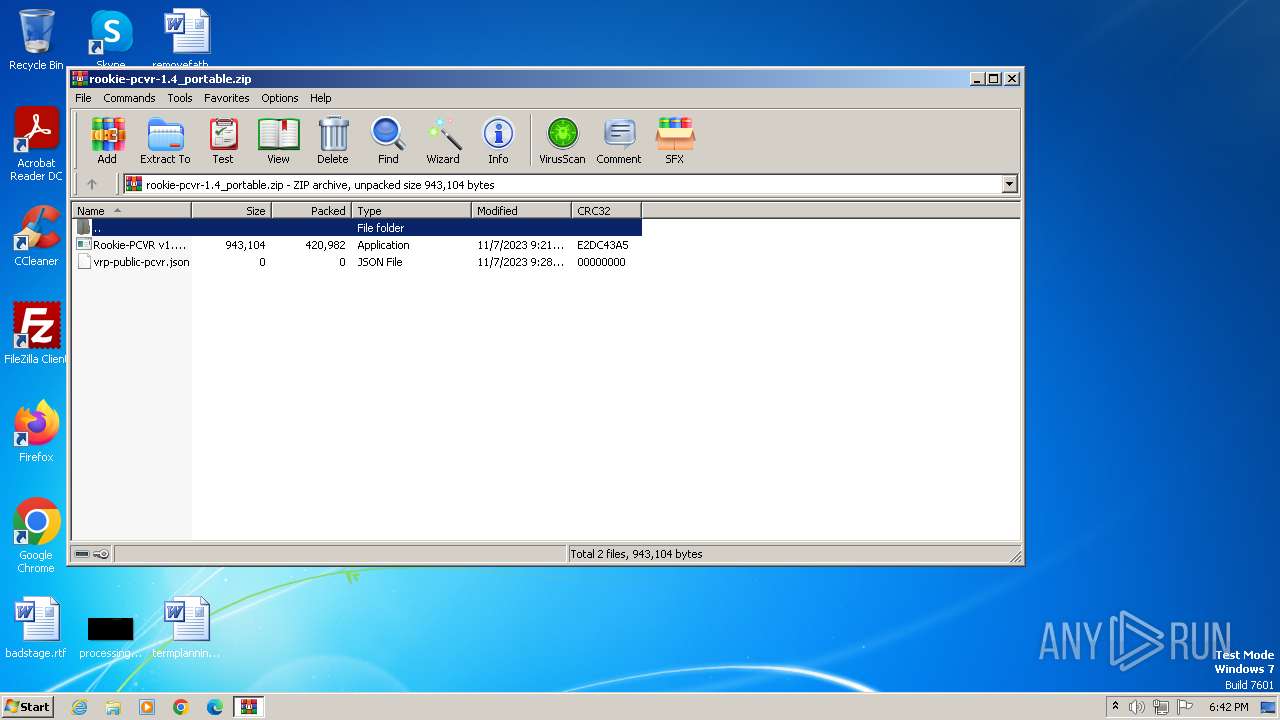
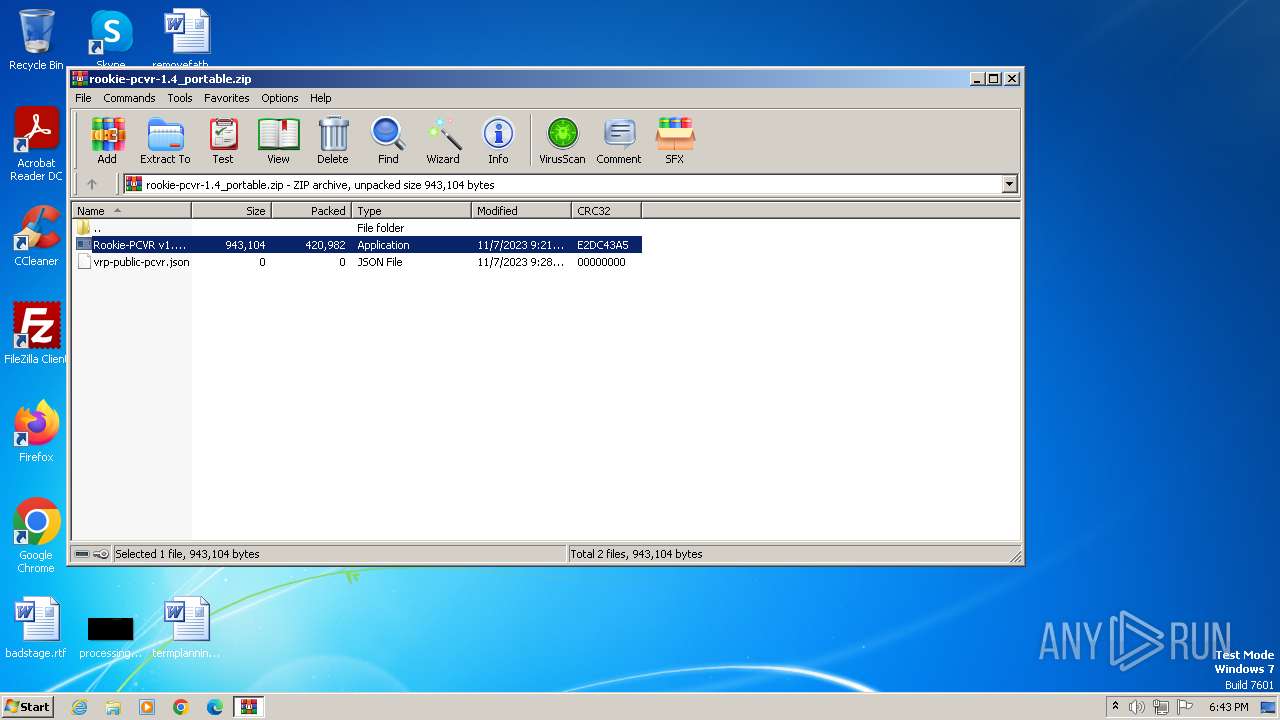
| File name: | rookie-pcvr-1.4_portable.zip |
| Full analysis: | https://app.any.run/tasks/df91d619-ed20-4819-9500-a09baafc192f |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2023, 18:42:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B1E9D348CA73E6E06CF57F64EB59A67D |
| SHA1: | 33E4F9C8F095587951BE0AF068EF407CA666AFE4 |
| SHA256: | AD7802BCD8894EB767D2A325E95B8C10528CDDC0250E88874A0464C1D3D1B397 |
| SSDEEP: | 12288:gOjUZC2evVTSUjphx7OP+s0L4Y97aa8PGy6SnIOmFWTwXTHc:gOjUZC7vVTSUj/x7OP+s0kY9B8PGy6zw |
MALICIOUS
Drops the executable file immediately after the start
- Rookie-PCVR v1.4.exe (PID: 2896)
SUSPICIOUS
Reads settings of System Certificates
- Rookie-PCVR v1.4.exe (PID: 2896)
- PCVR-Rookie v1.4.exe (PID: 3644)
- rclone.exe (PID: 3964)
Reads the Internet Settings
- Rookie-PCVR v1.4.exe (PID: 2896)
- PCVR-Rookie v1.4.exe (PID: 3644)
Drops 7-zip archiver for unpacking
- Rookie-PCVR v1.4.exe (PID: 2896)
Starts CMD.EXE for commands execution
- Rookie-PCVR v1.4.exe (PID: 2896)
Adds/modifies Windows certificates
- PCVR-Rookie v1.4.exe (PID: 3644)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3372)
Checks supported languages
- Rookie-PCVR v1.4.exe (PID: 2896)
- 7z.exe (PID: 3276)
- rclone.exe (PID: 3736)
- rclone.exe (PID: 3964)
- 7z.exe (PID: 3536)
- PCVR-Rookie v1.4.exe (PID: 3644)
Reads the computer name
- Rookie-PCVR v1.4.exe (PID: 2896)
- 7z.exe (PID: 3276)
- PCVR-Rookie v1.4.exe (PID: 3644)
- rclone.exe (PID: 3736)
- rclone.exe (PID: 3964)
- 7z.exe (PID: 3536)
Reads the machine GUID from the registry
- Rookie-PCVR v1.4.exe (PID: 2896)
- rclone.exe (PID: 3964)
- PCVR-Rookie v1.4.exe (PID: 3644)
Reads Environment values
- Rookie-PCVR v1.4.exe (PID: 2896)
- PCVR-Rookie v1.4.exe (PID: 3644)
Creates files or folders in the user directory
- Rookie-PCVR v1.4.exe (PID: 2896)
- PCVR-Rookie v1.4.exe (PID: 3644)
Create files in a temporary directory
- 7z.exe (PID: 3276)
- Rookie-PCVR v1.4.exe (PID: 2896)
- rclone.exe (PID: 3964)
- PCVR-Rookie v1.4.exe (PID: 3644)
- 7z.exe (PID: 3536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:07 15:21:02 |
| ZipCRC: | 0xe2dc43a5 |
| ZipCompressedSize: | 420982 |
| ZipUncompressedSize: | 943104 |
| ZipFileName: | Rookie-PCVR v1.4.exe |
Total processes
47
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2896 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\Rookie-PCVR v1.4.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\Rookie-PCVR v1.4.exe | WinRAR.exe | ||||||||||||
User: admin Company: Rookie.WTF Integrity Level: MEDIUM Description: AndroidSideloader Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 3276 | "7z.exe" x "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\rclone.zip" -y -o"C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\7z.exe | — | Rookie-PCVR v1.4.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 3372 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\rookie-pcvr-1.4_portable.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3536 | "7z.exe" x "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\meta.7z" -y -o"C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\meta" -p"gL59VfgPxoHR" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\7z.exe | — | PCVR-Rookie v1.4.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 3644 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\PCVR-Rookie v1.4.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\PCVR-Rookie v1.4.exe | Rookie-PCVR v1.4.exe | ||||||||||||
User: admin Company: Rookie.WTF Integrity Level: MEDIUM Description: AndroidSideloader Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 3736 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\rclone\rclone.exe" listremotes --config vrp.download.config | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\rclone\rclone.exe | — | PCVR-Rookie v1.4.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rsync for cloud storage Exit code: 0 Version: 1.62.2 Modules
| |||||||||||||||
| 3756 | "C:\Windows\System32\cmd.exe" /C choice /C Y /N /D Y /T 5 & Del "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\Rookie-PCVR v1.4.exe" | C:\Windows\System32\cmd.exe | — | Rookie-PCVR v1.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3812 | choice /C Y /N /D Y /T 5 | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3964 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\rclone\rclone.exe" sync ":http:/meta.7z" "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287" --http-url https://bactio.skizzle.cyou/ --tpslimit 1.0 --tpslimit-burst 3 | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\rclone\rclone.exe | PCVR-Rookie v1.4.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rsync for cloud storage Exit code: 0 Version: 1.62.2 Modules
| |||||||||||||||
Total events
15 321
Read events
15 247
Write events
72
Delete events
2
Modification events
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
4
Suspicious files
9
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | 7z.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\rclone-v1.62.2-windows-386\rclone.exe | — | |
MD5:— | SHA256:— | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\Rookie-PCVR v1.4.exe | executable | |
MD5:D3620F60747CFEB4D1C88A92772F1B87 | SHA256:32DF4F6570C5FC4431B39137A75B771AE657DE3F3CB3E274C2DC3CB47F9A4D2D | |||
| 2896 | Rookie-PCVR v1.4.exe | C:\Users\admin\AppData\Local\Rookie.WTF\Rookie-PCVR_v1.4.exe_Url_hzvcsvf5fnbdm4of32kc1r0ogt0n4fkf\2.0.0.0\user.config | xml | |
MD5:5E03A567670108DFD9AD8661ADD32A78 | SHA256:C6531239E95AD4EFEDA056A2E0E14A14334B297A44AF89AFD037A98532913709 | |||
| 2896 | Rookie-PCVR v1.4.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\vrp-public-pcvr.json | binary | |
MD5:813A9C8E88601C6DD32F134768CB9662 | SHA256:DE07FA47BC4C7C1AB648427FF6452BF02A22375BE48DE53E57BA9B9E8342B12C | |||
| 3644 | PCVR-Rookie v1.4.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\rclone\vrp.download.config | — | |
MD5:— | SHA256:— | |||
| 2896 | Rookie-PCVR v1.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:14EC6F2B75F5B00AED35C1378C8992E2 | SHA256:F0496AB2CE44721F8F917D0886CC8756D717FBCFD43942BADB3FFD2054B6FDD2 | |||
| 2896 | Rookie-PCVR v1.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\78118620D6B8F6CB2909CD29DD8239E9 | binary | |
MD5:A9445206486978B6FF0CB02B58077A54 | SHA256:288230CCCE2DAFC23FC124A279A9B7A7AD1FC870A25E4A3745E6342A32C85F9A | |||
| 2896 | Rookie-PCVR v1.4.exe | C:\Users\admin\AppData\Local\Temp\Tar8514.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2896 | Rookie-PCVR v1.4.exe | C:\Users\admin\AppData\Local\Rookie.WTF\Rookie-PCVR_v1.4.exe_Url_hzvcsvf5fnbdm4of32kc1r0ogt0n4fkf\2.0.0.0\xsx5hbjb.newcfg | xml | |
MD5:5E03A567670108DFD9AD8661ADD32A78 | SHA256:C6531239E95AD4EFEDA056A2E0E14A14334B297A44AF89AFD037A98532913709 | |||
| 2896 | Rookie-PCVR v1.4.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.5287\rclone.zip | compressed | |
MD5:70AEDE552F45E0A9BC6BAC985AA3D7BB | SHA256:5B91EE887762007CD9FEF64003A70C496F855602D1BBB1C32A364008611F98FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
15
DNS requests
8
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2896 | Rookie-PCVR v1.4.exe | GET | 200 | 172.64.149.23:80 | http://zerossl.crt.sectigo.com/ZeroSSLECCDomainSecureSiteCA.crt | unknown | binary | 905 b | unknown |
2896 | Rookie-PCVR v1.4.exe | GET | 200 | 184.24.77.184:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?09ca0ce4c8c68716 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2896 | Rookie-PCVR v1.4.exe | 185.247.224.87:443 | vrpirates.wiki | Flokinet Ltd | SC | unknown |
2896 | Rookie-PCVR v1.4.exe | 172.64.149.23:80 | zerossl.crt.sectigo.com | CLOUDFLARENET | US | unknown |
2896 | Rookie-PCVR v1.4.exe | 95.217.6.16:443 | downloads.rclone.org | Hetzner Online GmbH | FI | unknown |
2896 | Rookie-PCVR v1.4.exe | 184.24.77.184:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2896 | Rookie-PCVR v1.4.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
2896 | Rookie-PCVR v1.4.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vrpirates.wiki |
| unknown |
zerossl.crt.sectigo.com |
| whitelisted |
downloads.rclone.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
objects.githubusercontent.com |
| shared |
bactio.skizzle.cyou |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2896 | Rookie-PCVR v1.4.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3644 | PCVR-Rookie v1.4.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |