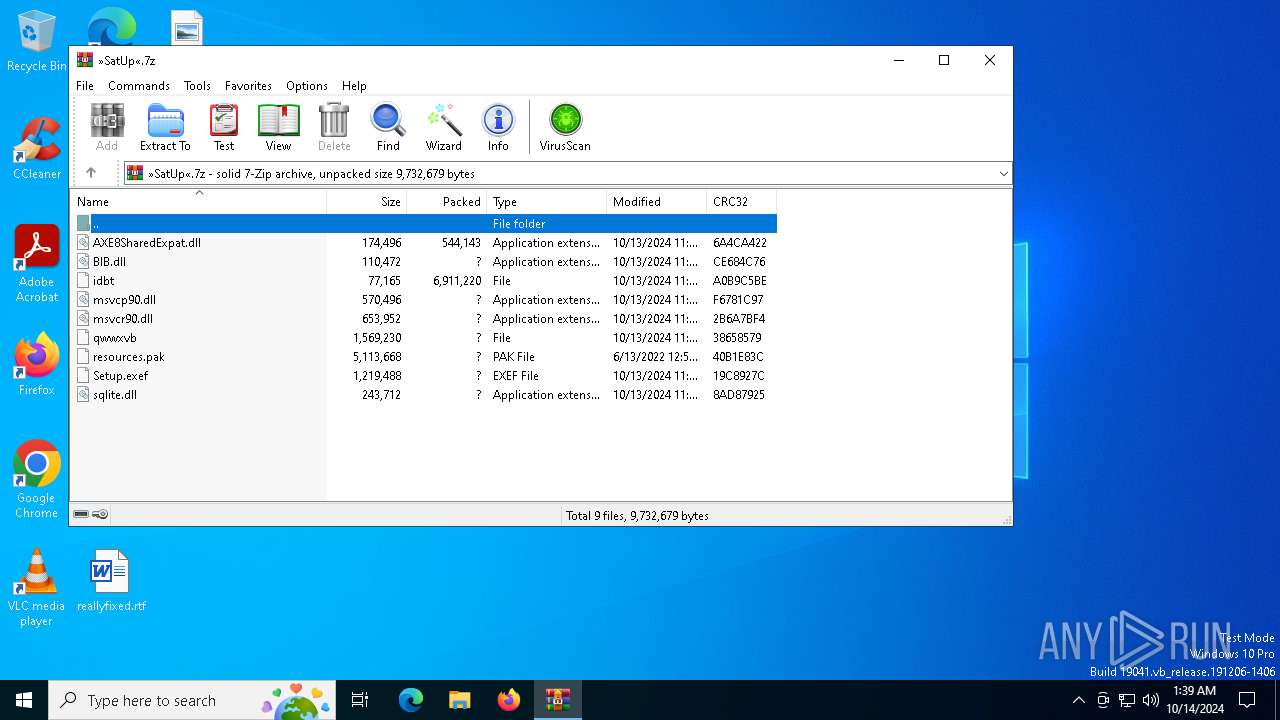
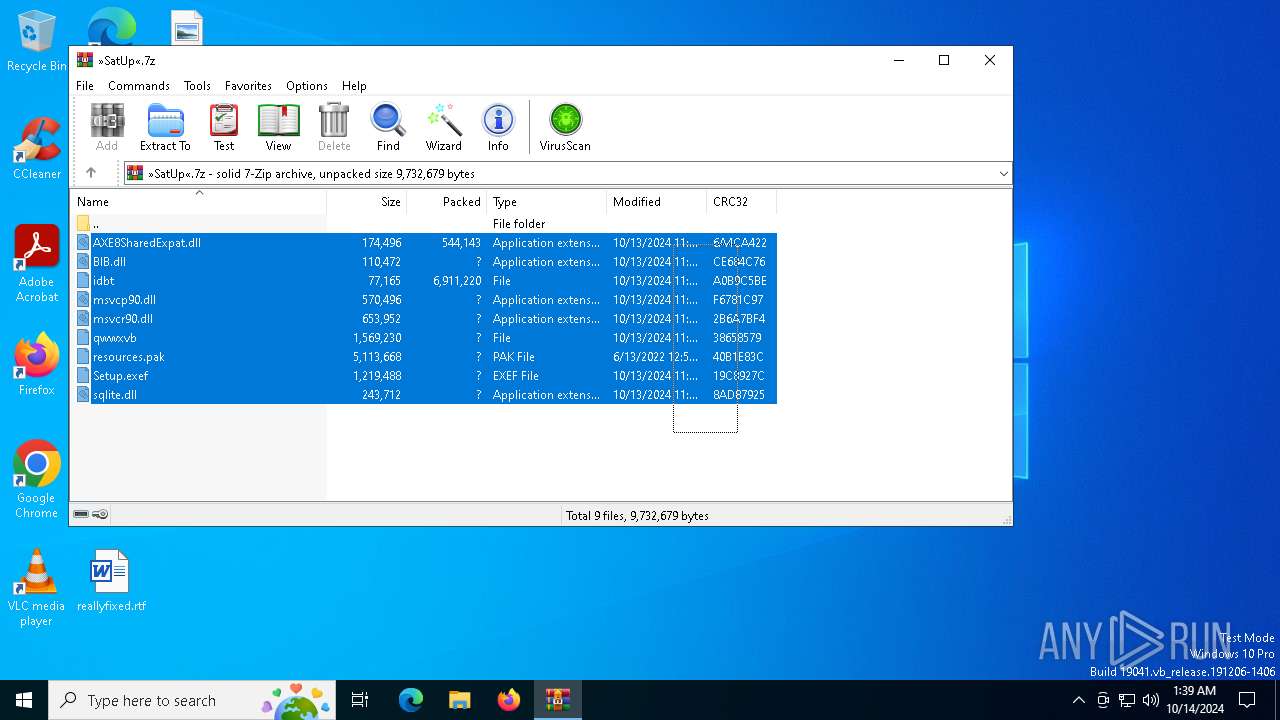
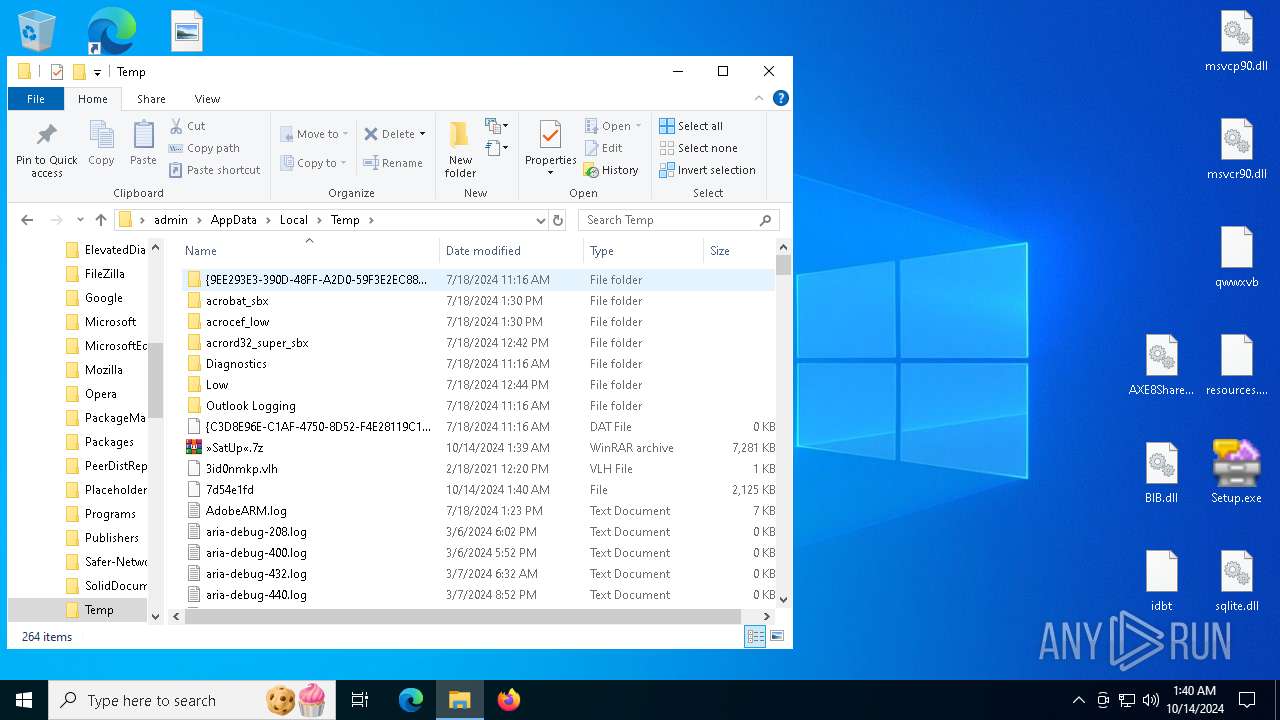
| File name: | »SatUp«.7z |
| Full analysis: | https://app.any.run/tasks/cfd3f764-c0d9-4825-8177-e564a6ae5712 |
| Verdict: | Malicious activity |
| Analysis date: | October 14, 2024, 01:39:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C3E08B6B4D4AA734554170B7E5E57420 |
| SHA1: | 1C3B74BE54467C79C5A1535B0C422EB3580CF353 |
| SHA256: | ADAD3B0E40258A64CB658464A0AADC908FE76CCF98E47AEA9F0895E161C25B2F |
| SSDEEP: | 98304:cZJCDPw2huUuH4MYaz2BZ6fUARx6weh654h1uXJJ3deDXpzJNNgfKH4rDCjvzSAH:cW6qhrS0Mgzfj |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6552)
Changes powershell execution policy (Bypass)
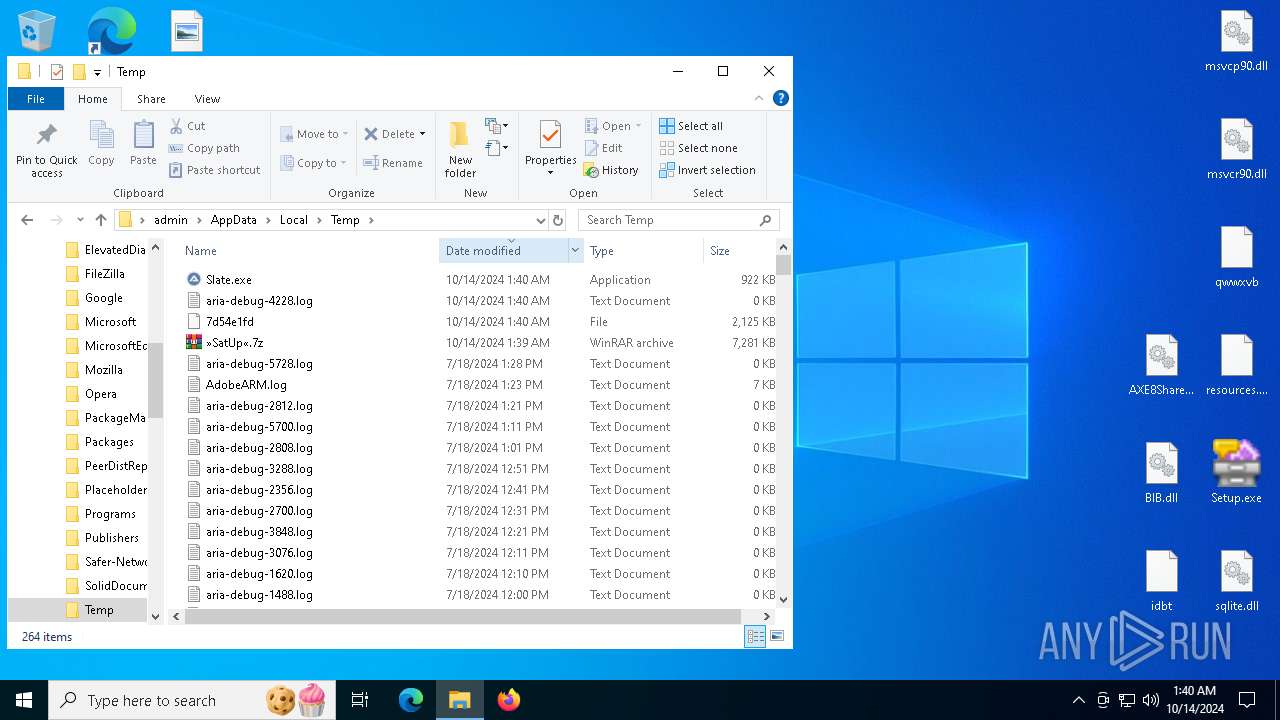
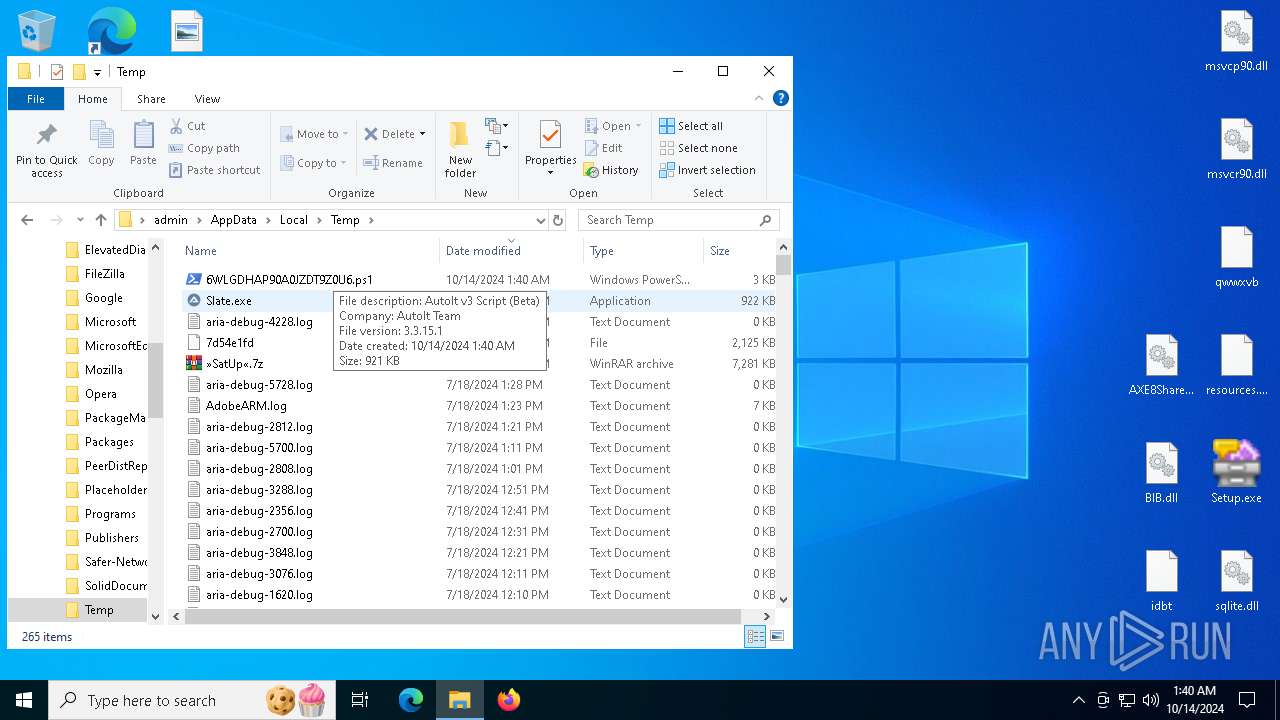
- Slate.exe (PID: 6880)
SUSPICIOUS
Process drops legitimate windows executable
- Setup.exe (PID: 2272)
- WinRAR.exe (PID: 3276)
The process drops C-runtime libraries
- WinRAR.exe (PID: 3276)
- Setup.exe (PID: 2272)
Executable content was dropped or overwritten
- Setup.exe (PID: 2272)
- more.com (PID: 5932)
Starts application with an unusual extension
- Setup.exe (PID: 2272)
The process executes Powershell scripts
- Slate.exe (PID: 6880)
Starts POWERSHELL.EXE for commands execution
- Slate.exe (PID: 6880)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 3276)
Creates files or folders in the user directory
- Setup.exe (PID: 2272)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3276)
Manual execution by a user
- Setup.exe (PID: 2272)
Checks supported languages
- Setup.exe (PID: 2272)
- StrCmp.exe (PID: 3604)
Reads the computer name
- Setup.exe (PID: 2272)
- StrCmp.exe (PID: 3604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
147
Monitored processes
12
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1700 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2272 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Collaboration Synchronizer 10.0 Exit code: 1 Version: 10.0.1.434 Modules
| |||||||||||||||
| 3276 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\»SatUp«.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3604 | C:\Users\admin\AppData\Roaming\TIQ\FEEDWZAUFCHAUJKPWEPZRAO\StrCmp.exe | C:\Users\admin\AppData\Roaming\TIQ\FEEDWZAUFCHAUJKPWEPZRAO\StrCmp.exe | — | Setup.exe | |||||||||||
User: admin Company: aaa Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3852 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3960 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4316 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5932 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6228 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6312 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 836
Read events
10 819
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\»SatUp«.7z | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
13
Suspicious files
6
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3276.29195\resources.pak | — | |
MD5:— | SHA256:— | |||
| 5932 | more.com | C:\Users\admin\AppData\Local\Temp\qdcxx | — | |
MD5:— | SHA256:— | |||
| 3276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3276.29195\BIB.dll | executable | |
