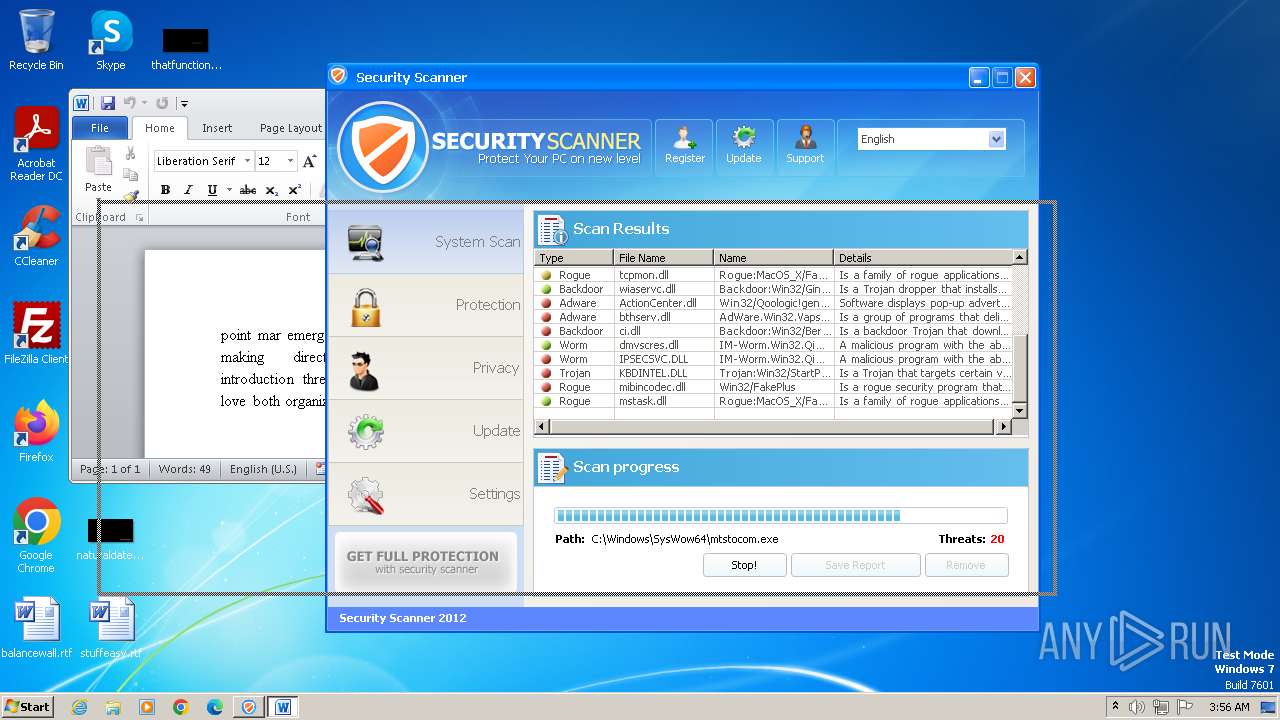
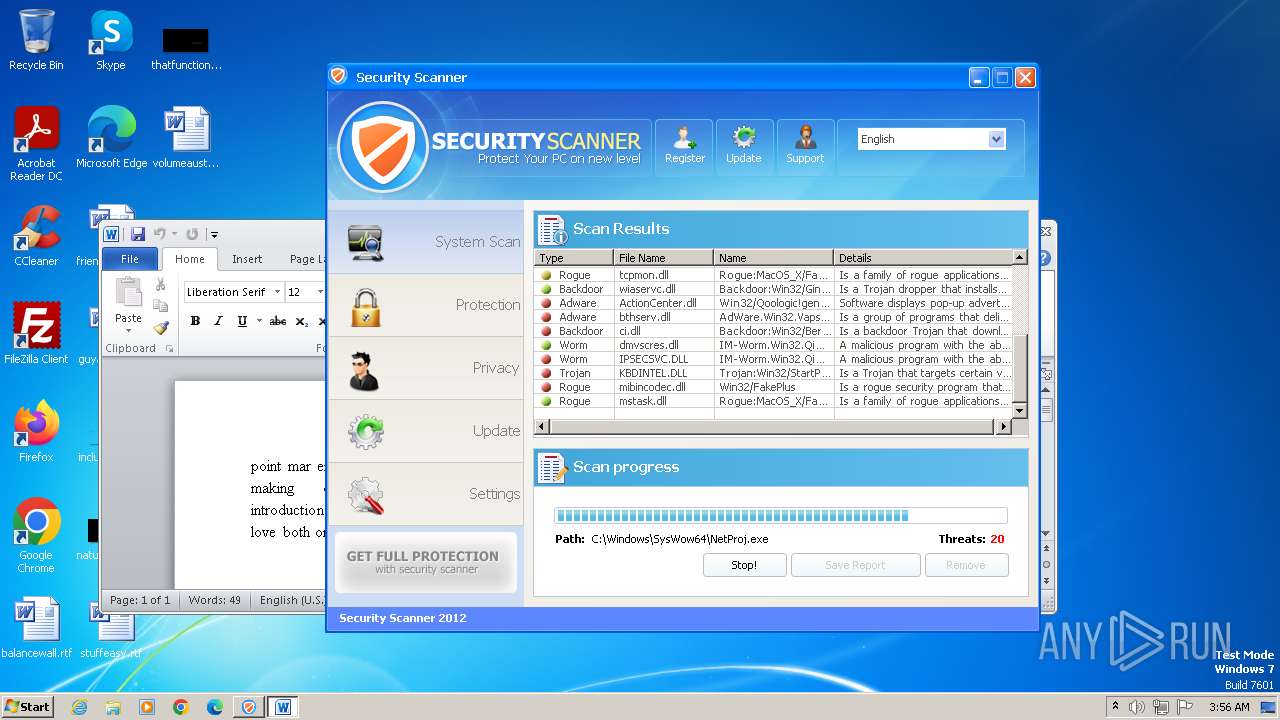
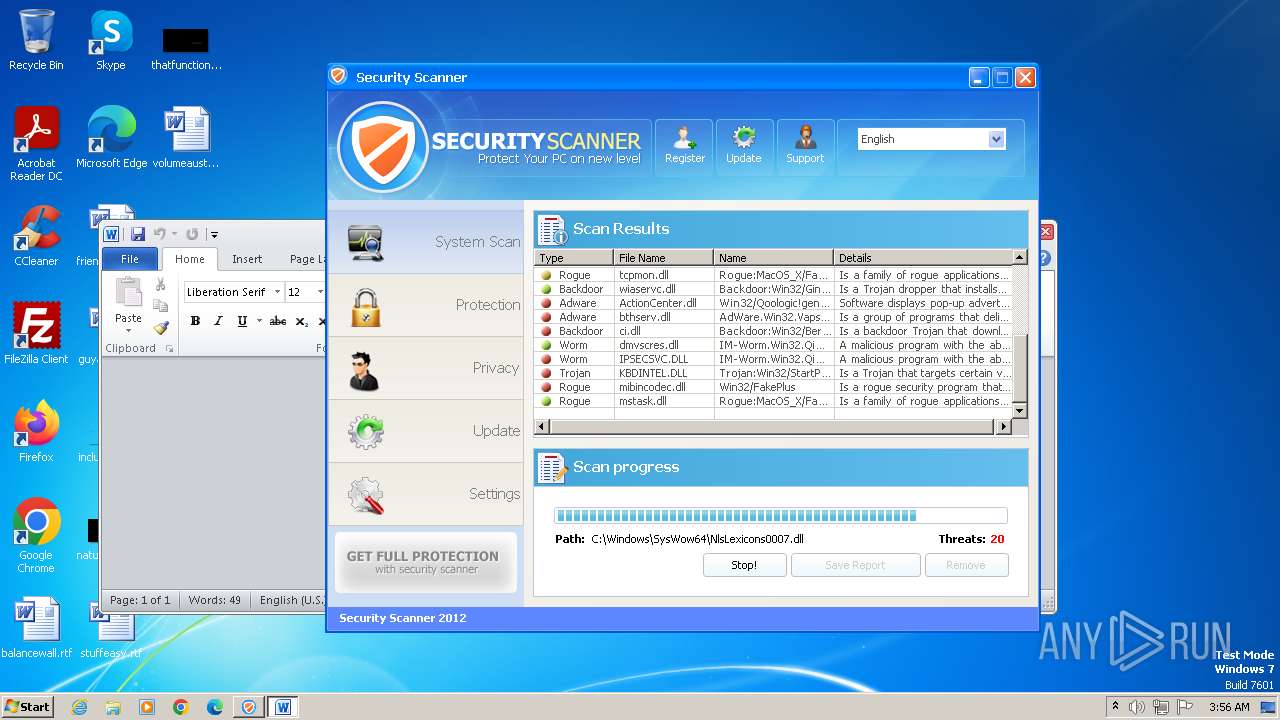
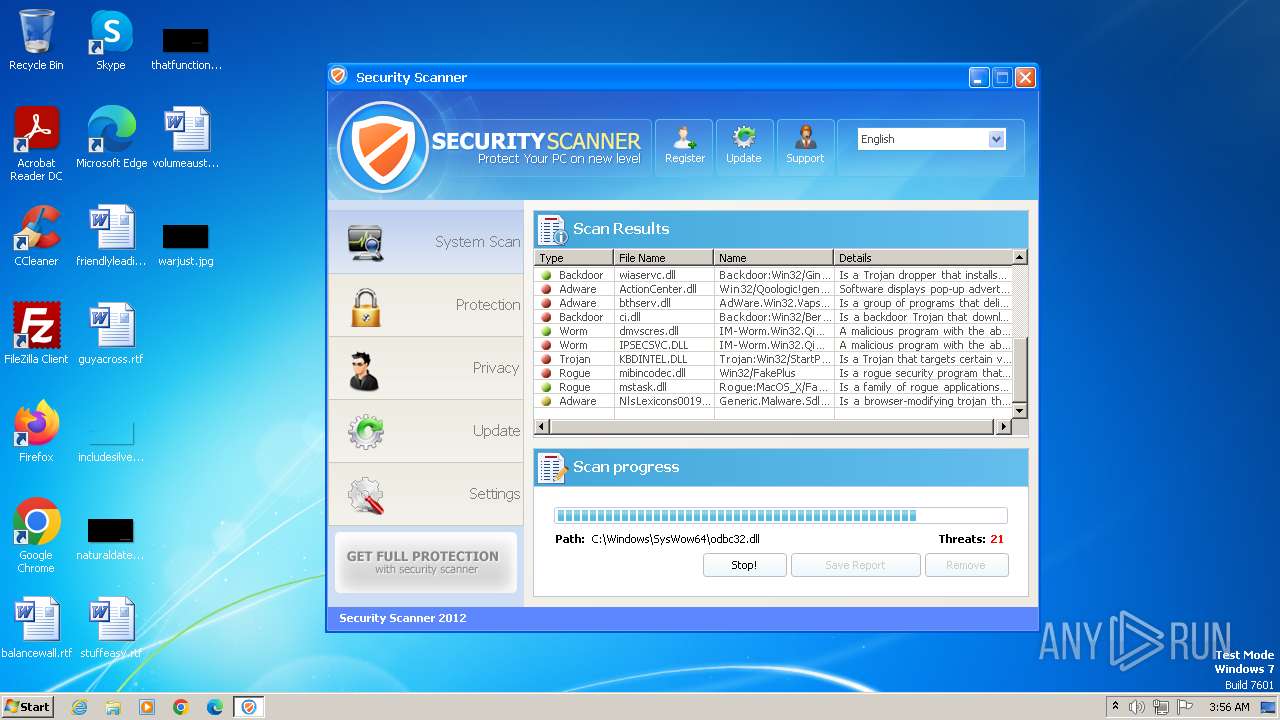
| File name: | Endermanch@Movie.mpeg.exe |
| Full analysis: | https://app.any.run/tasks/201b8924-f752-43b1-b1b8-8eeb00ef7e01 |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2024, 03:55:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D0DEB2644C9435EA701E88537787EA6E |
| SHA1: | 866E47ECD80DA89C4F56557659027A3AEE897132 |
| SHA256: | AD6CD46F373AADAD85FAB5ECDB4CB4AD7EBD0CBE44C84DB5D2A2EE1B54EB5EC3 |
| SSDEEP: | 12288:yArwT7R/jf4kWEFzRNFbtgDEOvAgZ6yvU/K4clr9IBp4T:ygwT7R/jf4kDhGDEeXUyvU/K4clr8p |
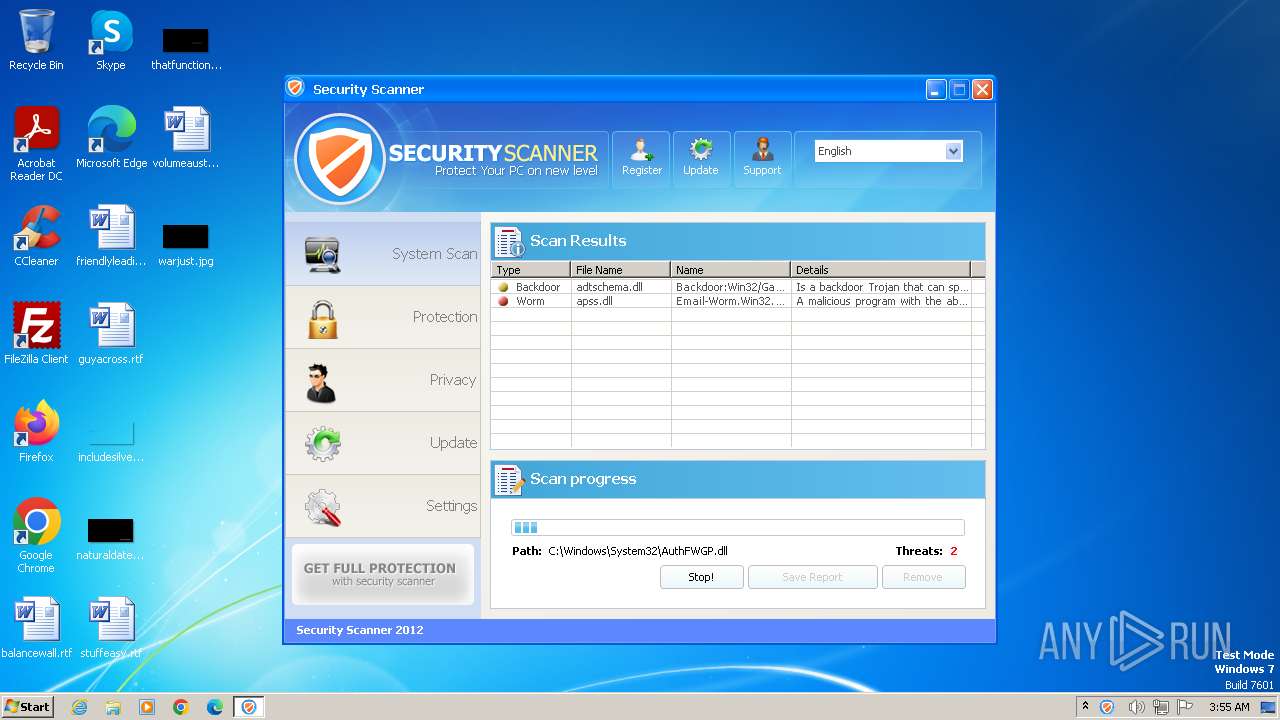
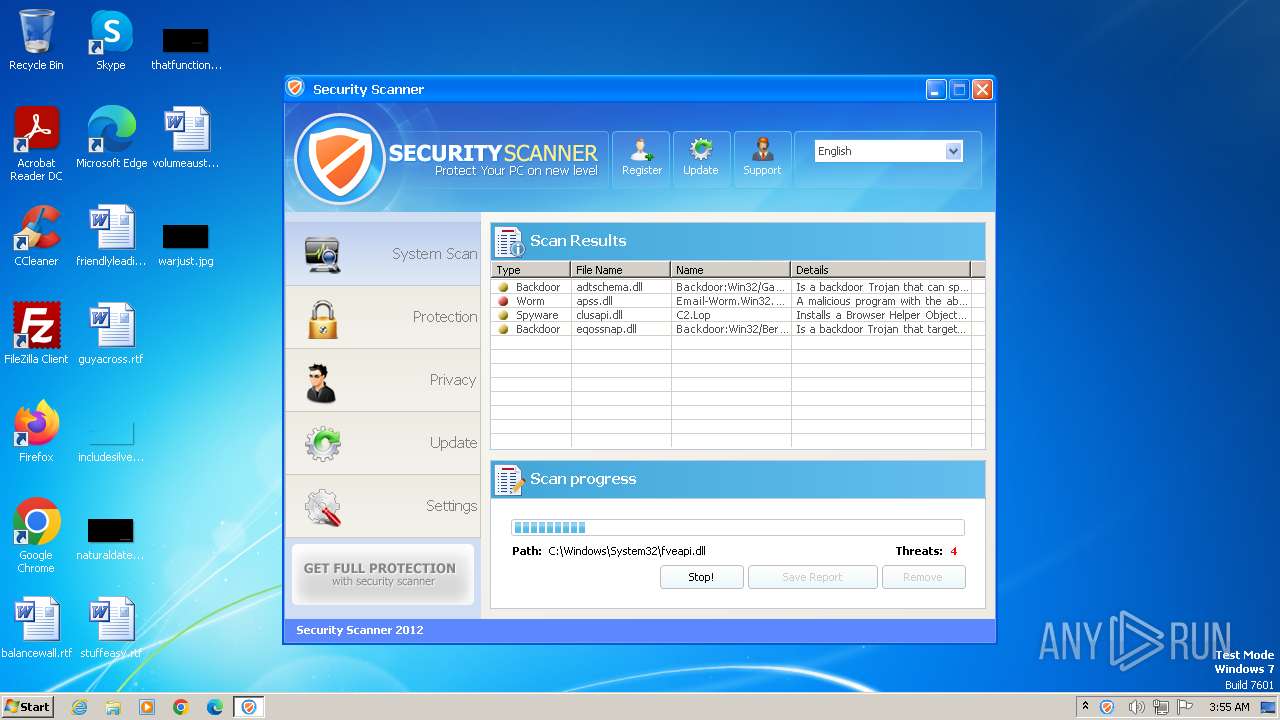
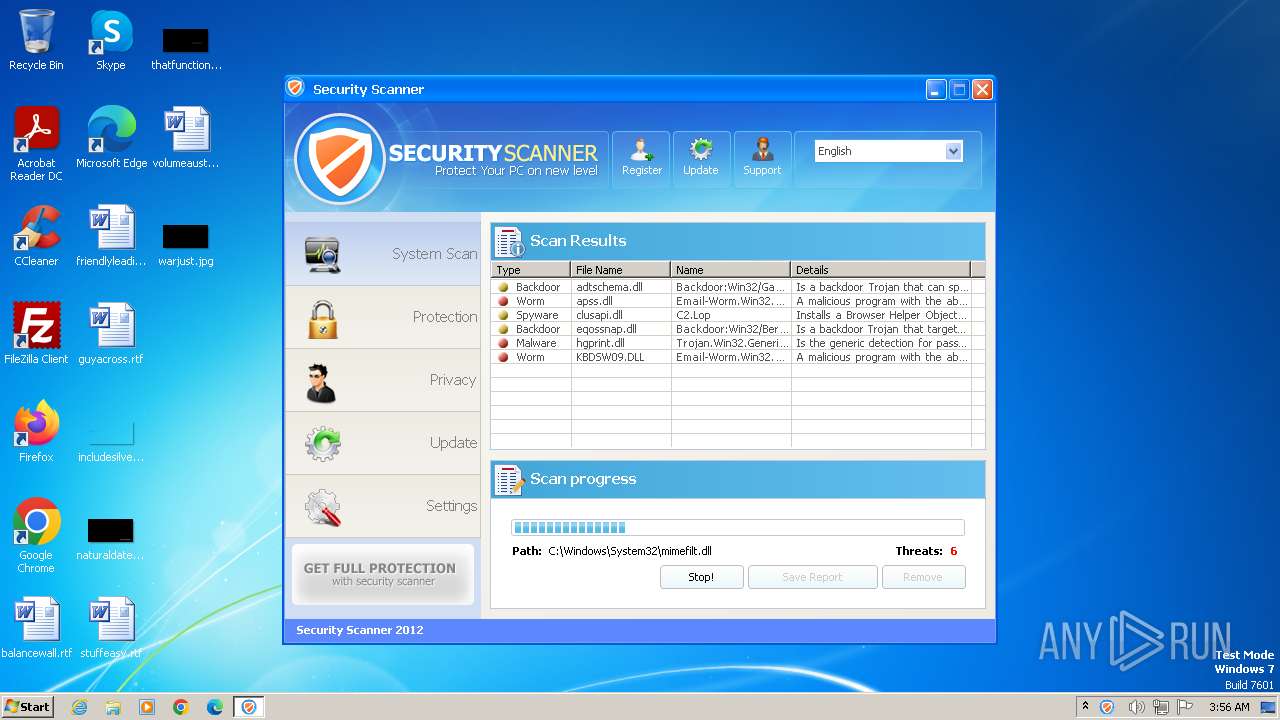
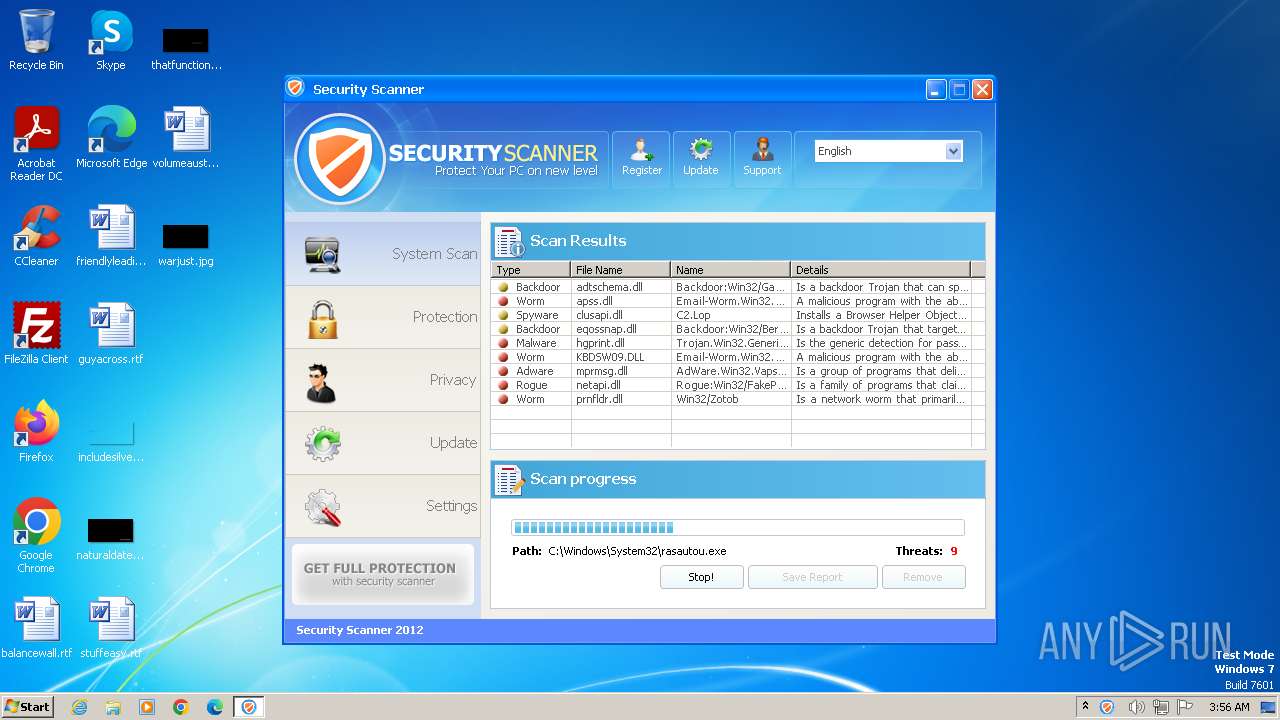
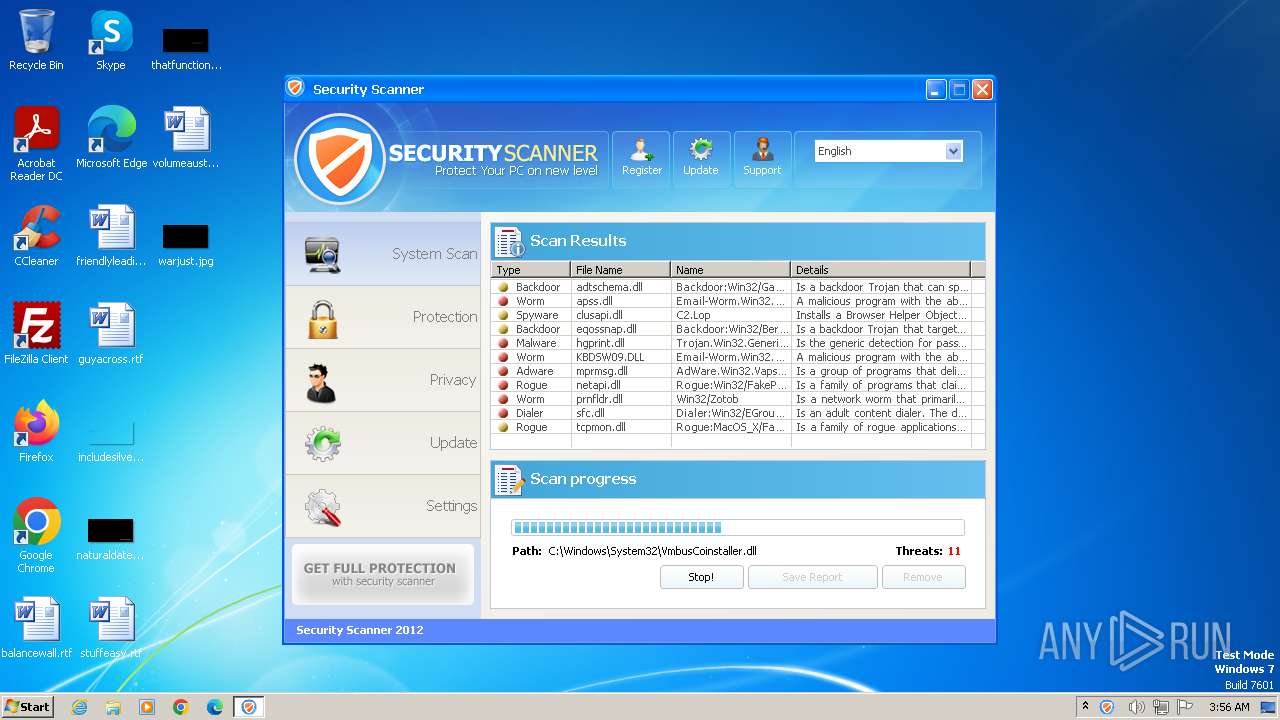
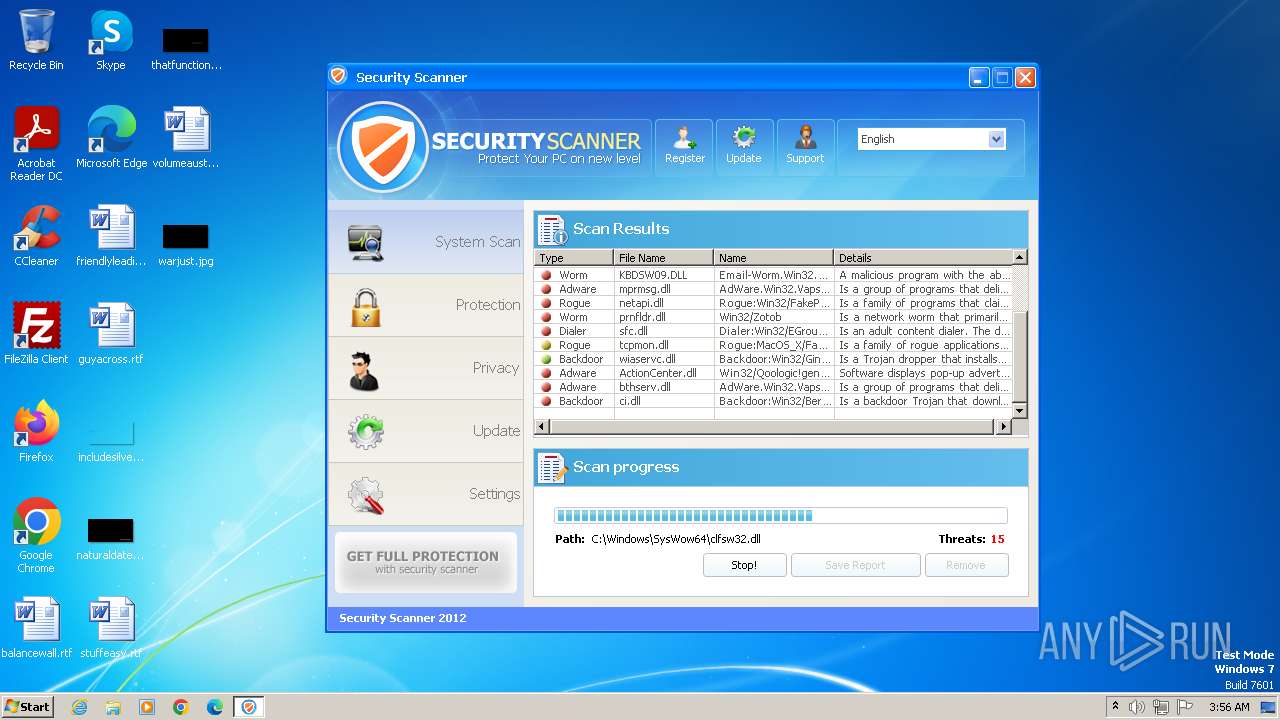
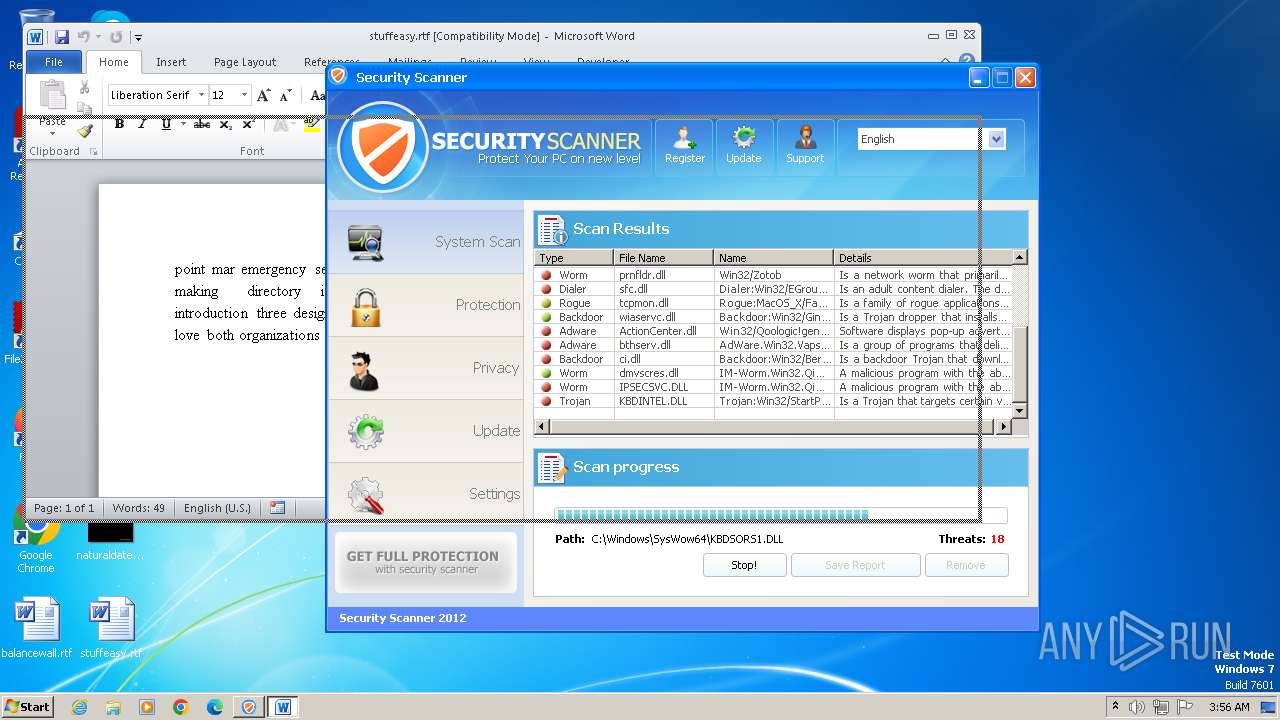
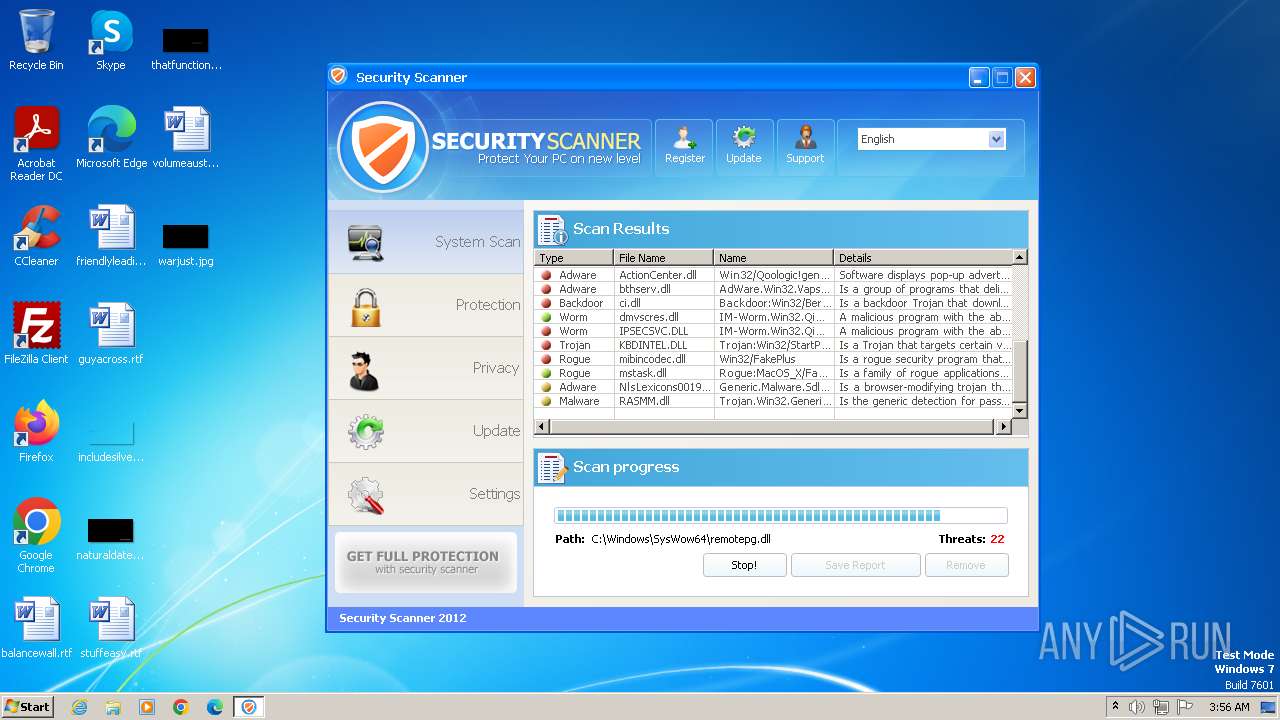
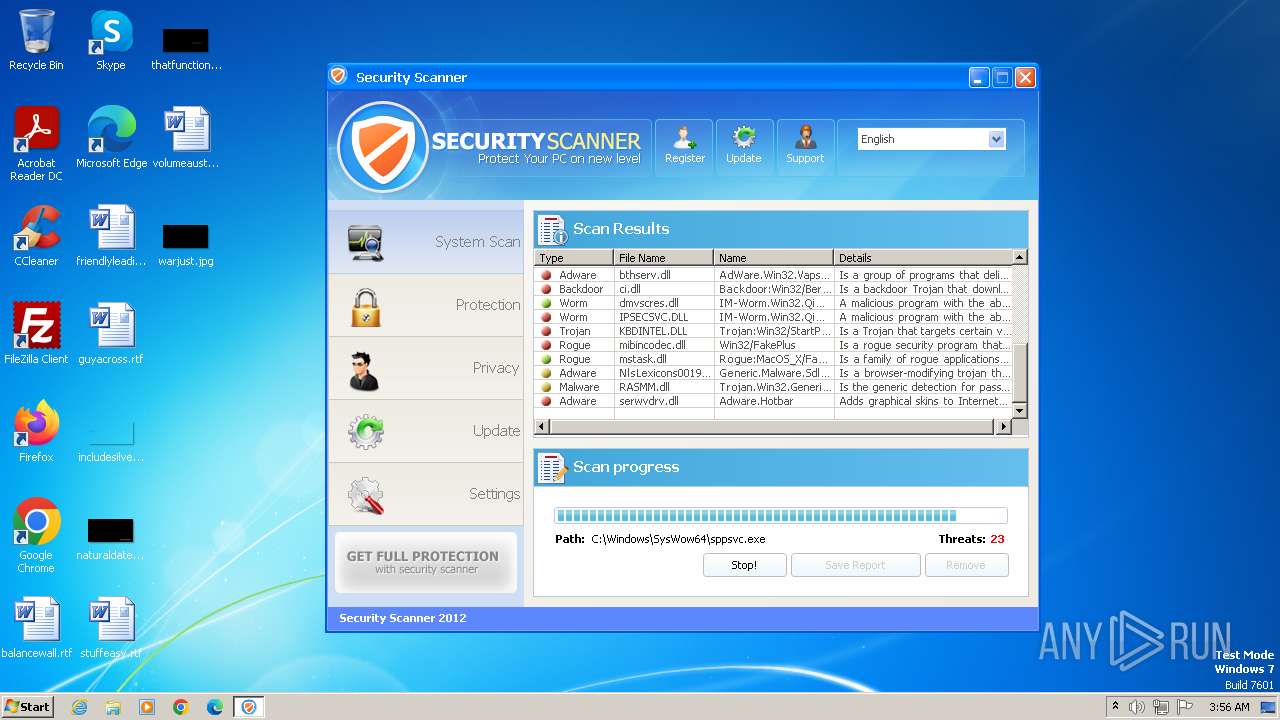
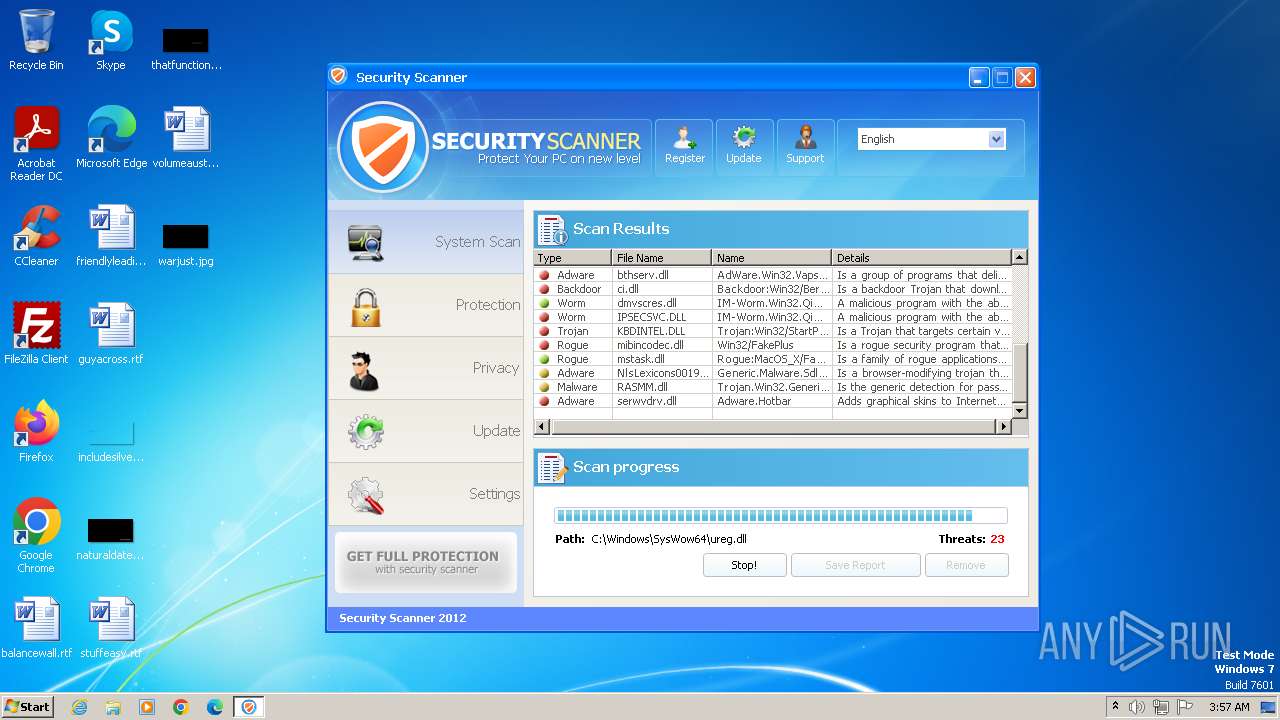
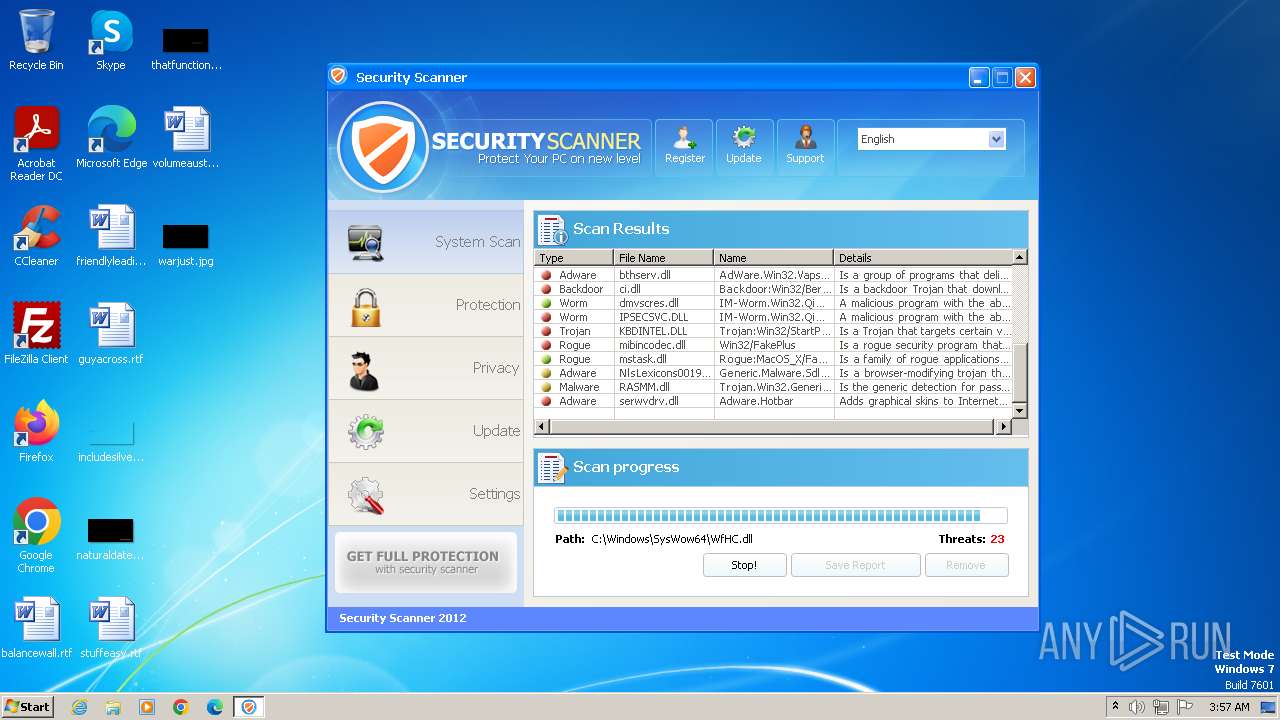
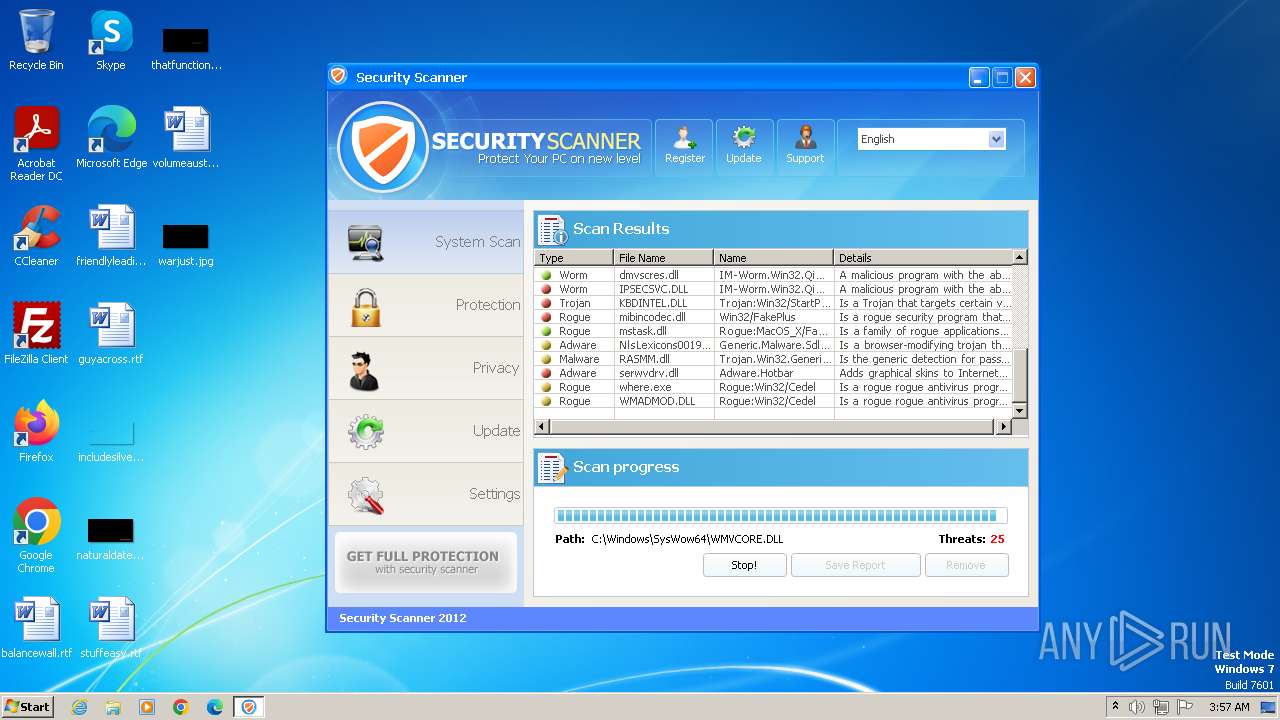
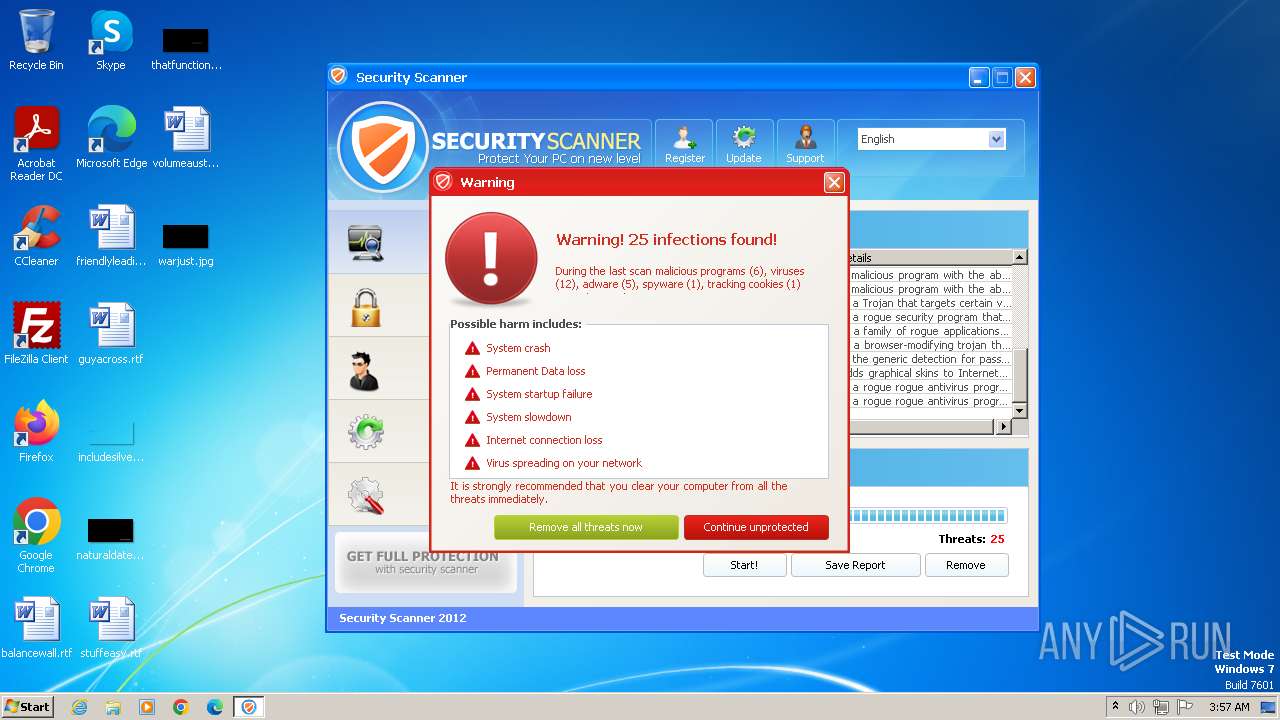
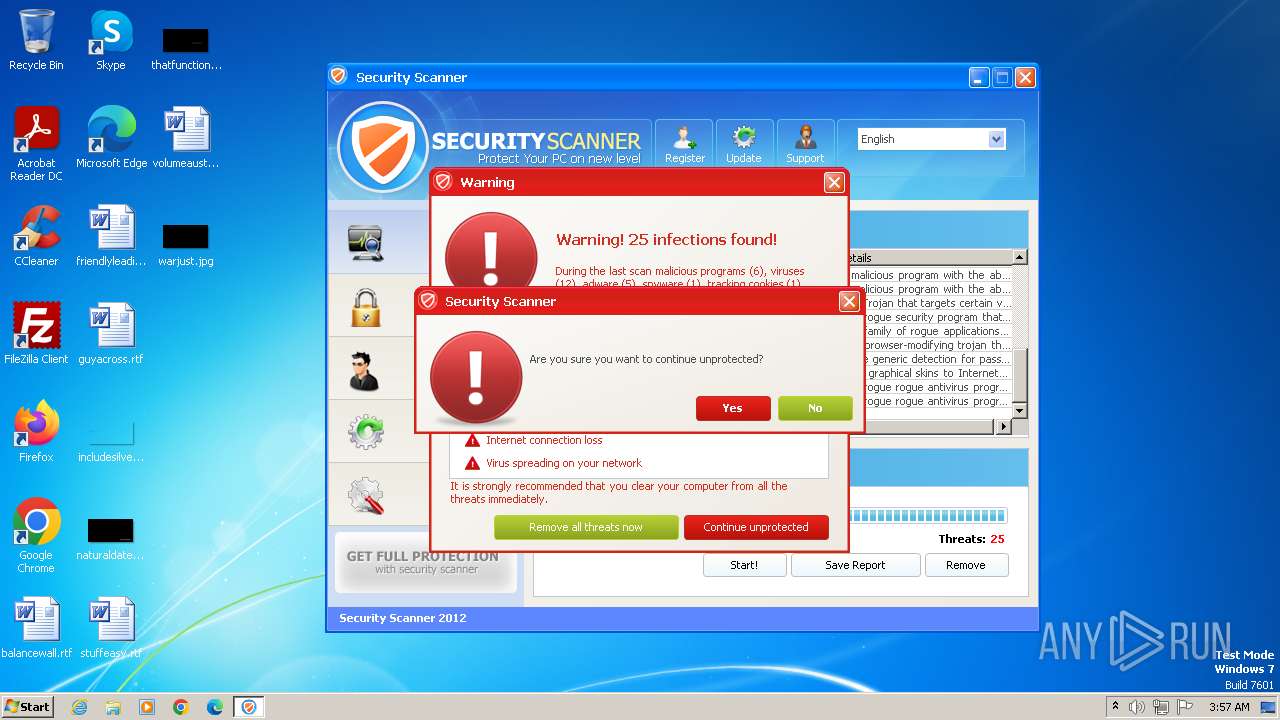
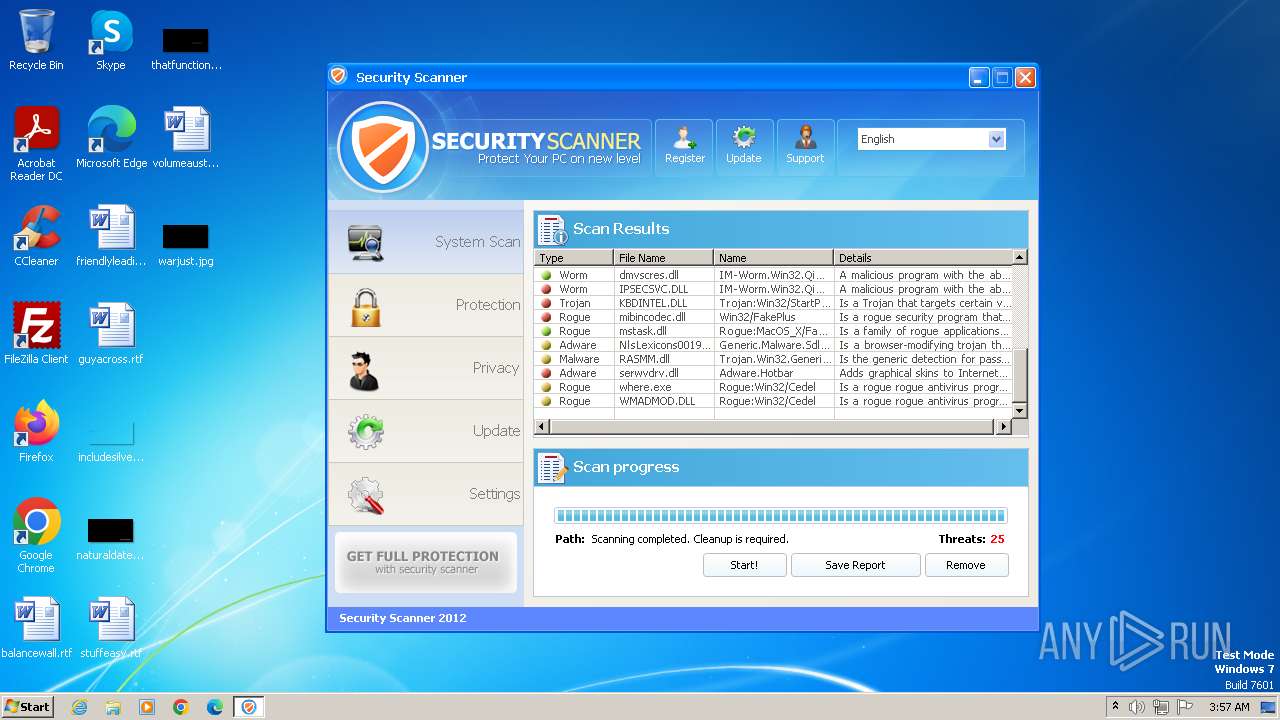
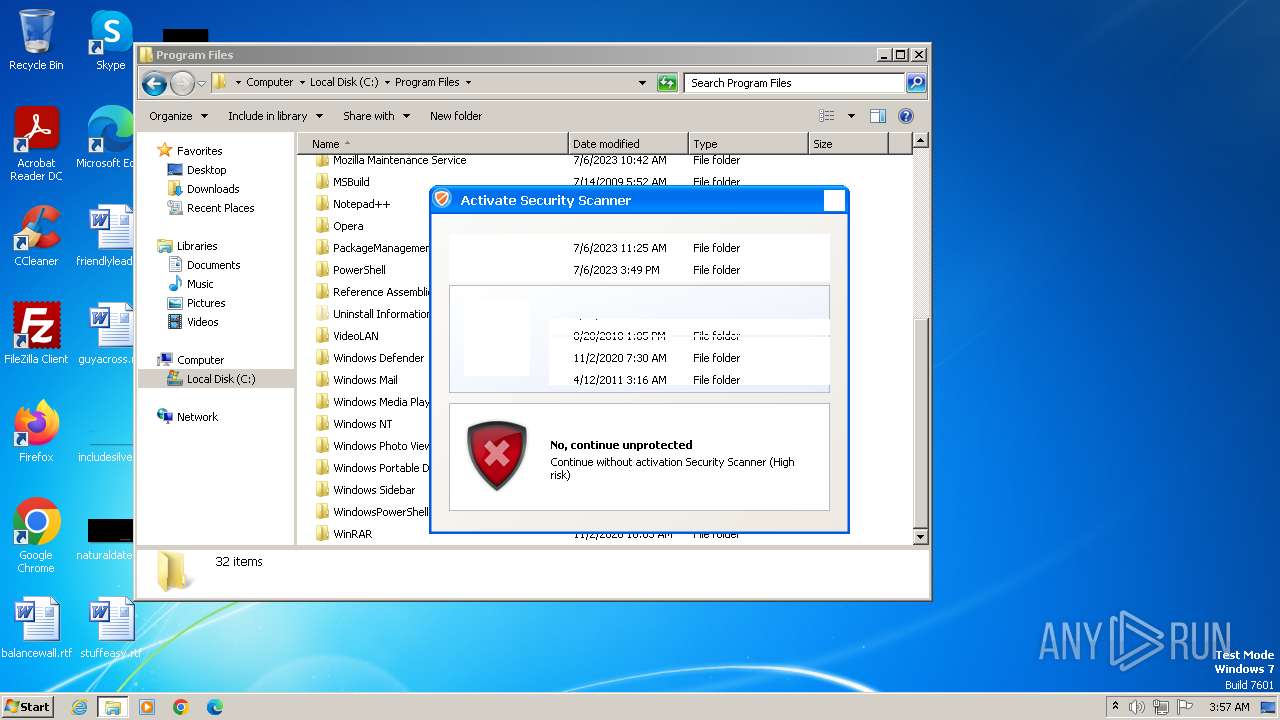
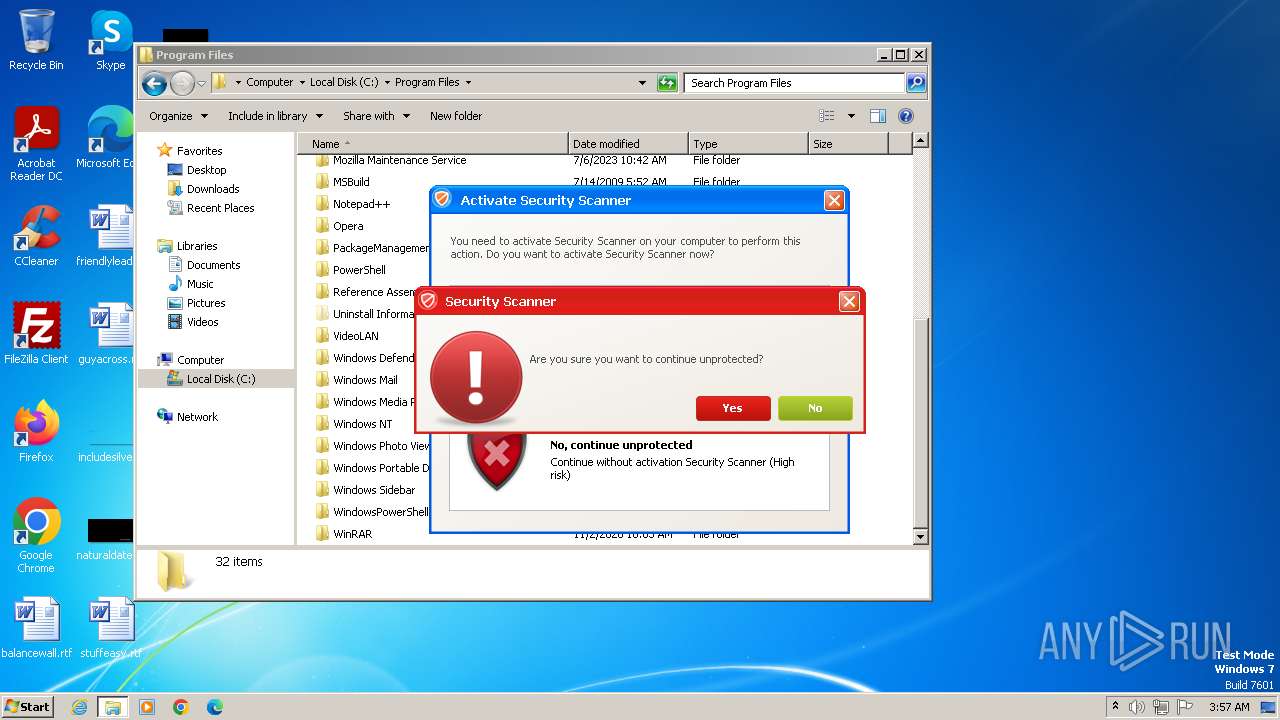
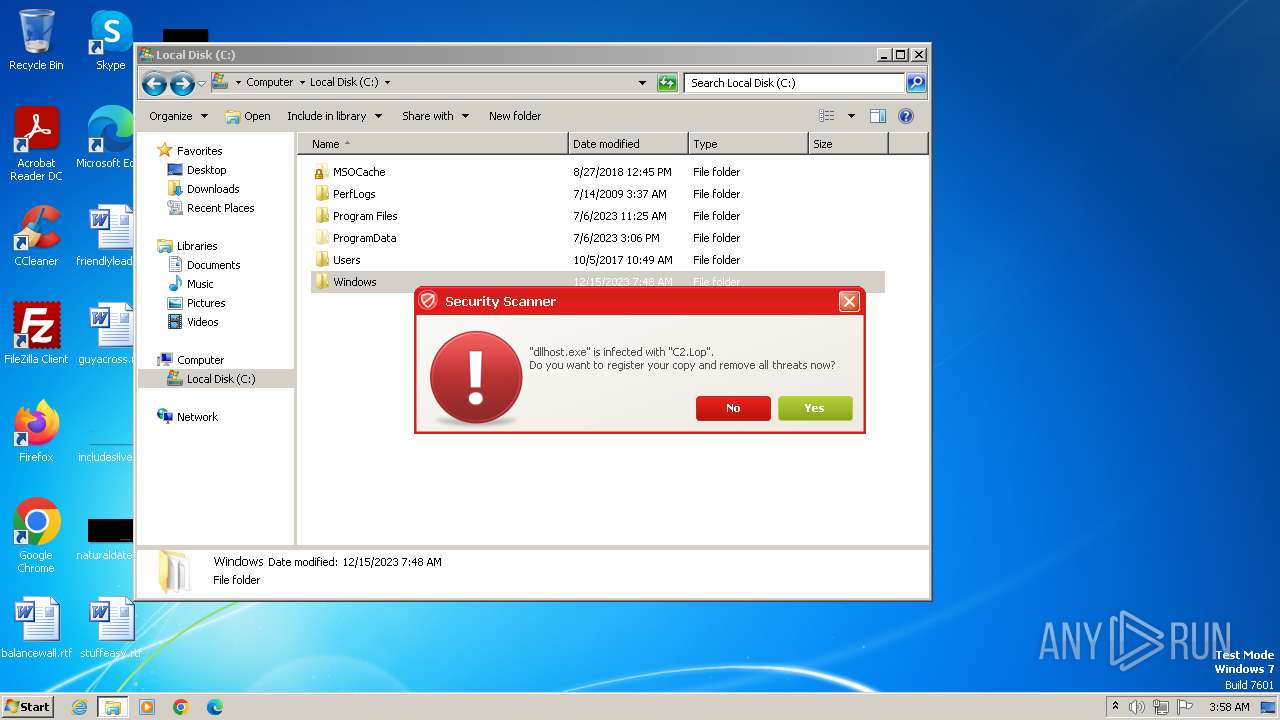
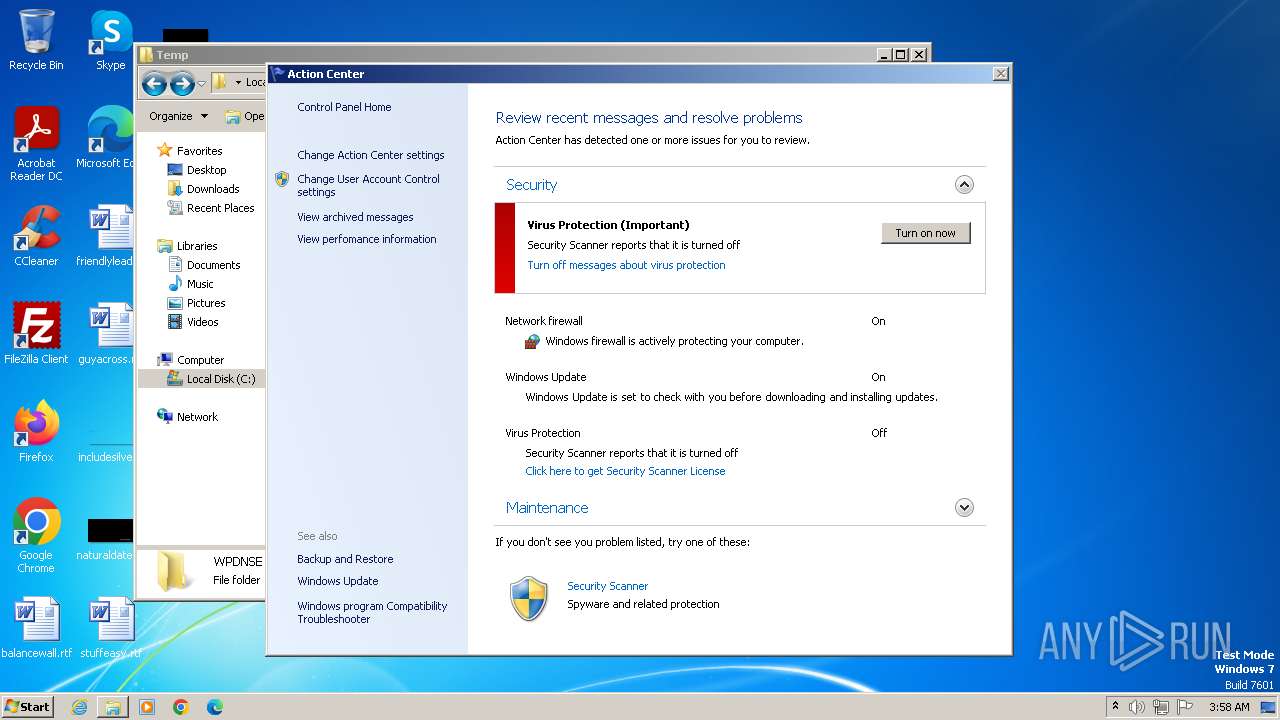
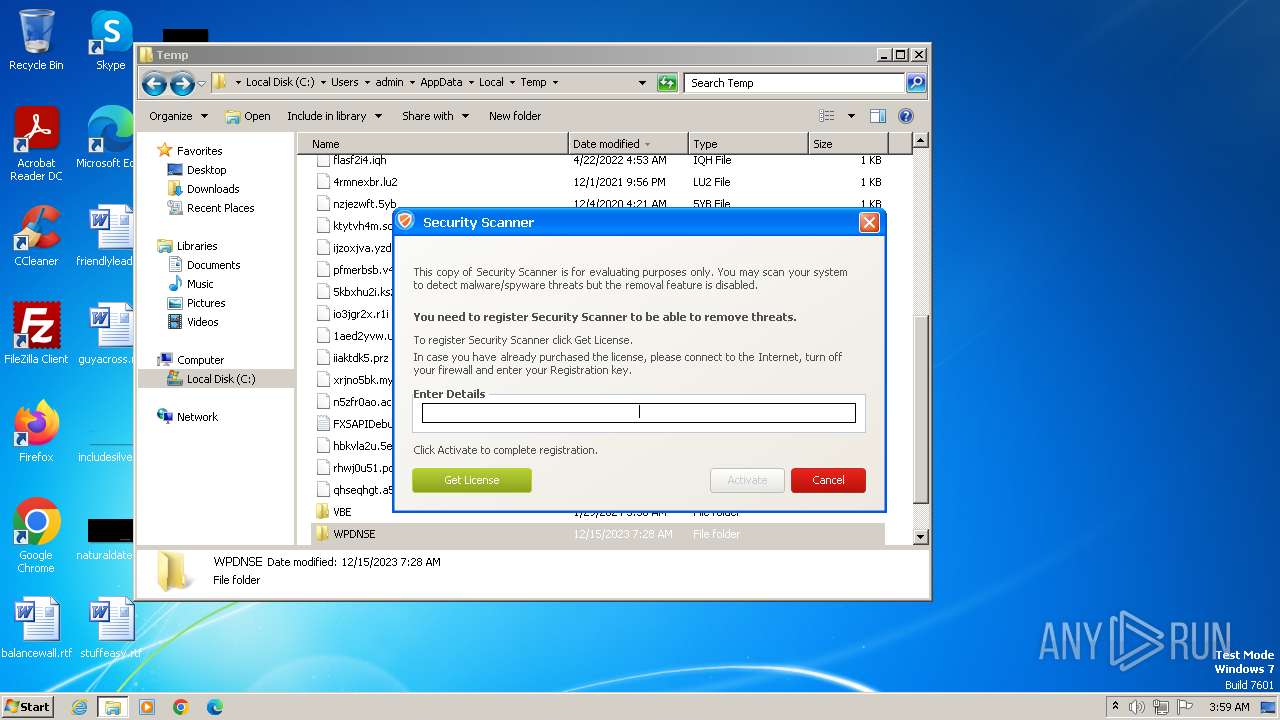
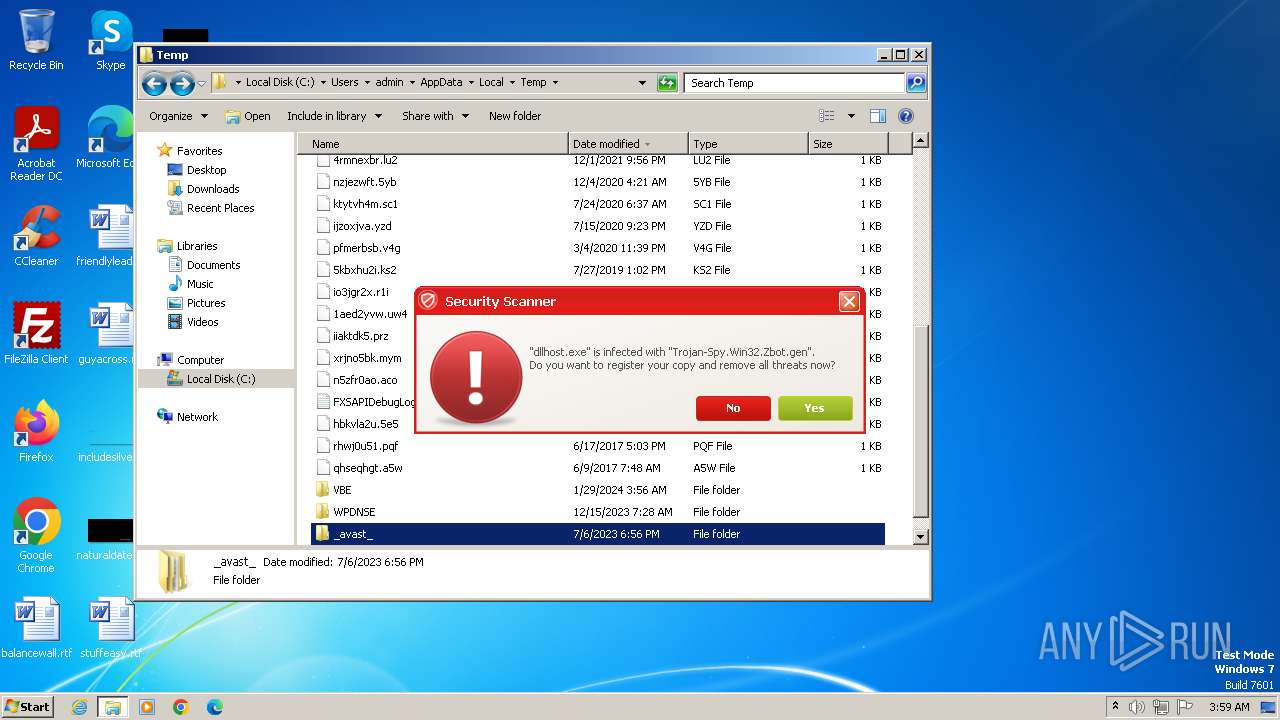
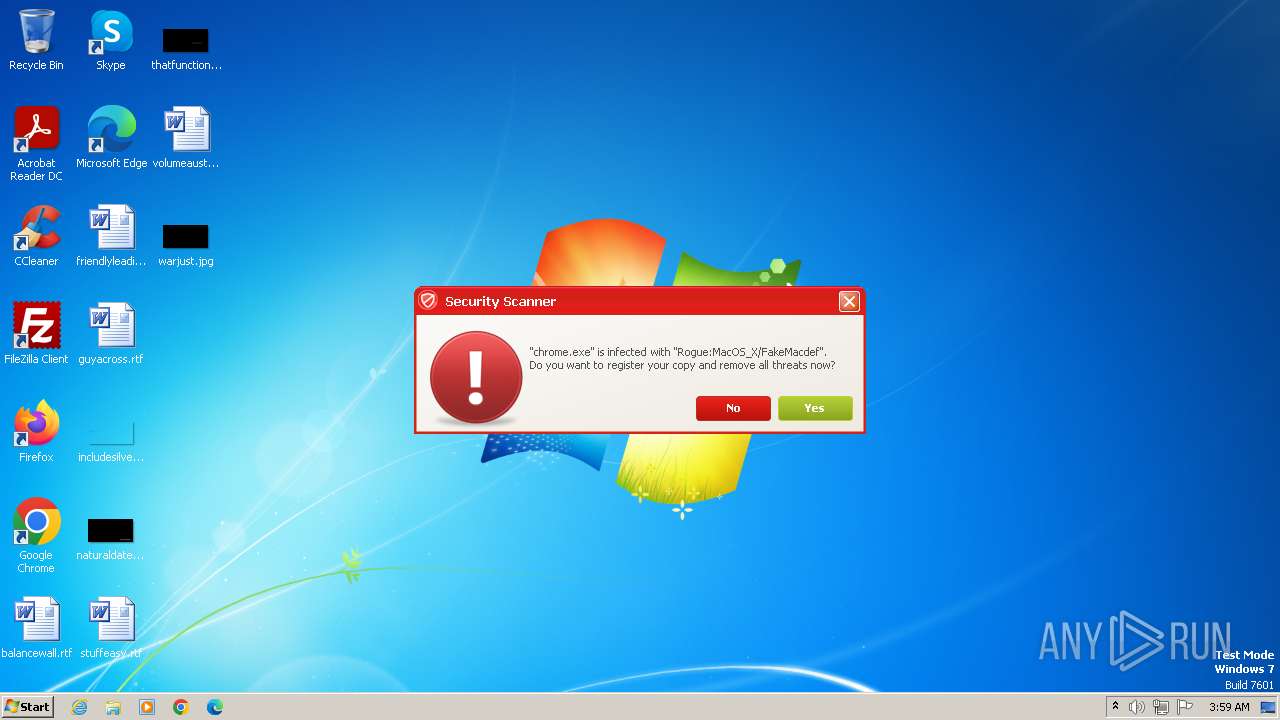
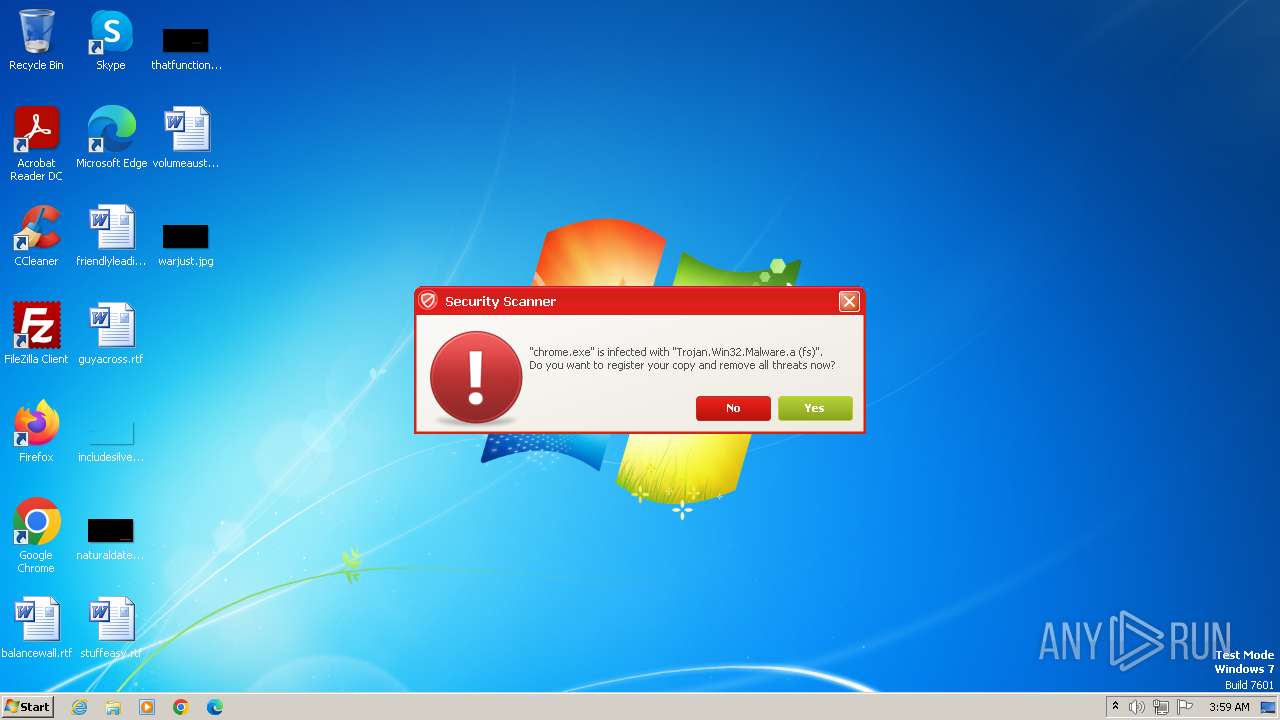
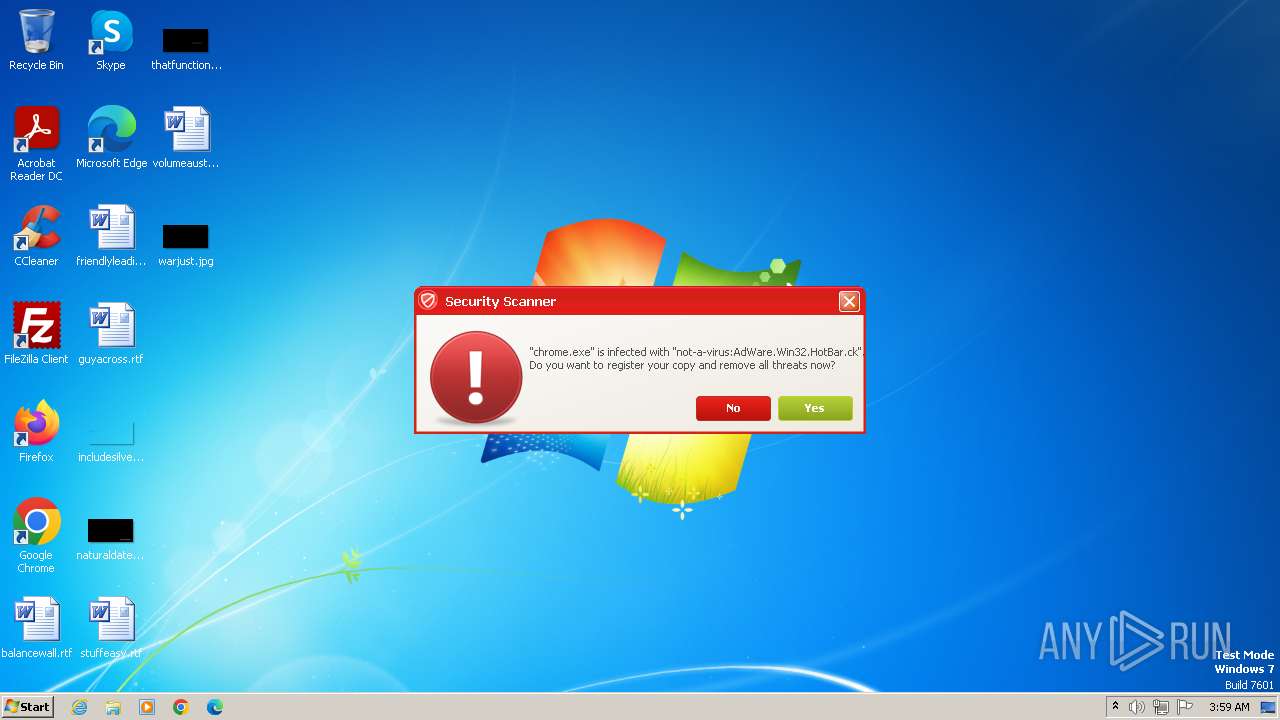
MALICIOUS
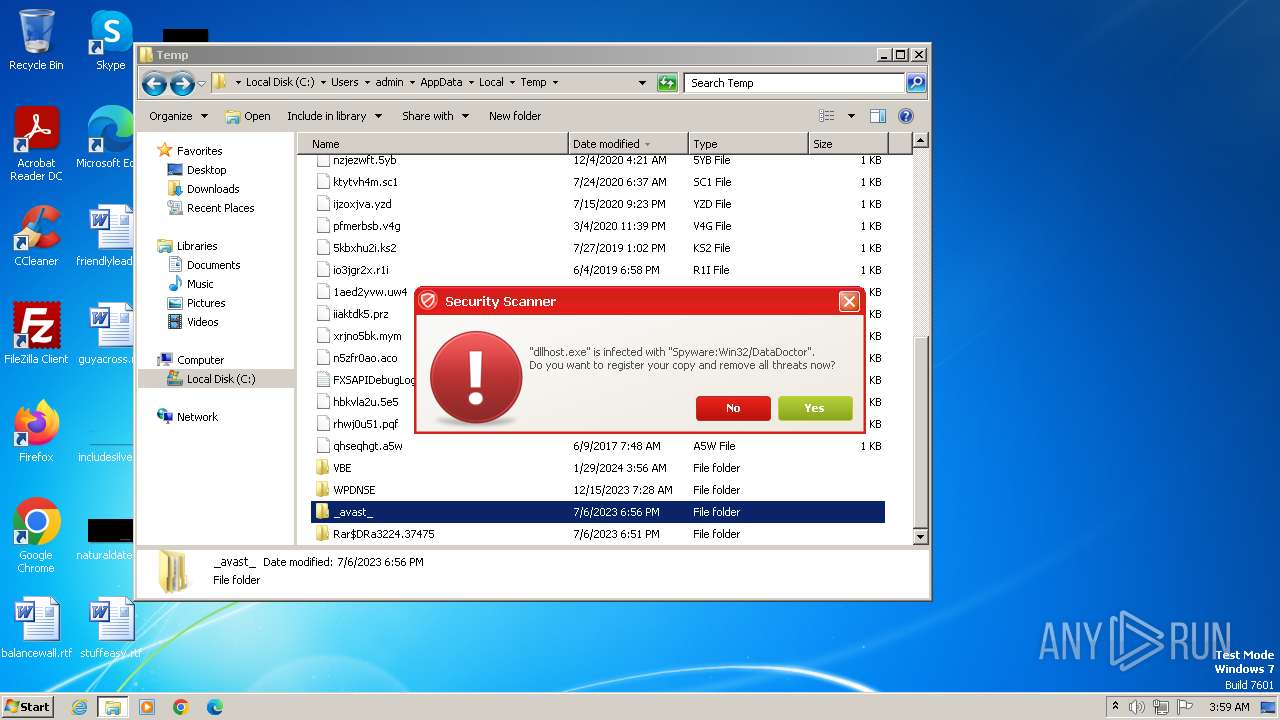
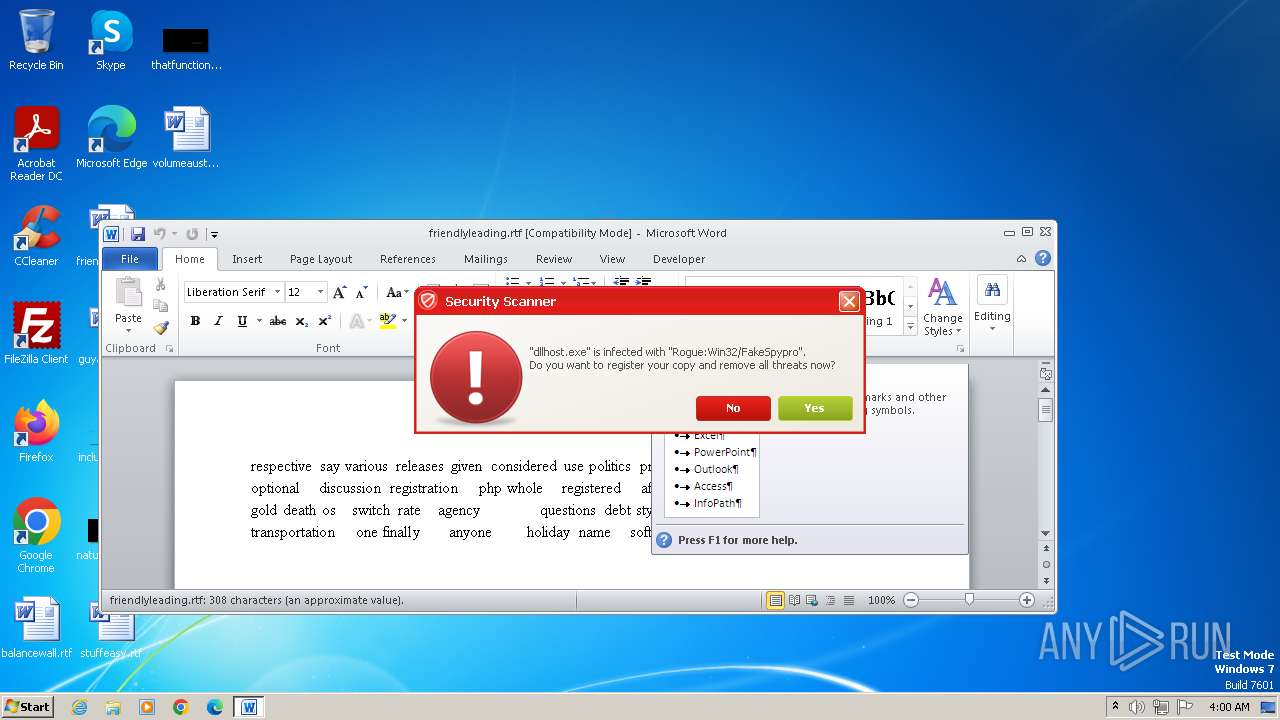
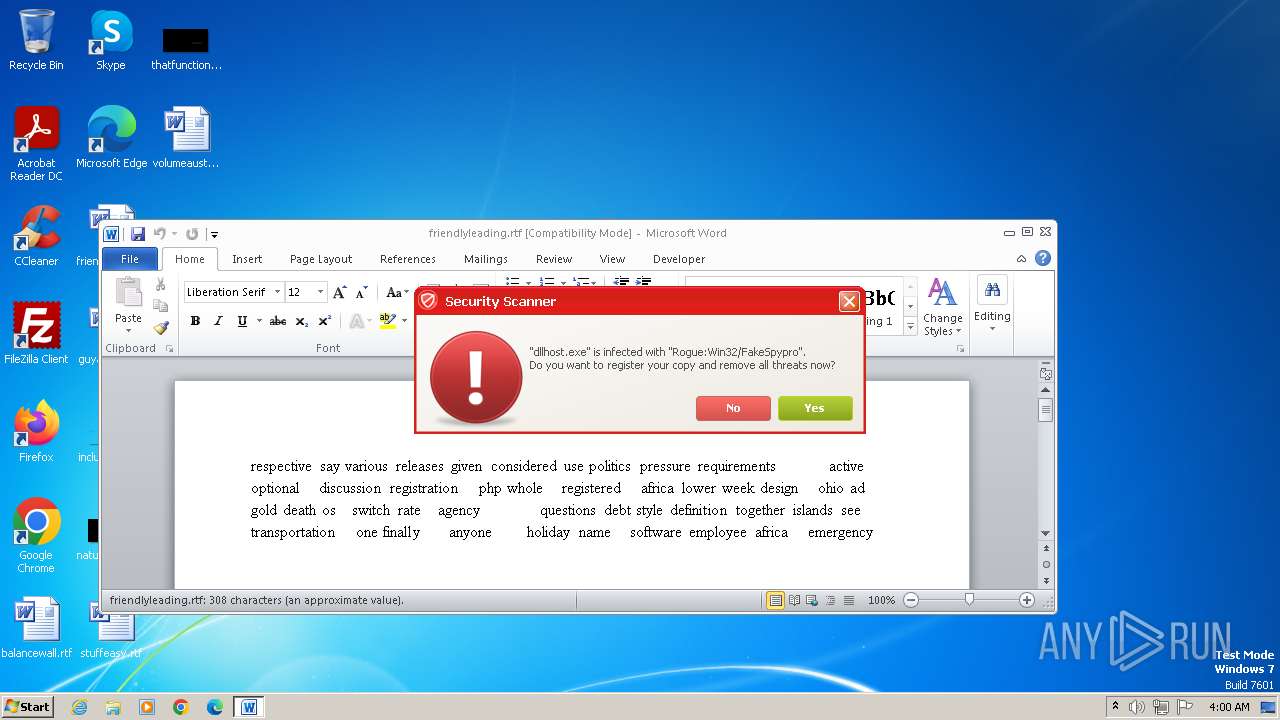
Drops the executable file immediately after the start
- Endermanch@Movie.mpeg.exe (PID: 3456)
Starts CMD.EXE for self-deleting
- Endermanch@Movie.mpeg.exe (PID: 3456)
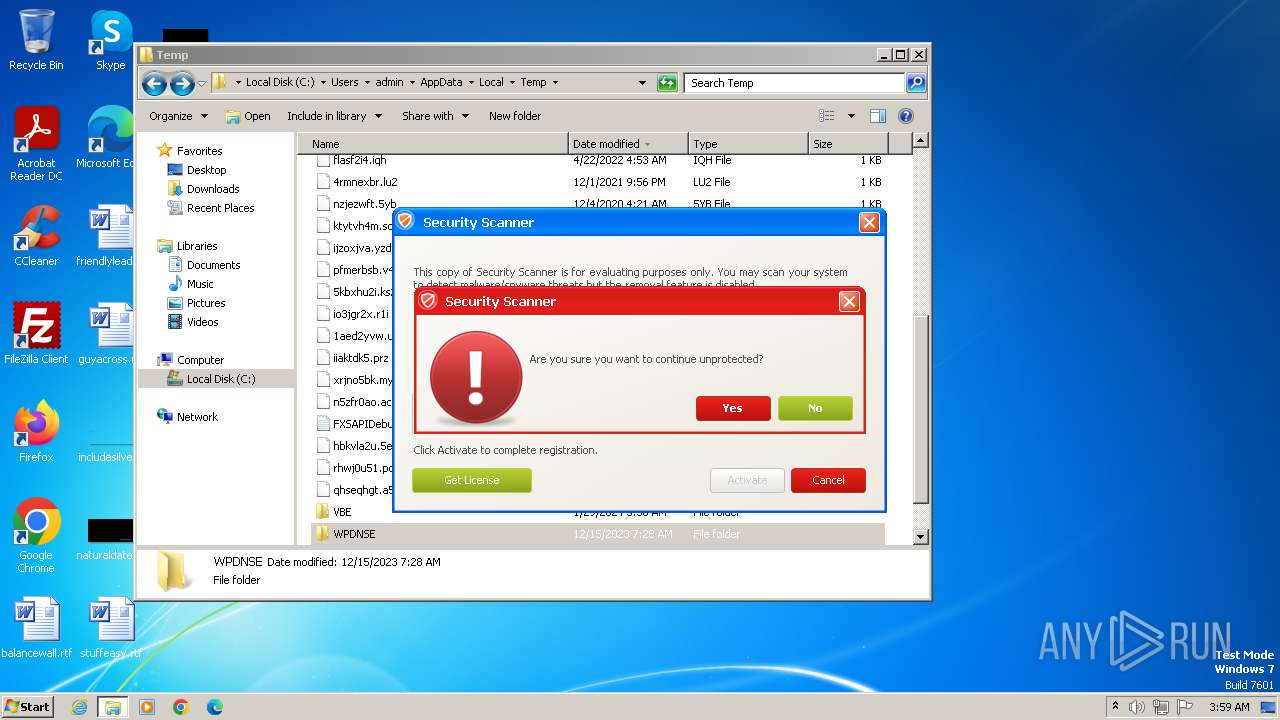
SUSPICIOUS
Executable content was dropped or overwritten
- Endermanch@Movie.mpeg.exe (PID: 3456)
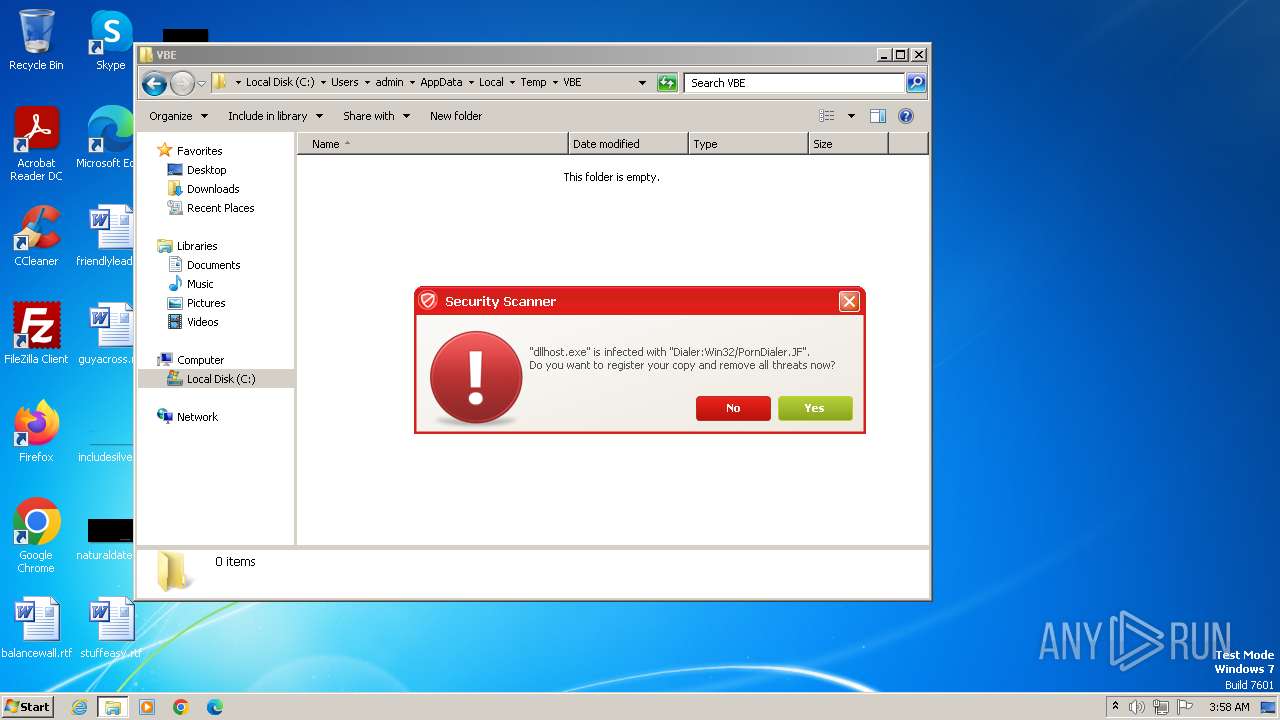
Reads the Internet Settings
- Endermanch@Movie.mpeg.exe (PID: 3456)
- ivdmnftdt.exe (PID: 2592)
Starts CMD.EXE for commands execution
- Endermanch@Movie.mpeg.exe (PID: 3456)
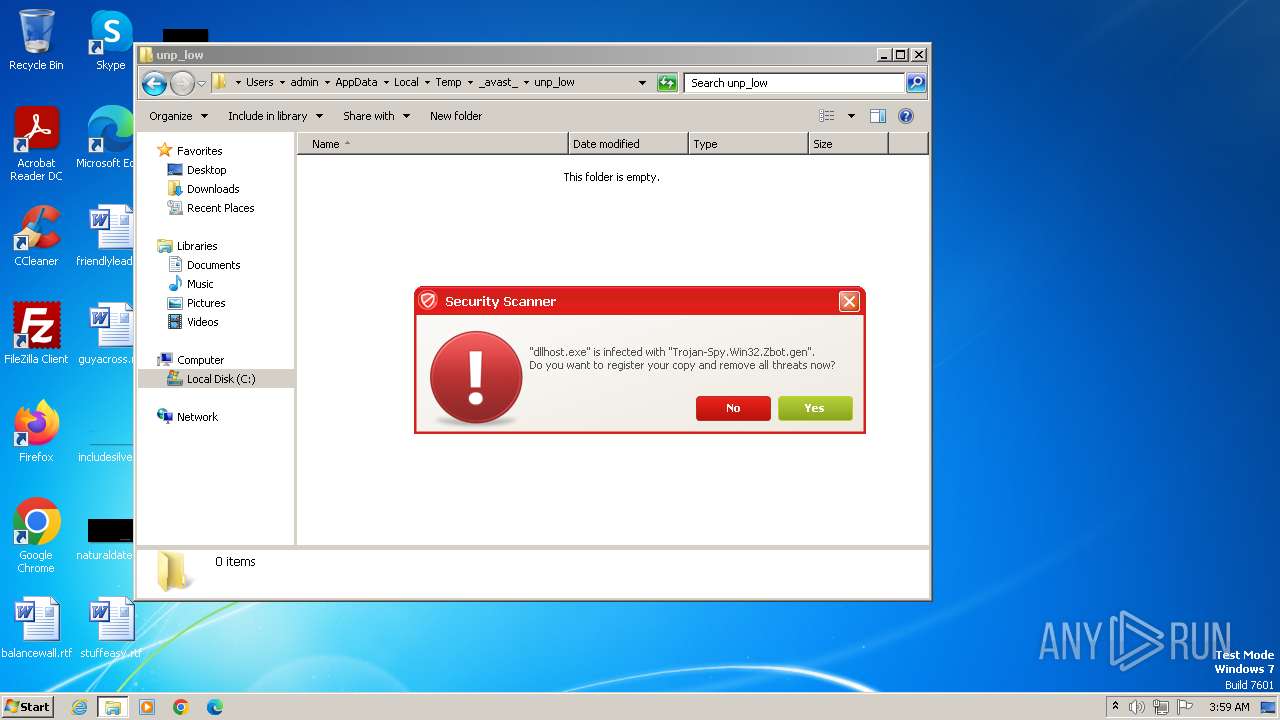
The executable file from the user directory is run by the CMD process
- ivdmnftdt.exe (PID: 2592)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2808)
Reads Microsoft Outlook installation path
- ivdmnftdt.exe (PID: 2592)
INFO
Reads the computer name
- Endermanch@Movie.mpeg.exe (PID: 3456)
- ivdmnftdt.exe (PID: 2592)
Checks supported languages
- Endermanch@Movie.mpeg.exe (PID: 3456)
- ivdmnftdt.exe (PID: 2592)
Reads the machine GUID from the registry
- Endermanch@Movie.mpeg.exe (PID: 3456)
- ivdmnftdt.exe (PID: 2592)
Creates files or folders in the user directory
- Endermanch@Movie.mpeg.exe (PID: 3456)
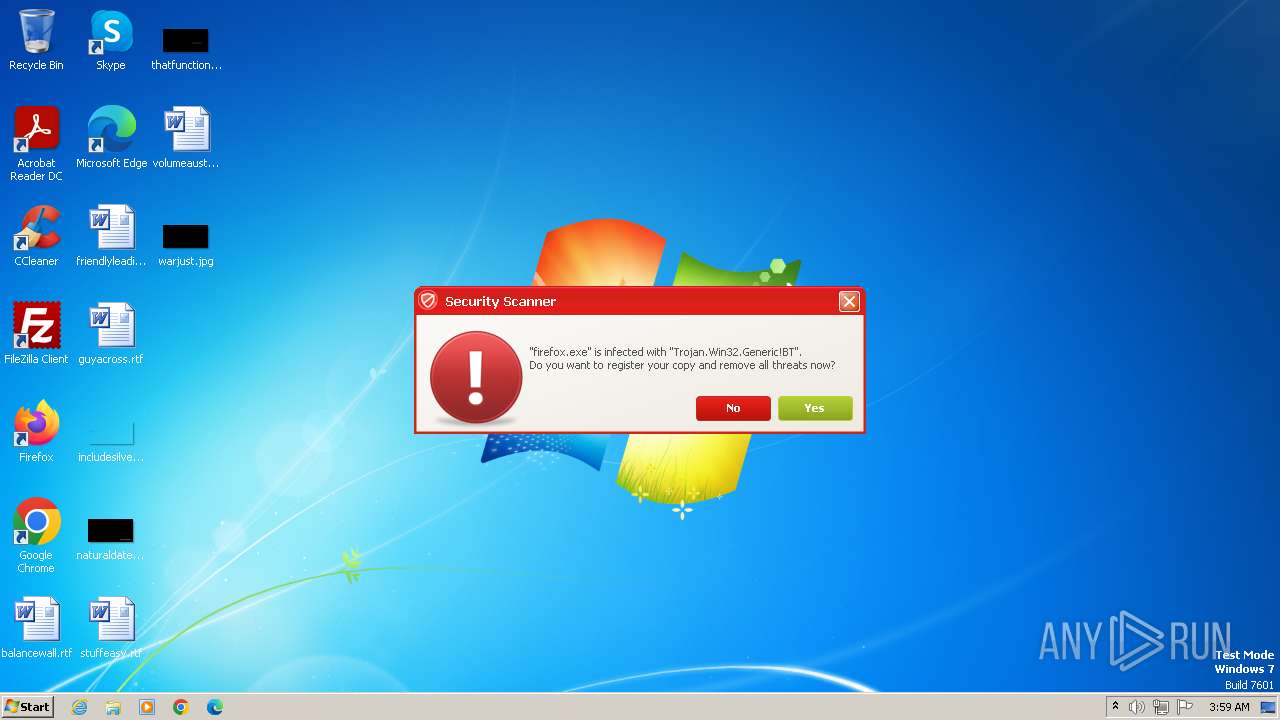
Manual execution by a user
- chrome.exe (PID: 3400)
- chrome.exe (PID: 1608)
- firefox.exe (PID: 2888)
- WINWORD.EXE (PID: 2452)
- chrome.exe (PID: 2992)
- WINWORD.EXE (PID: 2020)
Application launched itself
- chrome.exe (PID: 3400)
- chrome.exe (PID: 1608)
- firefox.exe (PID: 2888)
- chrome.exe (PID: 2992)
Checks proxy server information
- ivdmnftdt.exe (PID: 2592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:12 13:20:36+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7 |
| CodeSize: | 102400 |
| InitializedDataSize: | 314719 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1401 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
65
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | ping -n 3 127.1 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6b858b38,0x6b858b48,0x6b858b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | explorer.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2020 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\friendlyleading.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2156 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6bd58b38,0x6bd58b48,0x6bd58b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\stuffeasy.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6bd58b38,0x6bd58b48,0x6bd58b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2588 | taskkill /f /pid 3456 | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2592 | C:\Users\admin\AppData\Local\IVDMNF~1.EXE -f | C:\Users\admin\AppData\Local\ivdmnftdt.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
6 390
Read events
5 690
Write events
409
Delete events
291
Modification events
| (PID) Process: | (3456) Endermanch@Movie.mpeg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3456) Endermanch@Movie.mpeg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3456) Endermanch@Movie.mpeg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3456) Endermanch@Movie.mpeg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2452) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2452) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2452) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2452) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2452) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2452) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
Executable files
2
Suspicious files
11
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2452 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7BB1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2020 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA36F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2452 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\stuffeasy.rtf.LNK | binary | |
MD5:8D52ECC1F9BC014283C9FFCB33214FAA | SHA256:093A1A039ACBBD20E92090E1F5DD5E91CC4EC44A50FFDB1E513D0D4115EBE347 | |||
| 2452 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:F2524E7602DC79B2CA3B2F4240D932DF | SHA256:2D6CC55159946668D194AB25E48A40DEE6CDFEC24D71885599C5EE7817E14E5C | |||
| 2992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
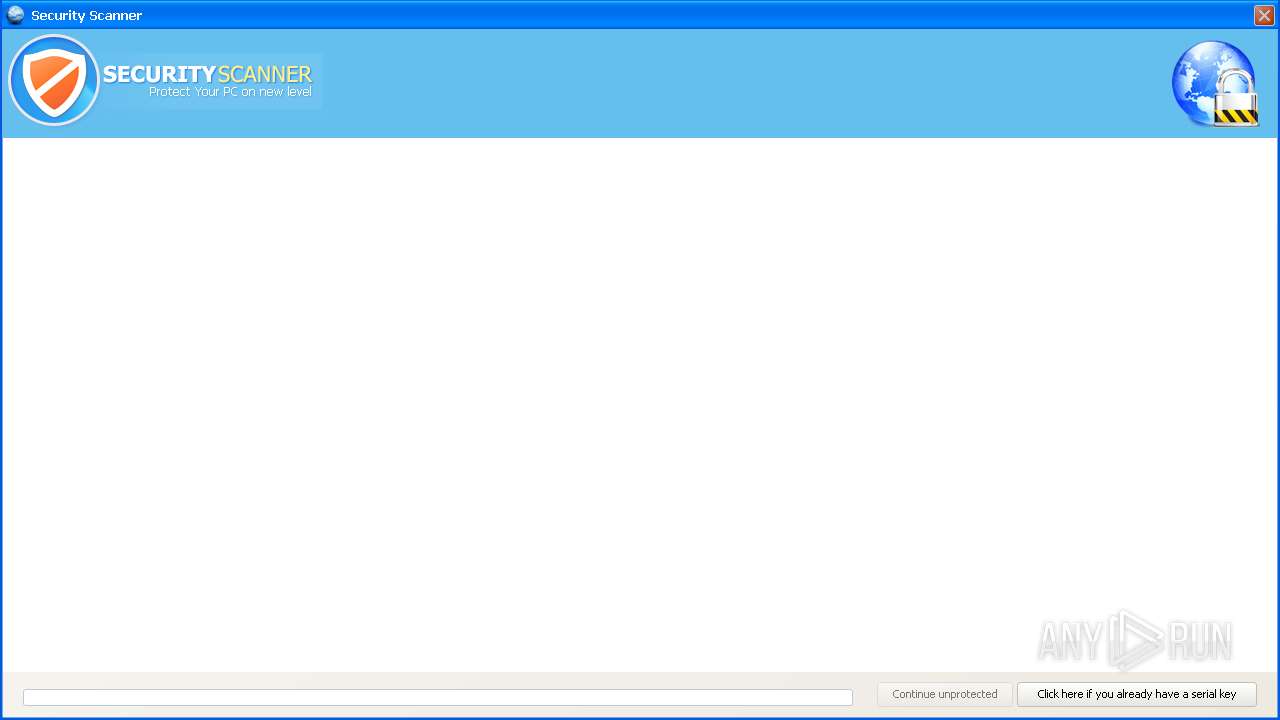
| 3456 | Endermanch@Movie.mpeg.exe | C:\Users\admin\AppData\Local\ivdmnftdt.exe | executable | |
MD5:D0DEB2644C9435EA701E88537787EA6E | SHA256:AD6CD46F373AADAD85FAB5ECDB4CB4AD7EBD0CBE44C84DB5D2A2EE1B54EB5EC3 | |||
| 2452 | WINWORD.EXE | C:\Users\admin\Desktop\~$uffeasy.rtf | binary | |
MD5:C4BCCEFAF538D7F0C53EFD838A7389E9 | SHA256:354F7BC562982C8F199DE817B30851E2801927E607B613BEA42E1B75E2E81B98 | |||
| 2020 | WINWORD.EXE | C:\Users\admin\Desktop\~$iendlyleading.rtf | binary | |
MD5:D1826C1030B4F0B691A0E3E2D766AD66 | SHA256:F8BE8D1D622C6F963F6D60916270B2CCCAD4C91356288F11FC6288542D76134C | |||
| 2452 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{068A3191-57B5-47EF-9E9A-CFF01915F6CF}.tmp | binary | |
MD5:34F0DF5BC81FF77F6C7CC7B25E8F211C | SHA256:964EE0CD51620DF5B8DD888AA6DCEFA601D4166C62A8C5A32099A762C5BBC518 | |||
| 2020 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\friendlyleading.rtf.LNK | binary | |
MD5:D0A6BBEE92C7B915AF402E650D1374CC | SHA256:B58290C958A39DF666DF1DC14BC7737A9C798C1455DF9E3D749CF28AF3AF3429 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2592 | ivdmnftdt.exe | 85.25.139.30:80 | — | Host Europe GmbH | FR | unknown |
2592 | ivdmnftdt.exe | 46.21.156.76:80 | — | HVC-AS | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |