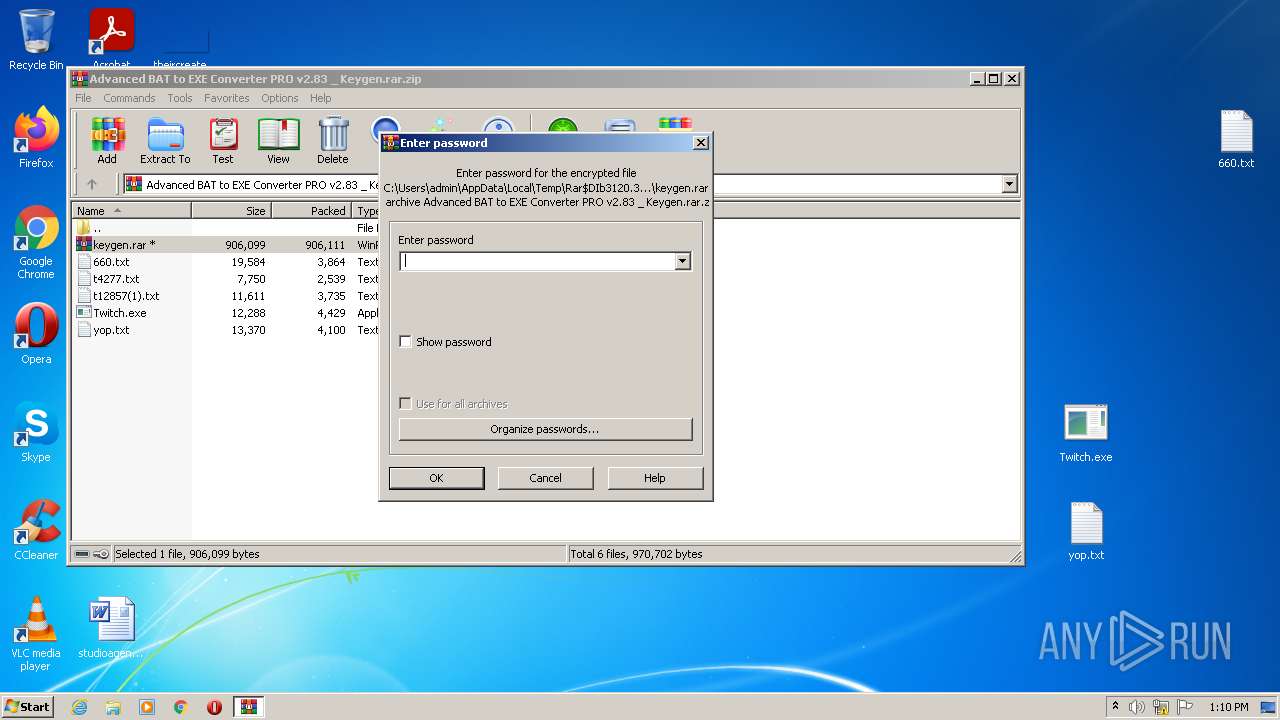
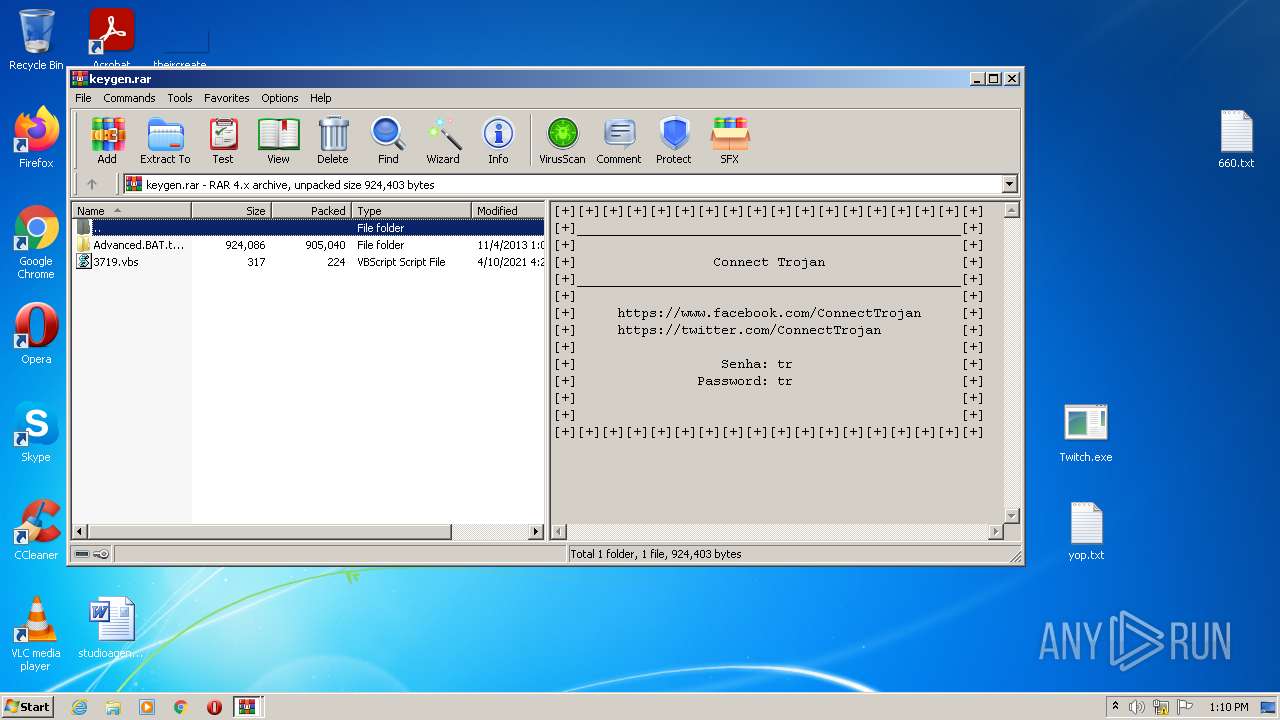
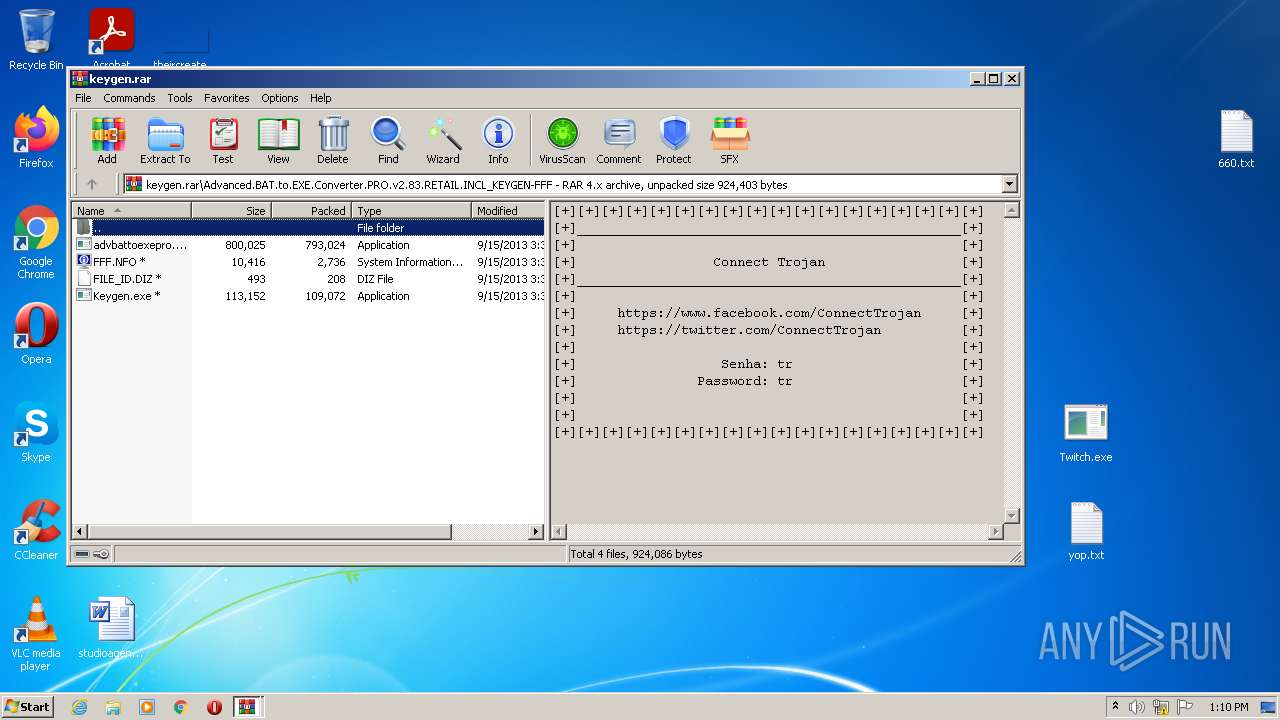
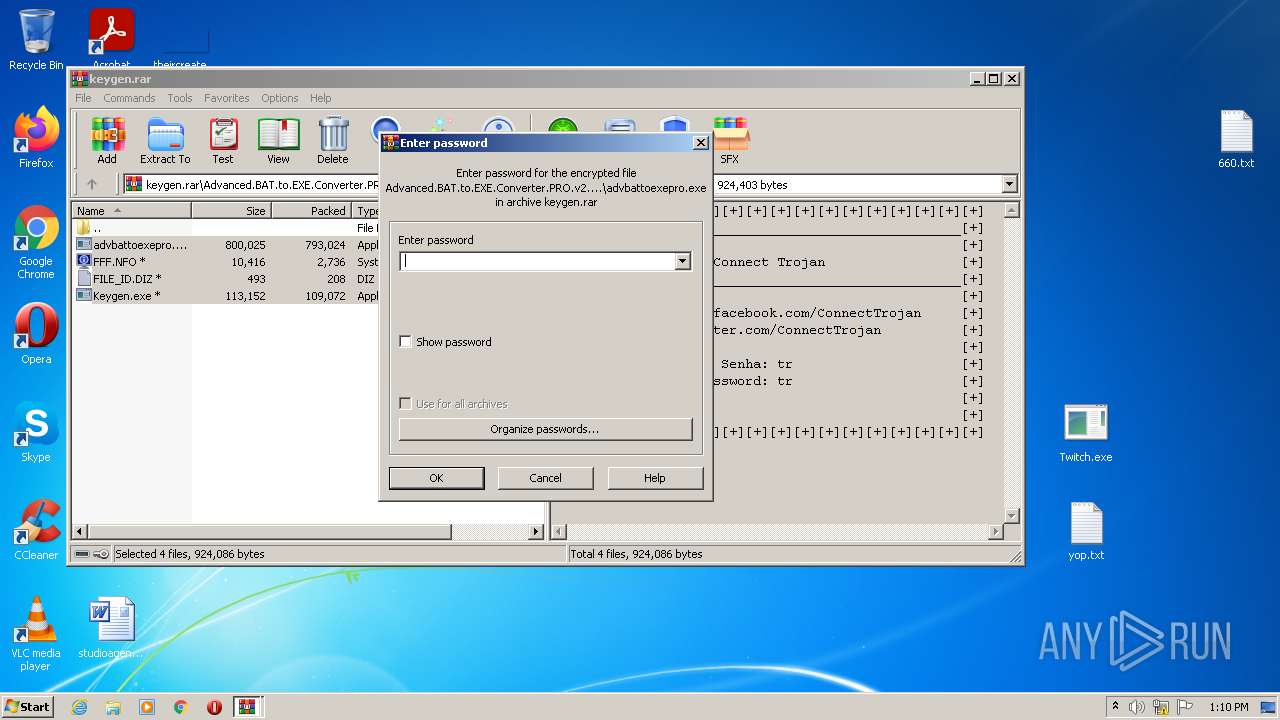
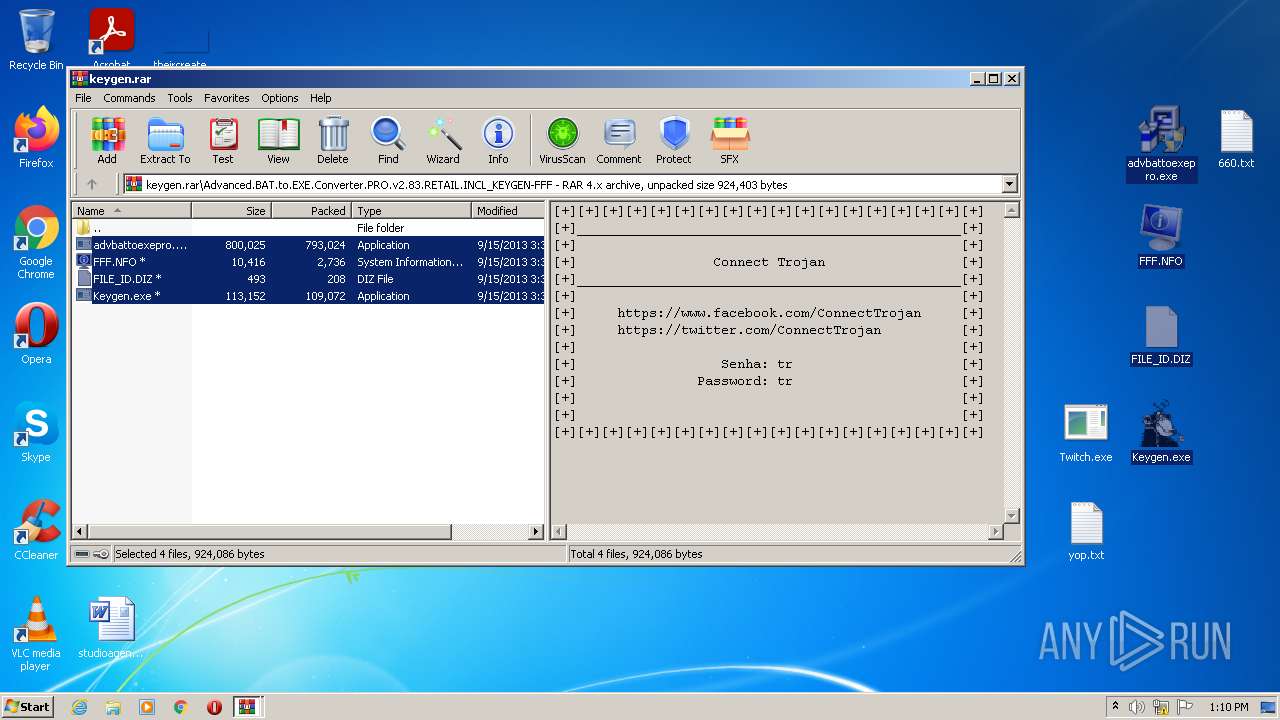
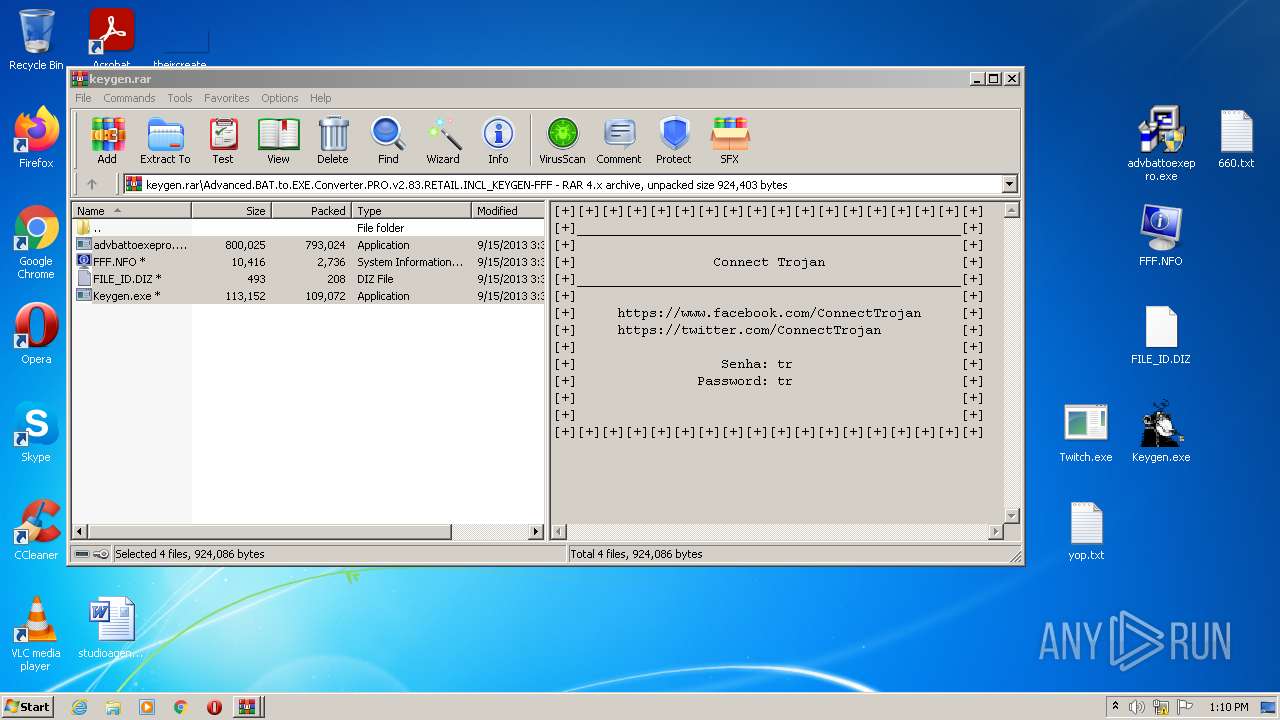
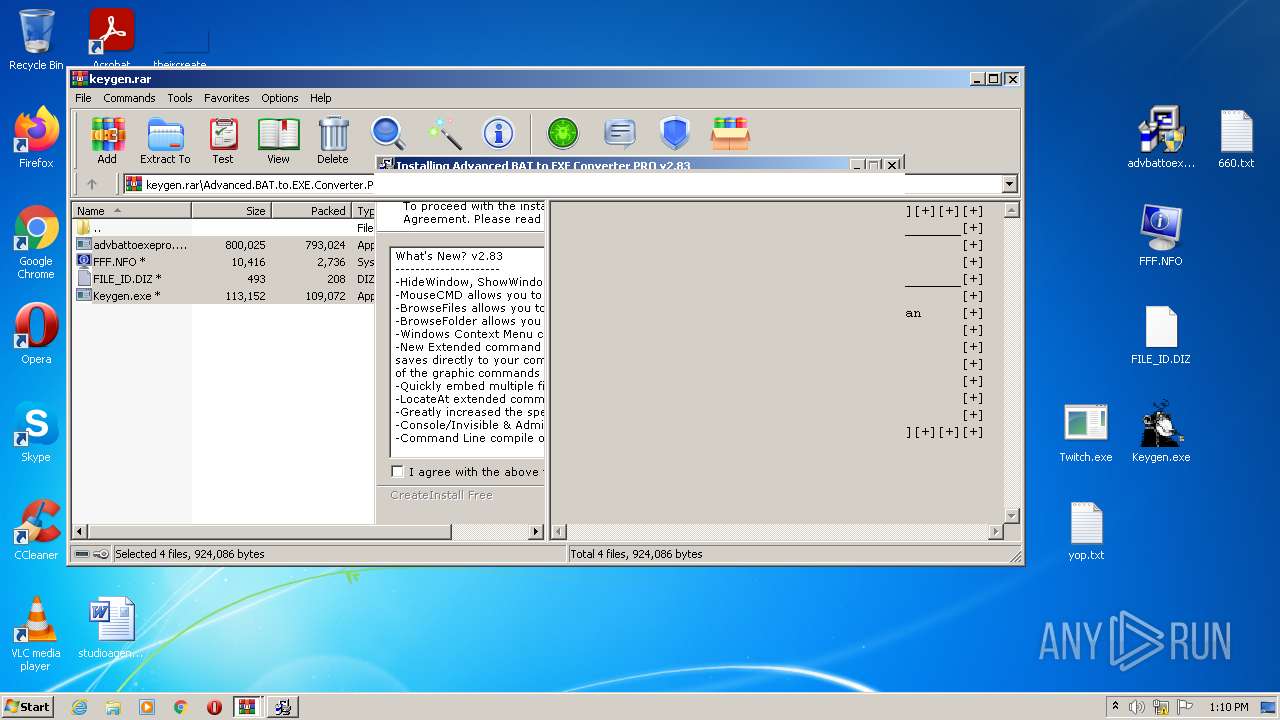
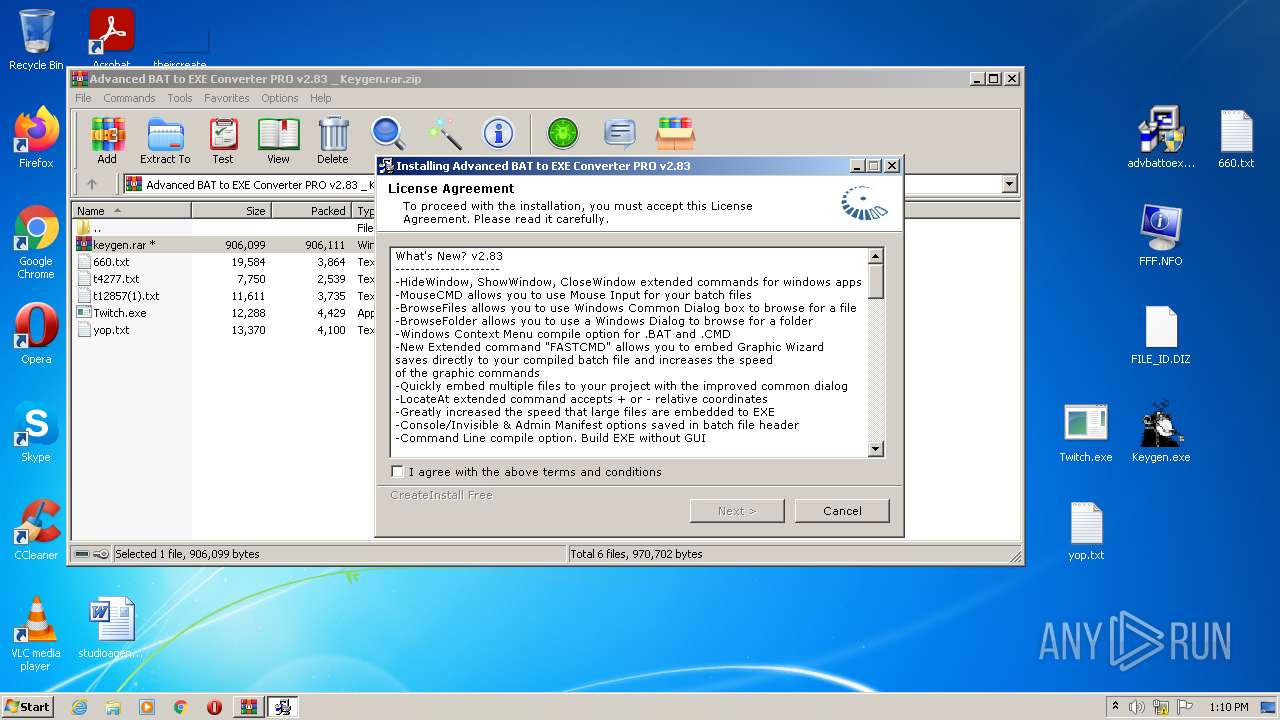
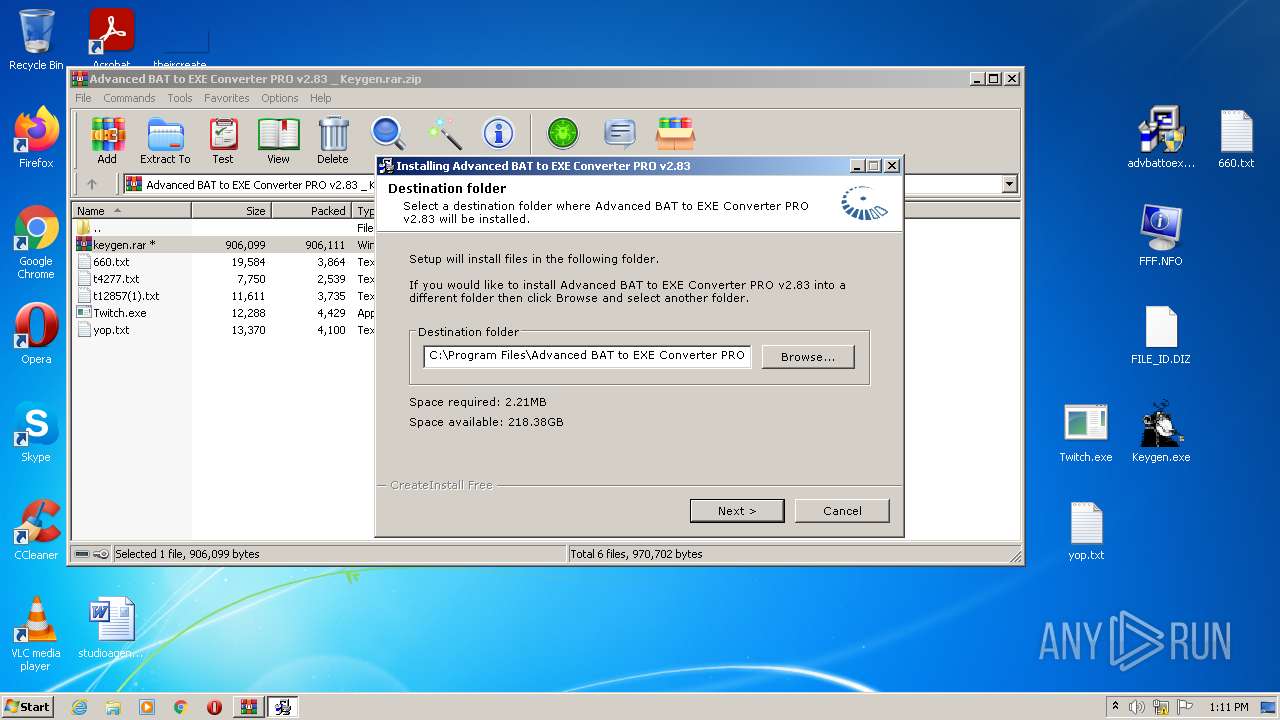
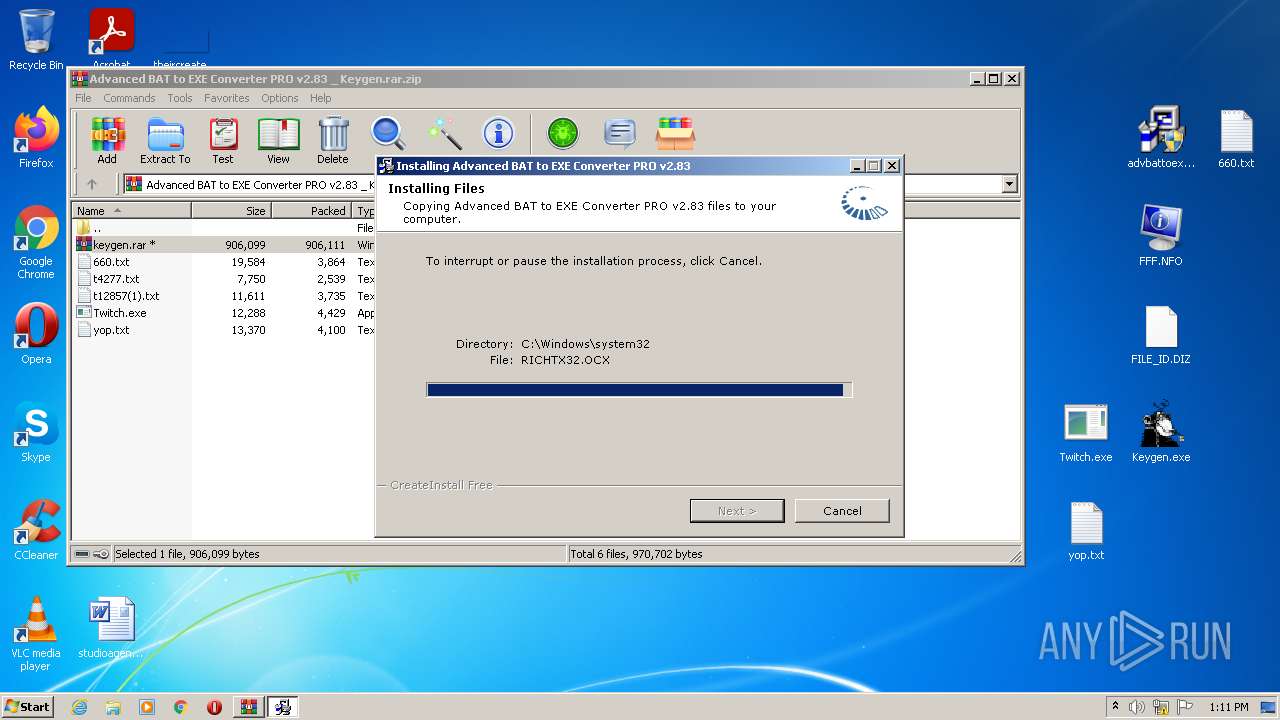
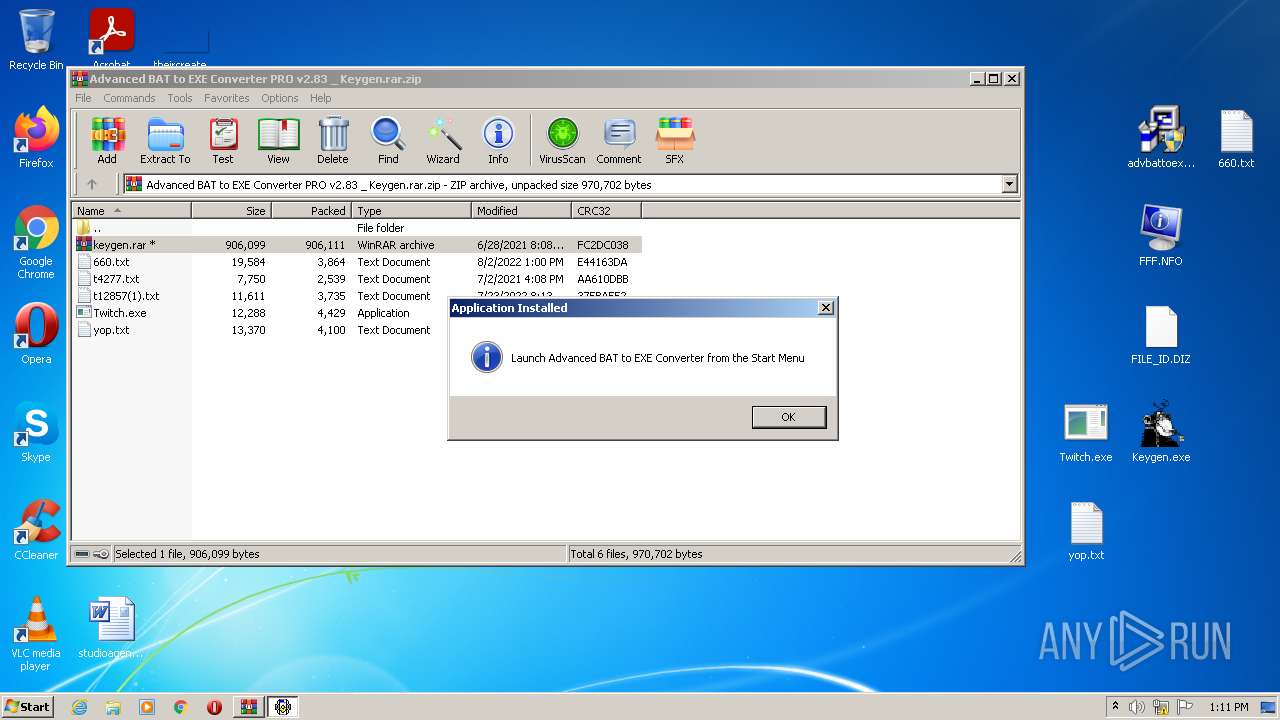
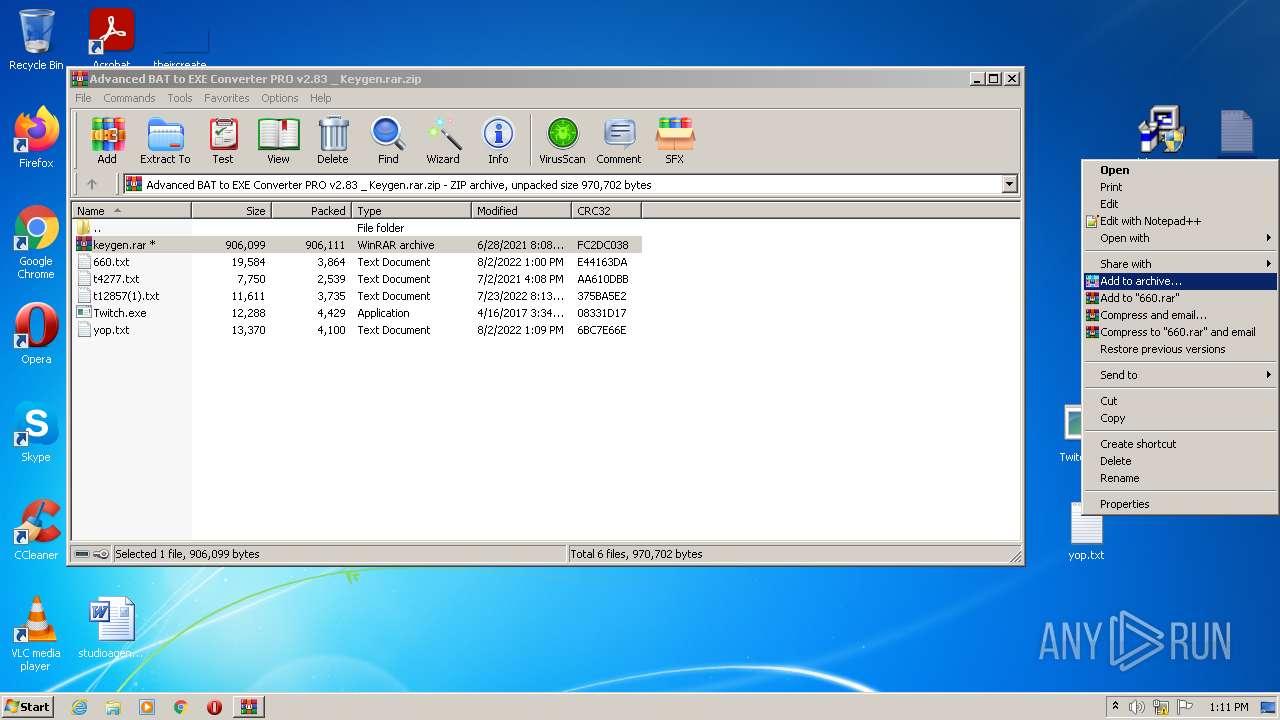
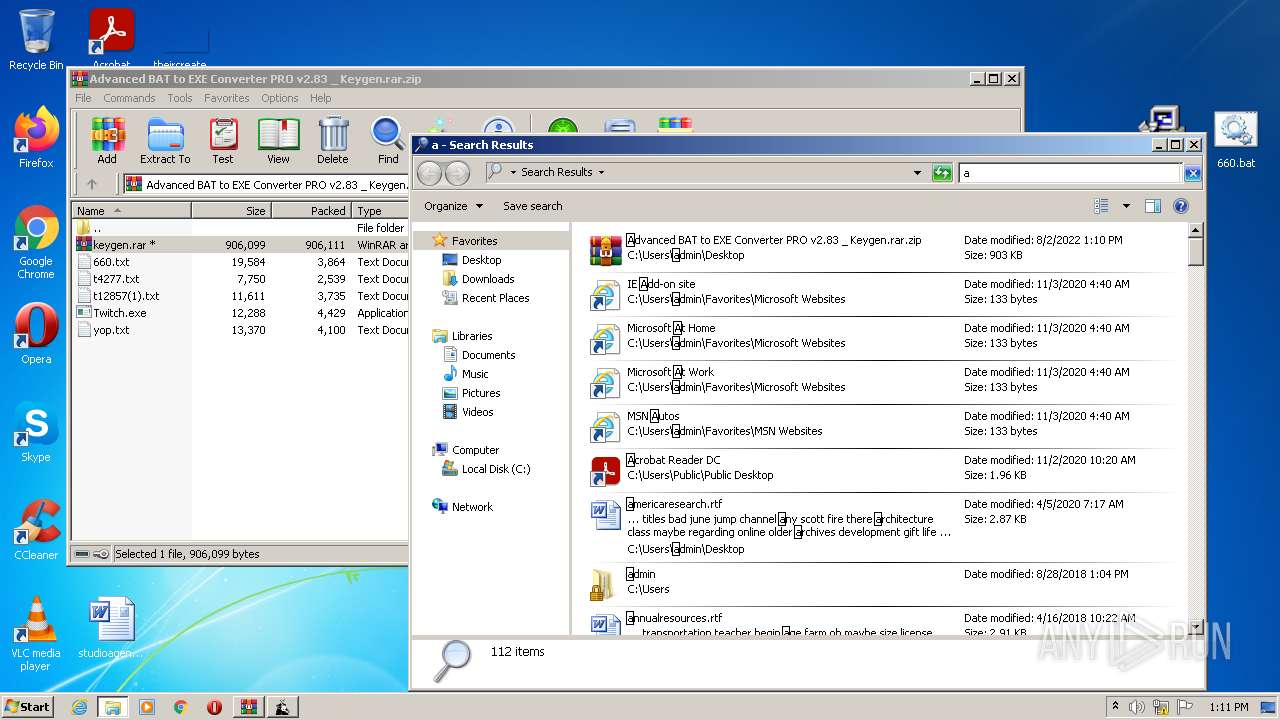
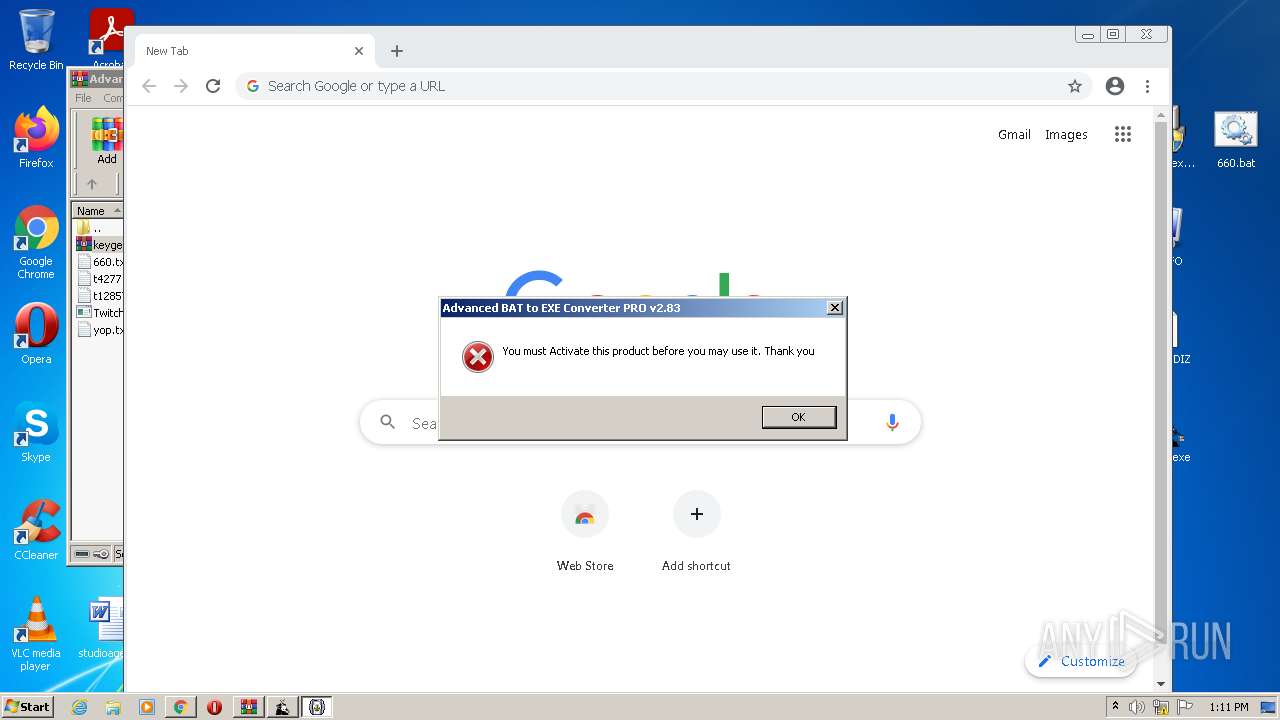
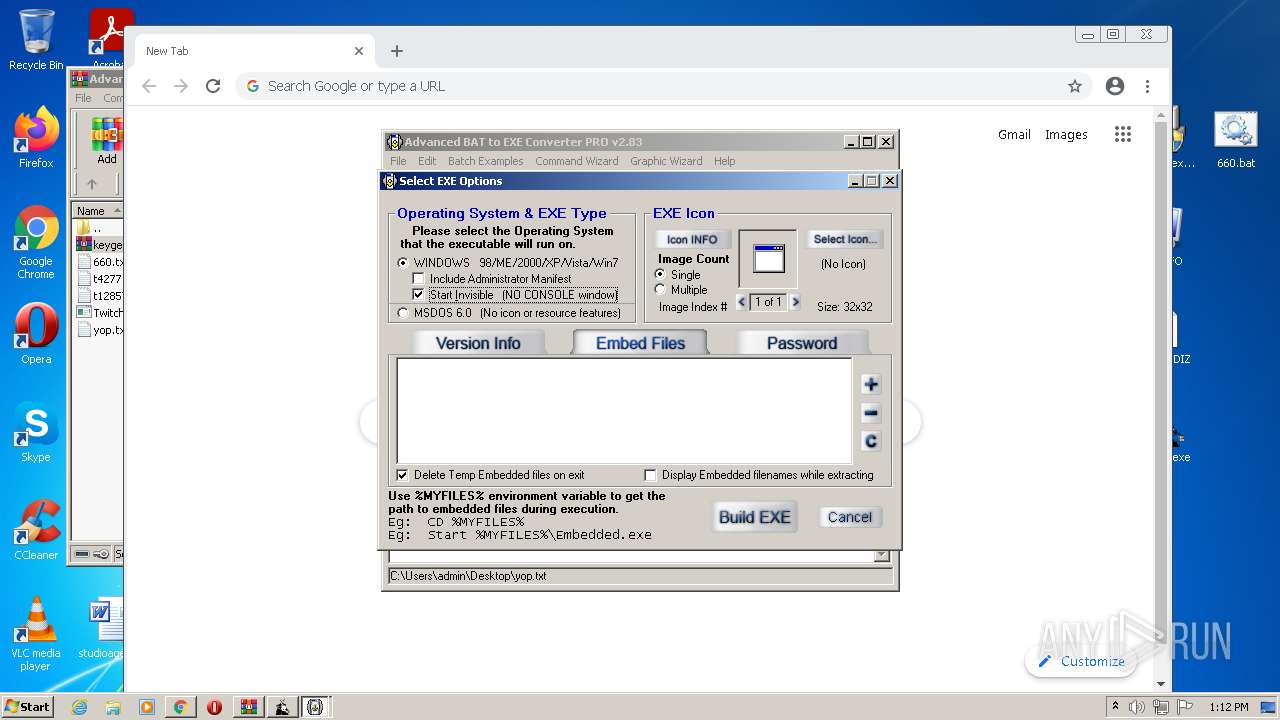
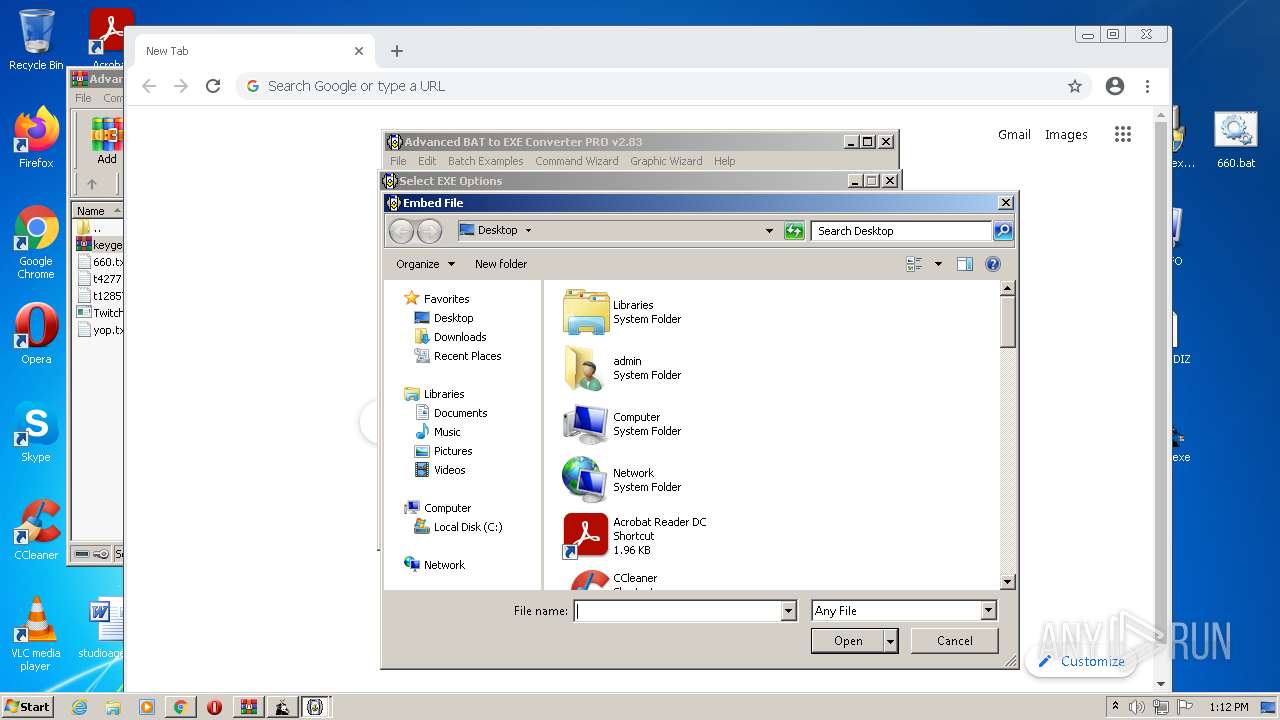
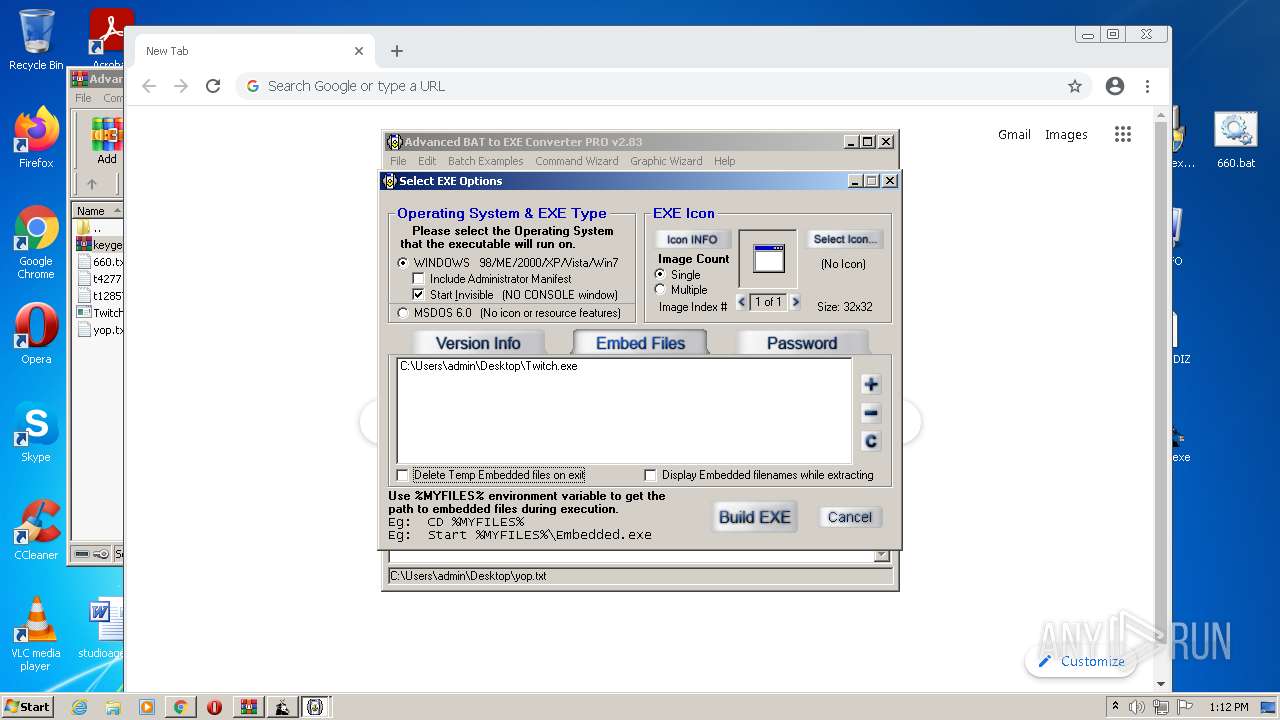
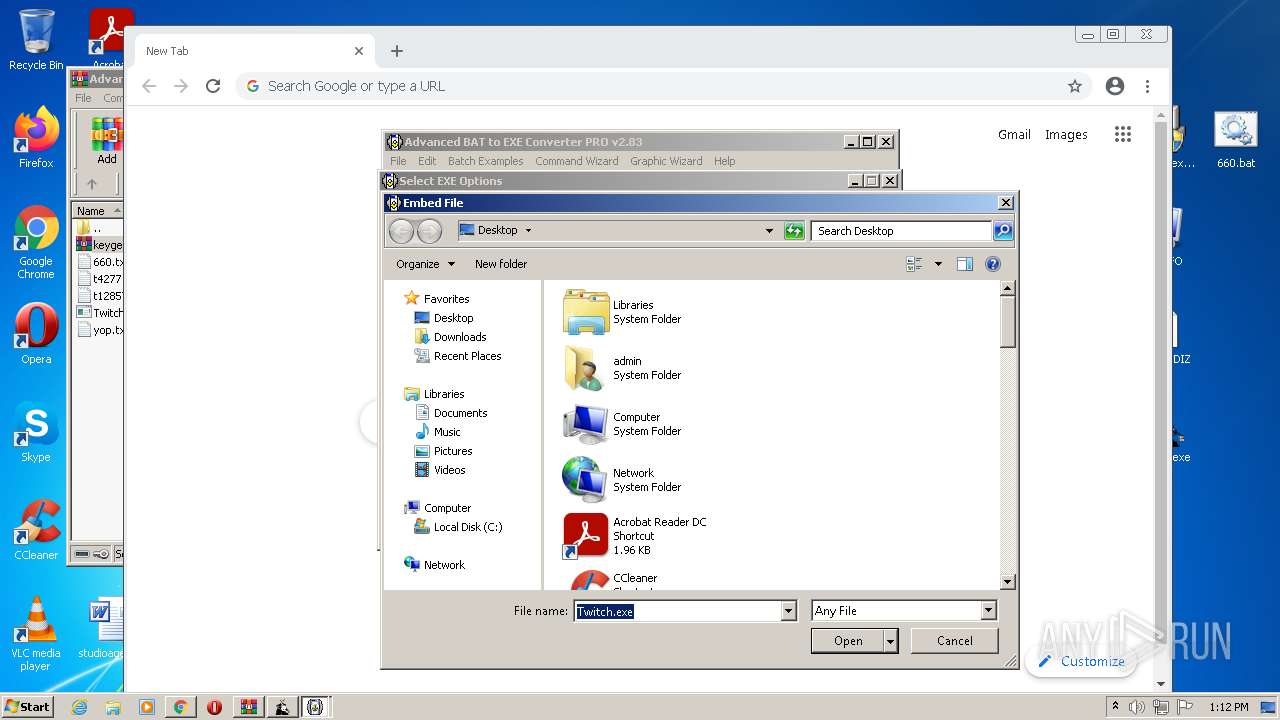
| File name: | Advanced BAT to EXE Converter PRO v2.83 _ Keygen.rar.zip |
| Full analysis: | https://app.any.run/tasks/6c34a3f8-e83b-45cb-943f-114ac354c9d4 |
| Verdict: | Malicious activity |
| Analysis date: | August 02, 2022, 12:10:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6E4EE3BBA46665452EFE7B8463695D54 |
| SHA1: | 05656764AC06CAEF7A3BBFE9BFBF19A7D66787CE |
| SHA256: | ADCC83251EFD9F82228E452F7325EA42B791BE9A4CA73572334B5BE2FB8078B9 |
| SSDEEP: | 24576:tjJSFn2OBu2FLwKNEUEOpSaWcAQl674mEH/ssvKa3:LSFfu2FEKCUtptWcAC6GHEu33 |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3120)
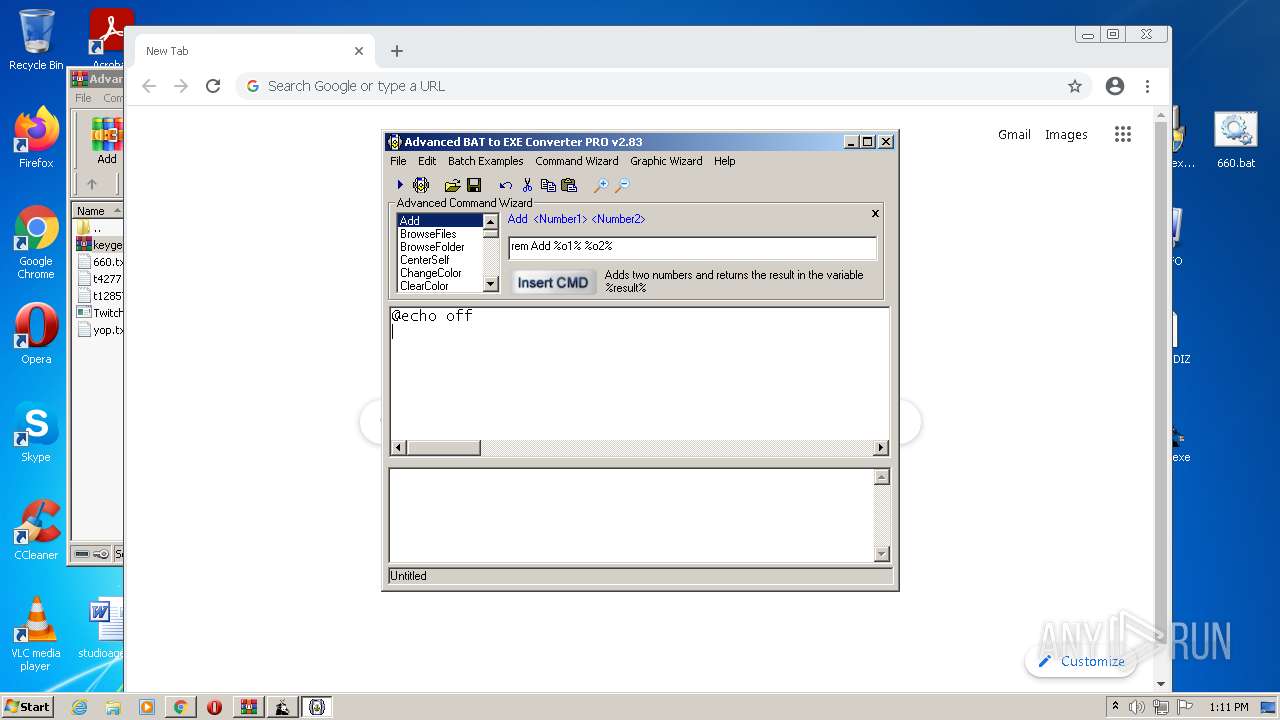
- advbattoexepro.exe (PID: 3408)
- WinRAR.exe (PID: 1816)
- ab2econv.exe (PID: 604)
- gfksopqm.exe (PID: 3540)
Application was dropped or rewritten from another process
- advbattoexepro.exe (PID: 1292)
- advbattoexepro.exe (PID: 3408)
- setupinf.exe (PID: 2212)
- Keygen.exe (PID: 2440)
- aB2Econv.exe (PID: 1804)
- activate.exe (PID: 1888)
- activate.exe (PID: 328)
- ab2econv.exe (PID: 604)
- gfksopqm.exe (PID: 3540)
- Twitch.exe (PID: 900)
- aB2Econv.exe (PID: 3160)
- aB2Econv.exe (PID: 2676)
Loads dropped or rewritten executable
- advbattoexepro.exe (PID: 3408)
- aB2Econv.exe (PID: 1804)
- ab2econv.exe (PID: 604)
- aB2Econv.exe (PID: 2676)
- aB2Econv.exe (PID: 3160)
Writes to a start menu file
- cmd.exe (PID: 2952)
Disables Windows System Restore
- reg.exe (PID: 2772)
Actions looks like stealing of personal data
- powershell.exe (PID: 1432)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3120)
- cmd.exe (PID: 3552)
- WScript.exe (PID: 3712)
Reads the computer name
- WinRAR.exe (PID: 3120)
- WinRAR.exe (PID: 1816)
- advbattoexepro.exe (PID: 3408)
- Keygen.exe (PID: 2440)
- aB2Econv.exe (PID: 1804)
- activate.exe (PID: 328)
- ab2econv.exe (PID: 604)
- gfksopqm.exe (PID: 3540)
- WScript.exe (PID: 2980)
- cmd.exe (PID: 2952)
- WScript.exe (PID: 2372)
- WScript.exe (PID: 3712)
- WMIC.exe (PID: 3316)
- WMIC.exe (PID: 3732)
- WMIC.exe (PID: 1040)
- WMIC.exe (PID: 476)
- powershell.exe (PID: 2108)
- powershell.exe (PID: 1432)
- Twitch.exe (PID: 900)
- WScript.exe (PID: 1432)
- powershell.exe (PID: 1796)
Checks supported languages
- WinRAR.exe (PID: 3120)
- WinRAR.exe (PID: 1816)
- advbattoexepro.exe (PID: 3408)
- Keygen.exe (PID: 2440)
- setupinf.exe (PID: 2212)
- aB2Econv.exe (PID: 1804)
- activate.exe (PID: 328)
- ab2econv.exe (PID: 604)
- gfksopqm.exe (PID: 3540)
- cmd.exe (PID: 2952)
- WScript.exe (PID: 2372)
- WScript.exe (PID: 2980)
- WScript.exe (PID: 3712)
- cmd.exe (PID: 3552)
- powershell.exe (PID: 1796)
- WMIC.exe (PID: 1040)
- WMIC.exe (PID: 3732)
- WMIC.exe (PID: 476)
- cmd.exe (PID: 2844)
- WMIC.exe (PID: 3316)
- powershell.exe (PID: 2108)
- powershell.exe (PID: 1432)
- Twitch.exe (PID: 900)
- aB2Econv.exe (PID: 3160)
- WScript.exe (PID: 1432)
- aB2Econv.exe (PID: 2676)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3120)
- WinRAR.exe (PID: 1816)
- advbattoexepro.exe (PID: 3408)
- ab2econv.exe (PID: 604)
- gfksopqm.exe (PID: 3540)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1816)
- advbattoexepro.exe (PID: 3408)
- WinRAR.exe (PID: 3120)
- ab2econv.exe (PID: 604)
- gfksopqm.exe (PID: 3540)
Creates files in the program directory
- advbattoexepro.exe (PID: 3408)
Creates a software uninstall entry
- advbattoexepro.exe (PID: 3408)
Creates a directory in Program Files
- advbattoexepro.exe (PID: 3408)
Changes default file association
- setupinf.exe (PID: 2212)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3992)
Reads default file associations for system extensions
- ab2econv.exe (PID: 604)
- chrome.exe (PID: 1180)
Reads Environment values
- netsh.exe (PID: 2416)
- powershell.exe (PID: 1432)
INFO
Manual execution by user
- advbattoexepro.exe (PID: 1292)
- advbattoexepro.exe (PID: 3408)
- Keygen.exe (PID: 2440)
- chrome.exe (PID: 3992)
- aB2Econv.exe (PID: 1804)
- gfksopqm.exe (PID: 3540)
- aB2Econv.exe (PID: 3160)
- aB2Econv.exe (PID: 2676)
Reads the computer name
- chrome.exe (PID: 3992)
- chrome.exe (PID: 1568)
- chrome.exe (PID: 2608)
- chrome.exe (PID: 3348)
- chrome.exe (PID: 128)
- chrome.exe (PID: 4036)
- chrome.exe (PID: 2396)
- chrome.exe (PID: 3840)
- chrome.exe (PID: 1180)
- takeown.exe (PID: 3296)
- takeown.exe (PID: 3876)
- takeown.exe (PID: 916)
- net1.exe (PID: 1620)
- systeminfo.exe (PID: 1876)
- ipconfig.exe (PID: 2672)
- netsh.exe (PID: 2416)
- NETSTAT.EXE (PID: 1816)
- chrome.exe (PID: 1888)
- chrome.exe (PID: 3664)
- chrome.exe (PID: 3996)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3084)
- chrome.exe (PID: 1776)
- chrome.exe (PID: 1724)
Checks supported languages
- chrome.exe (PID: 1984)
- chrome.exe (PID: 3992)
- chrome.exe (PID: 1568)
- chrome.exe (PID: 2608)
- chrome.exe (PID: 3528)
- chrome.exe (PID: 3716)
- chrome.exe (PID: 2876)
- chrome.exe (PID: 1228)
- chrome.exe (PID: 3348)
- chrome.exe (PID: 3876)
- chrome.exe (PID: 3624)
- chrome.exe (PID: 128)
- chrome.exe (PID: 3392)
- chrome.exe (PID: 4036)
- chrome.exe (PID: 3712)
- chrome.exe (PID: 3884)
- chrome.exe (PID: 2396)
- chrome.exe (PID: 3840)
- chrome.exe (PID: 128)
- chrome.exe (PID: 3456)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 2008)
- chrome.exe (PID: 1888)
- chrome.exe (PID: 3424)
- chrome.exe (PID: 3604)
- chrome.exe (PID: 3780)
- chrome.exe (PID: 1384)
- chrome.exe (PID: 1180)
- chrome.exe (PID: 2224)
- chrome.exe (PID: 3928)
- takeown.exe (PID: 3876)
- icacls.exe (PID: 1728)
- icacls.exe (PID: 2256)
- reg.exe (PID: 3744)
- reg.exe (PID: 2772)
- takeown.exe (PID: 916)
- takeown.exe (PID: 3296)
- icacls.exe (PID: 3352)
- net1.exe (PID: 1620)
- net.exe (PID: 1568)
- systeminfo.exe (PID: 1876)
- netsh.exe (PID: 2416)
- ipconfig.exe (PID: 2672)
- timeout.exe (PID: 3124)
- NETSTAT.EXE (PID: 1816)
- chrome.exe (PID: 1888)
- chrome.exe (PID: 1424)
- chrome.exe (PID: 3012)
- chrome.exe (PID: 564)
- chrome.exe (PID: 3664)
- chrome.exe (PID: 2096)
- chrome.exe (PID: 124)
- chrome.exe (PID: 3996)
- chrome.exe (PID: 2712)
- chrome.exe (PID: 3696)
- NOTEPAD.EXE (PID: 3208)
- chrome.exe (PID: 328)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3688)
- chrome.exe (PID: 2904)
- chrome.exe (PID: 748)
- chrome.exe (PID: 3188)
- chrome.exe (PID: 3084)
- chrome.exe (PID: 2736)
- chrome.exe (PID: 3716)
- chrome.exe (PID: 1776)
- chrome.exe (PID: 1312)
- chrome.exe (PID: 1724)
- chrome.exe (PID: 4032)
- chrome.exe (PID: 2096)
- chrome.exe (PID: 2280)
- chrome.exe (PID: 2924)
- chrome.exe (PID: 3560)
Application launched itself
- chrome.exe (PID: 3992)
- chrome.exe (PID: 1888)
- chrome.exe (PID: 3664)
- chrome.exe (PID: 3996)
- chrome.exe (PID: 3860)
- chrome.exe (PID: 3084)
- chrome.exe (PID: 1776)
- chrome.exe (PID: 1724)
Reads settings of System Certificates
- chrome.exe (PID: 2608)
- powershell.exe (PID: 2108)
- WScript.exe (PID: 1432)
Changes default file association
- chrome.exe (PID: 3992)
Reads the date of Windows installation
- chrome.exe (PID: 4036)
Checks Windows Trust Settings
- WScript.exe (PID: 2372)
- WScript.exe (PID: 2980)
- WScript.exe (PID: 3712)
- powershell.exe (PID: 1796)
- powershell.exe (PID: 2108)
- powershell.exe (PID: 1432)
- WScript.exe (PID: 1432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | keygen.rar |
|---|---|
| ZipUncompressedSize: | 906111 |
| ZipCompressedSize: | 906111 |
| ZipCRC: | 0xfc2dc038 |
| ZipModifyDate: | 2021:06:28 19:08:06 |
| ZipCompression: | None |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 788 |
Total processes
162
Monitored processes
101
Malicious processes
15
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,13188767992603912341,8381363107355207865,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2936 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1036,13188767992603912341,8381363107355207865,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3328 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1036,13188767992603912341,8381363107355207865,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1848 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
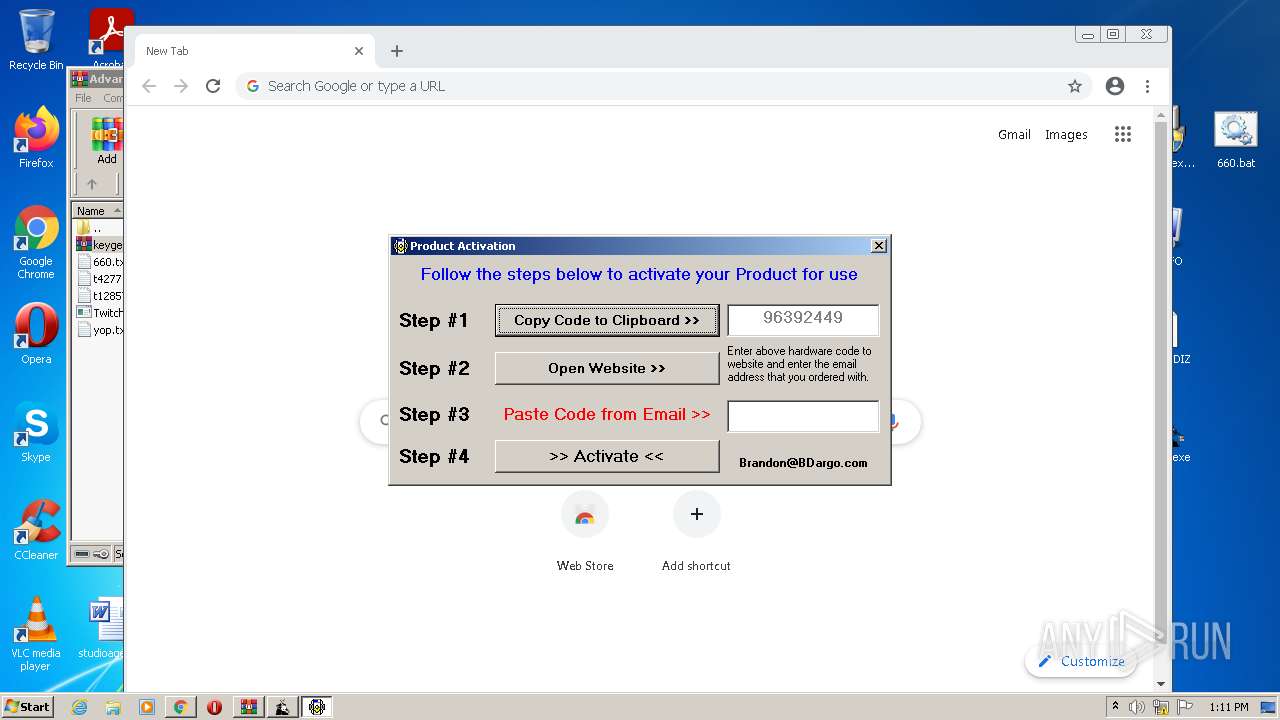
| 328 | "C:\Program Files\Advanced BAT to EXE Converter PRO v2.83\ab2econv283pro\activate.exe" | C:\Program Files\Advanced BAT to EXE Converter PRO v2.83\ab2econv283pro\activate.exe | aB2Econv.exe | ||||||||||||
User: admin Company: Brandon Dargo Integrity Level: HIGH Description: BDargo Software Activation Exit code: 0 Version: 1.01.0002 Modules
| |||||||||||||||
| 328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,13188767992603912341,8381363107355207865,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=34 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3220 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 476 | wmic csproduct get uuid | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,13188767992603912341,8381363107355207865,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2100 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
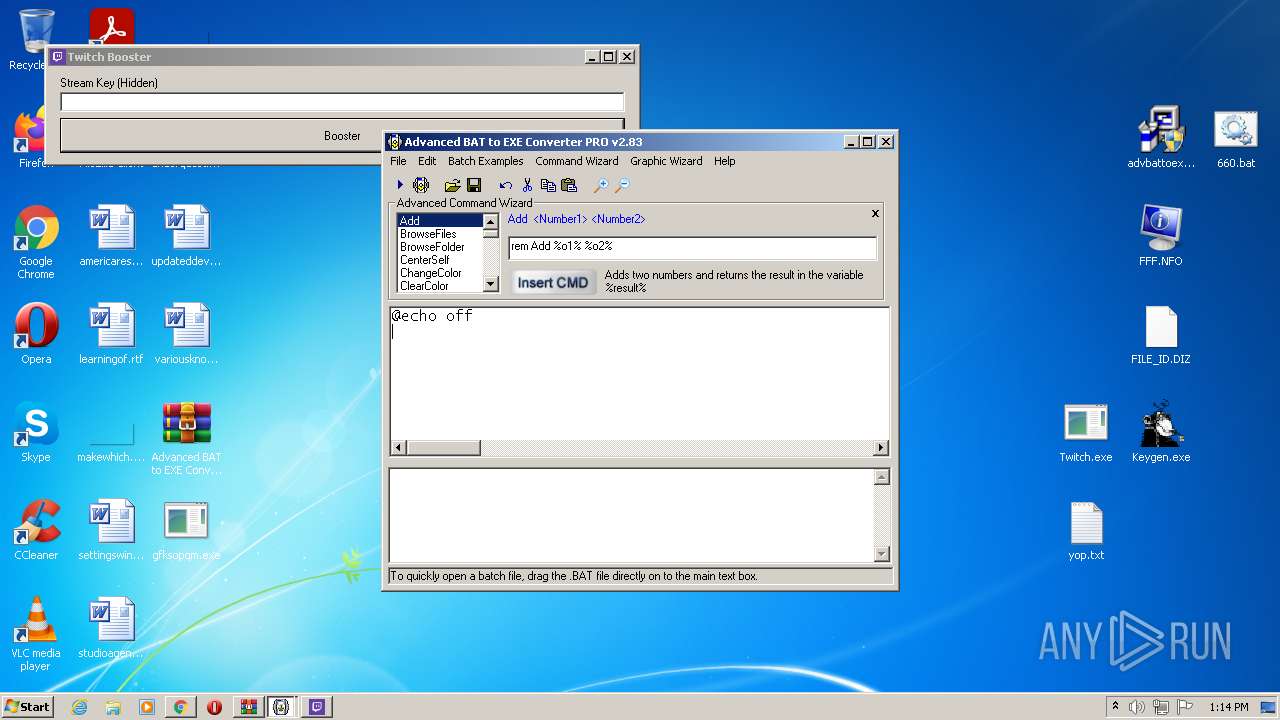
| 604 | "C:\Program Files\Advanced BAT to EXE Converter PRO v2.83\ab2econv283pro\ab2econv.exe" | C:\Program Files\Advanced BAT to EXE Converter PRO v2.83\ab2econv283pro\ab2econv.exe | activate.exe | ||||||||||||
User: admin Company: Brandon Dargo Integrity Level: HIGH Description: Advanced BAT to EXE Converter PRO Exit code: 0 Version: 2.08.0003 Modules
| |||||||||||||||
| 748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,13188767992603912341,8381363107355207865,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3784 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
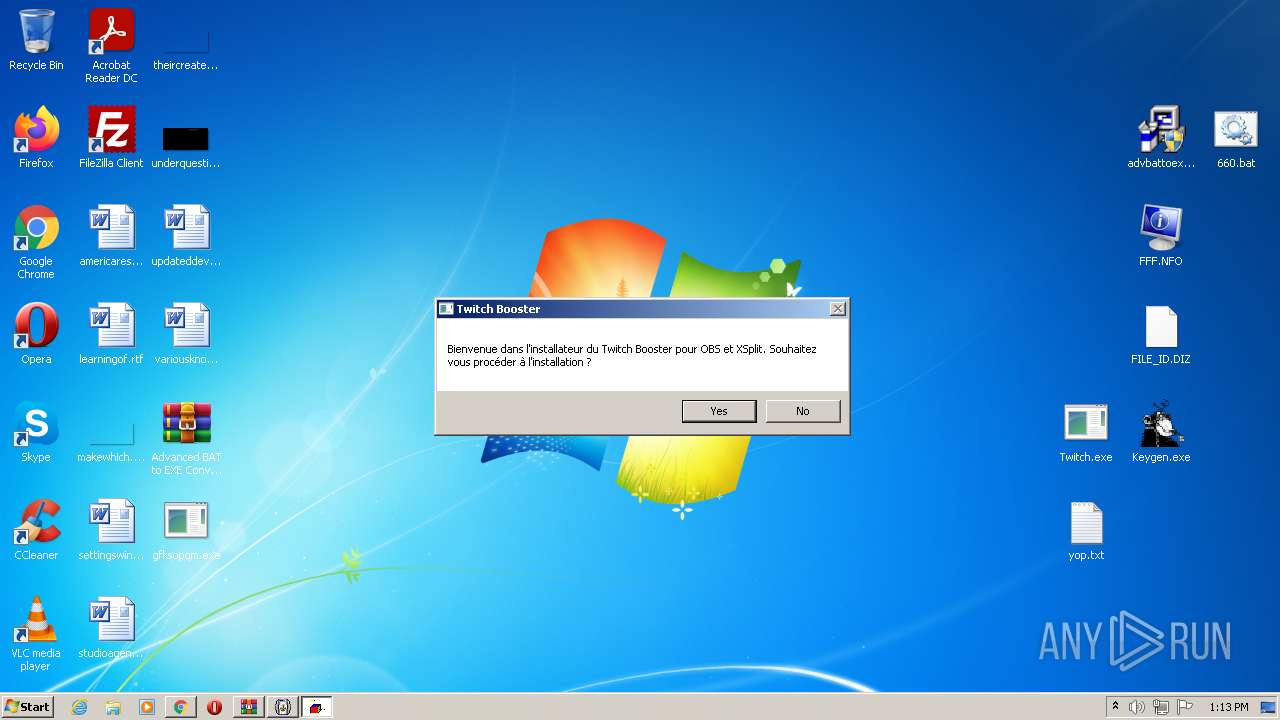
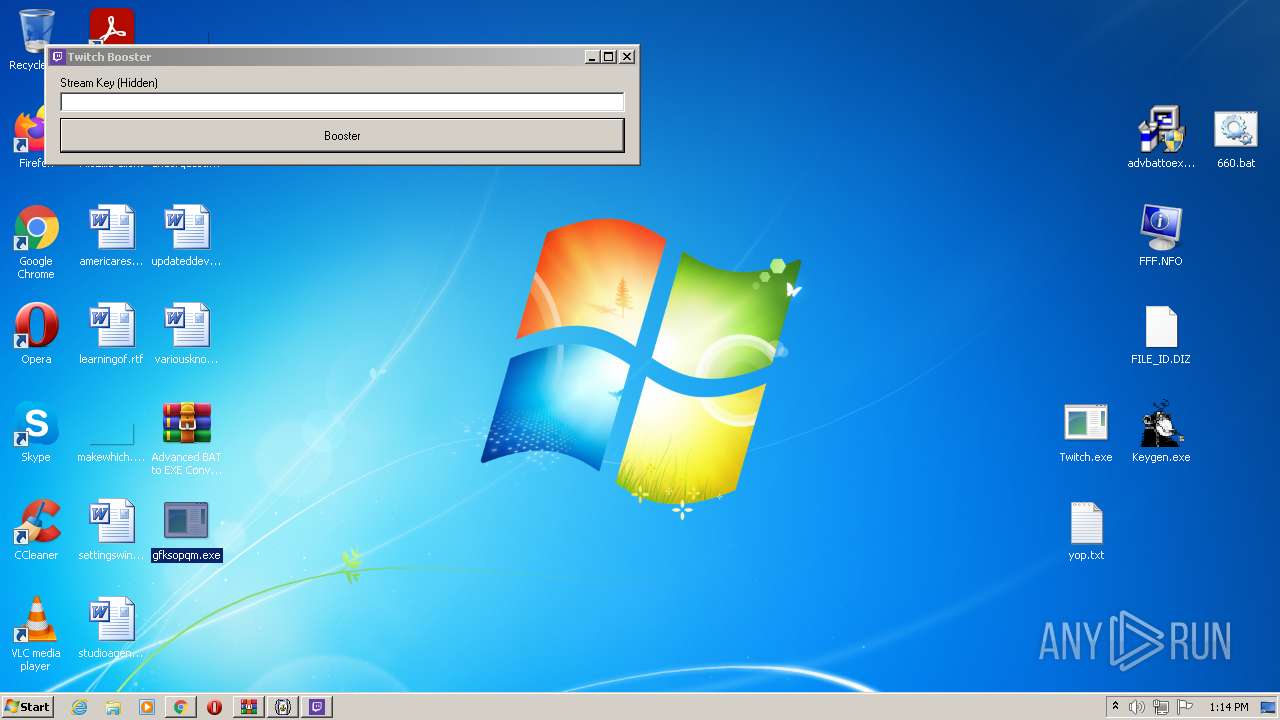
| 900 | "C:\Users\admin\AppData\Local\Temp\afolder\Twitch.exe" | C:\Users\admin\AppData\Local\Temp\afolder\Twitch.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: WindowsFormsApplication2 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
40 334
Read events
39 428
Write events
876
Delete events
30
Modification events
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Advanced BAT to EXE Converter PRO v2.83 _ Keygen.rar.zip | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
27
Suspicious files
191
Text files
265
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1816.39649\Advanced.BAT.to.EXE.Converter.PRO.v2.83.RETAIL.INCL_KEYGEN-FFF\Keygen.exe | executable | |
MD5:— | SHA256:— | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3120.38463\660.txt | text | |
MD5:— | SHA256:— | |||
| 3120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3120.38149\yop.txt | text | |
MD5:— | SHA256:— | |||
| 1816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1816.39649\Advanced.BAT.to.EXE.Converter.PRO.v2.83.RETAIL.INCL_KEYGEN-FFF\FILE_ID.DIZ | text | |
MD5:— | SHA256:— | |||
| 1816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1816.39649\Advanced.BAT.to.EXE.Converter.PRO.v2.83.RETAIL.INCL_KEYGEN-FFF\FFF.NFO | text | |
MD5:— | SHA256:— | |||
| 3408 | advbattoexepro.exe | C:\Users\admin\AppData\Local\Temp\gentee00\setup_temp.gea | bs | |
MD5:— | SHA256:— | |||
| 1816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1816.39649\Advanced.BAT.to.EXE.Converter.PRO.v2.83.RETAIL.INCL_KEYGEN-FFF\advbattoexepro.exe | executable | |
MD5:— | SHA256:— | |||
| 3408 | advbattoexepro.exe | C:\Program Files\Advanced BAT to EXE Converter PRO v2.83\ab2econv283pro\aB2Econv.exe | executable | |
MD5:— | SHA256:— | |||
| 3408 | advbattoexepro.exe | C:\Users\admin\AppData\Local\Temp\gentee00\1Default.bmp | image | |
MD5:0895D223FA59A94BED73D25D1CB5AF70 | SHA256:53228A7C924889D300C7FFE9BAA1879EE94BD9B4286E84B7B29F870E9567B82D | |||
| 3408 | advbattoexepro.exe | C:\Users\admin\AppData\Local\Temp\gentee00\gentee.dll | executable | |
MD5:30439E079A3D603C461D2C2F4F8CB064 | SHA256:D6D0535175FB2302E5B5A498119823C37F6BDDFF4AB24F551AA7E038C343077A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
74
TCP/UDP connections
73
DNS requests
40
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
— | — | HEAD | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/d73azlwdjoju4dawoukxfjz6bu_2022.7.25.1141/ggkkehgbnfjpeggfpleeakpidbkibbmn_2022.7.25.1141_all_ebemybvzva3g6qooytqjclbctq.crx3 | US | — | — | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 10.0 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 21.7 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 2.51 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 45.0 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 10.0 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 10.0 Kb | whitelisted |
2608 | chrome.exe | GET | 200 | 72.21.81.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d5bb93339391f740 | US | compressed | 60.2 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 39.9 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2608 | chrome.exe | 142.250.184.196:443 | www.google.com | Google Inc. | US | whitelisted |
2608 | chrome.exe | 142.250.185.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
2608 | chrome.exe | 142.250.185.109:443 | accounts.google.com | Google Inc. | US | suspicious |
2608 | chrome.exe | 142.250.186.33:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2608 | chrome.exe | 142.250.184.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2608 | chrome.exe | 216.58.212.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
— | — | 142.250.185.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
— | — | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
2608 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
2608 | chrome.exe | 142.250.184.238:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
1432 | powershell.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
1432 | WScript.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
1432 | WScript.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |