| download: | /LavaGang/MelonLoader/releases/download/v0.6.1/MelonLoader.Installer.exe |
| Full analysis: | https://app.any.run/tasks/b38affac-541a-452f-aad0-c8115583456b |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2023, 01:49:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 54DFF09CC998ADAC8E2B325FD2714230 |
| SHA1: | 31592045226B7546CEBC871B13941DCE602DCE3B |
| SHA256: | AD3015FCF72AF7FA32386E2D584DDC00BA10FEF82E84B4F57ADAFB6183177542 |
| SSDEEP: | 12288:LL2odKsoH3msuTmlOIq76xb35zdtKTKKpKKMpg:lO5gEMWx35pg |
MALICIOUS
Drops the executable file immediately after the start
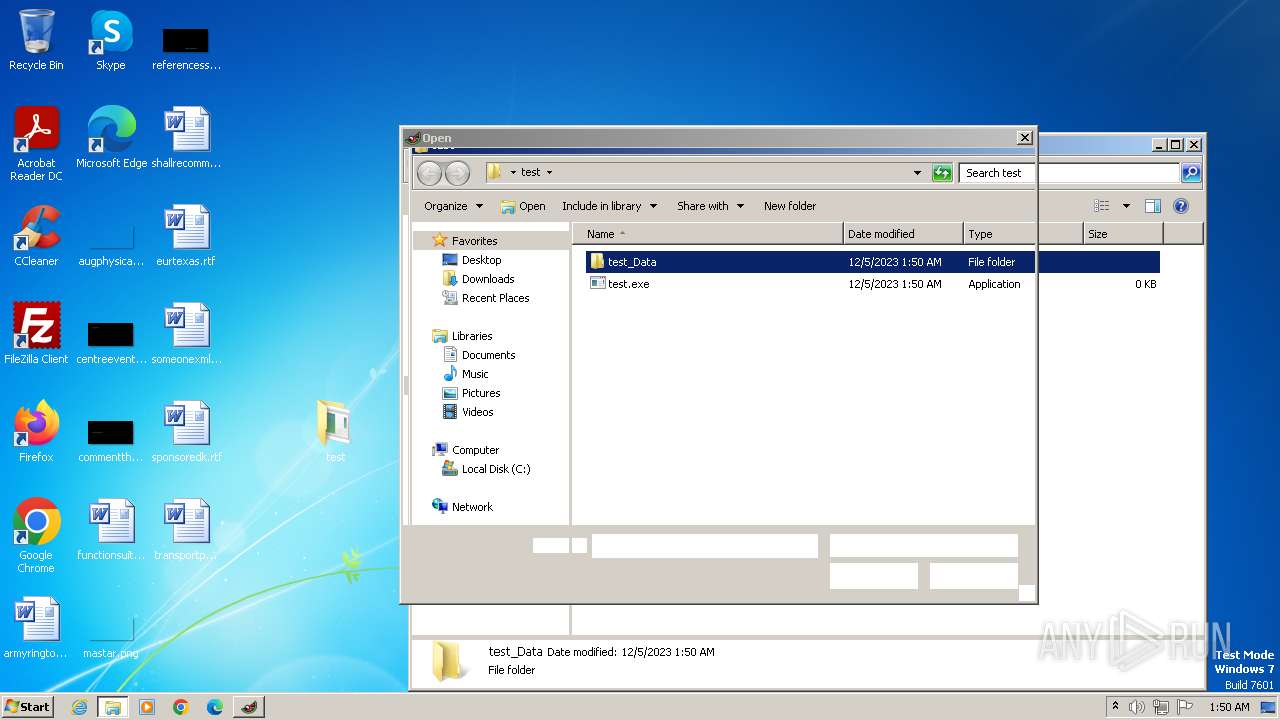
- MelonLoader.Installer.exe (PID: 3476)
SUSPICIOUS
Reads settings of System Certificates
- MelonLoader.Installer.exe (PID: 3476)
Reads the Internet Settings
- MelonLoader.Installer.exe (PID: 3476)
Process drops legitimate windows executable
- MelonLoader.Installer.exe (PID: 3476)
The process creates files with name similar to system file names
- MelonLoader.Installer.exe (PID: 3476)
INFO
Checks supported languages
- MelonLoader.Installer.exe (PID: 3476)
- wmpnscfg.exe (PID: 1640)
Reads the computer name
- MelonLoader.Installer.exe (PID: 3476)
- wmpnscfg.exe (PID: 1640)
Manual execution by a user
- wmpnscfg.exe (PID: 1640)
Creates files or folders in the user directory
- MelonLoader.Installer.exe (PID: 3476)
Create files in a temporary directory
- MelonLoader.Installer.exe (PID: 3476)
Reads Environment values
- MelonLoader.Installer.exe (PID: 3476)
Reads the machine GUID from the registry
- MelonLoader.Installer.exe (PID: 3476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2049:05:06 19:08:35+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 696832 |
| InitializedDataSize: | 40960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xac18e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.8.0 |
| ProductVersionNumber: | 3.0.8.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | MelonLoader Installer |
| CompanyName: | discord.gg/2Wn3N2P |
| FileDescription: | MelonLoader Installer |
| FileVersion: | 3.0.8 |
| InternalName: | MelonLoader.Installer.exe |
| LegalCopyright: | Created by Lava Gang |
| LegalTrademarks: | discord.gg/2Wn3N2P |
| OriginalFileName: | MelonLoader.Installer.exe |
| ProductName: | MelonLoader Installer |
| ProductVersion: | 3.0.8 |
| AssemblyVersion: | 3.0.8.0 |
Total processes
44
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1640 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3476 | "C:\Users\admin\AppData\Local\Temp\MelonLoader.Installer.exe" | C:\Users\admin\AppData\Local\Temp\MelonLoader.Installer.exe | explorer.exe | ||||||||||||
User: admin Company: discord.gg/2Wn3N2P Integrity Level: MEDIUM Description: MelonLoader Installer Exit code: 4294967295 Version: 3.0.8 Modules
| |||||||||||||||
Total events
9 524
Read events
9 379
Write events
144
Delete events
1
Modification events
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 07000000020000000100000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000070000000100000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (3476) MelonLoader.Installer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
Executable files
198
Suspicious files
7
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\AppData\Local\Temp\tmp4DF0.tmp | compressed | |
MD5:78879790E177340473660937C890586D | SHA256:6A233EB9FDAC98C6939F05F0C0DE5437DF18800B5EDBFA1EA0E5B3B691917B0A | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\MelonLoader\Dependencies\CompatibilityLayers\0Harmony.dll | executable | |
MD5:E6EB51B5F3562915B2596E0A627A2727 | SHA256:4A5CA12CD7BEFF7D4404D3E20627C378F36127F0E96E160B007601F19A6D1F8C | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\version.dll | executable | |
MD5:942A441AD7F1E646C2DD9CFC7A4318CB | SHA256:AC11F17E7E37CDDEC45DF6CF29FA7C67150D11CF88BEAA5AFAA1F12FDB9886F8 | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\MelonLoader\Dependencies\Bootstrap.dll | executable | |
MD5:5CC57CCBD2BB7842D52B1AF317C18950 | SHA256:ADB15413F0B4B5E80E86E30828EDFFA5BCA3436D805E53310A5FFB485C2A1F06 | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\MelonLoader\Dependencies\CompatibilityLayers\IPA.dll | executable | |
MD5:6D71DF4E72132111DF34812426C53E99 | SHA256:53A08A3F8F5C5D63CA8A2A3E6C5560A2C776E422966D86777E0B754B564BB53E | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\MelonLoader\MelonLoader.xml | xml | |
MD5:1DBDCB8CB53DC7DCDAA0F65AE49ED124 | SHA256:009549BAF726A2B5DA251123EEEC374F6EF89E51179C71A100635688C9B02E33 | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\dobby.dll | executable | |
MD5:C37027B9A39C205A9627C1EBEF2C5B4D | SHA256:61456FA9EA8400266335C081CD6995C912F6AB9EF3B798493CB0F17E203052A4 | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\NOTICE.txt | text | |
MD5:1D147069683FEDE444A8B01B52024898 | SHA256:081981B2760E887CD845AC478BEF503B3B61269B0F3C42007800FA6E00078258 | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\MelonLoader\Dependencies\CompatibilityLayers\Mono.Cecil.Mdb.dll | executable | |
MD5:1C6ACA0F1B1FA1661FC1E43C79334F7C | SHA256:411F8ED8C49738FA38A56ED8F991D556227D13602E83186E66AE1C4F821C940B | |||
| 3476 | MelonLoader.Installer.exe | C:\Users\admin\Desktop\test\MelonLoader\Dependencies\CompatibilityLayers\Mono.Cecil.Rocks.dll | executable | |
MD5:6E7F0F4FFF6C49E3F66127C23B7F1A53 | SHA256:2E2623319BDC362974A78EA4A43F4893011EC257884D24267F4594142FCD436E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
7
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3476 | MelonLoader.Installer.exe | 140.82.121.6:443 | api.github.com | GITHUB | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3476 | MelonLoader.Installer.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
3476 | MelonLoader.Installer.exe | 185.199.109.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.github.com |
| whitelisted |
github.com |
| shared |
objects.githubusercontent.com |
| shared |