| File name: | jailbreak-master.zip |
| Full analysis: | https://app.any.run/tasks/30fc9e80-e334-4dac-89a0-2c3f5657e076 |
| Verdict: | Malicious activity |
| Analysis date: | September 19, 2019, 10:27:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | B28DB8208018F46166CD34E2B603E5B1 |
| SHA1: | B3F3CE5BF914E944314282D8D2BB2A8F6BA249F6 |
| SHA256: | AD4B7DB6BE59E3F5A4D17087F0A48B567CF9AF49C0309E486A084C6C0A630DFC |
| SSDEEP: | 12288:5fofS7wYViDXiY0g5X/dHFCjtJORW6iZfoQS7wYViDm:5AKkYhY0wdHMJORW6OAbkYX |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2544)
- jailbreak32.exe (PID: 936)
- mmc.exe (PID: 2564)
Application was dropped or rewritten from another process
- jailbreak32.exe (PID: 936)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3524)
Reads Internet Cache Settings
- mmc.exe (PID: 2564)
Creates files in the user directory
- rundll32.exe (PID: 3292)
- notepad++.exe (PID: 2696)
INFO
Manual execution by user
- mmc.exe (PID: 3936)
- cmd.exe (PID: 3484)
- mmc.exe (PID: 2956)
- rundll32.exe (PID: 3292)
- notepad++.exe (PID: 2696)
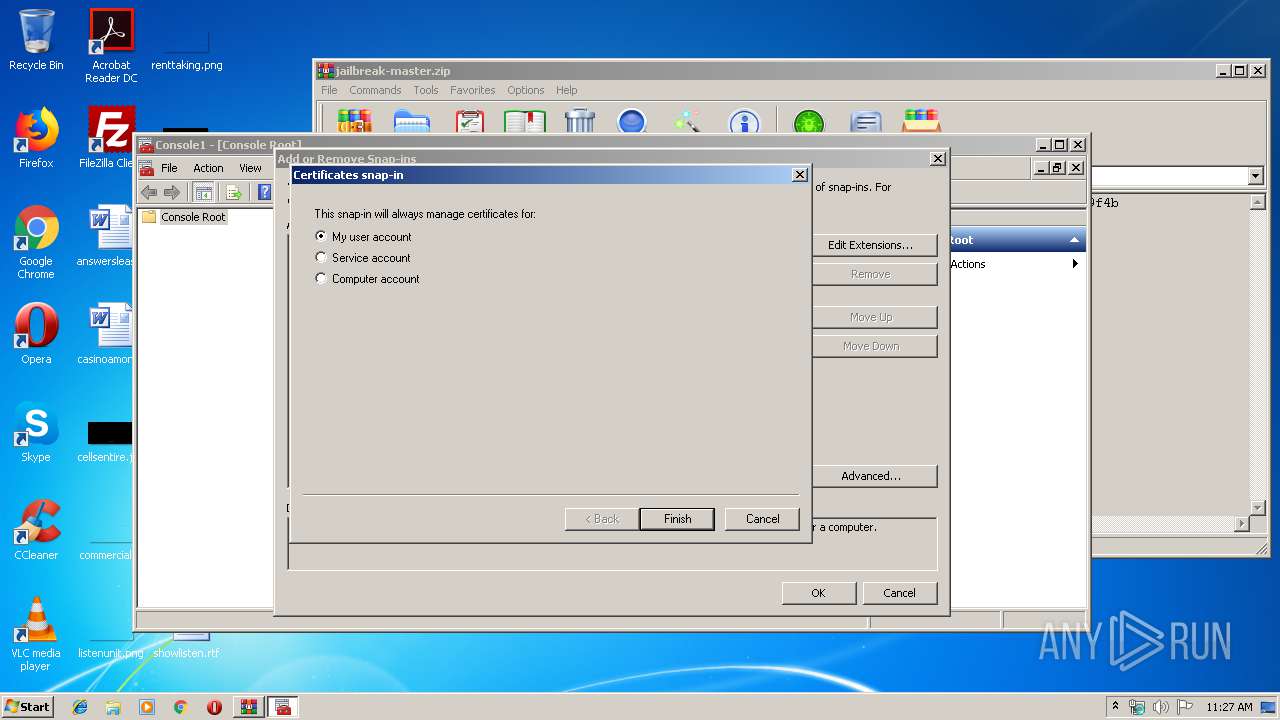
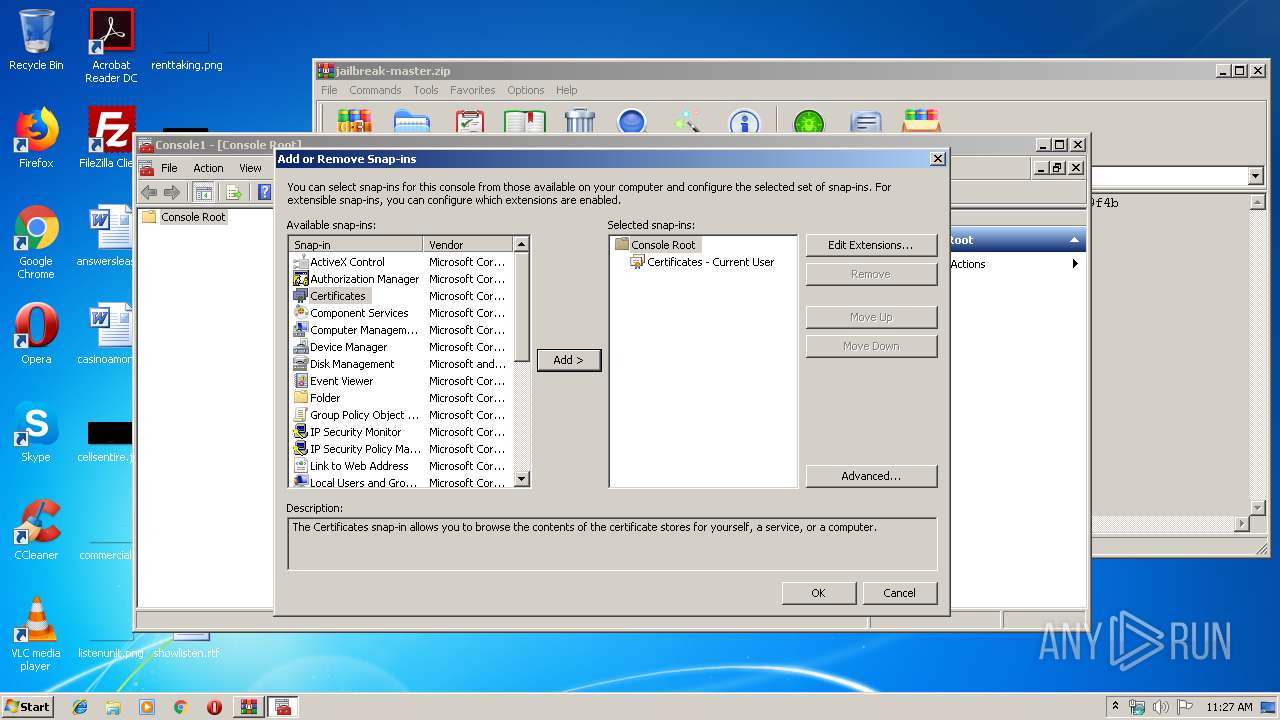
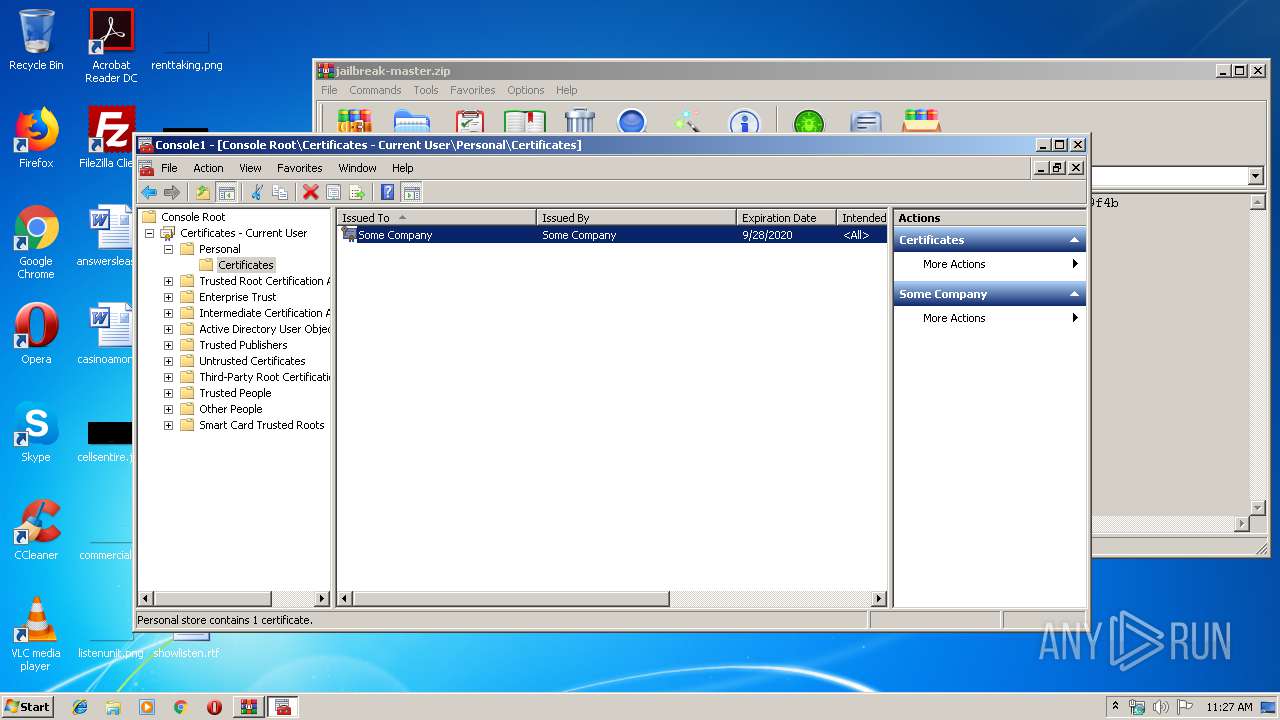
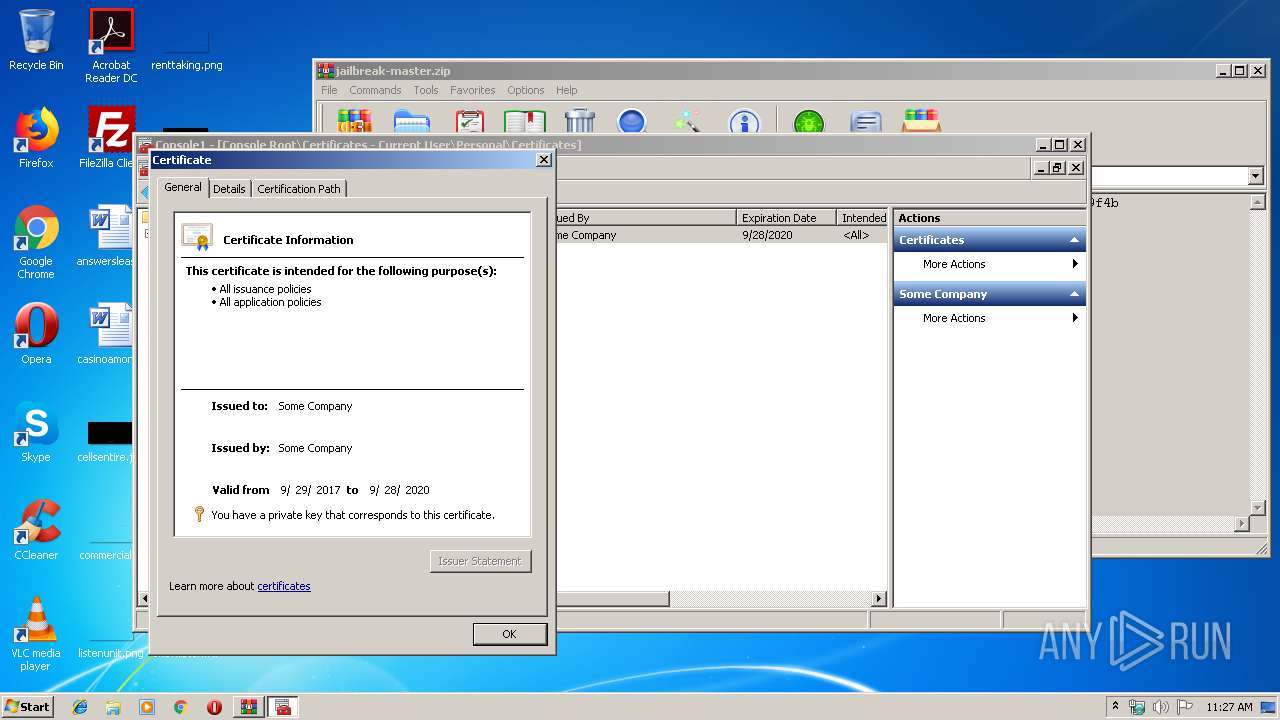
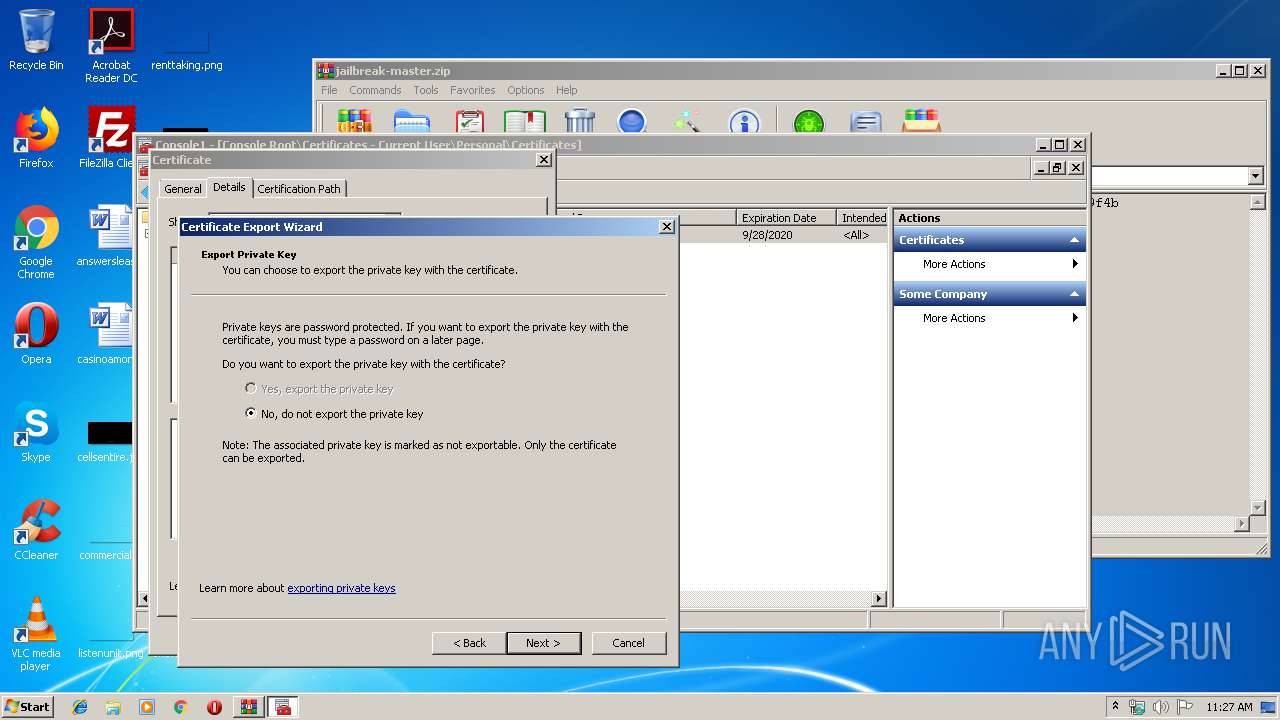
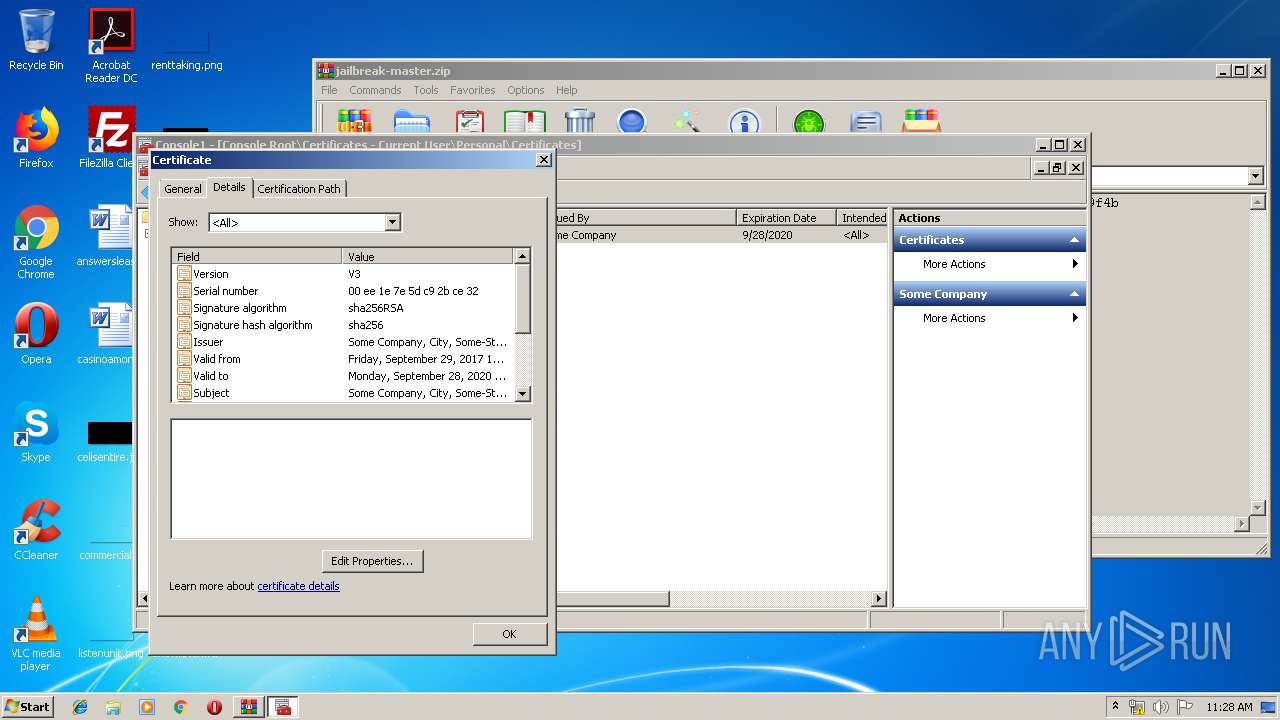
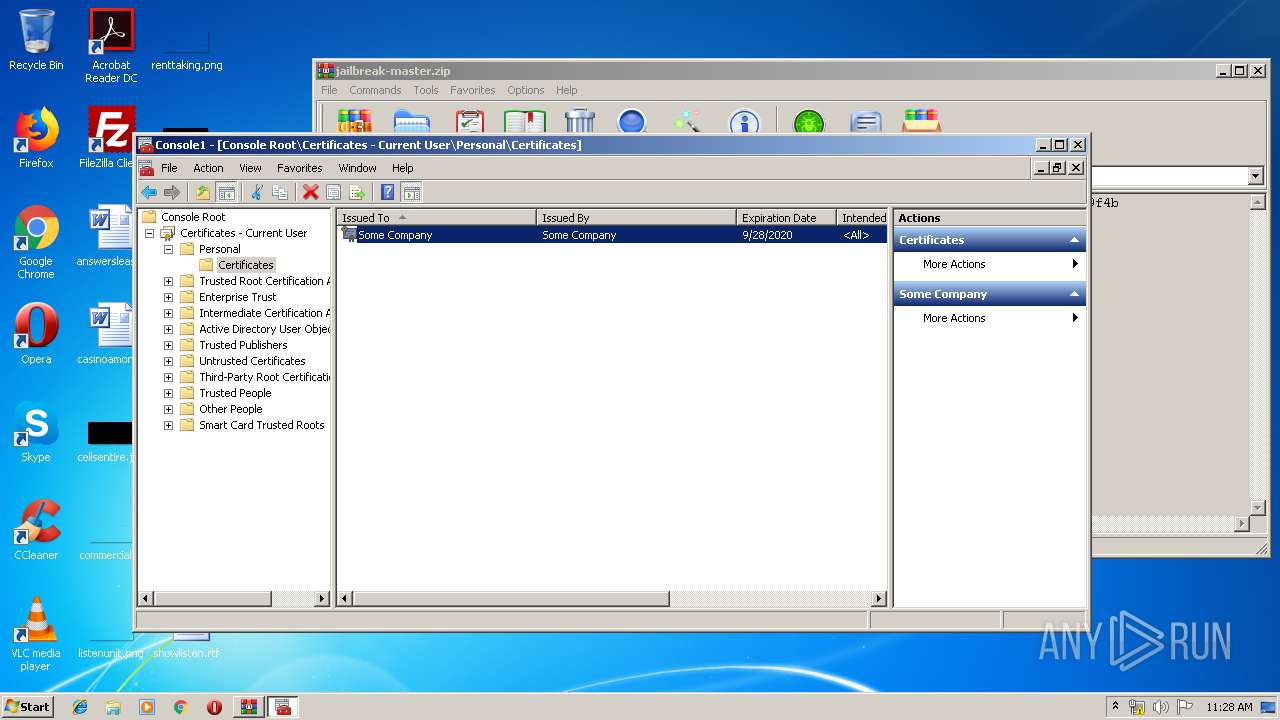
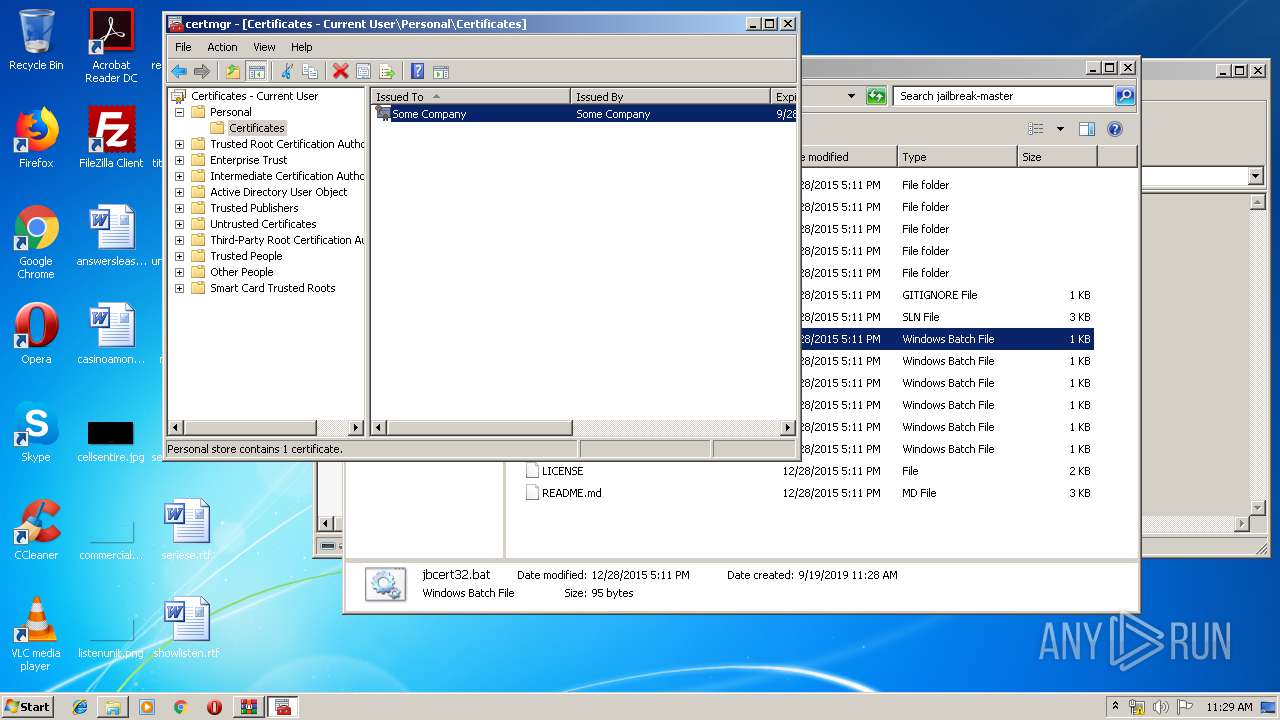
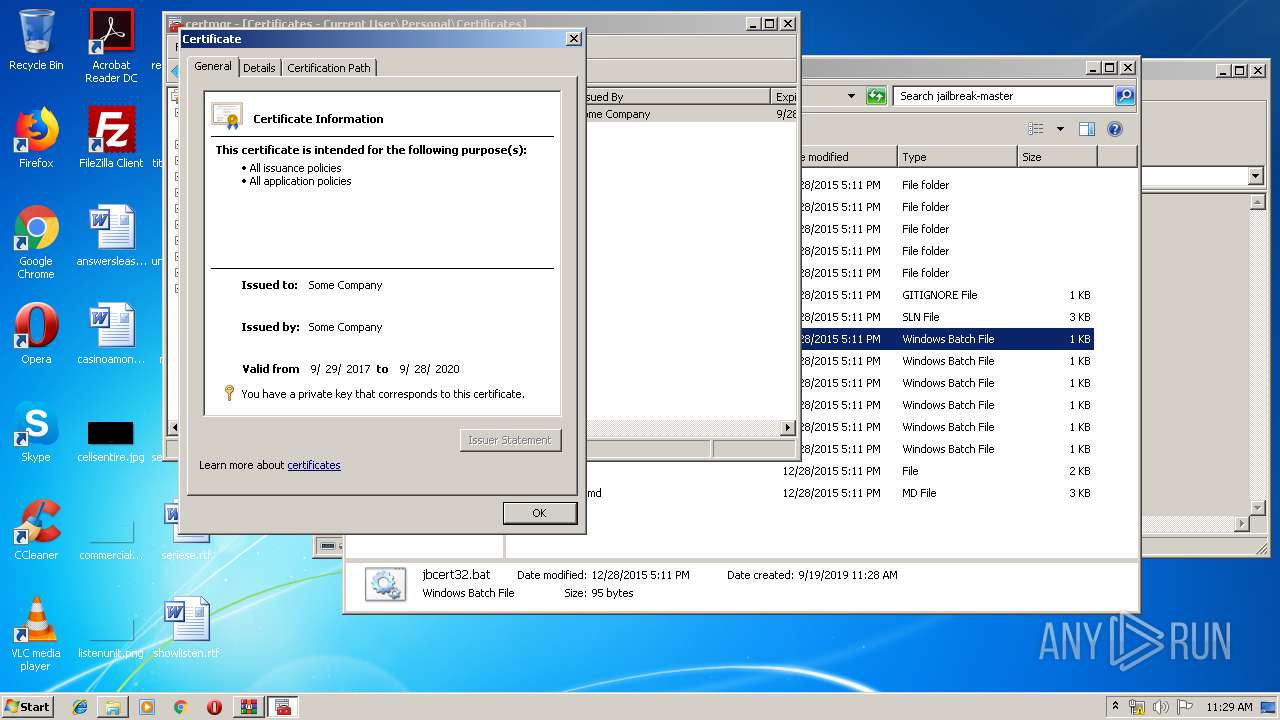
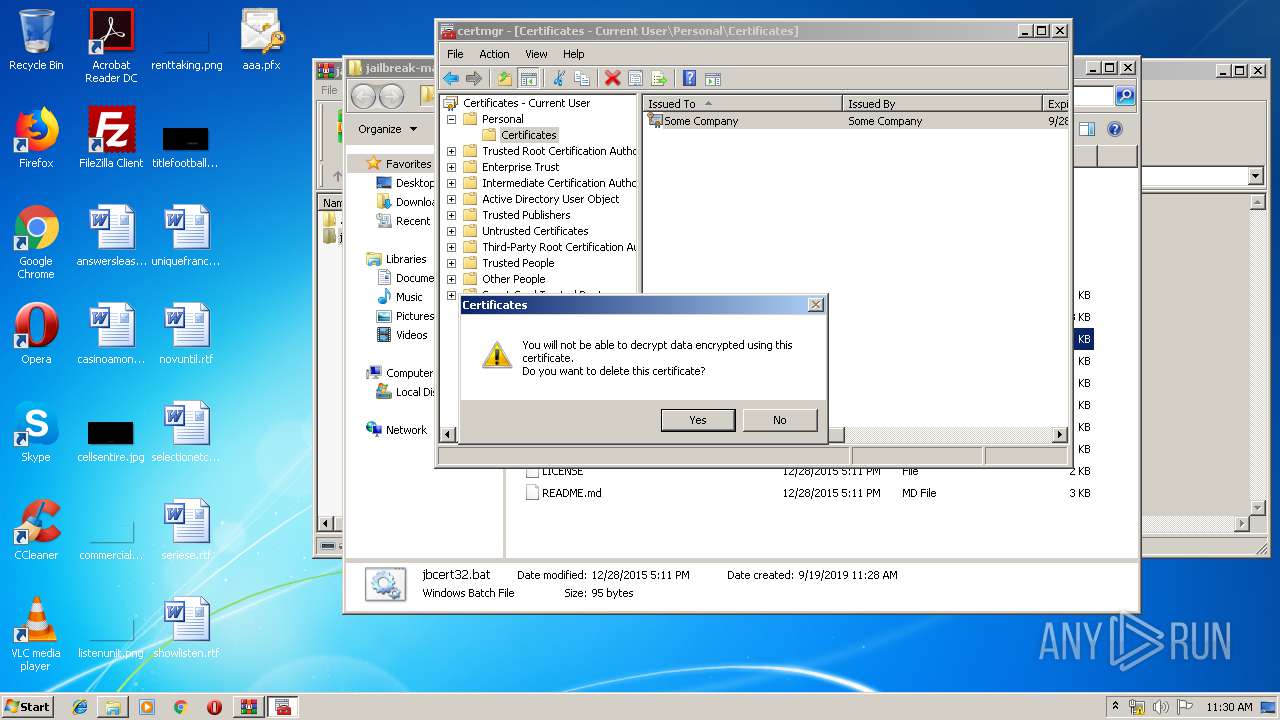
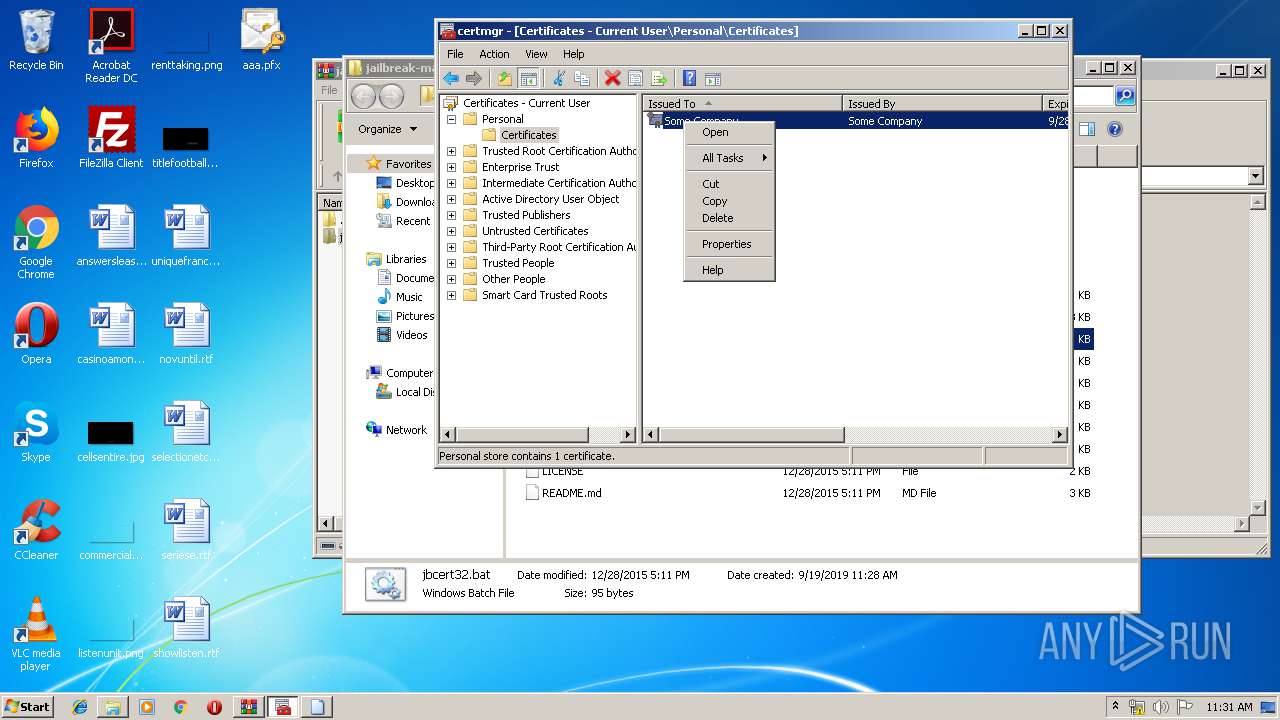
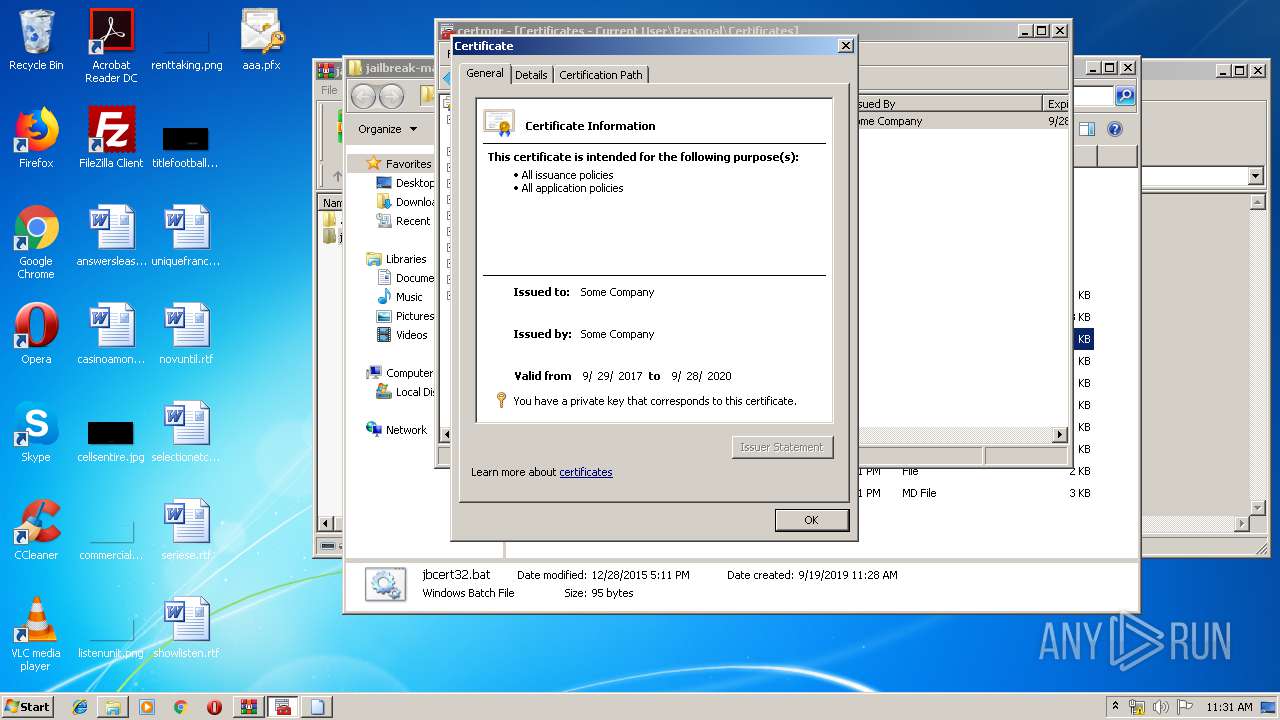
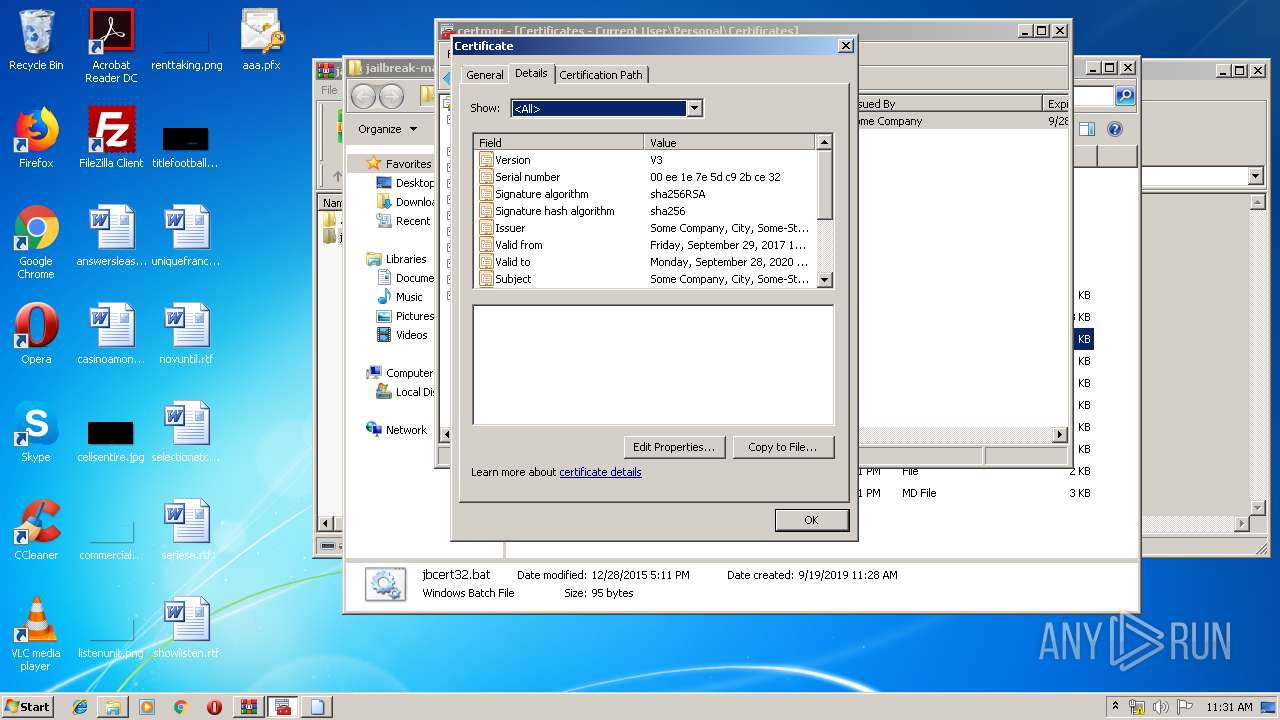
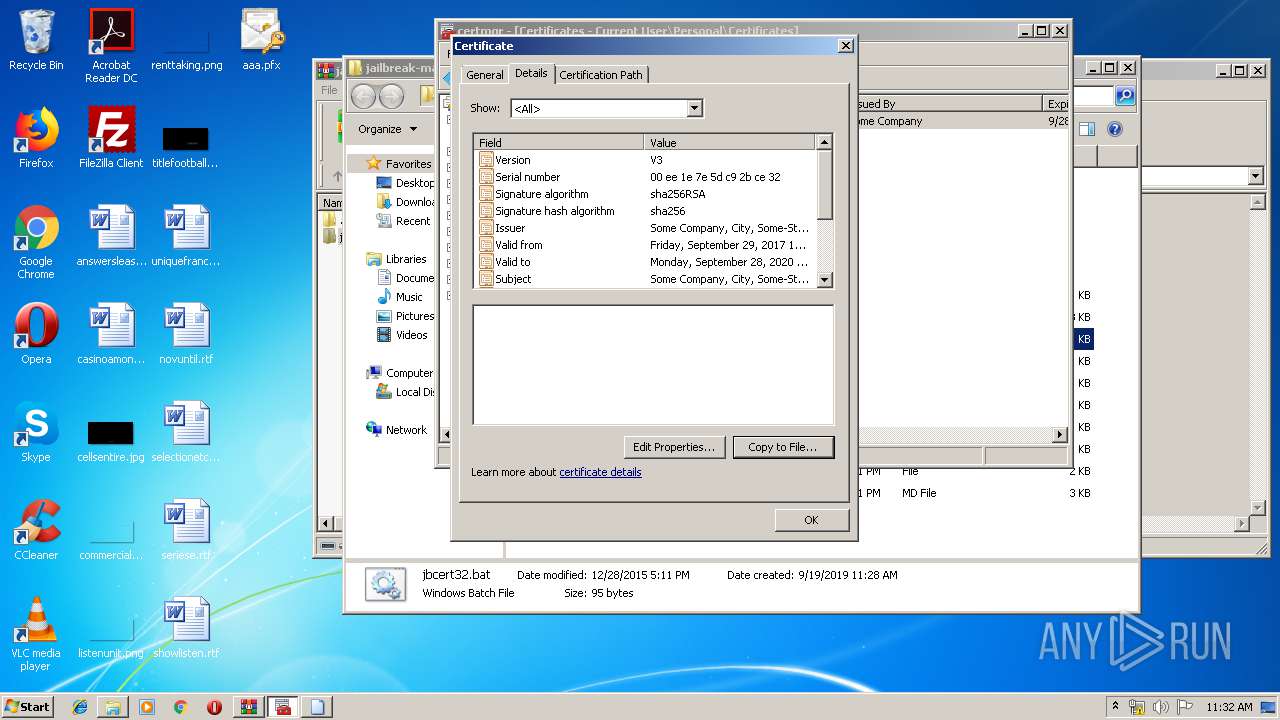
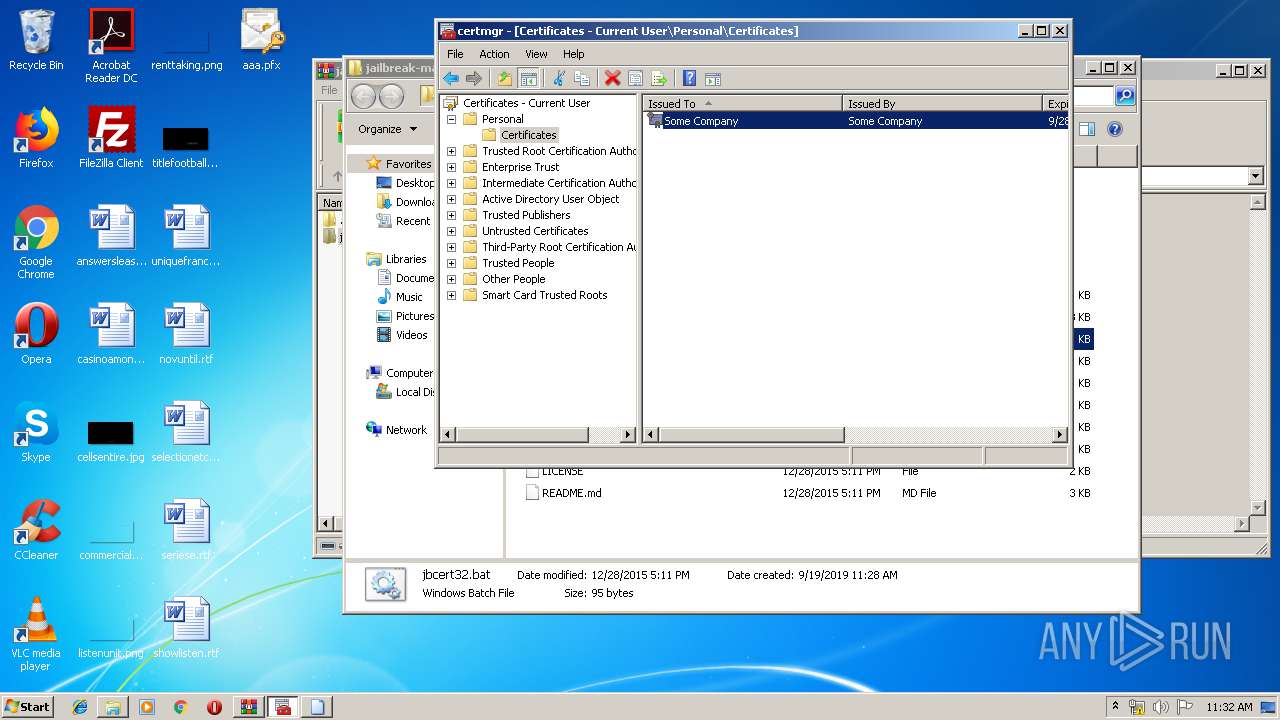
Reads settings of System Certificates
- mmc.exe (PID: 2564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2015:12:28 09:11:23 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | jailbreak-master/ |
Total processes
56
Monitored processes
10
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | jailbreak32.exe C:\Windows\system32\mmc.exe C:\Windows\system32\certmgr.msc -32 | C:\Users\admin\Desktop\jailbreak-master\binaries\jailbreak32.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2544 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2564 | C:\Windows\system32\mmc.exe C:\Windows\system32\certmgr.msc -32 | C:\Windows\system32\mmc.exe | — | jailbreak32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2696 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\aaa.pfx" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2956 | "C:\Windows\system32\mmc.exe" | C:\Windows\system32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3292 | "C:\Windows\system32\rundll32.exe" cryptext.dll,CryptExtAddPFX C:\Users\admin\Desktop\aaa.pfx | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3484 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\jailbreak-master\jbcert32.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3524 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\jailbreak-master.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3768 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 4294967295 Version: 4.1 Modules
| |||||||||||||||
| 3936 | "C:\Windows\system32\mmc.exe" | C:\Windows\system32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 706
Read events
1 423
Write events
278
Delete events
5
Modification events
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\jailbreak-master.zip | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3524) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3936) mmc.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3936) mmc.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | @mmcbase.dll,-14008 |
Value: Folder | |||
Executable files
10
Suspicious files
9
Text files
48
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
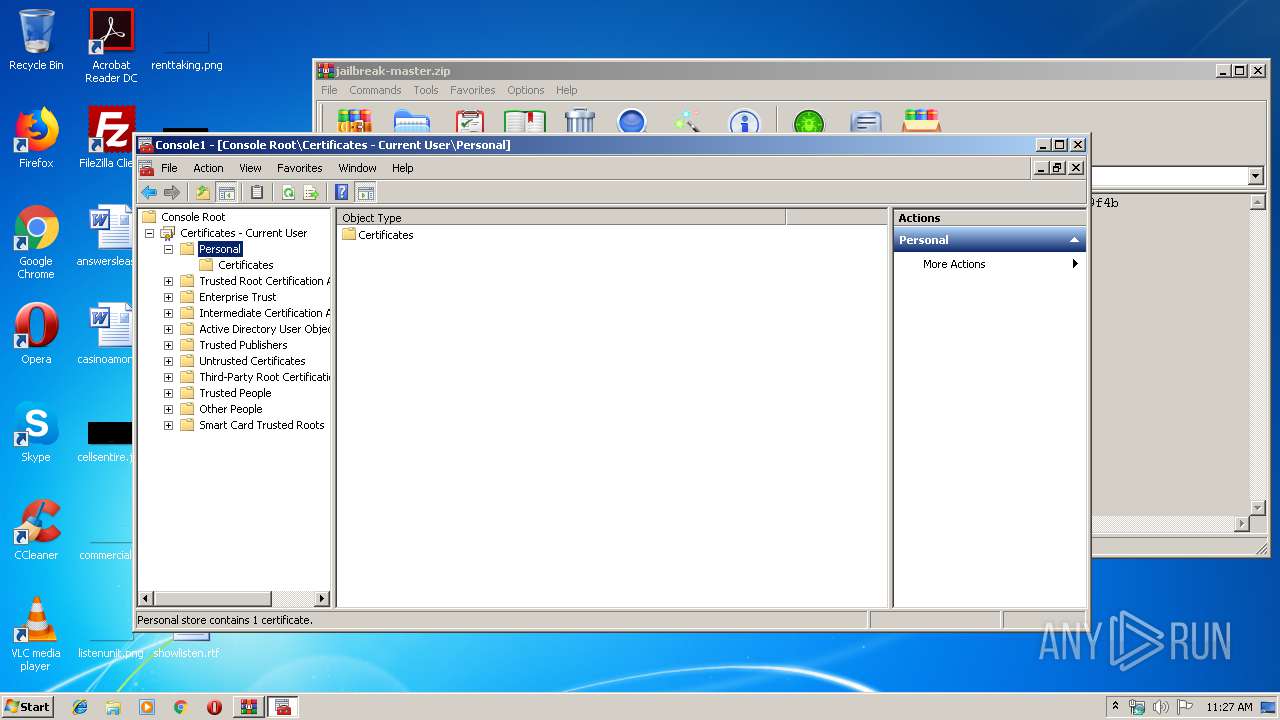
| 3936 | mmc.exe | C:\Users\admin\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\E02357FC7708441D4B0BE5F371F4B28961870F70 | binary | |
MD5:— | SHA256:— | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\binaries\EasyHook64.dll.sha256 | text | |
MD5:D3ADA1F2F27C81B86E50500B7DBA234A | SHA256:B5B1B541D75C7BE261A7B0B78218F0CBA1636B5B9EF74C66F23C9EB3E27AAC71 | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\LICENSE | text | |
MD5:D8406488EA21766D65902668C1F625F3 | SHA256:9D8CB63A8C8A1060D0162757DAE6BED58D0C66708D67E2300A834093A23F5D0A | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\.gitignore | text | |
MD5:710A4CB08A9DDD43ED04879169BD63DD | SHA256:2F6BEE2423BD7DEC17683E42B2A85A5EC446A5A22BEB70A49082BA72B638ABD2 | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\binaries\jailbreakhook32.dll.sha256 | text | |
MD5:BE5C02D593DE710A06E950BD1ACBD59B | SHA256:B597E0EA941E8C9C3DF51B8F51420C841785706CEA2D8D16C930600F51A7B583 | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\binaries\EasyHook32.dll | executable | |
MD5:F63E21C5C2D00209F6B81B39409833AA | SHA256:9344363DF85BC76135431E64F3BE606355A8C33D6EA9918573B53500537A1F2B | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\binaries\jailbreak32.exe | executable | |
MD5:8FBE0B5E85EE953A824CC952AE50D3B7 | SHA256:7E50BC71C20EFDAE915BA1647D7B8C4FDB2A189908D9861F795DEE699FFE1DE3 | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\binaries\EasyHook64.dll | executable | |
MD5:6AE73216F3E48A7C58B32C1056848F31 | SHA256:5D17FC73769E24DA1EC511B1EAC47A089F4CA6D9AAC67DC2B9BE0DDDFFA48049 | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\binaries\EasyHook32.dll.sha256 | text | |
MD5:97839BAF1FCE12D6FFAC0B2F4BE5E47B | SHA256:F553A7DE389B6FEB71282720D0A0706AF64D53A77B4105A6A8136F94F6266FFA | |||
| 3524 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3524.40028\jailbreak-master\README.md | text | |
MD5:4AAFD0BD76FF3FBA9FB78F86843510B4 | SHA256:86FD6A4F9CDD53F118044A5963F58BD77CEBBA1D369D96D990CB74936DE87A57 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3768 | gup.exe | 104.31.88.28:443 | notepad-plus-plus.org | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|