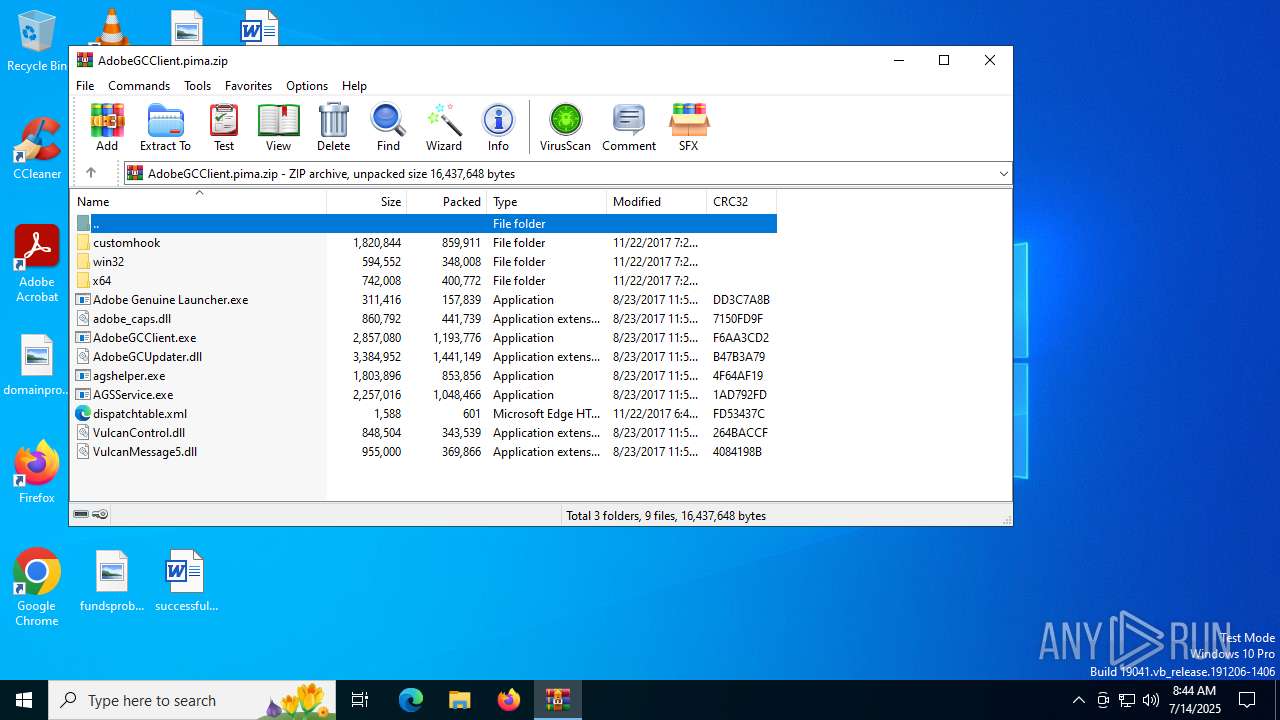
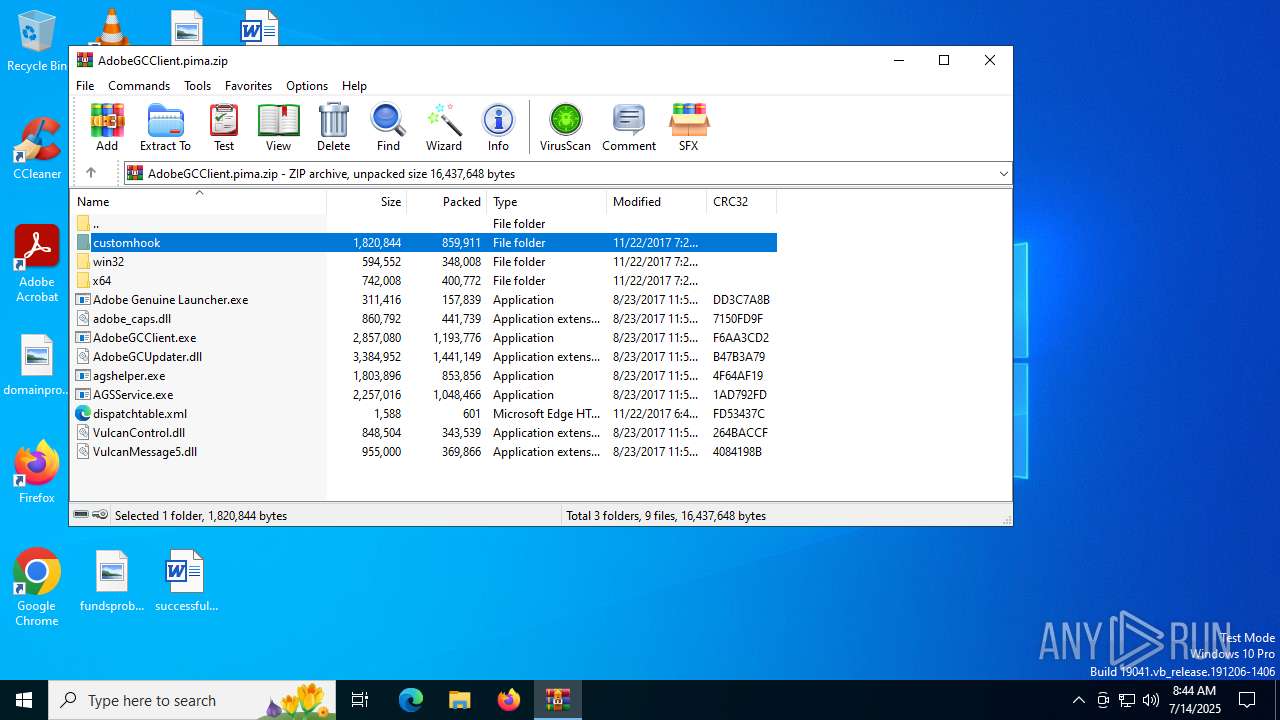
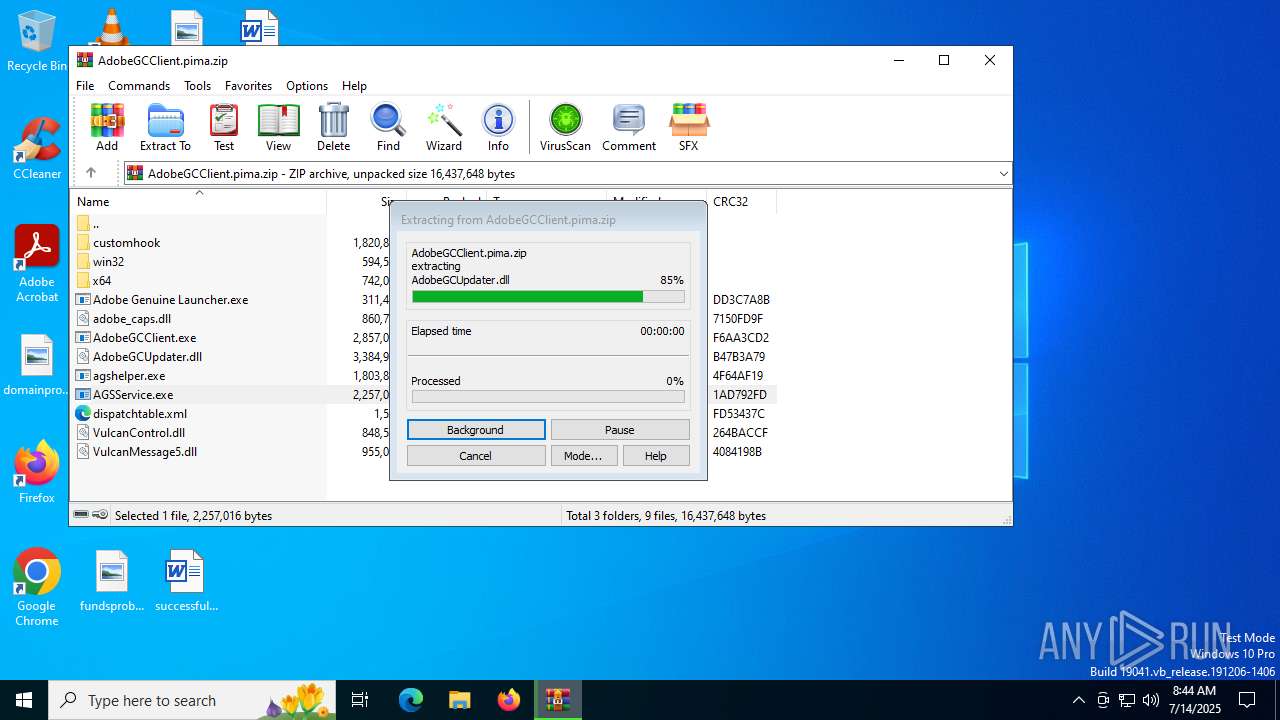
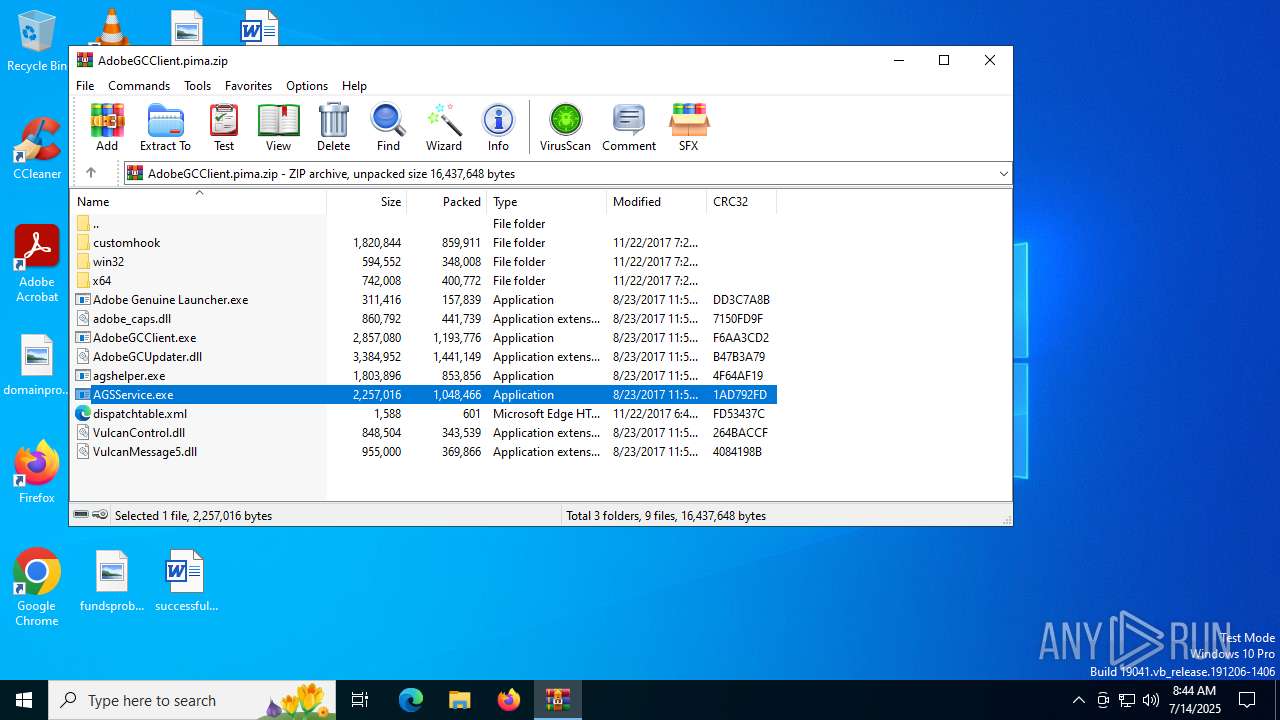
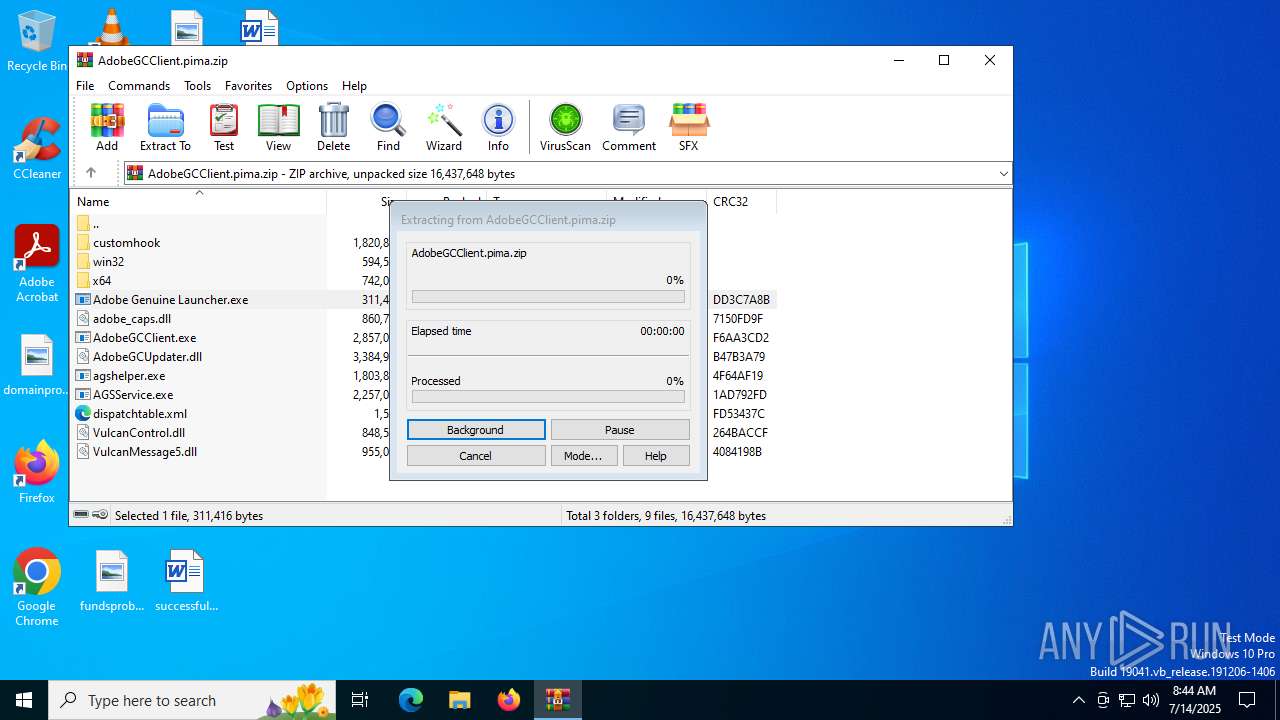
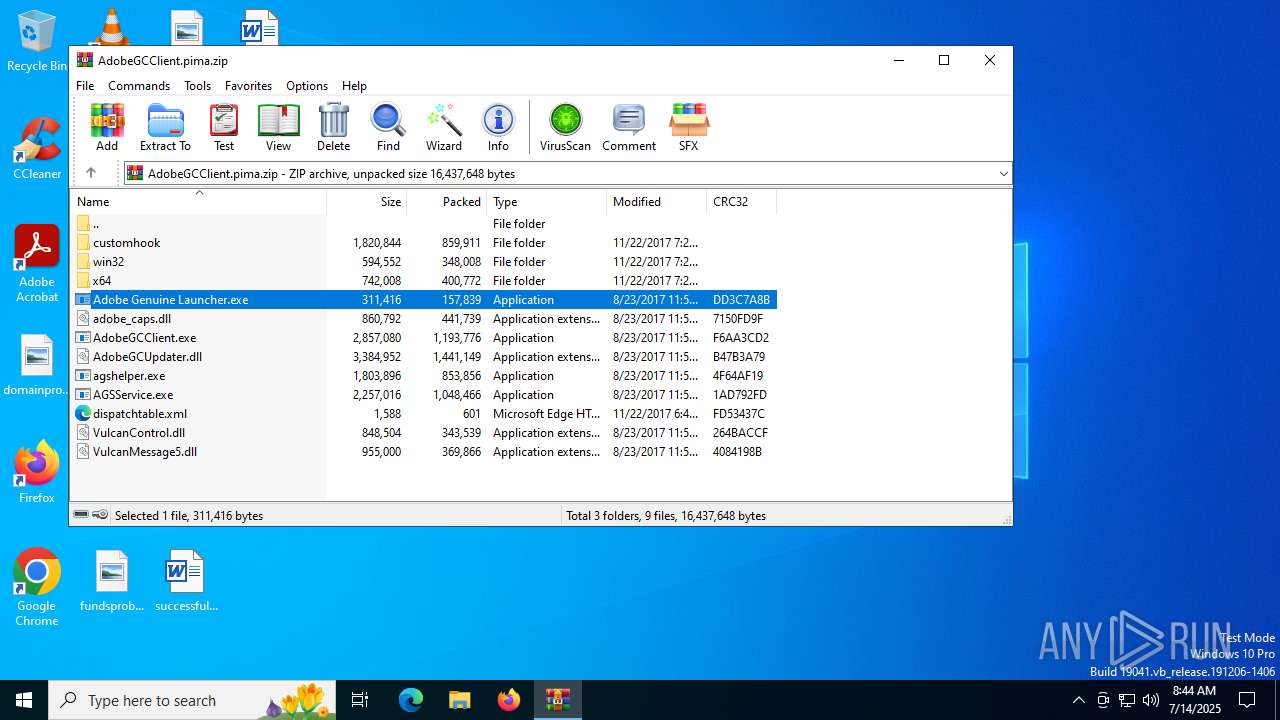
| File name: | AdobeGCClient.pima |
| Full analysis: | https://app.any.run/tasks/313262d9-c827-4129-ac21-8caf785f3ab2 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2025, 08:43:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B370D860A5F839D6A5598560433F4A39 |
| SHA1: | 47C882D34EDD3E6B0A2DE037D180FDA41189F9BE |
| SHA256: | AD8C3E619214DED7EF364C01F0EFBEC5617A9D343BD8A29F1E91F04D0E2BC847 |
| SSDEEP: | 98304:TZhtiO16ec/Dz+pnMgVFZQe983mh4oFbDq5NavCyFXpBNy/r9sxUQukeLo0LlTJH:QjRE7yCVUERBOn1x |
MALICIOUS
Executing a file with an untrusted certificate
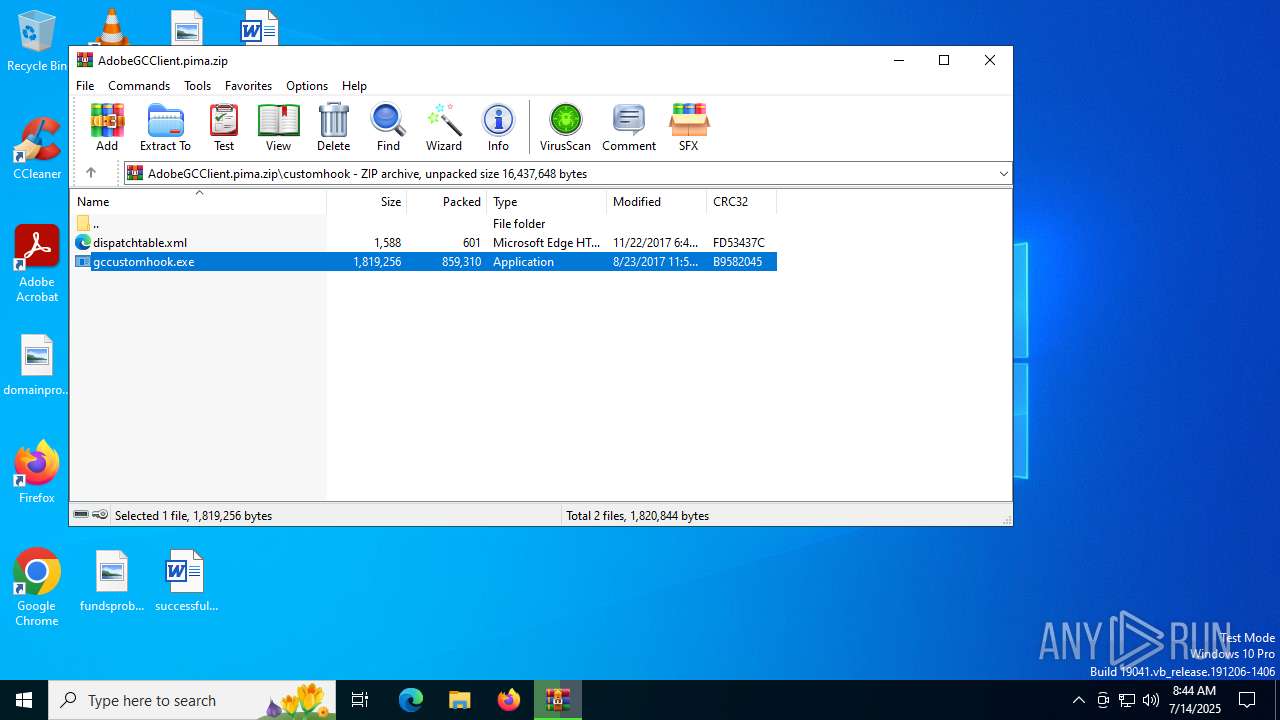
- gccustomhook.exe (PID: 3736)
- AGSService.exe (PID: 6260)
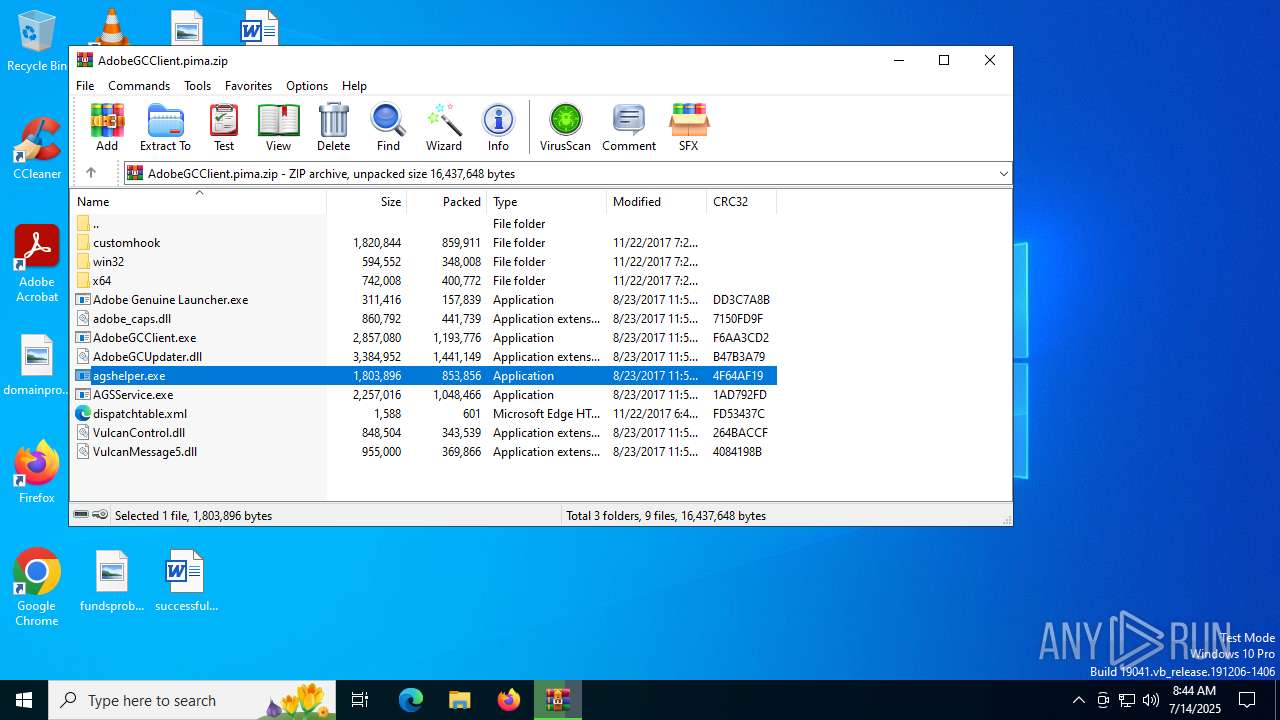
- agshelper.exe (PID: 1984)
- agshelper.exe (PID: 1036)
- Adobe Genuine Launcher.exe (PID: 7160)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1332)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1332)
The sample compiled with english language support
- WinRAR.exe (PID: 1332)
Create files in a temporary directory
- gccustomhook.exe (PID: 3736)
Checks supported languages
- gccustomhook.exe (PID: 3736)
- AGSService.exe (PID: 6260)
- agshelper.exe (PID: 1036)
- agshelper.exe (PID: 1984)
- Adobe Genuine Launcher.exe (PID: 7160)
Reads the computer name
- gccustomhook.exe (PID: 3736)
- agshelper.exe (PID: 1036)
- AGSService.exe (PID: 6260)
- agshelper.exe (PID: 1984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2017:08:23 11:51:36 |
| ZipCRC: | 0xdd3c7a8b |
| ZipCompressedSize: | 157839 |
| ZipUncompressedSize: | 311416 |
| ZipFileName: | Adobe Genuine Launcher.exe |
Total processes
146
Monitored processes
10
Malicious processes
1
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AGSService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.47718\agshelper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.47718\agshelper.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Adobe Systems, Incorporated Integrity Level: MEDIUM Description: AGS Helper Exit code: 0 Version: 4.4.0.652 Modules
| |||||||||||||||
| 1180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | agshelper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\AdobeGCClient.pima.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1984 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.47538\agshelper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.47538\agshelper.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Adobe Systems, Incorporated Integrity Level: MEDIUM Description: AGS Helper Exit code: 0 Version: 4.4.0.652 Modules
| |||||||||||||||
| 3704 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | agshelper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3736 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\customhook\gccustomhook.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\customhook\gccustomhook.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Adobe Systems, Incorporated Integrity Level: MEDIUM Description: Adobe GC Custom Hook Exit code: 0 Version: 4.4.0.652 Modules
| |||||||||||||||
| 4444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Adobe Genuine Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6260 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.47854\AGSService.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.47854\AGSService.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Adobe Systems, Incorporated Integrity Level: MEDIUM Description: Adobe Genuine Software Integrity Service Exit code: 0 Version: 4.4.0.652 Modules
| |||||||||||||||
| 7160 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.48175\Adobe Genuine Launcher.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.48175\Adobe Genuine Launcher.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Adobe Systems, Incorporated Integrity Level: MEDIUM Description: Adobe Genuine Launch Utility Exit code: 0 Version: 4.4.0.652 Modules
| |||||||||||||||
Total events
3 558
Read events
3 549
Write events
9
Delete events
0
Modification events
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AdobeGCClient.pima.zip | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Viewer |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3400000034000000F40300001D020000 | |||
Executable files
56
Suspicious files
0
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\VulcanMessage5.dll | executable | |
MD5:0F163233A44EE2F35C25DA149CD912C1 | SHA256:EA4DBD953A7EE702D296B3BD4F95B6AB56588A08040B7E0085518B38EE48BF76 | |||
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\adobe_caps.dll | executable | |
MD5:A7F6D47426E55F4695809261D02C4958 | SHA256:B1B91F6BCE976B2D93F1656FF9BB0F127BD7D66FE957C653ABB2DB04FDF00696 | |||
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\Adobe Genuine Launcher.exe | executable | |
MD5:8B99569B72F1828C8EEE062442C88A79 | SHA256:3FC4C11A1764875514F325C5C160D92E93CEBD9FBF7DE260ABE226AF6F71C333 | |||
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\agshelper.exe | executable | |
MD5:FD17012F293F21092982E66E68952E70 | SHA256:80E85013FA2441849DA9FECD8819084C8DD790AF2674871E95A06FC51125BCA3 | |||
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\VulcanControl.dll | executable | |
MD5:80F52DEDBB46457137F688A6FAFECD10 | SHA256:E28BED411003A175560AFDBD1889CFD569A093661092B4A22E06BCF058543C7E | |||
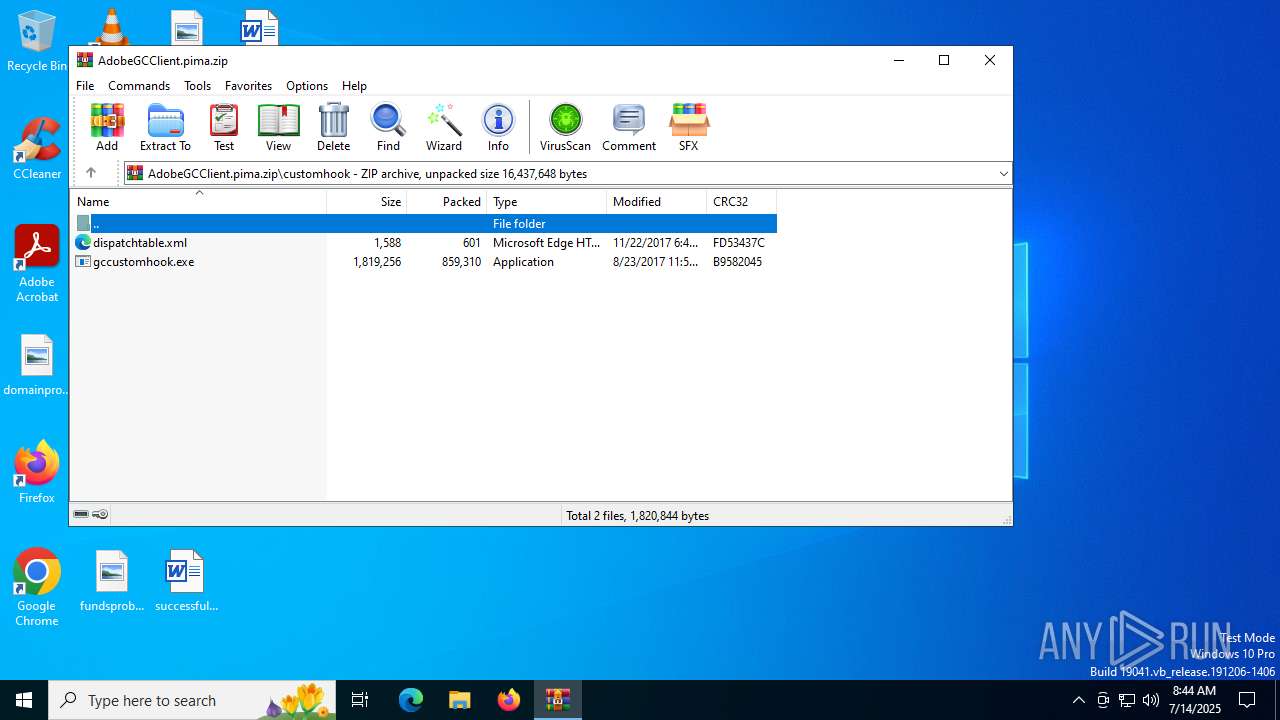
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\customhook\dispatchtable.xml | xml | |
MD5:B7ABE6BC7E8052FB65FE589109759875 | SHA256:39CEACFE40CA59FA66A03B1821A845D0D1602BA8FE441BDCEAC6F8258465D6AF | |||
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\dispatchtable.xml | xml | |
MD5:B7ABE6BC7E8052FB65FE589109759875 | SHA256:39CEACFE40CA59FA66A03B1821A845D0D1602BA8FE441BDCEAC6F8258465D6AF | |||
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\AGSService.exe | executable | |
MD5:0677F5ECD4F801403C428BBAE1286379 | SHA256:55E5C62253CA4E788815E3076CEE6FA55EDFED576DAC0210F5F58D84EAD4FA35 | |||
| 3736 | gccustomhook.exe | C:\Users\admin\AppData\Local\Temp\adobegc.log | text | |
MD5:ECAA88F7FA0BF610A5A26CF545DCD3AA | SHA256:F1945CD6C19E56B3C1C78943EF5EC18116907A4CA1EFC40A57D48AB1DB7ADFC5 | |||
| 1332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1332.46625\x64\gcsqlitewrapper.dll | executable | |
MD5:60A85B85D80BDC0246FD1C9190F9C9FD | SHA256:09B41D046B779EE97CB358DA0921B37FB4693A8BDB01F933E685774114E3CBED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4320 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2512 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2512 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5104 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4320 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4320 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |