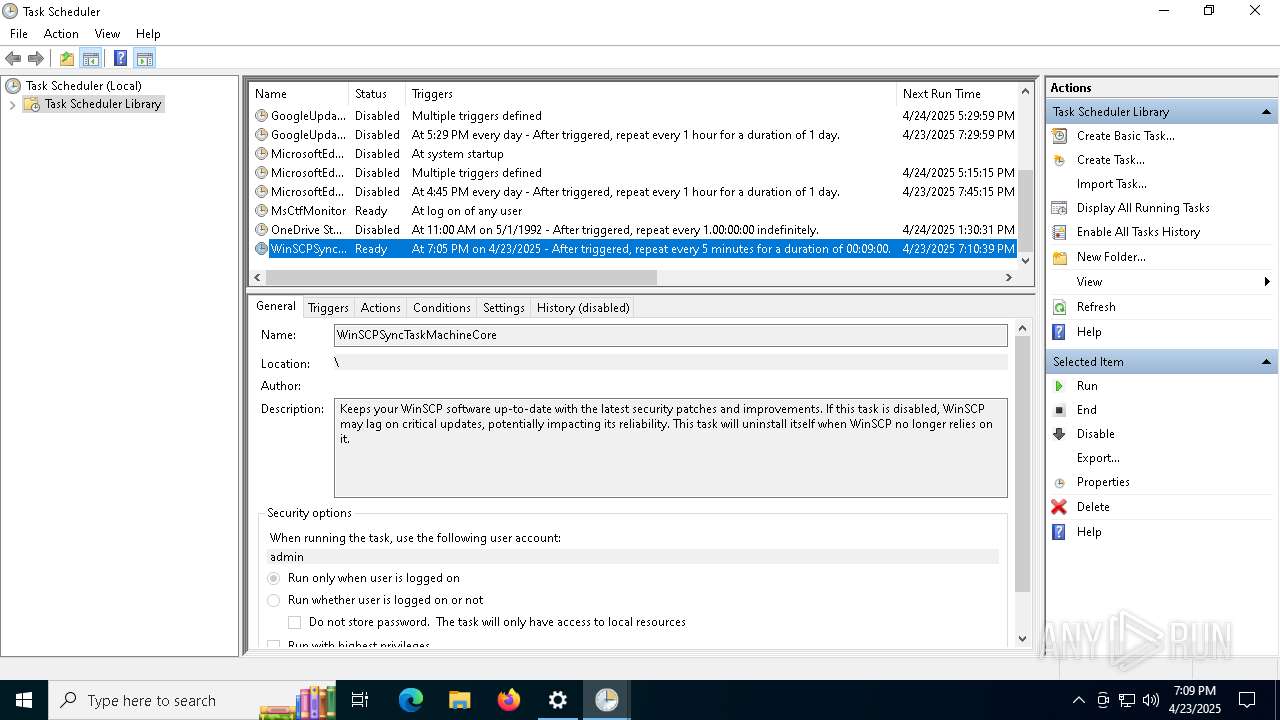
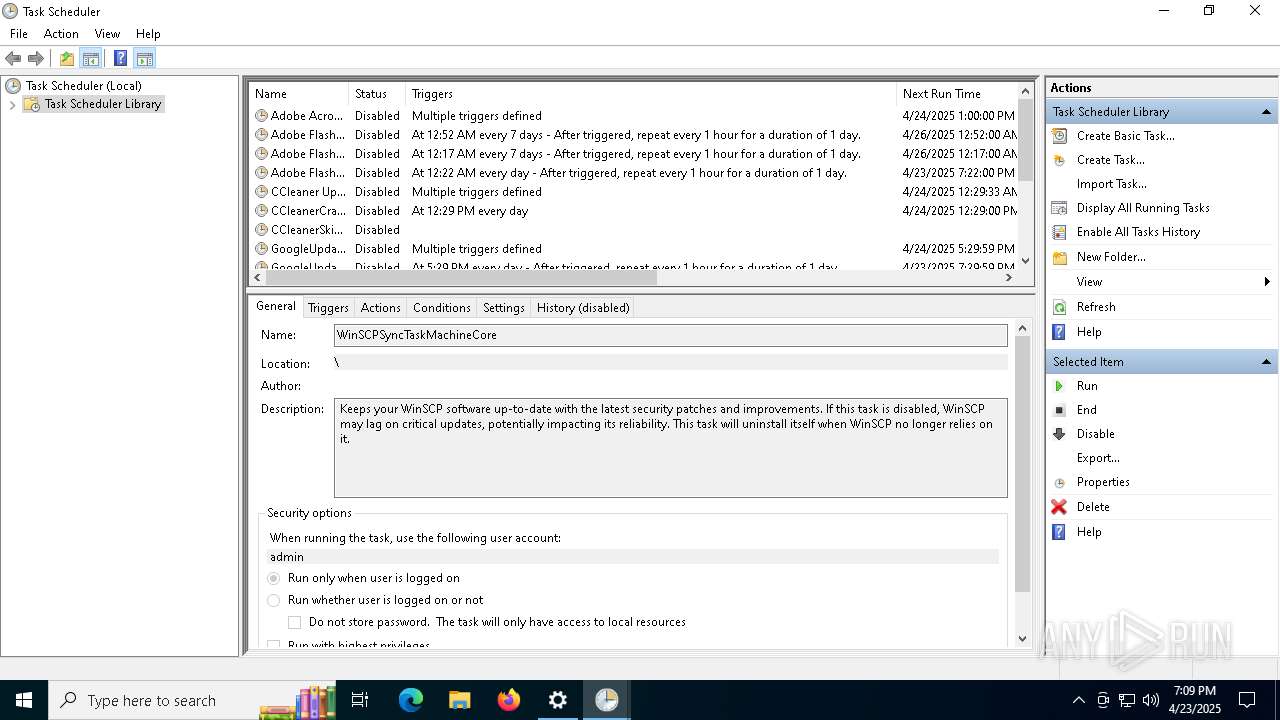
Uses Task Scheduler to run other applications
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
SUSPICIOUS
Executable content was dropped or overwritten
- Partnership Agreement for YouTube Cooperation.exe (PID: 6668)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 4692)
- idp.exe (PID: 7812)
- Partnership Agreement for YouTube Cooperation.exe (PID: 7236)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
Reads the Windows owner or organization settings
- Partnership Agreement for YouTube Cooperation.tmp (PID: 4692)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
Reads security settings of Internet Explorer
- Partnership Agreement for YouTube Cooperation.tmp (PID: 4692)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
Drops 7-zip archiver for unpacking
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7888)
Executing commands from ".cmd" file
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
Starts CMD.EXE for commands execution
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
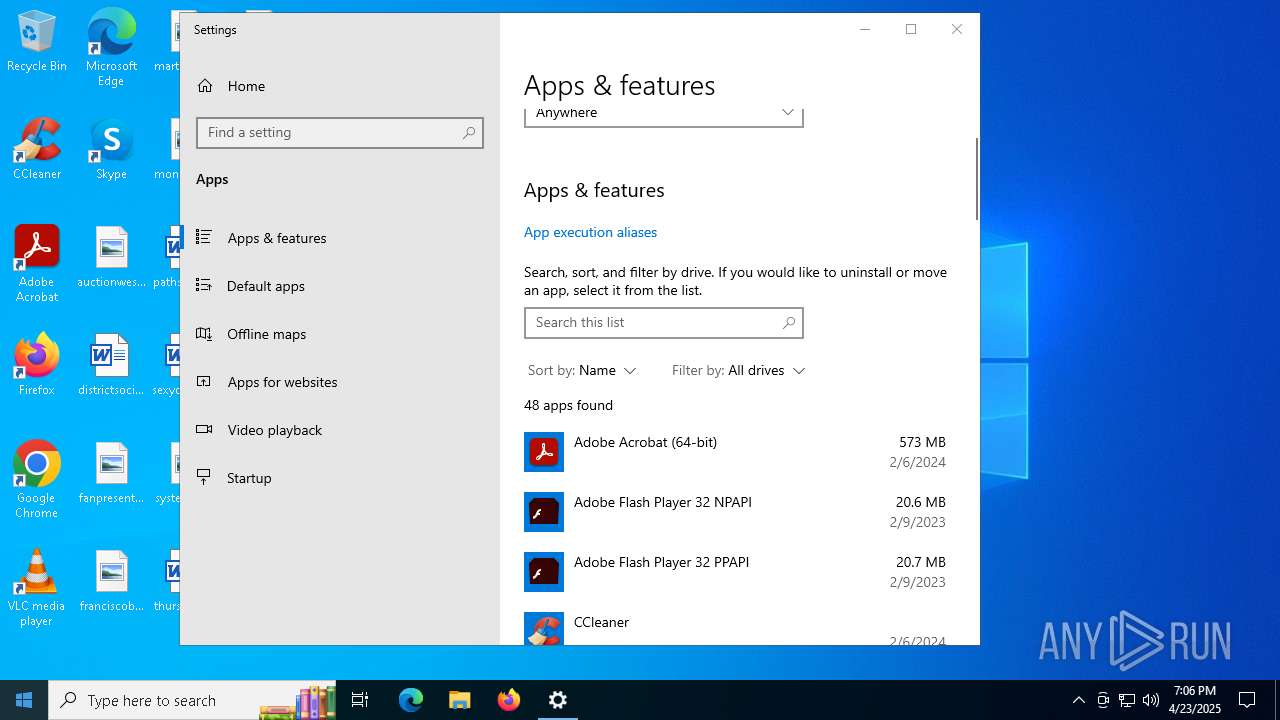
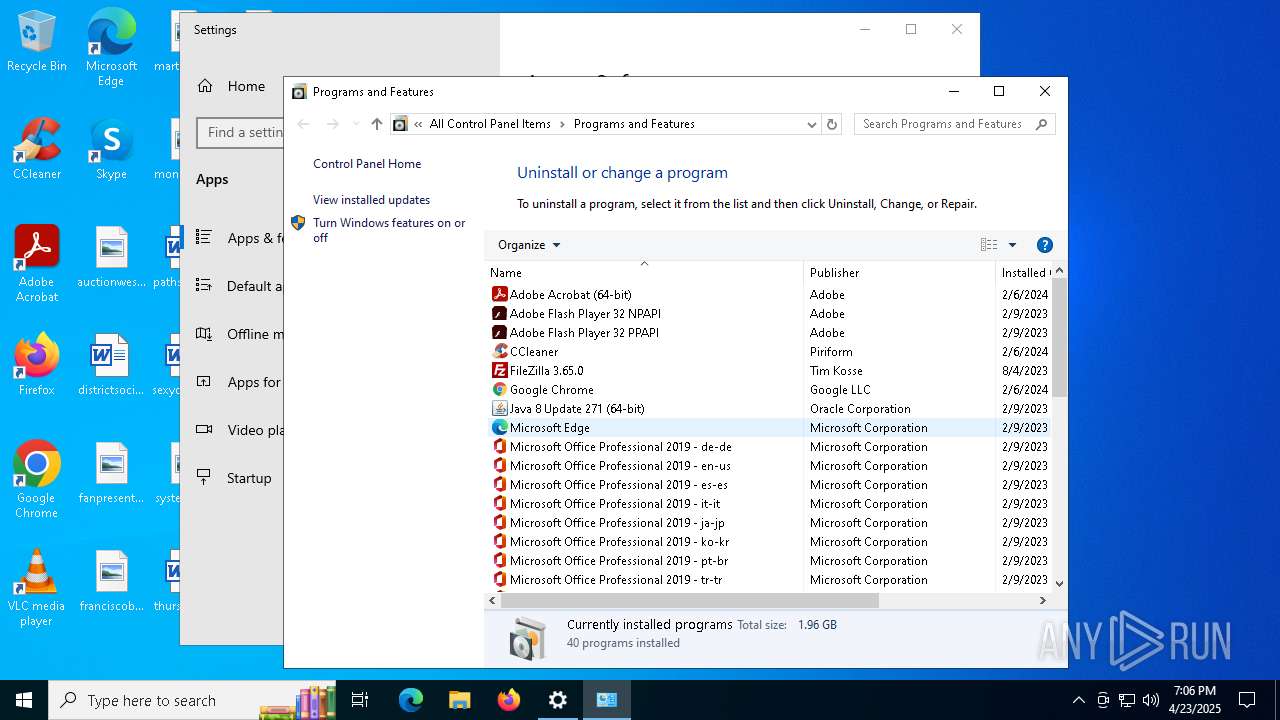
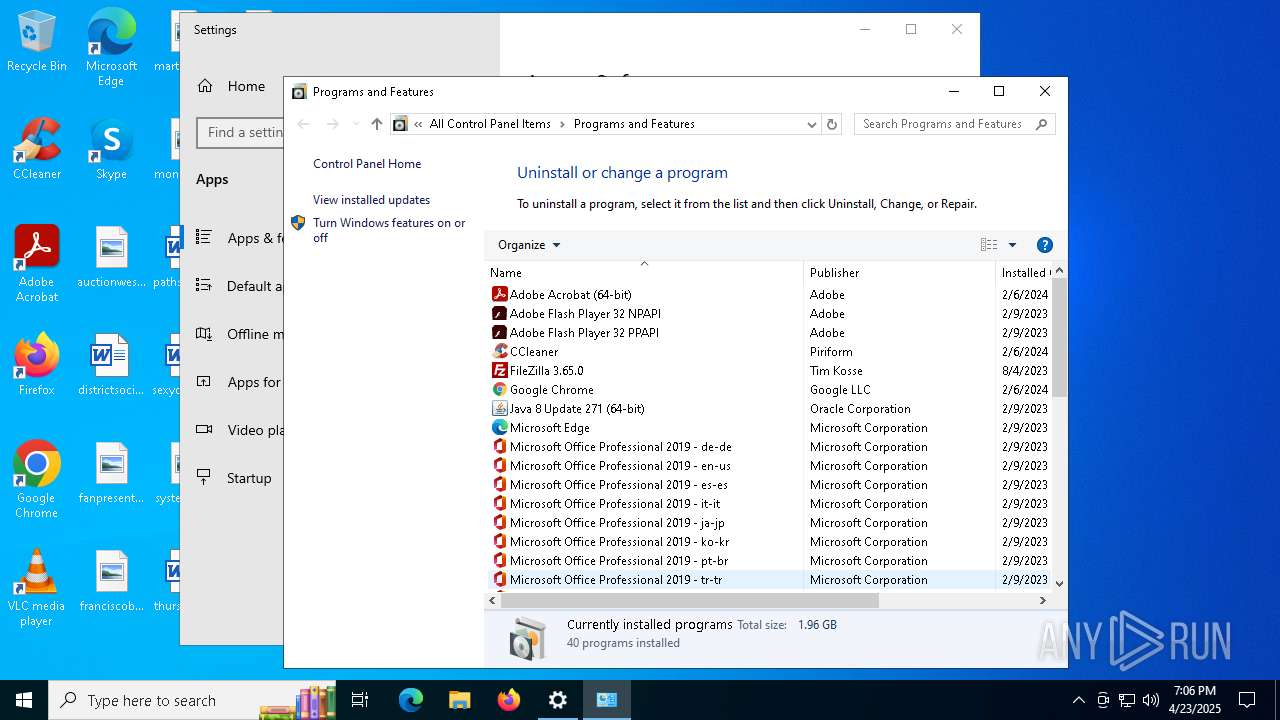
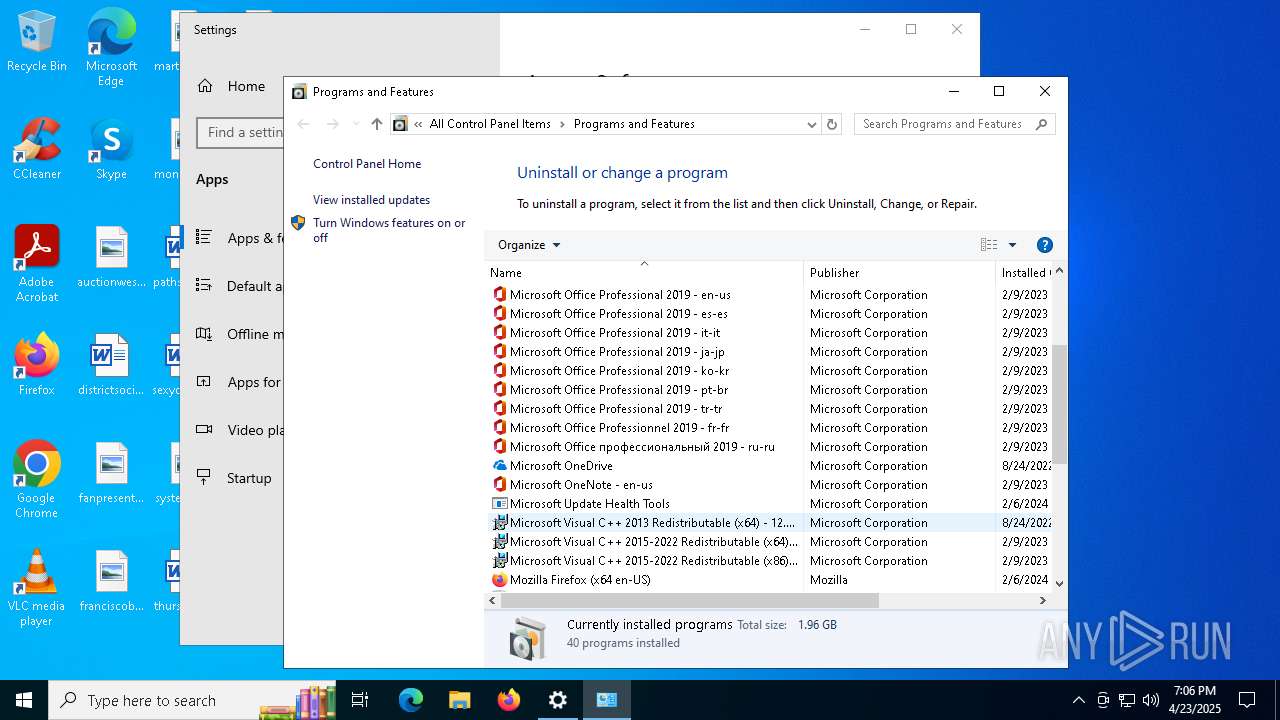
Searches for installed software
- explorer.exe (PID: 7980)
INFO
Checks supported languages
- Partnership Agreement for YouTube Cooperation.exe (PID: 6668)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 4692)
- Partnership Agreement for YouTube Cooperation.exe (PID: 7236)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
- idp.exe (PID: 7812)
Create files in a temporary directory
- Partnership Agreement for YouTube Cooperation.exe (PID: 6668)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 4692)
- Partnership Agreement for YouTube Cooperation.exe (PID: 7236)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
Reads the computer name
- Partnership Agreement for YouTube Cooperation.tmp (PID: 4692)
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
- idp.exe (PID: 7812)
Process checks computer location settings
- Partnership Agreement for YouTube Cooperation.tmp (PID: 4692)
Checks proxy server information
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
- slui.exe (PID: 7644)
Reads the software policy settings
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
- slui.exe (PID: 7392)
- slui.exe (PID: 7644)
Compiled with Borland Delphi (YARA)
- Partnership Agreement for YouTube Cooperation.exe (PID: 7236)
The sample compiled with english language support
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
Creates files or folders in the user directory
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
- idp.exe (PID: 7812)
Detects InnoSetup installer (YARA)
- Partnership Agreement for YouTube Cooperation.exe (PID: 7236)
Manual execution by a user
- mmc.exe (PID: 5324)
- mmc.exe (PID: 2384)
Reads security settings of Internet Explorer
- mmc.exe (PID: 2384)
Reads the machine GUID from the registry
- Partnership Agreement for YouTube Cooperation.tmp (PID: 7264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:06 14:39:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 83456 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x117dc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.1.3.73 |
| ProductVersionNumber: | 7.1.3.73 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | YouTube Cooperation |
| FileDescription: | Partnership Agreement for YT Cooperation |
| FileVersion: | 7.1.3.73 |
| LegalCopyright: | |
| ProductName: | YouTube Cooperation |
| ProductVersion: | 7.1.3.73 |
Total processes
164
Monitored processes
21
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2384 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4692 | "C:\Users\admin\AppData\Local\Temp\is-DLMAU.tmp\Partnership Agreement for YouTube Cooperation.tmp" /SL5="$6026C,616681,151040,C:\Users\admin\Desktop\Partnership Agreement for YouTube Cooperation.exe" | C:\Users\admin\AppData\Local\Temp\is-DLMAU.tmp\Partnership Agreement for YouTube Cooperation.tmp | Partnership Agreement for YouTube Cooperation.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 5324 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\taskschd.msc" /s | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6668 | "C:\Users\admin\Desktop\Partnership Agreement for YouTube Cooperation.exe" | C:\Users\admin\Desktop\Partnership Agreement for YouTube Cooperation.exe | explorer.exe | ||||||||||||
User: admin Company: YouTube Cooperation Integrity Level: MEDIUM Description: Partnership Agreement for YT Cooperation Exit code: 1 Version: 7.1.3.73 Modules
| |||||||||||||||
| 6960 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7236 | "C:\Users\admin\Desktop\Partnership Agreement for YouTube Cooperation.exe" /verysilent /sp- | C:\Users\admin\Desktop\Partnership Agreement for YouTube Cooperation.exe | Partnership Agreement for YouTube Cooperation.tmp | ||||||||||||
User: admin Company: YouTube Cooperation Integrity Level: MEDIUM Description: Partnership Agreement for YT Cooperation Exit code: 0 Version: 7.1.3.73 Modules
| |||||||||||||||
| 7264 | "C:\Users\admin\AppData\Local\Temp\is-VFJMC.tmp\Partnership Agreement for YouTube Cooperation.tmp" /SL5="$7026C,616681,151040,C:\Users\admin\Desktop\Partnership Agreement for YouTube Cooperation.exe" /verysilent /sp- | C:\Users\admin\AppData\Local\Temp\is-VFJMC.tmp\Partnership Agreement for YouTube Cooperation.tmp | Partnership Agreement for YouTube Cooperation.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 7360 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7392 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7644 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 380
Read events
17 345
Write events
33
Delete events
2
Modification events
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0000000004000000030000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\0\1 |
| Operation: | write | Name: | MRUListEx |
Value: 05000000000000000600000002000000010000000400000003000000FFFFFFFF | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\Microsoft.Windows.ControlPanel |
| Operation: | write | Name: | WFlags |
Value: 0 | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\Microsoft.Windows.ControlPanel |
| Operation: | write | Name: | ShowCmd |
Value: 1 | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\Microsoft.Windows.ControlPanel |
| Operation: | write | Name: | HotKey |
Value: 0 | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\77\Shell\{D674391B-52D9-4E07-834E-67C98610F39D} |
| Operation: | write | Name: | Rev |
Value: 0 | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\77\Shell\{D674391B-52D9-4E07-834E-67C98610F39D} |
| Operation: | write | Name: | FFlags |
Value: 18874433 | |||
| (PID) Process: | (7980) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\77\Shell\{D674391B-52D9-4E07-834E-67C98610F39D} |
| Operation: | write | Name: | Vid |
Value: {137E7700-3573-11CF-AE69-08002B2E1262} | |||
Executable files
9
Suspicious files
6
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7264 | Partnership Agreement for YouTube Cooperation.tmp | C:\Users\admin\AppData\Local\Temp\is-JQAVK.tmp\logs | — | |
MD5:— | SHA256:— | |||
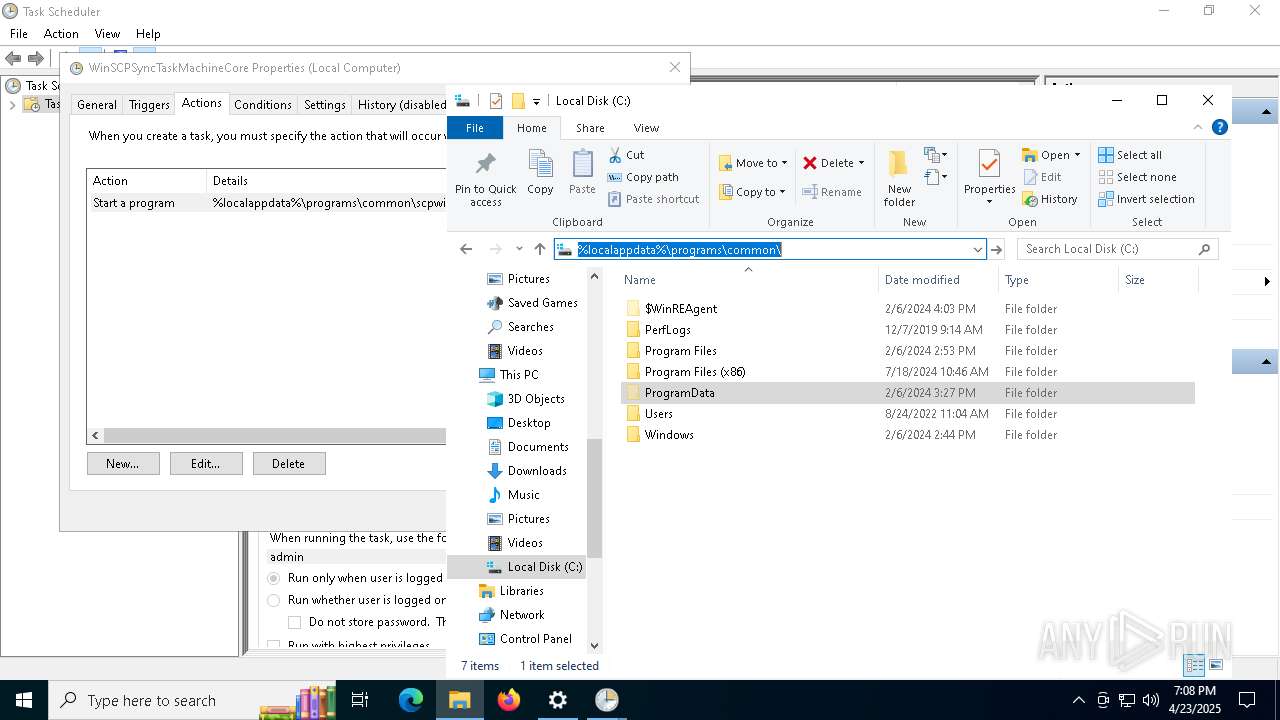
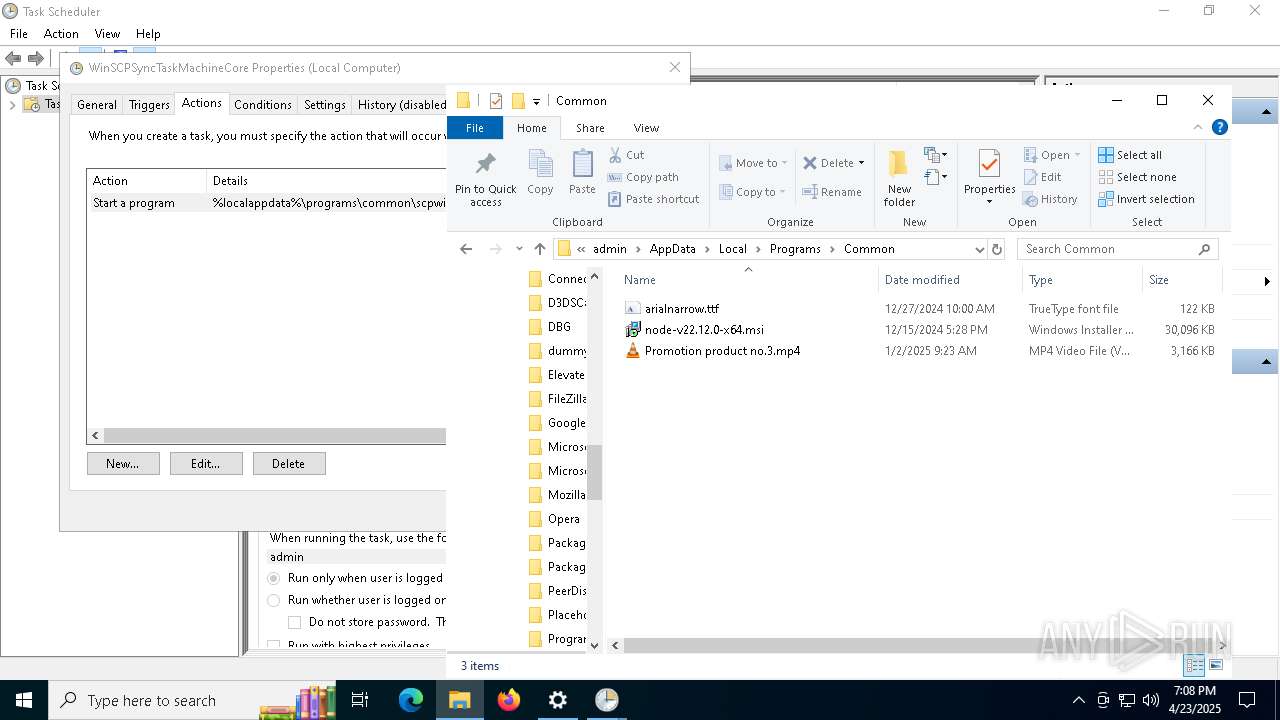
| 7812 | idp.exe | C:\Users\admin\AppData\Local\Programs\Common\node-v22.12.0-x64.msi | — | |
MD5:— | SHA256:— | |||
| 4692 | Partnership Agreement for YouTube Cooperation.tmp | C:\Users\admin\AppData\Local\Temp\is-QNA3R.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
| 7264 | Partnership Agreement for YouTube Cooperation.tmp | C:\Users\admin\AppData\Local\Temp\is-JQAVK.tmp\lang | xml | |
MD5:2135B15BB480EF462579D3F41B6614FC | SHA256:36276D88C584561A46F112B7124565E246199CDCC03C73F40D6E5750041F7629 | |||
| 7264 | Partnership Agreement for YouTube Cooperation.tmp | C:\Users\admin\AppData\Local\Temp\is-JQAVK.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
| 7264 | Partnership Agreement for YouTube Cooperation.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 7264 | Partnership Agreement for YouTube Cooperation.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\15FB0A7CD862229BC0D44684B9B989DB_A664EFC5A91FE41DE2ECB835E550D049 | binary | |
MD5:3C30B38ADC9A664733649644E7540C4D | SHA256:A855FD3ADB78E59B813BBCC283AD090ECF69C311176182A6FC16349F6DF7EC8A | |||
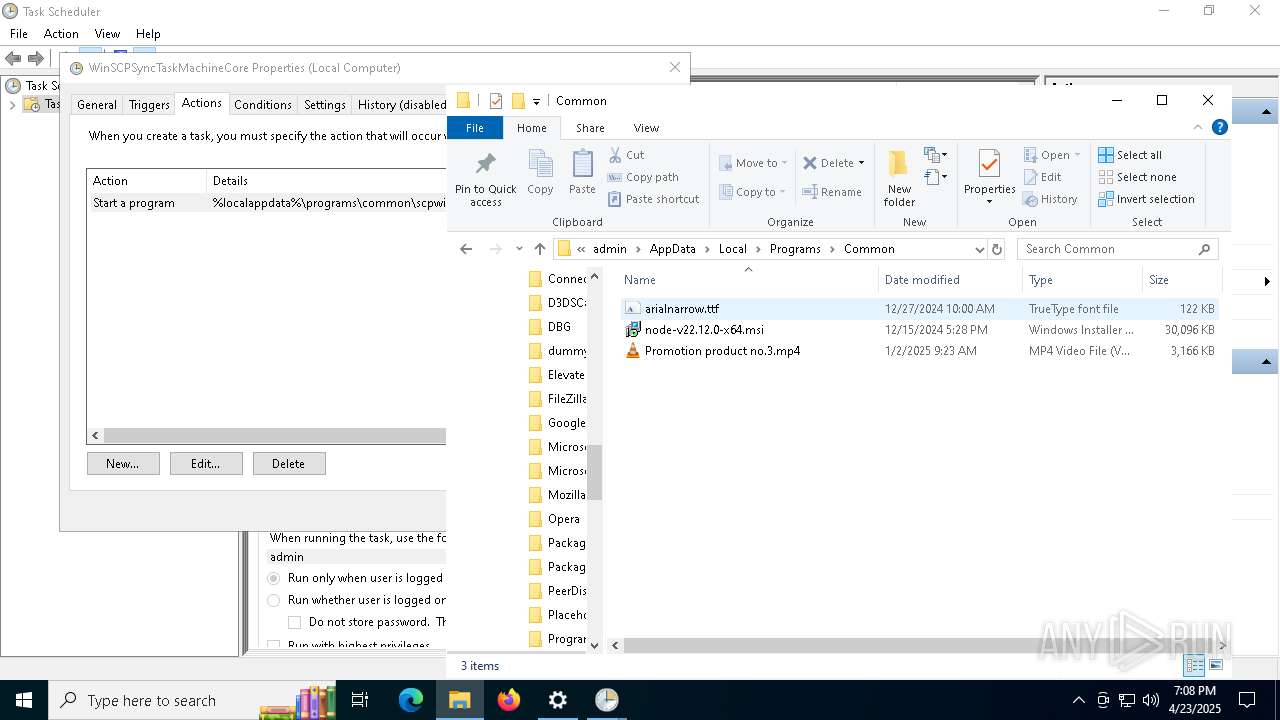
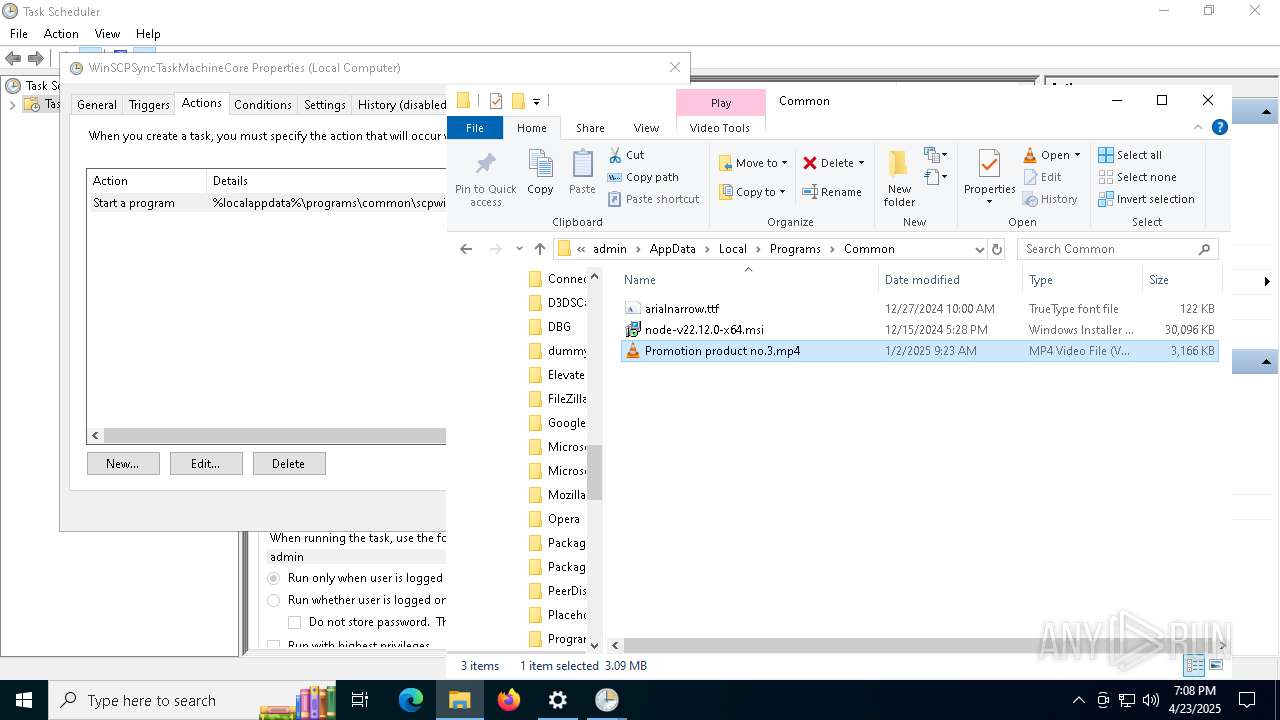
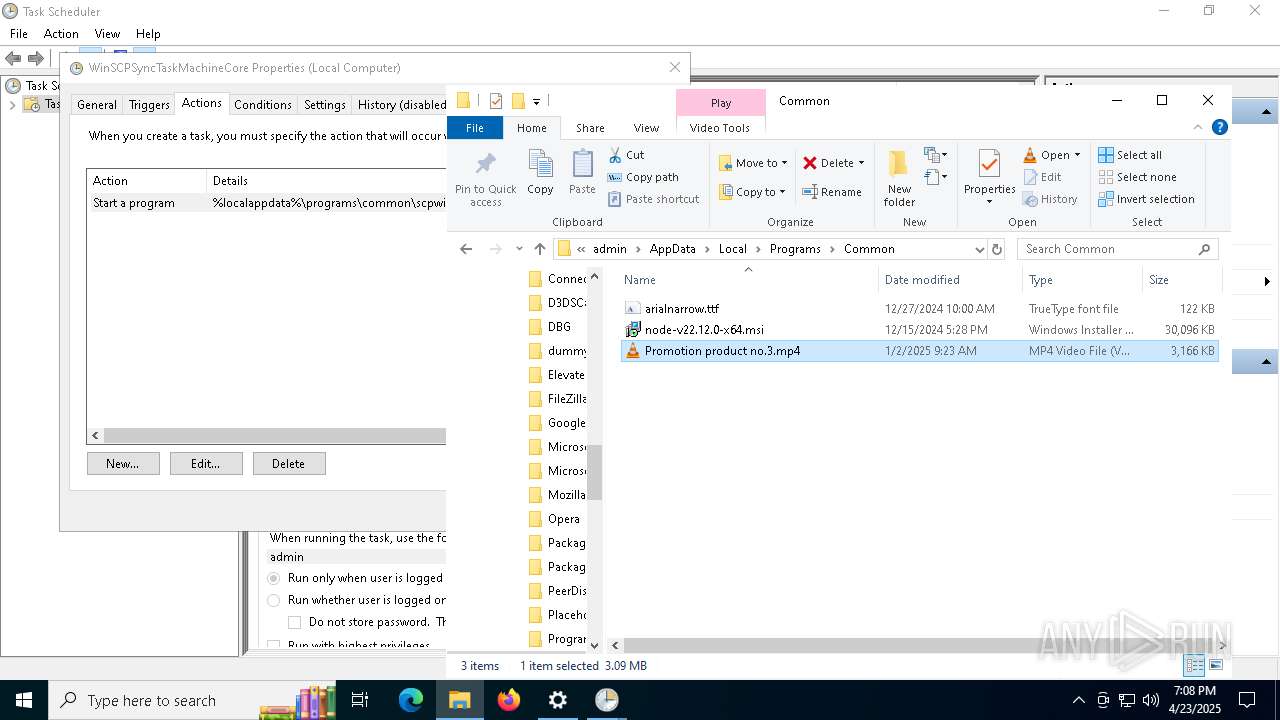
| 7812 | idp.exe | C:\Users\admin\AppData\Local\Programs\Common\Promotion product no.3.mp4 | binary | |
MD5:2B03D81599A02F52375608AEED62F254 | SHA256:2D3460D221D9C78C23A9BE39CF061E7564B76B413A39FC9F9184ADEFDBF31C8F | |||
| 7812 | idp.exe | C:\Users\admin\AppData\Local\Programs\Common\AdRem.exe | executable | |
MD5:B9B2CEA3D0188745EEE88719A5FAEFB3 | SHA256:217DAF8248177FCE9FA69FED22B43C32D8B8823EEDA886CD15CF4FC69F3E986D | |||
| 7264 | Partnership Agreement for YouTube Cooperation.tmp | C:\Users\admin\AppData\Local\Temp\is-JQAVK.tmp\idp.exe | executable | |
MD5:6482EE0F372469D1190C74BD70D76153 | SHA256:4B7FC7818F3168945DBEDADCFD7AAF470B88543EF6B685619AD1C942AC3B1DED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
63
DNS requests
46
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.48.23.185:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7264 | Partnership Agreement for YouTube Cooperation.tmp | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7264 | Partnership Agreement for YouTube Cooperation.tmp | GET | 200 | 184.24.77.79:80 | http://e6.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBTUejiAQejpjQc4fOz2ttjyD6VkMQQUDcXM%2FZvuFAWhTDCCpT5eisNYCdICEgVYbazQZAP%2FEajNeAopFEBc7g%3D%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8188 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8188 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4156 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 23.48.23.185:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7264 | Partnership Agreement for YouTube Cooperation.tmp | 104.18.111.161:443 | tinyurl.com | CLOUDFLARENET | — | whitelisted |
7264 | Partnership Agreement for YouTube Cooperation.tmp | 164.132.58.105:443 | rentry.org | OVH SAS | FR | suspicious |
7264 | Partnership Agreement for YouTube Cooperation.tmp | 148.251.0.164:443 | nascacs.co.za | Hetzner Online GmbH | DE | shared |
7264 | Partnership Agreement for YouTube Cooperation.tmp | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
tinyurl.com |
| whitelisted |
rentry.org |
| unknown |
nascacs.co.za |
| shared |
x1.c.lencr.org |
| whitelisted |
e6.o.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
2196 | svchost.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |