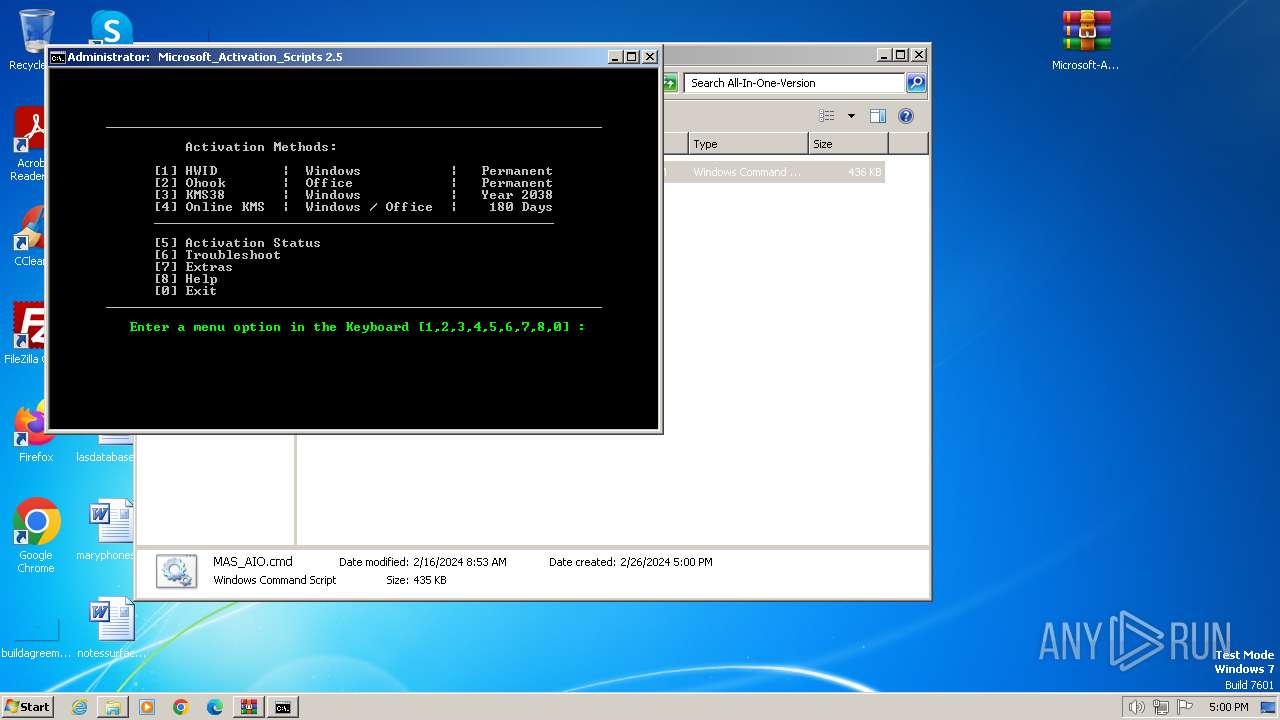
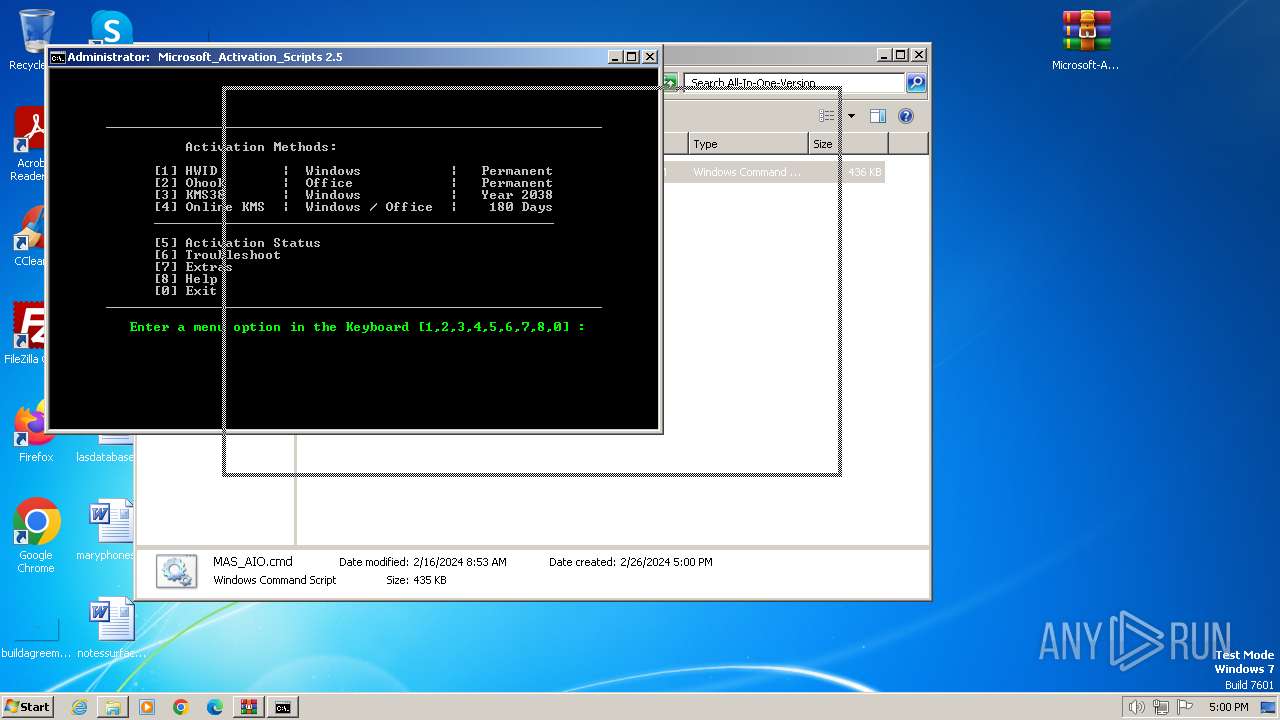
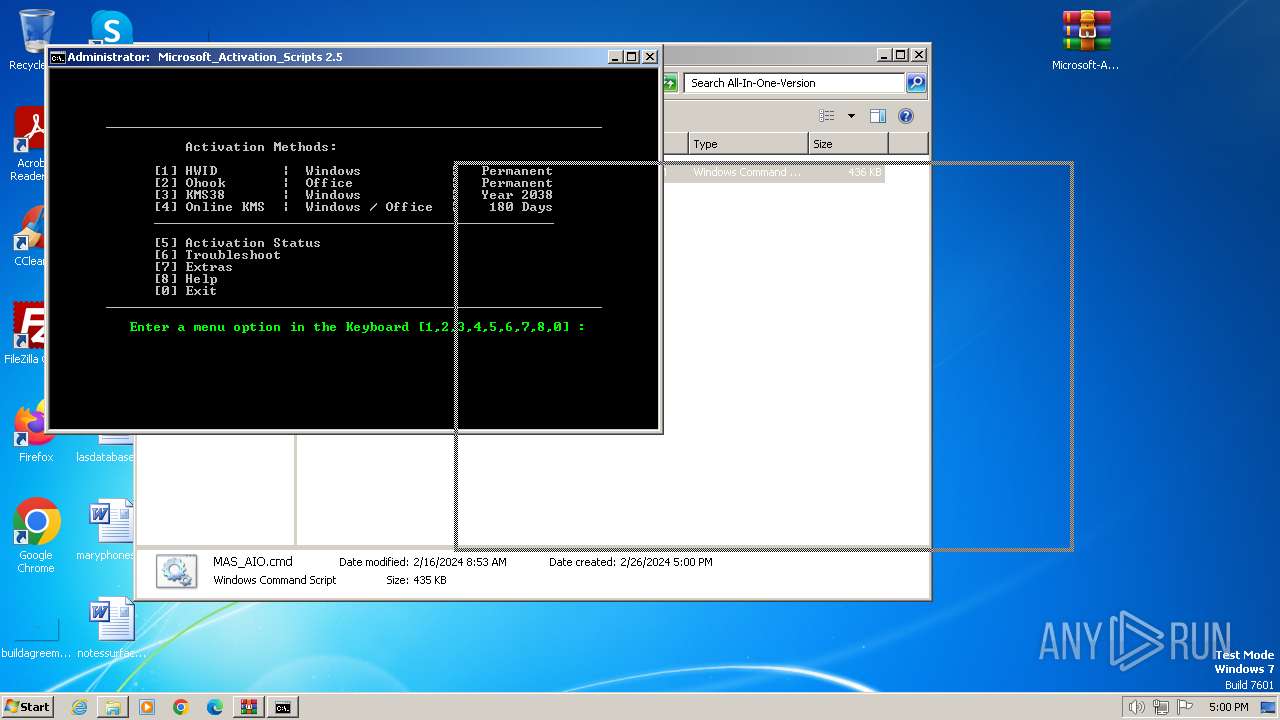
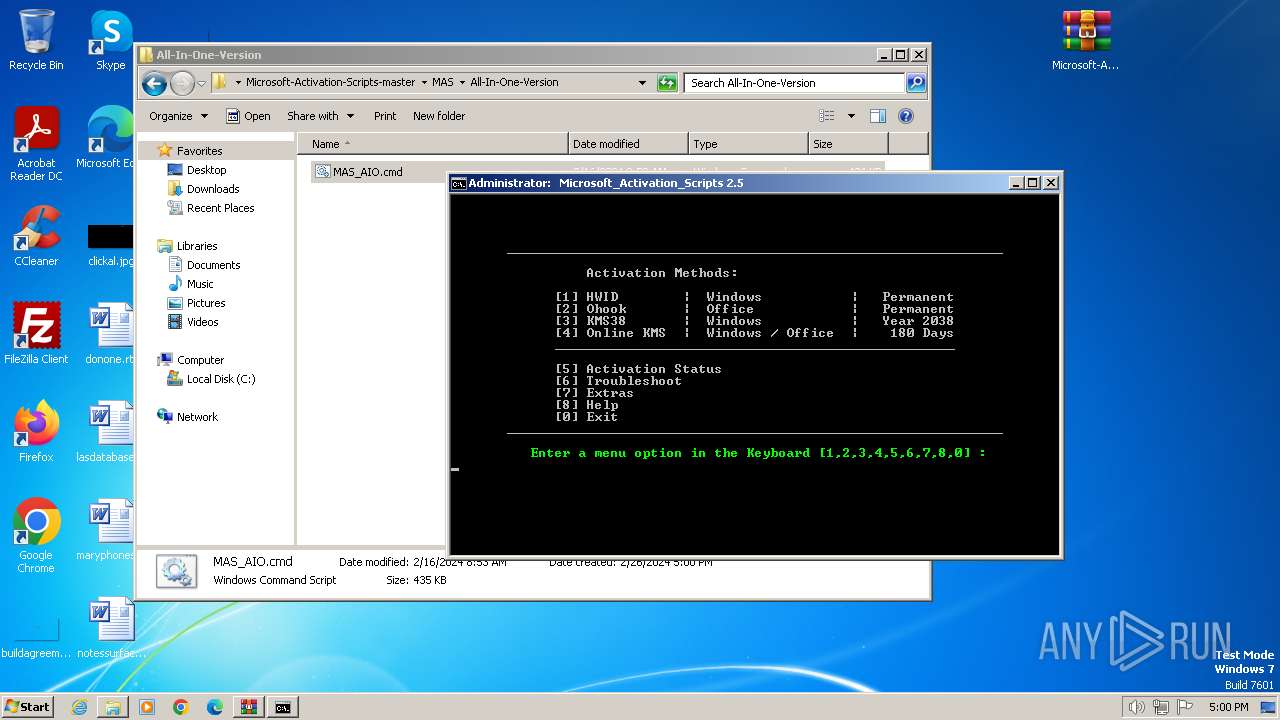
| File name: | Microsoft-Activation-Scripts-master.zip |
| Full analysis: | https://app.any.run/tasks/38db181d-109e-47e5-953c-3f471d3a98b1 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 16:59:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | EEC97E527C4E82296768769CBF05F298 |
| SHA1: | 1A4B49B1E948437E951930F43A1C31E5DB6F39EA |
| SHA256: | AD3EBD300EA84BF67CD74561803C4CC1FFB73B41172E2D430E71816D21CEE0B5 |
| SSDEEP: | 12288:oaGOzLaRAs/u6nHcCDeXfJp4j+wtZN4BYxEklp:o5OzLaRAsW6nHcCDeXfJp4j+wtZN4B8/ |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 2576)
- net.exe (PID: 2324)
- net.exe (PID: 2948)
- net.exe (PID: 2712)
SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 2576)
- cmd.exe (PID: 2440)
Executing commands from ".cmd" file
- powershell.exe (PID: 1644)
- cmd.exe (PID: 2576)
- cmd.exe (PID: 2440)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2576)
- cmd.exe (PID: 2440)
- powershell.exe (PID: 1644)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2576)
- cmd.exe (PID: 2440)
Application launched itself
- cmd.exe (PID: 2440)
- cmd.exe (PID: 2576)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2576)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2576)
Reads the Internet Settings
- WMIC.exe (PID: 3292)
- WMIC.exe (PID: 3644)
- WMIC.exe (PID: 2804)
- WMIC.exe (PID: 2320)
- WMIC.exe (PID: 3620)
- WMIC.exe (PID: 1740)
- WMIC.exe (PID: 1232)
- powershell.exe (PID: 1644)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2576)
- cmd.exe (PID: 2440)
Starts NET.EXE to map network drives
- cmd.exe (PID: 2576)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2576)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 1644)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3952)
- mode.com (PID: 2480)
- mode.com (PID: 3236)
- mode.com (PID: 2532)
Checks operating system version
- cmd.exe (PID: 2576)
- cmd.exe (PID: 2440)
Reads the computer name
- wmpnscfg.exe (PID: 3952)
Manual execution by a user
- wmpnscfg.exe (PID: 3952)
- WinRAR.exe (PID: 2964)
- cmd.exe (PID: 2440)
Reads Microsoft Office registry keys
- reg.exe (PID: 2420)
- reg.exe (PID: 2208)
- reg.exe (PID: 3516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:02:16 00:53:42 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Microsoft-Activation-Scripts-master/ |
Total processes
223
Monitored processes
175
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | find /i "C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | C:\Windows\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Microsoft\Office\16.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 268 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 324 | reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sppsvc.exe" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | C:\Windows\system32\cmd.exe /c ping -4 -n 1 updatecheck.massgrave.dev | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | find /i "Office 15" "C:\Windows\Temp\sppchk.txt" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | find /i "Office 21" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 604 | powershell.exe "&{$W=$Host.UI.RawUI.WindowSize;$B=$Host.UI.RawUI.BufferSize;$W.Height=31;$B.Height=300;$Host.UI.RawUI.WindowSize=$W;$Host.UI.RawUI.BufferSize=$B;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
13 191
Read events
13 135
Write events
38
Delete events
18
Modification events
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Microsoft-Activation-Scripts-master.zip | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
3
Text files
18
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\.gitattributes | text | |
MD5:87EB06393A7628EA5CE171C620ECB45E | SHA256:0AD46C92E5970CD411D921177BCBE77FB73A14901EE619312D6445E03E74C47F | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\MAS\All-In-One-Version\MAS_AIO.cmd | text | |
MD5:9D4FF1BD95E8767C13AB017F9BF6EF88 | SHA256:A3FF73134206AE3DC8AB309197C357B94E0711523249B406F1F4B9D1DD481F31 | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Activators\KMS38_Activation.cmd | text | |
MD5:BEF5B180D317FB7713C5B4BA9BF00BBB | SHA256:9C9B7D7ABA4CE7B0D5B30CF278DB1A1DEBD76857A6C37982D25C61BB82CF0B1D | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Activators\Ohook_Activation_AIO.cmd | text | |
MD5:F4F7B936D380CBC609AEFB1CCC02CF25 | SHA256:202BAF2D427D49E05ED0FE6586F9351DC59013CE3025D4D9DEE359AD78F5C495 | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Extract_OEM_Folder.cmd | text | |
MD5:37A2205CAF8DC4386761BDFC150997C6 | SHA256:2013EDA675C560A377753CE2AE69F2BDCDC13D17D1E1B484393FA548F8AC0C68 | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Troubleshoot.cmd | text | |
MD5:454AA88549FA33A2663CC6A400099BF7 | SHA256:B63700BB397A91AE2147D3B87F754D59A7BE4BD680B0697DE2BDC77213449D77 | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\LICENSE | text | |
MD5:5B4473596678D62D9D83096273422C8C | SHA256:E57F1C320B8CF8798A7D2FF83A6F9E06A33A03585F6E065FEA97F1D86DB84052 | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Activators\Online_KMS_Activation.cmd | text | |
MD5:38B73CE97282C793F581F52A2C26D4E0 | SHA256:ED4D9F0525C57A352E0A4F1719579D979BFCBE3D143074F3CDD46AFBC61CDB46 | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Activators\ReadMe.txt | text | |
MD5:B7FA33165116723BC2F83676FD62CC69 | SHA256:B0218B2723A32157A094EE3B852159B339EC3E01CE25AA05E19B28F55A0E9528 | |||
| 2964 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Check-Activation-Status-wmi.cmd | text | |
MD5:FC7DFD4ABBD167E7303301FA7F593CC2 | SHA256:DE2A3F3016732D6C46CEFA13BA70889EDEDA8FAE3A244DD1C507F1B80D4579F3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
updatecheck.massgrave.dev |
| unknown |
kms.zhuxiaole.org |
| unknown |
kms.moeyuuko.com |
| unknown |