MD5:759D71FC9442AB5A9B5749C0F6C0C263 | SHA256:109647F58E7E8386A4C025F2C8175A4D638E5C0E62768953390764010EA22A2E | |||
| 3276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3276.29195\idbt | binary | |
MD5:CA7696BA867DF0EF181CE2399C0B91CD | SHA256:0281BF37D42D810B7DAAC8ADF8BFA28C6EC1C22A7C8A233C79AEE8D94511D43A | |||
| 3276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3276.29195\msvcp90.dll | executable | |
MD5:90A32D8E07F7FB3D102EAB1DA28F0723 | SHA256:004ED24507DC7307CEC1A3732FA57EABF19E918C3E1B54561E6CC01F554C0B77 | |||
| 2272 | Setup.exe | C:\Users\admin\AppData\Roaming\TIQ\qwwxvb | binary | |
MD5:C78A05E723173C1A7D3B7BBC98F5F9D8 | SHA256:8A04378F86958AAC65002ECCBF45C5F58B168E3E75AD67694337E273DE297351 | |||
| 2272 | Setup.exe | C:\Users\admin\AppData\Roaming\TIQ\BIB.dll | executable | |
MD5:759D71FC9442AB5A9B5749C0F6C0C263 | SHA256:109647F58E7E8386A4C025F2C8175A4D638E5C0E62768953390764010EA22A2E | |||
| 2272 | Setup.exe | C:\Users\admin\AppData\Roaming\TIQ\AXE8SharedExpat.dll | executable | |
MD5:0CFB90C28768E26498834D780FBBD754 | SHA256:5B3434727CD6805870550C4912E23543D3F9B58A19D32C412B8978D1515E1229 | |||
| 2272 | Setup.exe | C:\Users\admin\AppData\Roaming\TIQ\msvcp90.dll | executable | |
MD5:90A32D8E07F7FB3D102EAB1DA28F0723 | SHA256:004ED24507DC7307CEC1A3732FA57EABF19E918C3E1B54561E6CC01F554C0B77 | |||
| 2272 | Setup.exe | C:\Users\admin\AppData\Roaming\TIQ\sqlite.dll | executable | |
MD5:F638120367926F0F8F7B59C49037056D | SHA256:04EA2DCEA08C524ECDAF663BFBD12AC29B6F929831DB7DCE4AF8CE3FDB06A56C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
68
DNS requests
29
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4896 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4896 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
540 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4292 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4360 | SearchApp.exe | 23.212.110.144:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6880 | Slate.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
2172 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |