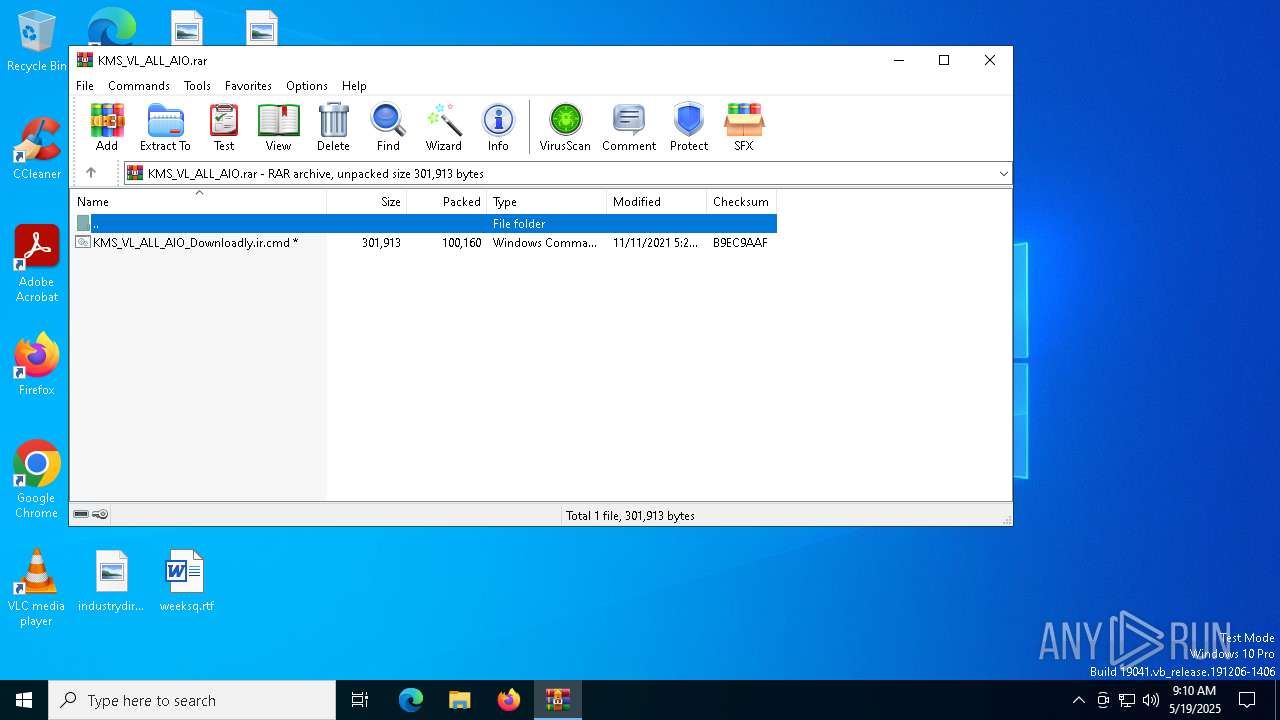
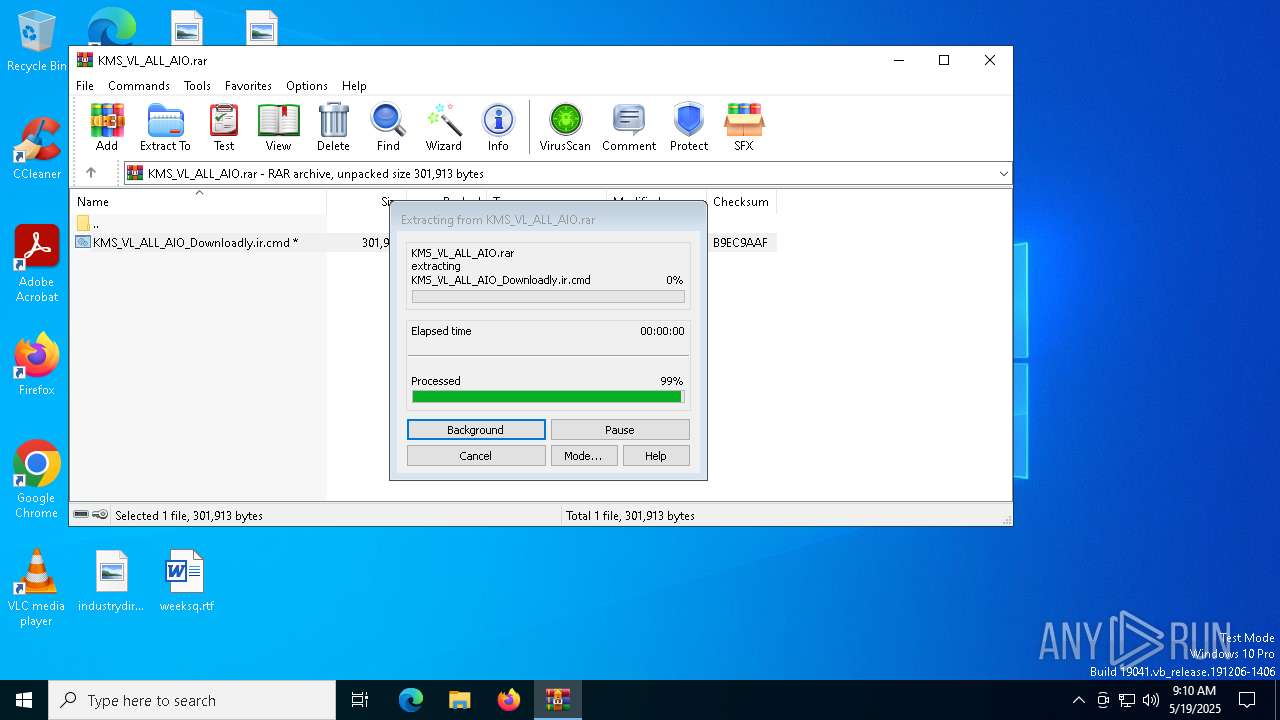
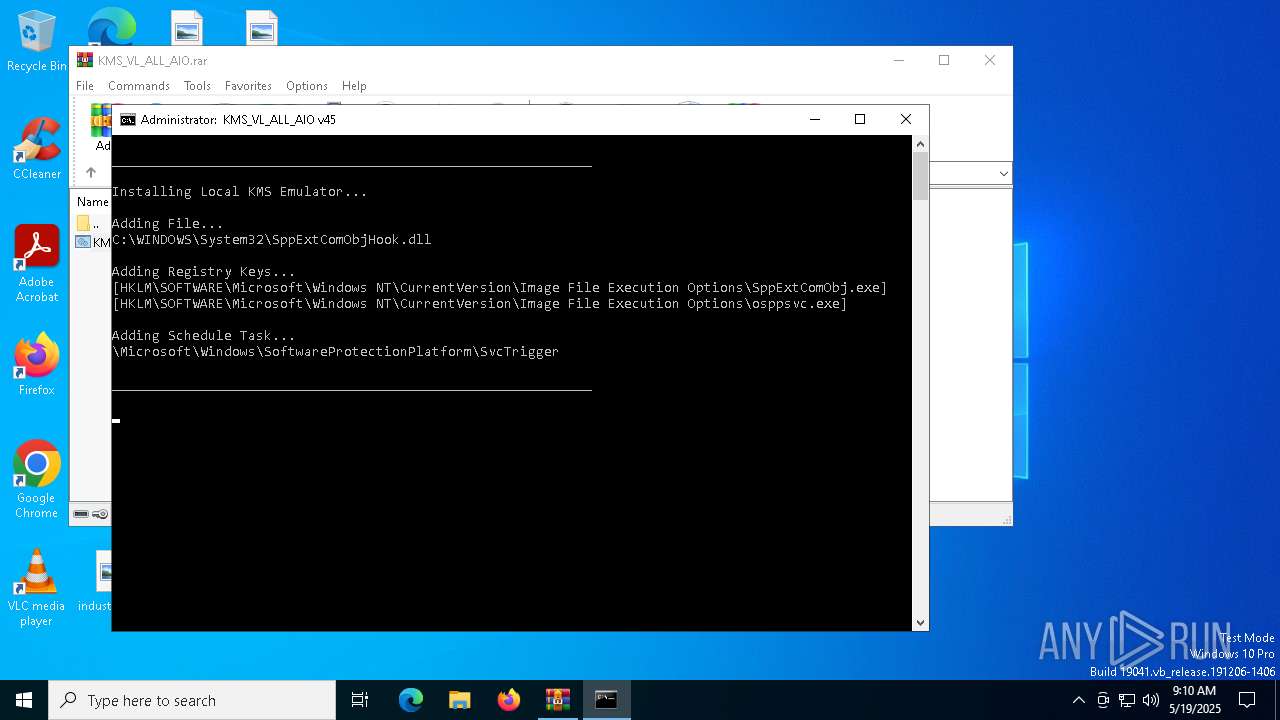
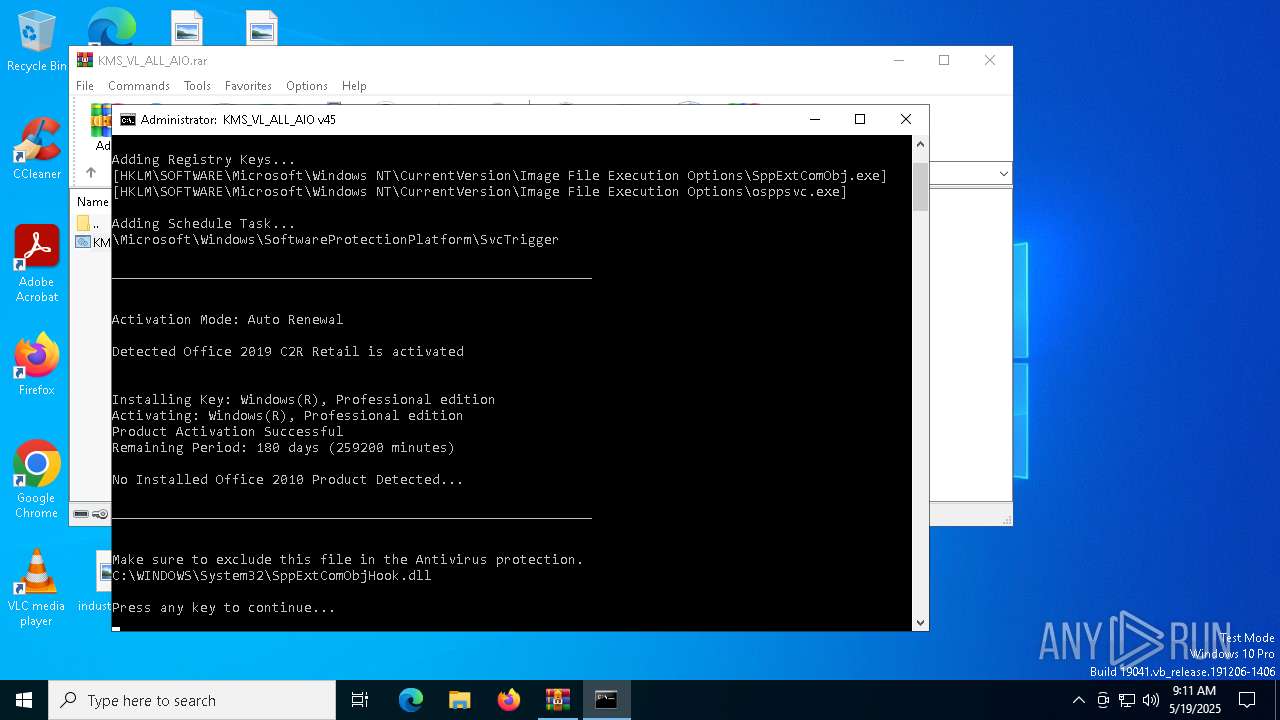
| File name: | KMS_VL_ALL_AIO.rar |
| Full analysis: | https://app.any.run/tasks/dc6b34d3-4e76-46c0-a4ca-802303b46903 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 09:10:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1C8C6BB4BEA2BD7B6E0866B0C6F8EF8D |
| SHA1: | 63D25485DD5027AA7DBC7D8B9C9EFE9C10804CF8 |
| SHA256: | ADC6C82808FC1EAFA4C0FBFFDBED9CF5F30A851513924567FFEA2CF6215C8D9A |
| SSDEEP: | 3072:+5rOexzSuNmDF5vpj12SD+Bzr/gxJu2/n:CtFPIF5BjnezrgxJu2f |
MALICIOUS
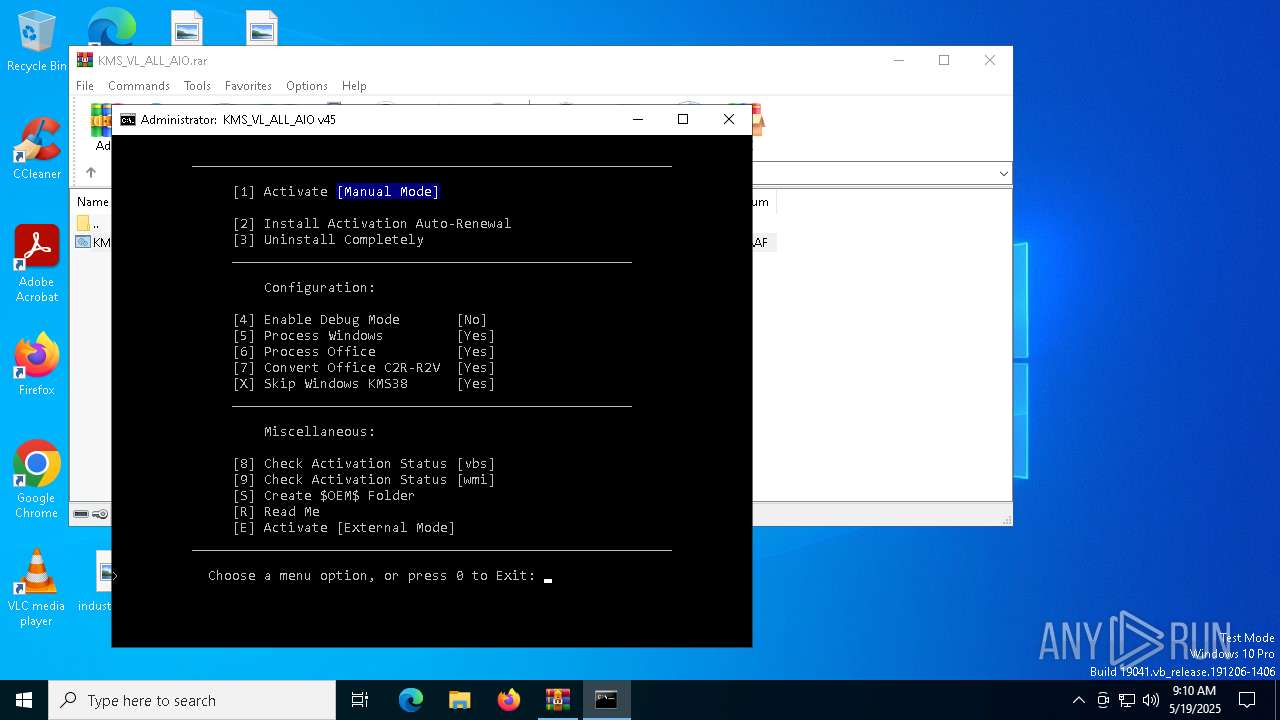
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 8076)
Starts NET.EXE for service management
- cmd.exe (PID: 8076)
- net.exe (PID: 7512)
- net.exe (PID: 7520)
- net.exe (PID: 8144)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 8076)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6028)
- cscript.exe (PID: 7904)
- cmd.exe (PID: 8076)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6028)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 6028)
- cscript.exe (PID: 7904)
Uses RUNDLL32.EXE to load library
- cscript.exe (PID: 7904)
Runs shell command (SCRIPT)
- cscript.exe (PID: 7904)
Windows service management via SC.EXE
- sc.exe (PID: 2148)
- sc.exe (PID: 7628)
- sc.exe (PID: 5304)
- sc.exe (PID: 1660)
- sc.exe (PID: 6112)
- sc.exe (PID: 6816)
- sc.exe (PID: 6136)
- sc.exe (PID: 5156)
- sc.exe (PID: 8188)
- sc.exe (PID: 5408)
Application launched itself
- cmd.exe (PID: 8076)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8076)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 8076)
Executes script without checking the security policy
- powershell.exe (PID: 1180)
- powershell.exe (PID: 7644)
- powershell.exe (PID: 8184)
Starts SC.EXE for service management
- cmd.exe (PID: 8076)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 8076)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 8076)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 7644)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 7644)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7644)
CSC.EXE is used to compile C# code
- csc.exe (PID: 4892)
Executable content was dropped or overwritten
- powershell.exe (PID: 7644)
- csc.exe (PID: 4892)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8076)
Modifies existing scheduled task
- schtasks.exe (PID: 7824)
Lists all scheduled tasks
- schtasks.exe (PID: 7912)
- schtasks.exe (PID: 7908)
- schtasks.exe (PID: 7852)
- schtasks.exe (PID: 7224)
- schtasks.exe (PID: 8156)
Hides command output
- cmd.exe (PID: 5256)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 7684)
- cmd.exe (PID: 7728)
- cmd.exe (PID: 7524)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 5136)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 7764)
- cmd.exe (PID: 7528)
- cmd.exe (PID: 7724)
- cmd.exe (PID: 1568)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 7796)
- cmd.exe (PID: 7812)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 7732)
- cmd.exe (PID: 5960)
- cmd.exe (PID: 6512)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 8076)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 7524)
- cmd.exe (PID: 6468)
- cmd.exe (PID: 7284)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8076)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7940)
- cmd.exe (PID: 8076)
- cmd.exe (PID: 5436)
The process executes VB scripts
- cmd.exe (PID: 8076)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 3396)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3396)
INFO
Reads security settings of Internet Explorer
- cscript.exe (PID: 7904)
- WMIC.exe (PID: 7520)
- WMIC.exe (PID: 7676)
- WMIC.exe (PID: 7632)
- WMIC.exe (PID: 7696)
- WMIC.exe (PID: 8164)
- WMIC.exe (PID: 7572)
- WMIC.exe (PID: 8044)
- WMIC.exe (PID: 5548)
- WMIC.exe (PID: 2552)
- WMIC.exe (PID: 5400)
- WMIC.exe (PID: 7408)
- WMIC.exe (PID: 5544)
- WMIC.exe (PID: 1240)
- WMIC.exe (PID: 7864)
- WMIC.exe (PID: 4692)
- WMIC.exe (PID: 6960)
Checks operating system version
- cmd.exe (PID: 8076)
Starts MODE.COM to configure console settings
- mode.com (PID: 1188)
- mode.com (PID: 5376)
- mode.com (PID: 5528)
Checks supported languages
- mode.com (PID: 1188)
- mode.com (PID: 5376)
- csc.exe (PID: 4892)
- cvtres.exe (PID: 7752)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7644)
Reads the machine GUID from the registry
- csc.exe (PID: 4892)
Create files in a temporary directory
- cvtres.exe (PID: 7752)
- csc.exe (PID: 4892)
Reads Microsoft Office registry keys
- reg.exe (PID: 6156)
- reg.exe (PID: 7156)
- reg.exe (PID: 7416)
- reg.exe (PID: 3884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 100160 |
| UncompressedSize: | 301913 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | KMS_VL_ALL_AIO_Downloadly.ir.cmd |
Total processes
607
Monitored processes
472
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | findstr /I /C:"Outlook2019Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | REG QUERY "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages" /f "Microsoft-Windows-*Edition~31bf3856ad364e35" /k | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | findstr /I /C:"HomeStudent2021Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | findstr /I /C:"VisioStdVolume" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | findstr /I /C:"AccessRetail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe" /f /v VerifierDlls /t REG_SZ /d "SppExtComObjHook.dll" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | reg query HKLM\SOFTWARE\Microsoft\Office\ClickToRun /v InstallPath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | findstr /I /C:"ProfessionalRetail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | wmic path SoftwareLicensingProduct where (ID='e0c42288-980c-4788-a014-c080d2e1926e') get LicenseStatus /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | findstr /I /C:"Word2021Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 712
Read events
27 672
Write events
40
Delete events
0
Modification events
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMS_VL_ALL_AIO.rar | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6028) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (632) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | VerifierDlls |
Value: SppExtComObjHook.dll | |||
Executable files
2
Suspicious files
3
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb6028.12857\KMS_VL_ALL_AIO_Downloadly.ir.cmd | text | |
MD5:B3B521A815CB5C8B7CFACEBE41D20DE2 | SHA256:207C742365C044CA5B27F3977EFC324927C51539A09DB2EB1A632375B737458A | |||
| 4892 | csc.exe | C:\Users\admin\AppData\Local\Temp\4cs2ky2n\CSCBC84369245A04055B6DF6B78B27FD32.TMP | binary | |
MD5:8E645D63D2082487B1B5C7D42946C9E7 | SHA256:796075E52C7F97D943786EB835016E3347237A02F6C737EF02D2679E60249D1E | |||
| 1180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gnbc0eoj.1xe.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8184 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pph2wjy1.mba.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1180 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bvtoa3zr.qy3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4cs2ky2n\4cs2ky2n.0.cs | text | |
MD5:EAFBB318108FC62A15B458EBBA405940 | SHA256:45EE3DD57AA47FCF92C09A44276DE5EF1688BB0563E09206D8E882528E6DE9D2 | |||
| 7644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qyqys1q2.tlh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7752 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES2BB0.tmp | binary | |
MD5:180820230AA8612237C4560A73CD8454 | SHA256:54E27104B3B7EA2AE59E4545443C7EFA5A68A015F2C218EAAE2F3F9325B43B3B | |||
| 4892 | csc.exe | C:\Users\admin\AppData\Local\Temp\4cs2ky2n\4cs2ky2n.out | text | |
MD5:B13ECA55BFCBE331A43A8E1FCC55C6F5 | SHA256:B262BC4C3AC61A3D250442C583277AA2EEC203CBCD7F8B06D87747002E3E0430 | |||
| 7644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4cs2ky2n\4cs2ky2n.cmdline | text | |
MD5:736B710B676788DB8F9BF83D3DE0062F | SHA256:20BB069BB6F90C8C7316224C9263EDA0AB765FA485737EAA7231D5D2AB25E9FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7688 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7688 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5512 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |