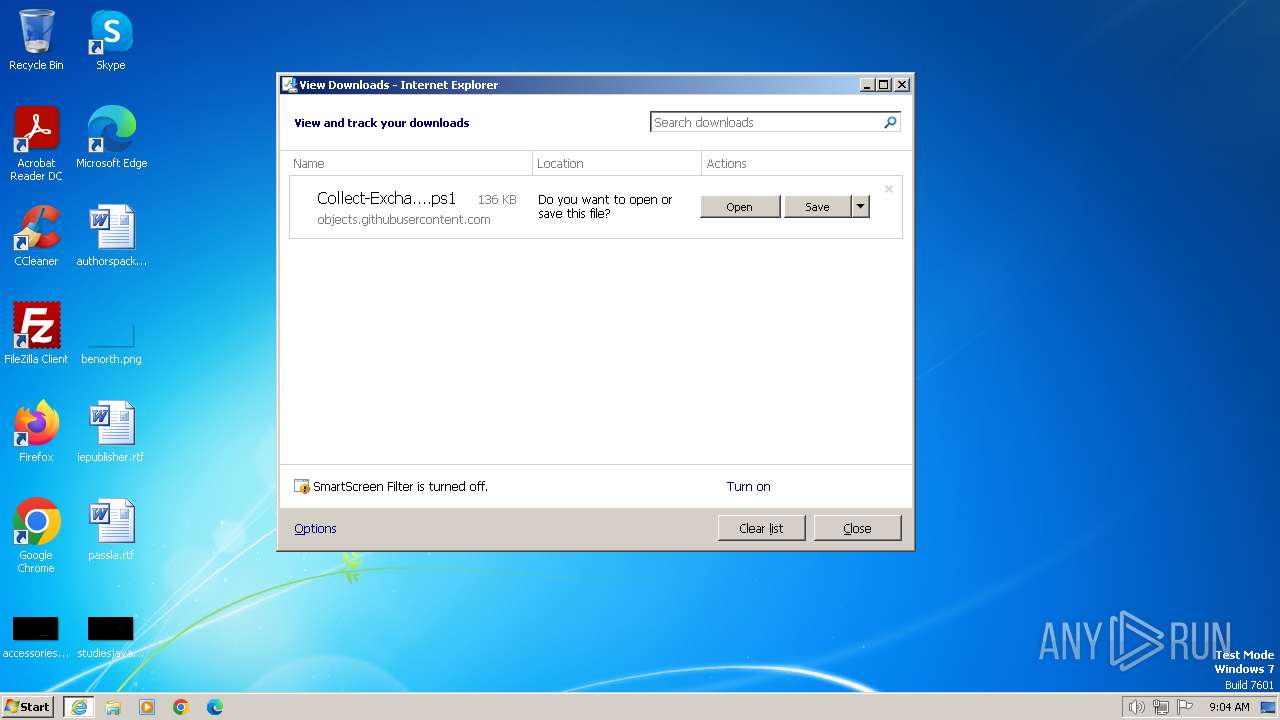
| URL: | https://github.com/jpmessaging/CollectExchangeInfo/releases/download/v2023-09-05/Collect-ExchangeInfo.ps1 |
| Full analysis: | https://app.any.run/tasks/f3c7fcde-4fb0-4ae6-b3fb-4636a93fdefe |
| Verdict: | Malicious activity |
| Analysis date: | January 05, 2024, 09:04:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1CEF5D767FD50E9AE417C9416E4043A3 |
| SHA1: | 8BAF7012B53A078EED2BE11E14C2D59FB9DB9093 |
| SHA256: | AD22A8C895CF8250474202E77C01EDEF54DD2DB3BF8B57327971B3321F99AD3E |
| SSDEEP: | 3:N8tEd/iz3J/6nsBhrkC9Z/uWnsI:2uMzIUoe |
MALICIOUS
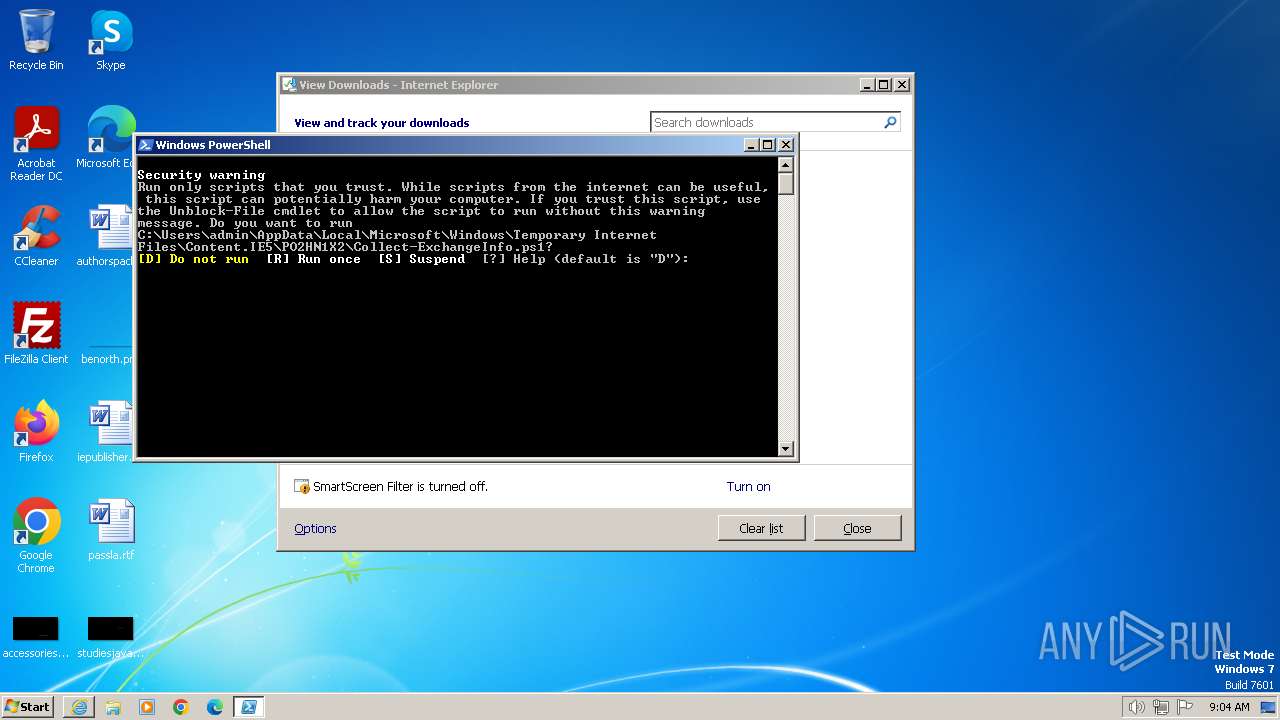
Starts POWERSHELL.EXE for commands execution
- iexplore.exe (PID: 116)
SUSPICIOUS
The process executes Powershell scripts
- iexplore.exe (PID: 116)
Reads the Internet Settings
- powershell.exe (PID: 956)
INFO
Application launched itself
- iexplore.exe (PID: 116)
The process uses the downloaded file
- powershell.exe (PID: 956)
- iexplore.exe (PID: 116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/jpmessaging/CollectExchangeInfo/releases/download/v2023-09-05/Collect-ExchangeInfo.ps1" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 956 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Collect-ExchangeInfo.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2032 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:116 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 606
Read events
17 488
Write events
118
Delete events
0
Modification events
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
19
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:827D6C2E9EDB19DD12C92A2F5AB48790 | SHA256:434AC6AA3CF8016632333B7CC3891EB842C1062C0B604461189055658A3C0B2C | |||
| 956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1Q19H61P7GT7JICJY2XT.temp | binary | |
MD5:F500255BDC0DD45A0934243E38529D10 | SHA256:AD4304402753CEF71770C63692428001309617BDA00D87E229D197721D29496E | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:FD024718351D004FA1F6A1E1EA47DB9E | SHA256:C062660363F181B0C43C9E82904EA2F778F422F08F978DCFAEE148A788D2B092 | |||
| 116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Collect-ExchangeInfo.ps1 | text | |
MD5:B64E19B6B41542ACCB624E8A2EE4F797 | SHA256:49D93D4DC4D2F52400074AF348E704752979FF0728A6B0D64C9C27413446E2D4 | |||
| 116 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE5C7B79A083F3E2A.TMP | binary | |
MD5:BD60B399092029FA6EFC537EE295033B | SHA256:3AA80213F16711C627D0AC27687335A0D26461DCF9E448D19A9F6CFFA5D9AF8A | |||
| 116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{6DAF8A2F-ABA9-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:60D73175842E470A94749FC5DCF92F33 | SHA256:007F89F1D81507311B99D17B53271675A50FE47B57B6C041D011BF1AA2FB51CE | |||
| 956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\raxzv2gj.ta4.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFe2007.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:91D8D3D70EA558869EC9FD095D9A0FFE | SHA256:28EBF9F77C385FA4F63216D47A7C380238C0A5DA291A6FAC104247E07F744226 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
18
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | iexplore.exe | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6243fee378382ed7 | unknown | compressed | 4.66 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f6bf34dbb61e71d7 | unknown | compressed | 4.66 Kb | unknown |
2032 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
2032 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 312 b | unknown |
2032 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 304 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a414549a770d7263 | unknown | — | — | unknown |
116 | iexplore.exe | GET | — | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
116 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | unknown | binary | 779 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2032 | iexplore.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
2032 | iexplore.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2032 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2032 | iexplore.exe | 185.199.111.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
116 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |