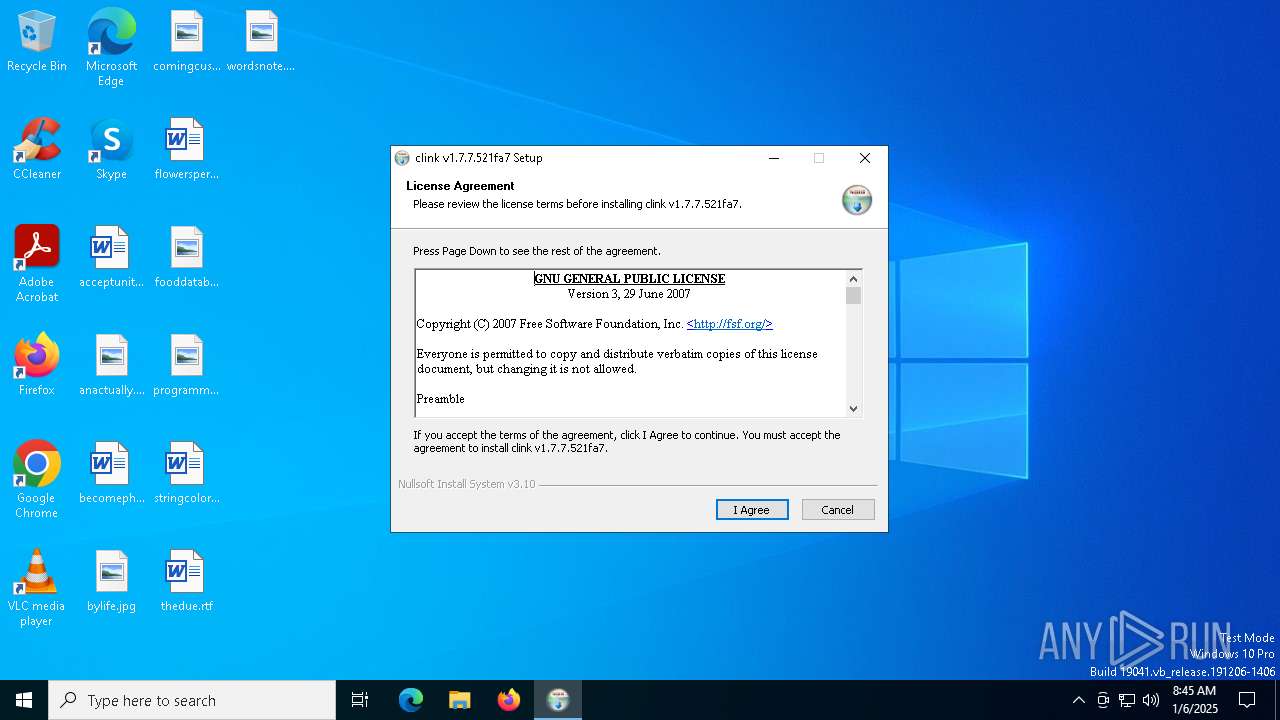
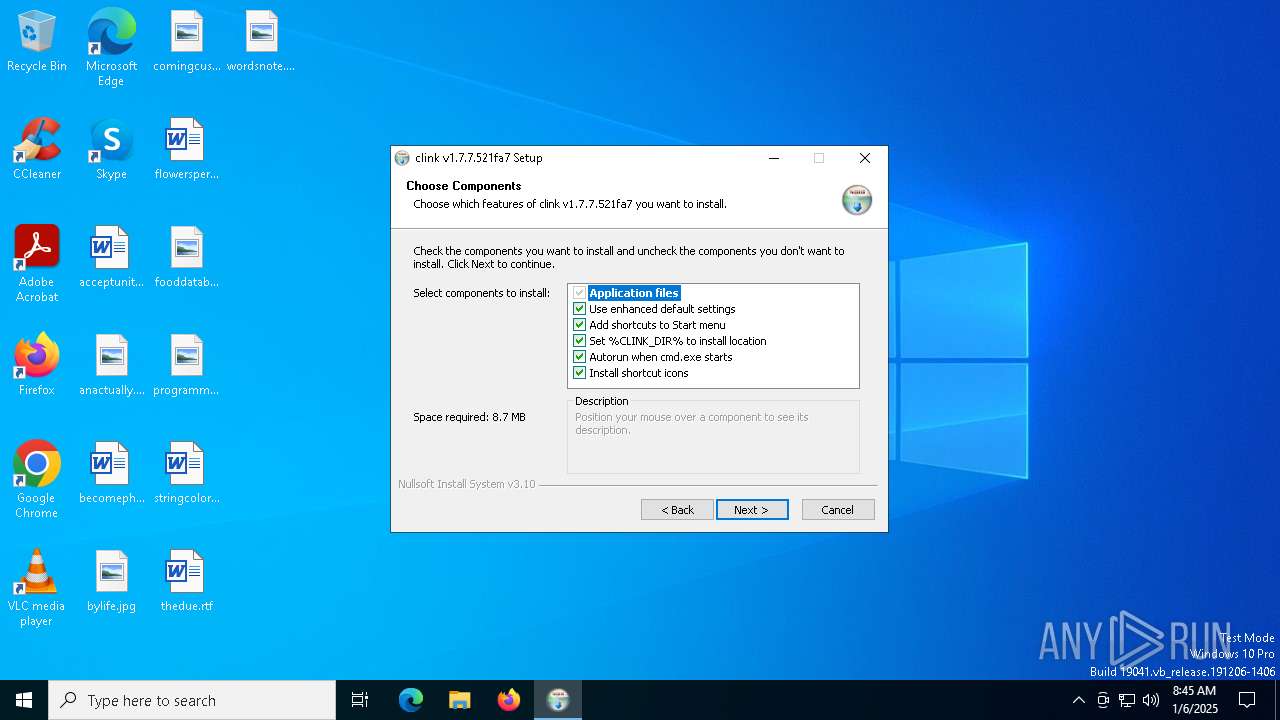
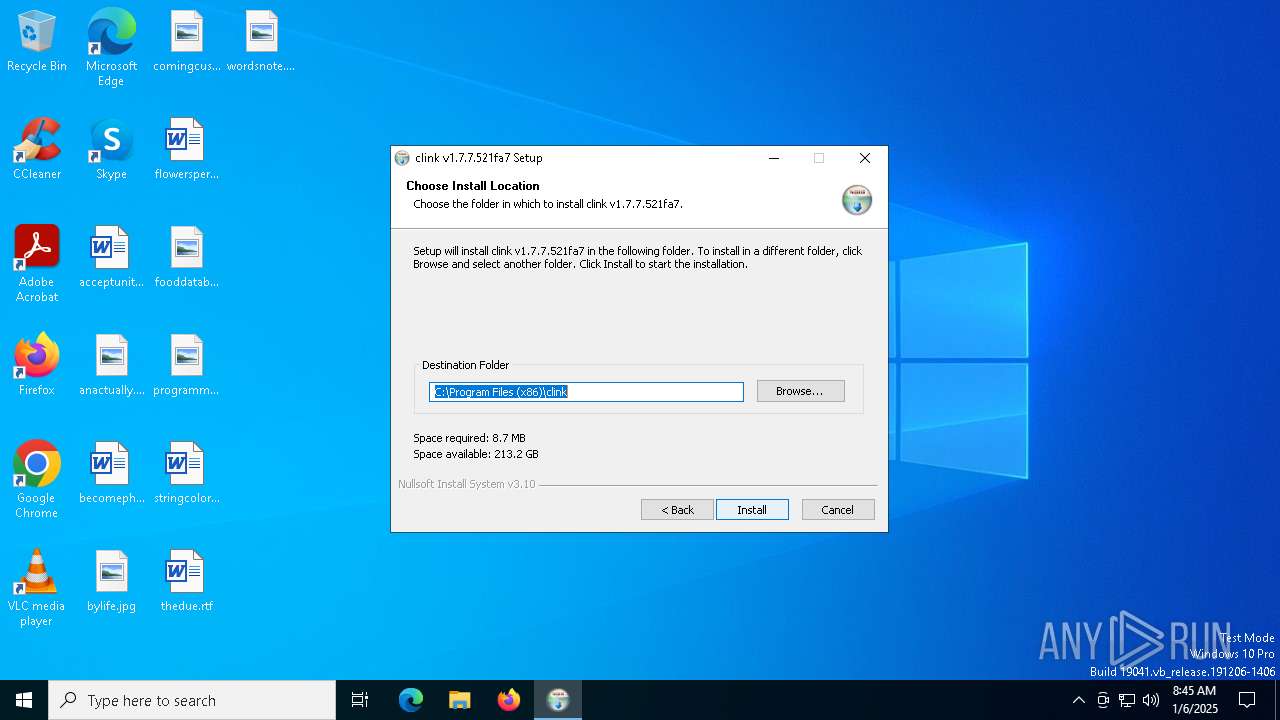
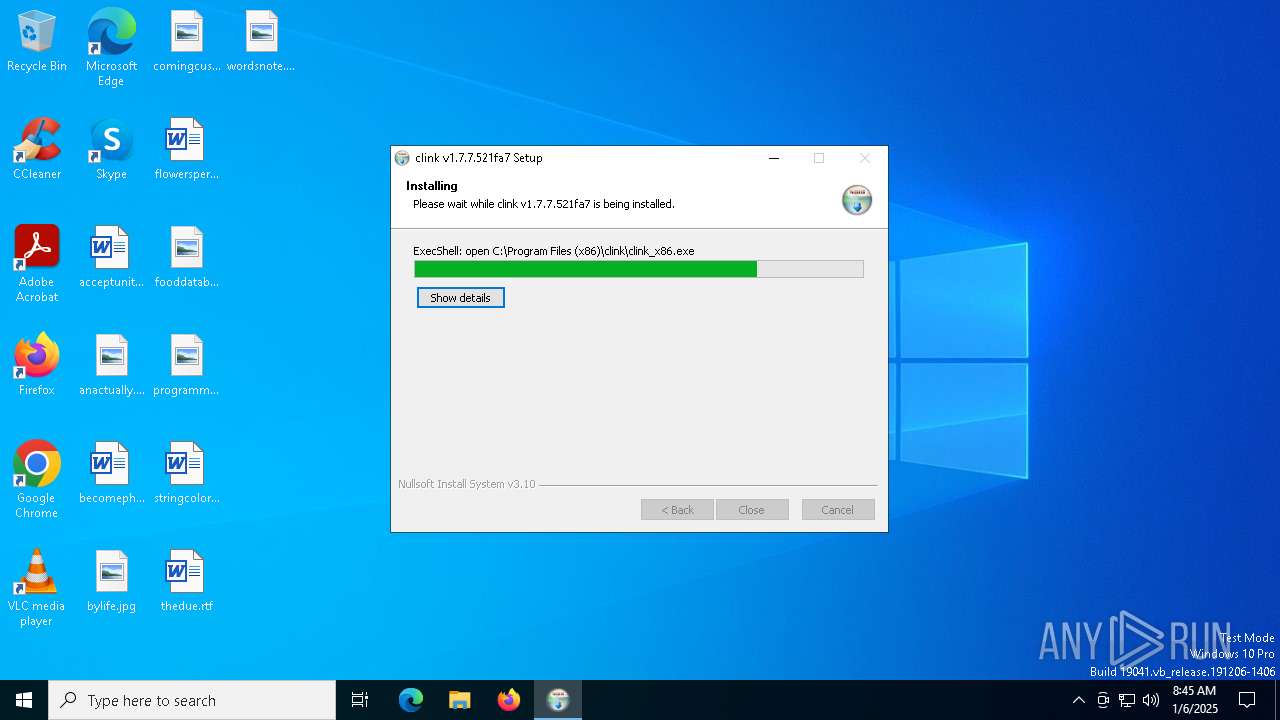
| File name: | clink.1.7.7.521fa7_setup.exe |
| Full analysis: | https://app.any.run/tasks/e48c84be-26bd-4960-8255-2bdb36d751d6 |
| Verdict: | Malicious activity |
| Analysis date: | January 06, 2025, 08:45:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | C3837671A7CAEB9F5CD5124F047F647D |
| SHA1: | 08EFFF928313584FD770E963A3DBD5808BA2162B |
| SHA256: | AD35745FEE134F26FEE83D9B890141484F74C9506FCA88C2F3FCBE029B2E7EB6 |
| SSDEEP: | 98304:ALWb2wqGTgTFkW4v430DKYexi9oy71sgIOlz7TV1QoJBwugfhtpC+Ion5jCPEgqL:zIb+u |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
Malware-specific behavior (creating "System.dll" in Temp)
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
Executable content was dropped or overwritten
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
- clink_x64.exe (PID: 2996)
Reads security settings of Internet Explorer
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
Application launched itself
- cmd.exe (PID: 6612)
- cmd.exe (PID: 2324)
Executing commands from a ".bat" file
- cmd.exe (PID: 6612)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6400)
- cmd.exe (PID: 5076)
- cmd.exe (PID: 6148)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 1344)
- powershell.exe (PID: 3612)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 3612)
Found IP address in command line
- powershell.exe (PID: 3612)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2324)
- cmd.exe (PID: 6612)
INFO
Checks supported languages
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
- clink_x86.exe (PID: 5300)
- clink_x86.exe (PID: 2676)
- clink_x64.exe (PID: 3736)
- clink_x64.exe (PID: 6856)
- clink_x64.exe (PID: 6884)
- clink_x64.exe (PID: 7032)
- clink_x64.exe (PID: 1144)
Reads the computer name
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
The sample compiled with english language support
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
- clink_x64.exe (PID: 2996)
- powershell.exe (PID: 3612)
Create files in a temporary directory
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
Creates files in the program directory
- clink.1.7.7.521fa7_setup.exe (PID: 6764)
Manual execution by a user
- cmd.exe (PID: 6612)
Checks proxy server information
- powershell.exe (PID: 1344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:19+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3665 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
150
Monitored processes
23
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1144 | "C:\Program Files (x86)\clink\\clink_x64.exe" inject --autorun --profile ~\clink | C:\Program Files (x86)\clink\clink_x64.exe | — | cmd.exe | |||||||||||
User: admin Company: Martin Ridgers, Christopher Antos Integrity Level: MEDIUM Description: Clink Exit code: 0 Version: 1.7.7.521fa7 Modules
| |||||||||||||||
| 1344 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "$ProgressPreference='SilentlyContinue' ; [System.Net.ServicePointManager]::SecurityProtocol = [System.Net.SecurityProtocolType]::Tls12 ; Invoke-WebRequest -Headers @{\"cache-control\"=\"no-cache\"} -UseBasicParsing https://api.github.com/repos/chrisant996/clink/releases/latest | Select-Object -ExpandProperty Content" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | cmd.exe /s /k ""C:\Program Files (x86)\clink\clink.bat" inject --profile "~\clink"" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2676 | "C:\Program Files (x86)\clink\clink_x86.exe" autorun install -- --profile "~\clink" | C:\Program Files (x86)\clink\clink_x86.exe | — | clink.1.7.7.521fa7_setup.exe | |||||||||||
User: admin Company: Martin Ridgers, Christopher Antos Integrity Level: HIGH Description: Clink Exit code: 0 Version: 1.7.7.521fa7 Modules
| |||||||||||||||
| 2996 | "C:\Program Files (x86)\clink\\clink_x64.exe" inject --autorun --profile ~\clink | C:\Program Files (x86)\clink\clink_x64.exe | cmd.exe | ||||||||||||
User: admin Company: Martin Ridgers, Christopher Antos Integrity Level: MEDIUM Description: Clink Exit code: 0 Version: 1.7.7.521fa7 Modules
| |||||||||||||||
| 3260 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | clink_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "$ProgressPreference='SilentlyContinue' ; [System.Net.ServicePointManager]::SecurityProtocol = [System.Net.SecurityProtocolType]::Tls12 ; Invoke-WebRequest 'https://github.com/chrisant996/clink/releases/download/v1.7.7/clink.1.7.7.521fa7.zip' -OutFile 'C:\Users\admin\AppData\Local\Temp\clink\updater\v1.7.7.zip'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3736 | "C:\Program Files (x86)\clink\\clink_x64.exe" inject --profile "~\clink" | C:\Program Files (x86)\clink\clink_x64.exe | — | cmd.exe | |||||||||||
User: admin Company: Martin Ridgers, Christopher Antos Integrity Level: MEDIUM Description: Clink Exit code: 1 Version: 1.7.7.521fa7 Modules
| |||||||||||||||
| 4684 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "Get-Host | Select-Object Version" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 817
Read events
13 801
Write events
16
Delete events
0
Modification events
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | DisplayName |
Value: Clink v1.7.7 | |||
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\clink\clink_uninstall_1.7.7.521fa7.exe | |||
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | Publisher |
Value: Christopher Antos | |||
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\clink\clink.ico,0 | |||
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | URLInfoAbout |
Value: http://chrisant996.github.io/clink | |||
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | HelpLink |
Value: http://chrisant996.github.io/clink | |||
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\clink | |||
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | DisplayVersion |
Value: 1.7.7 | |||
| (PID) Process: | (6764) clink.1.7.7.521fa7_setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\clink_chrisant996 |
| Operation: | write | Name: | EstimatedSize |
Value: 8666 | |||
| (PID) Process: | (2676) clink_x86.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wow6432Node\Microsoft\Command Processor |
| Operation: | write | Name: | AutoRun |
Value: "C:\Program Files (x86)\clink\clink.bat" inject --autorun --profile ~\clink | |||
Executable files
12
Suspicious files
11
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\clink_dll_x64.dll | executable | |
MD5:3FAD74F4BCB6FEF36ED4F5E240402524 | SHA256:28CF42B2C9BFDCE9186ADC5D976EB8A8A7E58EB0A208F7C43342F29F288D9859 | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\clink_x64.exe | executable | |
MD5:60257CE3DF14E18A26A7D731D154E4D2 | SHA256:301C2F6CFB2B5961F5C5A320F80D94180B32C6E7C329A2A58BA6F3579E5227DA | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\clink.ico | image | |
MD5:4224AAD900086608D923F50EF78F6F34 | SHA256:D30A814738D1BC32C0C6F97B590F58B587A4FB486A3E9940904DDB14AEE91F5D | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\clink.html | html | |
MD5:E9201C54C1AA3F8A45D0ACE5678439CF | SHA256:1305706C437ABF362C494FA4A14A9AB627600411807D63A6B448429330091AE9 | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\themes\Dracula.clinktheme | text | |
MD5:8D86628E2AEE78A999621D1A8F3917DD | SHA256:64CFD1E033F75CE9A2ACCCF0FA7B2DD825908B6FF394BFCAAAF5D93CD03CA2E2 | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\themes\Plain.clinktheme | text | |
MD5:6D70FC802BB64A00B66254D05F1520BF | SHA256:C8498543808F1227D01DA8DAF42EBA558F084B2C3A09B2828BBCD7EDD2D01052 | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\themes\Tomorrow.clinktheme | text | |
MD5:6F43A5727899B4ACEABD6E0F5CDE7DBA | SHA256:D3D729FD86B64DD763EEB1F13BA4B3953C9834A1016D5CA10AD77AE4044BAC37 | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\themes\Enhanced Defaults.clinktheme | text | |
MD5:A11DC0F446EAE8C92DF8B1D3C4A76740 | SHA256:82E70E6019577C0788A864485126DED59E059A3A5EFBEB783193A1ECBBB42E92 | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\themes\Tomorrow Night Eighties.clinktheme | text | |
MD5:71A374B76220FDFC983F9473FE18EB84 | SHA256:EBA409441B83A7EAE8C63F0783918A1FCBC125769EB4FE49BC19E3EFF981FEE2 | |||
| 6764 | clink.1.7.7.521fa7_setup.exe | C:\Program Files (x86)\clink\themes\Solarized Dark.clinktheme | text | |
MD5:7ED8396238FE8F5F5DCAF49FF2880E60 | SHA256:4ABA097CCCA0ECDF759C0EB209575073042443F483C55061F2703DE609B255FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
46
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7076 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6184 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7076 | SIHClient.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 23.56.254.14:443 | go.microsoft.com | Mobile Telecommunications Company | KW | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |