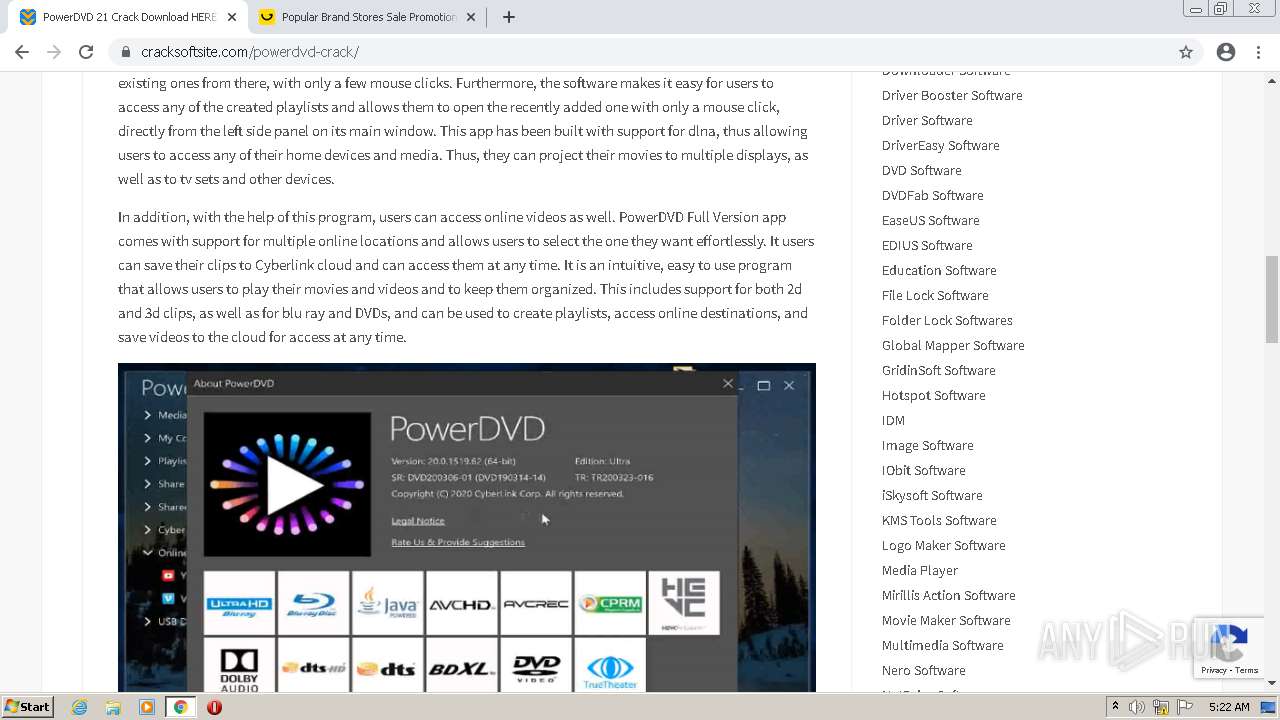
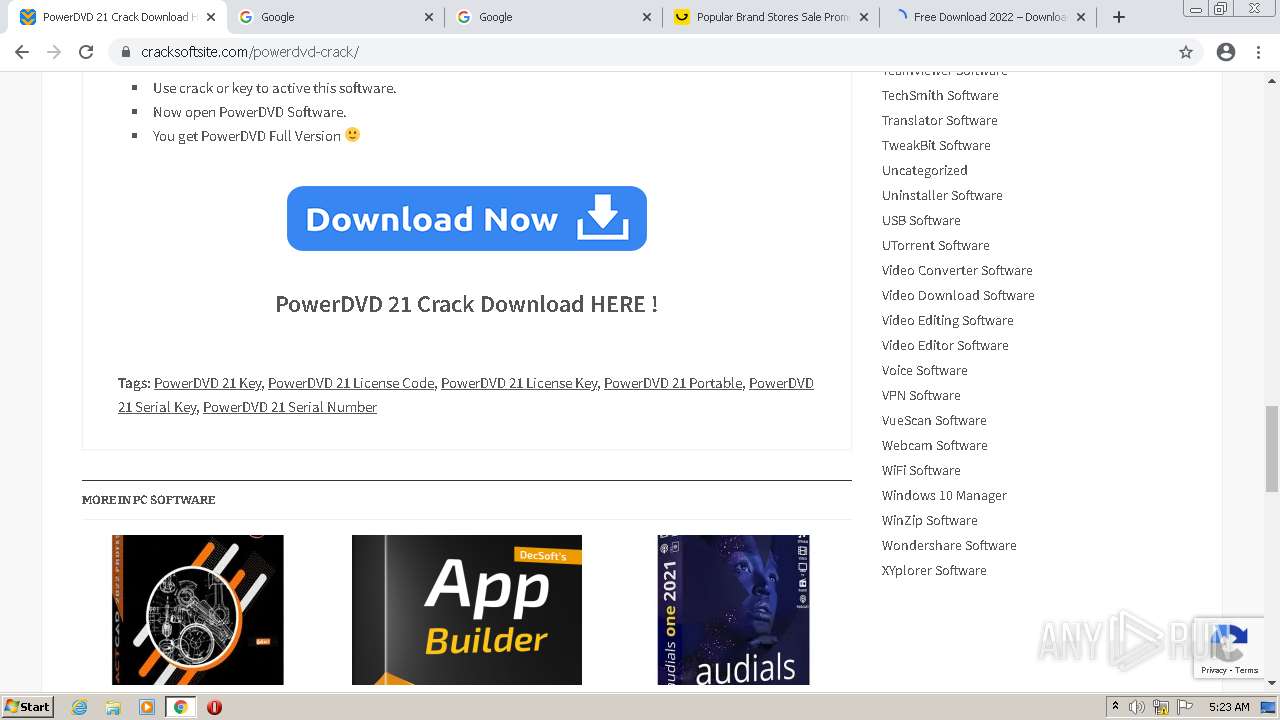
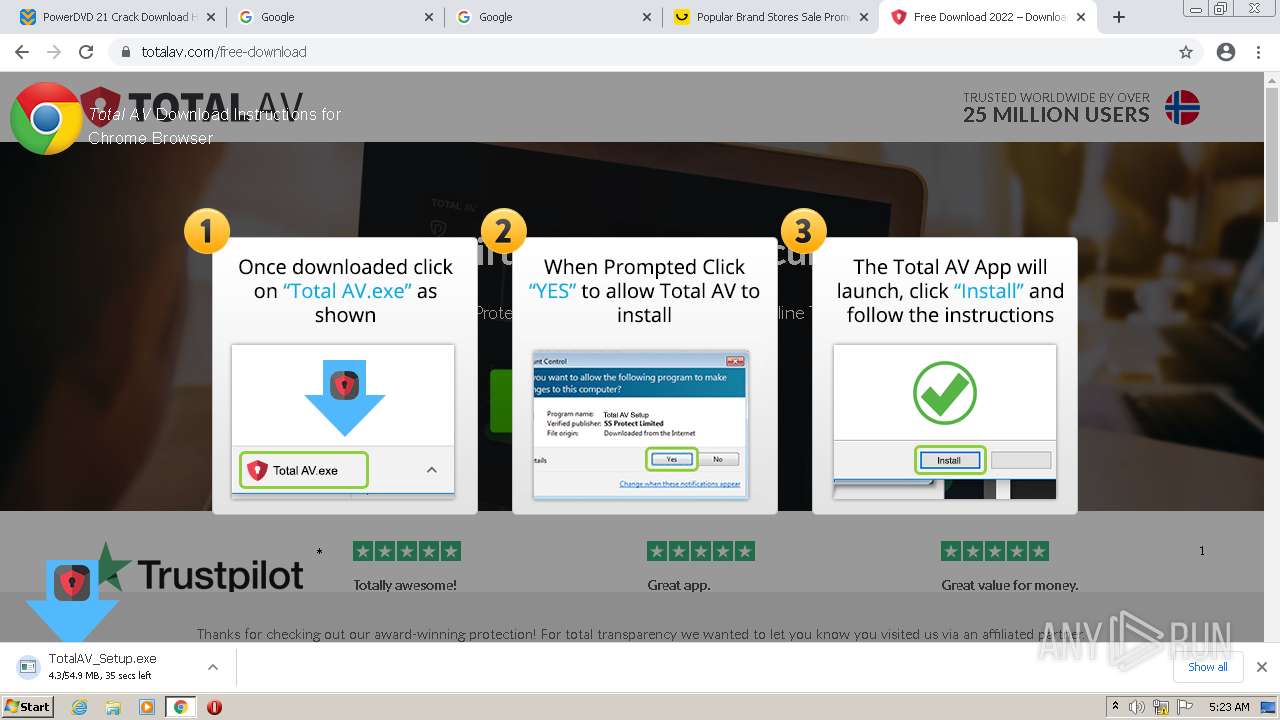
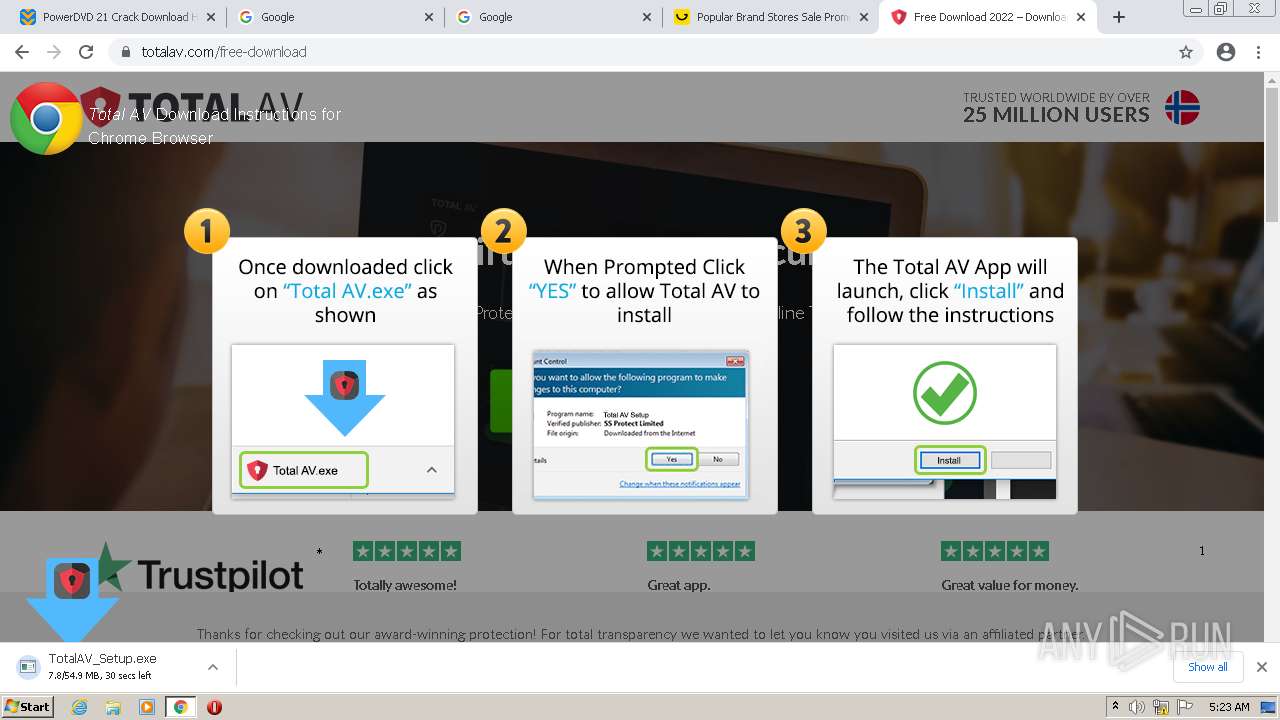
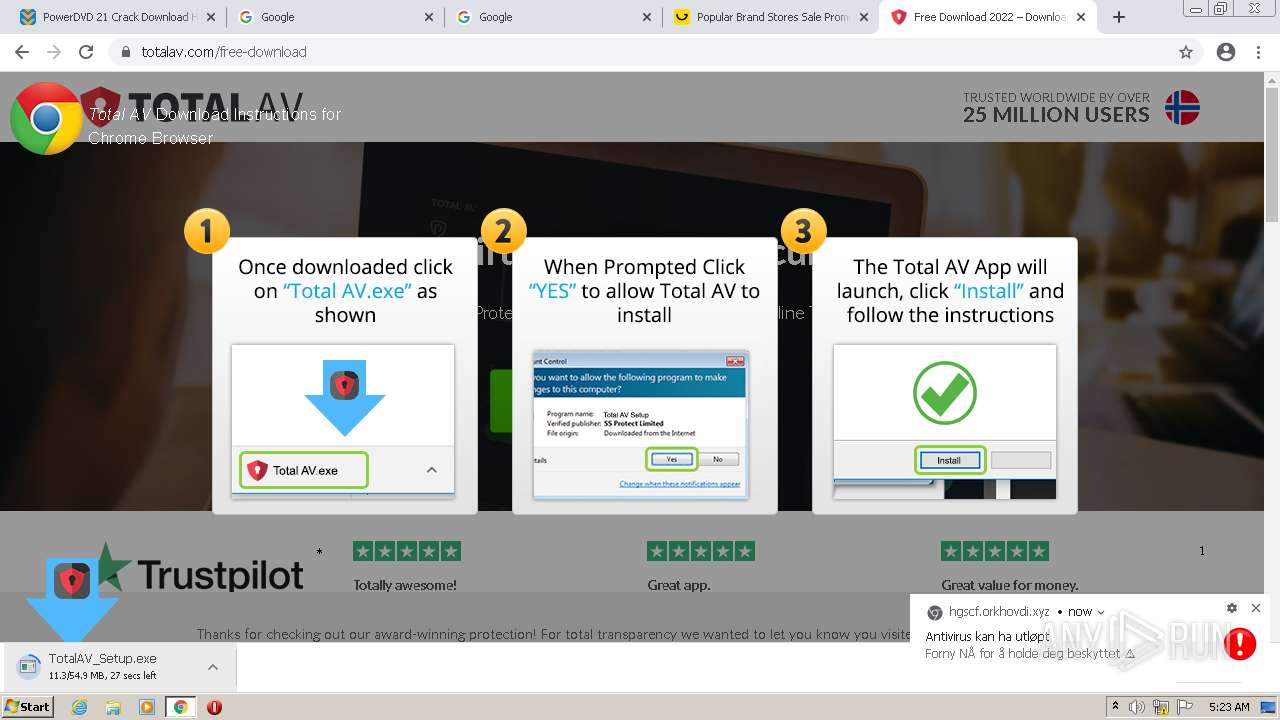
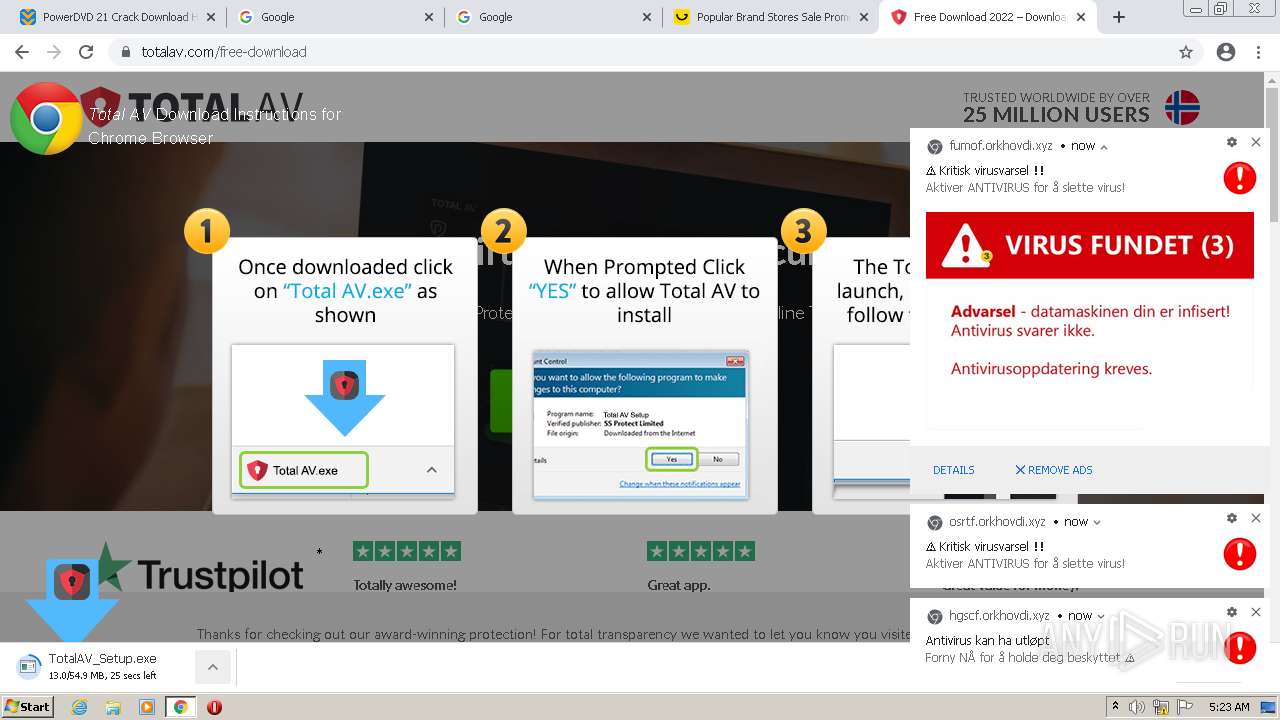
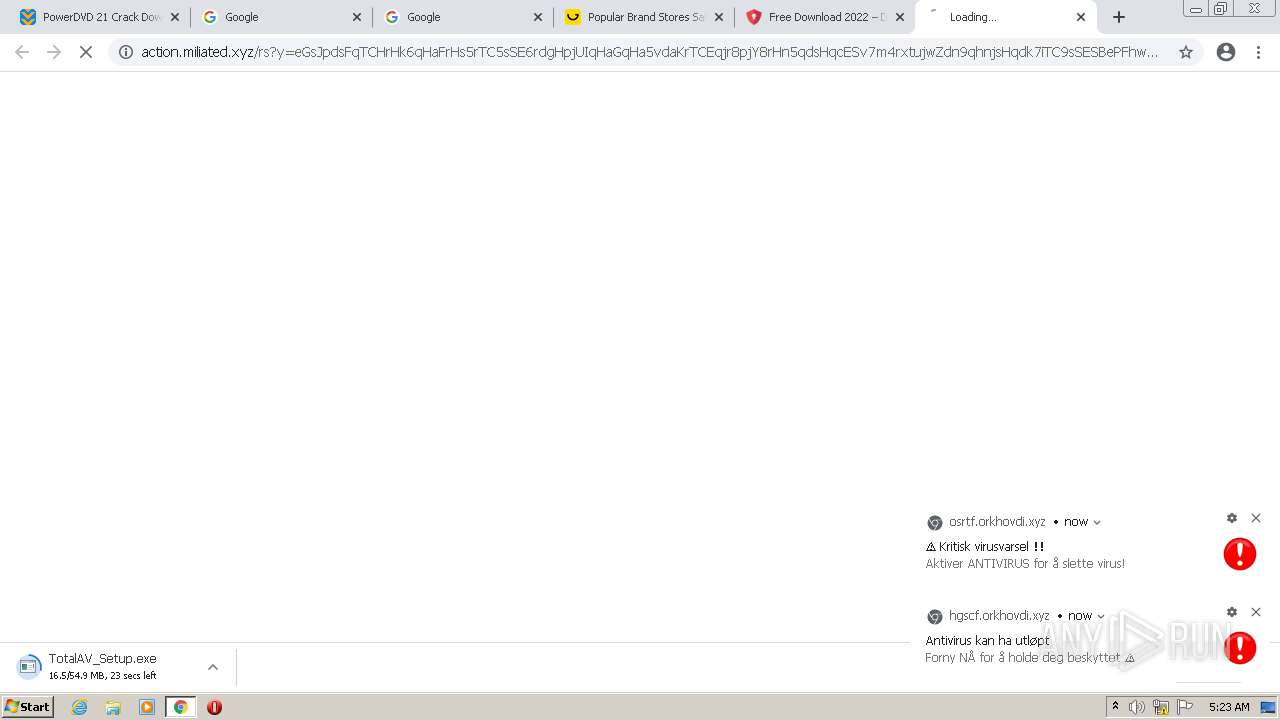
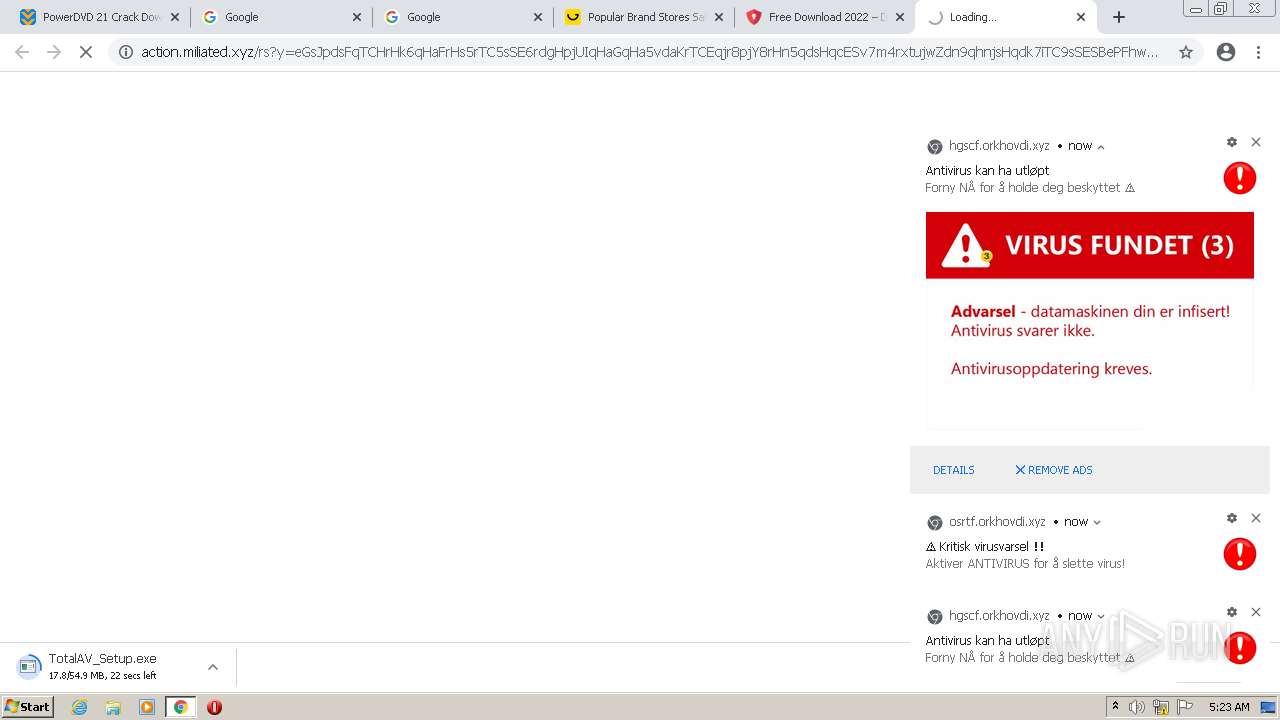
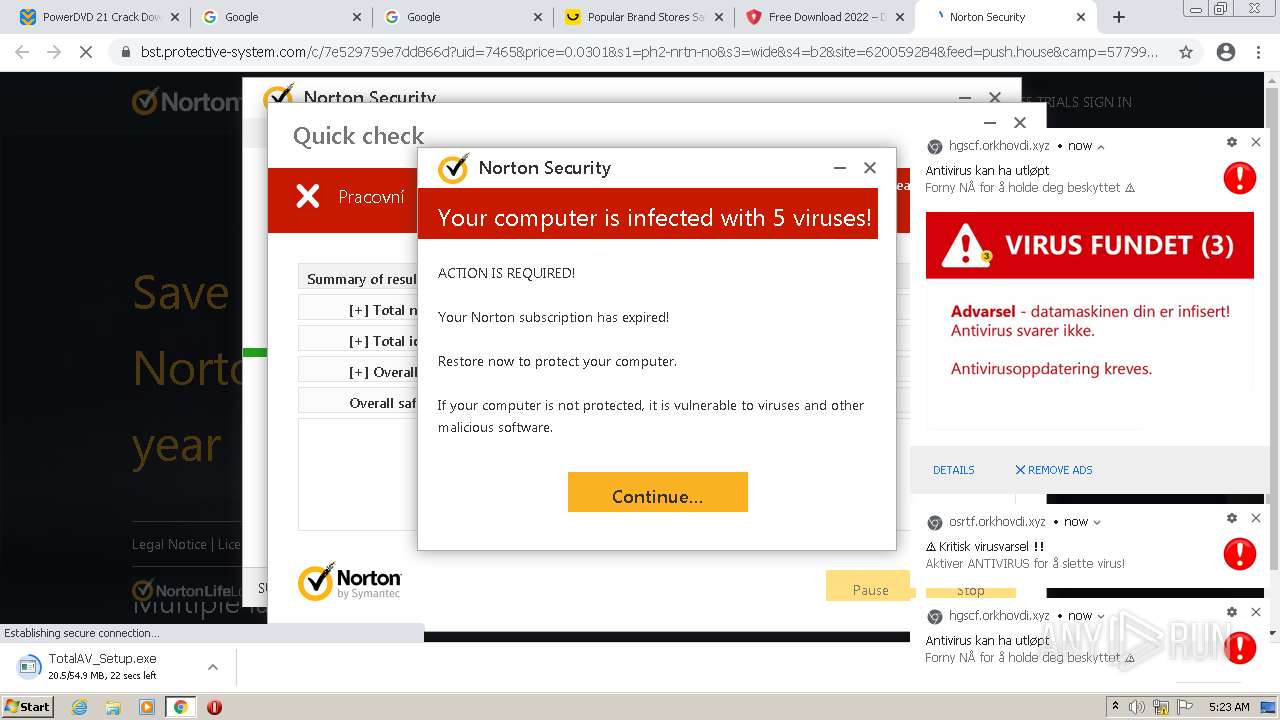
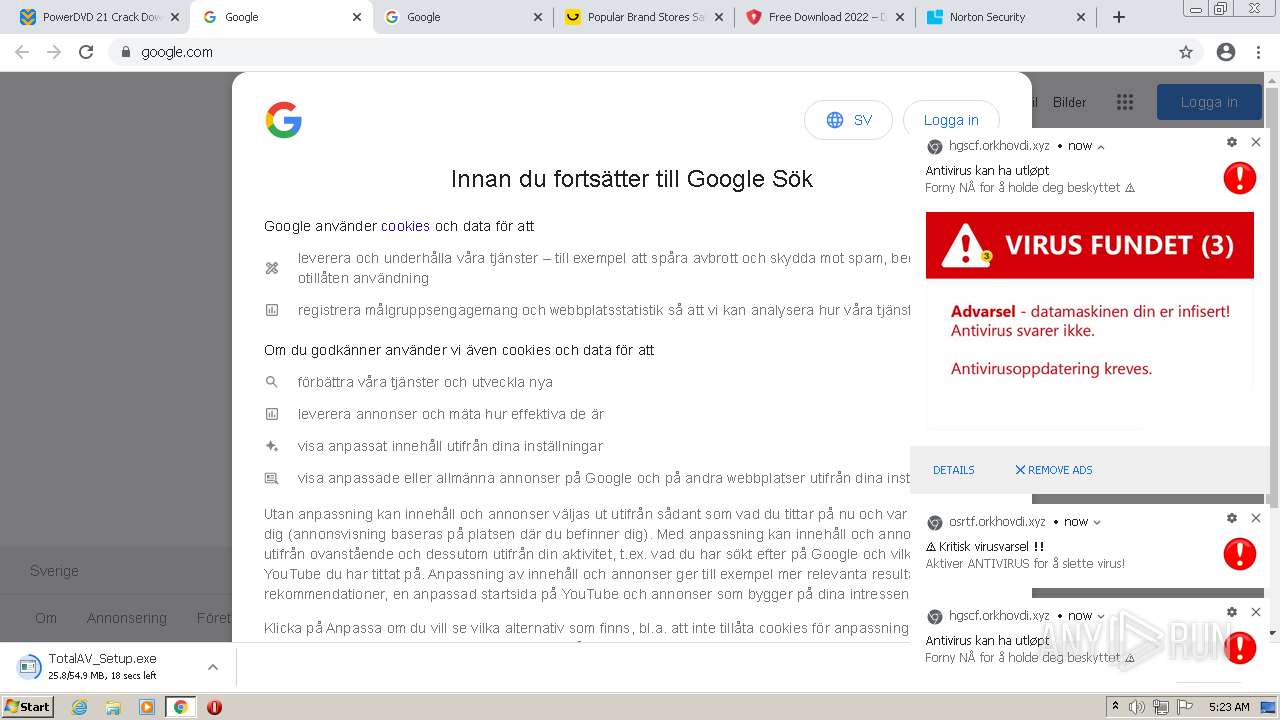
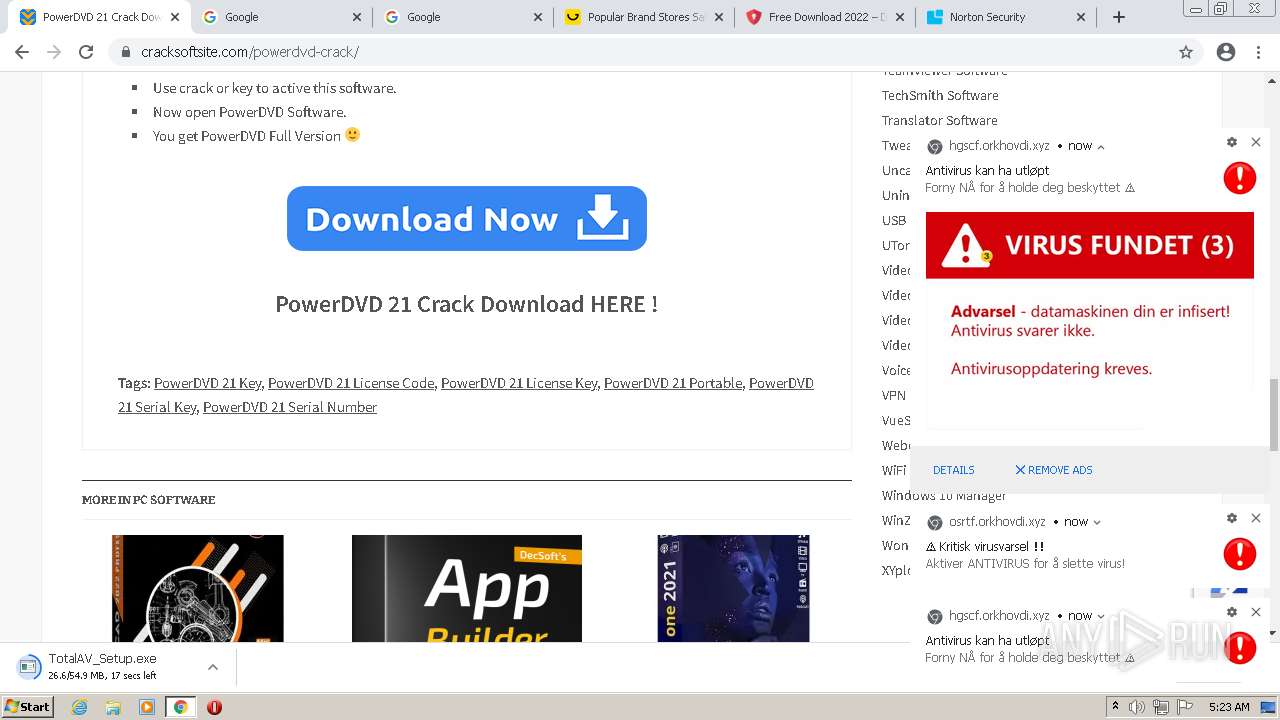
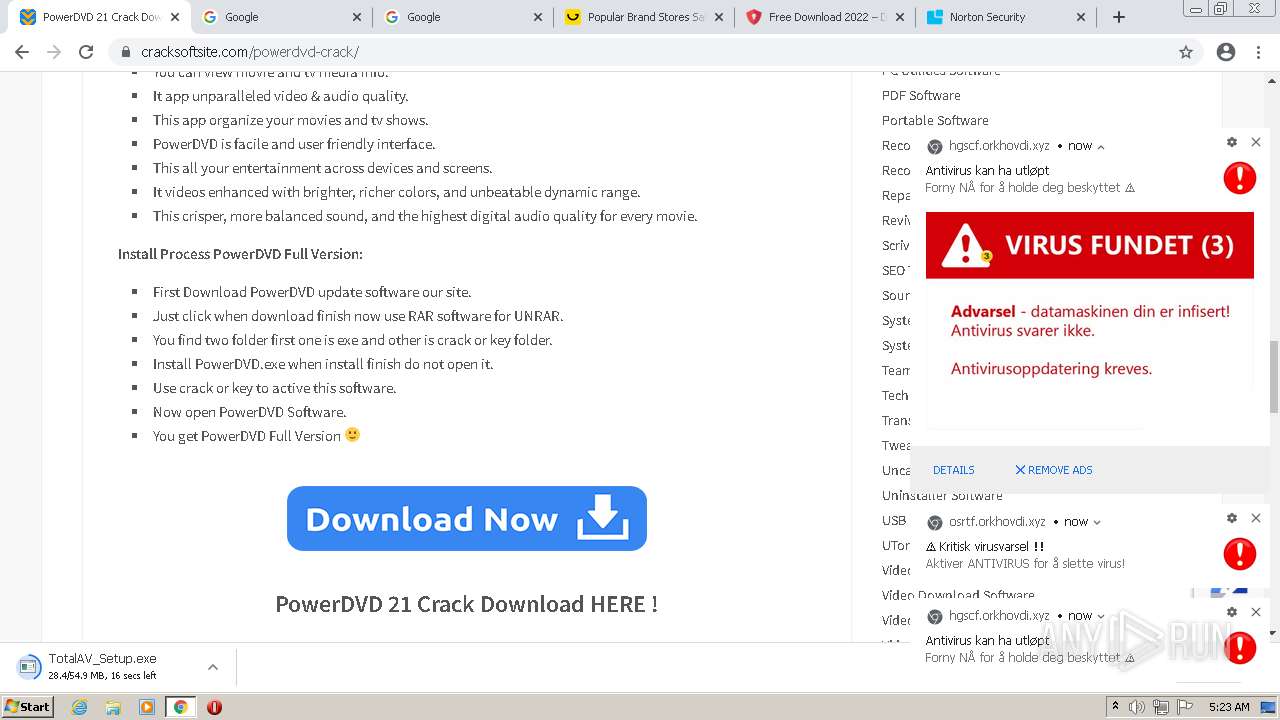
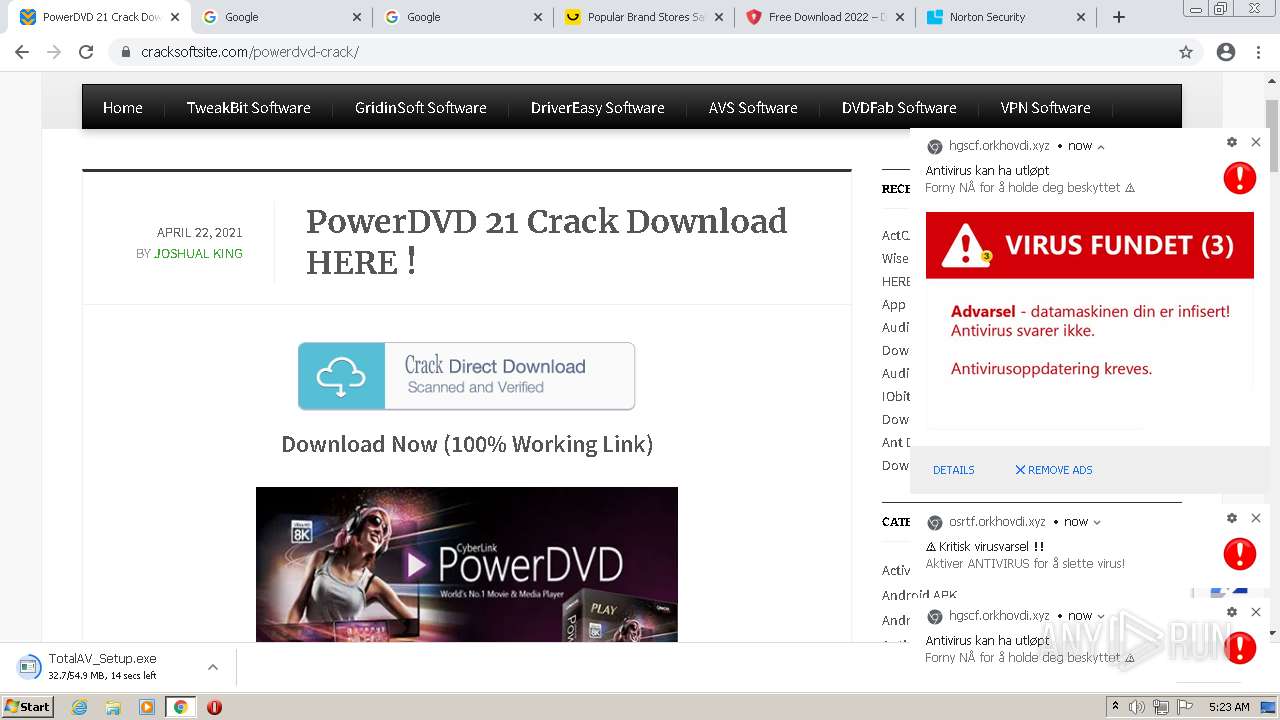
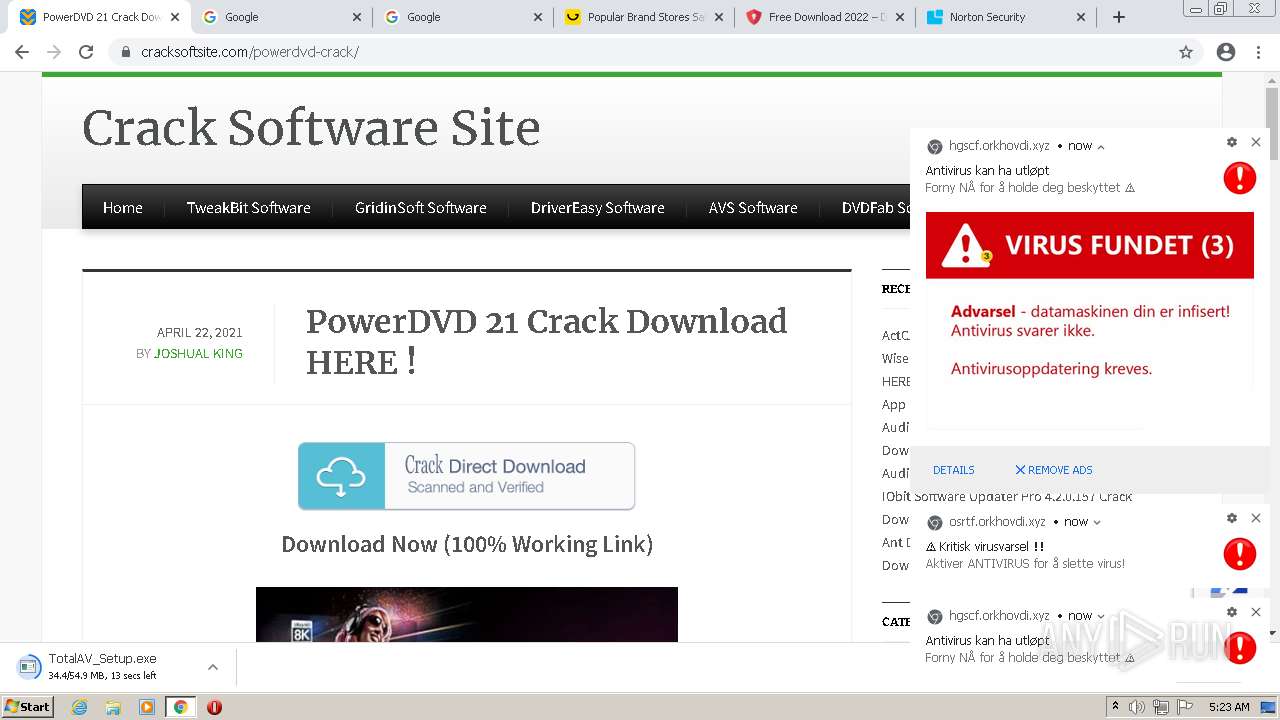
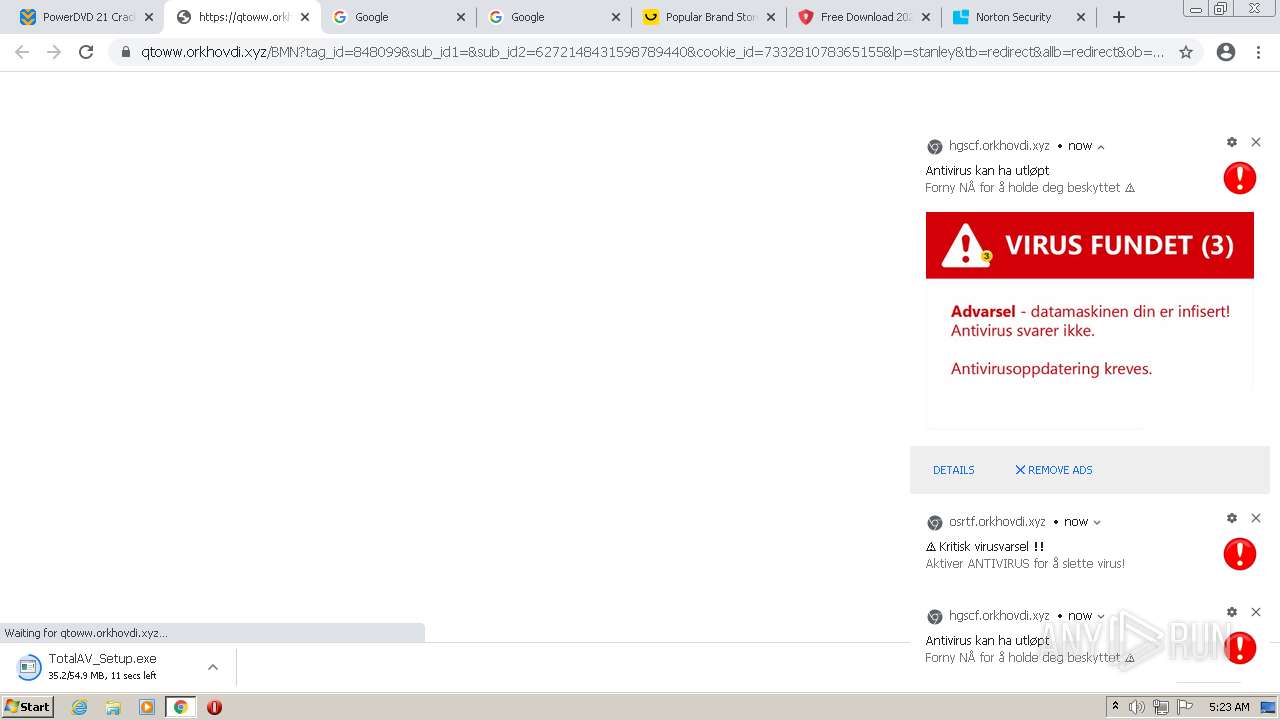
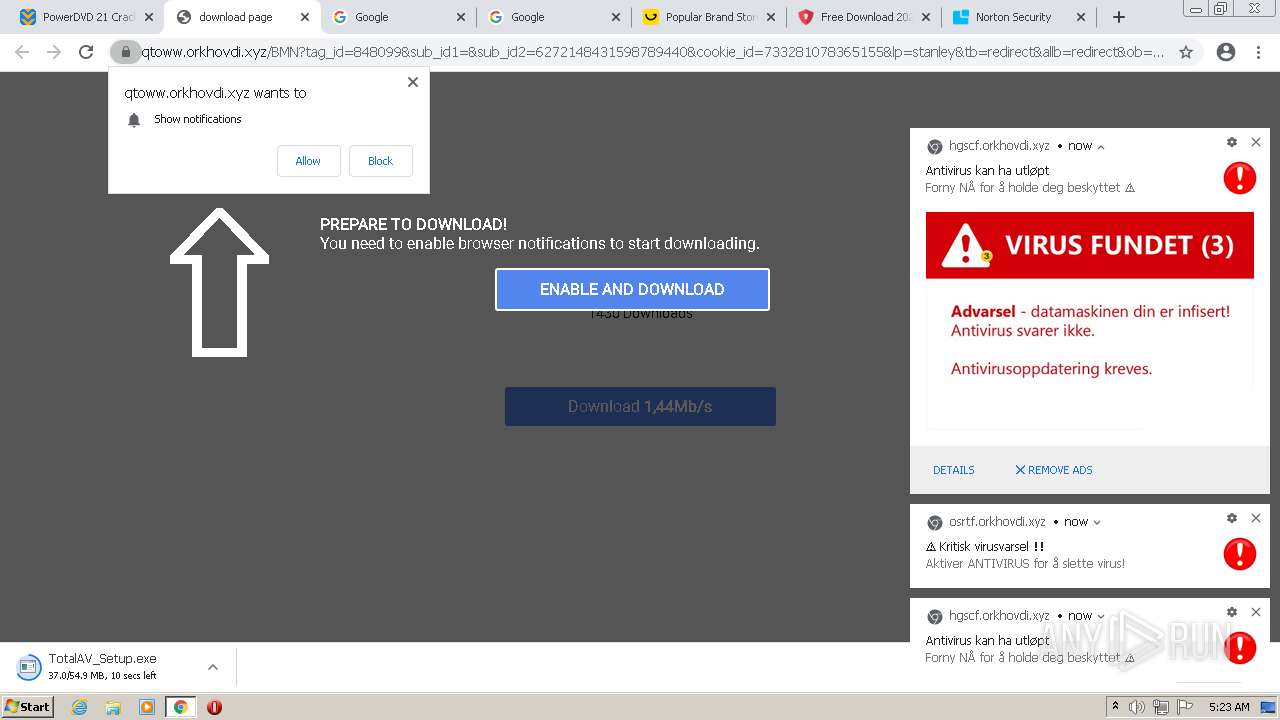
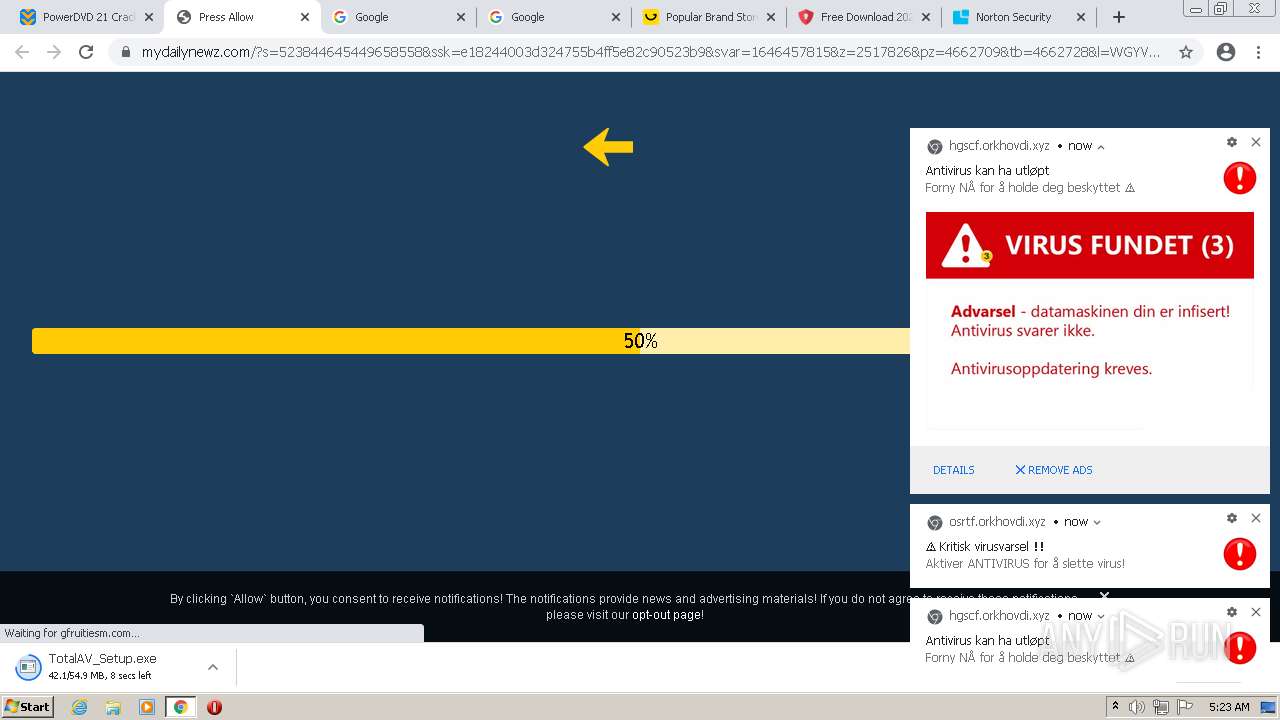
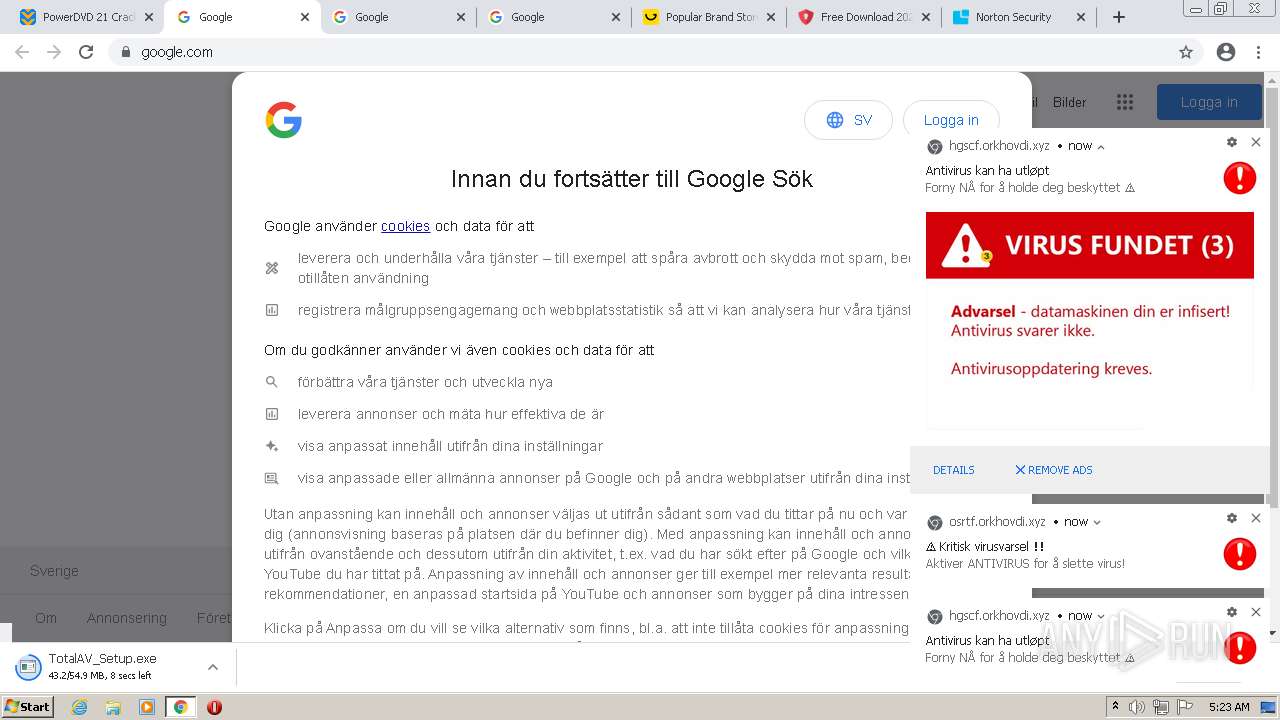
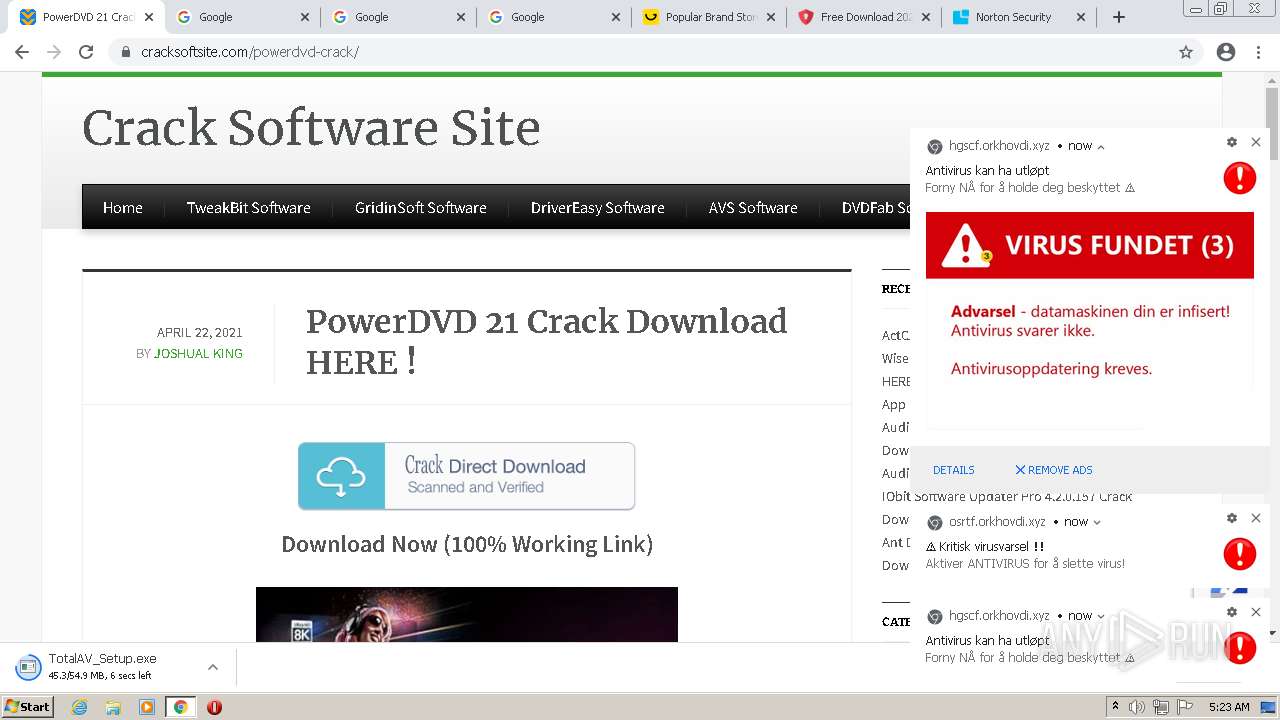
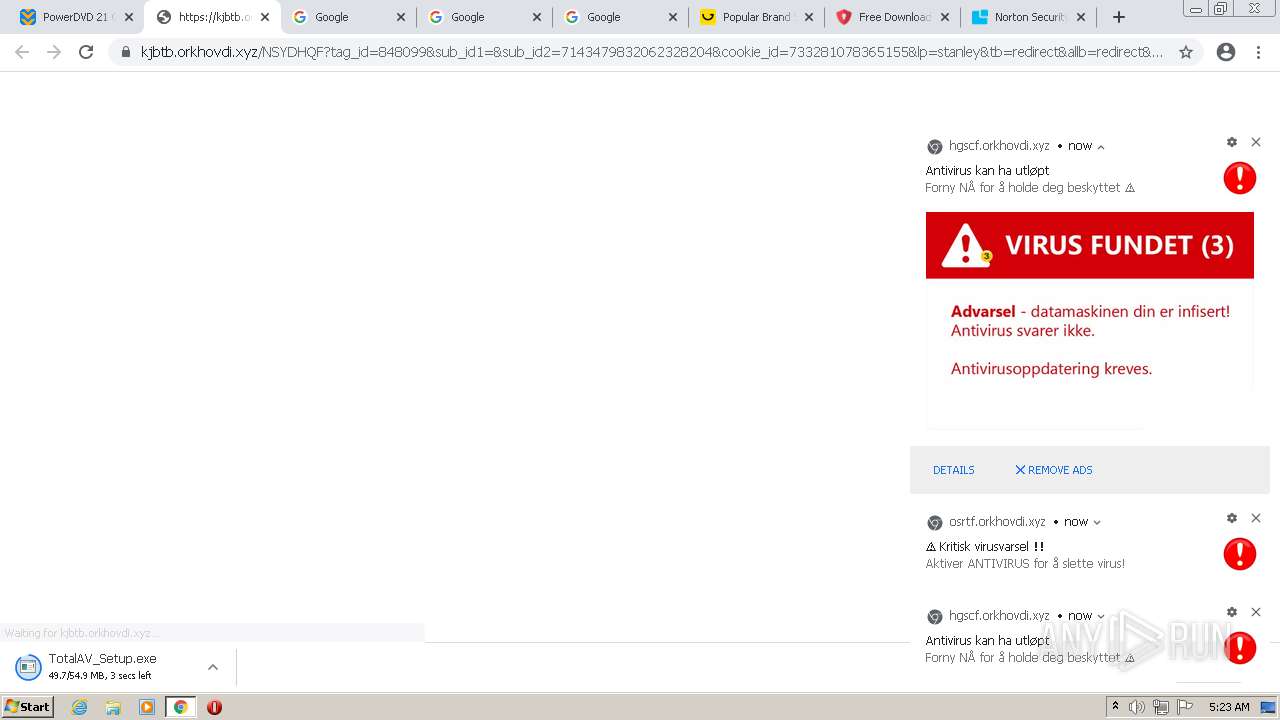
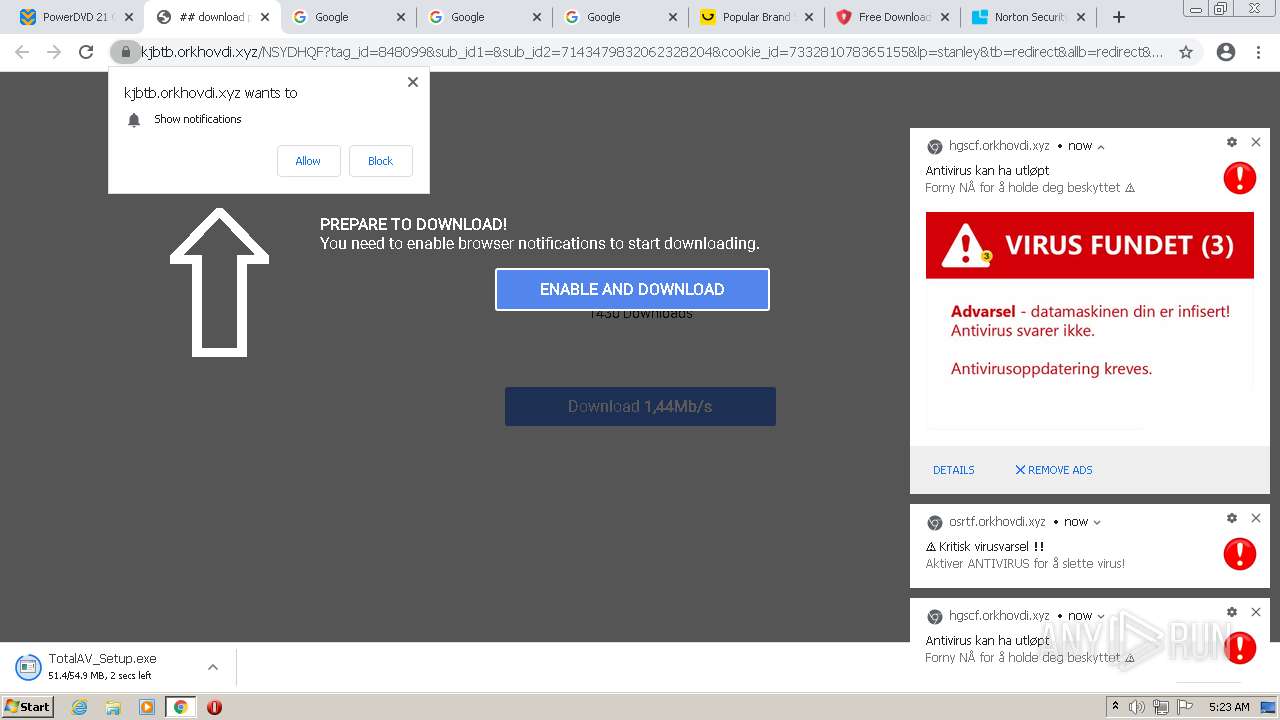
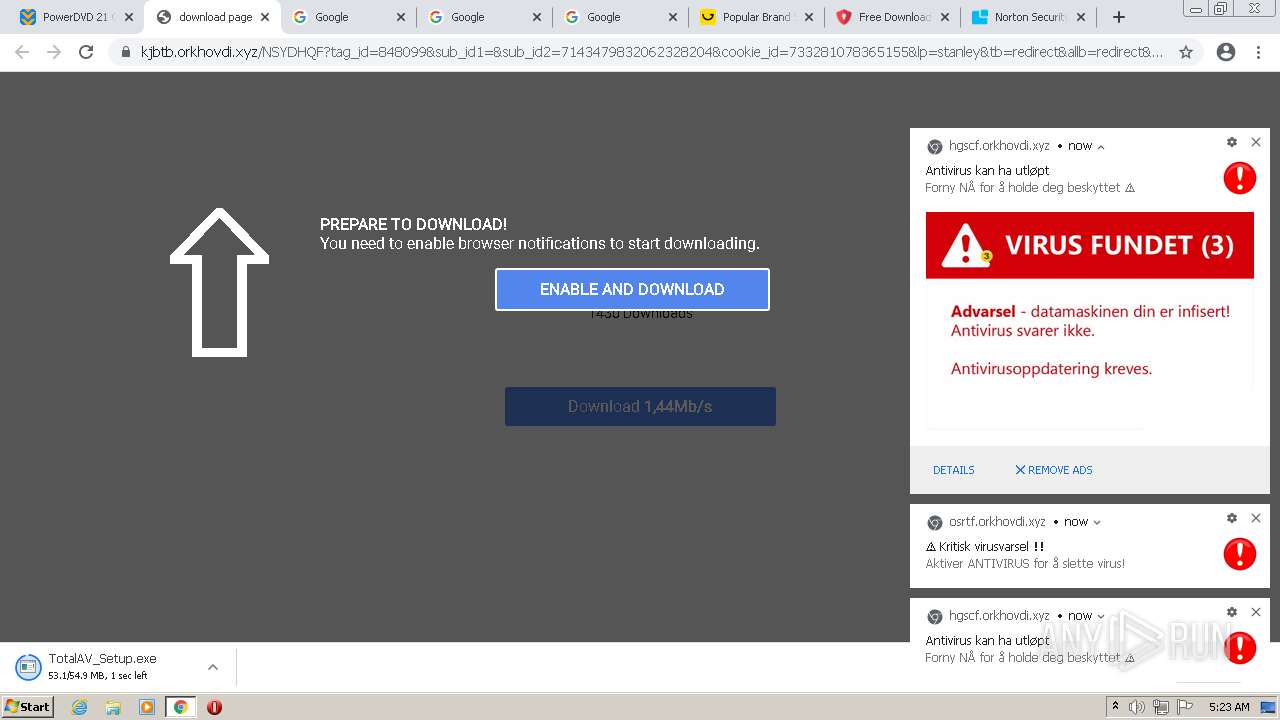
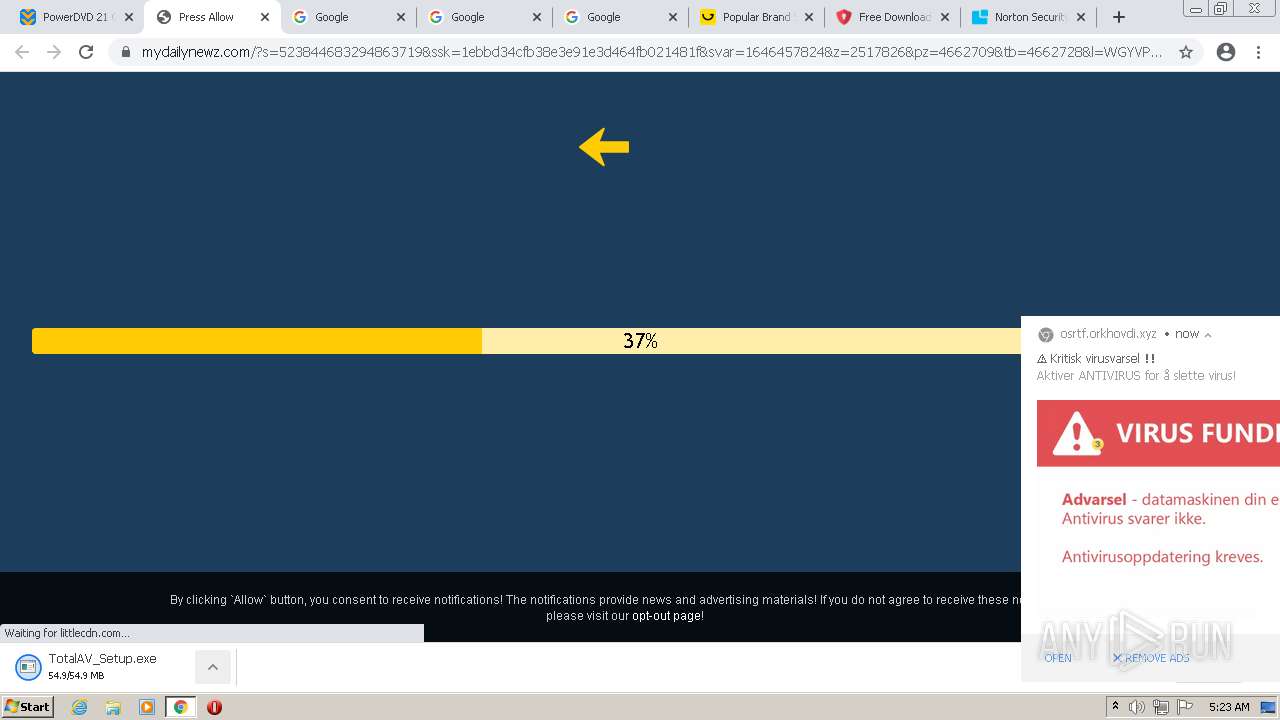
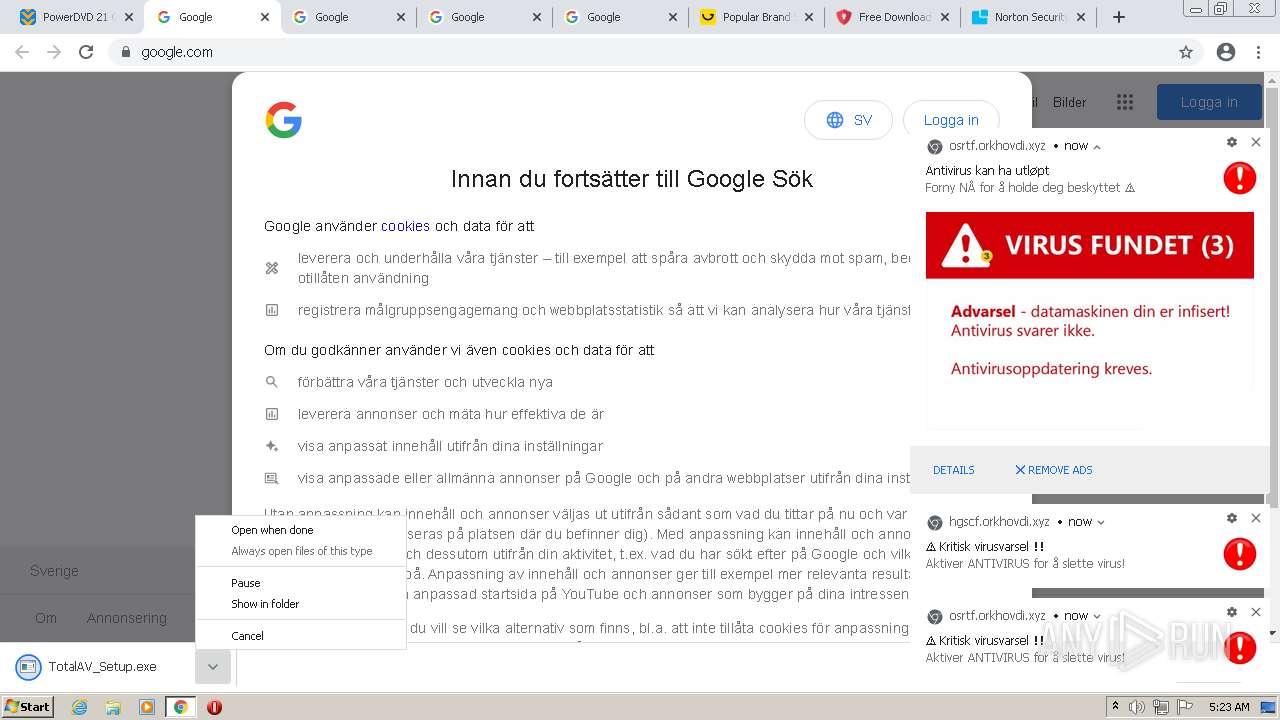
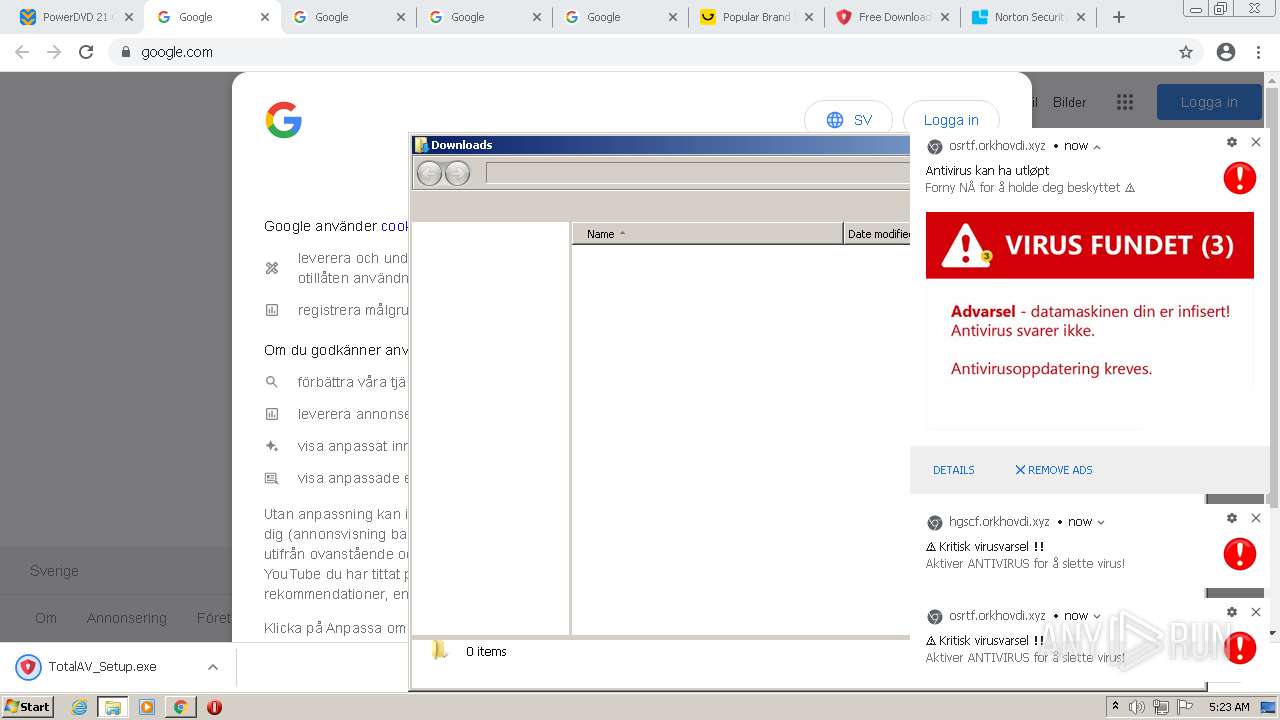
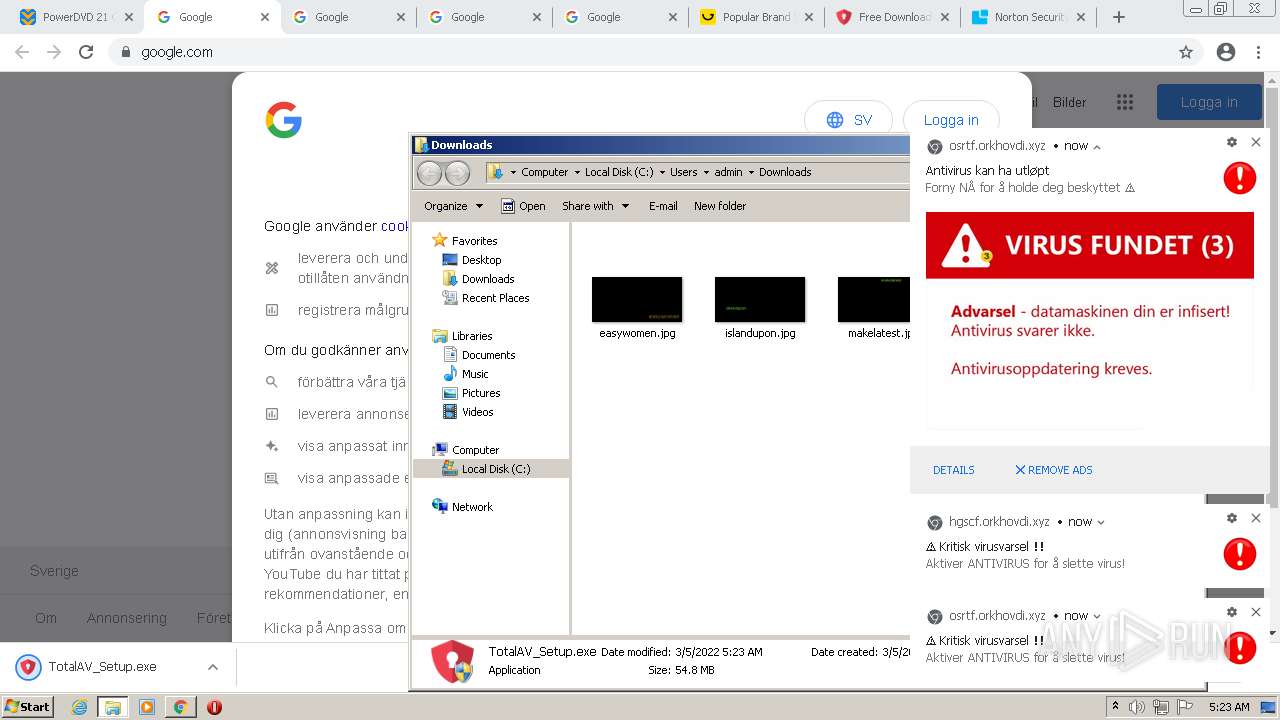
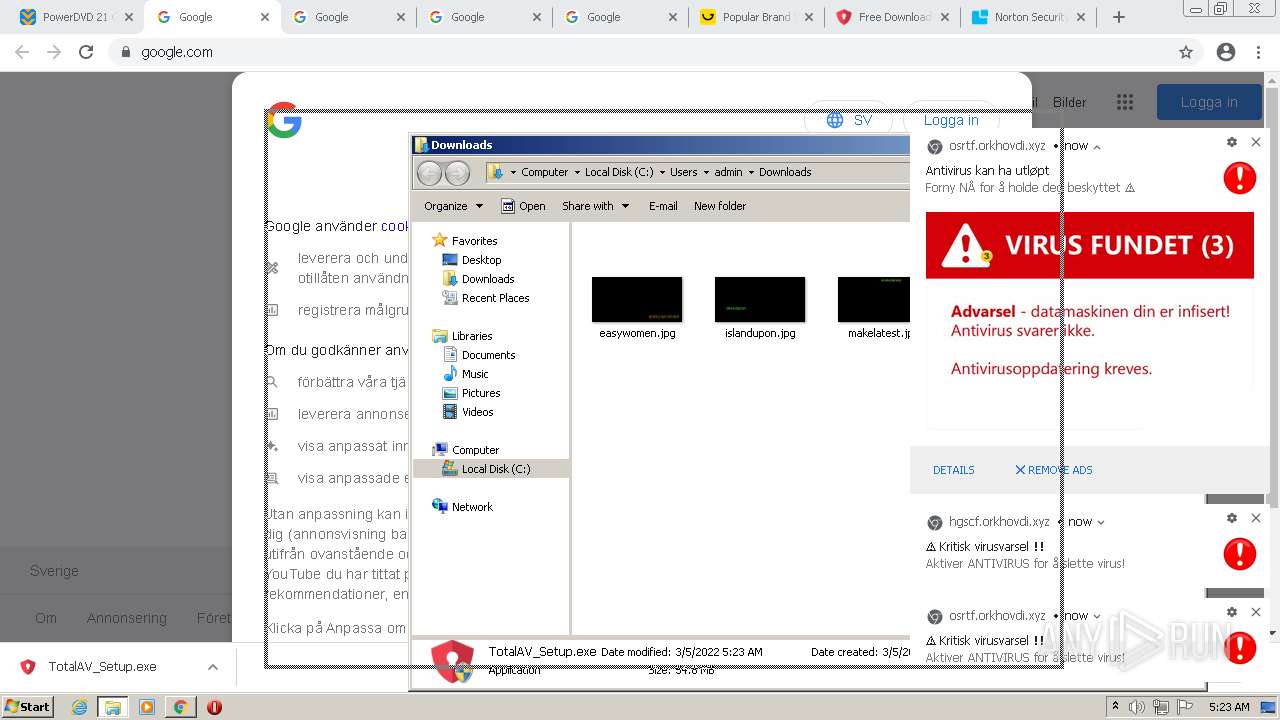
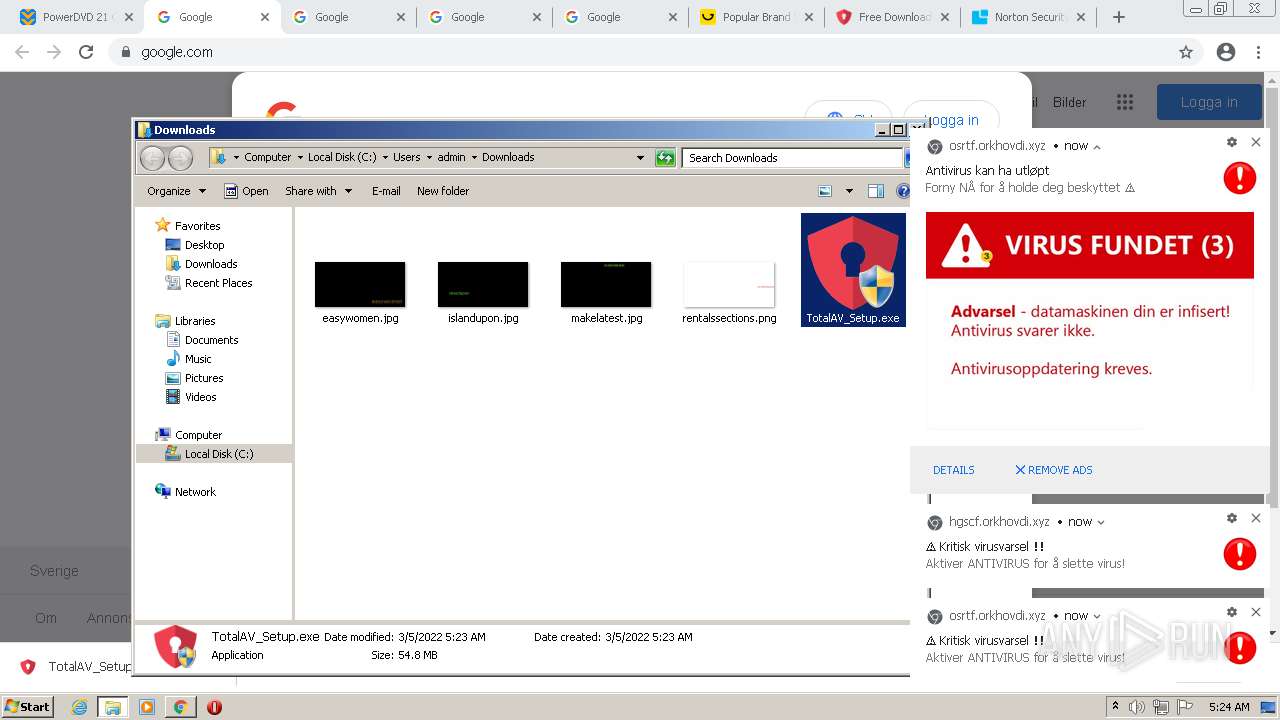
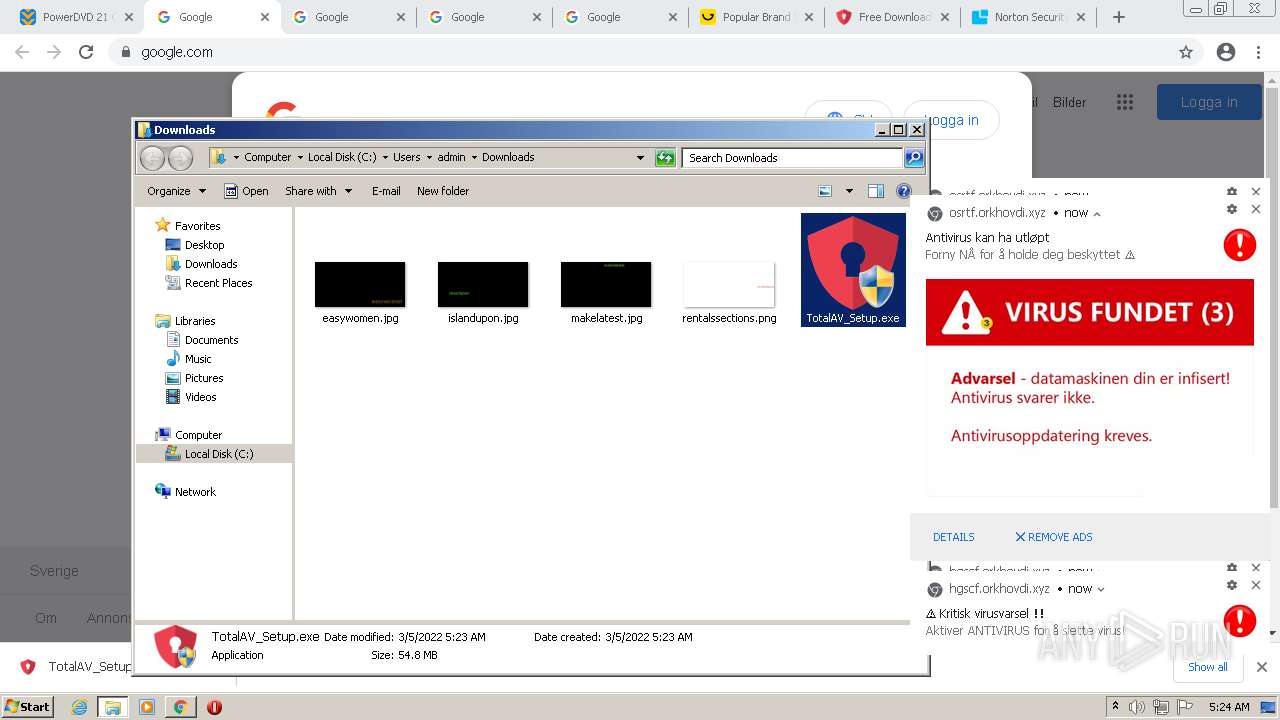
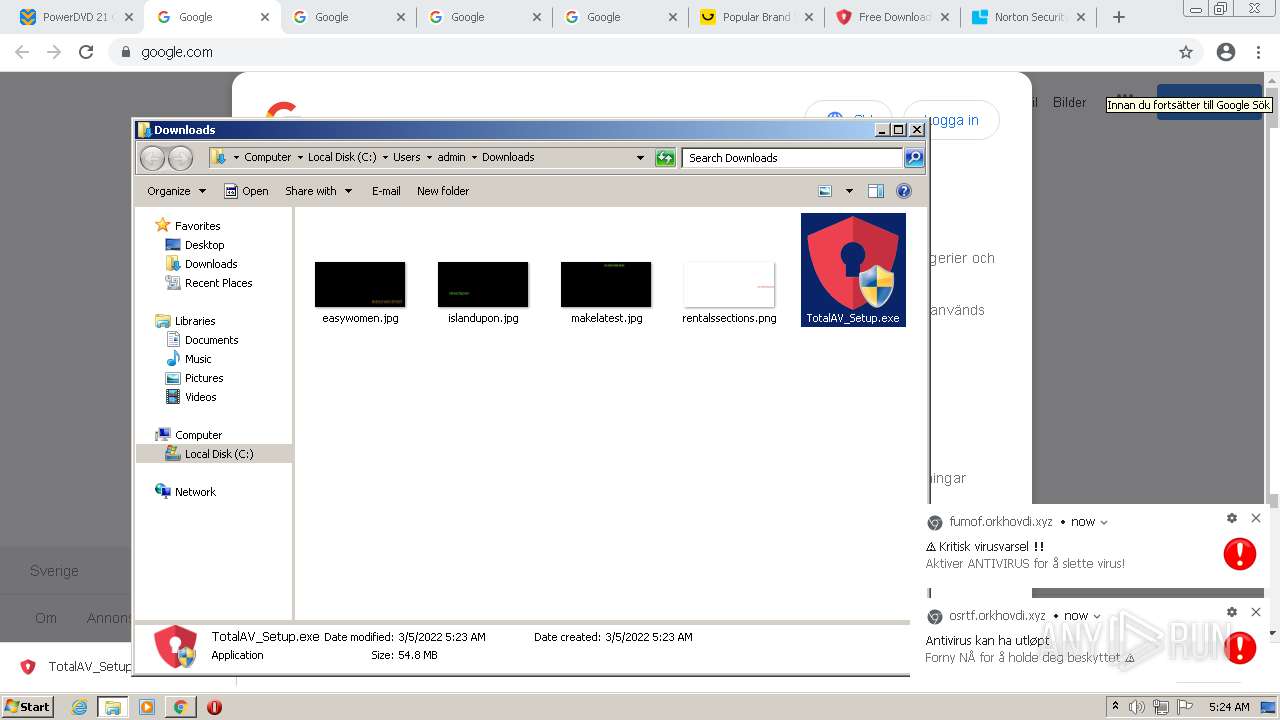
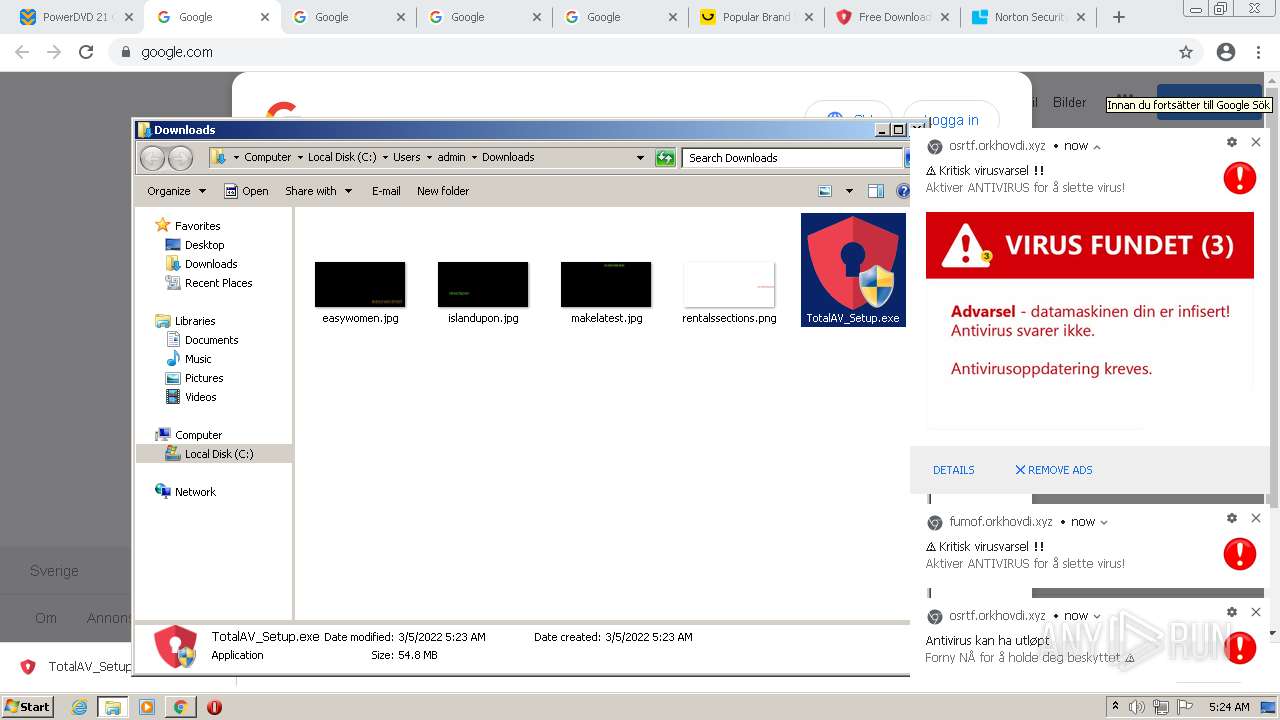
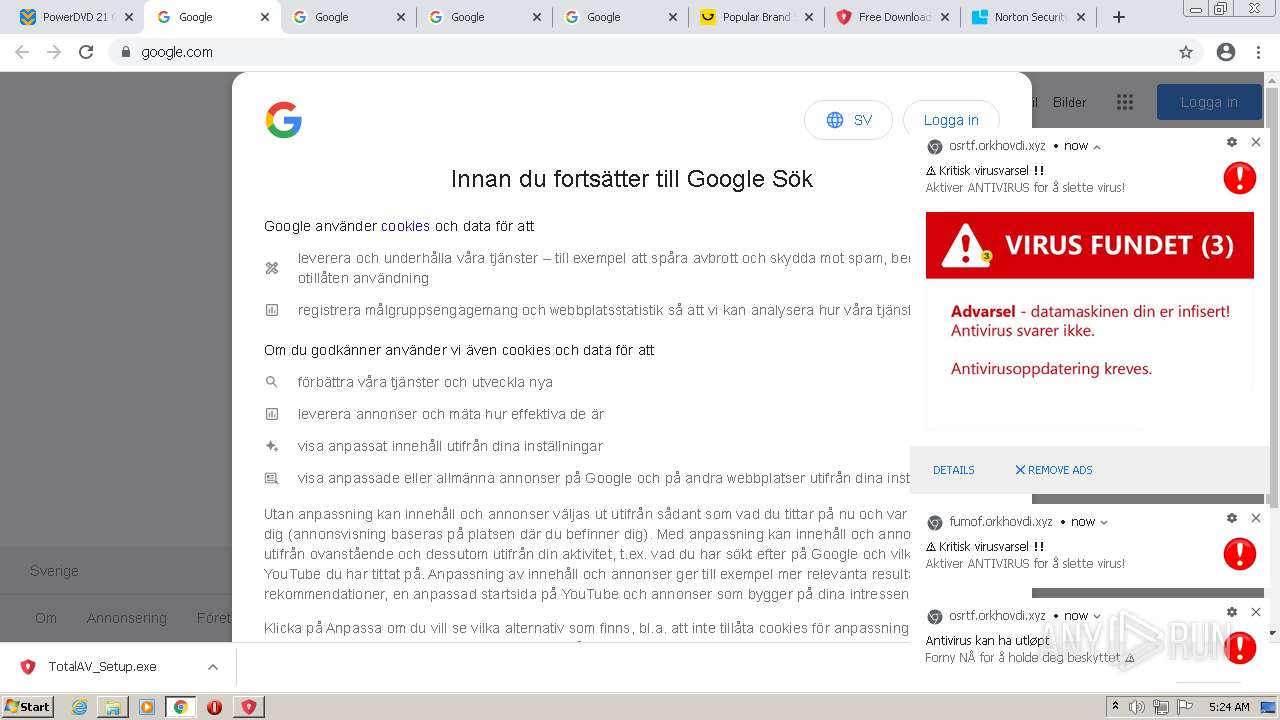
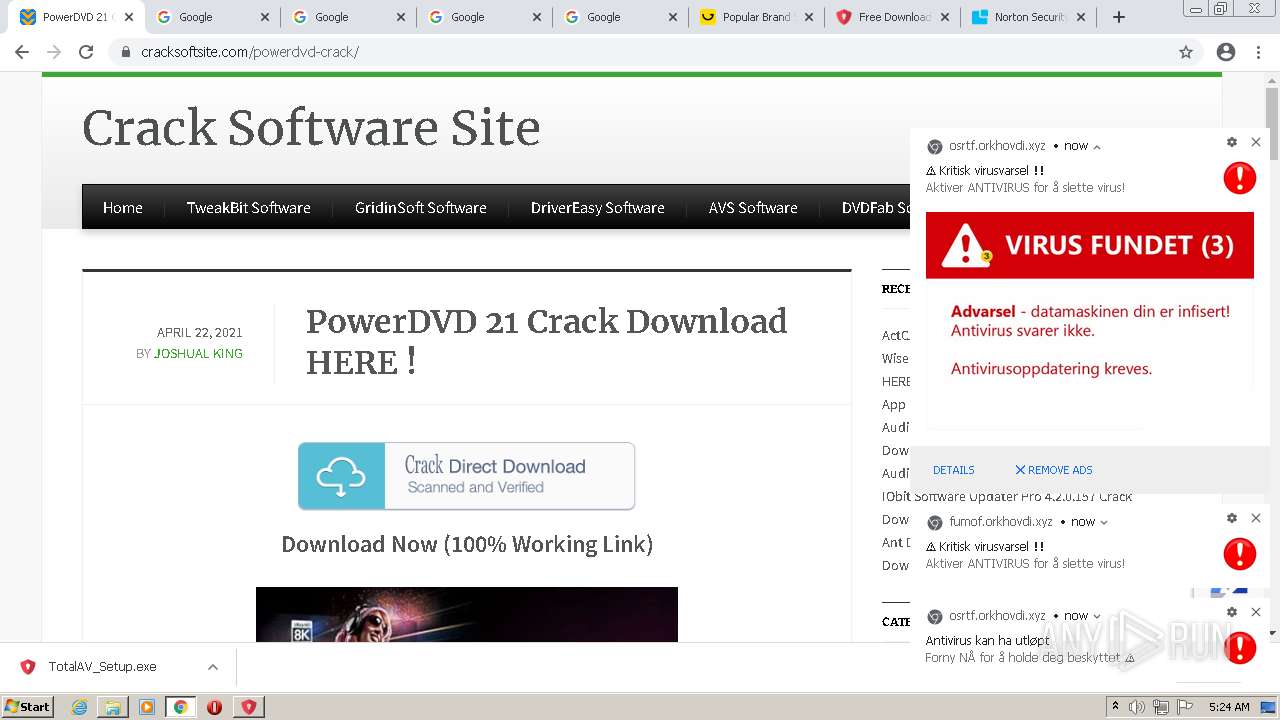
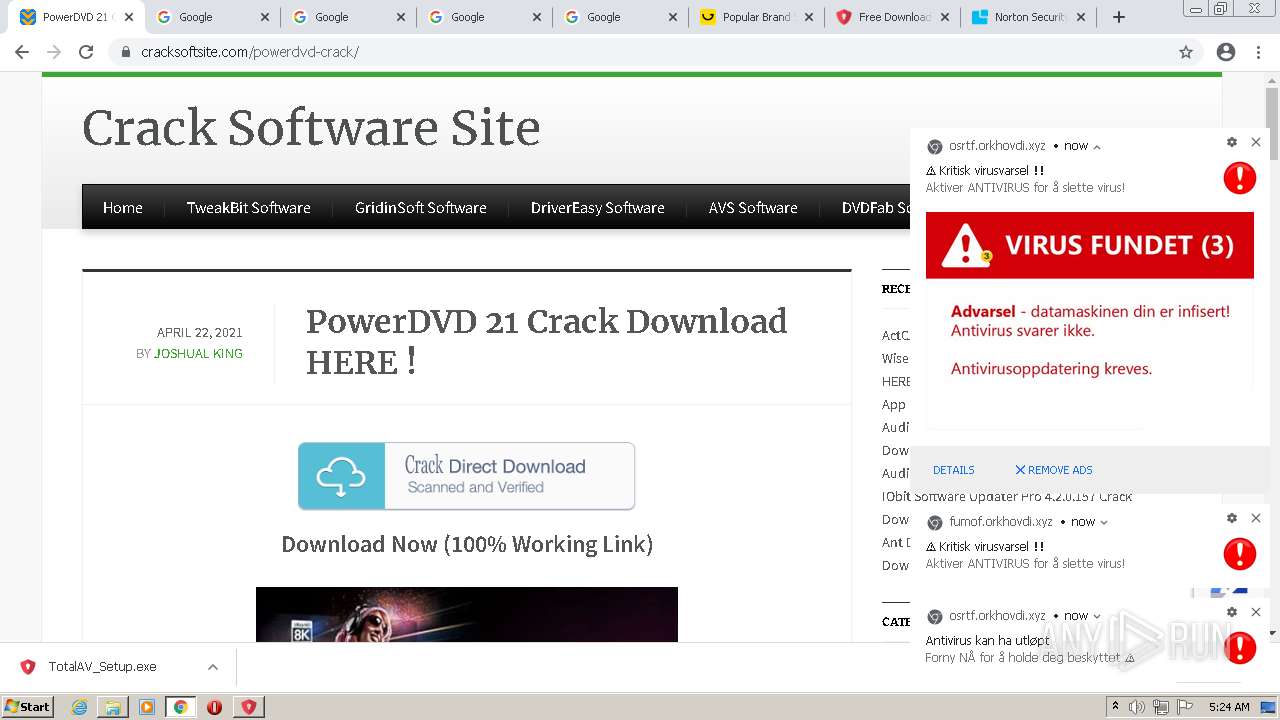
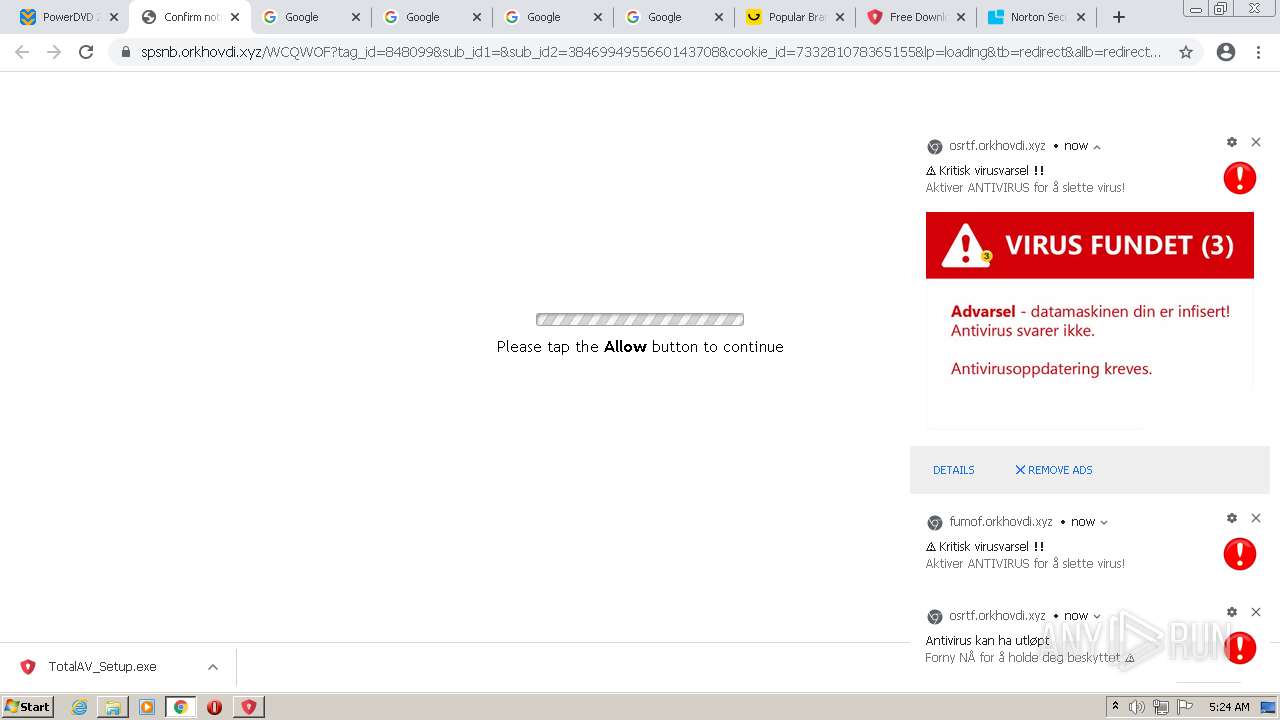
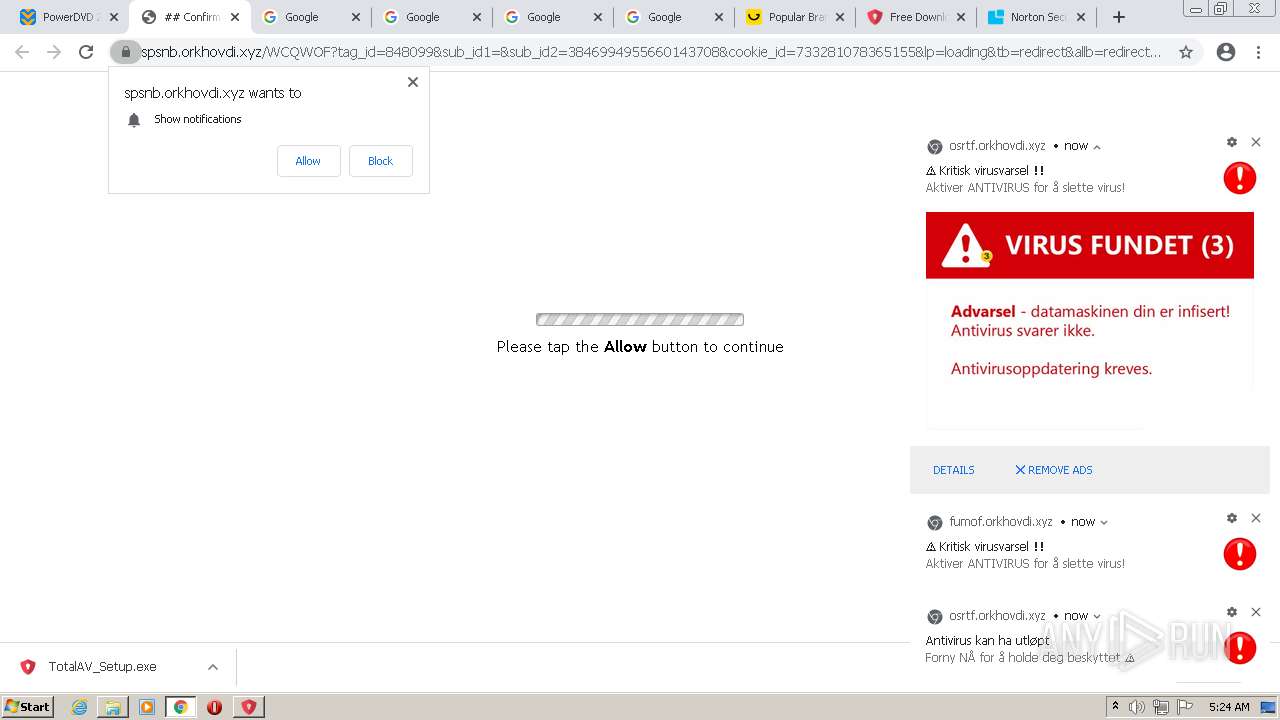
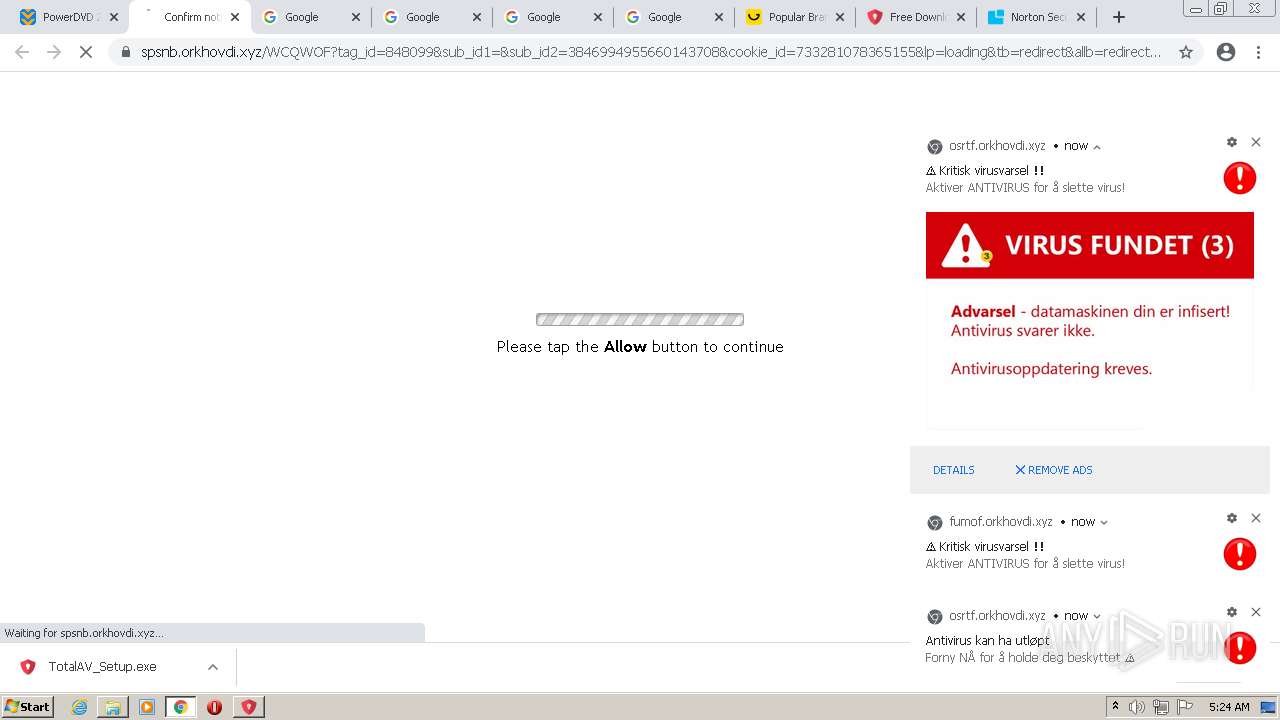
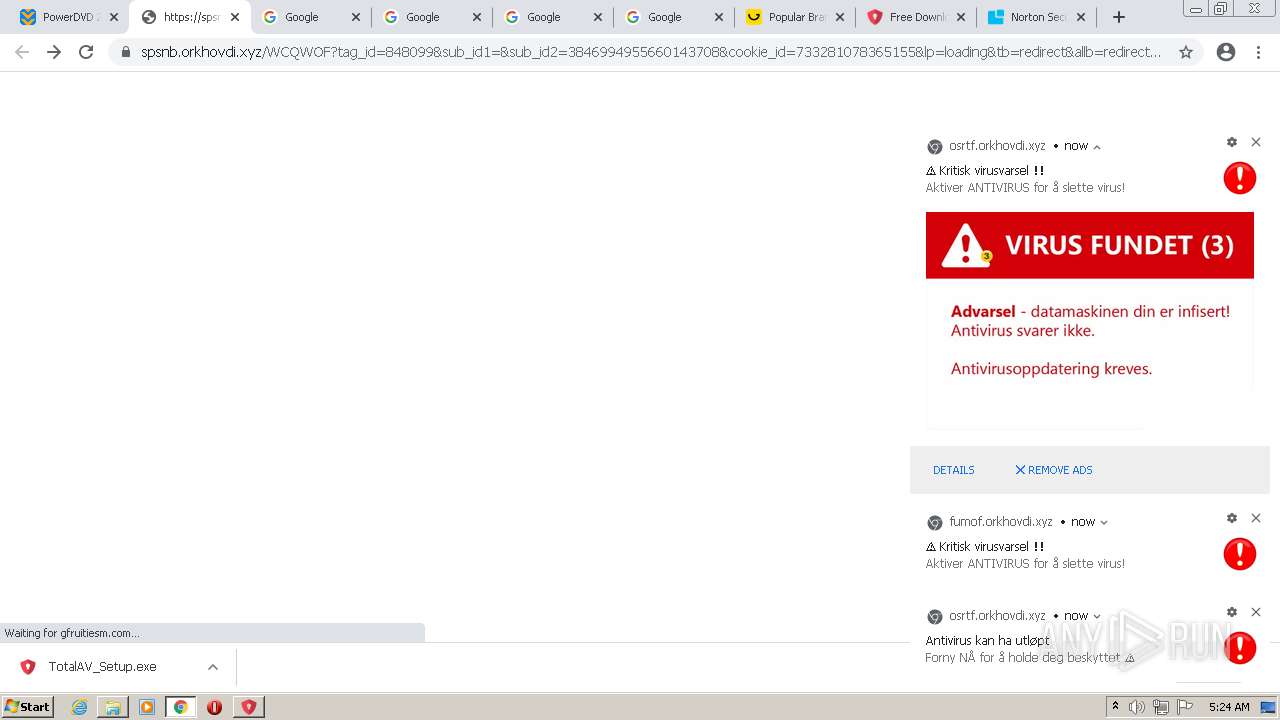
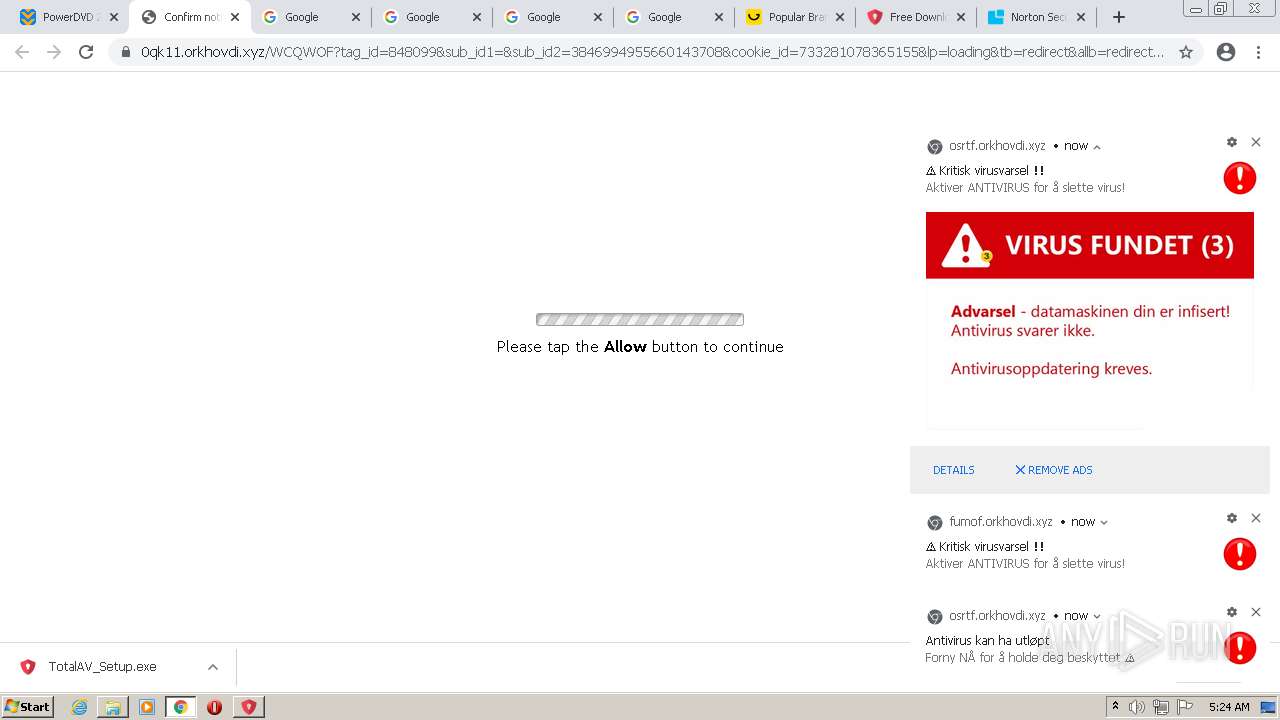
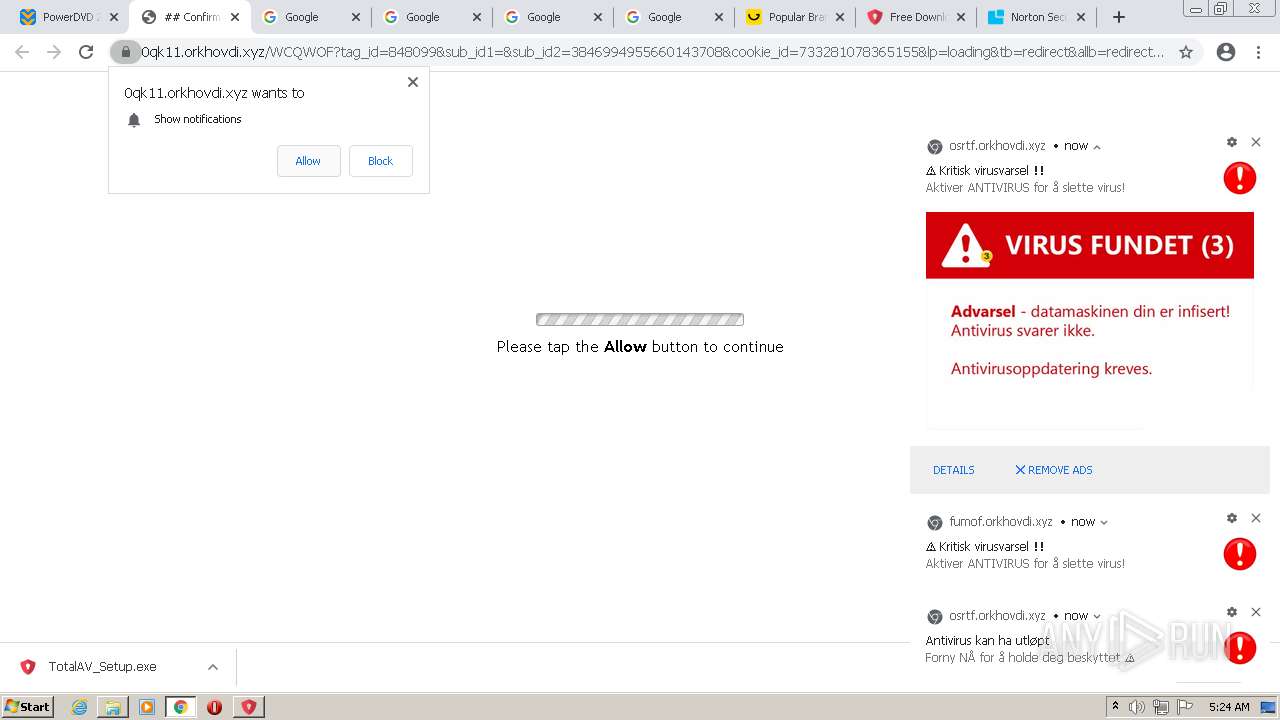
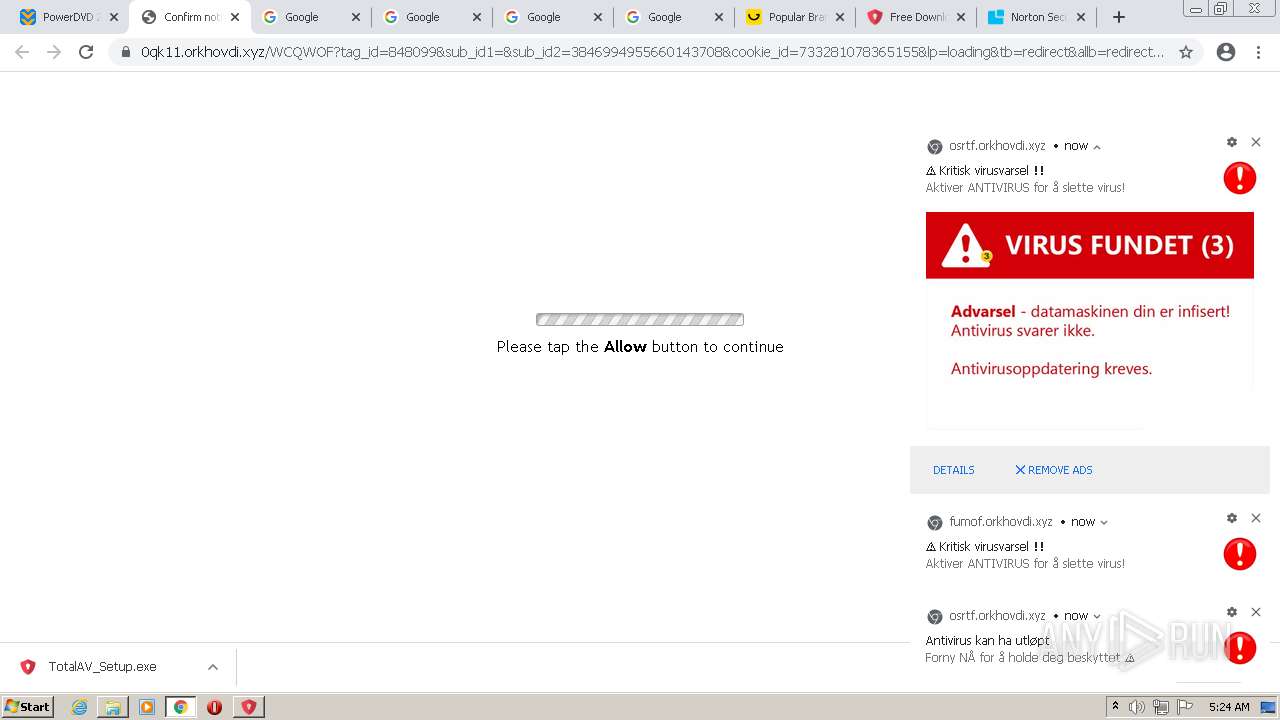
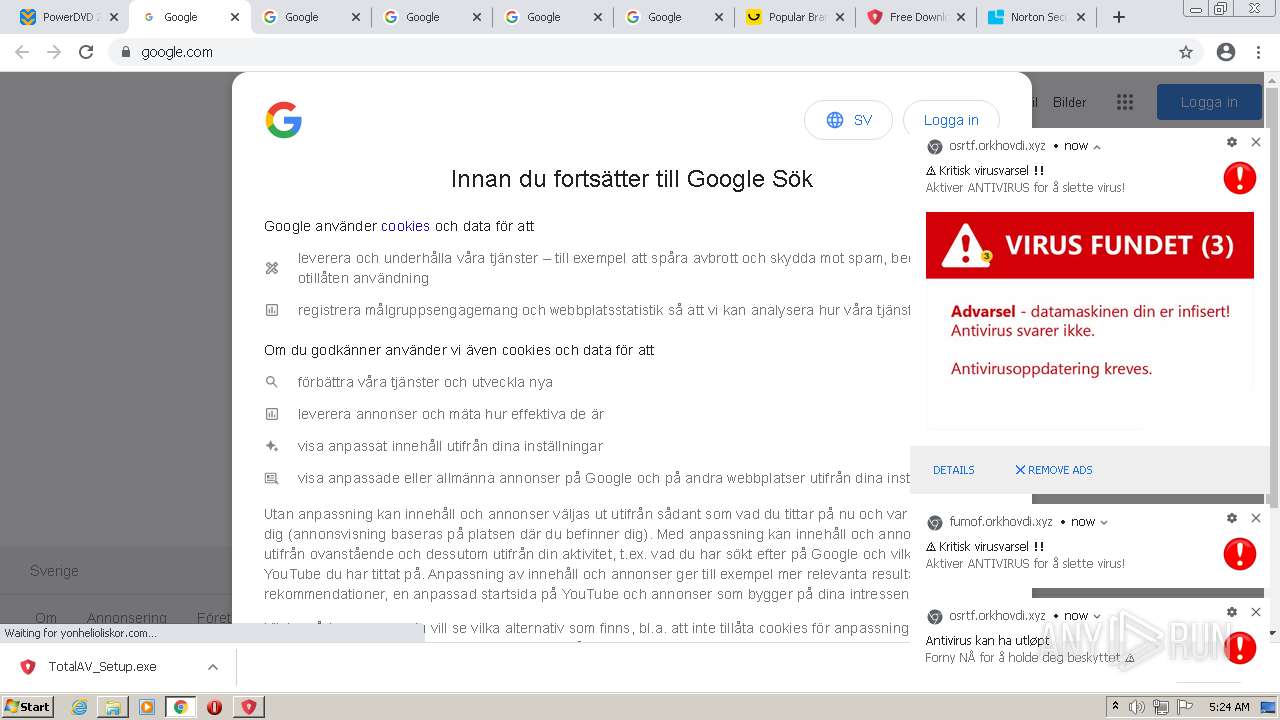
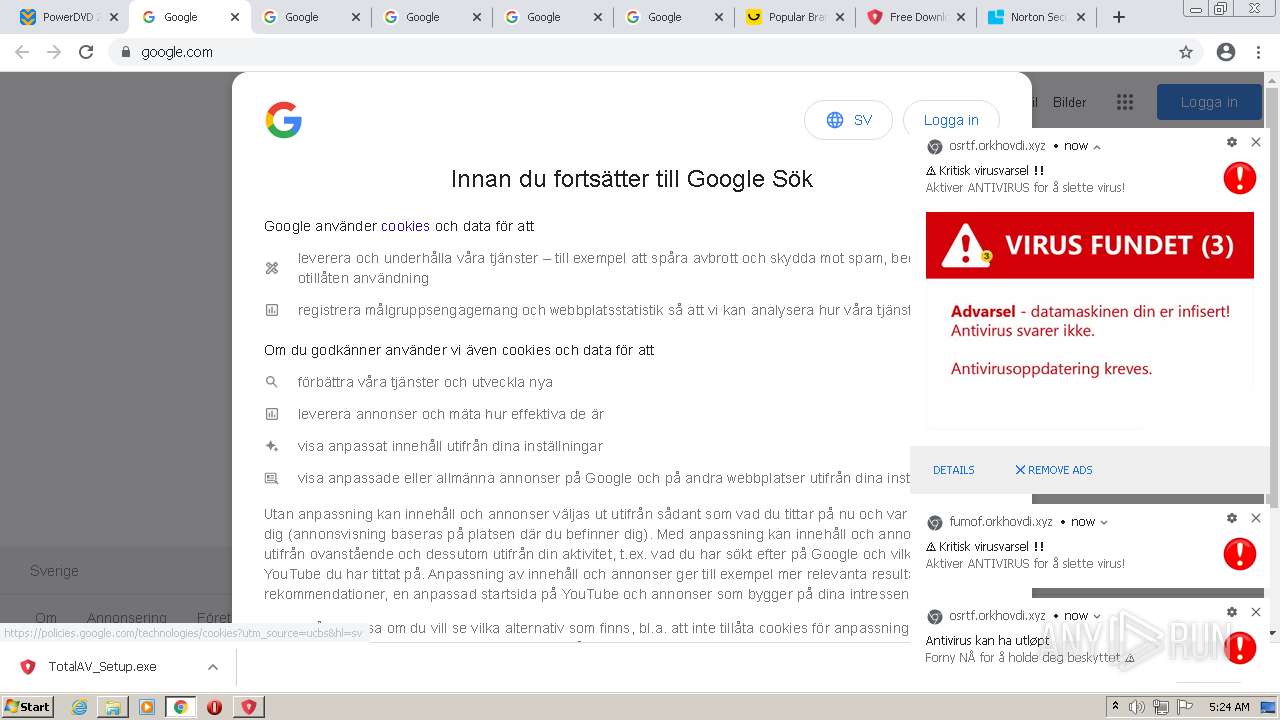
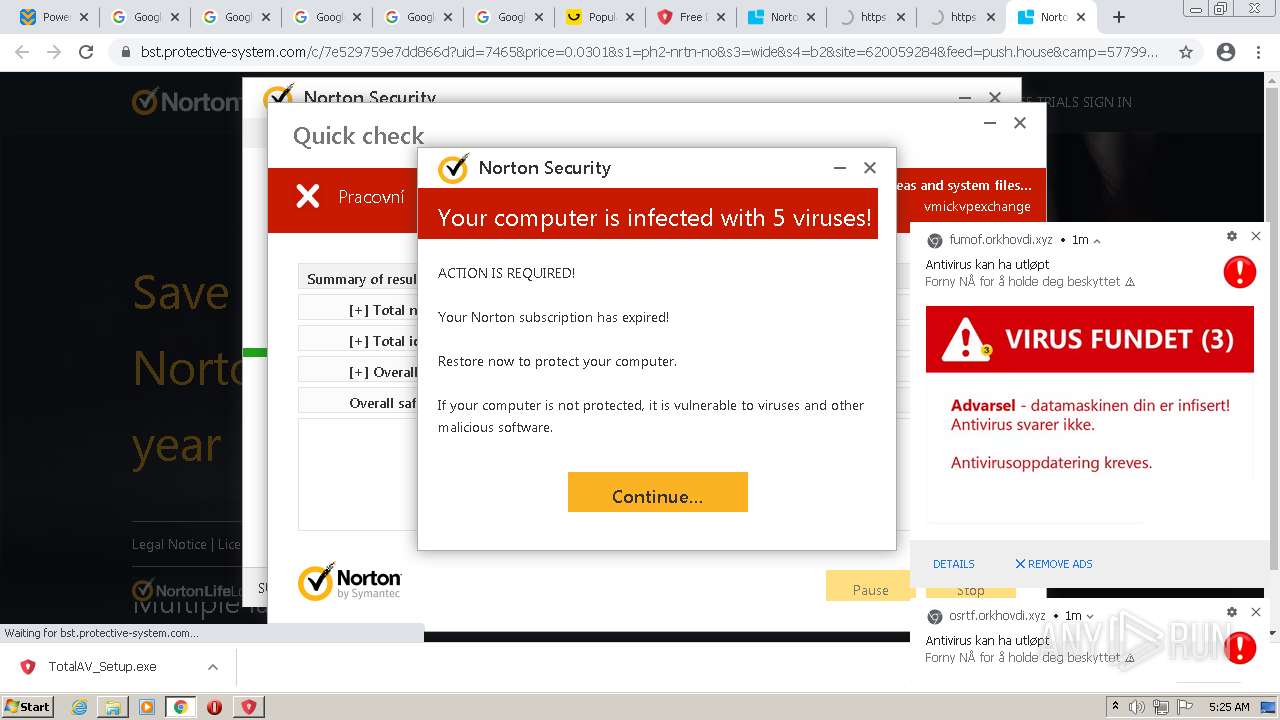
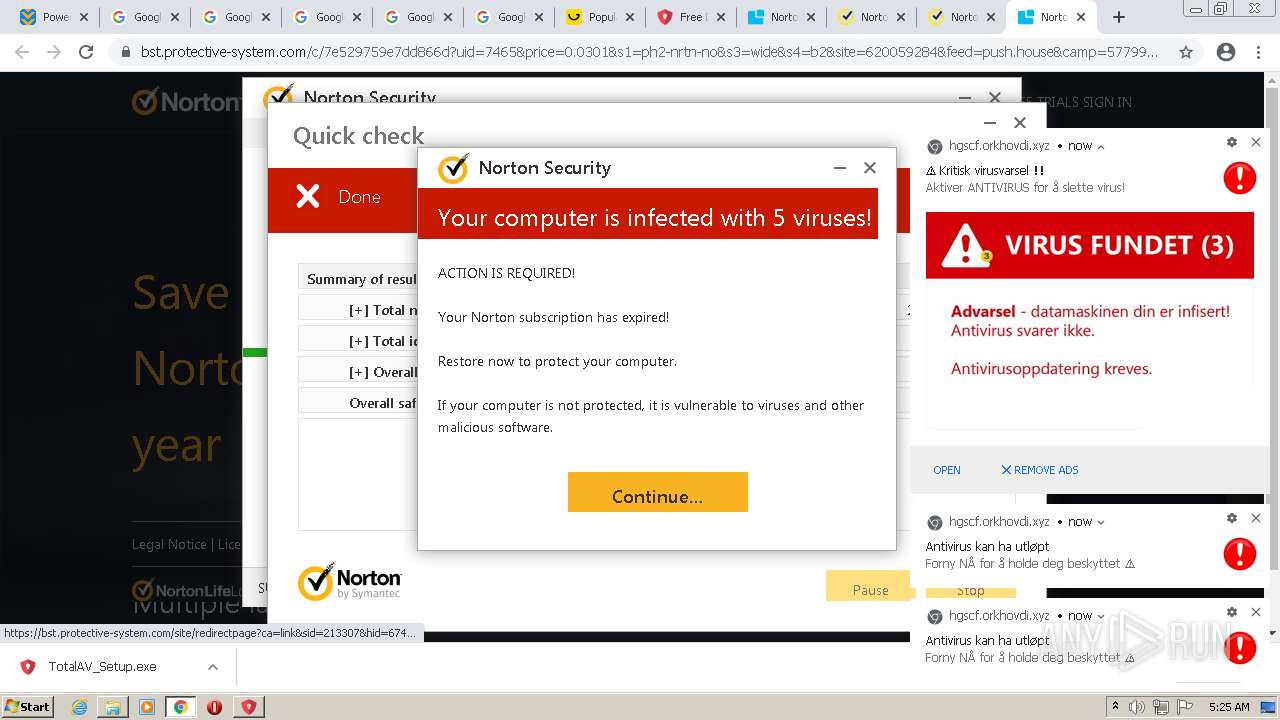
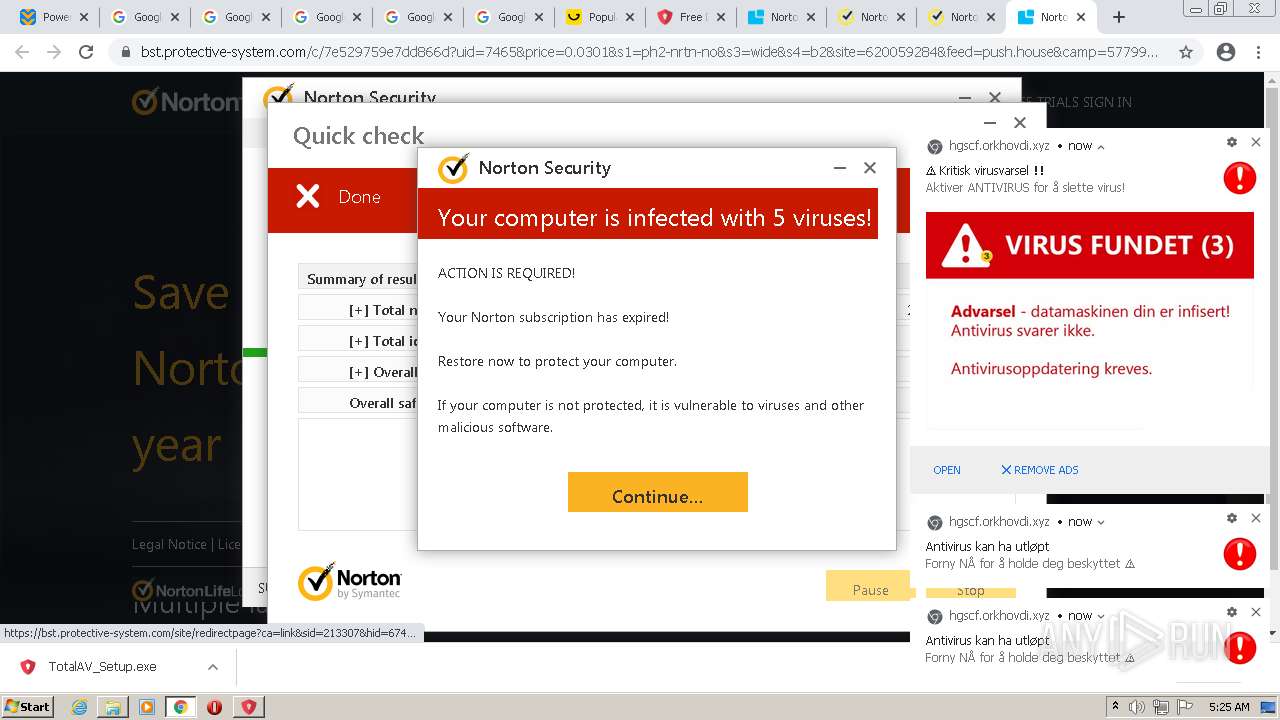
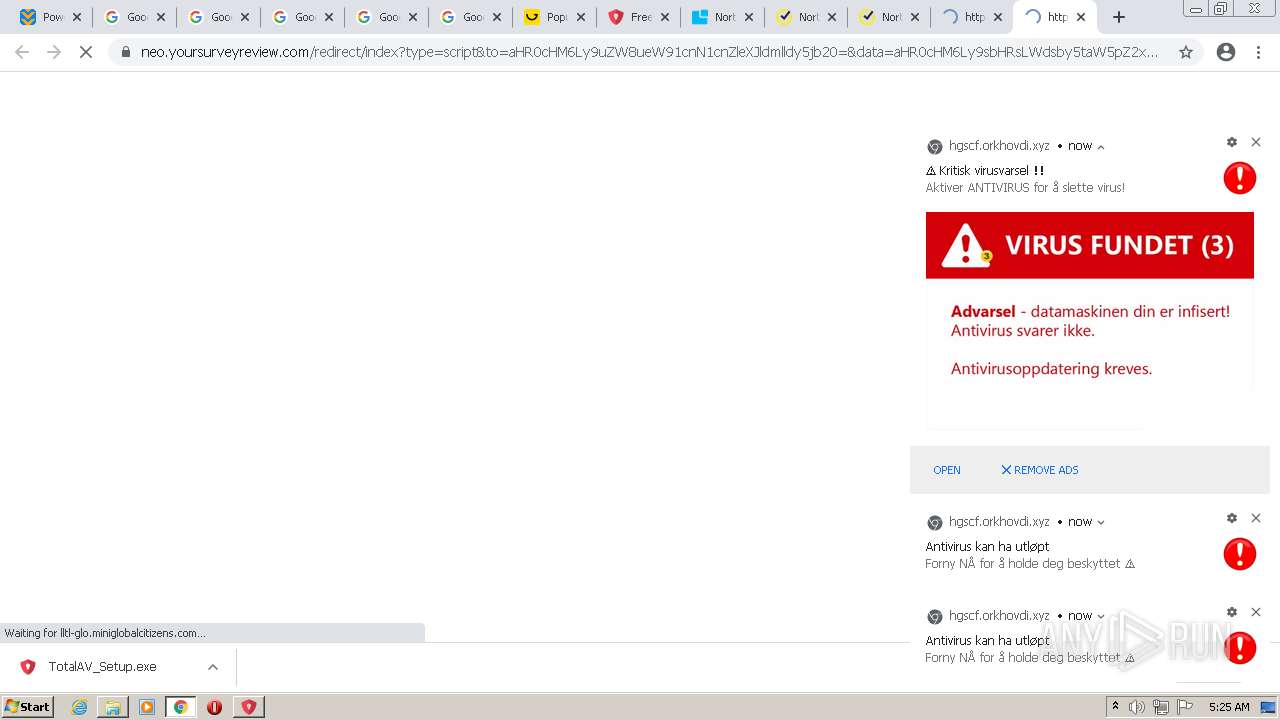
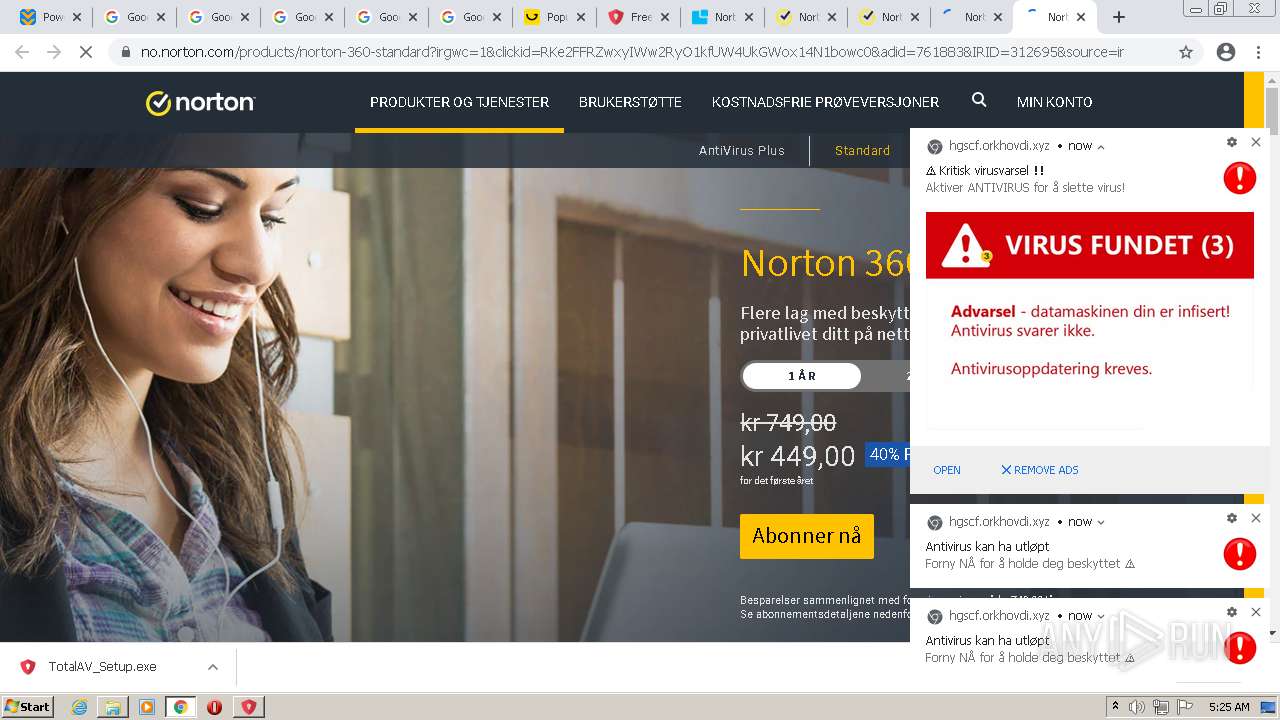
| URL: | https://www.cracksoftsite.com |
| Full analysis: | https://app.any.run/tasks/e4c00974-b355-4572-96d7-5b8b571b1ba2 |
| Verdict: | Malicious activity |
| Analysis date: | March 05, 2022, 05:22:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 209E5CF24BED73C5467BD99D5A4BCF7A |
| SHA1: | C35C1A2B056721C585A3371787CBD10B369E81D7 |
| SHA256: | AD9DCB7E39697BCB55953E3C0F4533B4277457FAF6D87D20E9C82D4201A00620 |
| SSDEEP: | 3:N8DSLbWYwg:2OL9wg |
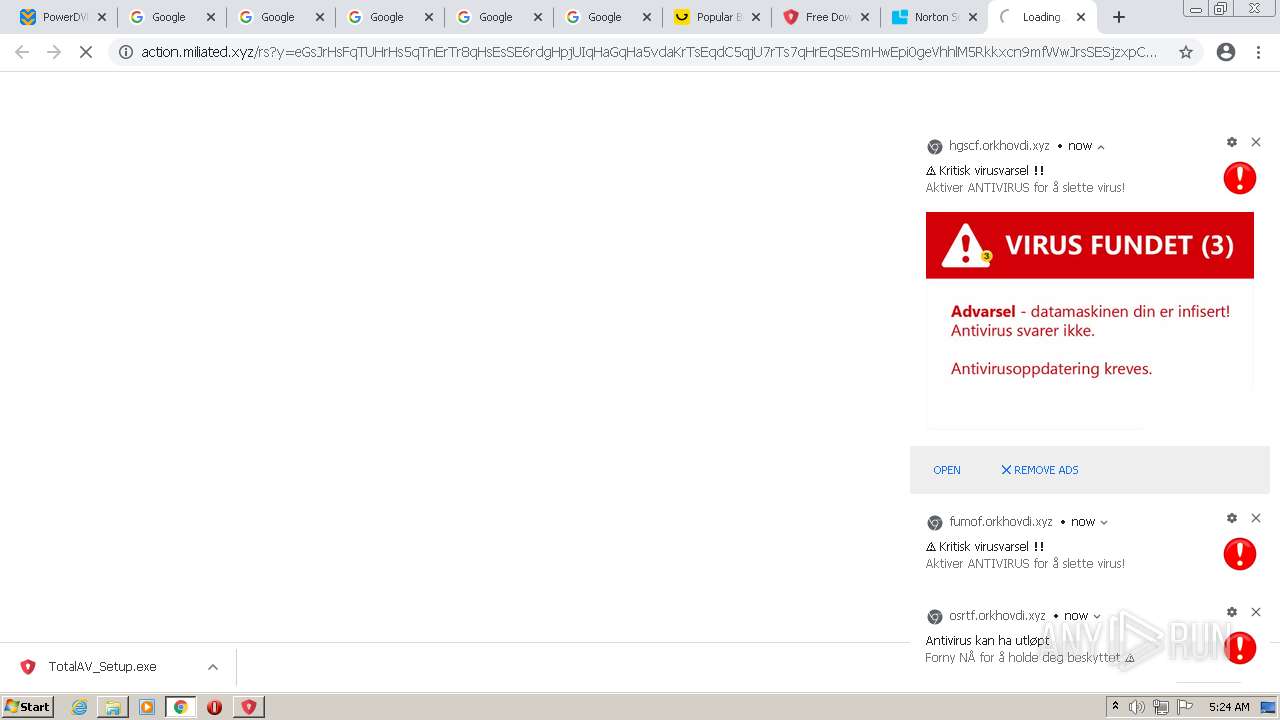
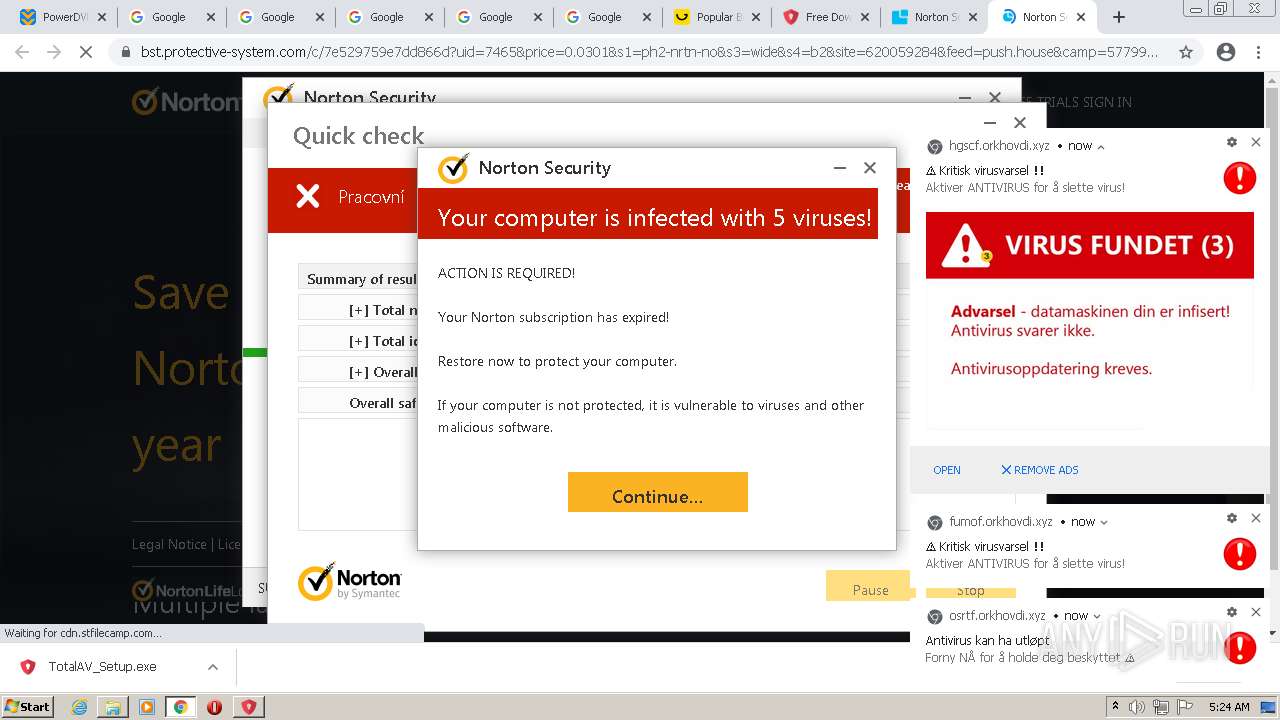
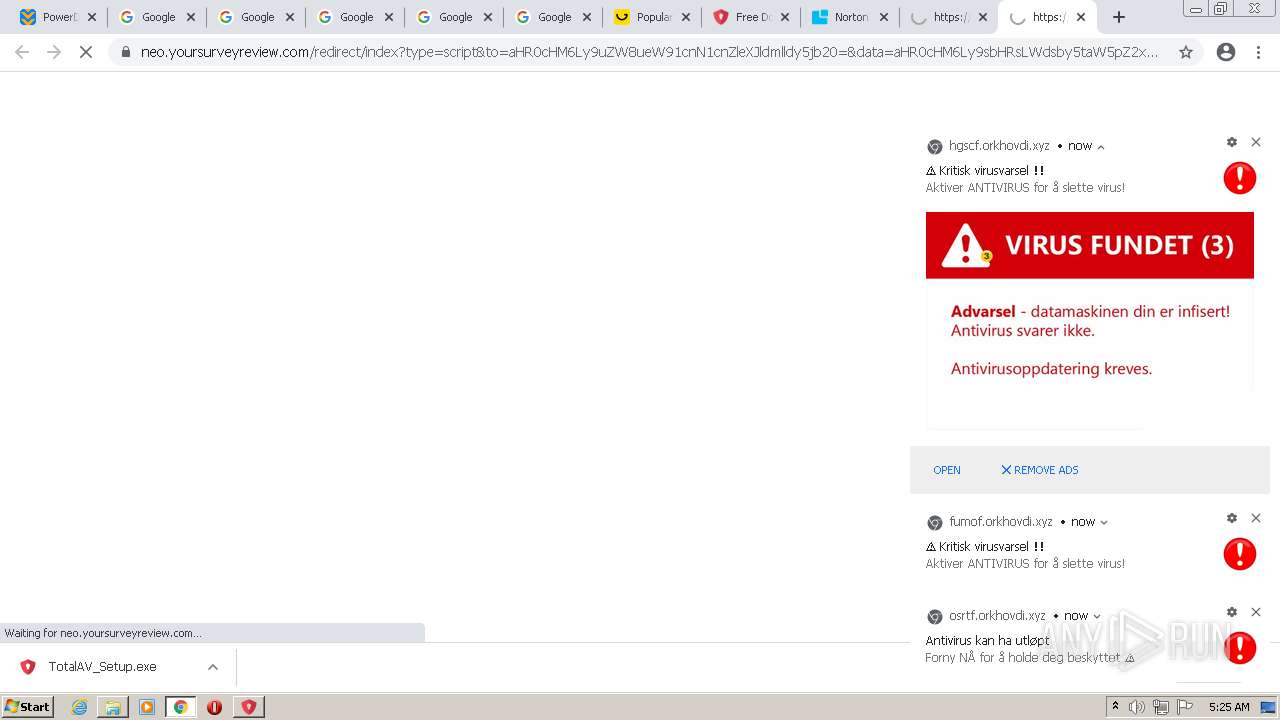
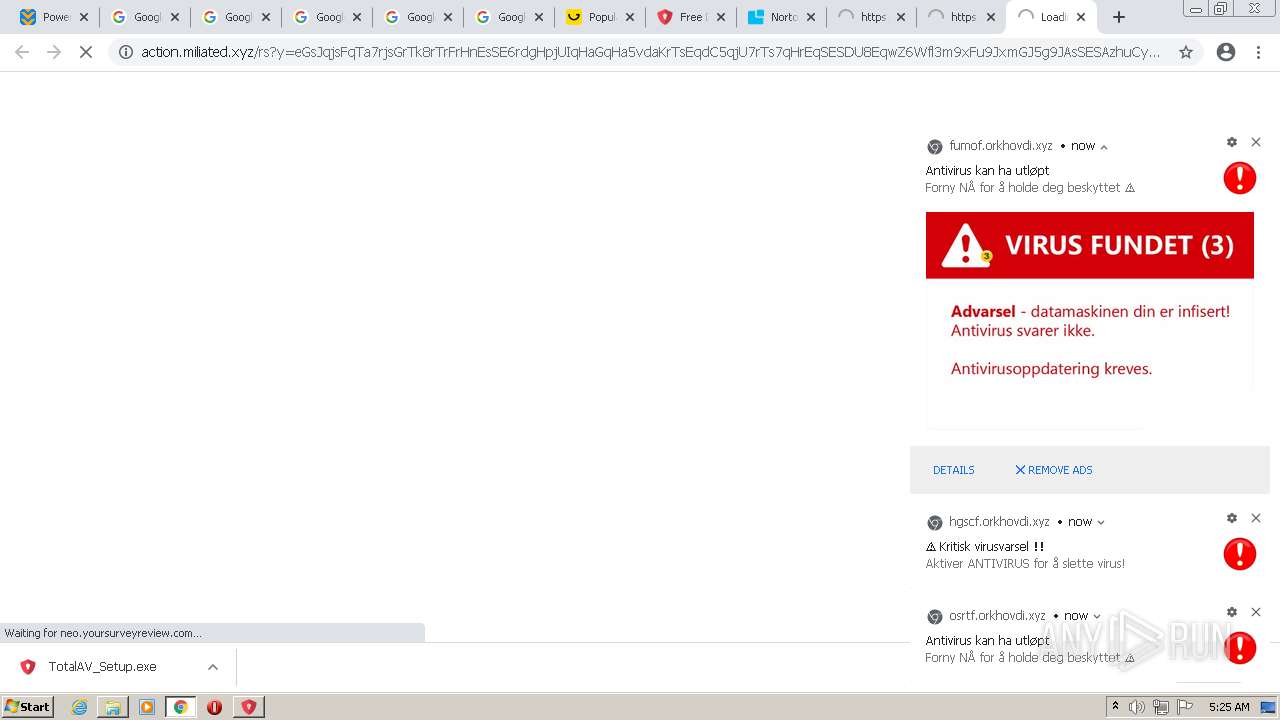
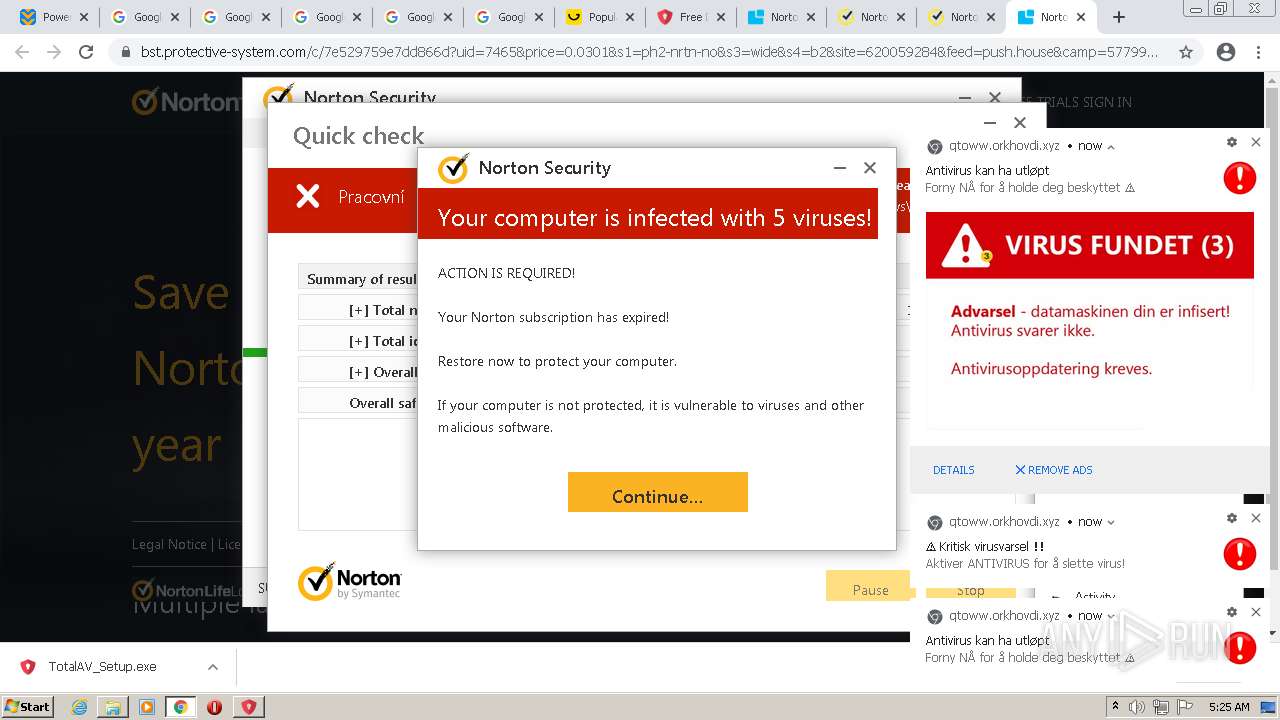
MALICIOUS
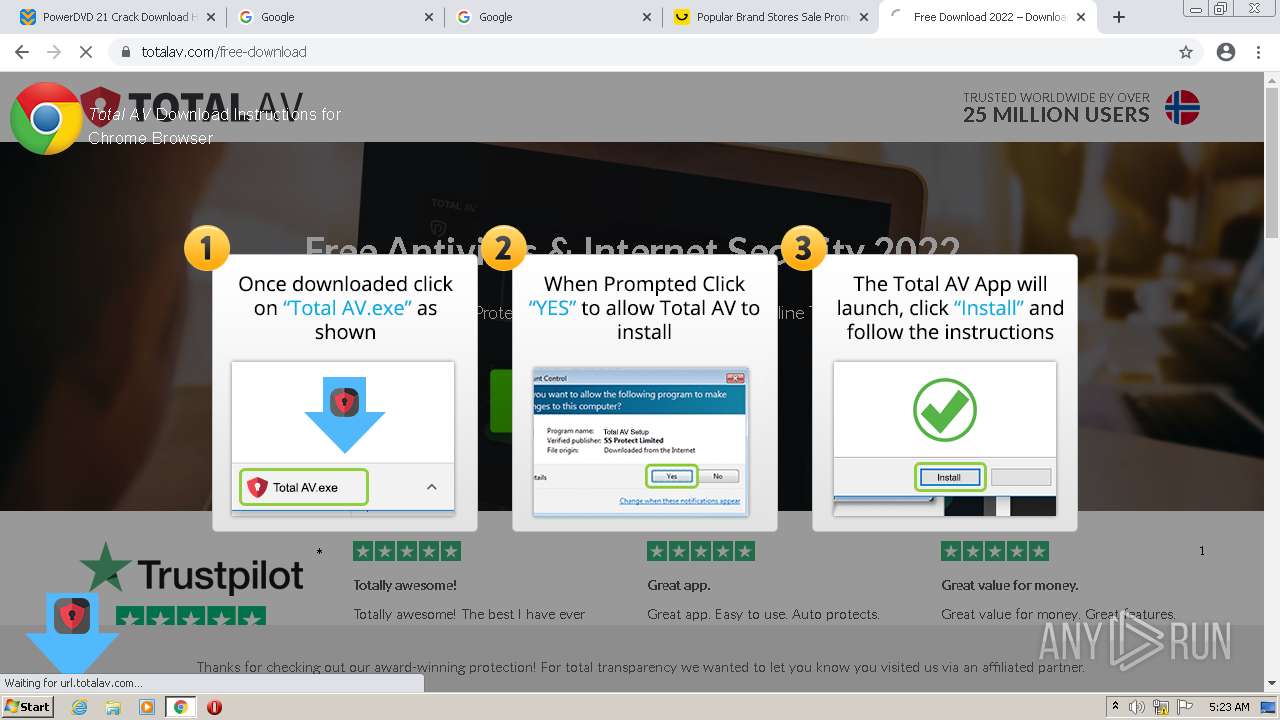
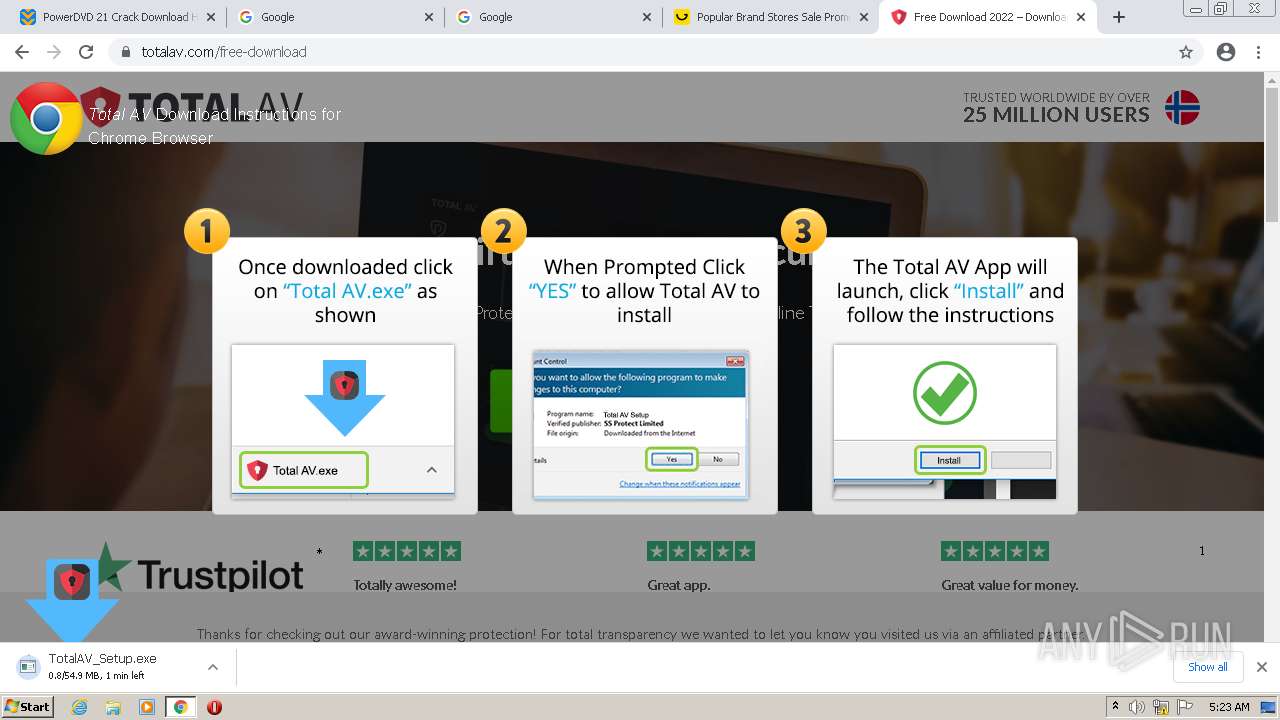
Drops executable file immediately after starts
- chrome.exe (PID: 2292)
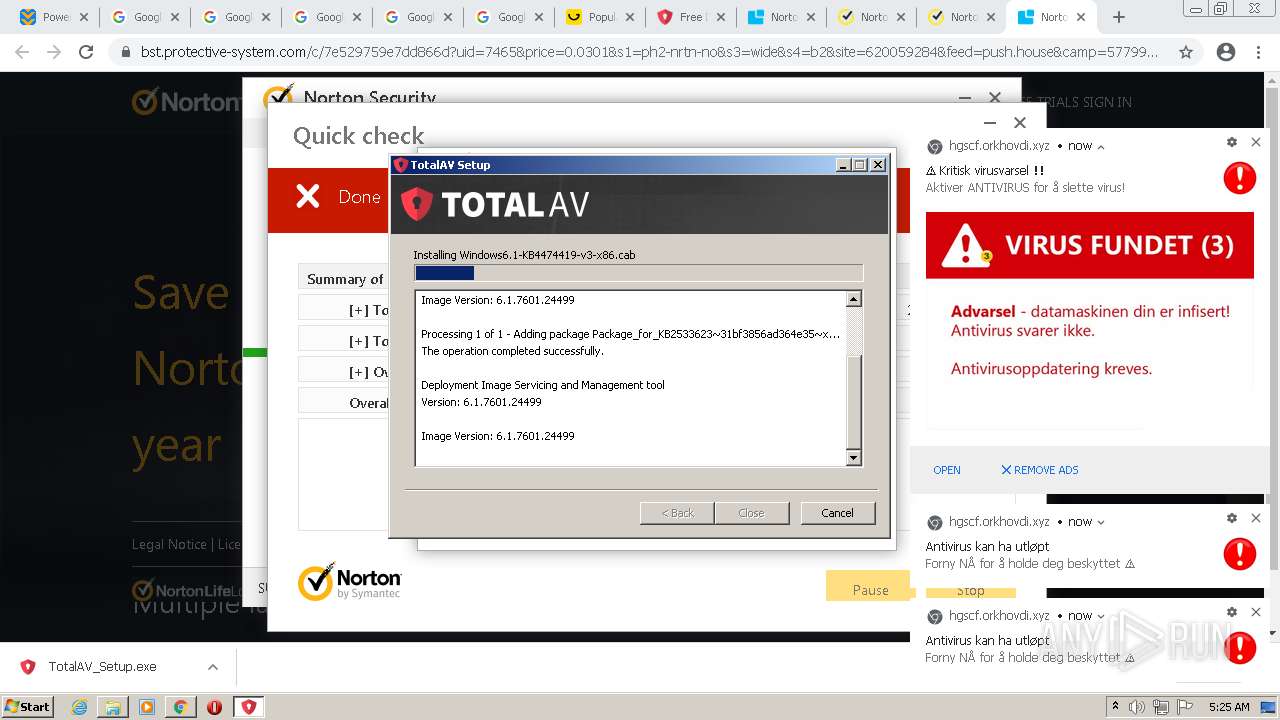
- TotalAV_Setup.exe (PID: 3884)
- Dism.exe (PID: 4036)
- Dism.exe (PID: 3508)
- Dism.exe (PID: 572)
- TotalAV_Setup.exe (PID: 3316)
- dism.exe (PID: 540)
Application was dropped or rewritten from another process
- dismhost.exe (PID: 3584)
- dismhost.exe (PID: 3760)
- dismhost.exe (PID: 992)
- dismhost.exe (PID: 1124)
- dismhost.exe (PID: 3560)
Loads dropped or rewritten executable
- TrustedInstaller.exe (PID: 1388)
- TotalAV_Setup.exe (PID: 3884)
- Dism.exe (PID: 3508)
- Dism.exe (PID: 4036)
- dismhost.exe (PID: 3584)
- Dism.exe (PID: 572)
- dismhost.exe (PID: 3760)
- dismhost.exe (PID: 992)
- Dism.exe (PID: 120)
- TotalAV_Setup.exe (PID: 3316)
- Dism.exe (PID: 3756)
- Dism.exe (PID: 2096)
- dism.exe (PID: 540)
- dismhost.exe (PID: 1124)
- dism.exe (PID: 2628)
- dismhost.exe (PID: 3560)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3492)
- chrome.exe (PID: 2292)
- TotalAV_Setup.exe (PID: 3884)
- Dism.exe (PID: 4036)
- Dism.exe (PID: 3508)
- Dism.exe (PID: 572)
- TotalAV_Setup.exe (PID: 3316)
- dism.exe (PID: 540)
- TrustedInstaller.exe (PID: 1388)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 2292)
- Dism.exe (PID: 4036)
- Dism.exe (PID: 3508)
- Dism.exe (PID: 572)
- dism.exe (PID: 540)
- TrustedInstaller.exe (PID: 1388)
Checks supported languages
- TotalAV_Setup.exe (PID: 3884)
- nsBA03.tmp (PID: 3772)
- cmd.exe (PID: 3236)
- dismhost.exe (PID: 3584)
- TrustedInstaller.exe (PID: 1388)
- nsD9F0.tmp (PID: 3364)
- cmd.exe (PID: 3988)
- dismhost.exe (PID: 3760)
- nsF25B.tmp (PID: 1588)
- cmd.exe (PID: 1188)
- TotalAV_Setup.exe (PID: 3316)
- ns7A6.tmp (PID: 1080)
- dismhost.exe (PID: 992)
- cmd.exe (PID: 2264)
- ns814.tmp (PID: 2084)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 2552)
- ns883.tmp (PID: 1612)
- nsFF6.tmp (PID: 3688)
- wmic.exe (PID: 3756)
- ns10C2.tmp (PID: 1308)
- ns1130.tmp (PID: 3696)
- ns119F.tmp (PID: 120)
- ns120D.tmp (PID: 328)
- ns4DFE.tmp (PID: 3112)
- dismhost.exe (PID: 1124)
- nsB7A6.tmp (PID: 2988)
- dismhost.exe (PID: 3560)
Reads the computer name
- TotalAV_Setup.exe (PID: 3884)
- dismhost.exe (PID: 3584)
- TrustedInstaller.exe (PID: 1388)
- dismhost.exe (PID: 992)
- TotalAV_Setup.exe (PID: 3316)
- dismhost.exe (PID: 3760)
- wmic.exe (PID: 3756)
- dismhost.exe (PID: 1124)
- dismhost.exe (PID: 3560)
Starts application with an unusual extension
- TotalAV_Setup.exe (PID: 3884)
- TotalAV_Setup.exe (PID: 3316)
Starts CMD.EXE for commands execution
- nsBA03.tmp (PID: 3772)
- nsD9F0.tmp (PID: 3364)
- nsF25B.tmp (PID: 1588)
- ns7A6.tmp (PID: 1080)
- ns814.tmp (PID: 2084)
- ns883.tmp (PID: 1612)
Drops a file with too old compile date
- Dism.exe (PID: 4036)
- Dism.exe (PID: 572)
- Dism.exe (PID: 3508)
- TotalAV_Setup.exe (PID: 3316)
- dism.exe (PID: 540)
Creates files in the Windows directory
- TrustedInstaller.exe (PID: 1388)
Removes files from Windows directory
- TrustedInstaller.exe (PID: 1388)
Uses TASKKILL.EXE to kill process
- ns10C2.tmp (PID: 1308)
- ns1130.tmp (PID: 3696)
- ns119F.tmp (PID: 120)
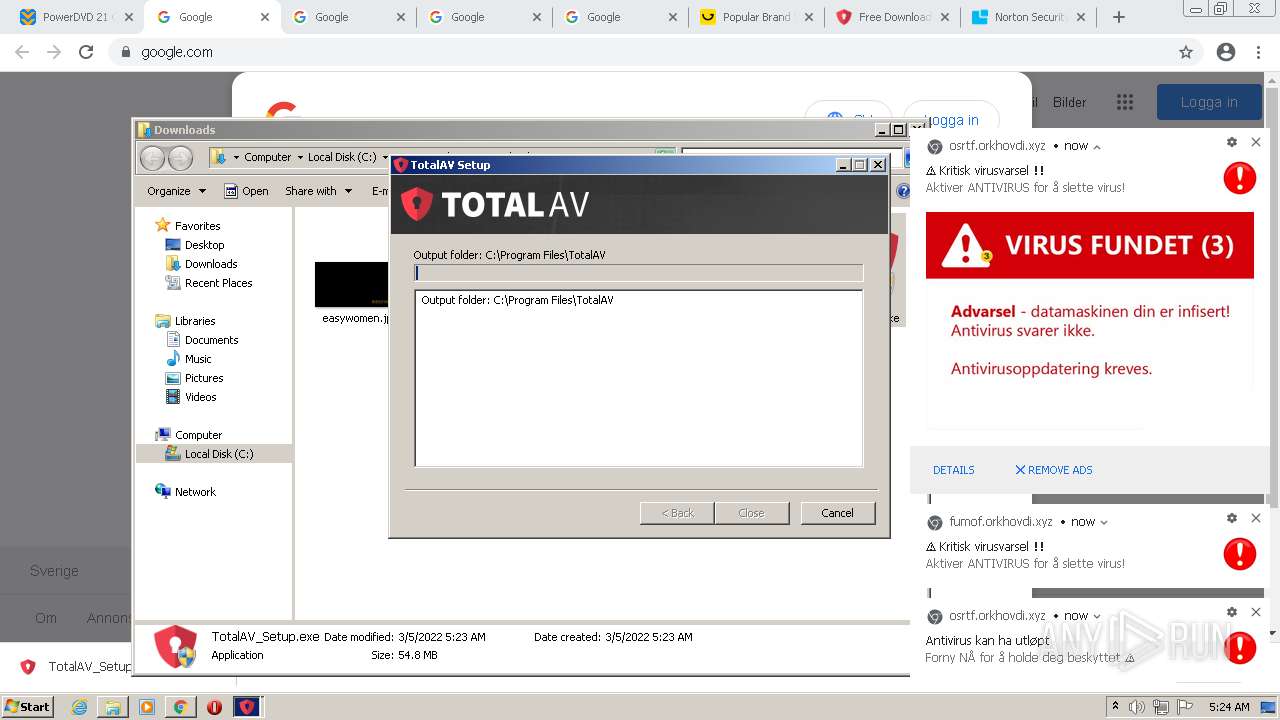
Creates a directory in Program Files
- TotalAV_Setup.exe (PID: 3316)
Executed as Windows Service
- vssvc.exe (PID: 3020)
Reads Environment values
- vssvc.exe (PID: 3020)
Executed via COM
- DllHost.exe (PID: 3360)
Searches for installed software
- DllHost.exe (PID: 3360)
- TrustedInstaller.exe (PID: 1388)
- TotalAV_Setup.exe (PID: 3316)
Creates files in the program directory
- TotalAV_Setup.exe (PID: 3316)
INFO
Checks supported languages
- chrome.exe (PID: 3492)
- chrome.exe (PID: 3616)
- chrome.exe (PID: 2496)
- chrome.exe (PID: 3768)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 1576)
- chrome.exe (PID: 2868)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 2396)
- chrome.exe (PID: 2676)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 2204)
- chrome.exe (PID: 3836)
- chrome.exe (PID: 3208)
- chrome.exe (PID: 656)
- chrome.exe (PID: 3216)
- chrome.exe (PID: 2592)
- chrome.exe (PID: 1576)
- chrome.exe (PID: 2260)
- chrome.exe (PID: 2392)
- chrome.exe (PID: 2732)
- chrome.exe (PID: 3108)
- chrome.exe (PID: 2096)
- chrome.exe (PID: 3744)
- chrome.exe (PID: 3144)
- chrome.exe (PID: 2800)
- chrome.exe (PID: 2596)
- chrome.exe (PID: 3840)
- chrome.exe (PID: 2248)
- chrome.exe (PID: 3736)
- chrome.exe (PID: 444)
- chrome.exe (PID: 440)
- chrome.exe (PID: 924)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 1768)
- chrome.exe (PID: 2600)
- chrome.exe (PID: 2640)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 2228)
- chrome.exe (PID: 3656)
- chrome.exe (PID: 3716)
- chrome.exe (PID: 1032)
- chrome.exe (PID: 3108)
- chrome.exe (PID: 3348)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 460)
- chrome.exe (PID: 1864)
- chrome.exe (PID: 3512)
- chrome.exe (PID: 1092)
- chrome.exe (PID: 3136)
- chrome.exe (PID: 2704)
- chrome.exe (PID: 3412)
- chrome.exe (PID: 3684)
- chrome.exe (PID: 2108)
- chrome.exe (PID: 540)
- chrome.exe (PID: 2420)
- chrome.exe (PID: 2260)
- chrome.exe (PID: 2180)
- chrome.exe (PID: 3320)
- chrome.exe (PID: 3636)
- chrome.exe (PID: 3108)
- chrome.exe (PID: 2292)
- Dism.exe (PID: 4036)
- findstr.exe (PID: 1068)
- findstr.exe (PID: 2924)
- Dism.exe (PID: 3508)
- Dism.exe (PID: 572)
- findstr.exe (PID: 1640)
- chrome.exe (PID: 2476)
- Dism.exe (PID: 120)
- findstr.exe (PID: 3208)
- Dism.exe (PID: 3756)
- Dism.exe (PID: 2096)
- findstr.exe (PID: 2392)
- findstr.exe (PID: 2888)
- taskkill.exe (PID: 2636)
- taskkill.exe (PID: 3136)
- chrome.exe (PID: 3364)
- vssvc.exe (PID: 3020)
- DllHost.exe (PID: 3360)
- chrome.exe (PID: 2516)
- dism.exe (PID: 540)
- chrome.exe (PID: 3760)
- chrome.exe (PID: 3808)
- chrome.exe (PID: 2184)
- chrome.exe (PID: 1148)
- chrome.exe (PID: 2208)
- chrome.exe (PID: 3328)
- chrome.exe (PID: 3956)
- chrome.exe (PID: 3784)
- chrome.exe (PID: 3984)
- chrome.exe (PID: 3604)
- dism.exe (PID: 2628)
- chrome.exe (PID: 3668)
- chrome.exe (PID: 404)
- chrome.exe (PID: 2888)
- chrome.exe (PID: 3988)
- chrome.exe (PID: 3172)
- chrome.exe (PID: 400)
- chrome.exe (PID: 3512)
- taskkill.exe (PID: 908)
- chrome.exe (PID: 3352)
- chrome.exe (PID: 1104)
- chrome.exe (PID: 632)
- chrome.exe (PID: 540)
- chrome.exe (PID: 3580)
- chrome.exe (PID: 2976)
Reads the hosts file
- chrome.exe (PID: 3616)
- chrome.exe (PID: 3492)
Reads the computer name
- chrome.exe (PID: 3492)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 3616)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 3208)
- chrome.exe (PID: 3144)
- chrome.exe (PID: 924)
- chrome.exe (PID: 2096)
- chrome.exe (PID: 3412)
- chrome.exe (PID: 2260)
- Dism.exe (PID: 4036)
- Dism.exe (PID: 3508)
- Dism.exe (PID: 572)
- Dism.exe (PID: 120)
- Dism.exe (PID: 3756)
- Dism.exe (PID: 2096)
- taskkill.exe (PID: 2636)
- taskkill.exe (PID: 3136)
- vssvc.exe (PID: 3020)
- taskkill.exe (PID: 908)
- DllHost.exe (PID: 3360)
- dism.exe (PID: 540)
- dism.exe (PID: 2628)
Reads settings of System Certificates
- chrome.exe (PID: 3616)
- chrome.exe (PID: 3492)
- TrustedInstaller.exe (PID: 1388)
Application launched itself
- chrome.exe (PID: 3492)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3492)
- TotalAV_Setup.exe (PID: 3884)
- TrustedInstaller.exe (PID: 1388)
Reads the date of Windows installation
- chrome.exe (PID: 3144)
Checks Windows Trust Settings
- chrome.exe (PID: 3492)
- TrustedInstaller.exe (PID: 1388)
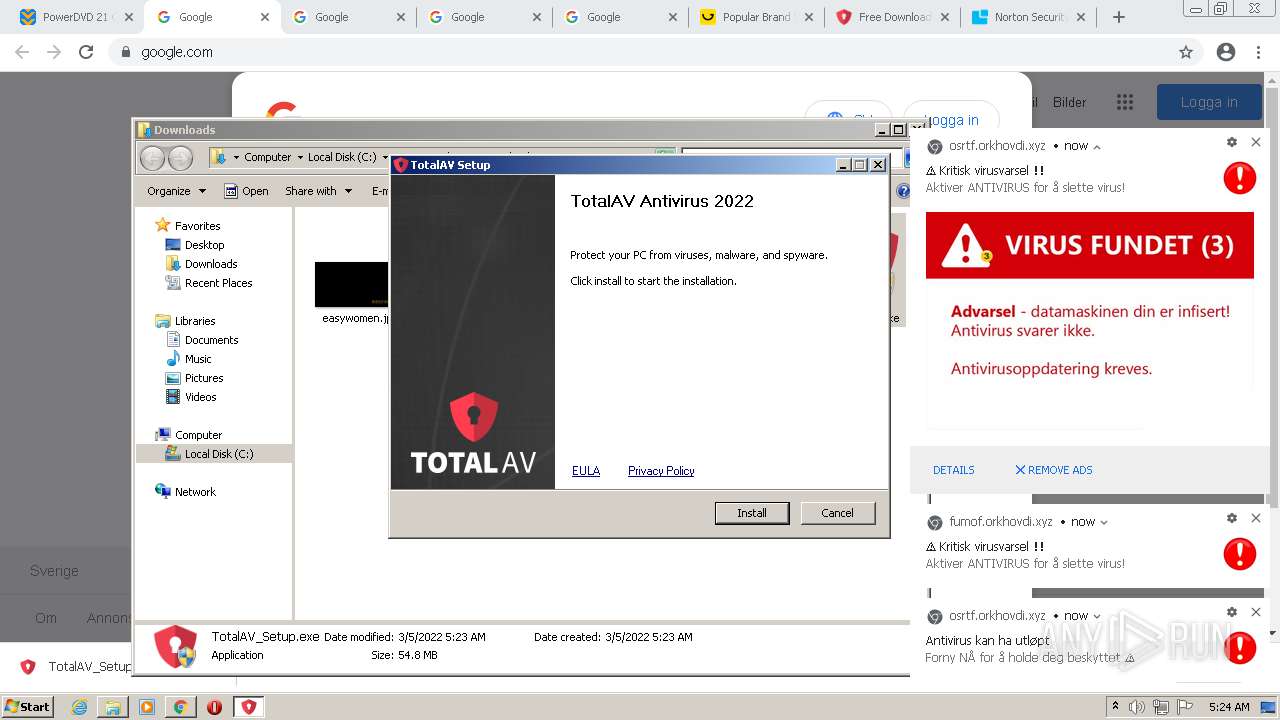
Manual execution by user
- TotalAV_Setup.exe (PID: 3504)
- TotalAV_Setup.exe (PID: 3884)
- TotalAV_Setup.exe (PID: 3316)
- TotalAV_Setup.exe (PID: 3624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
201
Monitored processes
137
Malicious processes
15
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
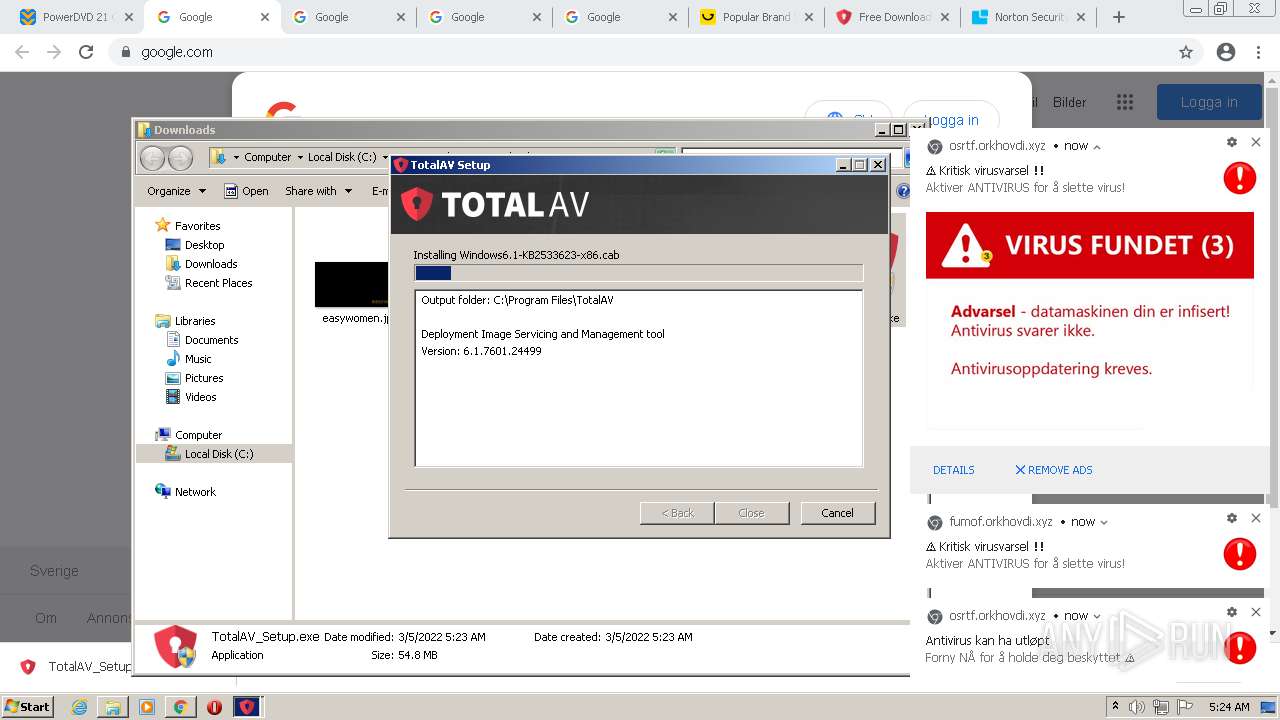
| 120 | dism.exe /online /get-packages | C:\Windows\system32\Dism.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Exit code: 183 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 120 | "C:\Users\admin\AppData\Local\Temp\nsb7A5.tmp\ns119F.tmp" "taskkill" /f /T /IM "PasswordExtension.Win.exe" | C:\Users\admin\AppData\Local\Temp\nsb7A5.tmp\ns119F.tmp | — | TotalAV_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 128 Modules
| |||||||||||||||
| 328 | "C:\Users\admin\AppData\Local\Temp\nsb7A5.tmp\ns120D.tmp" "C:\Program Files\TotalAV\SecurityService.exe" "--uninstall" "--for-install" | C:\Users\admin\AppData\Local\Temp\nsb7A5.tmp\ns120D.tmp | — | TotalAV_Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225501 Modules
| |||||||||||||||
| 400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=80 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5440 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=76 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3800 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3280 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3228 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=48 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2272 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,8488715243025668231,18249990012085048492,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=54 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3436 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
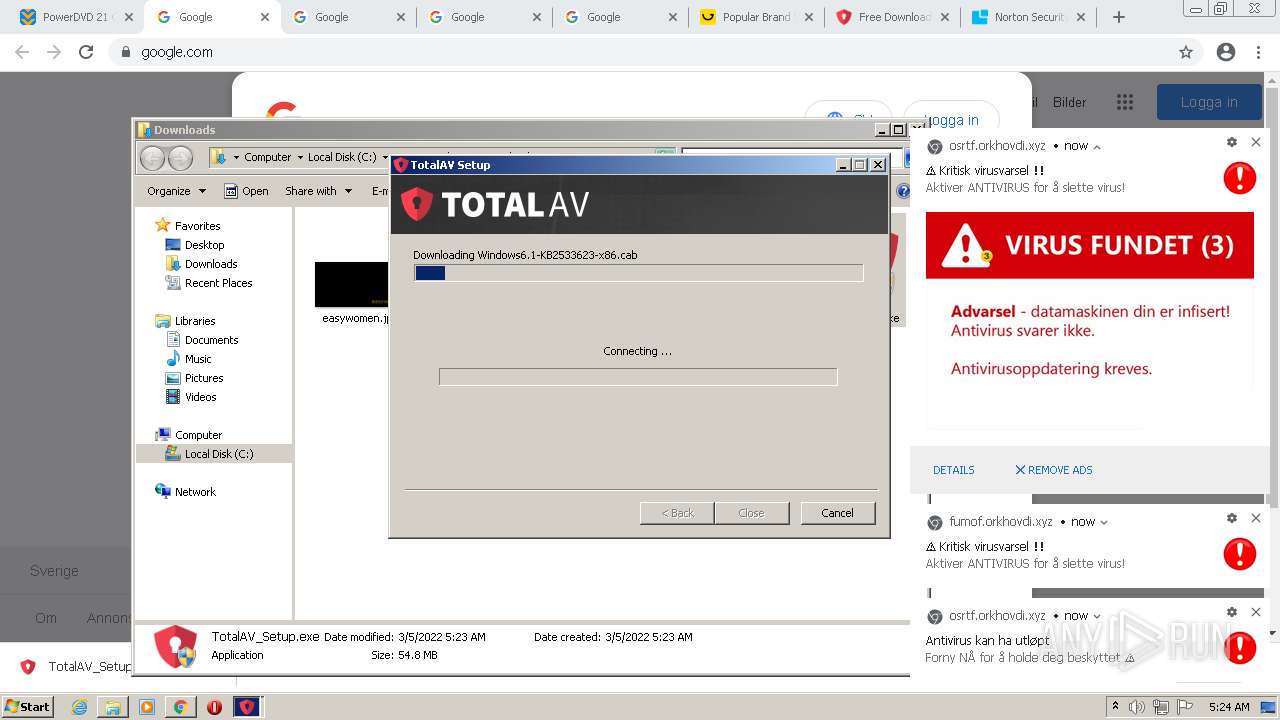
| 540 | "dism" /Online /Add-Package /PackagePath:C:\Users\admin\AppData\Local\Temp\Windows6.1-KB2533623-x86.cab /norestart | C:\Windows\system32\dism.exe | ns4DFE.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
91 290
Read events
88 895
Write events
2 161
Delete events
234
Modification events
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3492) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
405
Suspicious files
152
Text files
1 199
Unknown types
51
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-6222F384-DA4.pma | — | |
MD5:— | SHA256:— | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\cf7c05d3-93e9-4bf1-bdf4-64c278bb4a50.tmp | text | |
MD5:— | SHA256:— | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RFe29fa.TMP | text | |
MD5:81F483F77EE490F35306A4F94DB2286B | SHA256:82434CE3C9D13F509EBEEBE3A7A1A1DE9AB4557629D9FC855761E0CFA45E8BCE | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\f4520f01-1d16-4b63-b1da-7905e08894e0.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extension State\LOG.old~RFe312d.TMP | text | |
MD5:D097F8EB2230B3F32C41C5D75790508C | SHA256:ADDF87D20CD455CFB4AACB6B76719629C0277A4CF70B496343047BB73ABBAEF5 | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Extension Settings\pkedcjkdefgpdelpbcmbmeomcjbeemfm\LOG.old~RFe2d55.TMP | text | |
MD5:D0BA19096D6C8F8DE58312E8D938E893 | SHA256:AADE90A7B0984F3C719D528E4E6FAE3854E28B30363BDD4DF65037E69784A078 | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFe29ea.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 3492 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
63
TCP/UDP connections
281
DNS requests
153
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
872 | svchost.exe | HEAD | 302 | 142.250.185.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTVkQUFYWTN2V0pFMl9rR2VLalMxS0pyZw/1.0.0.12_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
872 | svchost.exe | HEAD | 200 | 173.194.150.217:80 | http://r3---sn-5goeen7r.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw?cms_redirect=yes&mh=LV&mip=45.92.228.76&mm=28&mn=sn-5goeen7r&ms=nvh&mt=1646457380&mv=m&mvi=3&pl=24&rmhost=r5---sn-5goeen7r.gvt1.com&shardbypass=yes&smhost=r2---sn-5goeen7k.gvt1.com | US | — | — | whitelisted |
872 | svchost.exe | HEAD | 302 | 142.250.185.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | html | 593 b | whitelisted |
872 | svchost.exe | GET | 302 | 142.250.185.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | html | 540 b | whitelisted |
872 | svchost.exe | GET | 302 | 142.250.185.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | html | 540 b | whitelisted |
3616 | chrome.exe | GET | 200 | 178.79.242.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a0757494316afd8b | DE | compressed | 59.5 Kb | whitelisted |
872 | svchost.exe | GET | 302 | 142.250.185.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | html | 540 b | whitelisted |
872 | svchost.exe | GET | 302 | 142.250.185.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | html | 540 b | whitelisted |
3616 | chrome.exe | GET | 200 | 178.79.242.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?70e9d0484a775b31 | DE | compressed | 59.5 Kb | whitelisted |
872 | svchost.exe | GET | 200 | 74.125.110.136:80 | http://r3---sn-5goeen7y.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTVkQUFYWTN2V0pFMl9rR2VLalMxS0pyZw/1.0.0.12_llkgjffcdpffmhiakmfcdcblohccpfmo.crx?cms_redirect=yes&mh=8_&mip=45.92.228.76&mm=28&mn=sn-5goeen7y&ms=nvh&mt=1646457380&mv=m&mvi=3&pl=24&rmhost=r2---sn-5goeen7y.gvt1.com&shardbypass=yes&smhost=r6---sn-5goeen76.gvt1.com | US | crx | 2.84 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3616 | chrome.exe | 142.250.186.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
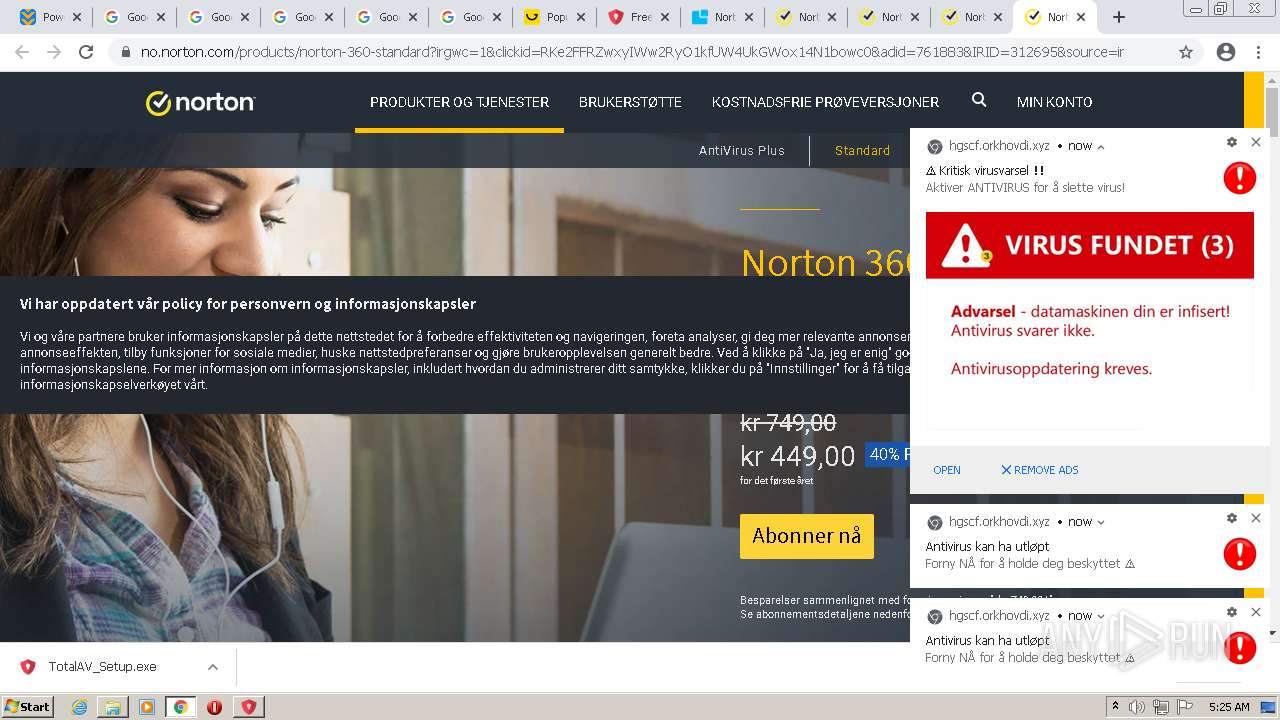
3616 | chrome.exe | 142.250.186.77:443 | accounts.google.com | Google Inc. | US | suspicious |
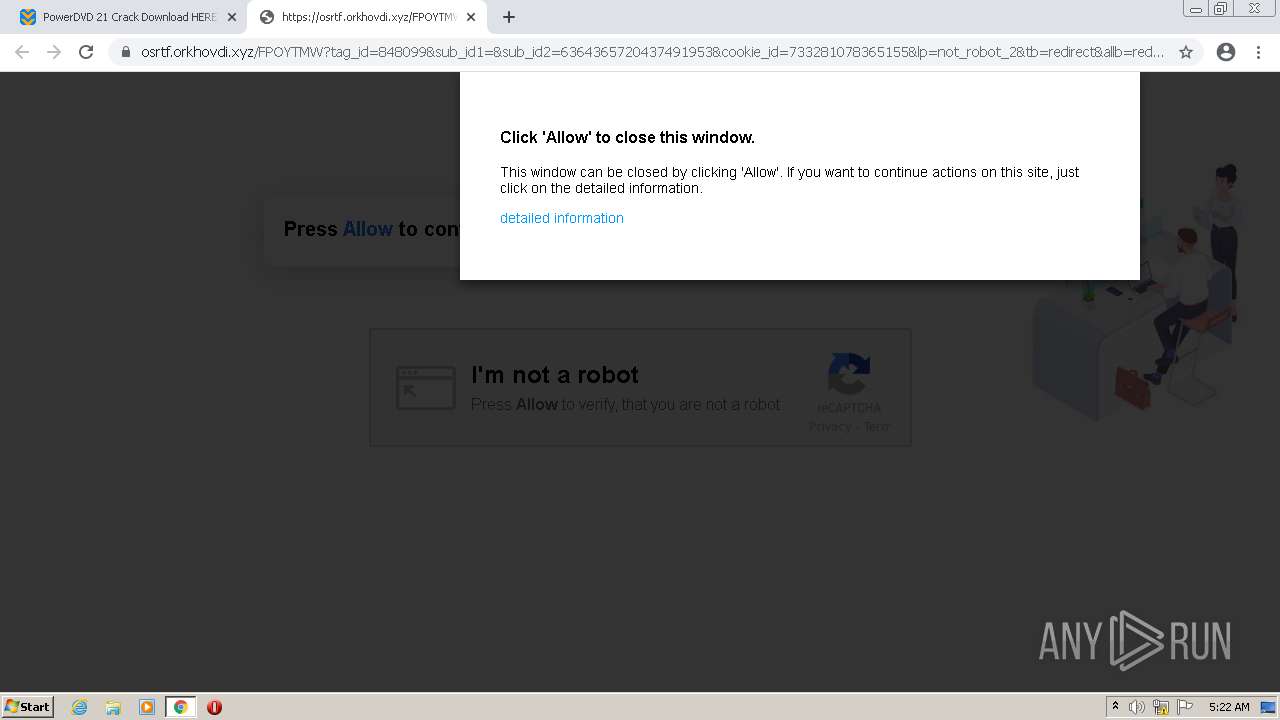
3616 | chrome.exe | 104.21.8.28:443 | www.cracksoftsite.com | Cloudflare Inc | US | suspicious |
3616 | chrome.exe | 13.225.84.130:443 | ds88pc0kw6cvc.cloudfront.net | — | US | unknown |
3616 | chrome.exe | 142.250.184.200:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3616 | chrome.exe | 192.0.77.37:443 | c0.wp.com | Automattic, Inc | US | suspicious |
3616 | chrome.exe | 99.86.7.99:443 | gfruitiesm.com | AT&T Services, Inc. | US | suspicious |
3616 | chrome.exe | 142.250.186.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3616 | chrome.exe | 216.58.212.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3616 | chrome.exe | 192.0.77.2:443 | i0.wp.com | Automattic, Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
www.cracksoftsite.com |
| malicious |
c0.wp.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ds88pc0kw6cvc.cloudfront.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
stats.wp.com |
| whitelisted |
s.w.org |
| whitelisted |
i0.wp.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3616 | chrome.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
— | — | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3316 | TotalAV_Setup.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
3316 | TotalAV_Setup.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
Process | Message |
|---|---|
Dism.exe | PID=4036 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=4036 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=4036 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=4036 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=4036 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=4036 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
Dism.exe | PID=4036 Getting Provider OSServices - CDISMProviderStore::GetProvider |
Dism.exe | PID=4036 The requested provider was not found in the Provider Store. - CDISMProviderStore::Internal_GetProvider(hr:0x80004005) |
Dism.exe | PID=4036 Failed to get an OSServices provider. Must be running in local store. Falling back to checking alongside the log provider for wdscore.dll. - CDISMLogger::FindWdsCore(hr:0x80004005) |
dismhost.exe | PID=3584 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |